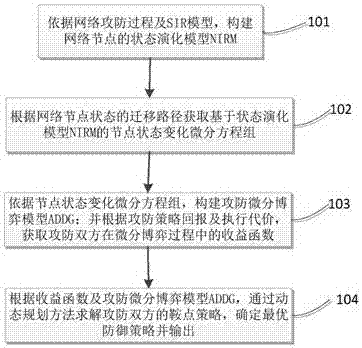
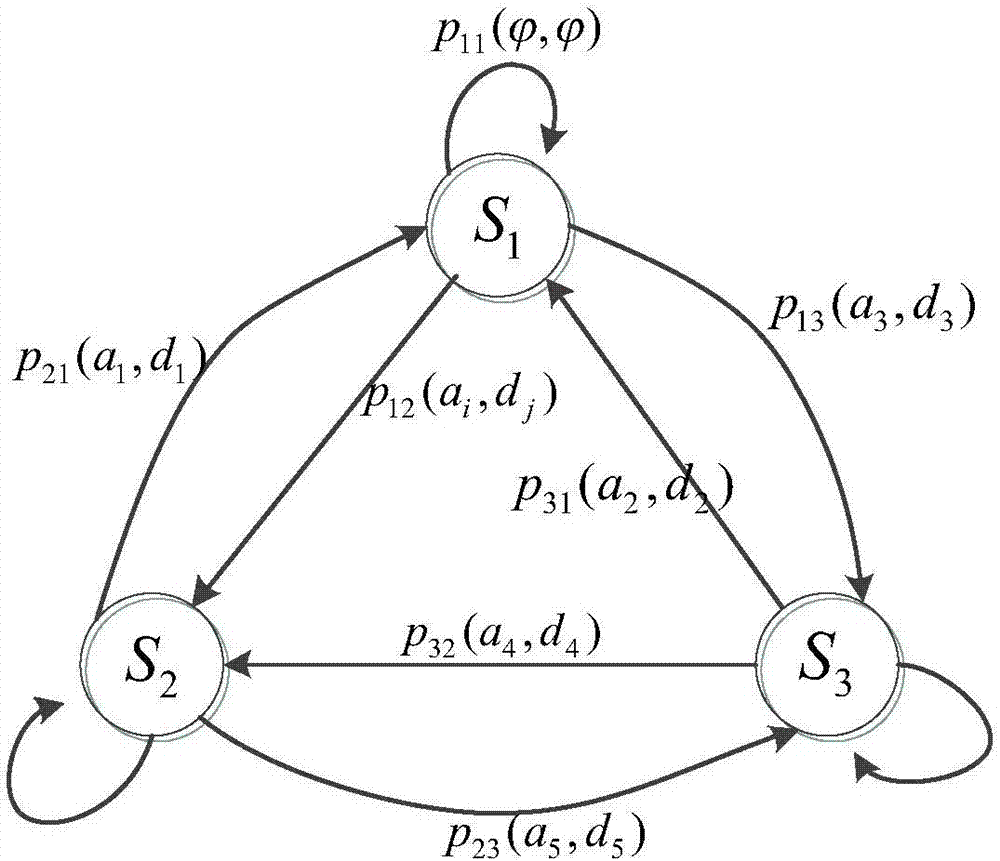
Attack and defense differential game-based network security defense decision determination method and device
A technology for determining methods and network security, applied to electrical components, transmission systems, etc., can solve problems such as reducing the effectiveness of models and methods, and large differences
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] Network Attack-Defense: It mainly refers to the process in which both the offensive and defensive parties take certain measures to generate confrontation. The attacker chooses an attack strategy to attack the opponent’s network, so as to obtain the opponent’s information or even destroy the opponent’s network; Attack behavior, the defender will use various defense measures to carry out network security defense to minimize its own losses. Games: In certain environmental conditions, under certain rules, some individuals or organizations select their own strategies from their respective optional strategy sets and implement them at the same time or successively, one or more times, and finally obtain processes with corresponding results. Nash Equilibrium: In the game G={S 1 ,...,S n ; u 1 ,...,u n}, a certain strategy combination composed of each strategy of each player In , the strategy of any player i If the conditions are met: for any s ij ∈ S i are establishe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com