Network defense method and device
A technology for network and business requests, applied in the field of network security, can solve the problems of single protection method, long-lasting effect, manslaughter, etc., and achieve the effect of improving the scope and level of security defense, and preventing robot access and malicious access.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 2
[0093] 10.6.183.75(Client)->10.6.183.95(Proxy)->10.6.183.96(Server)
[0094] 2) The client accesses the server through the external network
example 3
[0097] 202.106.139.5(Client)->10.6.183.96(Server)
[0098] 3) The client accesses the server through a proxy
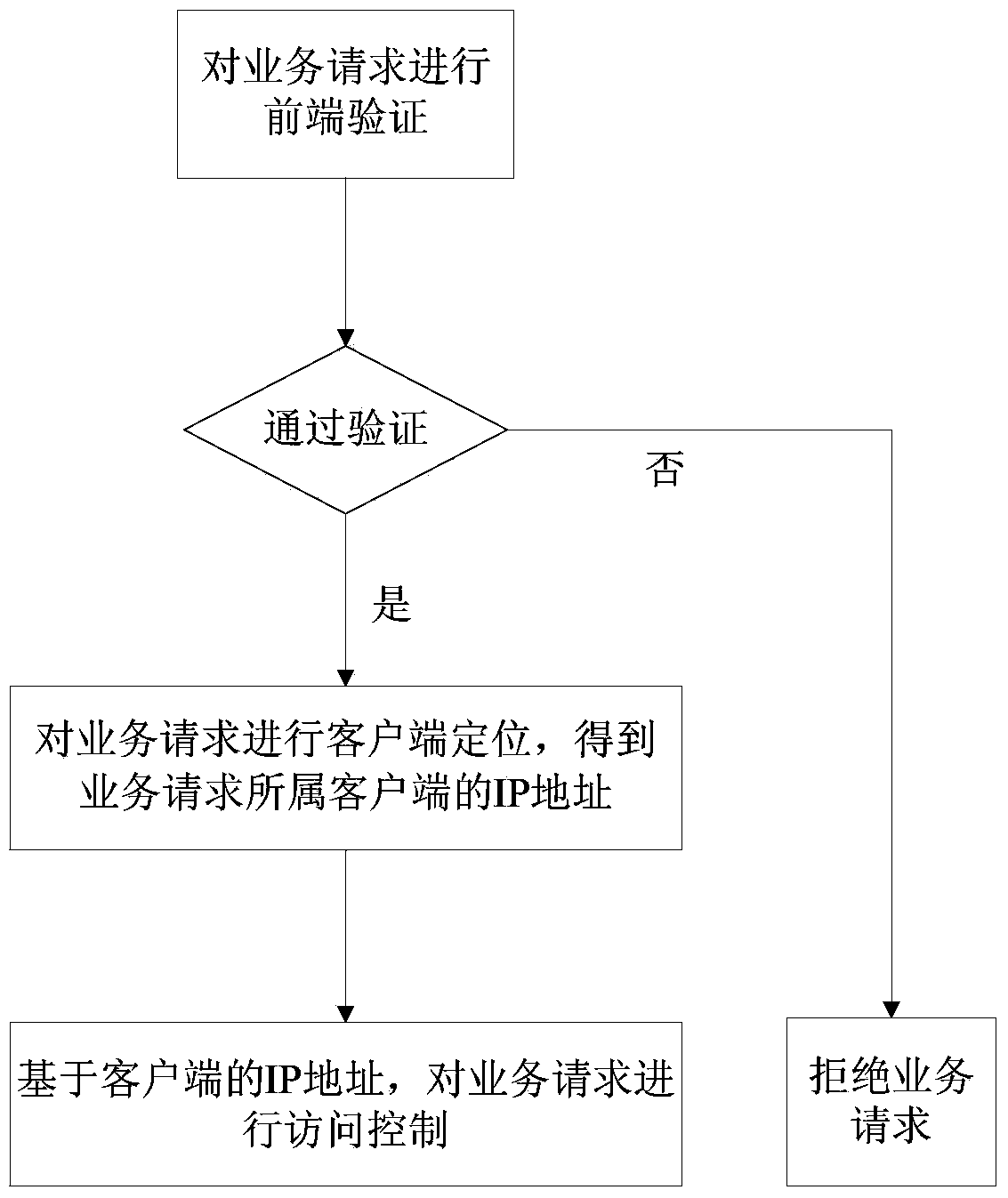
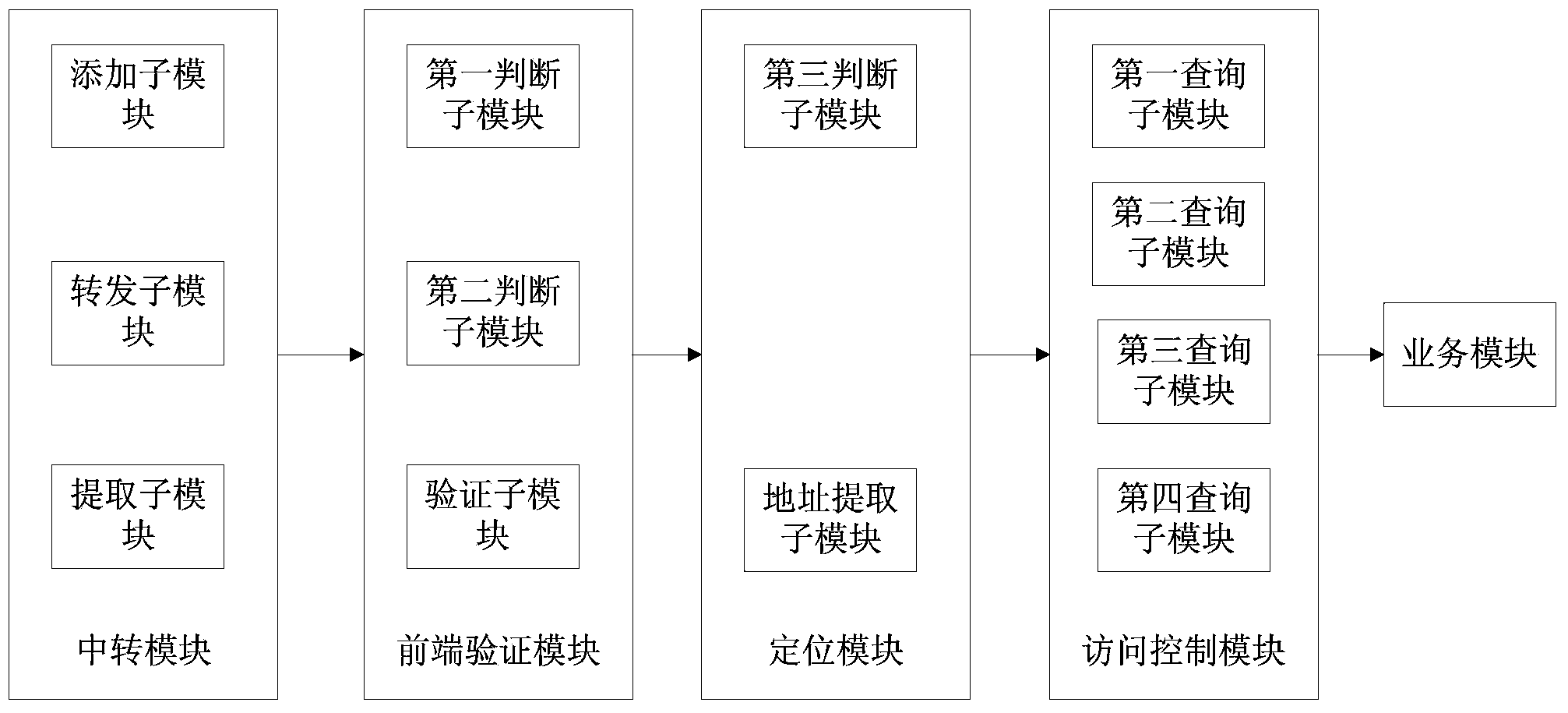
[0099] It is also a more access method for the client to access the server through the proxy. When the client accesses the server through the proxy, it only obtains the IP of the proxy using request.getRemoteAddr(). Therefore, to accurately locate the actual IP of the client, it needs to be obtained from the request. getHeader("x-forwarded-for") to get the original proxied ip (that is, the first ip in the ip list), that is, to get the proxy information from the http header to locate the client ip, use this The method can also prevent the client from accessing the server by frequently switching agents. The following example 4-6 is an example of accessing the server by frequently switching agents:
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com