Credible Agent based MT (Mobile Terminal) credible state monitoring method
A mobile terminal and credible technology, applied in the field of information security, can solve problems such as the powerlessness of measurement, failure to describe application program integrity measurement, and inability to reflect changes in the status of mobile terminals, so as to ensure efficiency and accuracy, and ensure security and credibility Effect
Active Publication Date: 2012-10-31
CHINA ELECTRIC POWER RES INST +3
View PDF3 Cites 16 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
[0004] However, there are still some deficiencies in improving the security protection capabilities of mobile terminals through the use of trusted computing: 1) Currently, the relevant specifications of trusted computing only define the integrity measurement in the process of trusted transfer from platform power-up to operating system loading, It does not describe how to measure the integrity of the application program after the system is booted, and cannot guarantee the security and credibility of the application program of the user's behavior on the mobile terminal; 2) the current trusted
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
 Login to View More
Login to View More PUM
 Login to View More
Login to View More Abstract
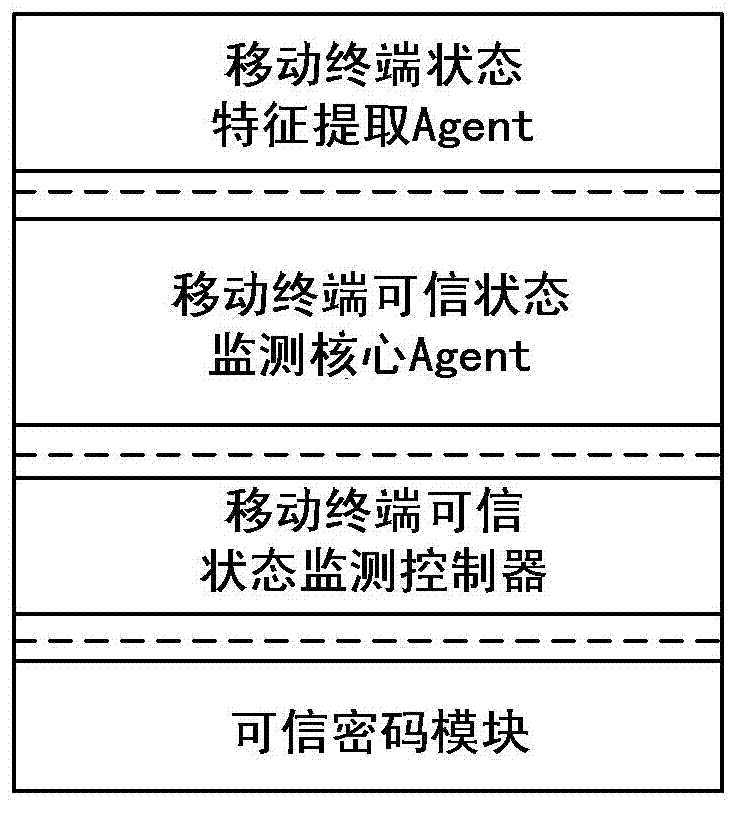
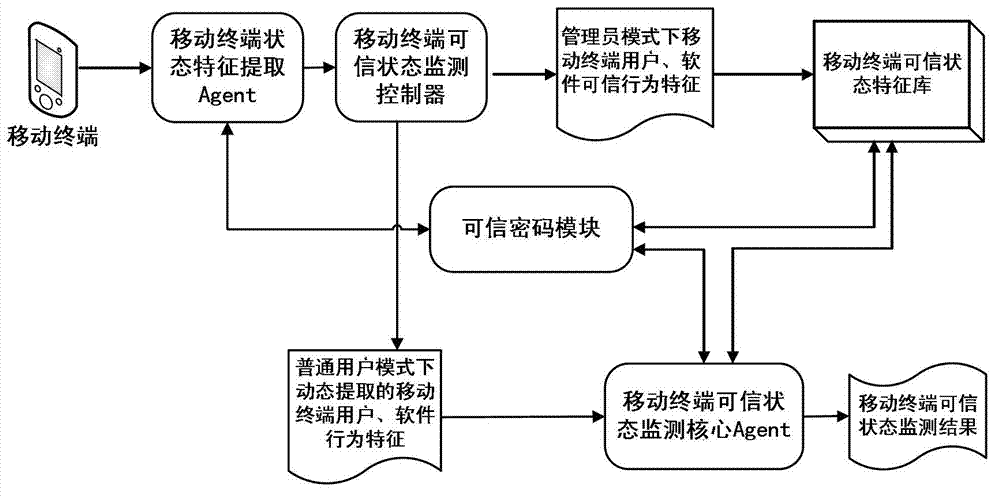
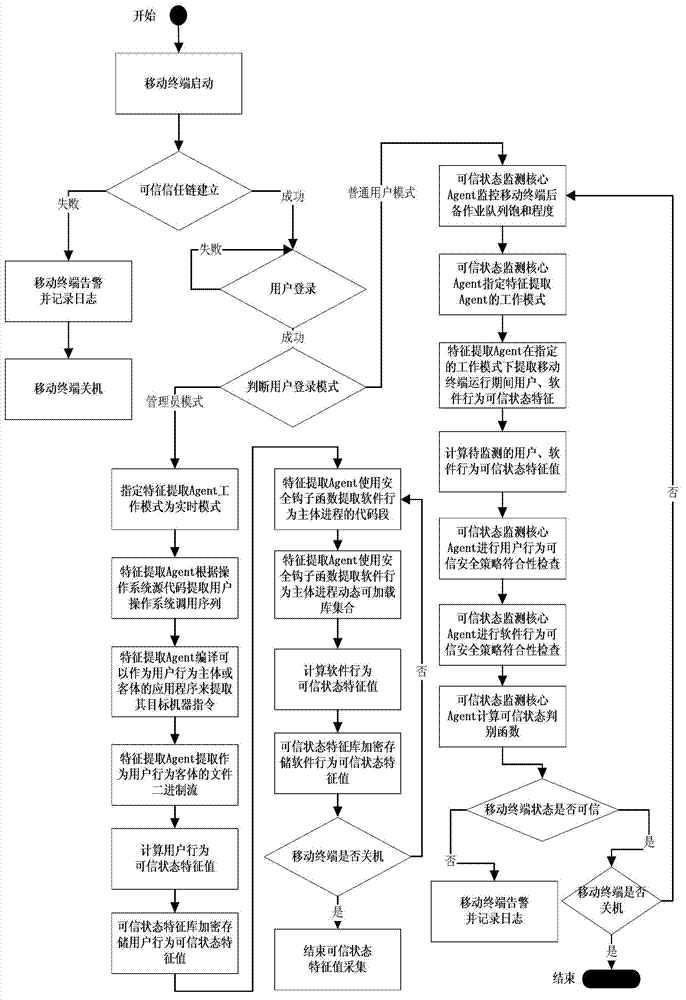
The invention provides a credible Agent based MT (Mobile Terminal) credible state monitoring method. The method comprises the steps of: (1) starting the MT mobile terminal credibly; (2) judging identity of a user at the MT; if the user is in a manager mode, turning to the step 3; and if the user is in a normal user mode, turning to step 4; (3) in the manager mode, extracting characteristics of the credible state of the MT; and (4) in the normal user mode, monitoring the credible state of the MT. The credible Agent based MT credible state monitoring method, disclosed by the invention, has the advantages of solving credible state monitoring problem of the MT during the running time, being capable of extracting characteristics of the credible state of user and software behaviors comprehensively and exactly during the running time of the MT, thereby efficiently judging the credible state of the MT, simplifying monitoring complexity of the credible state through introduction of the Agent technology and improving monitoring accuracy and monitoring efficiency of the credible state.
Description
technical field [0001] The invention belongs to the field of information security, and in particular relates to a method for monitoring a trusted state of a mobile terminal based on a trusted Agent. Background technique [0002] With the development of information networks, various mobile terminals such as mobile personal digital assistants (PDAs) and mobile smart phones have been widely used. and other problems, resulting in a large number of potential safety hazards in mobile terminals. Malicious codes such as viruses, worms, and Trojan horses attack the information network through the vulnerabilities of mobile terminals, making the network in an unsafe state. Whether the terminal has the password or key of the authentication protocol is used to determine whether it is connected to the network, ignoring whether the terminal system itself is safe and credible. This requires ensuring the information security of mobile terminals from the source. By using Trusted Computing (T...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): G06F21/00
Inventor 张涛林为民费稼轩陈亚东曾荣邓松邵志鹏楚杰陈牧徐敏
Owner CHINA ELECTRIC POWER RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com