Intrusion detection method of radio frequency identification system based on ontology
A radio frequency identification system and intrusion detection technology, applied in the transmission system, electrical components, etc., can solve the problems of reducing the reading rate of the card reader, difficult to implement, and unable to develop known loopholes in radio frequency identification tags
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The specific flow of inference clone tag intrusion in this intrusion detection method is as follows:
[0048] Step 1: Analyze and process the data in the audit records, complete the preliminary analysis of the read and write data in the RFID system, and set the following detection rules according to the data records included in the audit:
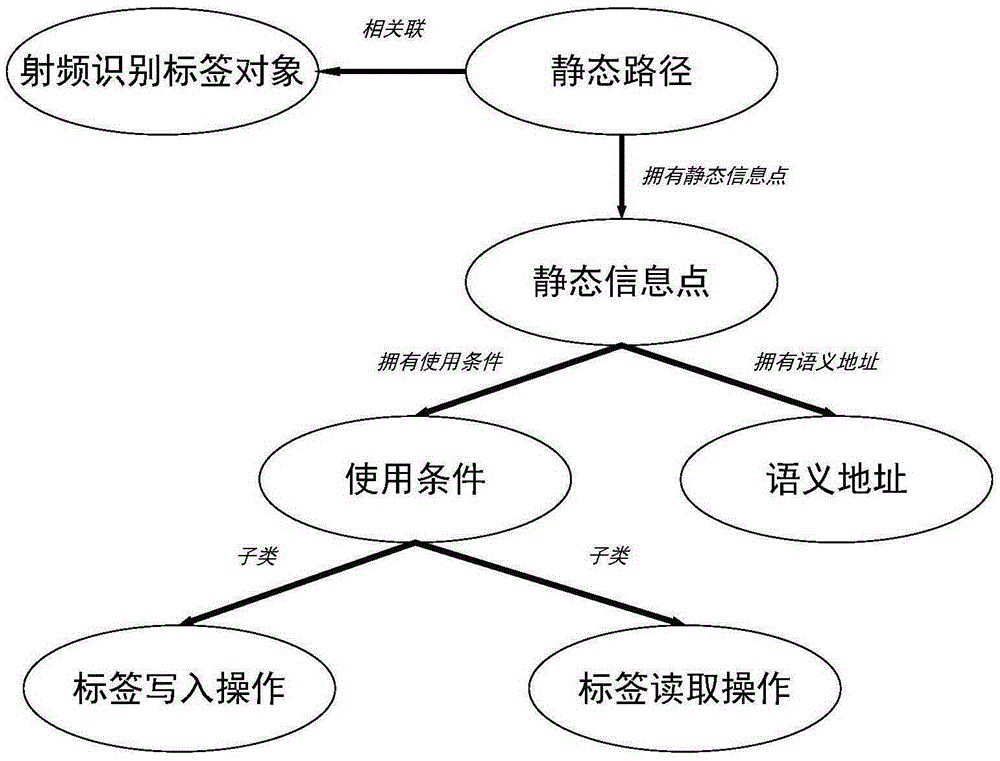
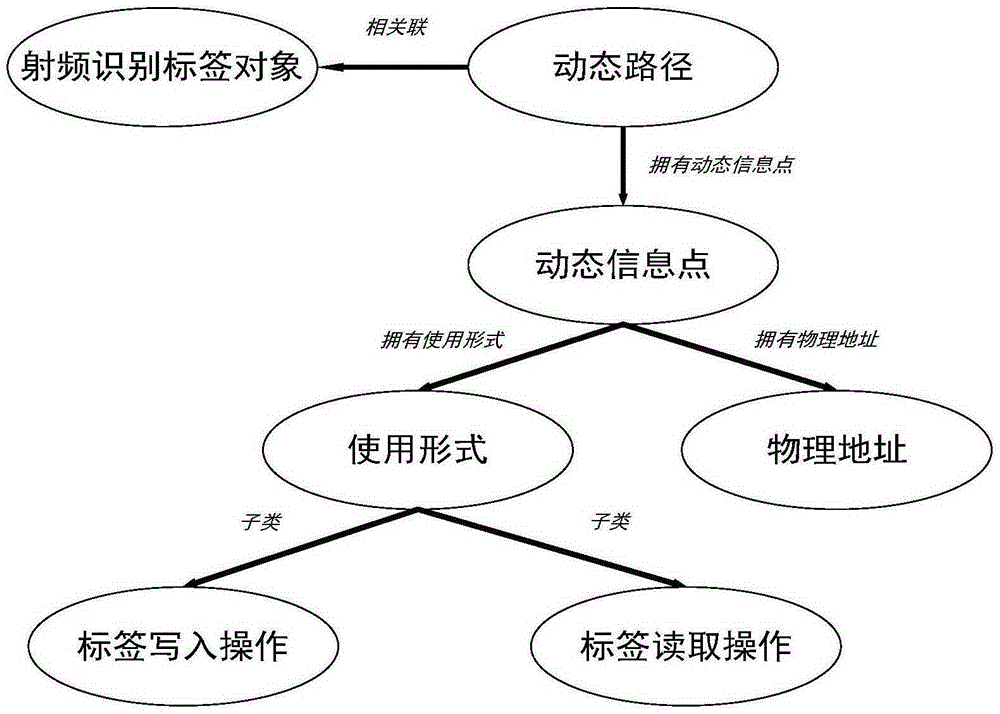
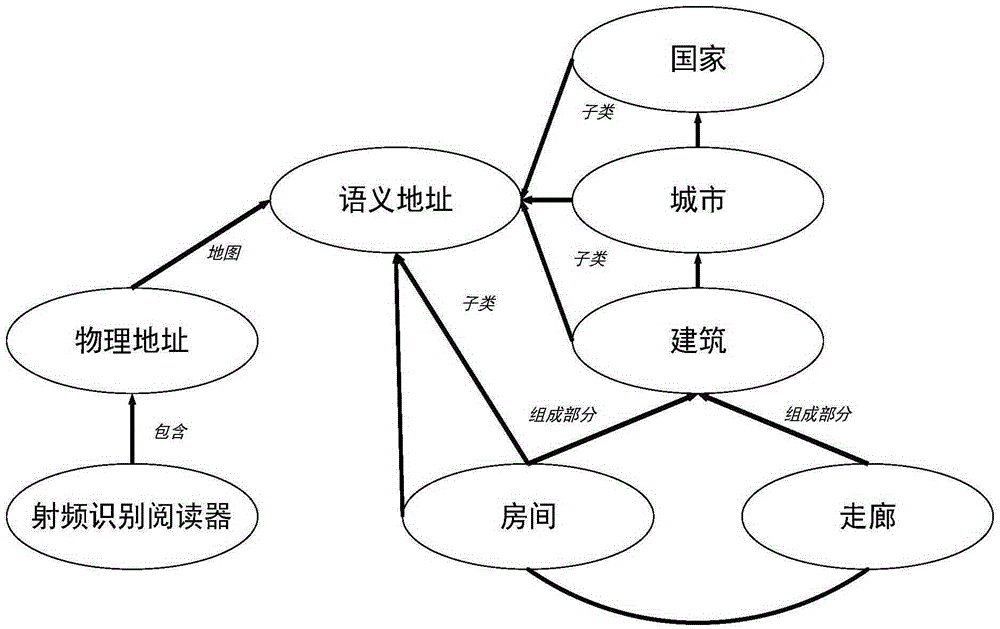
[0049] 1) Determine the physical address of the tag that is close to the radio frequency identification reader and has performed read and write operations,
[0050] 2) When the detected physical address does not belong to the original information point, add a new dynamic information point. This new information point also needs to be characterized by the usage form and related timestamp extracted from the audit record treatment;
[0051] 3) When the detected physical address belongs to the existing information point, update the existing dynamic information point in time, but at this time a new read and write operation has been comple...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com