Active network defense system for embedded equipment and defense method thereof
An active network and defense system technology, applied in transmission systems, electrical components, etc., can solve problems such as ARP spoofing, replay attacks, and inability to accurately judge network messages, and achieve convenient and flexible use, high accuracy, and security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
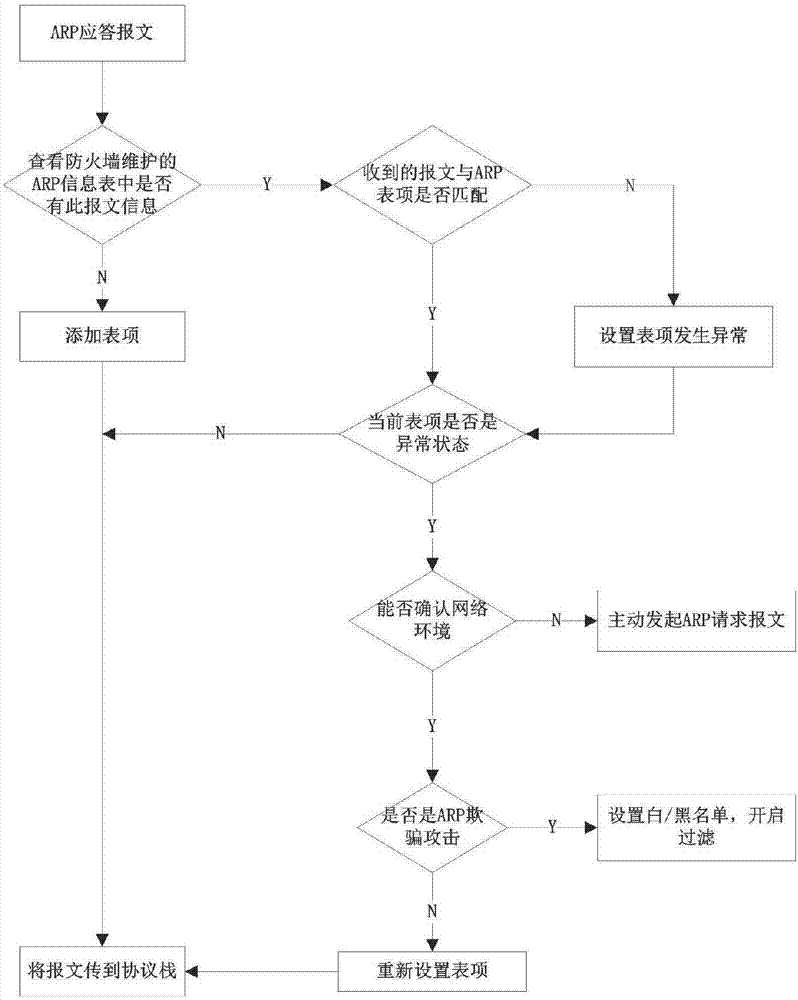
[0046] Example 1: as image 3 As shown, for ARP spoofing, the specific steps of the defense method of the active network defense system of the present invention are as follows:
[0047] 1. An ARP information table will be maintained within the system. When an ARP reply message is received, it will first detect whether there are relevant entries in the current table. If not, add it to it, and let the message pass the detection and pass it to the protocol stack.
[0048] 2. If there is an entry, it will be judged whether the content of the currently received message is consistent with the description of the entry. If they are consistent, go to step 3 to determine whether the current entry is in an abnormal state. If it is inconsistent, the current entry flag will be set, indicating that an exception occurs and the same goes to step 3.
[0049] 3. When detecting the abnormal state of the entry, if the flag bit shows that it is not abnormal, the message will be passed directly ...
Embodiment 2
[0065] Example 2: as Figure 4 As shown, for network storm, SYN flood attack, the defense method of the active network defense system of the present invention, the specific steps are as follows:
[0066] 1. First receive the network packet and judge whether it is a broadcast packet. If it is a broadcast packet, go to the next step. If it is not a broadcast packet, further judge whether there is an IP packet header. If there is an IP packet header, go to the next step. The IP packet header determines that the current packet is allowed to pass;
[0067] 2. Set the detection flag bit according to the message type, and determine whether there is this device information in the device information table, if not, create a new device entry information and then go to the next step, if there is, go directly to the next step;
[0068] 3. Make a corresponding cumulative count judgment according to the flag bit, and judge whether the number of received packets in one second is greater than...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com