Method and system for managing and controlling mobile medium access authority in domestic operating system
A technology of mobile media and operating system, which is applied in the field of computer security to achieve the effects of preventing loss, ensuring real-time performance, and ensuring safety and credibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
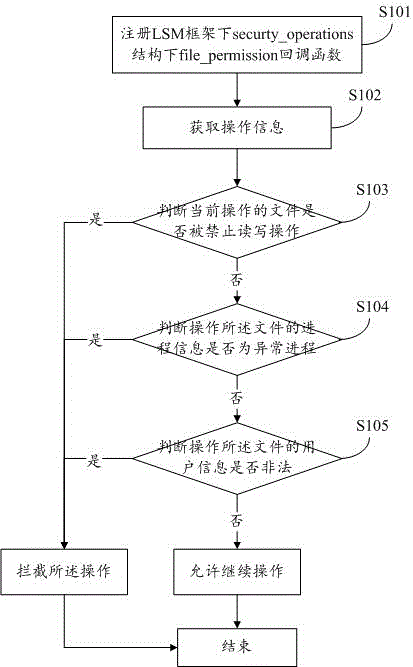
[0044] Embodiment 1 is the read and write permission control method in the present invention, which is used to control the data read and write permissions in removable media, because some malicious code injection usually needs to write or rewrite some parts in the file, and the purpose of injection has been achieved. At this time, the injection operation information can be obtained to intercept the operation. like figure 1 Shown:
[0045] S101: Register the file_permission callback function under the security_operations structure under the LSM framework;
[0046] S102: Obtain operation information, where the operation information is the file name of the currently operated file, process information for operating the file, and user information for operating the file;
[0047] S103: Determine whether the currently operated file is prohibited from reading and writing operations, and if so, intercept the operation; otherwise, execute S104;
[0048] S104: Determine whether the proc...
Embodiment 2
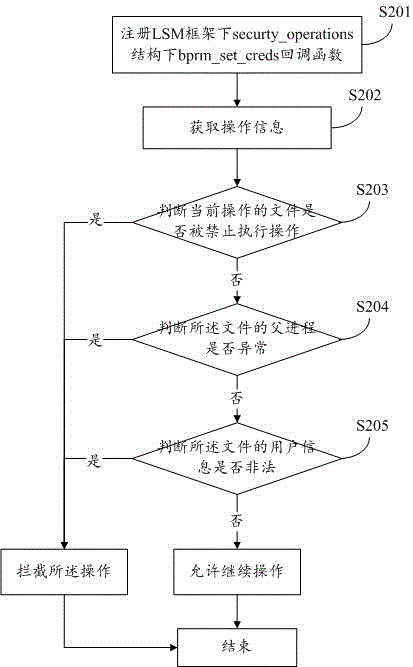
[0050] Embodiment 2 is the execution authority control method in the present invention, which is used to control the execution authority of files in removable media. This control method intercepts programs with malicious behaviors before the programs are executed to prevent harm caused by malicious codes. For some unknown executable programs, it has a very good killing effect. Such as figure 2 Shown:
[0051] S201: Register the bprm_set_creds callback function under the security_operations structure under the LSM framework;
[0052] S202: Obtain operation information, where the operation information is the file name of the currently operated file, process information of the file, and user information for operating the file;
[0053] S203: Determine whether the currently operated file is prohibited from performing operations, if yes, intercept the operation; otherwise execute S204
[0054] S204: Determine whether the parent process of the file is abnormal, if so, intercept ...
Embodiment 3
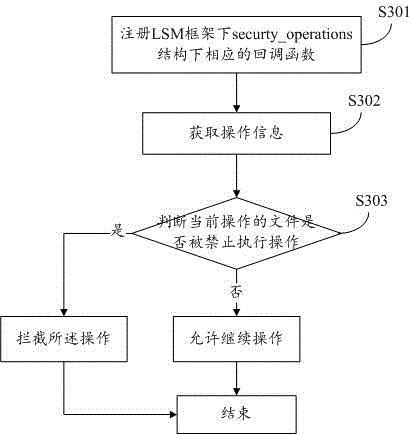
[0056] Embodiment 3 is a method for renaming permissions, deleting permissions or changing permissions in the present invention. Since the movement, change or deletion of some protected important files or directories may have a great impact on users, it is not allowed for some To change deleted files or directories, you need to control their corresponding permissions. Changing the execution permissions of executable files is generally a dangerous behavior that may cause serious consequences. Therefore, it is necessary to effectively control the behavior of changing permissions. Such as image 3 Shown:
[0057] S301: Register the corresponding callback function under the security_operations structure under the LSM framework; if it is a renaming permission, register the path_rename callback function; if it is a deletion permission, register the path_unlink and path_rmdir callback functions; if it is a permission change, register the inode_setattr callback function;
[0058] S3...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com