A Design Method of Trust Chain Based on SM9 Cryptographic Algorithm
A design method and cryptographic algorithm technology, applied to key distribution, can solve the problems of configuration register reset, single definition of trust chain model, and increase the complexity of application process, so as to improve efficiency, ensure security and credibility, protect integrity and authenticity effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
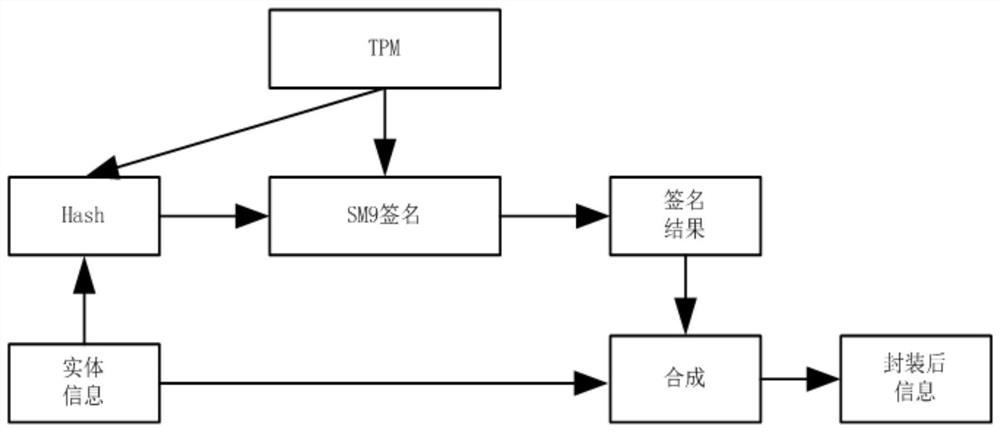
[0030] A new trust chain design method based on the SM9 cryptographic algorithm, the design process is as follows:
[0031] 1) Initialization
[0032] TPM chip factory initialization settings, according to the algorithm process of SM9, set the public parameters of SM9 key generation, signature algorithm, and verification signature algorithm;
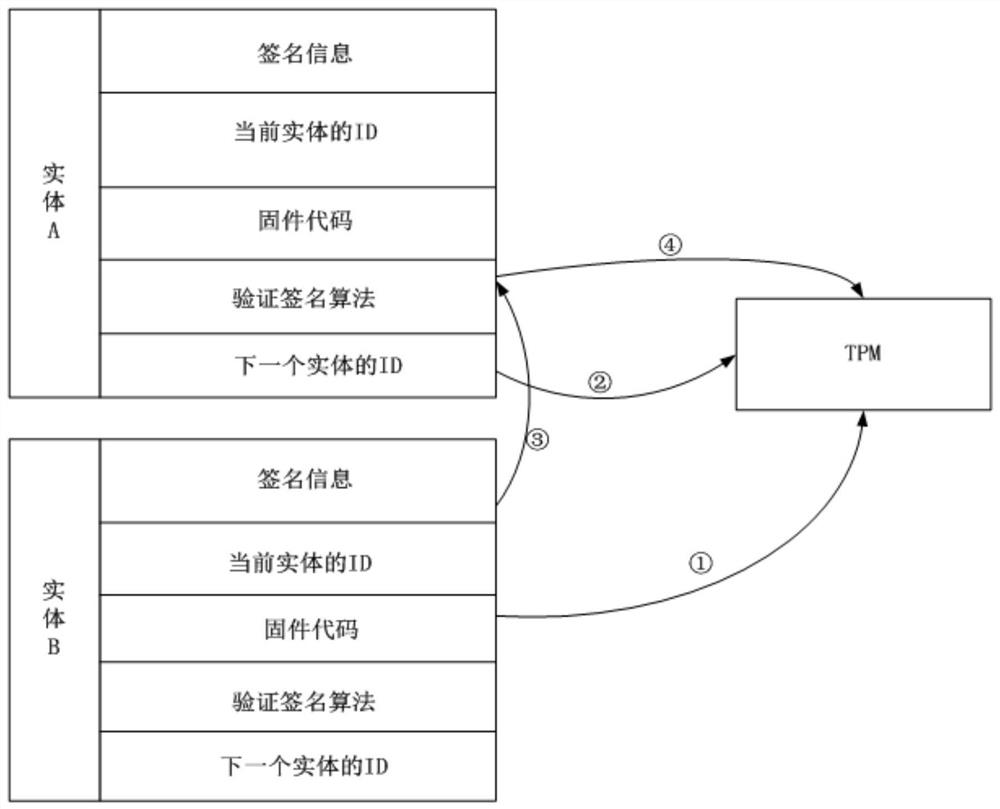
[0033] 2) Create a key mapping table
[0034] TPM is used as the trusted center key generation center KGC, and the identity of a single component on the trust chain is marked as ID i , record the trusted path from the trusted root to the ordered node sequence of the module whose signature is currently being verified as IDT=(ID 1 , ID 2 ,...ID n ), before loading each component, the verifier first...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com