Extension defense method based on network intrusion
A network intrusion and network technology, applied in the field of extended defense based on network intrusion, can solve the problem that the intruder's behavior, motivation, method and source cannot be fully obtained, and achieve the effect of delaying the intrusion time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
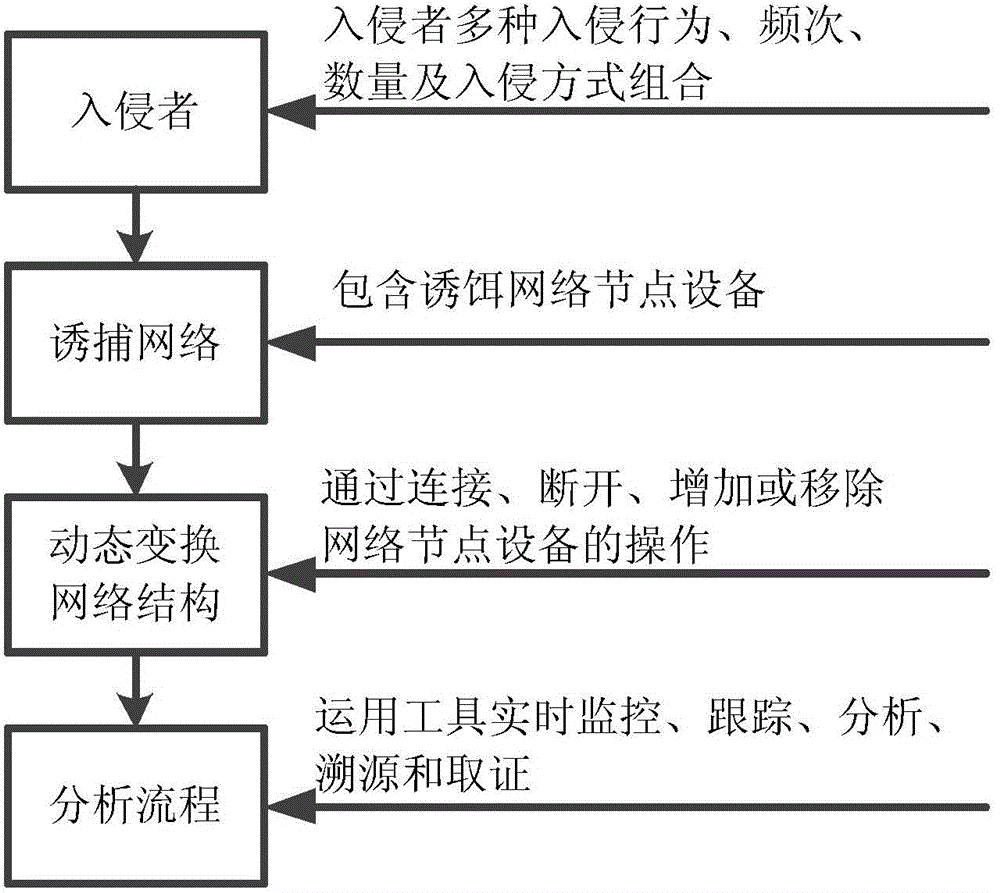
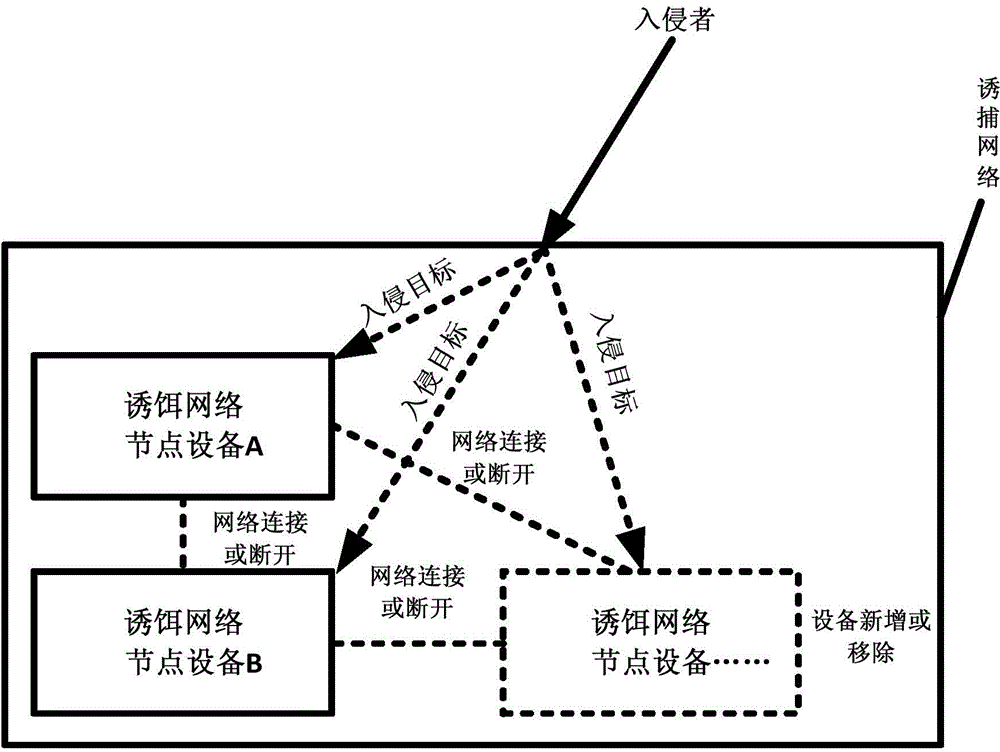
[0020] The specific implementation of the present invention can be realized in multiple ways, combining figure 1 with figure 2 As shown, those skilled in the art can complete the deployment and implementation of the method through the following steps:
[0021] 1. Establish a decoy network, and deploy decoy network node device A, decoy network node device B or possible decoy network node devices...;
[0022] 2. In response to various intrusion behaviors taken by intruders, the trapping network and its decoy network node equipment have the defect of being invaded and attacked. The methods include but are not limited to:
[0023] Make the decoy network, decoy network node equipment A, B or possible decoy network node equipment... have one or several obvious network vulnerabilities, system vulnerabilities, software vulnerabilities, improper application configuration, false sensitive information or weak / no password ;
[0024] 3. According to the actual situation of the intruder...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com