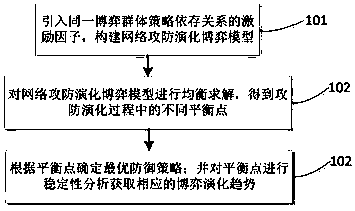
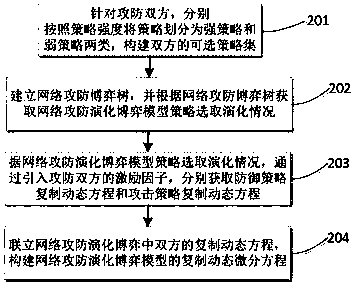
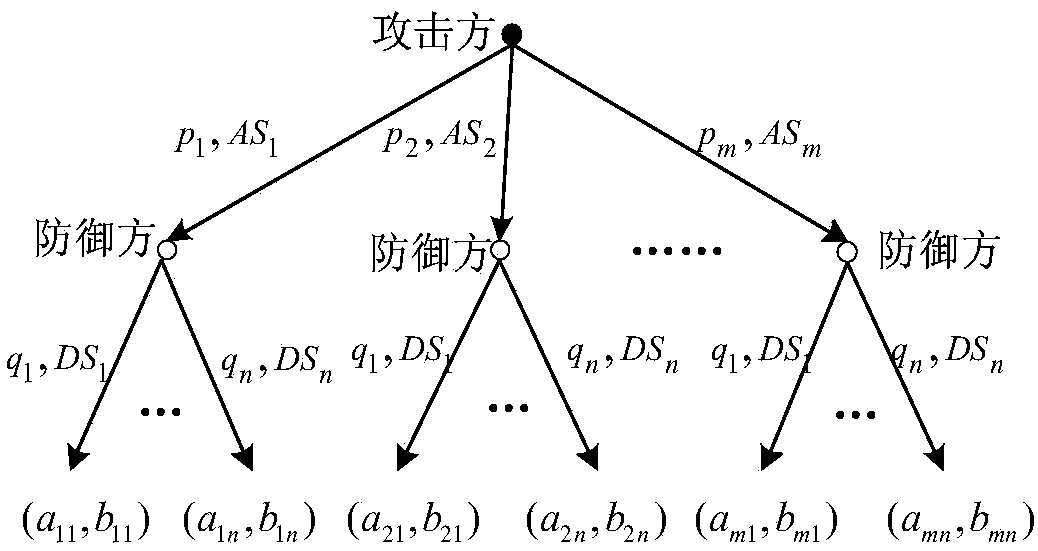
Attack and defense evolutionary game analysis based network defense action decision method
An evolutionary game and decision-making method technology, applied in the field of network security, can solve problems such as ignoring dependencies, failing to consider attack-defense dependencies, reducing the effectiveness and accuracy of models and methods, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to make the objectives, technical solutions and advantages of the present invention clearer and more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
[0032] The technical terms involved in the examples are explained as follows: Evolutionary Game Theory: Evolutionary GameTheory originated from Darwin's theory of biological evolution, inheriting the biological theory of species evolution, starting from the condition of individual bounded rationality, and taking group behavior as the research object In explaining the development process and evolutionary selection of biological species, it explains the evolutionary game process of biological behavior. Through long-term trial and error, imitation, and improvement, all game players will tend to a stable strategy, which may be stable for a long time in the group organization. This stable strategy equilibrium is very sim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com