A method and system for storing copyright event authentication based on block chain
A copyright and event technology, applied in the information field, can solve the problem that the record of the certificate is easy to be tampered with or destroyed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] As mentioned above, the server of a single work service provider to store copyright events is actually a centralized data storage method, and the centralized data storage method naturally has the disadvantage that the data is easily tampered with or destroyed .
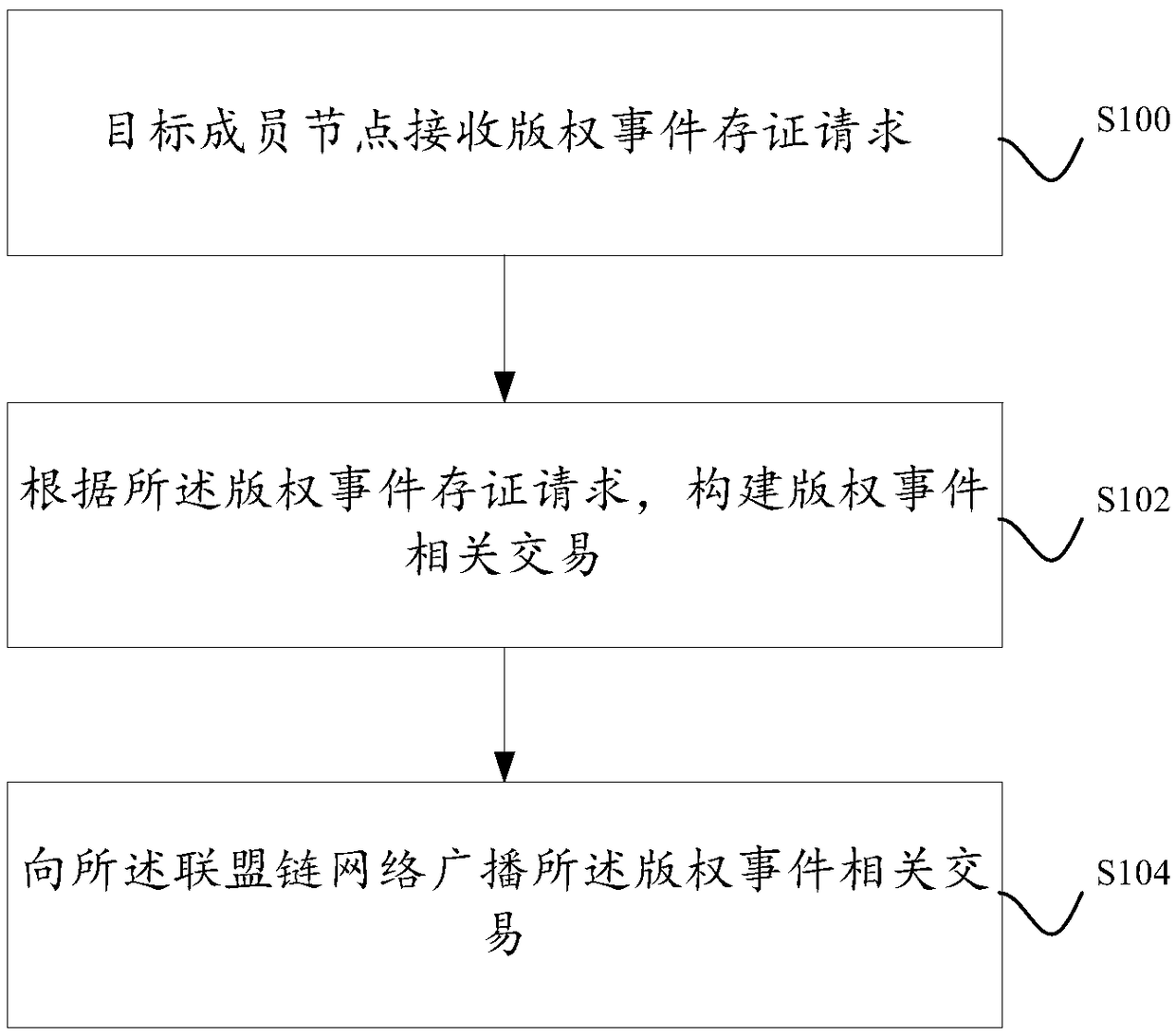
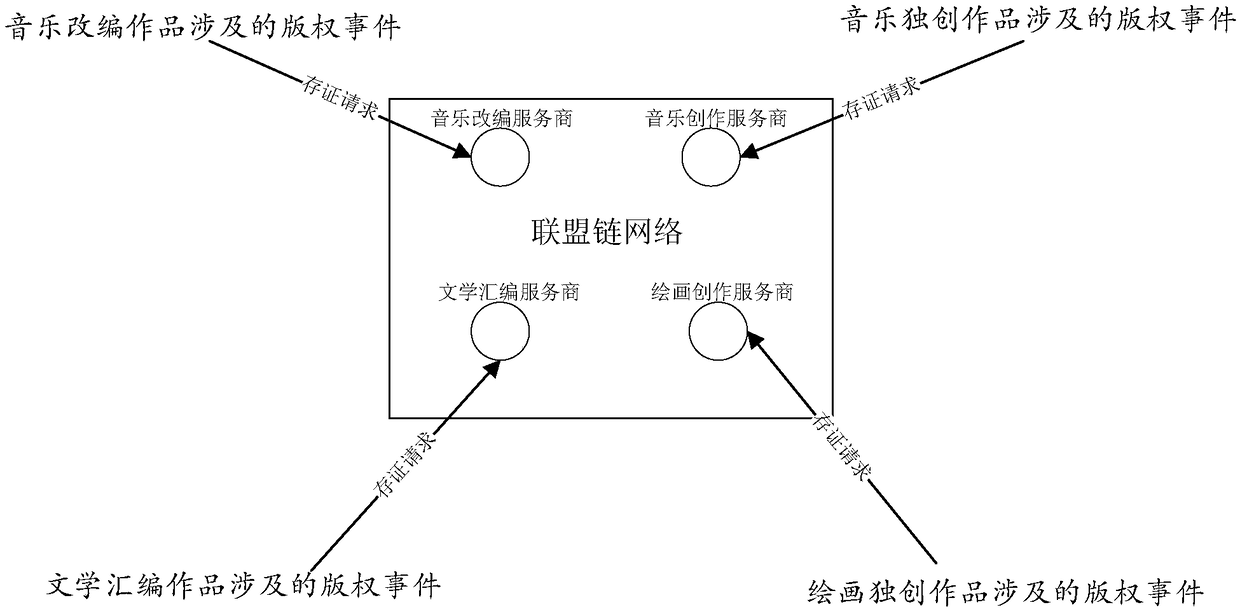
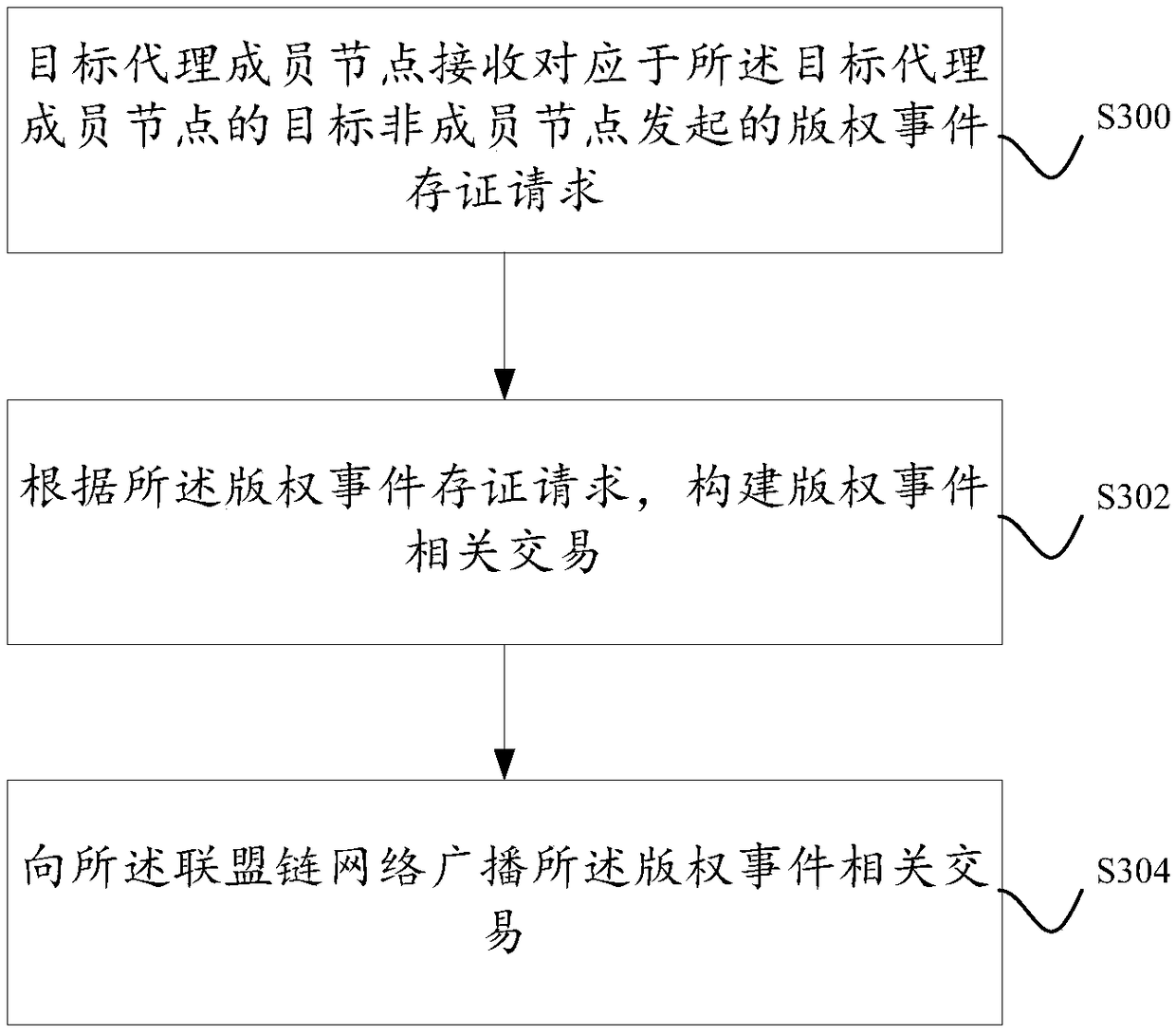
[0030] In order to deal with this disadvantage, in one or more embodiments of this specification, the devices of several work service providers are used as member nodes to form a consortium chain network, so that the work service provider corresponding to any member node in the consortium chain network can Upload the event-related information of the copyright event that you have monitored to the blockchain network in time for deposit. Since the data in the blockchain is non-tamperable and non-destroyable, the certificate records of copyright events are also non-tamperable and non-destroyable.
[0031] In addition, in practice, the copyright events monitored by the work service provider are usually generated ba...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com