Embedded system and implementation method of secure operating system
A security operating system and embedded system technology, applied in the direction of memory address/allocation/relocation, etc., can solve problems such as the limitation of protection function, and achieve the effect of ensuring security and reliability and ensuring system security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
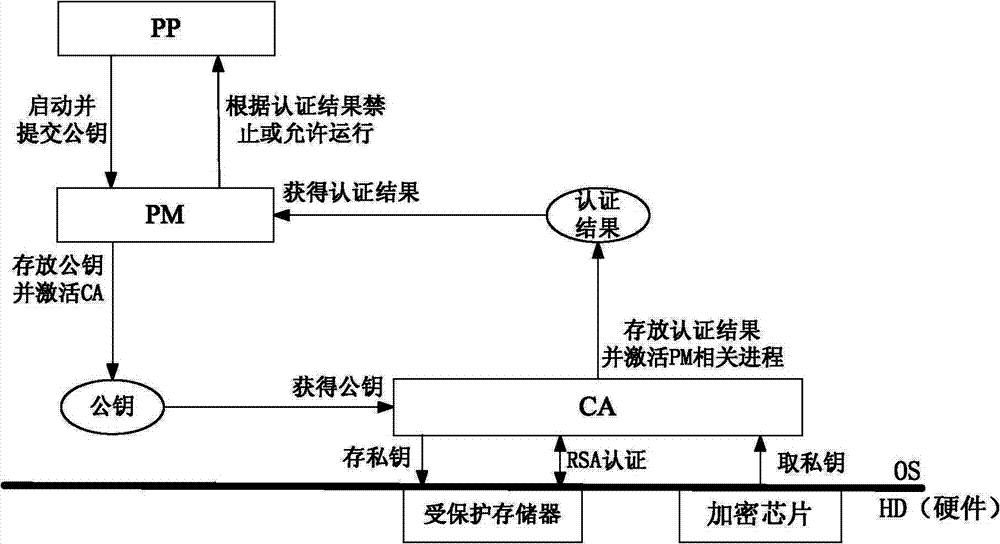
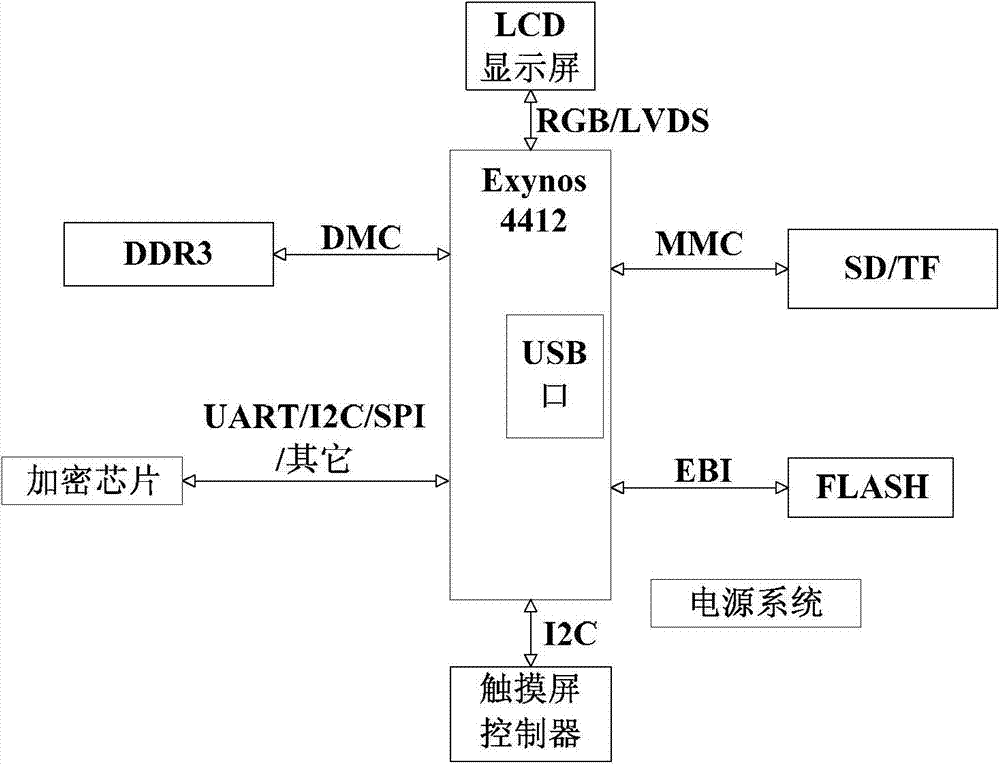
[0046] Such as Figure 1-2, a method for implementing a secure operating system, in which an encryption chip that supports the RSA asymmetric encryption algorithm and can provide a 2048-bit private key and a protected non-volatile memory are set in the hardware system; the memory is FLASH memory;
[0047] On the basis of the Linux operating system, the process (PP) carrying the public key is authenticated based on an asymmetric encryption algorithm. If the authentication is passed, the process management module (PM) of the operating system allows the process to continue running. If the authentication fails, the process The management module (PM) prohibits the process from running;
[0048] The authentication process is:
[0049] 1): The process (PP) carrying the public key is started by the process management module (PM), and the public key is submitted to the process management module, after which the process carrying the public key enters a waiting state;
[0050] 2) Afte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com