Active network defense method and system
A technology of active network and defense system, applied in transmission systems, digital transmission systems, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The above and other technical features and advantages of the present invention will be described in more detail below in conjunction with the accompanying drawings.
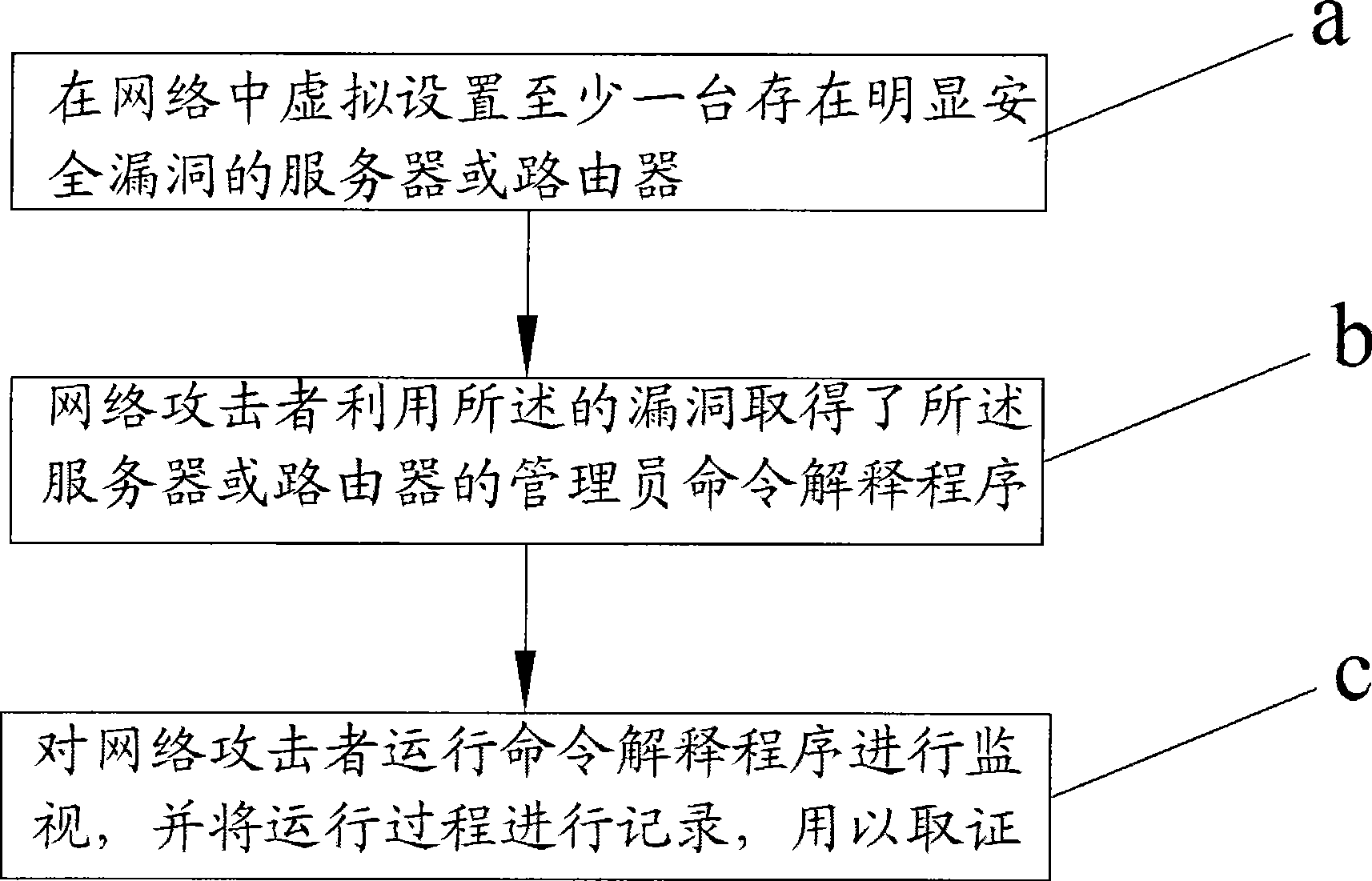
[0028] see figure 1 As shown, it is a flowchart of the active network defense method of the present invention, and the steps it includes are:
[0029] Step a: Virtually set up at least one server or router with obvious security holes in the network;
[0030] Step b: the network attacker obtains the administrator command interpretation program of the server or router by utilizing the vulnerability;
[0031] Step c: monitor the command interpretation program run by the network attacker, and record the running process for evidence collection.
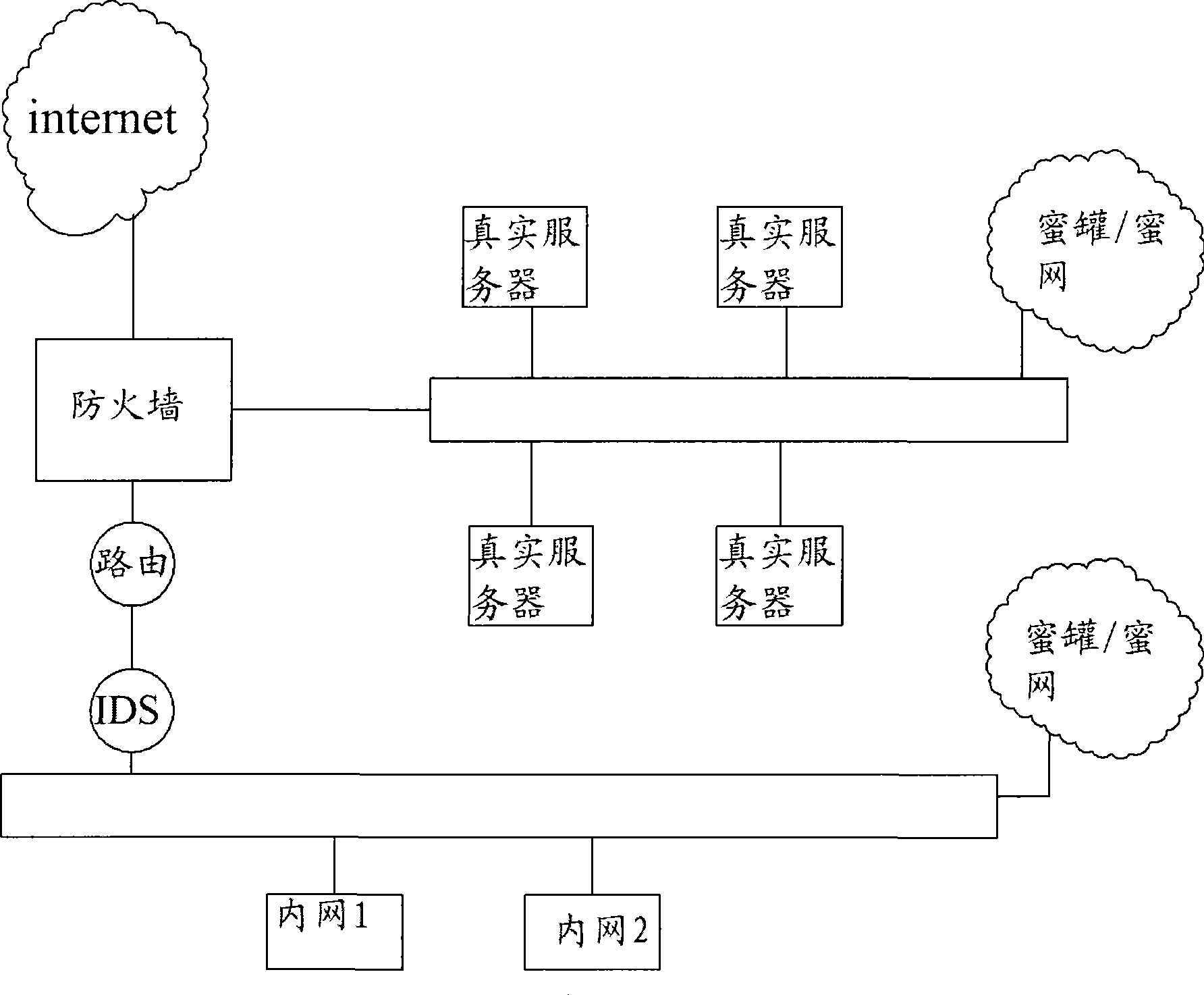
[0032] Wherein, the at least one server or router with obvious security loopholes set virtually in the network is the honeypot, and its most fundamental feature is a virtual service with loopholes intentionally left. These services are set up on a certain system. A...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com