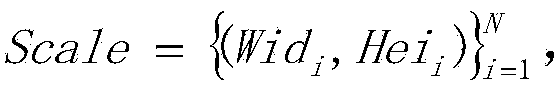Patents
Literature
249results about How to "Precise filter" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
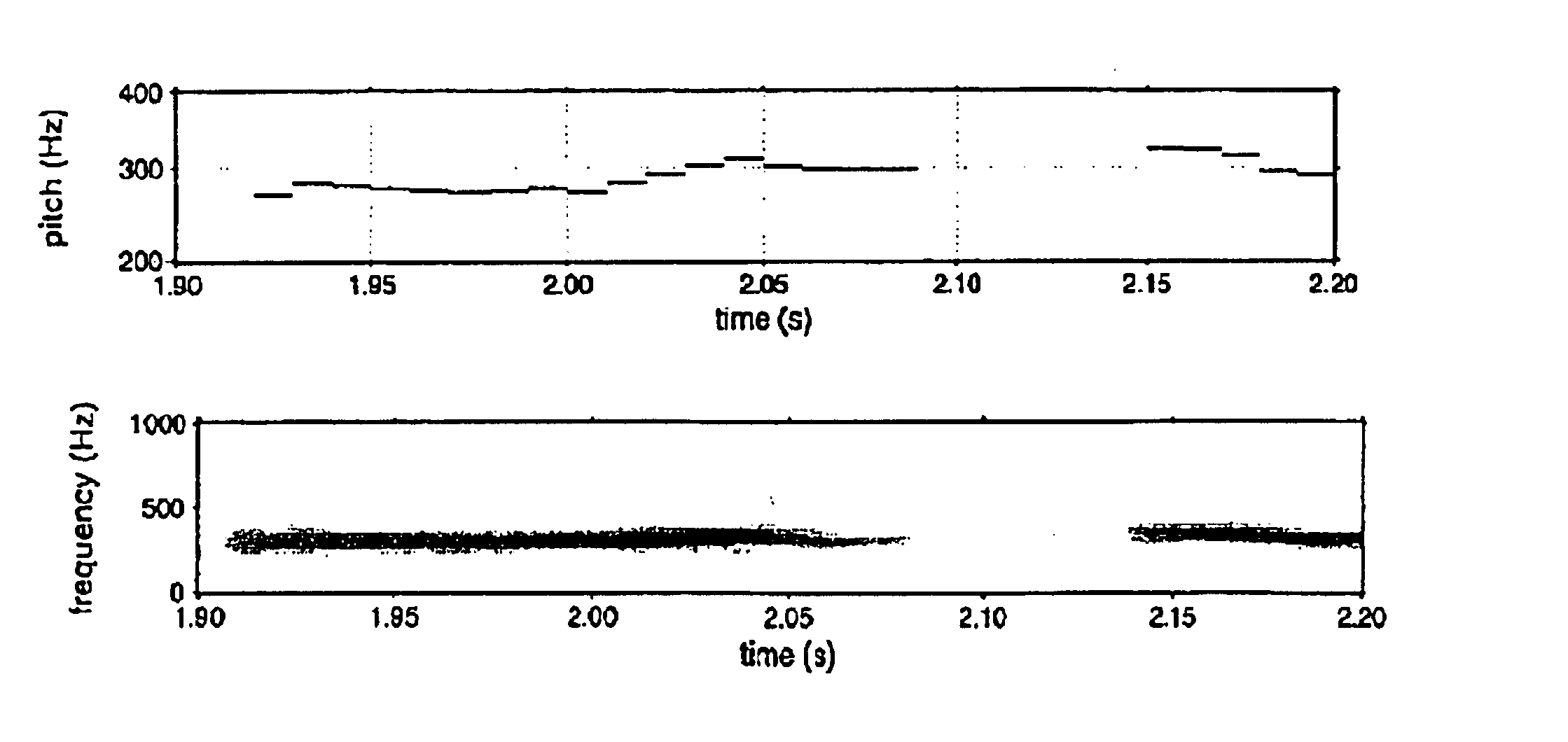
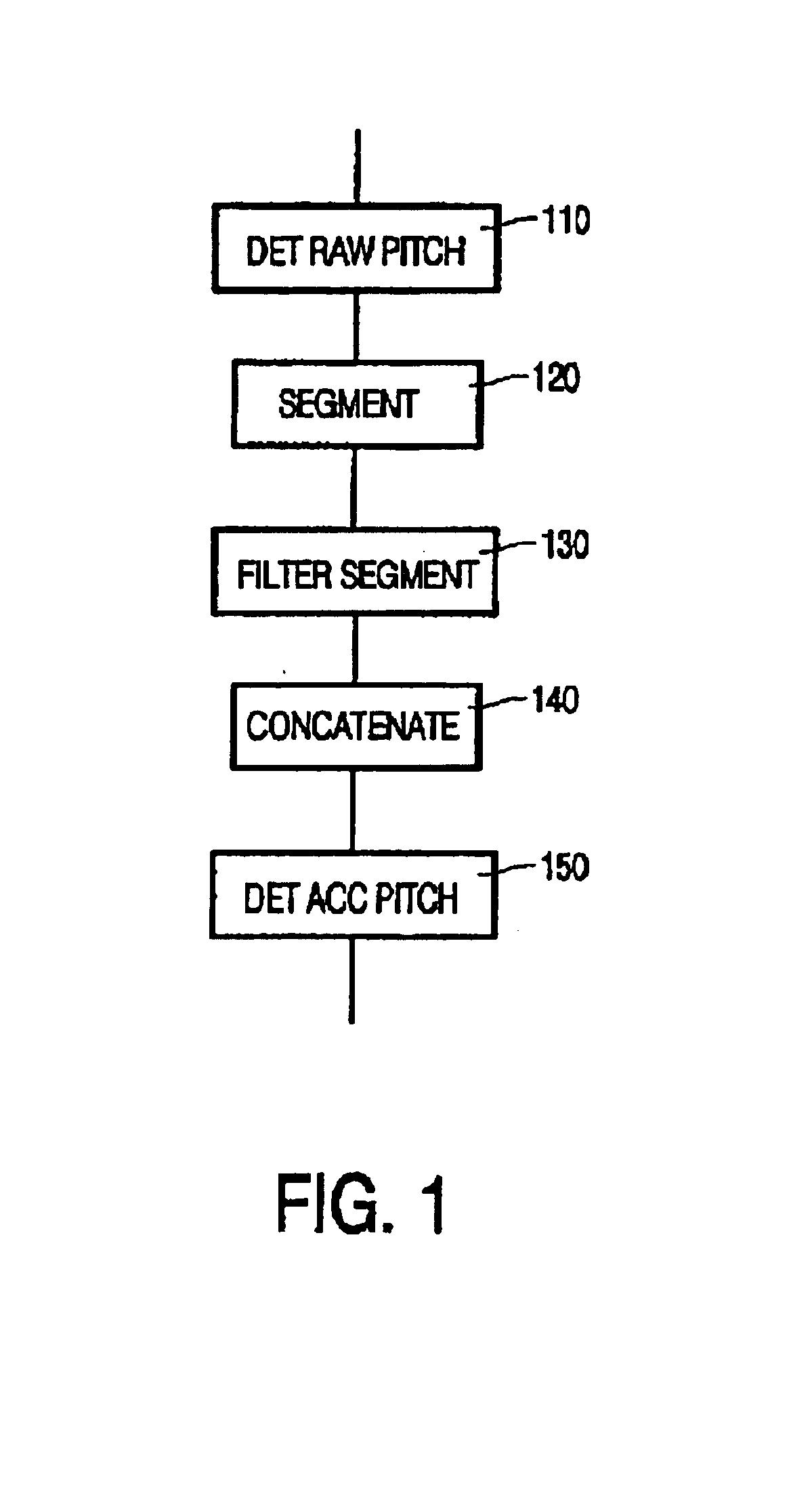
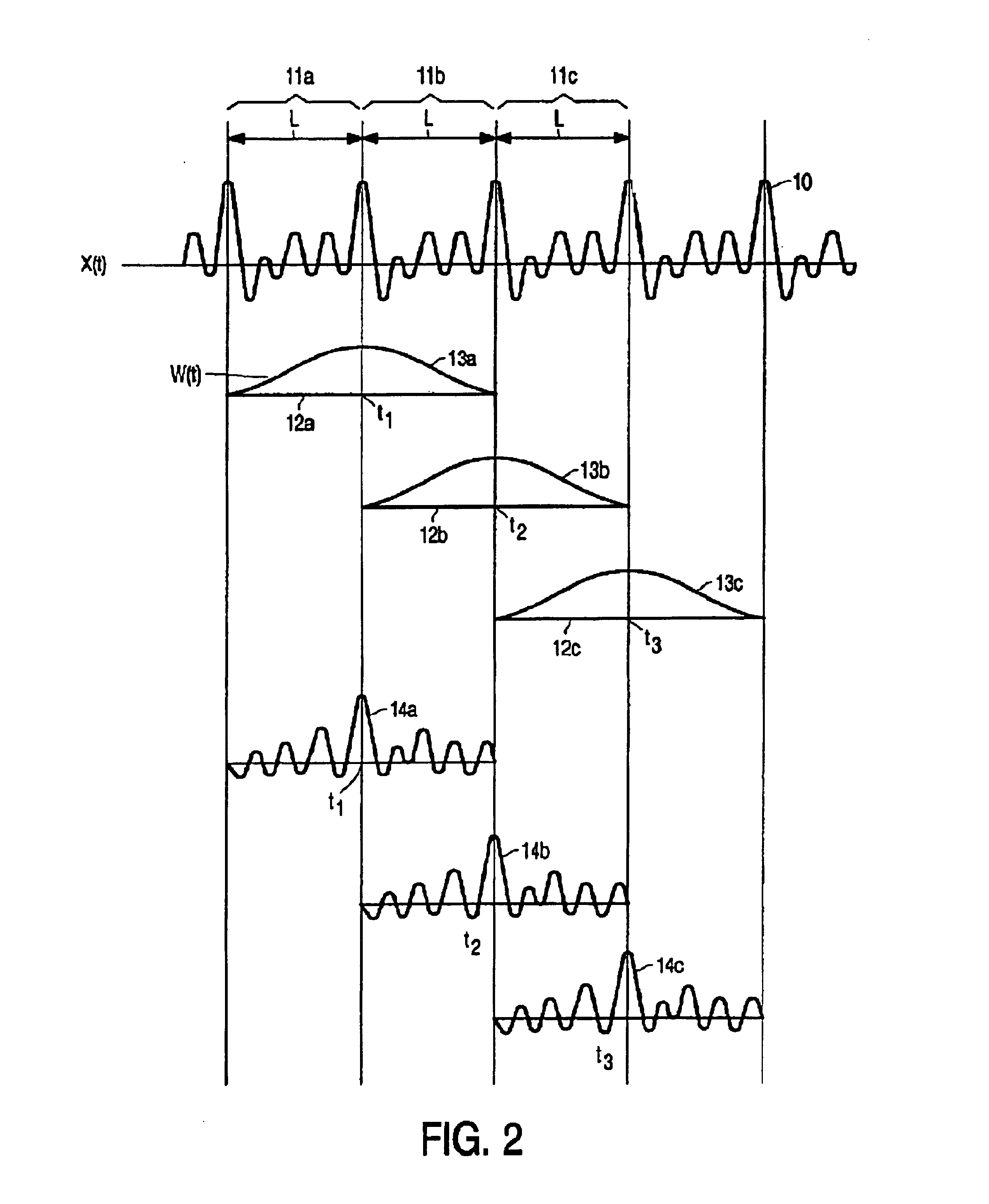
Refinement of pitch detection
InactiveUS6885986B1High resolutionPromote more developedSpeech analysisCode conversionEngineeringAudio frequency
Successive pitch periods / frequencies are accurately determined in an audio equivalent signal. Using a suitable conventional pitch detection technique, an initial value of the pitch frequency / period is determined for so-called pitch detection segments of the audio equivalent signal. Based on the determined initial value, a refined value of the pitch frequency / period is determined. To this end, the signal is divided into a sequence of pitch refinement segments. Each pitch refinement segment is associated with at least one of the pitch detection segments. The pitch refinement segments are filtered to extract a frequency component with a frequency substantially corresponding to an initially determined pitch frequency of an associated pitch detection segment. The successive pitch periods / frequencies are determined in the filtered signal.
Owner:NXP BV +1
Surround sensing system with telecentric optics
ActiveUS10183541B2Reduce the amount requiredAccurate detectionUsing optical meansResilient suspensionsBandpass filteringAngle of incidence
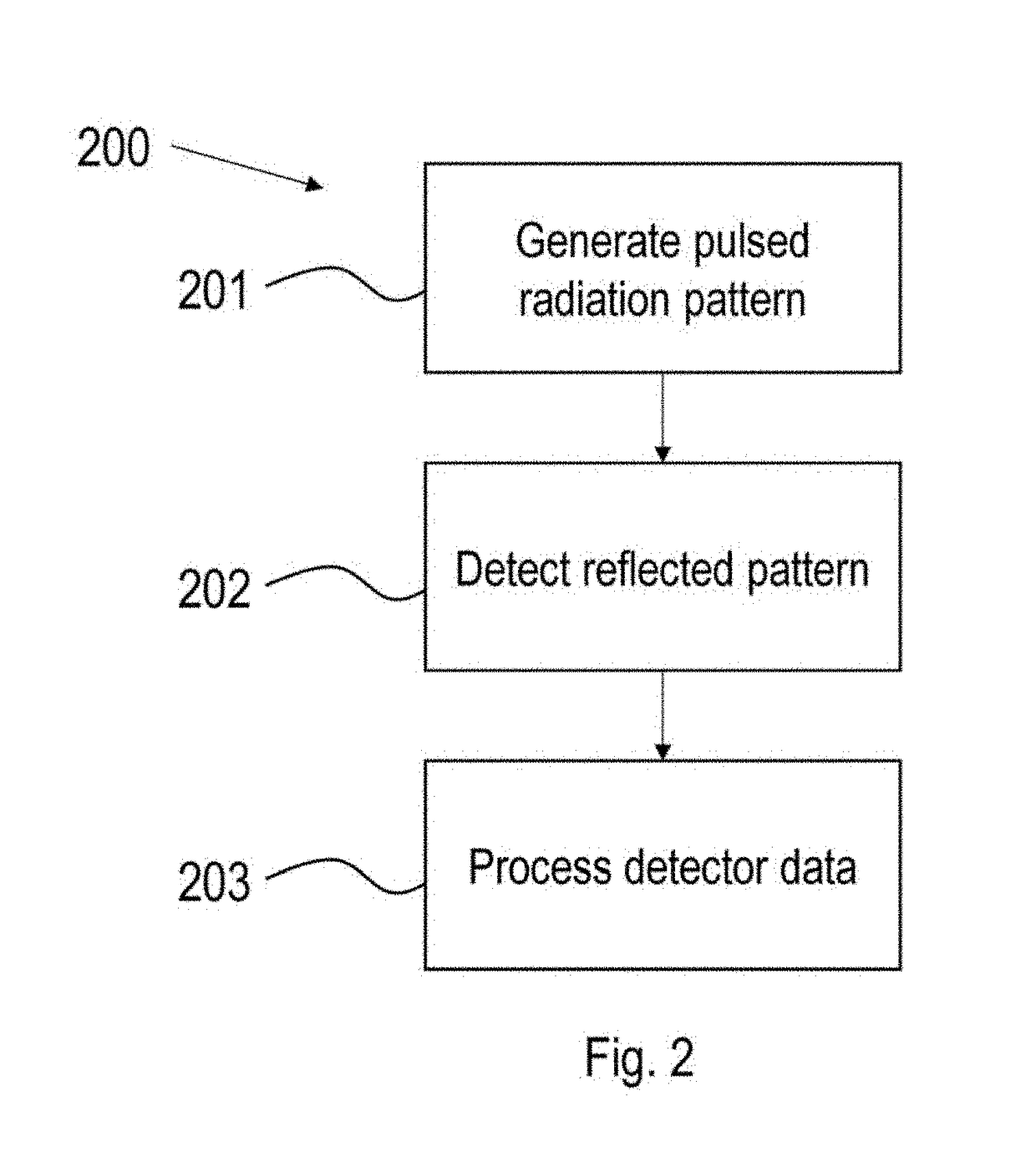
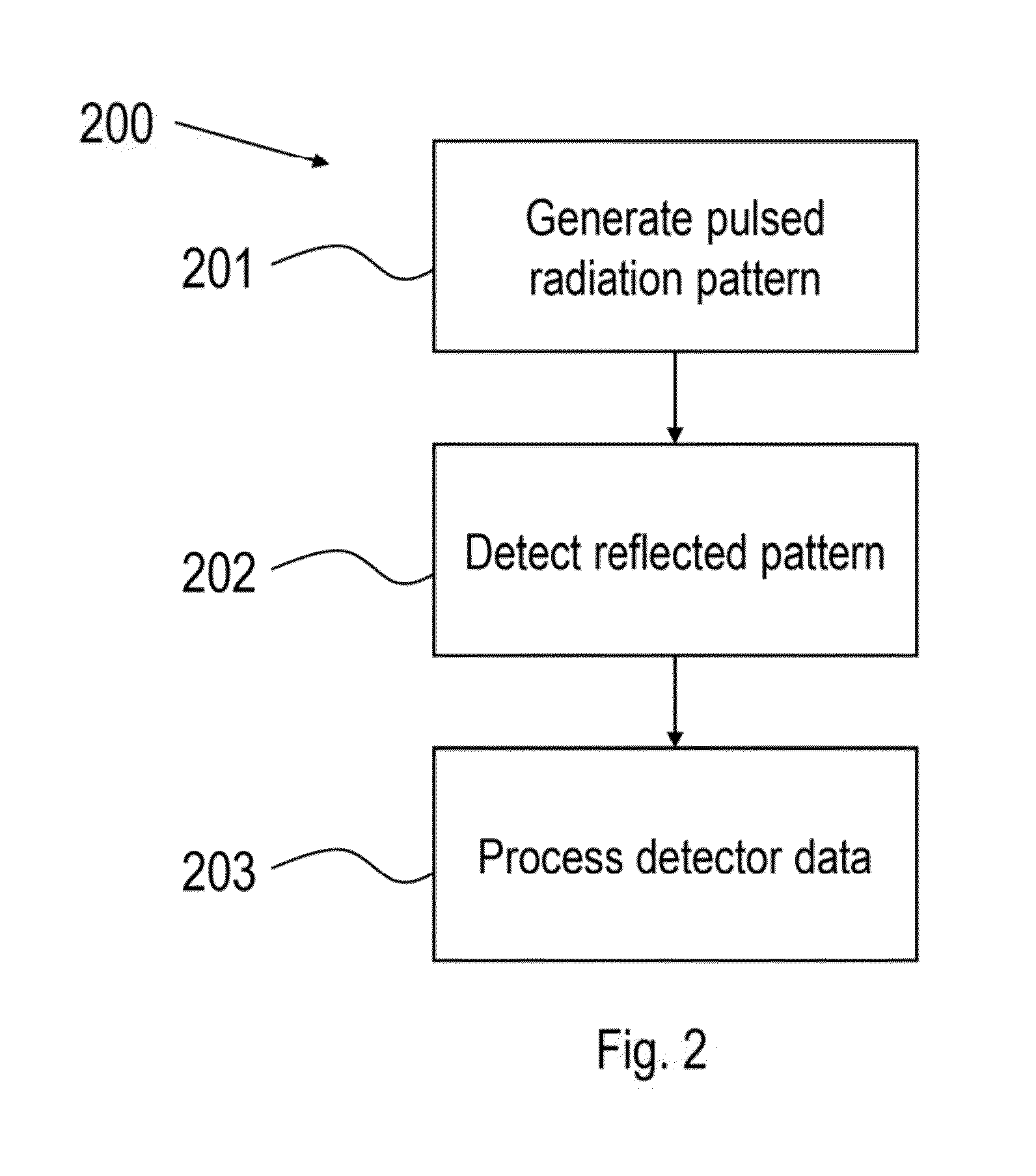
The invention pertains to a system comprising: a source to generate a pulsed radiation pattern; a detector; a processor to process data from the detector when radiation is reflected by an object; a synchronization means interfacing between the detector and the source; wherein: the detector is synchronized with the source so that radiation to be processed is detected only during the pulses, the processor determines a characteristic of the object by determining displacement of detected spots with reference to predetermined positions, the source emits monochromatic light and the detector is equipped with a bandpass filter and optics arranged so as to modify an angle of incidence onto said filter to confine light to a predetermined range around a normal of said filter, said optics comprising an image-space telecentric lens.
Owner:XENOMATIX NV
Surround sensing system with telecentric optics
ActiveUS20160200161A1Decrease the filling factorReduce lossesDigital data processing detailsAnimal undercarriagesBandpass filteringAngle of incidence
The invention pertains to a system comprising: a source to generate a pulsed radiation pattern; a detector; a processor to process data from the detector when radiation is reflected by an object; a synchronization means interfacing between the detector and the source; wherein: the detector is synchronized with the source so that radiation to be processed is detected only during the pulses, the processor determines a characteristic of the object by determining displacement of detected spots with reference to predetermined positions, the source emits monochromatic light and the detector is equipped with a bandpass filter and optics arranged so as to modify an angle of incidence onto said filter to confine light to a predetermined range around a normal of said filter, said optics comprising an image-space telecentric lens.
Owner:XENOMATIX NV
Method for filtering internet cartoon medium rubbish information based on content
InactiveCN101276417APrecise filterHEPA filterCharacter and pattern recognitionSupport vector machineImaging processing
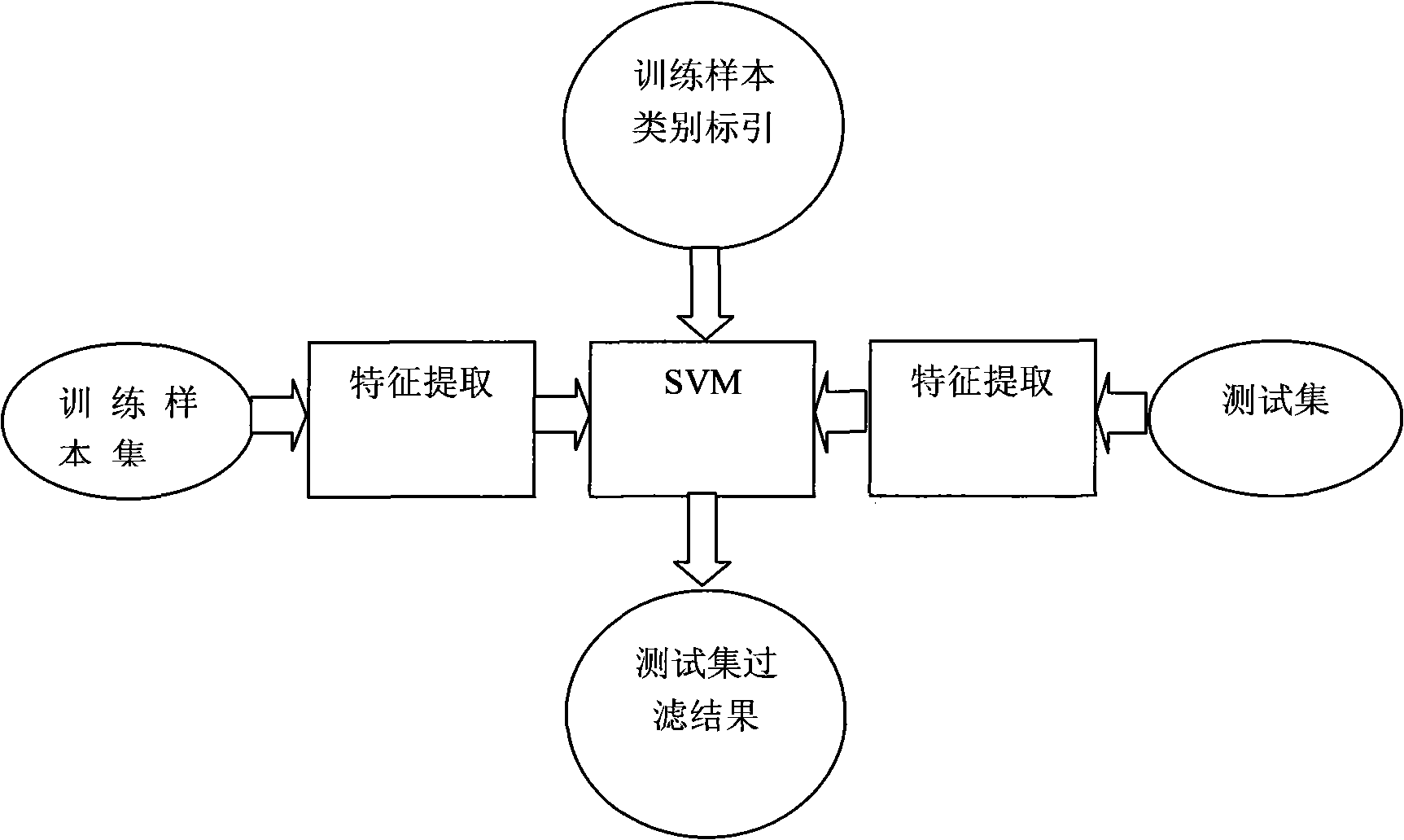
A method for filtering garbage information of Internet animation media based on contents in the fields of image processing and mode identification is disclosed, comprising the steps: 1, collecting at random a plurality of advertisement or non-advertisement animations from the Internet as training sample set, and extracting colour characteristics, texture characteristics, character information characteristics, animation length characteristics, animation geometric size characteristics and animation dynamic characteristics of all the animations; 2, inputting six characteristics of animations and type indexing into a support vector machine which obtains a model of the support vector machine describing the difference between advertisement and non-advertisement animation media; 3, according to the method for extracting the animation characteristics in the step 1, extracting six characteristics of animations to be tested and inputting into the model of the support vector machine so that the support vector machine is able to judge the animation belongs to either the advertisement animation or the non-advertisement animation. The invention can identify the advertisement animation or the non-advertisement animation as well as have high processing speed and identification accuracy.
Owner:SHANGHAI JIAO TONG UNIV
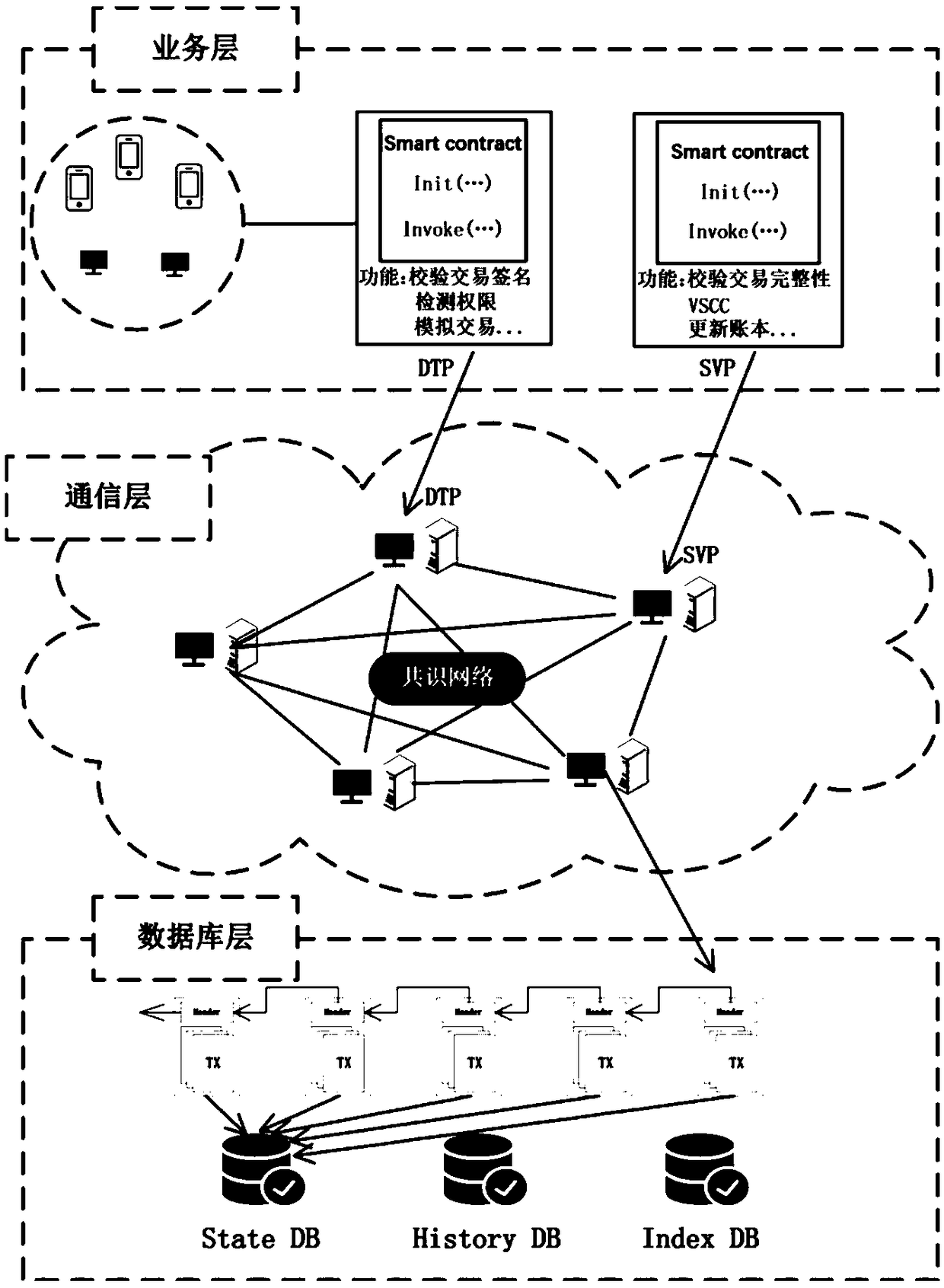
Food safety risk traceability analysis system and method based on block chain
The invention relates to a food safety risk traceability analysis method and a system based on a block chain. The block chain technology is applied to a database layer and a communication layer of thesystem, and the visualization technology is applied to a service layer of the system. Data upload requires the initiator's digital signature to ensure that the data is not tampered with and that thedata is stored in the block chain. Data access is controlled by permissions to access data in the chunk chain by executing smart contracts. Use Force-Directed Graph and flow maps show the food risk traceability process. When tracing the source of food safety risk, the user can trace the source of food safety risk through Force-Directed Graph Drills up to trace the source, then down to track the flow of food, Force-Directed Graph drill-through operations are shown in conjunction with a flow map in which arrows indicate the flow direction of risky foods, where different shades of color representdifferent degrees of risk flow. The invention not only solves the problems of unsafe storage of the traditional food traceability data and the vulnerability of the central database, but also providesa friendly visual interaction interface for users.
Owner:BEIJING TECHNOLOGY AND BUSINESS UNIVERSITY
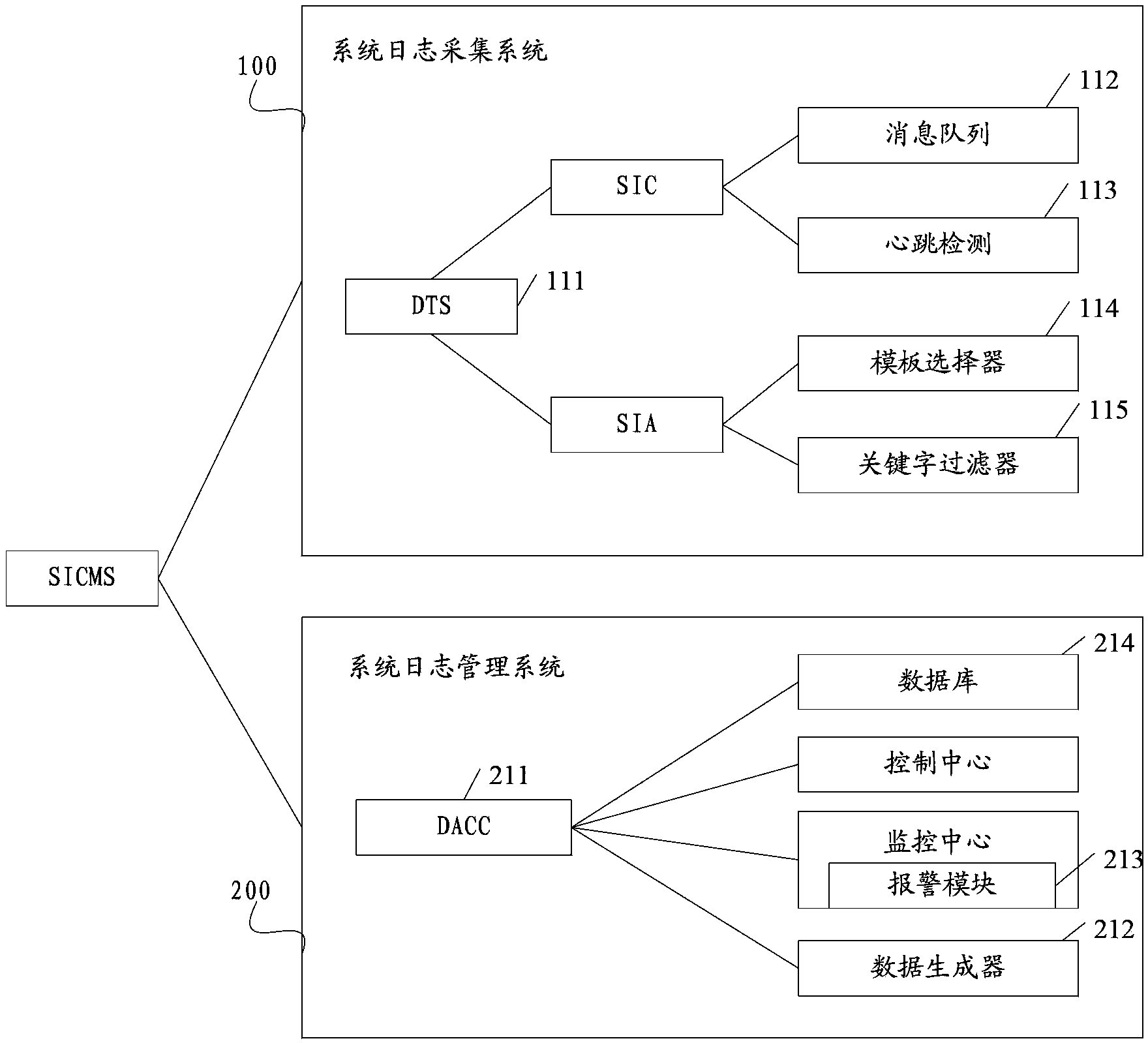
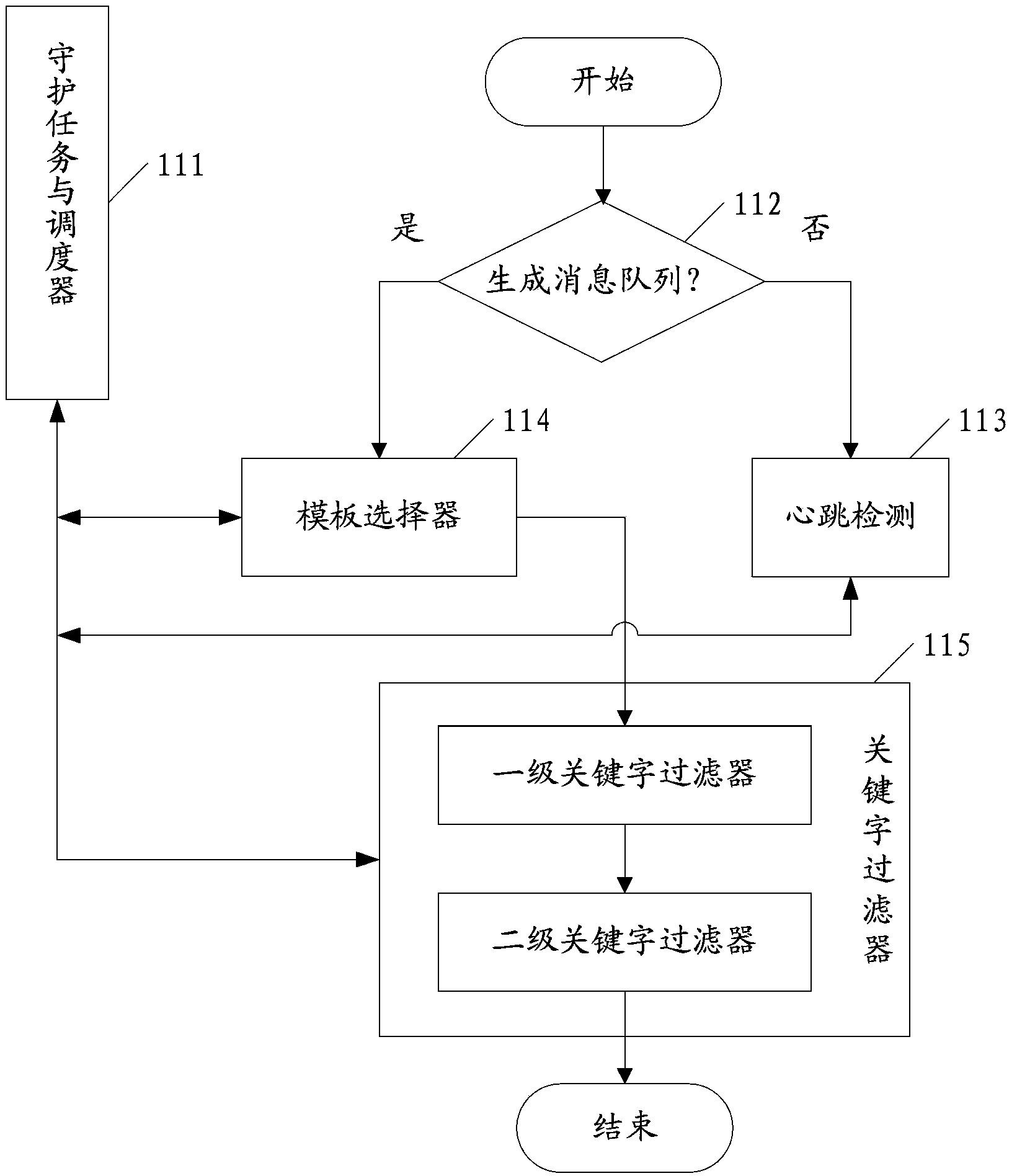
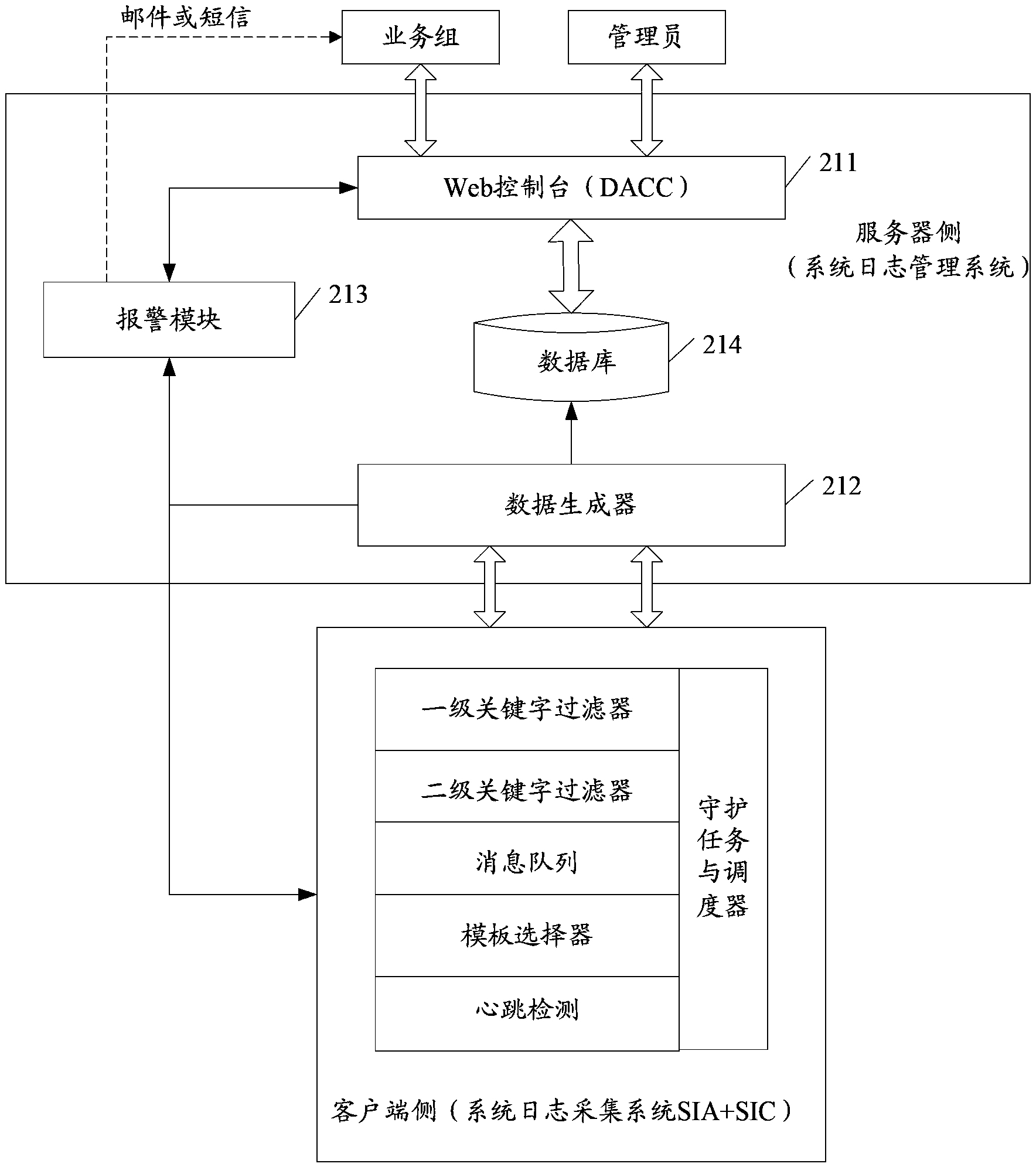
System log processing method and platform
ActiveCN104144071AComprehensive filteringPrecise filterData switching networksDevice typeEmbedded system
The invention discloses a system log processing method and platform. The system log processing method includes the steps of having access to equipment generating system logs, collecting the system logs from the equipment, carrying out matching between the formats of the collected system logs and an appointed equipment template, determining corresponding equipment types of the system logs, filtering the system logs through an appointed key word template according to the equipment types of the system logs, sending a filtering result to a server side, and carrying out alarm processing on the system logs by the server side.
Owner:BEIJING FEINNO COMM TECH
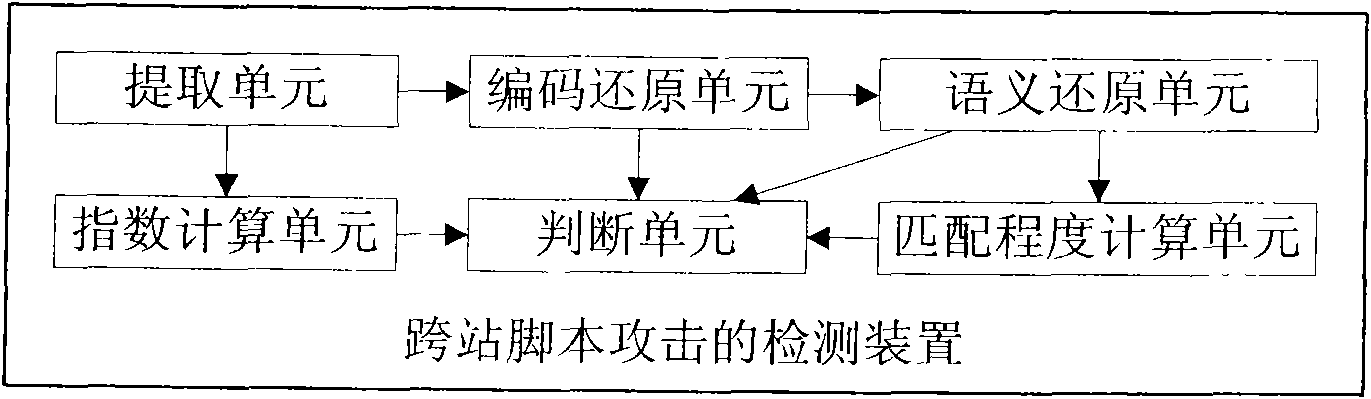
Method and device for detecting cross site scripting
InactiveCN101901221AEfficient and accurate distinctionGuaranteed to passPlatform integrity maintainanceSpecial data processing applicationsNetwork terminationPattern matching
The invention provides a device for detecting cross site scripting. The device comprises an index calculating unit, an extracting unit, a code restoring unit, a semantics restoring unit, a matching degree calculating unit and a judging unit which cooperate with each other; and malicious cross site scripts entrained in a Web page are identified and extracted by a comprehensive HTML label analysis methods (comprising four methods, namely EJSRF analysis, JavaScript code deformation analysis, JavaScript semantics denaturation analysis and XSS attack characteristic mode matching). The cross site script identification and extraction technology taking HTML label analysis as a core can efficiently and accurately distinguish a normal JavaScript from the malicious cross site scripts in the Web page to make network security detection equipment and a network terminal accurately identify and filter the Web page which contains the malicious cross site scripts, and simultaneously guarantee legal Web page (without entrained malicious cross site scripts) normally pass.
Owner:BEIJING VENUS INFORMATION TECH +1
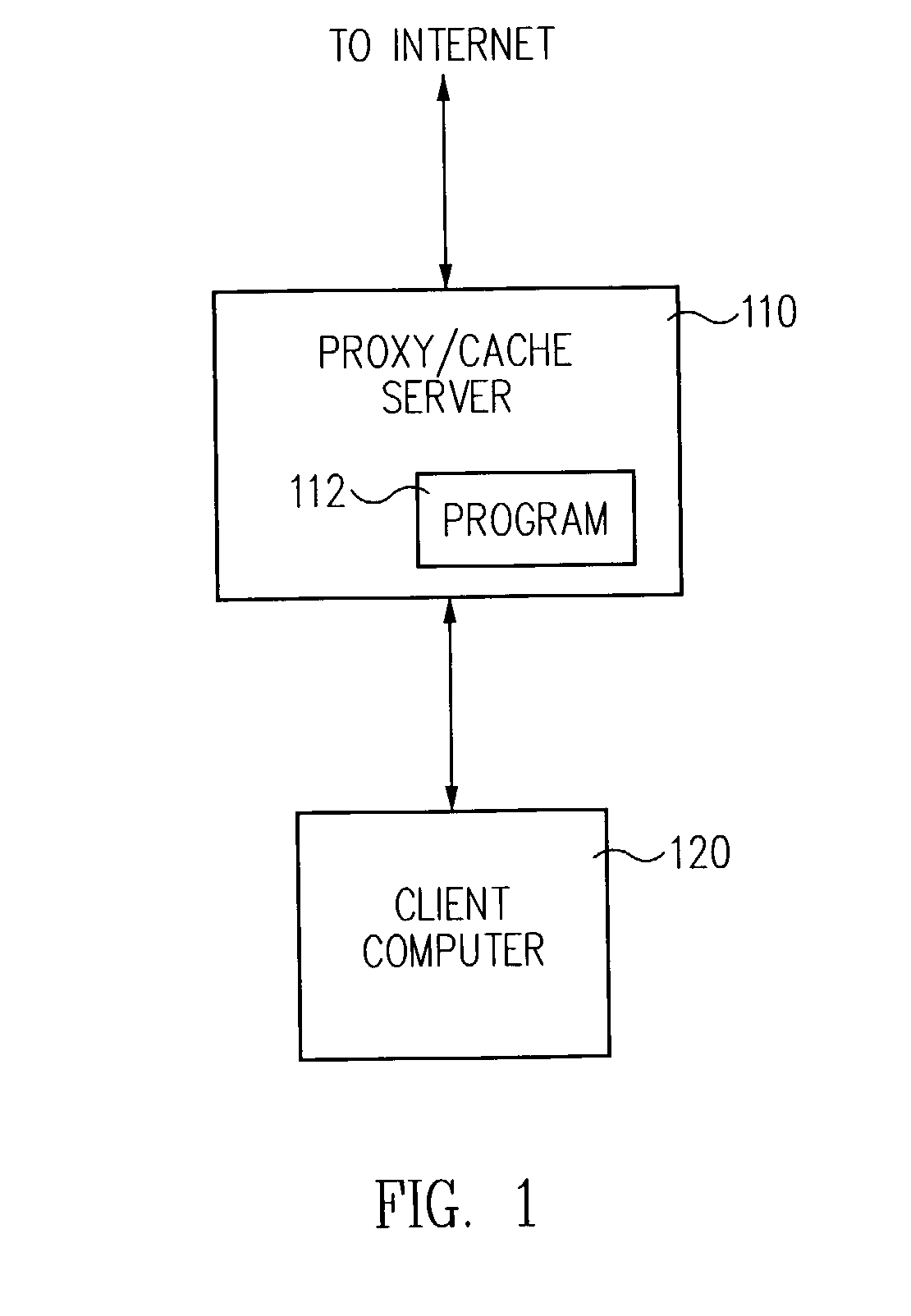
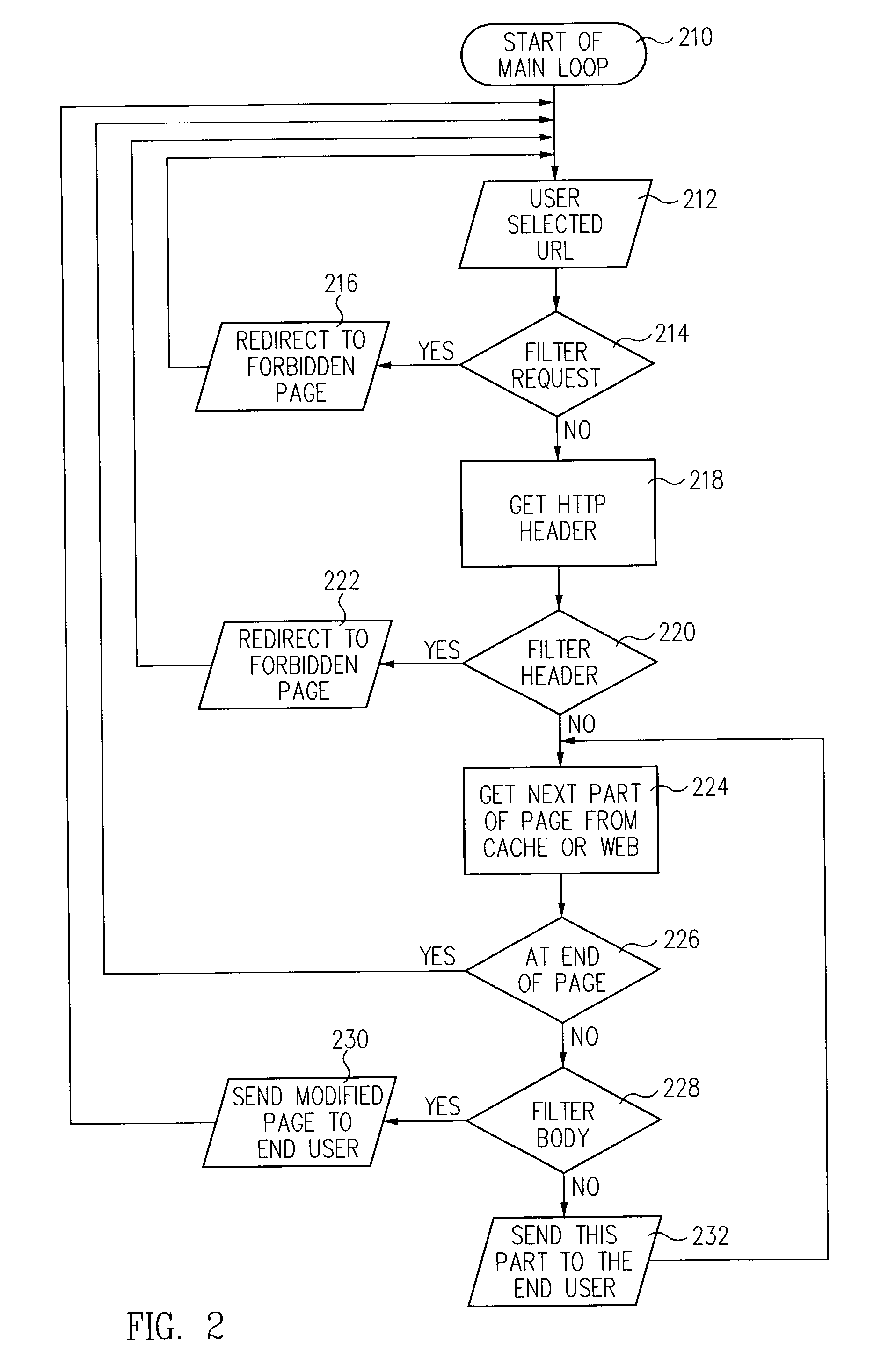
System and method for filtering data received by a computer system
ActiveUS8224950B2Overcome disadvantagesPrecise filterDigital data information retrievalMultiple digital computer combinationsComputer monitorThe Internet
The present invention provides a system and method for restricting access to data received by a computer over a network by filtering certain data from the data received. In a preferred embodiment, the present invention provides a computer based method for filtering objectionable or target text data from World Wide Web pages which are received by a computer system connected to the Internet. According to the method, if the web page requested by the user contains only a minimum of objectionable or target data, the user may receive a portion of the filtered web page for downloading and viewing on his or her computer. If the web page requested contains a large amount of objectionable or target data, the invention will cause a “forbidden” page to be displayed on the user's computer monitor.
Owner:CA TECH INC
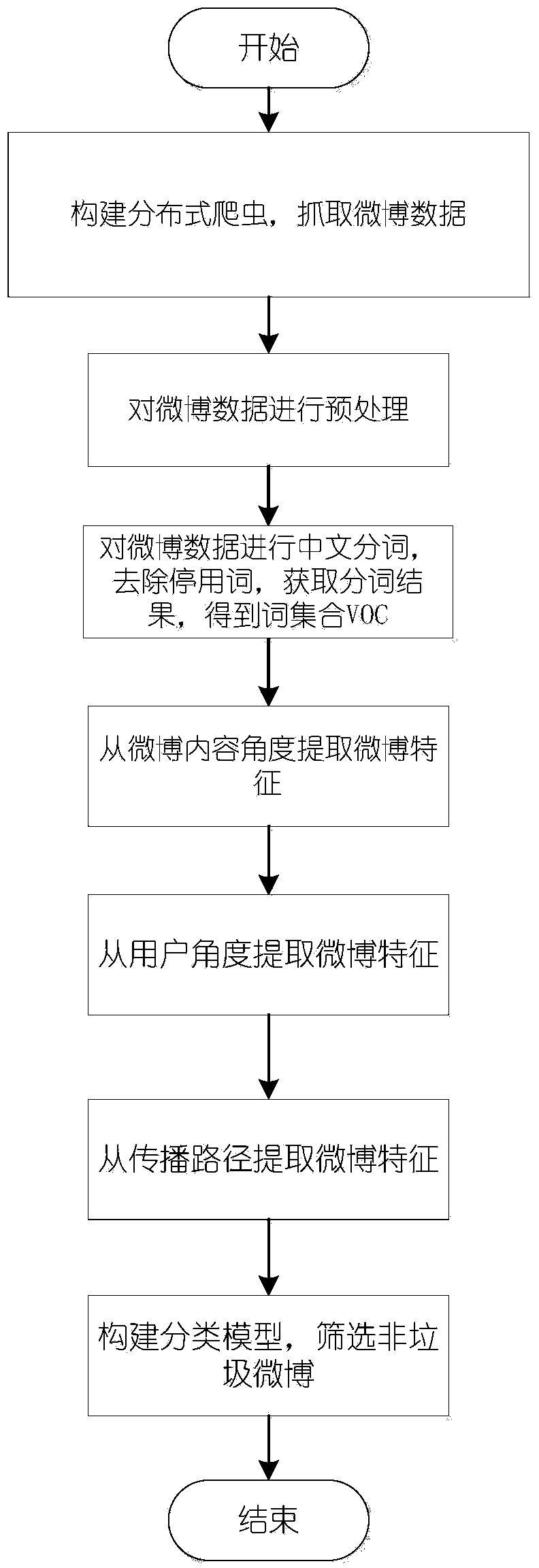
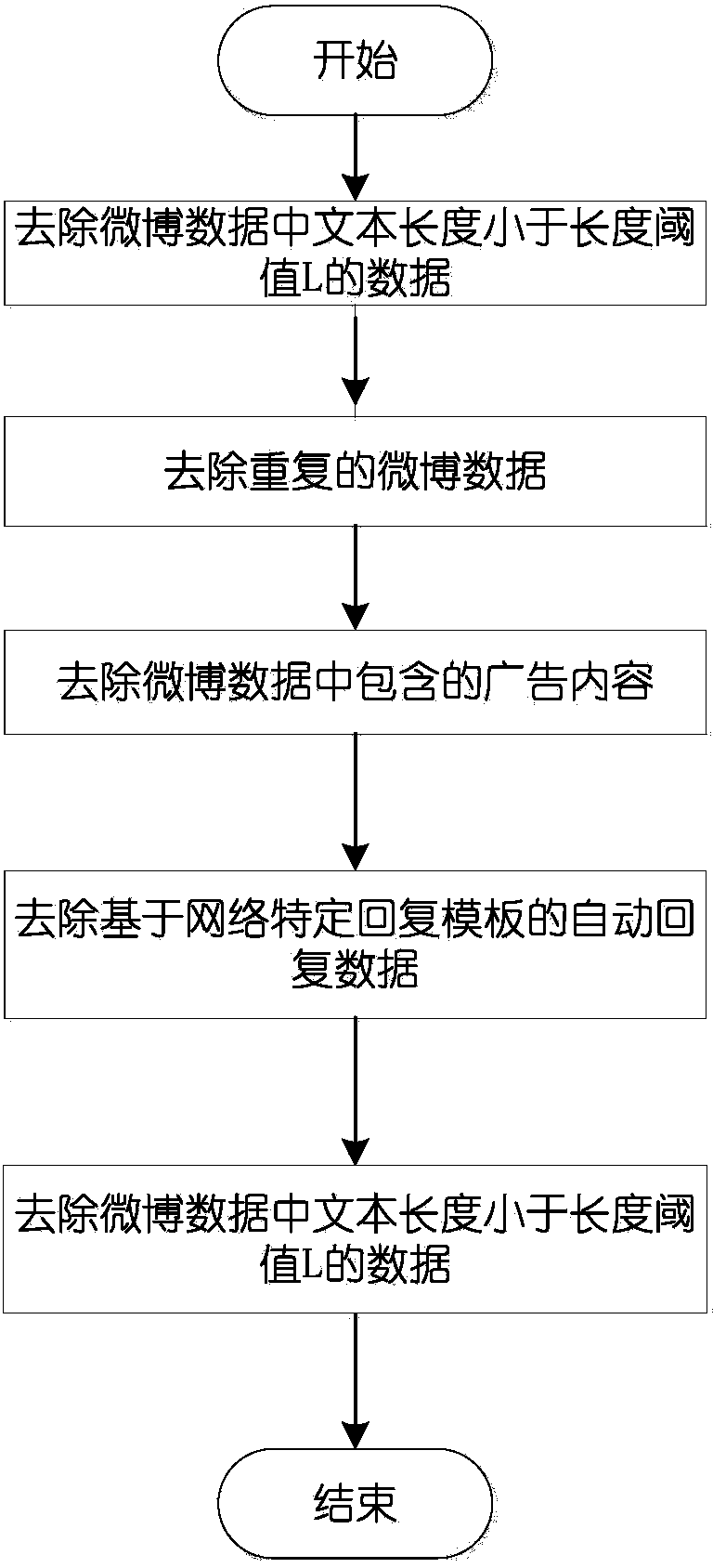
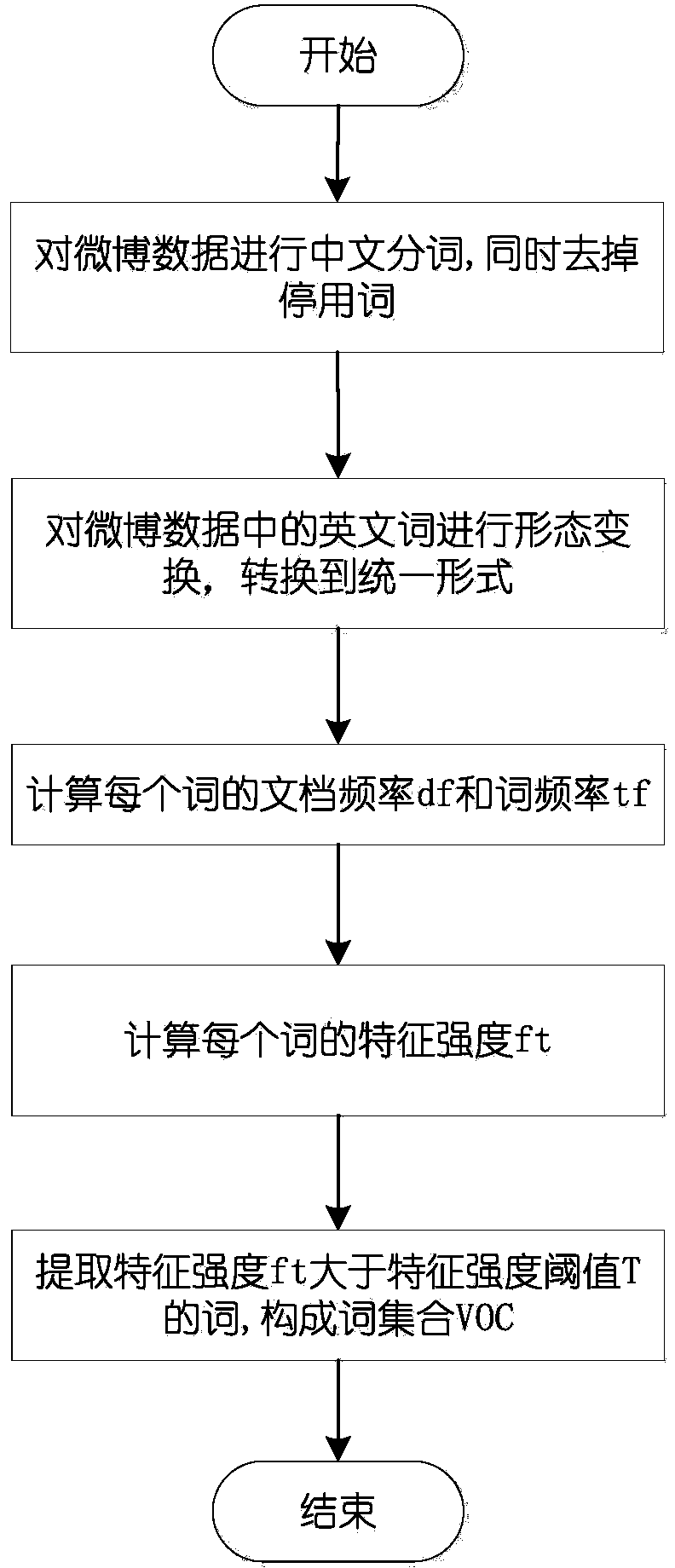
Microblog information filtering method based on multi-information fusion
ActiveCN104239539AImprove recognition accuracyQuality improvementWebsite content managementSpecial data processing applicationsInformation processingMicroblogging
The invention provides a microblog information filtering method based on multi-information fusion, which belongs to the technical field of intelligent information processing. The method comprises the following steps of step 1, building distributed crawling, and crawling microblog data; step 2, preprocessing the microblog data; step 3, carrying out Chinese word segmentation on the microblog data, deleting stop words, acquiring a word segmentation result, and obtaining a word set VOC; step 4, extracting characteristics from the perspective of microblog contents; step 5, extracting microblog characteristics from the perspective of the client; step 6, extracting characteristics from a transmission path; step 7, building a classification model, and screening non-junk microblogs. According to the microblog information filtering method based on multi-information fusion, the double processes of microblog information duplicate removal and a classification learning algorithm are combined to delete microblog junk information, so that the microblog information can be filtered, and not only is reduplicative microblog information filtered, but also junk microblog information can be filtered.
Owner:中科嘉速(北京)信息技术有限公司
Method and instrument for detecting and analyzing intelligent network vision target
InactiveCN101493979AImprove monitoring effectReduce the burden onTelevision system detailsColor television detailsVideo recordingVisual perception
The invention discloses a vision object detection and analysis method of an intelligent network and a device thereof. The method comprises the following steps: a standard television signal is obtained from a fixed camera, compiled to MPEG-4 format and then sent to a digital signal image processing and analysis unit; a three-dimensional modeling is carried out in the digital signal image processing and analysis unit through a reference object in a detected area; when a moving object appears in a monitored area, the moving object is separated from background frames and compared with entries of a database model which is embedded in a storage unit and is called out, such as the size of the moving object, moving track characteristics and shapes of the moving object, which are output from; when large parts of the entries are identical, the moving object is identified as a dangerous object and the alarm is sent immediately; simultaneously, the digital signal image processing and analysis unit outputs a video recording instruction to a monitoring device. The method can solve and automatically detect the technical problems whether the video frame in a monitoring system has the dangerous object and the alarm signal is sent or not.
Owner:SHENZHEN BELLSENT INTELLIGENT SYST
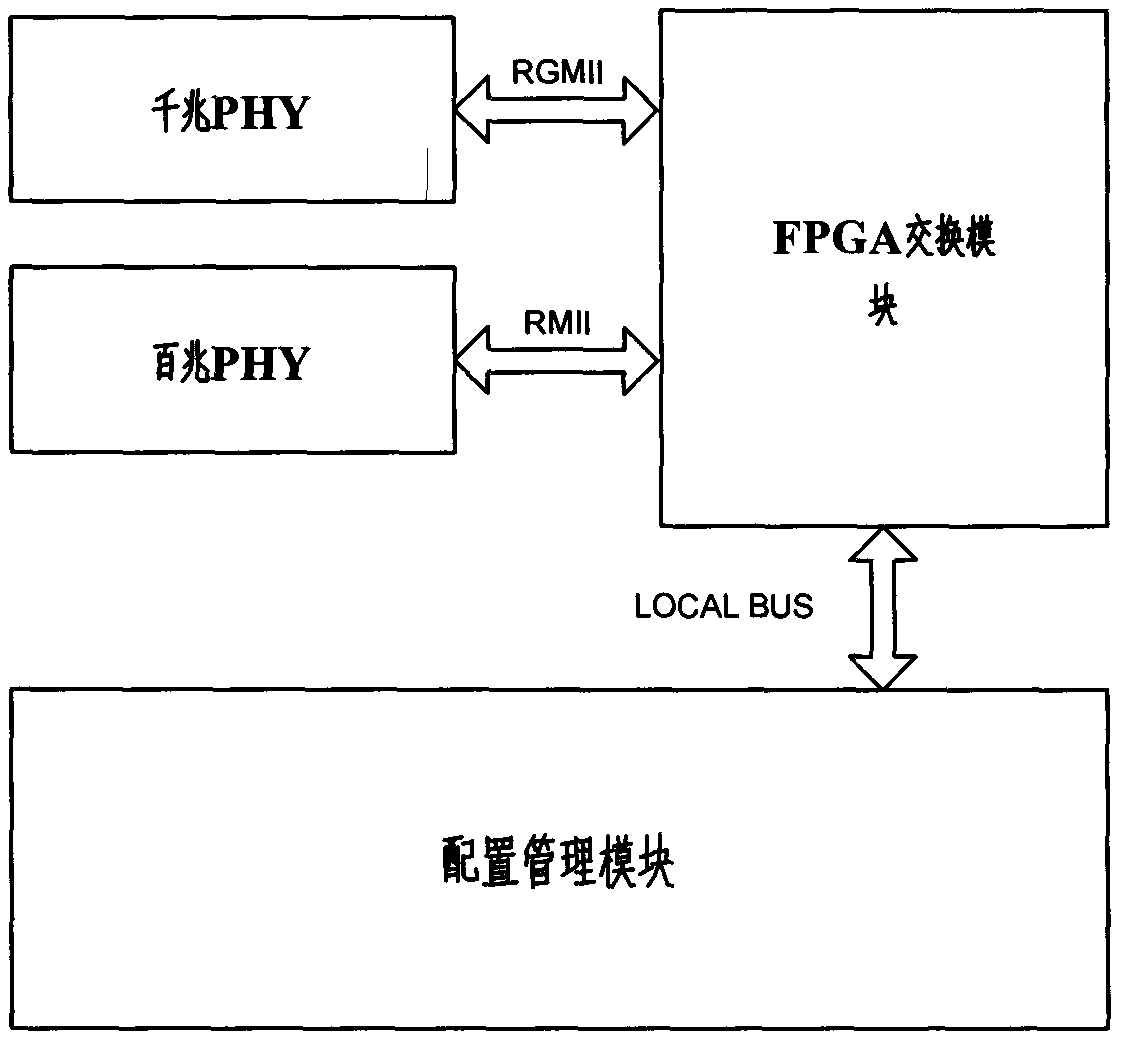
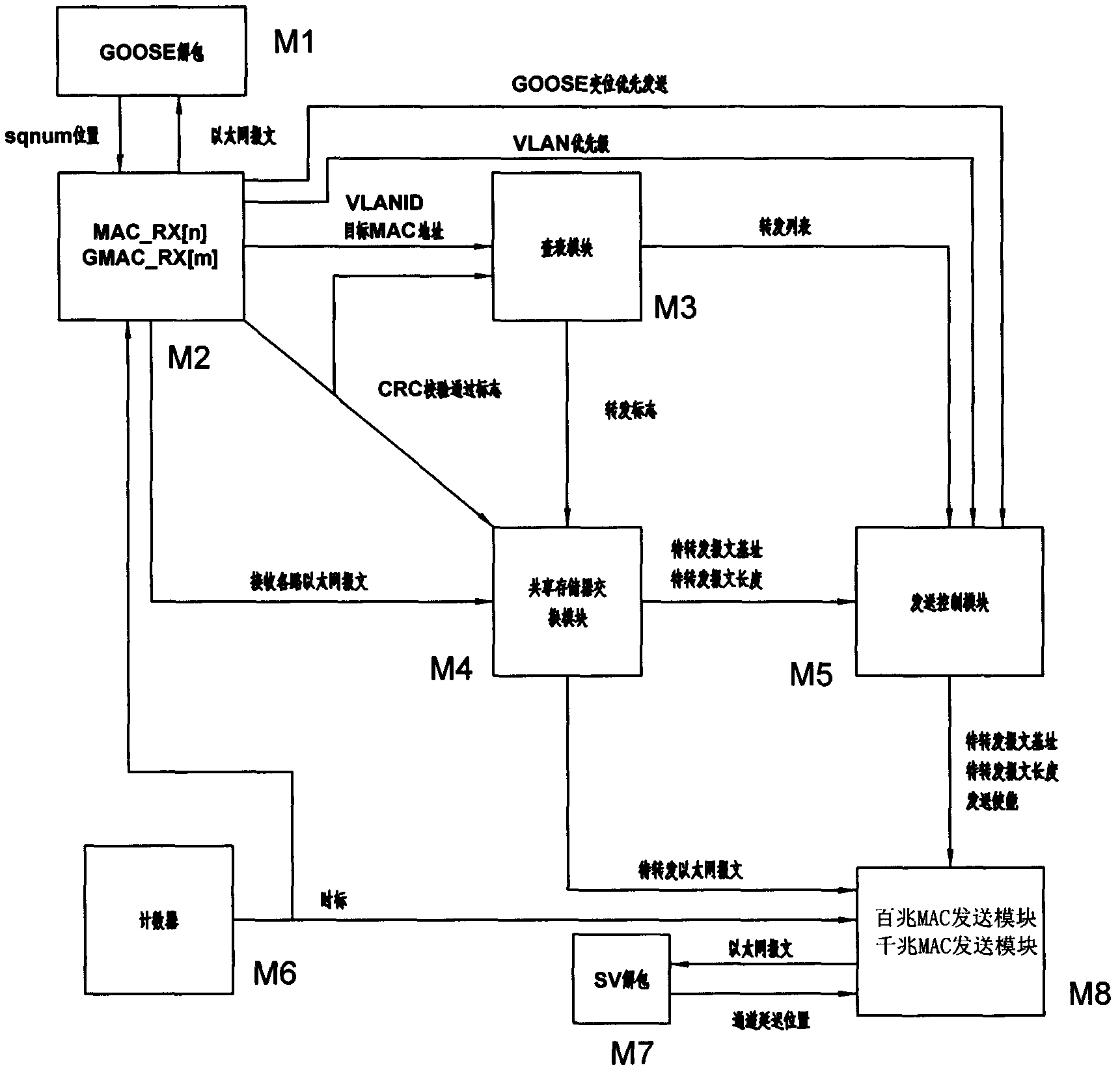
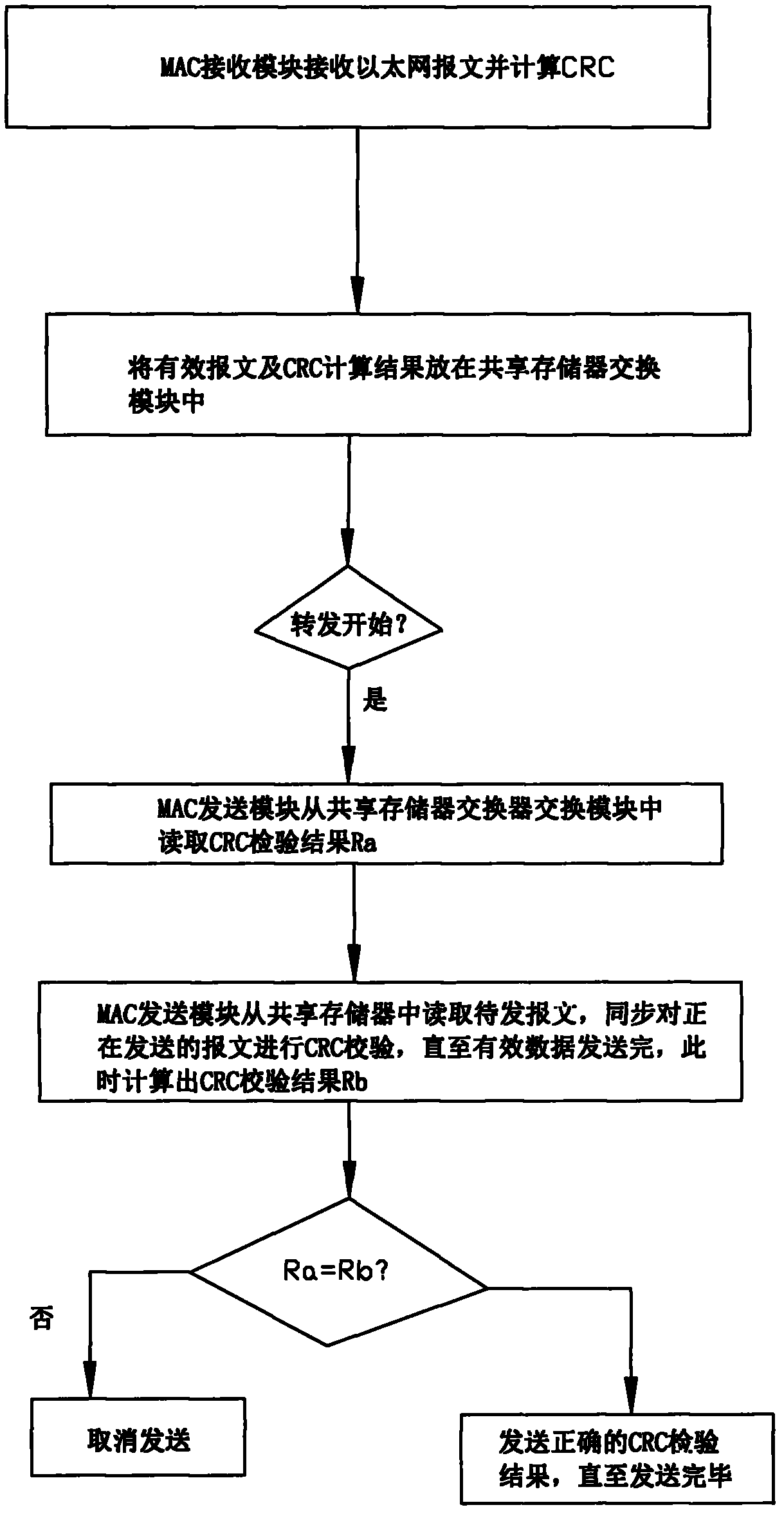
Digital substation process level data exchanging device
InactiveCN103326963AGuarantee real-time and reliabilityAccurate filteringData switching networksStormLevel data
The invention discloses a digital substation process level data exchanging device. The core of the device is a configurable data exchanging module based on the FPGA. A simple and efficient data exchanging mode is achieved on the basis of IEC61850. The unique functions of SV message rated delaying automatic updating, GOOSE deflected message prior transmission, data storm rapid accurate restraint and the like are particularly achieved. The problems that the process level SV networking communication depends on GPS synchronization, the transmission and delay of the GOOSE are uncontrollable and even packet loss occurs under the mode that the SV and the GOOSE are combined in network, and the storm restraint time is over long are solved. The motion delay of tripping operation of the GOOSE is reduced. The digital substation process level data exchanging device is creative, practical and economical and capable of promoting the reform of a digital substation process level networking mode.
Owner:麦康世 +1
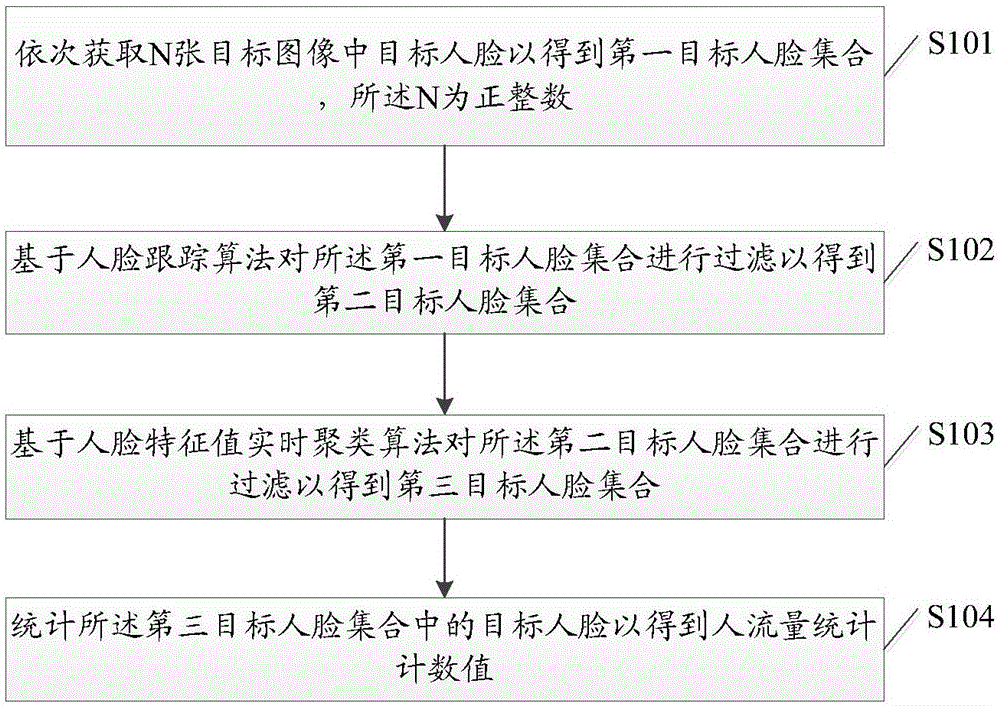
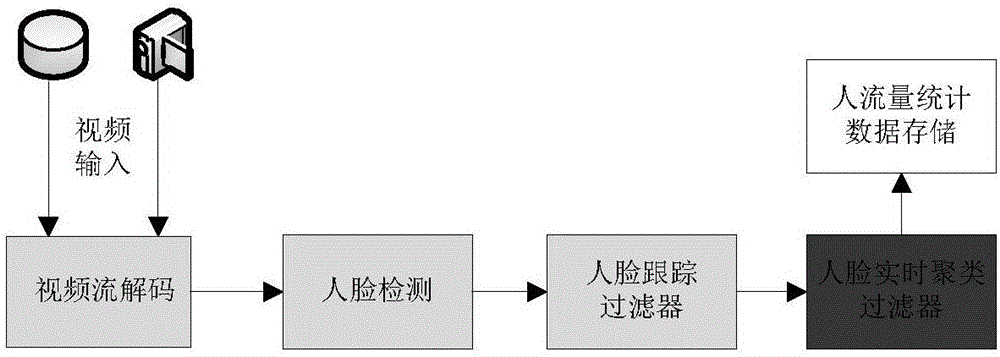
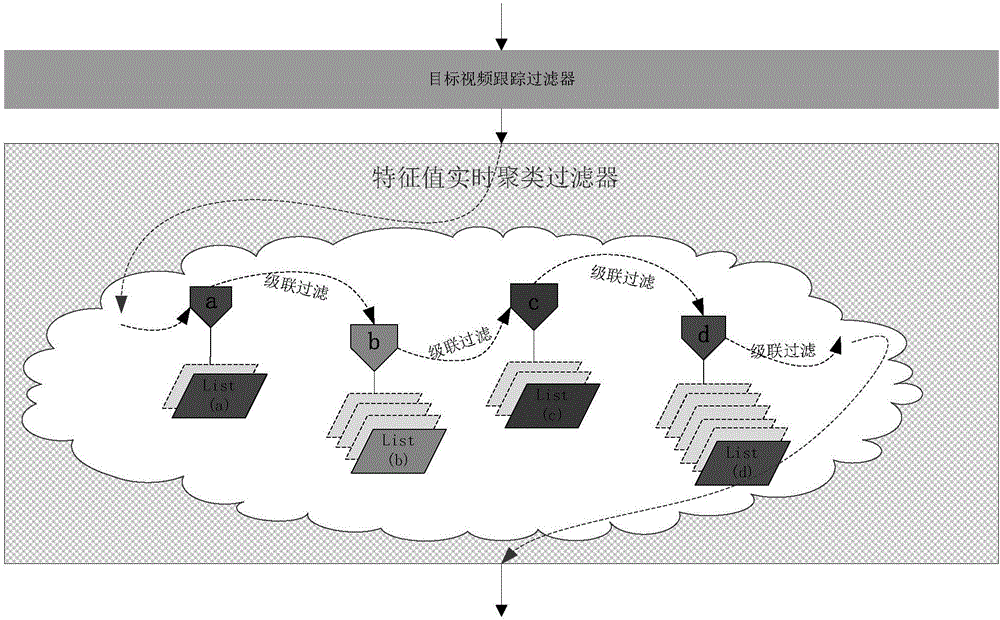
Visitor flow rate statistical method and device based on image recognition
ActiveCN106570465AAvoid double countingImprove accuracyCharacter and pattern recognitionPattern recognitionCluster algorithm
The embodiment of the invention discloses a visitor flow rate statistical method and device based on image recognition, and the method comprises the steps: sequentially obtaining target human faces in N target images, so as to obtain a first target human face set, wherein N is a positive integer; carrying out the filtering of the first target human face set based on a human face tracking algorithm, so as to obtain a second target human face set; carrying out the filtering of the second target human face set based on a human face feature value real-time clustering algorithm, so as to obtain a third target human face set; and counting the target human faces in the third target human face set, so as to obtain a visitor flow rate statistical value. The method carries out the two-layer filtering of N target images, and can accurately filter out repeated human faces in the target human faces, so as to avoid the repeated counting of target human faces, and improve the visitor flow rate statistical accuracy.
Owner:SHENZHEN INTELLIFUSION TECHNOLOGIES CO LTD
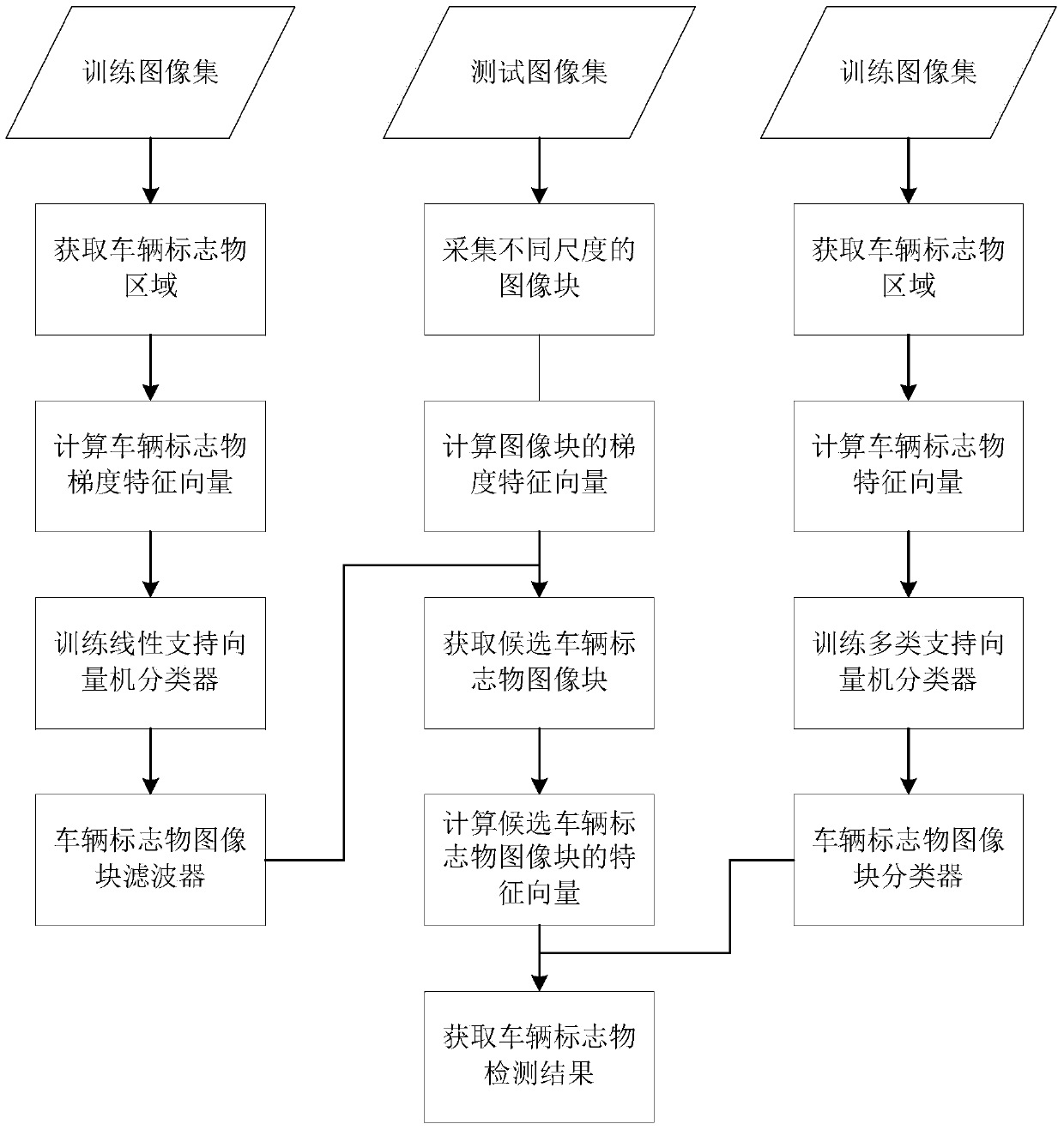
Vehicle logo detection method and system based on two-layer classification
ActiveCN104217217AAccurate detectionImprove detection accuracyCharacter and pattern recognitionHistogram of oriented gradientsEngineering
The invention discloses a vehicle logo detection method based on two-layer classification. The method comprises the following steps: firstly acquiring a vehicle logo and background in a windshield image in a training data set, and then respectively training a vehicle logo image block detector and a vehicle logo image block classifier; for a test image, firstly acquiring gradient feature vectors of image blocks in the image, and acquiring a candidate vehicle logo image block by using the trained vehicle logo detector, and then computing a HOG (histogram of oriented gradients) feature vector, an LBP feature vector and a color histogram feature vector for the acquired candidate vehicle logo image block, splicing the computed vectors into the feature vector of the image block, and classifying by using the trained vehicle logo classifier to acquire the category of the vehicle logo. The vehicle logo detection process disclosed by the invention is simple and easy to implement, the detection accuracy is high, and the detection speed is fast.
Owner:武汉睿智视讯科技有限公司
Mass short message information filtering method based on semantic extension
ActiveCN103455581AAvoid negative effectsImprove execution efficiencySpecial data processing applicationsSupport vector machineContext based
The invention provides a mass short message information filtering method based on semantic extension and can solve the short message feather sparsity problem. The method comprises the following steps that 1, an initial training sample set is built, and expansion is carried out for each sample of the training sample set on the basis of the context information; 2, the expanded training sample set is subjected to text preprocessing; 3, a theme feather dictionary is built on the basis of the training sample set subjected to the preprocessing; 4, each text of the training sample set is subjected to text expression in a hidden theme space; 5, an SVM (support vector machine) filter is built; 6, the text to be filtered is subjected to expansion and text preprocessing to be converted into a feather word set on the basis of the context information, is then subjected to text expression in the hidden theme space, and is filtered by a filter; and 7, novel samples are regularly collected, the word item probability distribution of the theme is updated in the existing hidden theme space, the novel samples are subjected to text expression, and the SVM filter is rebuilt.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
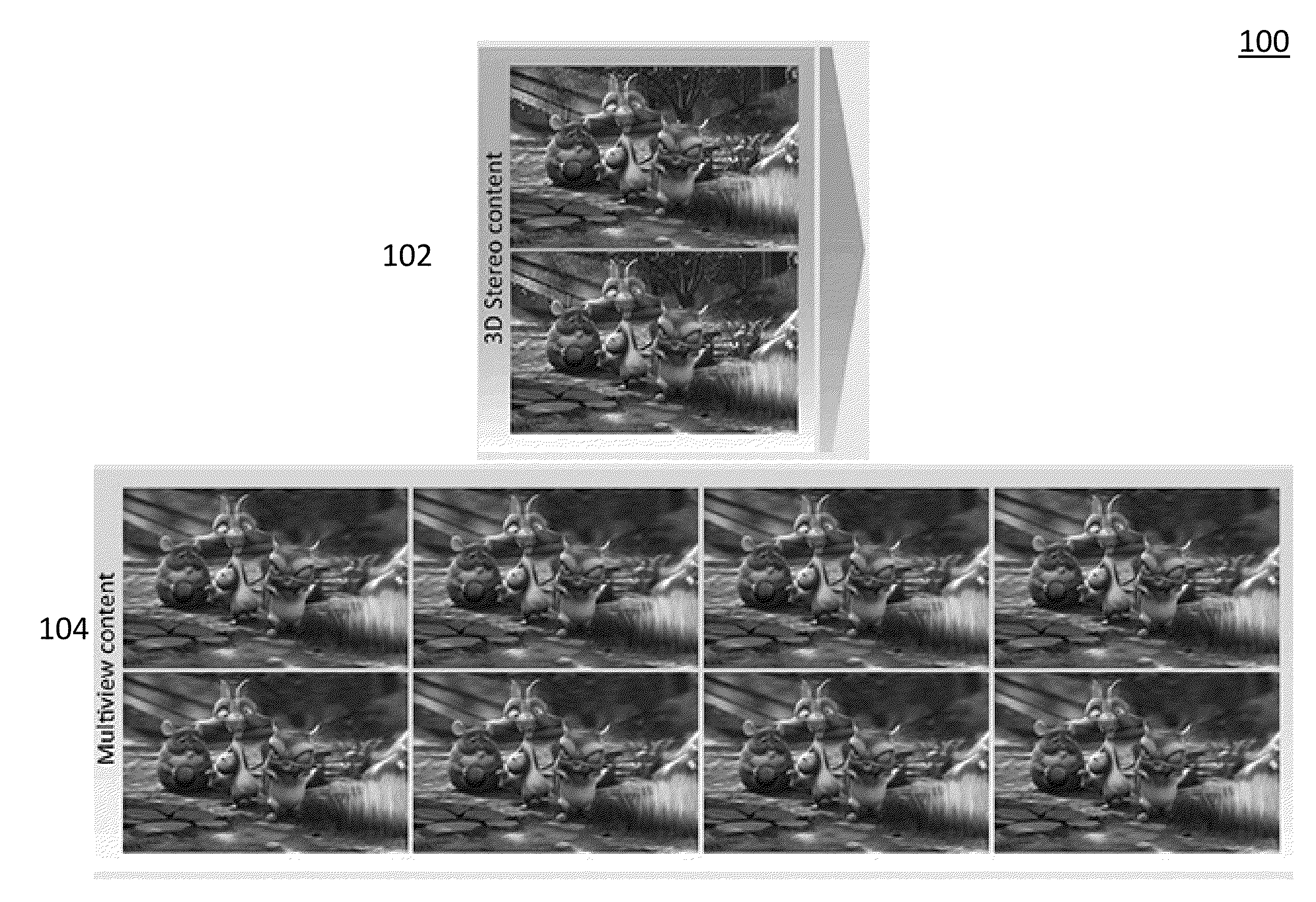
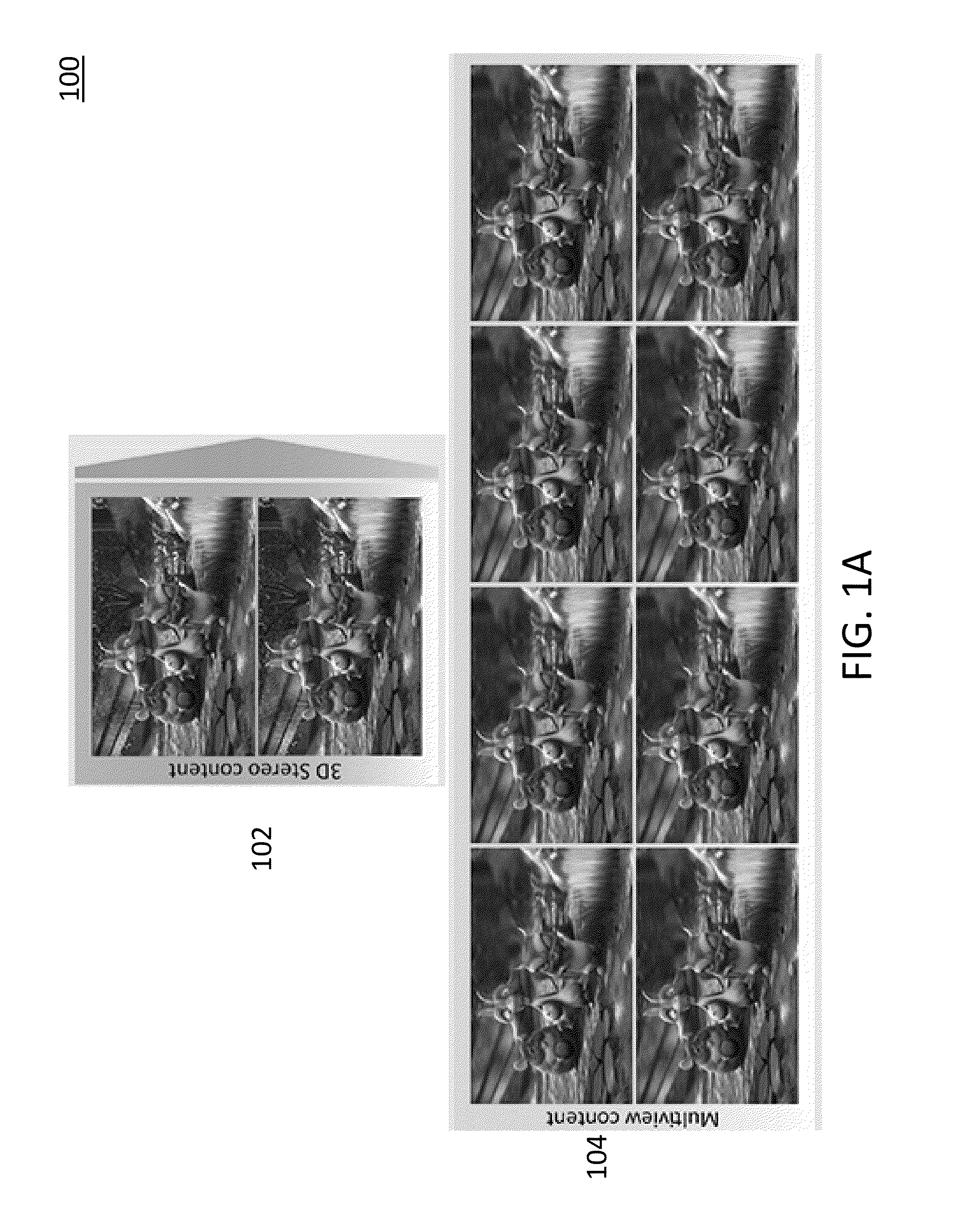
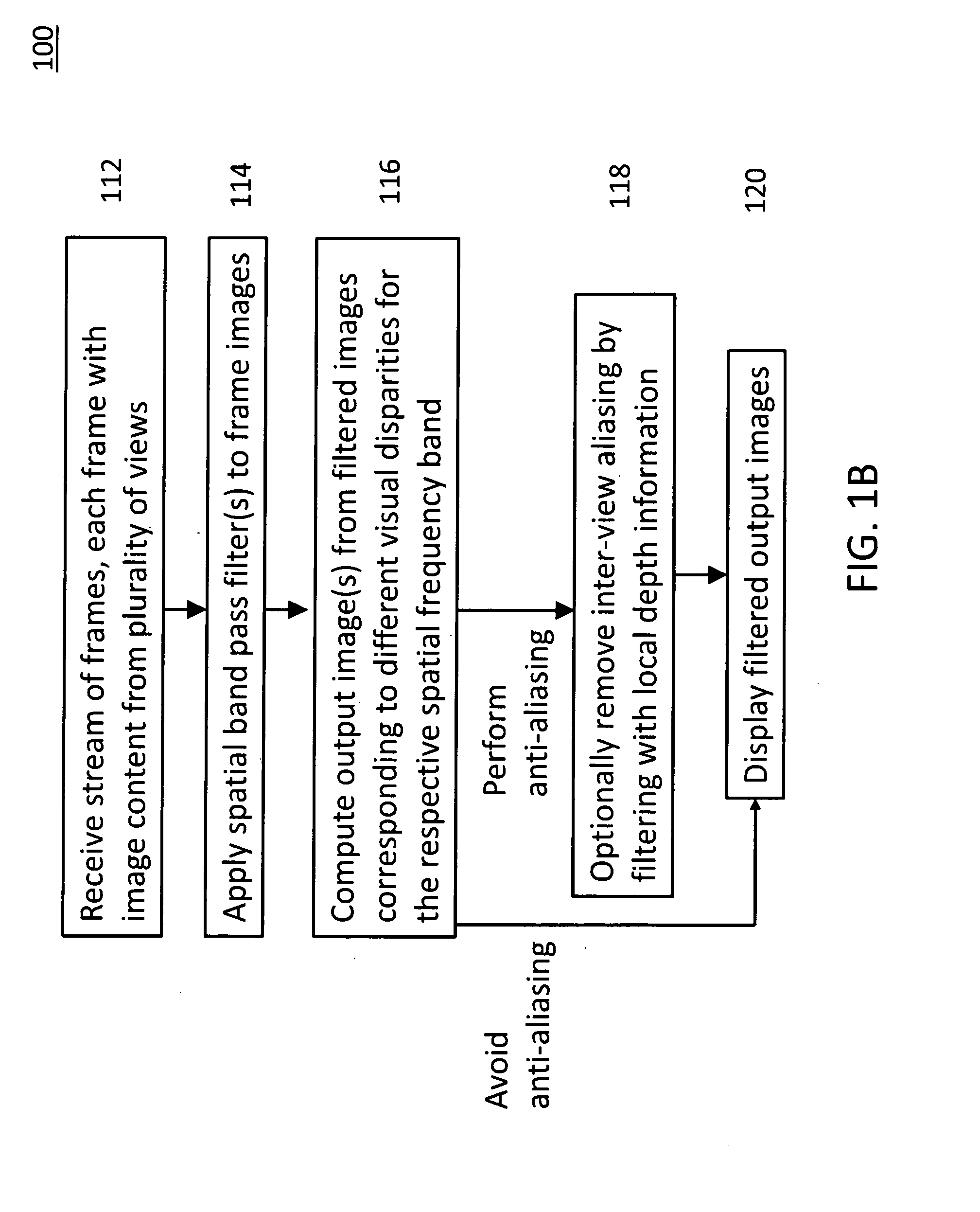
Joint View Expansion And Filtering For Automultiscopic 3D Displays
ActiveUS20150124062A1Good effectReduce the numberSteroscopic systemsStereoscopic videoDisplay device
Multi-view autostereoscopic displays provide an immersive, glasses-free 3D viewing experience, but they preferably use correctly filtered content from multiple viewpoints. The filtered content, however, may not be easily obtained with current stereoscopic production pipelines. The proposed method and system takes a stereoscopic video as an input and converts it to multi-view and filtered video streams that may be used to drive multi-view autostereoscopic displays. The method combines a phase-based video magnification and an interperspective antialiasing into a single filtering process. The whole algorithm is simple and may be efficiently implemented on current GPUs to yield real-time performance. Furthermore, the ability to retarget disparity is naturally supported. The method is robust and works transparent materials, and specularities. The method provides superior results when compared to the state-of-the-art depth-based rendering methods. The method is showcased in the context of a real-time 3D videoconferencing system.
Owner:MASSACHUSETTS INST OF TECH
Illegal website filtering method and device
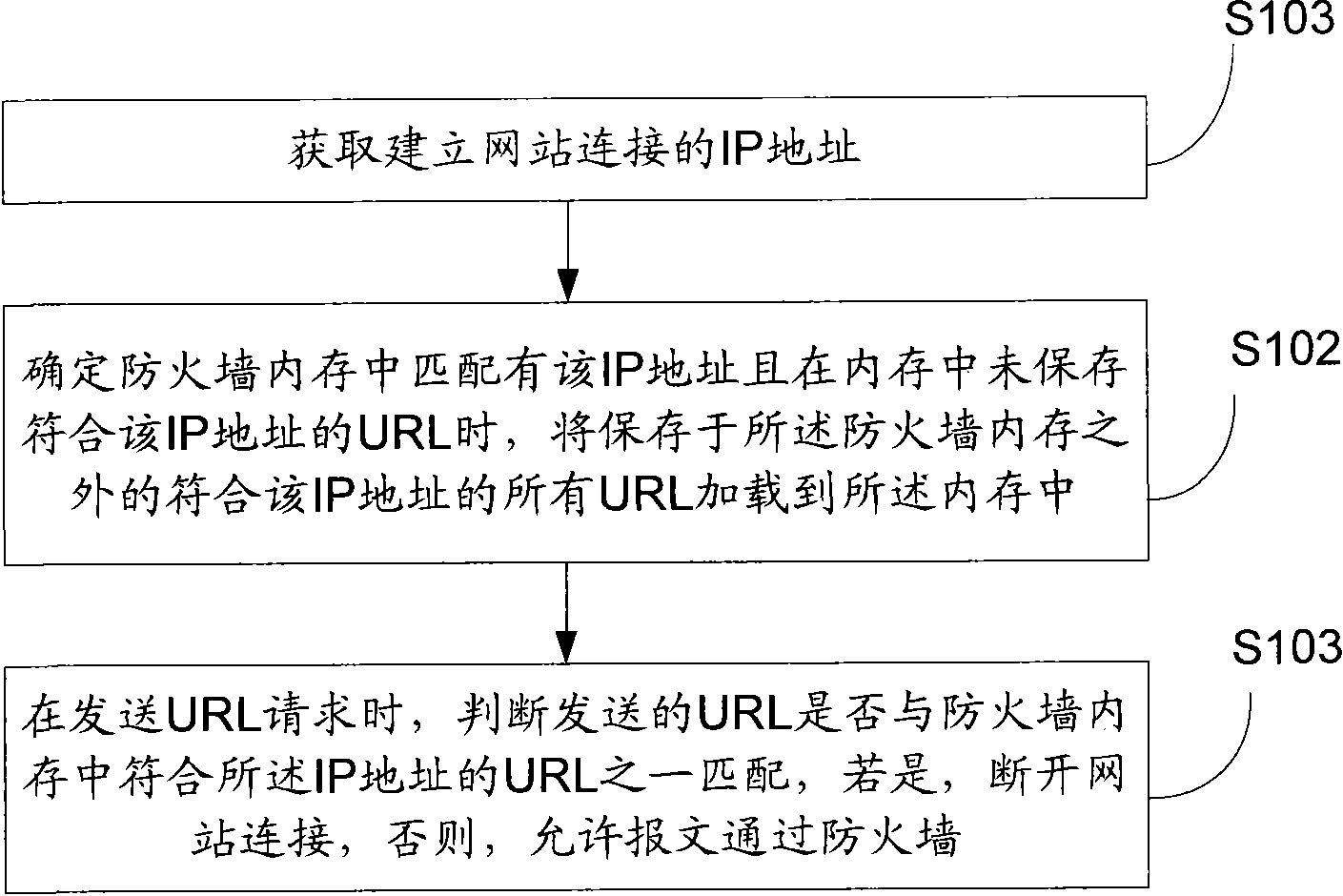
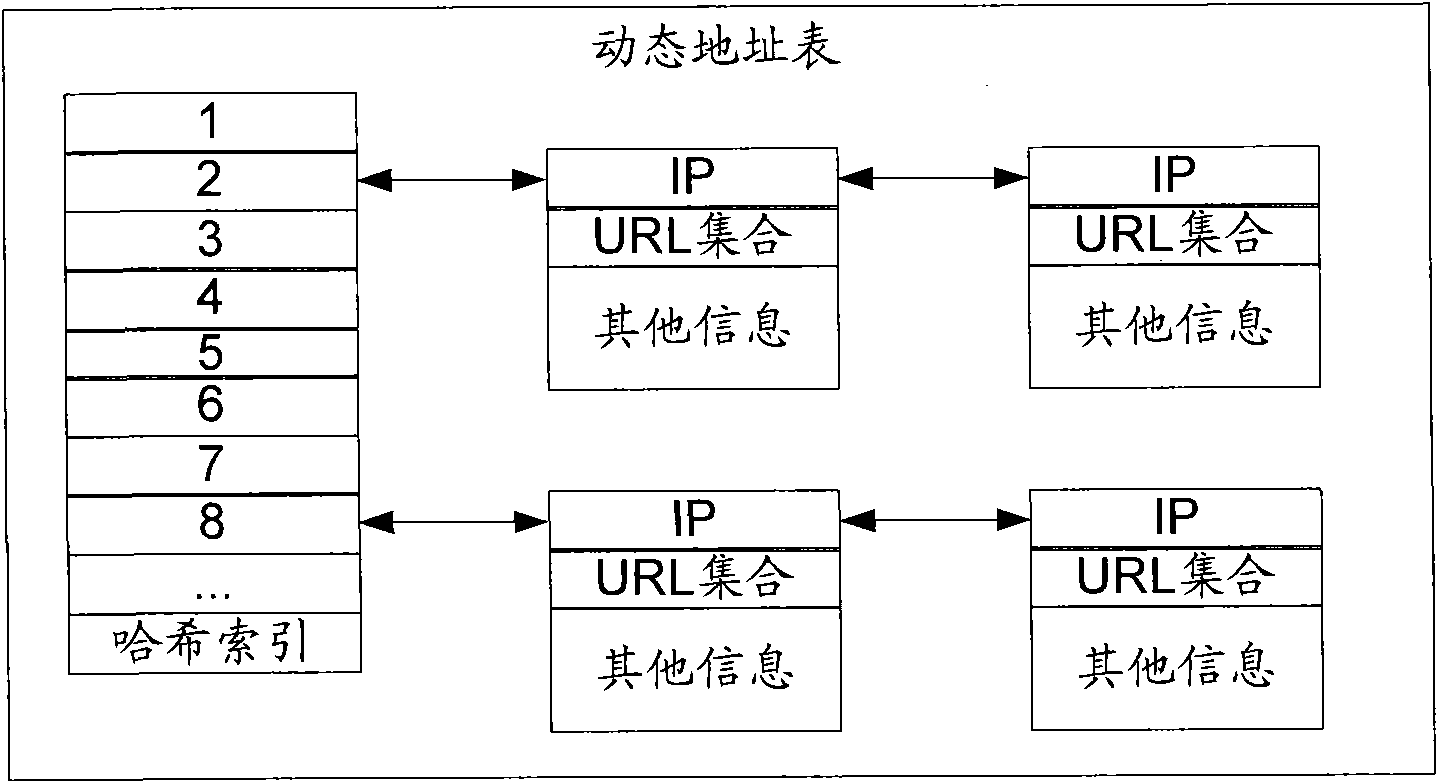
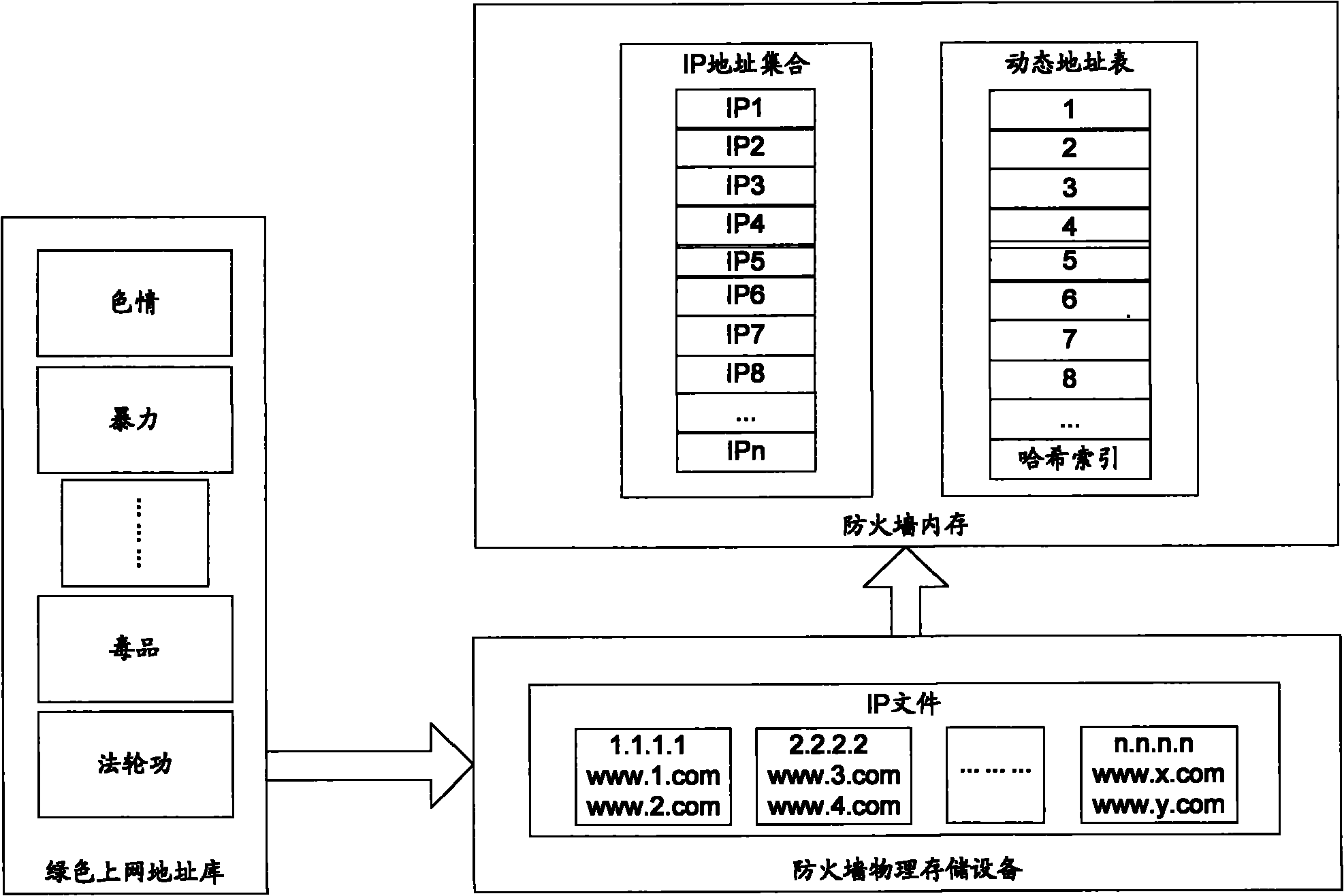
InactiveCN101795272AOvercome misusePrecise filterComputer security arrangementsTransmissionIp addressUniform resource locator
The invention discloses illegal website filtering method and device. The method comprises the following steps of: obtaining an IP address for establishing website connection, and loading all URL (Uniform Resource Locator) conforming to the IP address outside a memory of a fireproof wall into the memory when determining that the memory of the fireproof wall has the IP address and the UPL conforming to the IP address is not stored in the memory; when sending the URL request, judging whether the sent URL is matched with one of the URLs conforming to the IP address in the memory of the fireproof wall, if so, disconnecting the connection, or else, allowing the message to pass through the fireproof wall. The invention can solve the problem of loading an address base into the memory once due to overlarge capacity, and can also accurately filter illegal websites through the dual comparison of the IP address and the URL.
Owner:BEIJING LEADSEC TECH
Method and unit for extracting traffic attack message characteristics on network equipment
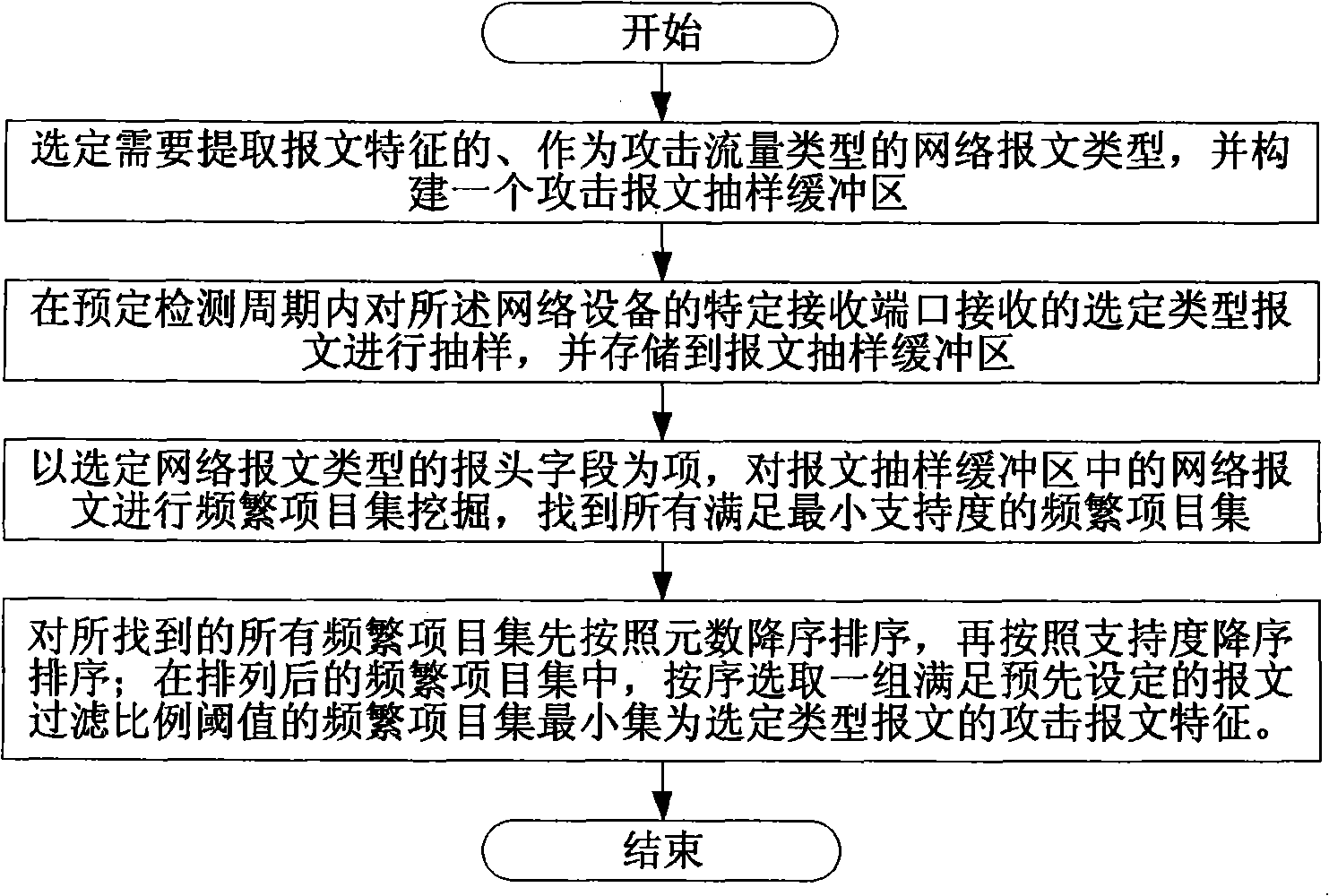
InactiveCN101640594AGuaranteed normal passagePrecise filterData switching networksSecuring communicationTraffic characteristicTraffic capacity
The invention discloses a method and a unit for extracting traffic attack message characteristics on network equipment. The method comprises the steps of: selecting a network message type which needs to extract message characteristics and is taken as an attack traffic type; taking a header field of a message with the selected type as an item, and finding all frequent item sets which meet the requirement of minimum support in the received network message with the selected type; performing descending sort on all the found frequent item sets according to element numbers, and then performing descending sort on the frequent item sets with the same element number according to the support; and sequentially selecting a group of minimum sets of frequent item sets which meet the requirement of a message filtration proportion threshold value as the attack message characteristics of the message with the selected type from the sorted frequent item sets. The method and the unit overcome the one sidedness of a traffic characteristic extraction method, can accurately filter, avoid error killing, and guarantee the normal pass of valid network traffic.
Owner:BEIJING VENUS INFORMATION TECH +1
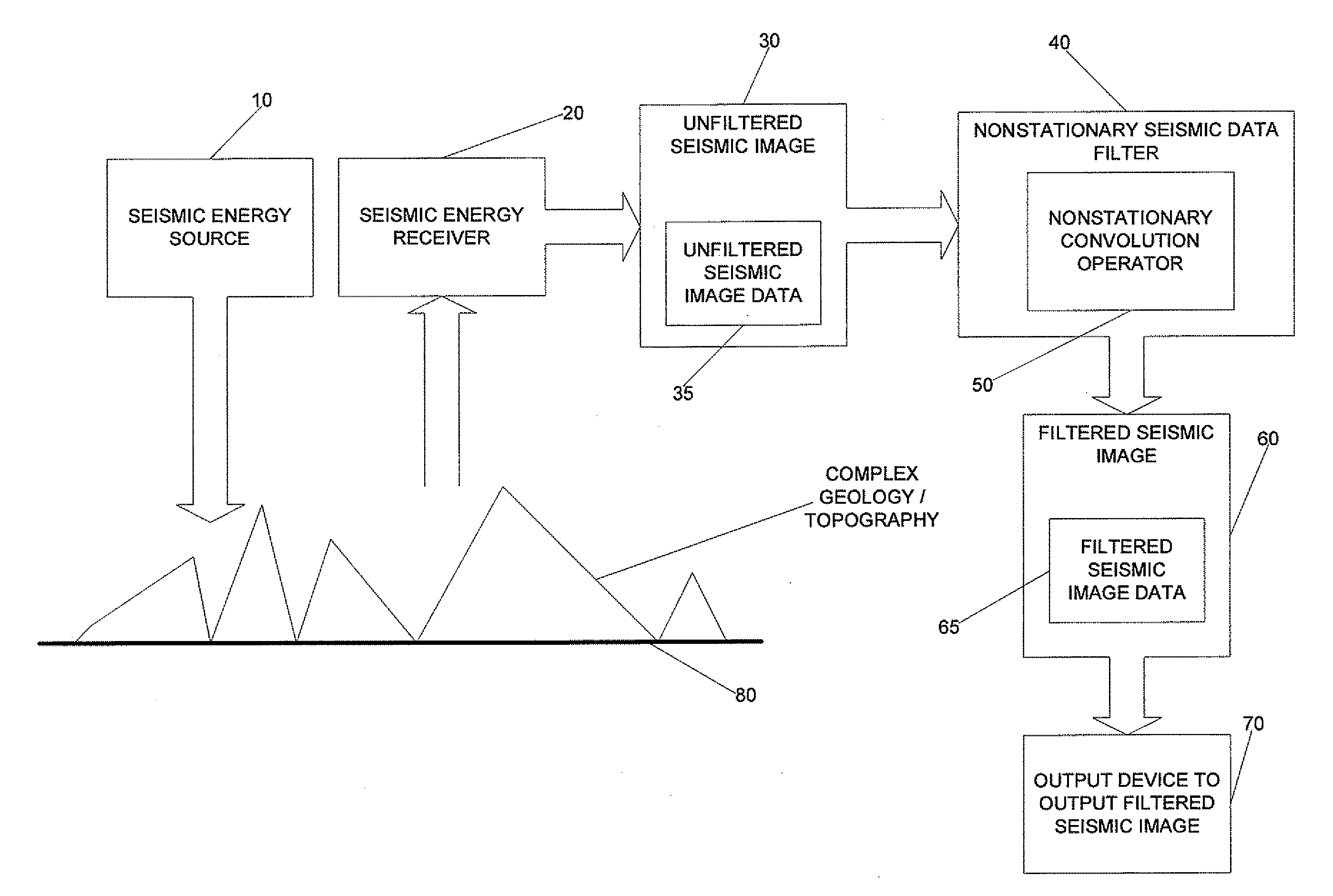
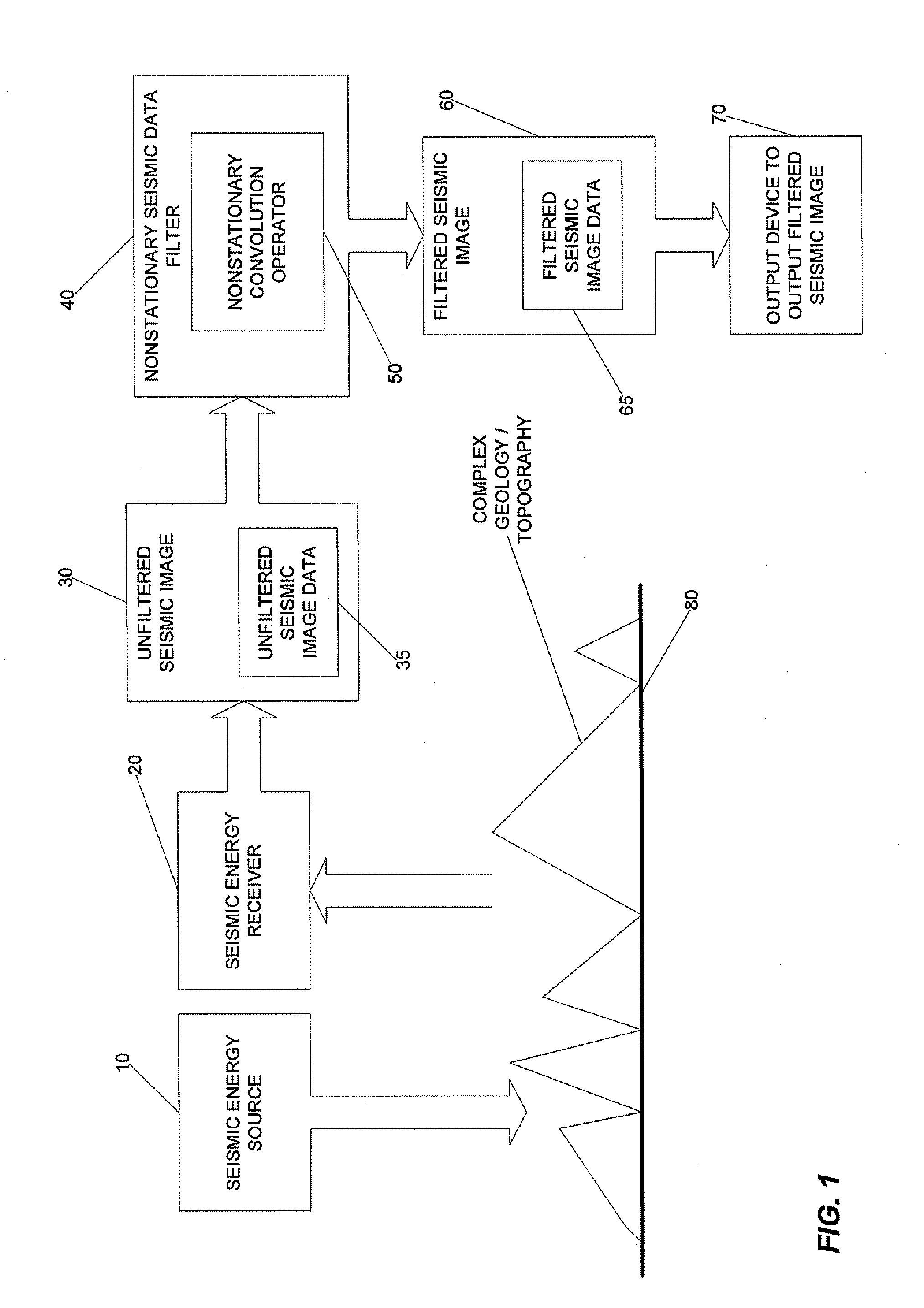
Seismic image filtering machine to generate a filtered seismic image, program products, and related methods
ActiveUS8321134B2Faster and efficient attenuationLow cost2D-image generationSeismic signal processingWave fieldAcoustics
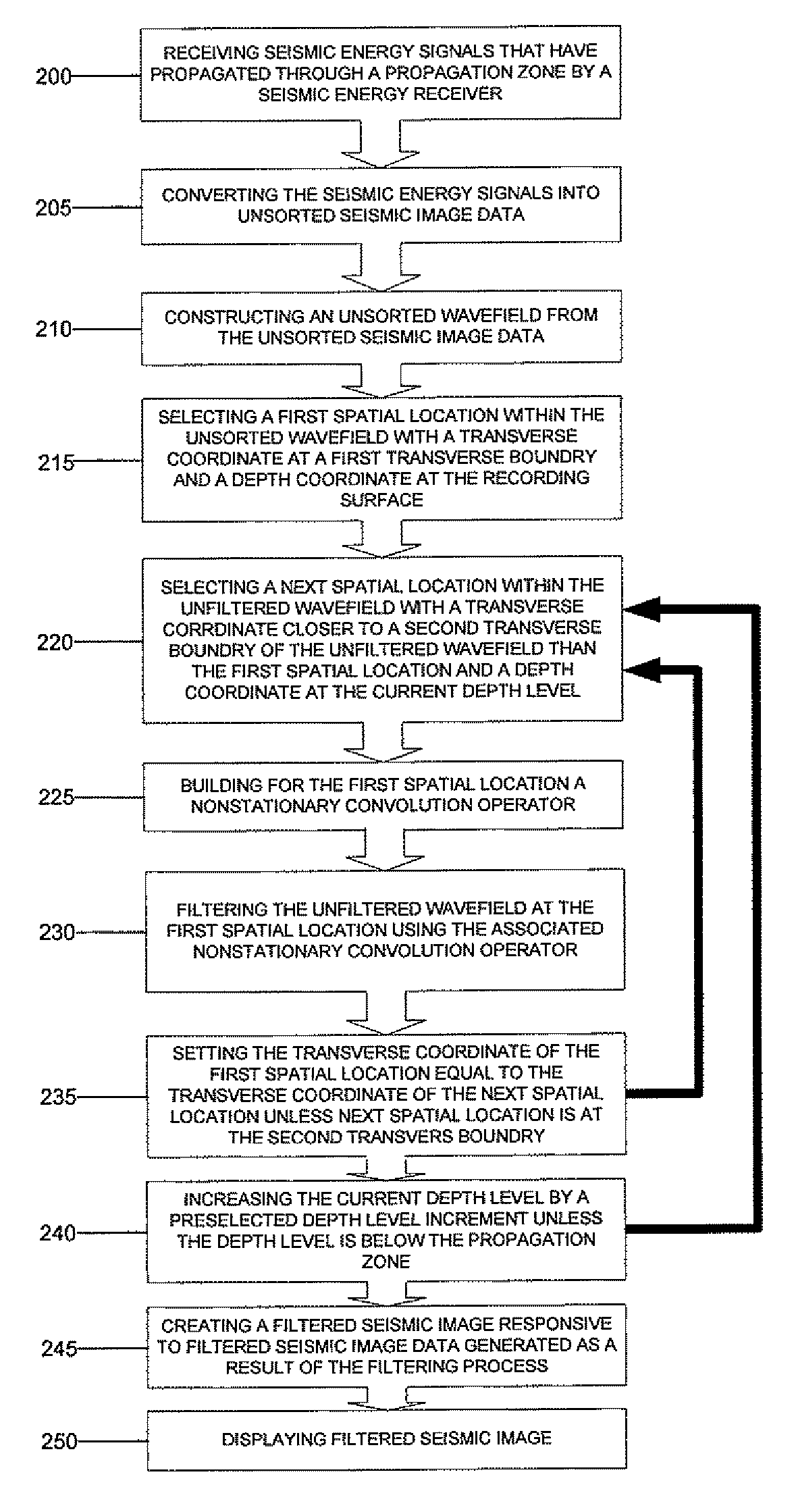
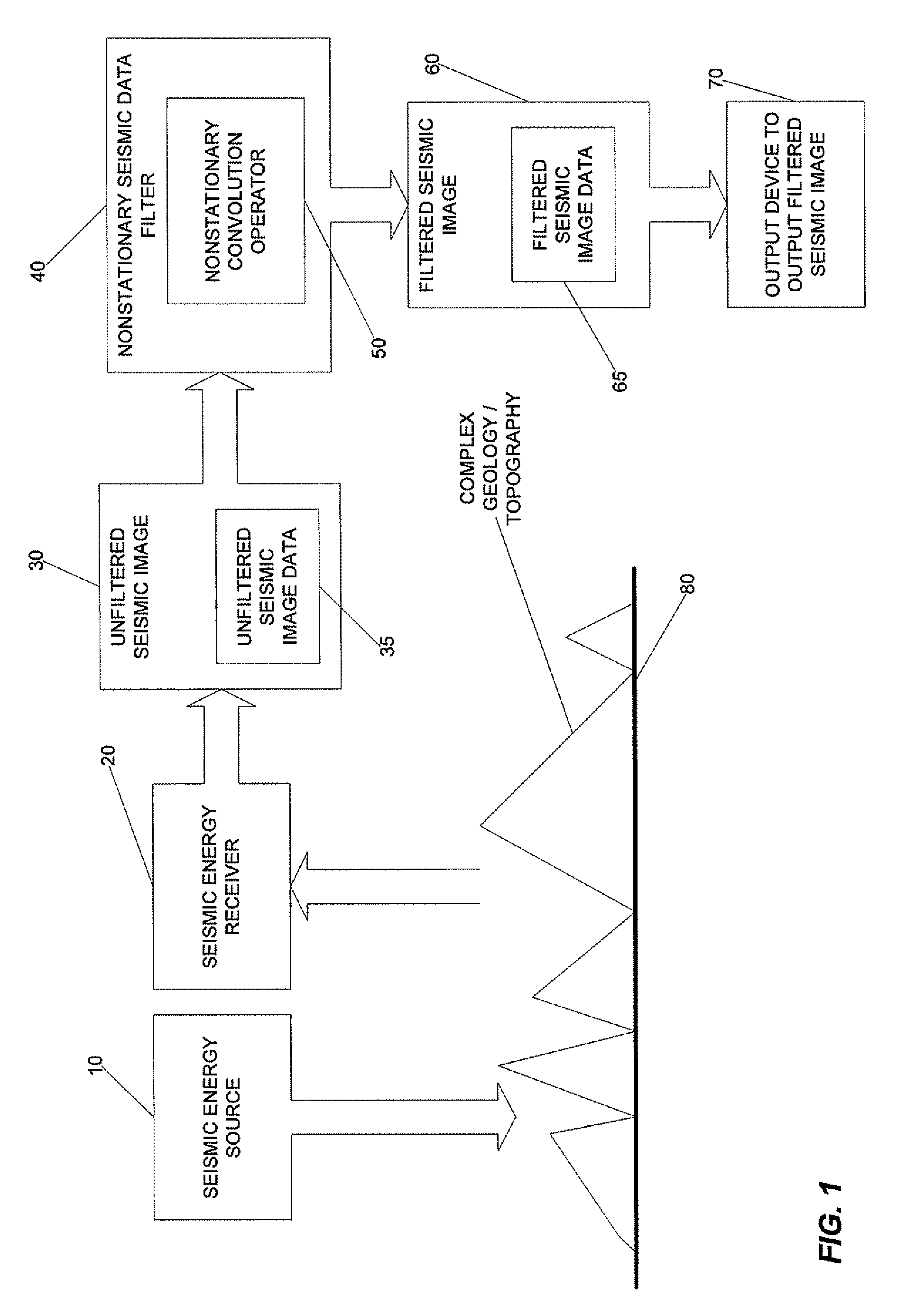
Seismic image filtering machines, systems, program products, and computer implemented methods are provided to generate a filtered seismic image responsive to filtered seismic image data generated by attenuating coherent seismic noise from surface waves of an unfiltered wavefield constructed from unfiltered seismic image data through a single downward extrapolation of the unfiltered wavefield using a plurality of nonstationary convolution operators to perform localized filtering at each of a plurality of spatial locations of the unfiltered wavefield. Various embodiments, for example, can beneficially handle strong lateral velocity variations thus making various embodiments effective tools to remove complicated coherent seismic noise which is typically in the form of exponentially decaying evanescent waves. Embodiments of the present invention, for example, can use, as a part of the filtering mechanism, specially designed nonstationary convolution operators that are implemented in the space-frequency domain as nonstationary filters.
Owner:SAUDI ARABIAN OIL CO
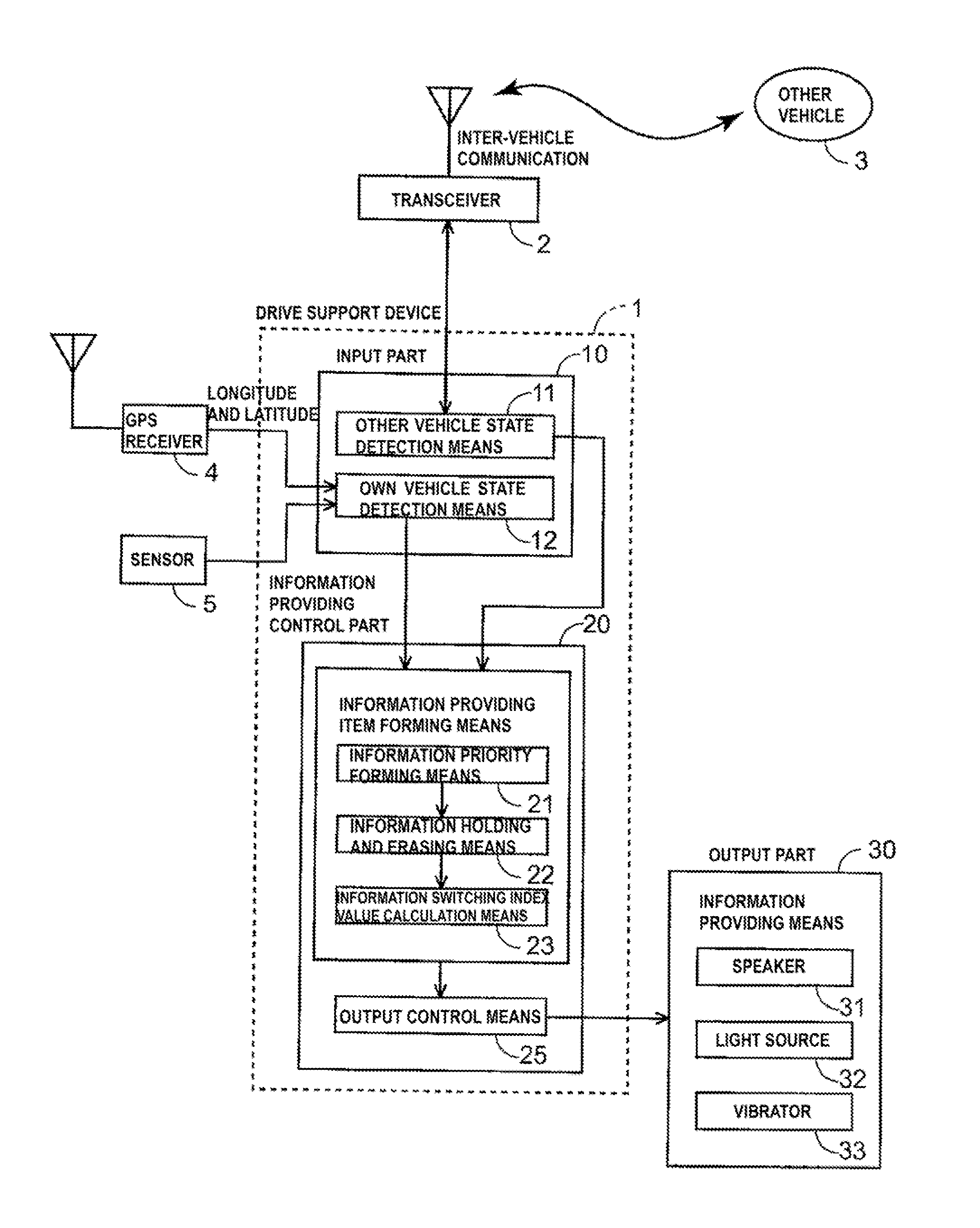
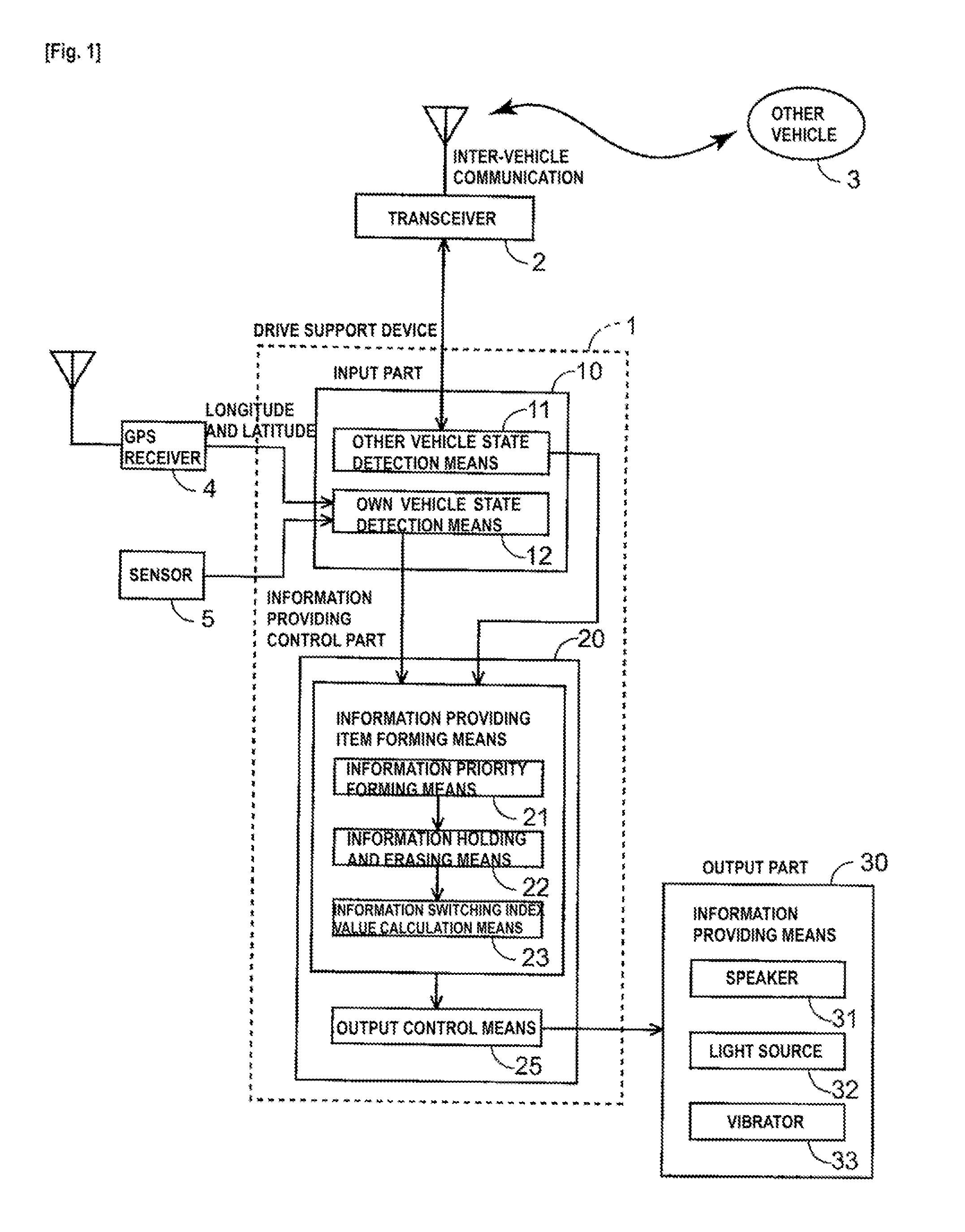
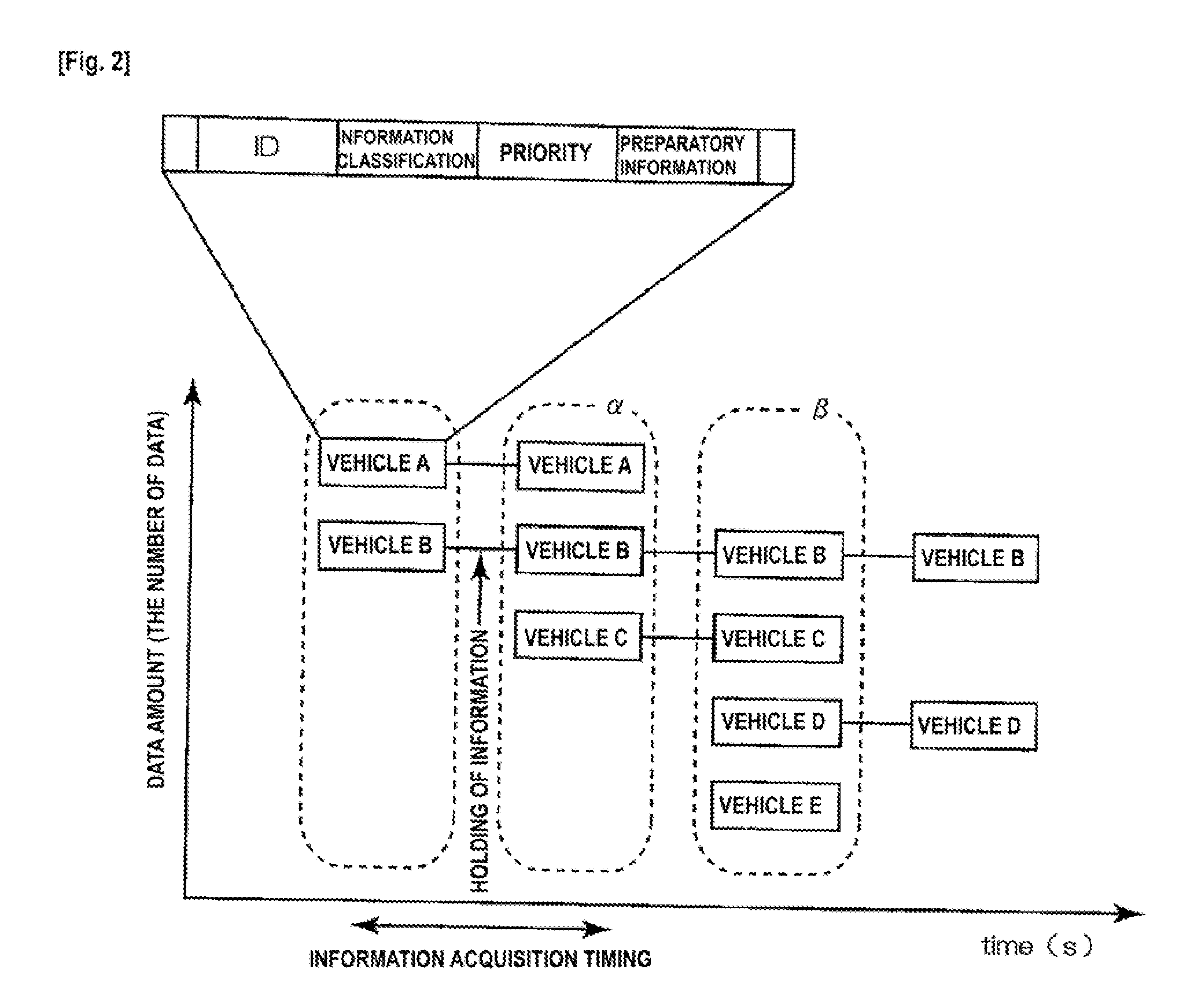
Other vehicle information providing device
ActiveUS20120083998A1Reduce storage capacityAvoid storage problemsAnalogue computers for vehiclesRoad vehicles traffic controlInformation provisionReal-time computing
Owner:HONDA MOTOR CO LTD
Seismic Image Filtering Machine To Generate A Filtered Seismic Image, Program Products, And Related Methods
ActiveUS20100114495A1Lower costIncreasing supply2D-image generationSeismic signal processingLateral velocitySurface wave
Seismic image filtering machines, systems, program products, and computer implemented methods are provided to generate a filtered seismic image responsive to filtered seismic image data generated by attenuating coherent seismic noise from surface waves of an unfiltered wavefield constructed from unfiltered seismic image data through a single downward extrapolation of the unfiltered wavefield using a plurality of nonstationary convolution operators to perform localized filtering at each of a plurality of spatial locations of the unfiltered wavefield. Various embodiments, for example, can beneficially handle strong lateral velocity variations thus making various embodiments effective tools to remove complicated coherent seismic noise which is typically in the form of exponentially decaying evanescent waves. Embodiments of the present invention, for example, can use, as a part of the filtering mechanism, specially designed nonstationary convolution operators that are implemented in the space-frequency domain as nonstationary filters.
Owner:SAUDI ARABIAN OIL CO
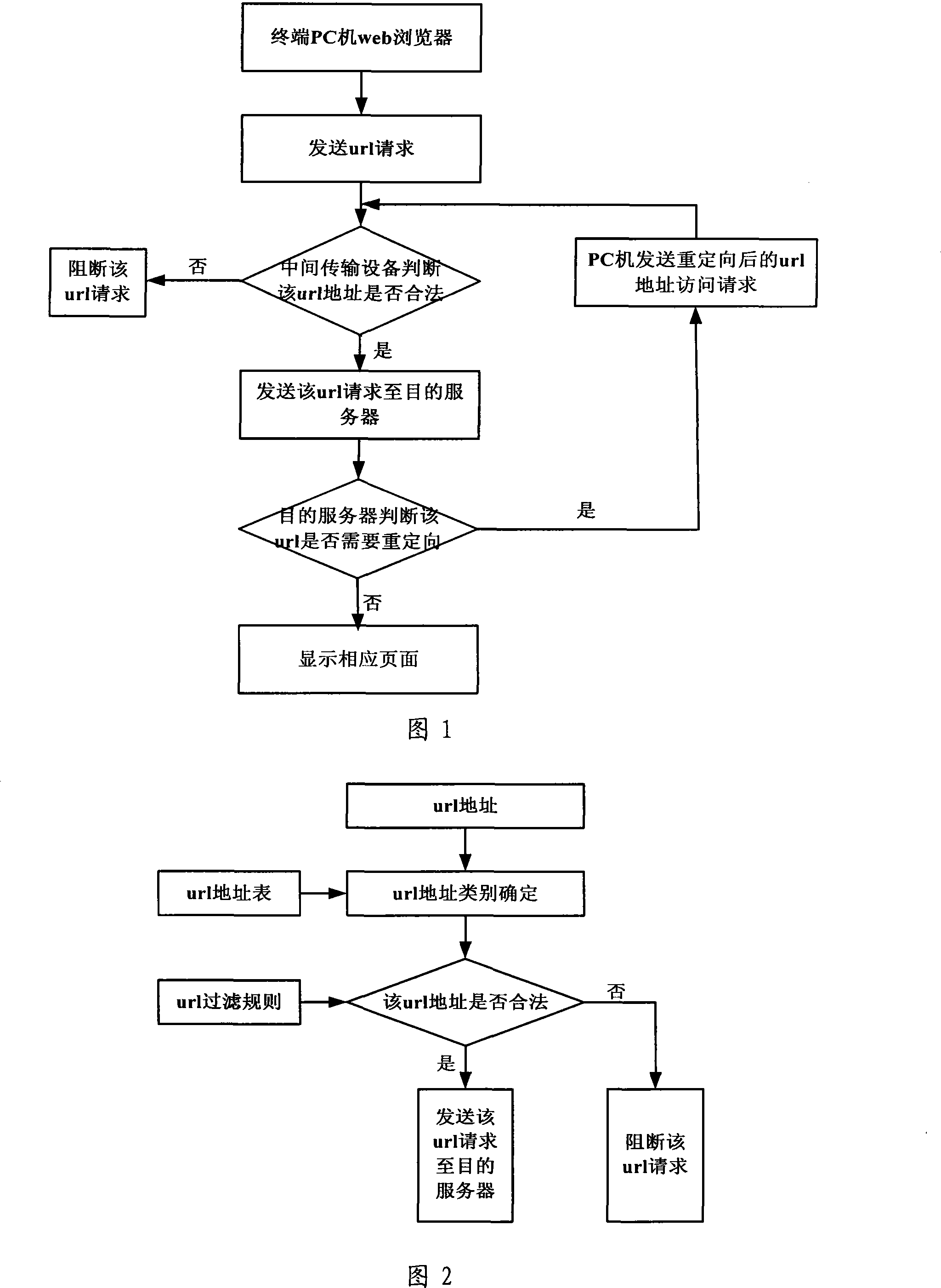
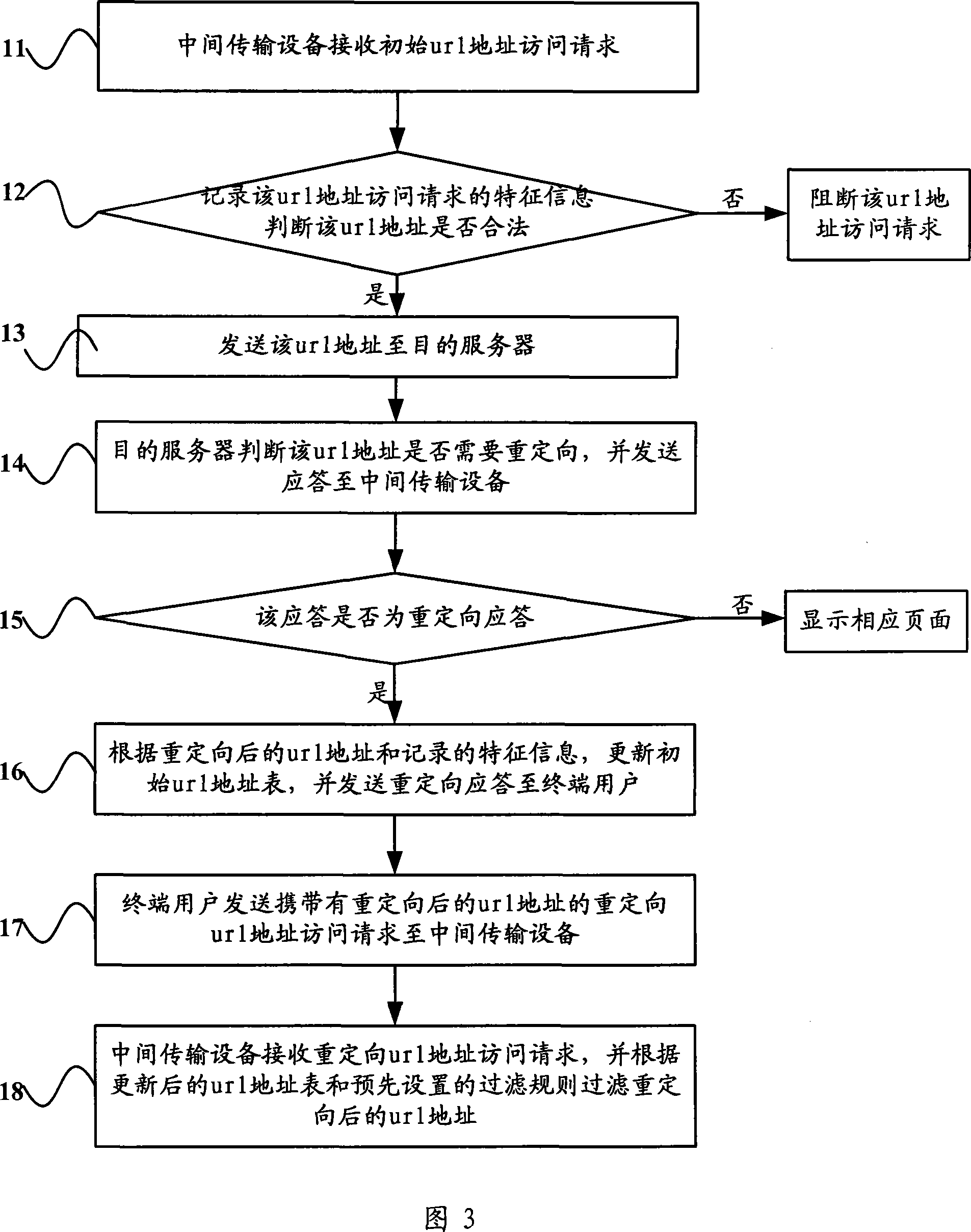
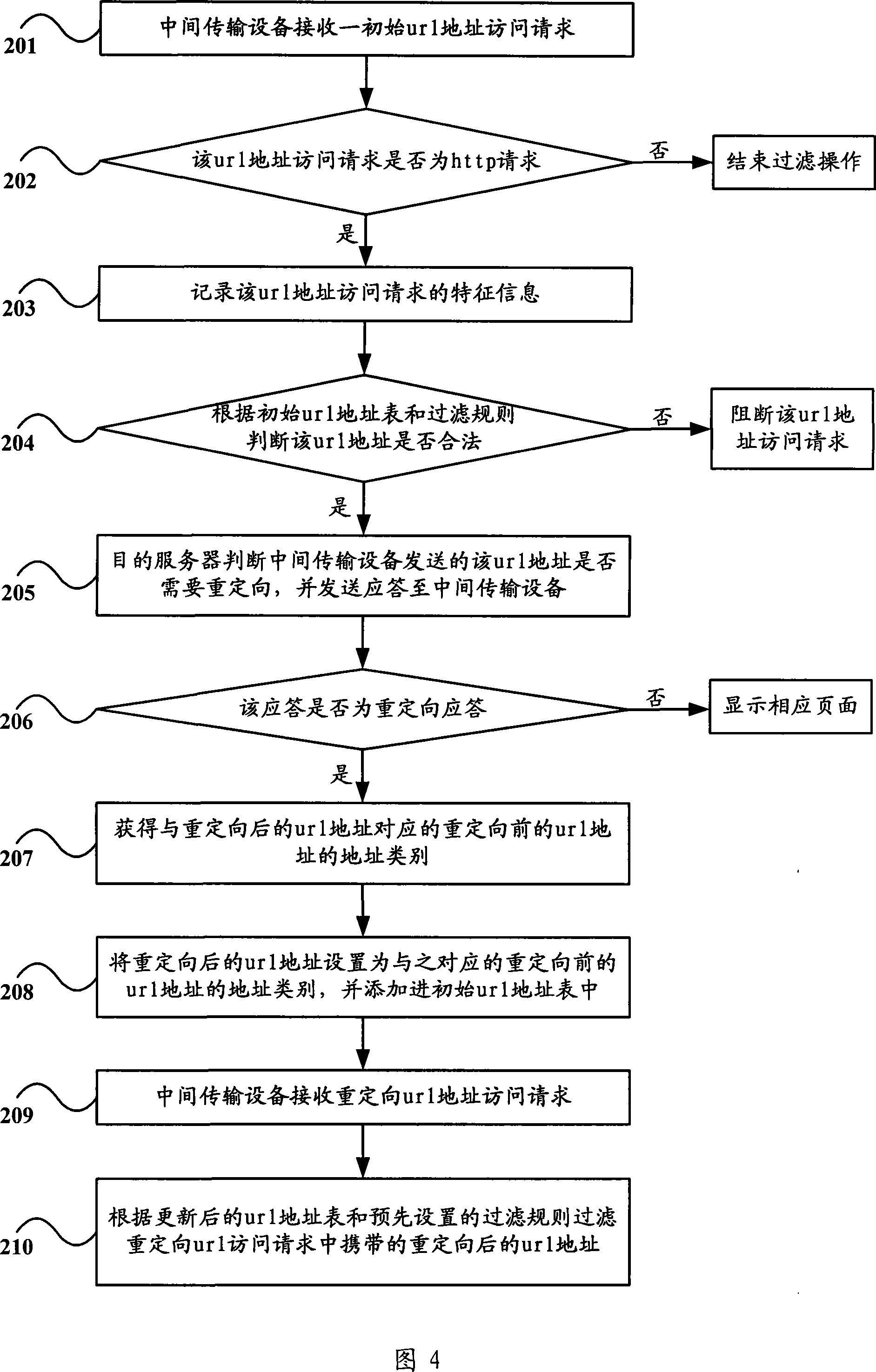
United resource localizer address filtering method and intermediate transmission equipment
ActiveCN101163161APrecise filterImplement updateError prevention/detection by using return channelData switching networksFiltering rulesUniform resource locator
The invention relates to a filtering method and a middle transmission equipment for url address. The filtering method for url address comprises the followings: characteristic information of access request of a url address is recorded, when redirection occurs, an initial url address list is updated according to the characteristic information and the redirected url address so that the redirected url address brings in correspondence with the address category of the url address before redirection and the redirected url address is filtered according to the updated url address list and a preset filtering rule; the middle transmission equipment comprises a unit recoding the characteristic information of access request of the initial address and a unit updating the initial url address list according to the redirected url address and the recorded characteristic information. With the filtering method and the middle transmission equipment for url address of the invention, the url address list can be updated dynamically and correct filtering of the redirected url address can be realized.
Owner:BEIJING ZHIGU TECH SERVICE
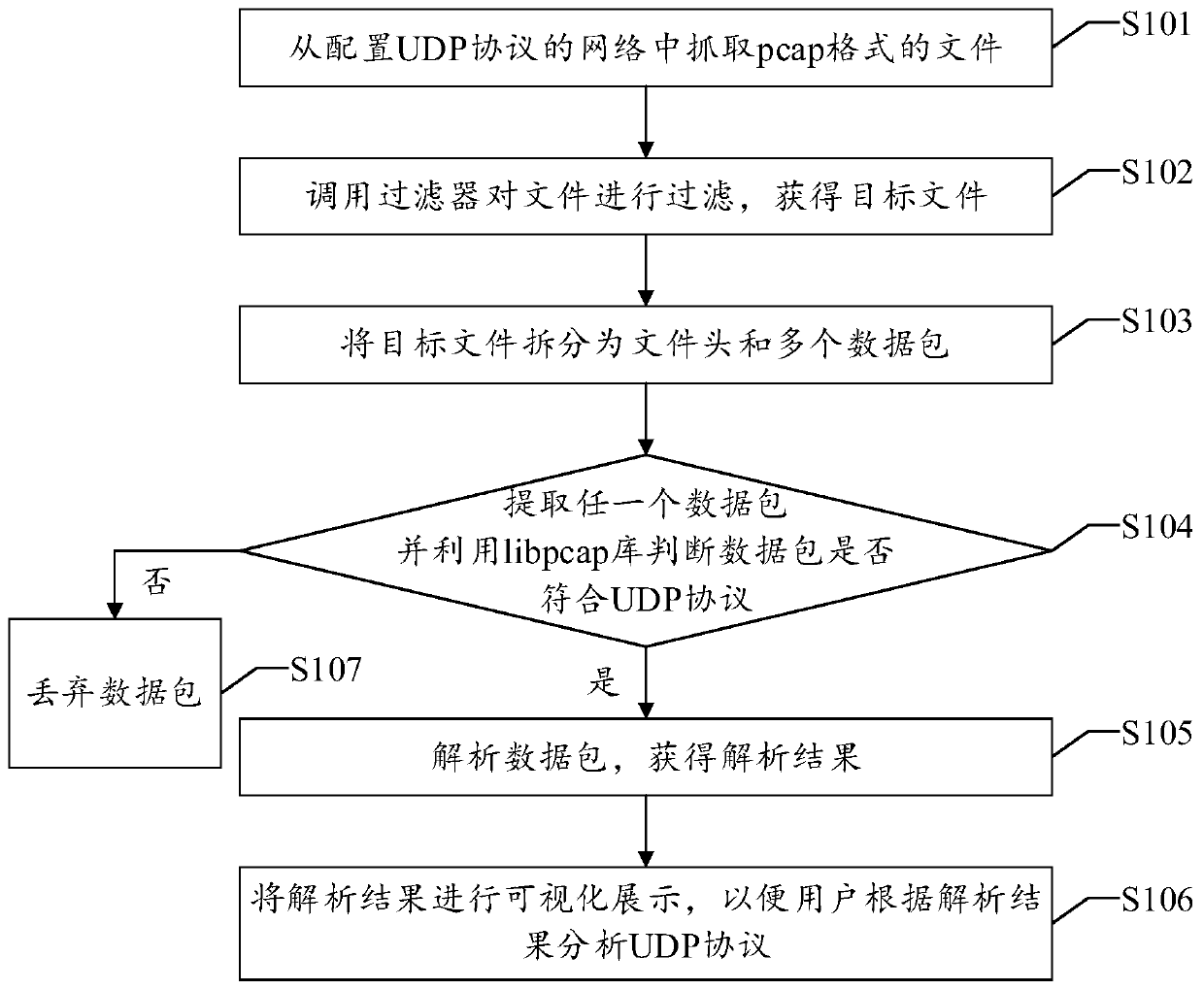
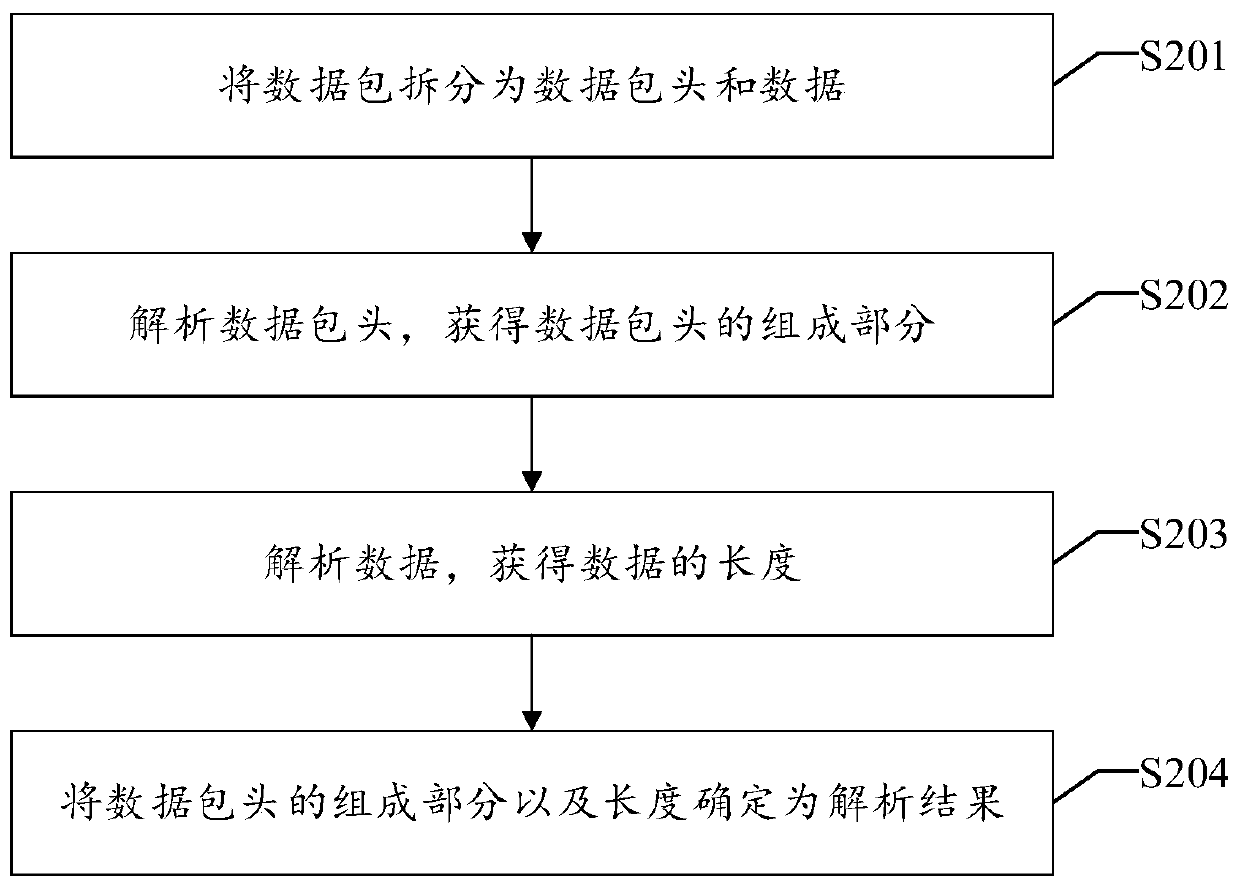
File analysis UDP protocol method, device based on file in pcap format
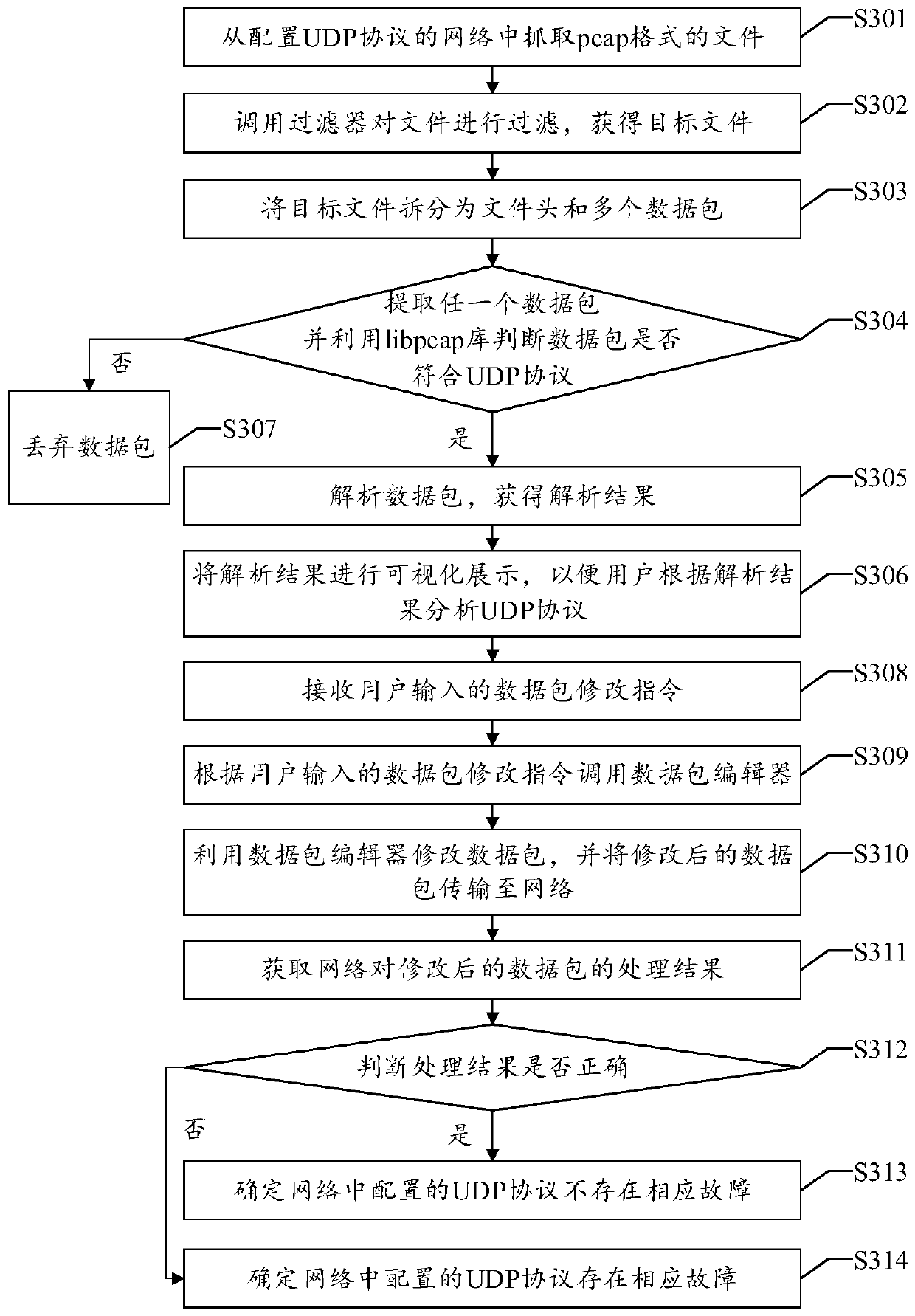
ActiveCN110661683AImprove accuracyImprove positioning accuracyData switching networksComputer securityUser Datagram Protocol
The invention discloses a file analysis UDP protocol method, device and apparatus based on a pcap format and a readable storage medium. The method disclosed by the invention comprises the following steps: capturing a file in a pcap format from a network configured with a UDP protocol; calling a filter to filter the file to obtain a target file; splitting the target file into a file header and a plurality of data packets; extracting any data packet, and judging whether the data packet conforms to a UDP (User Datagram Protocol) or not by utilizing a libpcap library; and if so, analyzing the datapacket to obtain an analysis result, and visually displaying the analysis result, so that the user analyzes the UDP protocol according to the analysis result. The filter and the libpcap library are utilized to avoid the influence of other data on the analysis result, and the analysis result can be visually displayed, so that the analysis accuracy of the UDP protocol and the positioning accuracy of the UDP protocol fault are improved.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Method and device for filtering out abnormal GPS data
The invention discloses a method and device for filtering out abnormal GPS data. The method includes the following steps that: GPS data uploaded in a preset time interval are acquired; the average traveling speed of a distance between adjacent GPS data is calculated according to position information in the GPS data and uploading time; the quantile of the upper-side preset percentage of the probability distribution of the average traveling speed is obtained, and the quantile is adopted as an abnormal speed threshold value; and abnormal average traveling speed in the average traveling speed, which is greater than the abnormal speed threshold value, is obtained, and GPS data corresponding to the abnormal average traveling speed is marked as abnormal GPS data. The invention also discloses a device for filtering out abnormal GPS data. According to the method and device of the present invention, the abnormal speed threshold value in a current time interval which is determined according to conditions in the preset time interval is more accurate; and the filtering out of the abnormal GPS data is more accurate since the abnormal speed threshold value is accurate.
Owner:SHENZHEN AUTONET CO LTD
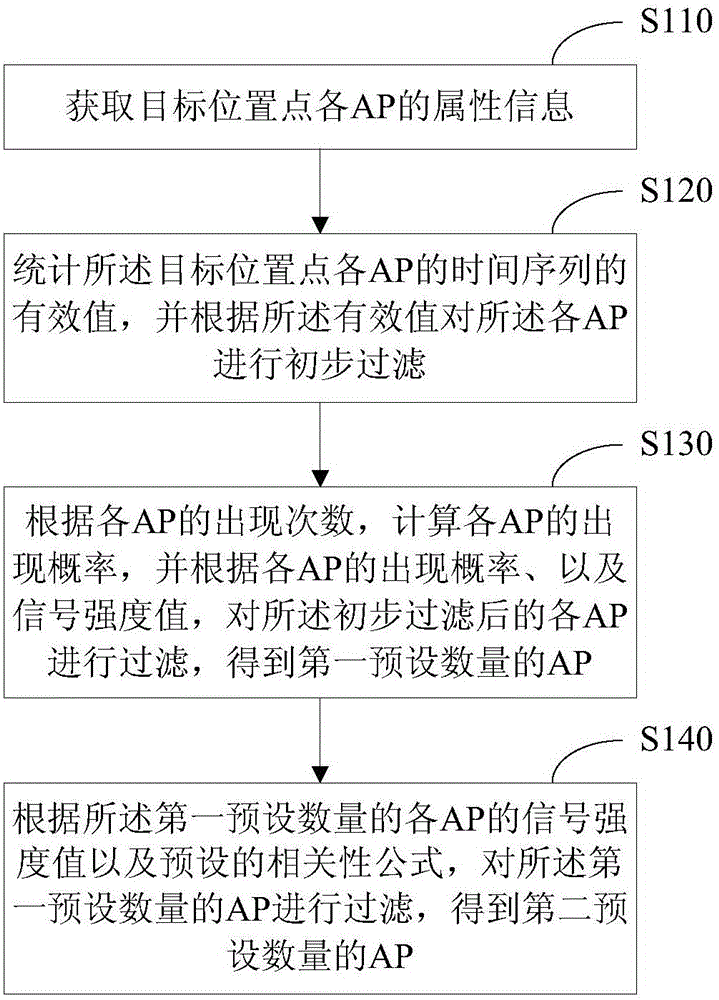
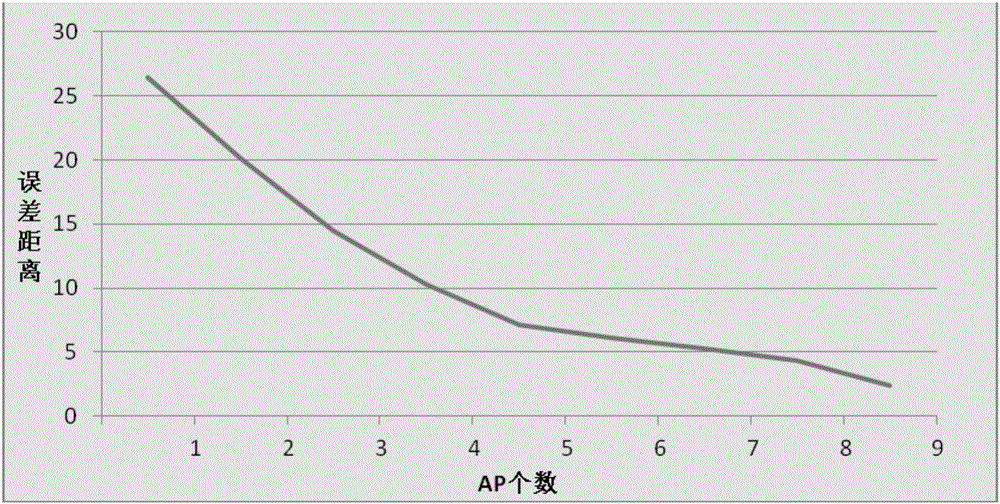
AP filtering method and device
ActiveCN106376080APrecise filterAvoid interferenceBeacon systems using radio wavesWireless communicationFrequency of occurrenceValid Value
An embodiment of the invention discloses an AP filtering method and device. The method comprises the following steps: attribute information of each AP of an object position is obtained; the attribute information at least comprises frequency of occurrence and signal intensity value; statistics is run on effective value of a time sequence of each AP of the object position, all APs are subjected to preliminary filtering operation according to the effective value, probability of occurrence of each AP is calculated according to the frequency of occurrence of each AP, all preliminarily filtered APs are subjected to filtering operation according to the probability of occurrence of each AP and the signal intensity value, and a first preset number of APs are obtained; according to the signal intensity value of each of the first preset number of APs and a preset correlation formula, the first preset number of APs are subjected to filtering operation, and a second preset number of APs are obtained. Via application of the AP filtering method and device, redundant APs can be filtered out accurately, on-line positioning complexity can be lowered, and on-line positioning precision can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Process and device for diagnostic and maintenance operations of aircraft
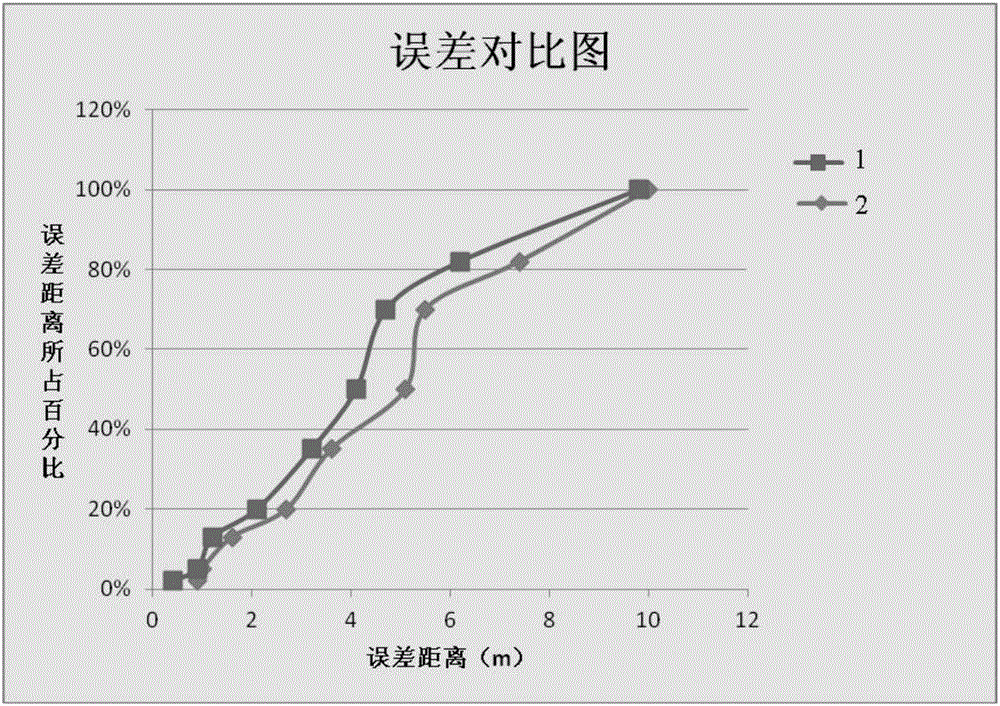
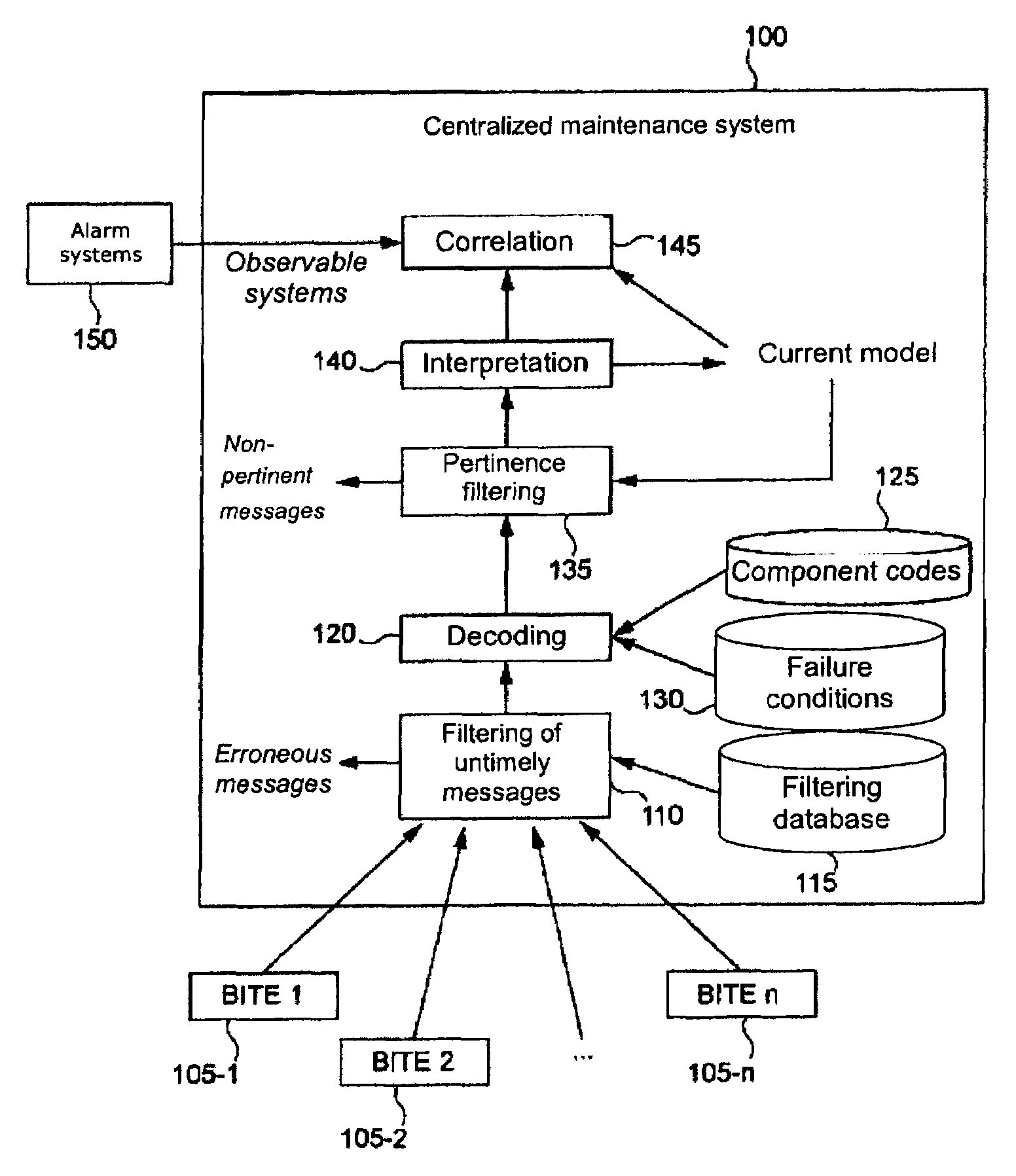
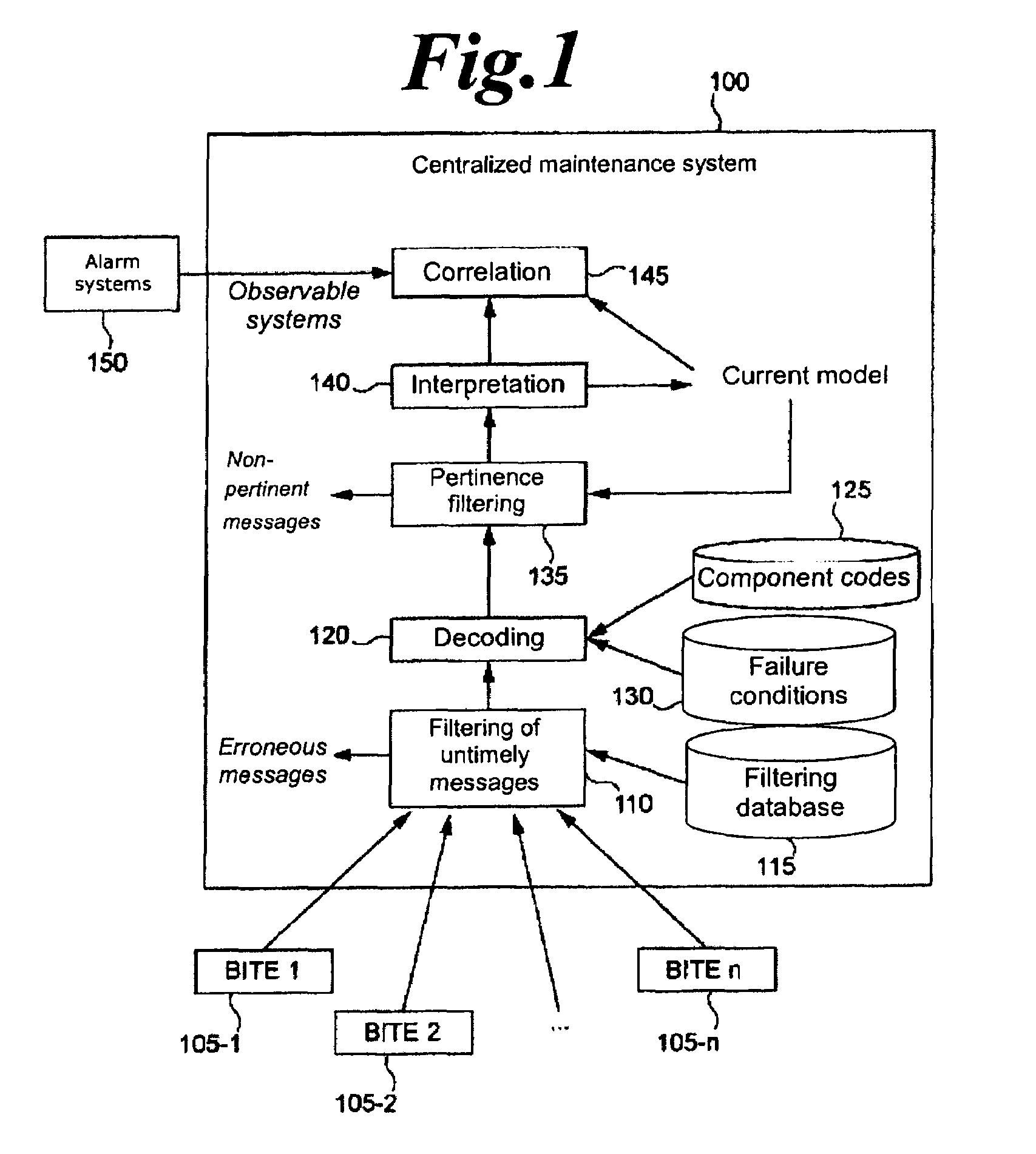
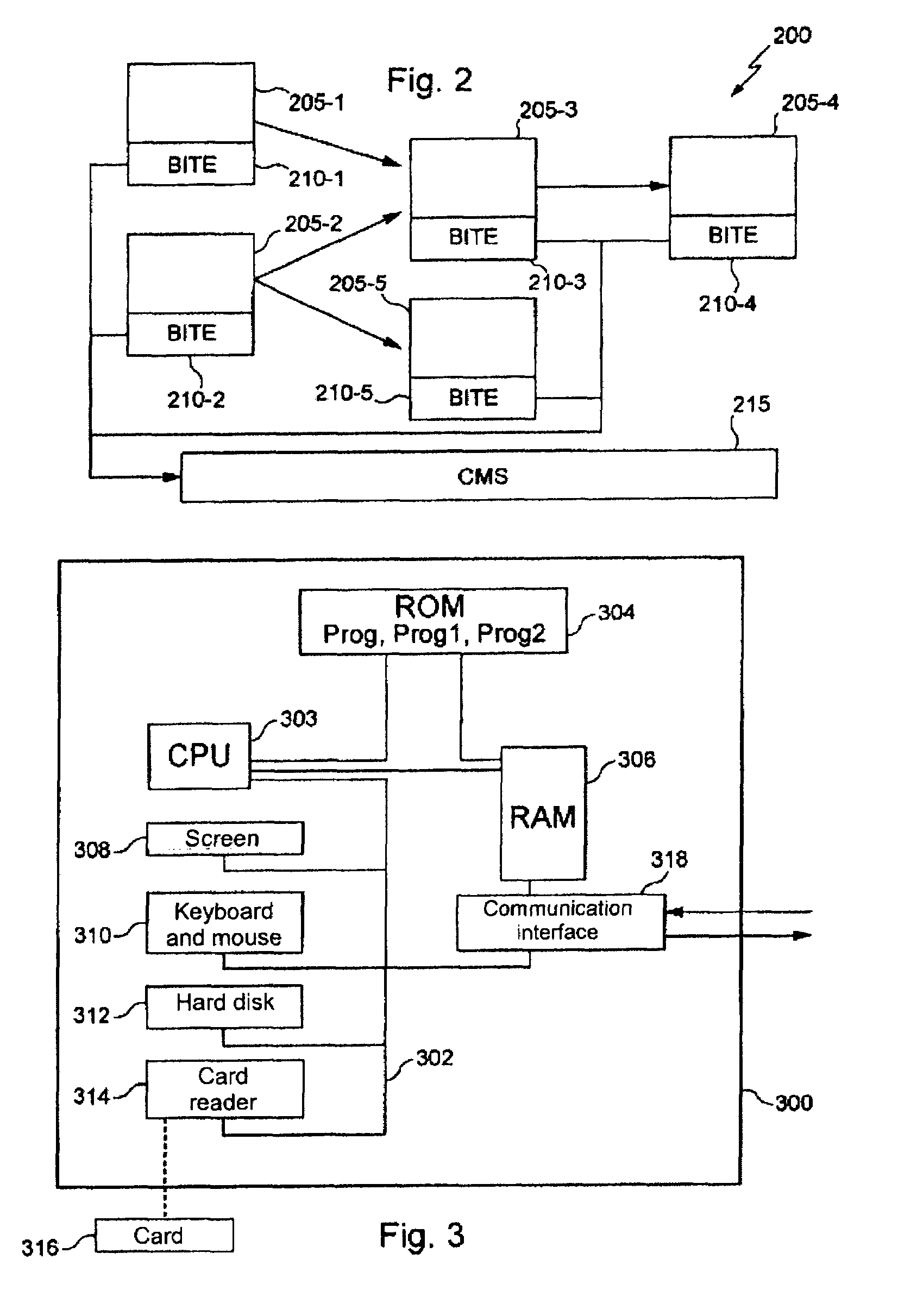
ActiveUS20090210104A1Precise filterVehicle testingRegistering/indicating working of vehiclesAirplaneComputer science
The object of the invention is a method and a device for filtering diagnostic messages obtained from a plurality of elements of a system, each of these elements comprising diagnostic means capable of detecting a failure and of transmitting a message comprising at least one failure indication. The state of at least certain elements of the said plurality of elements is represented by a model of state. After at least one failure message has been received, this message is filtered according to the failure indication that it contains and according to the model of state. In response to the filtering step, the model of state is updated according to the failure indication or the message is rejected. The filtering step is advantageously based on a propositional logic mechanism.
Owner:AIRBUS OPERATIONS SAS
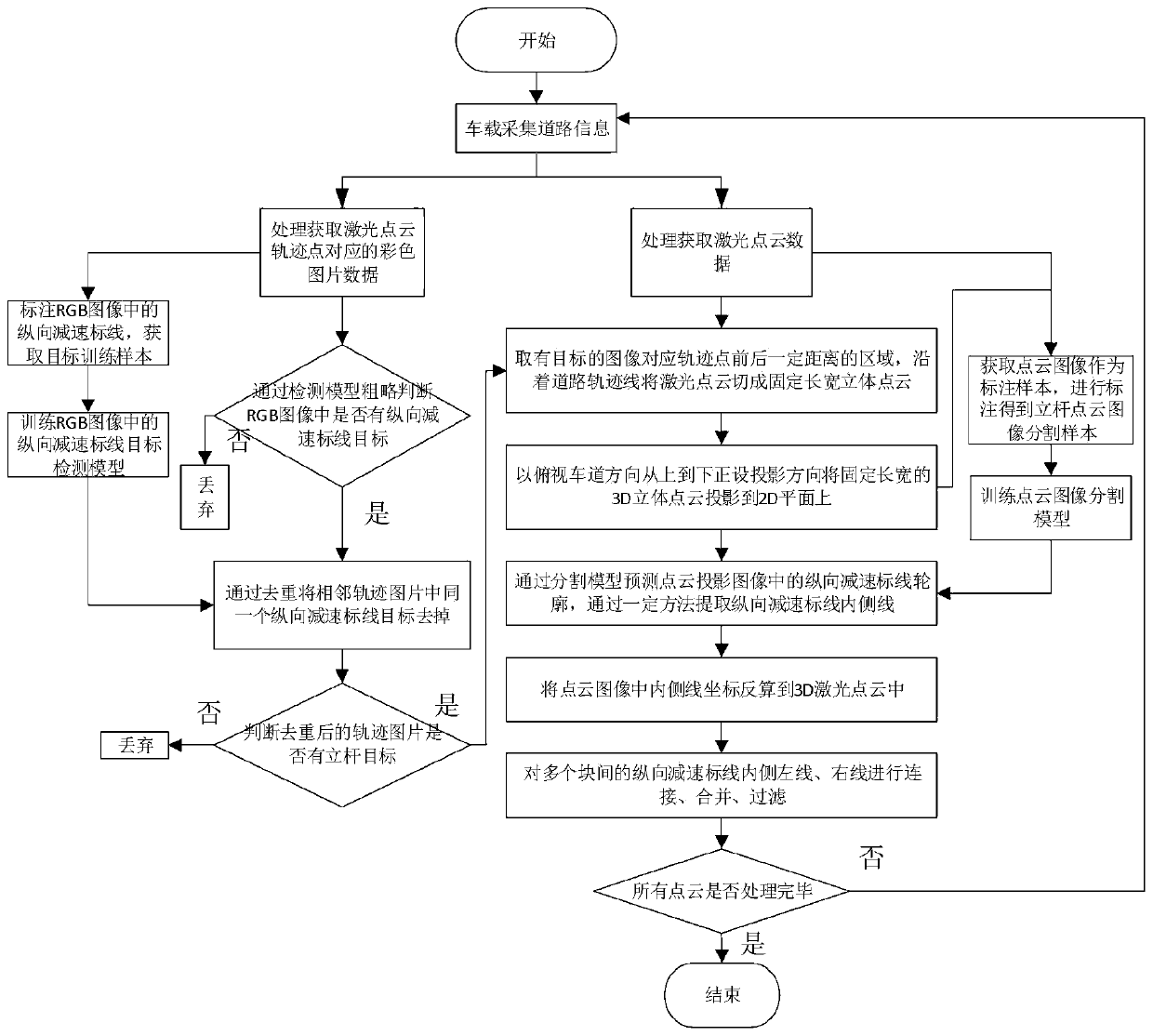
Method and device for automatically extracting longitudinal deceleration marked line in high-precision map making
The embodiment of the invention provides a method and a device for automatically extracting a longitudinal deceleration marked line in high-precision map making, and the method comprises the steps: quickly filtering a three-dimensional laser point cloud region where the longitudinal deceleration marked line is located through the extraction of the longitudinal deceleration marked line target detection network of a color image; besides, projecting the three-dimensional laser point cloud into a two-dimensional projection image, performing fine extraction of the longitudinal deceleration marked line conducted through a semantic segmentation network, and obtaining the inner side lines of the longitudinal deceleration marked line; furthermore, filtering an inner side line which is short in length and is mistakenly identified through a straight line connection line in the three-dimensional laser so that the longitudinal deceleration marked line is accurately extracted, and the precision of the longitudinal deceleration marked line extracted from the three-dimensional point cloud meets the requirement of high-precision map making. With application of AI training, the longitudinal deceleration marking line can be suitable for various complex traffic road scenes.
Owner:WUHAN ZHONGHAITING DATA TECH CO LTD
VPLS (Virtual Private LAN Service) output route filtering method and device based on BGP (Border Gateway Protocol)
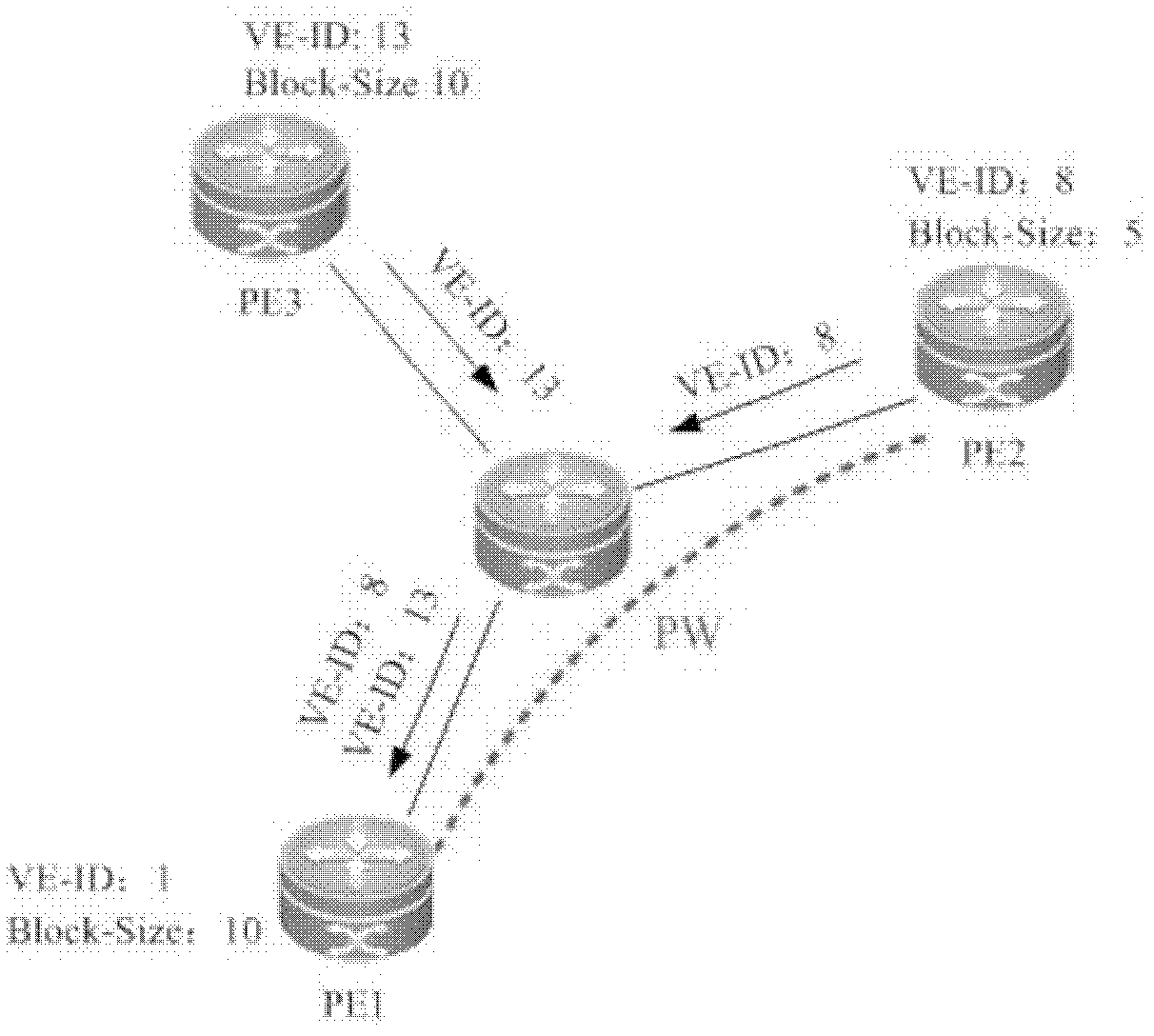
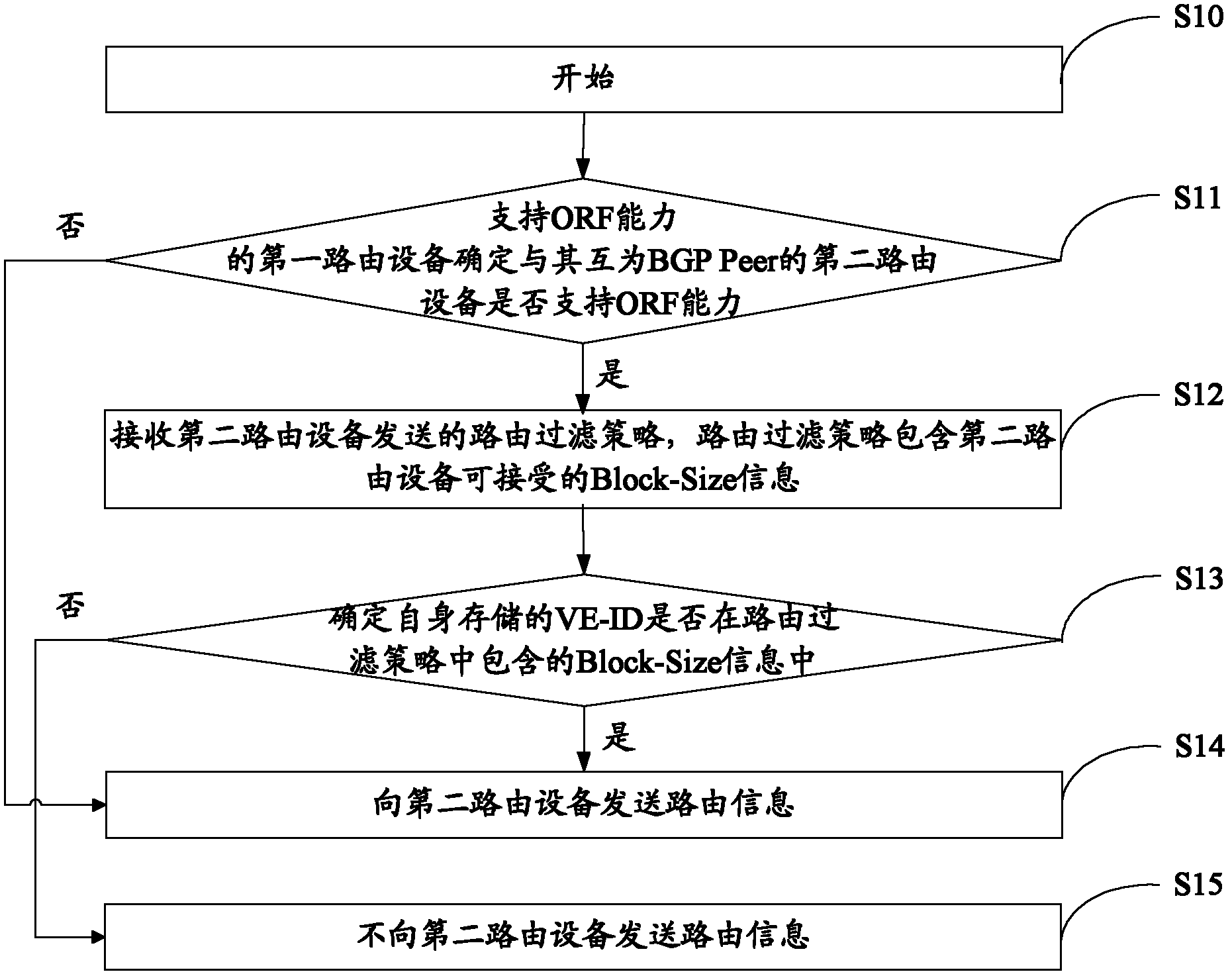
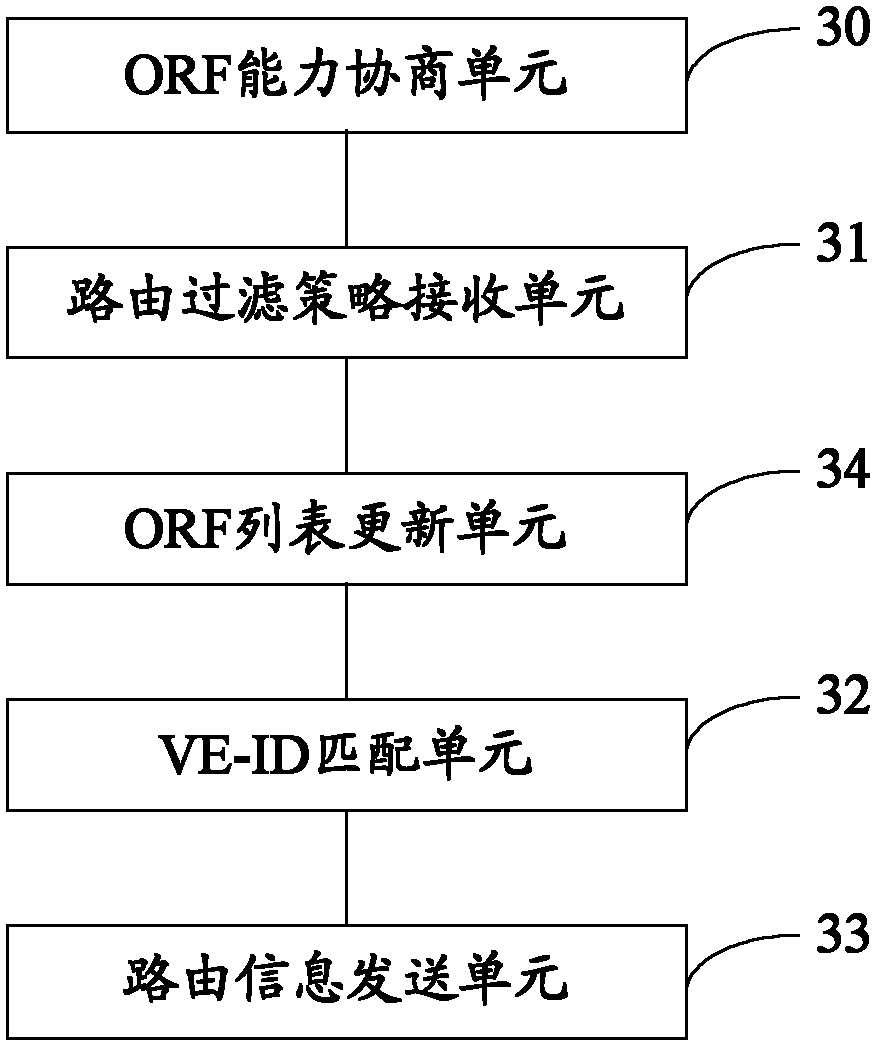
InactiveCN102611632APrecise filterSave resourcesNetworks interconnectionInternal memoryBorder Gateway Protocol
The invention discloses a VPLS (Virtual Private LAN Service) output route filtering method and a device based on a BGP (Border Gateway Protocol). The VPLS output route filtering method comprises the following steps that: after first route equipment which supports an output route filtering ORF (Open Reading Frame) capacity determines that second route equipment, which is a BGP Peer with the first route equipment, supports the ORF capacity, a route filtering strategy sent by the second route equipment is received, wherein the route filtering strategy comprises acceptable station point range Block-Size information of the second route equipment; and when the first route equipment determines that the station point information VE-ID stored by the first route equipment is in the Block-Size information included by the route filtering strategy, route information is sent to the second route equipment. With the adoption of the scheme, the useless information of a receiver can be accurately filtered, so as to save network resources and internal memories of the route equipment.
Owner:RUIJIE NETWORKS CO LTD
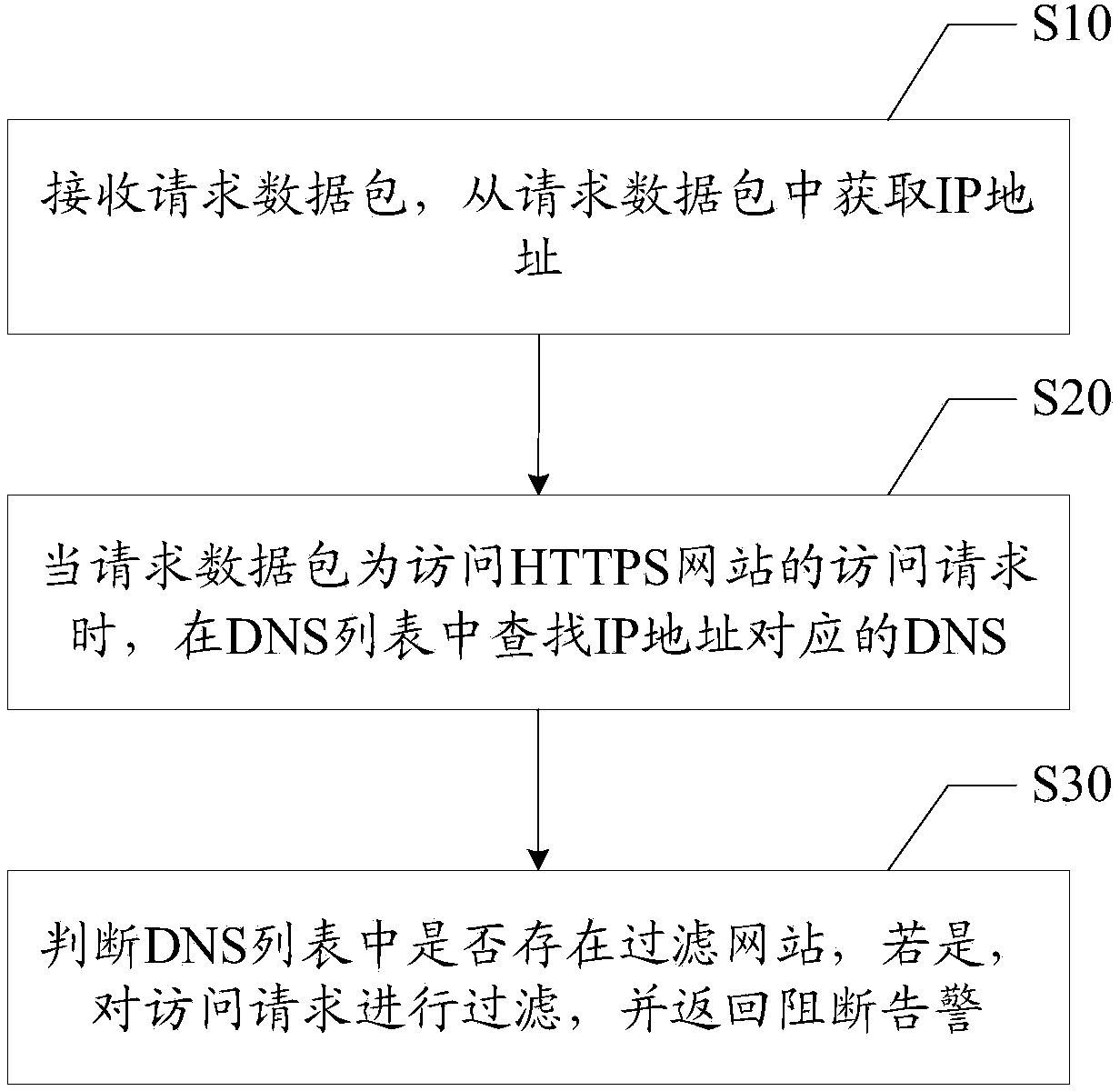
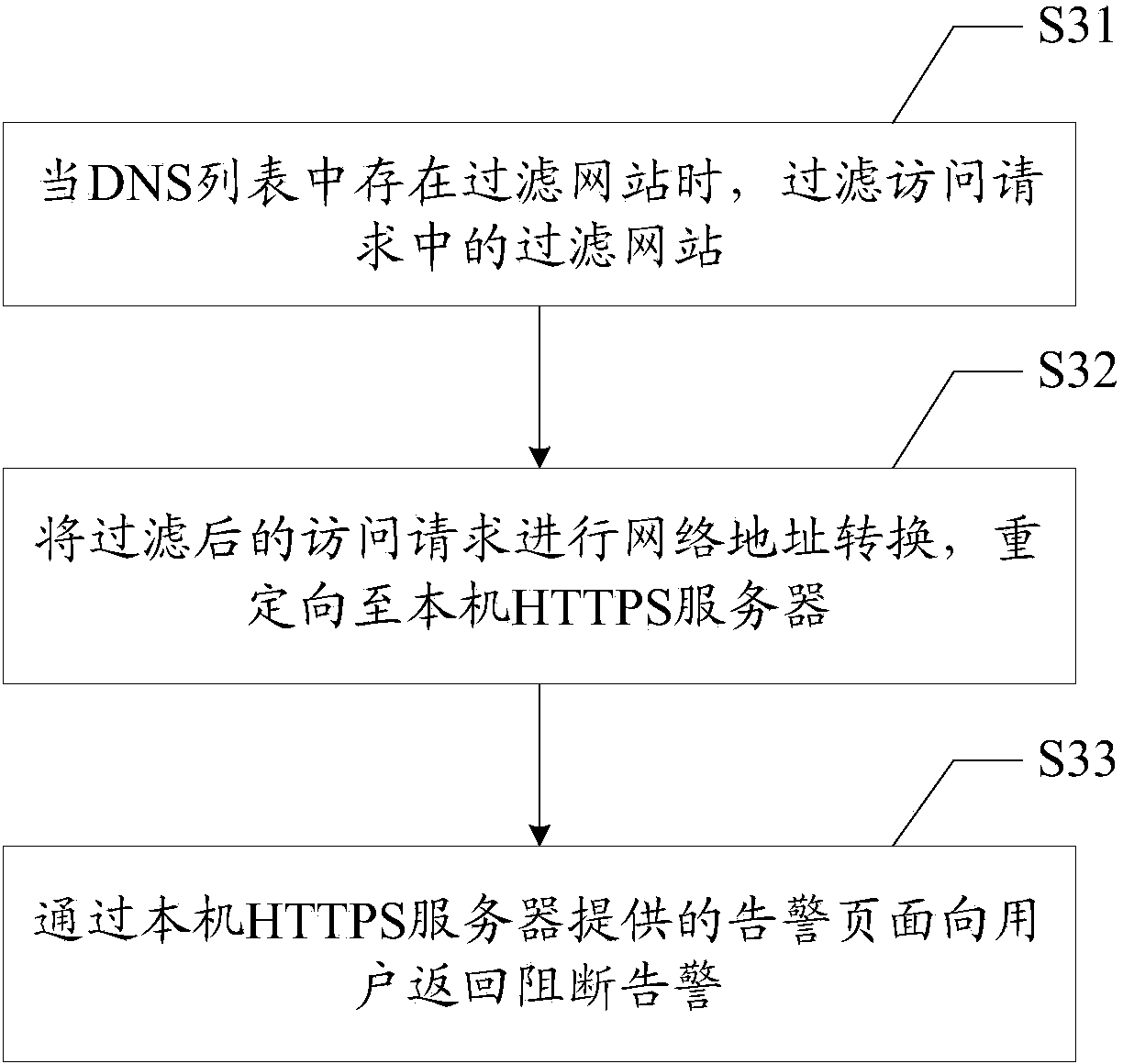
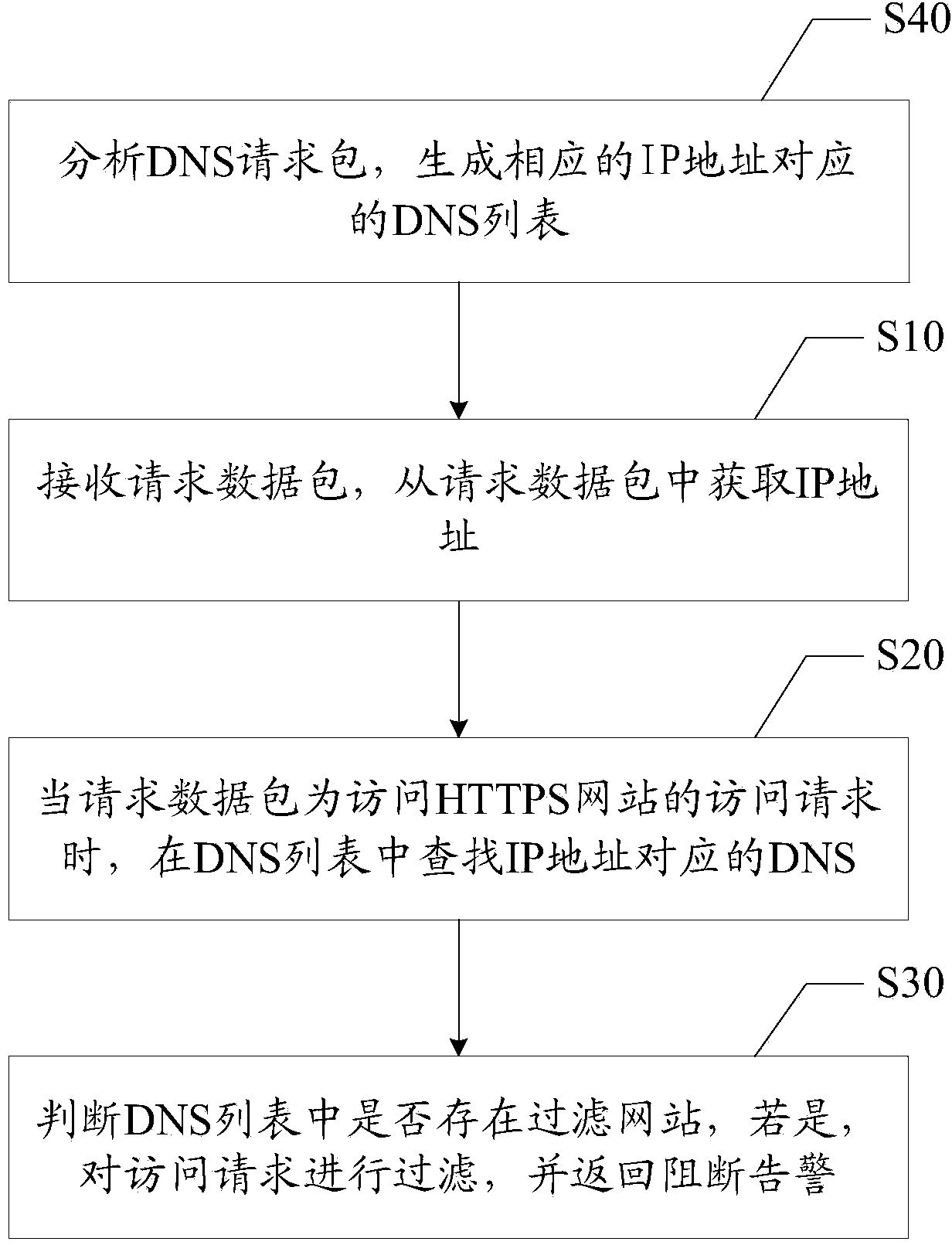
HTTPS (Hypertext Transfer Protocol Secure) website filtration and interdict alarm method and device
The invention discloses an HTTPS (Hypertext Transfer Protocol Secure) website filtration and interdict alarm method. The method comprises the following steps of receiving a request data package and obtaining an IP (Internet protocol) address from the request data package; when the request data package is an access request for accessing an HTTPS website, searching for a DNS (Domain Name Server) corresponding to the IP address in a DNS list; judging whether a filtration website exists in the DNS list; if so, filtering the access request, and returning an interdict alarm. The invention also discloses an HTTPS website filtration and interdict alarm device. As not all HTTPS requests need to be intercepted and captured, only the HTTPS request in which the filtration website exists in the DNS list is filtered, other HTTPS requests pass, and thus the HTTPS website is accurately filtered, and the interdict alarm can be provided for a user after the requests are filtered.
Owner:SANGFOR TECH INC
Image filtering method and device
ActiveCN102521610APrecise filterReduce false positive rateImage analysisCharacter and pattern recognitionSKIN REGIONSFilter methods
The invention discloses an image filtering method and a device capable of greatly reducing misjudgment ratio in a filtering process and quickly and accurately filtering porn. The image filtering method, provided by the embodiment of the invention, comprises the steps of: extracting a skin region in an original picture by picture region segmentation, calculating area ratio of the skin region in the original picture, permitting the original picture when the area ratio is smaller than a first threshold, obtaining a clipped picture including the skin region according to the original picture when the area ratio is more than the first threshold and less than a second threshold, filtering the original picture by the area ratio of the skin region in the clipped picture, detecting a face skin region in the original picture when the area ratio is more than the second threshold, and filtering the original picture according to the area ratio of the face skin region in the skin region.
Owner:BEIJING FEINNO COMM TECH
Target image detection method, device and system
InactiveCN109034266APrecise filterAccurately determineCharacter and pattern recognitionImage detectionNetwork model
The invention discloses a target image detection method, a device and a system. The method comprises: inputting an image to be processed into a full convolution neural network model, so that the fullconvolution neural network model identifies an image to be processed to output candidate position information of each candidate target image; and outputting the candidate position information of the candidate target image to be processed; extracting candidate target images corresponding to each candidate position information; enlarging each candidate target image to form a standard image, and recording an enlargement multiple corresponding to each standard image; aiming at the standard image, the standard image being inputted into the cascade convolution neural network model, so that the cascade convolution neural network model recognizing the standard image and outputting the current position information and classification probability of the suspicious target image. According to the current position information and classification probability of the suspicious target image, the magnification corresponding to each standard image and the candidate position information of each candidate target image, the position information of the target image is determined. The technical proposal of the invention can more accurately determine the position information of the target image.
Owner:ENNEW DIGITAL TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com