Method and unit for extracting traffic attack message characteristics on network equipment
A technology for network messages and network equipment, applied in data exchange networks, electrical components, digital transmission systems, etc., can solve problems such as manslaughter, and achieve the effect of ensuring normal passage and accurate filtering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The technical solution of the present invention will be described in more detail below with reference to the drawings and embodiments.
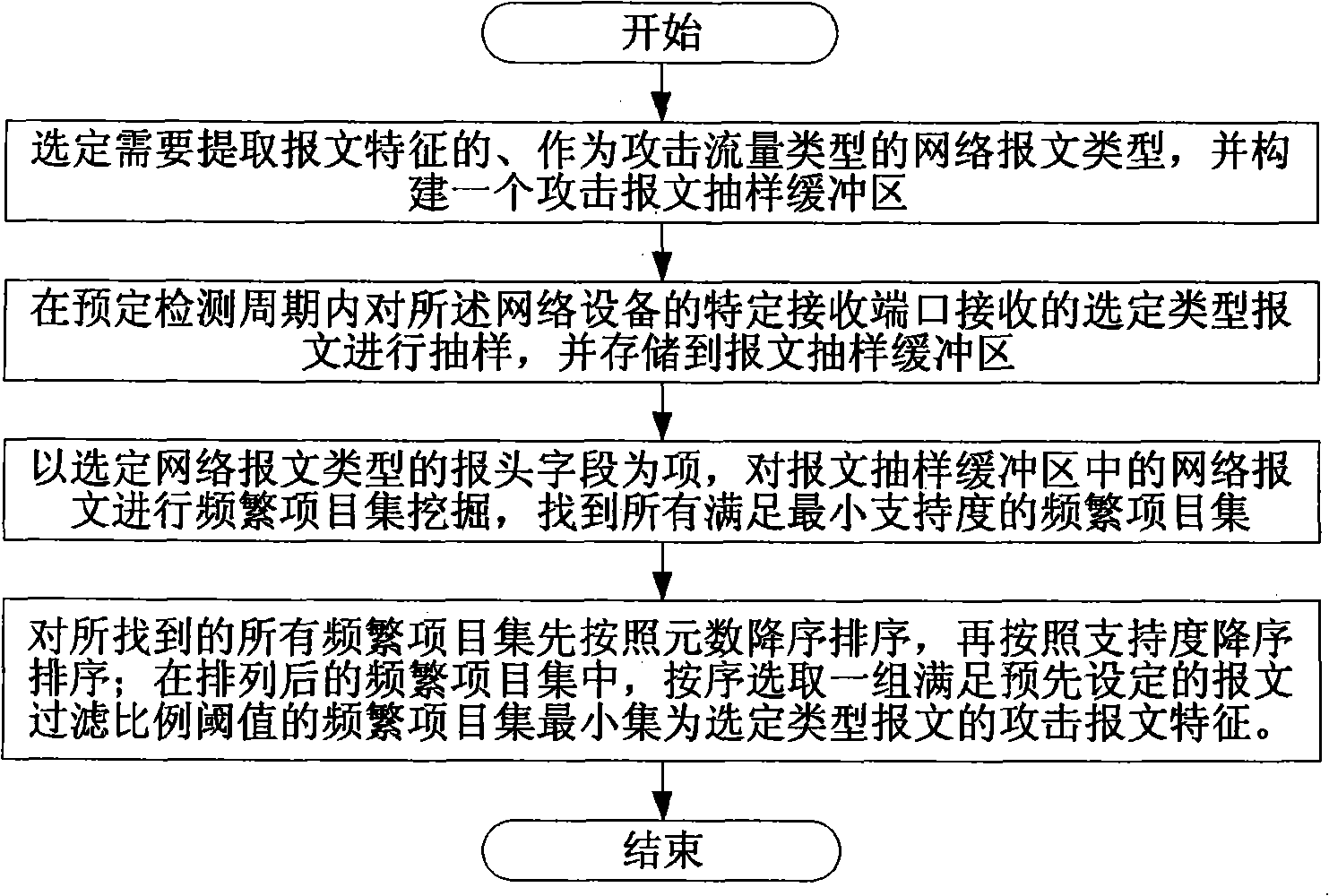
[0054] The present invention provides a method for extracting characteristics of traffic attack messages on network equipment, including:
[0055] Select the type of network packet that needs to extract packet features as the type of attack traffic;
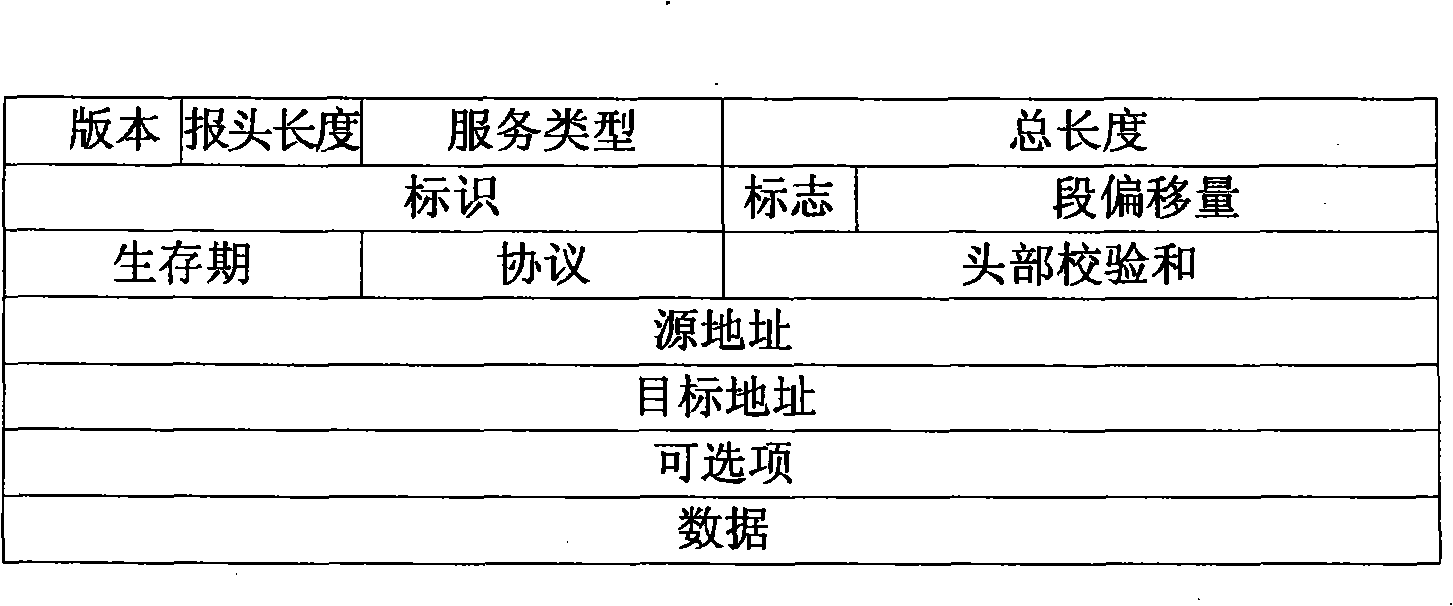
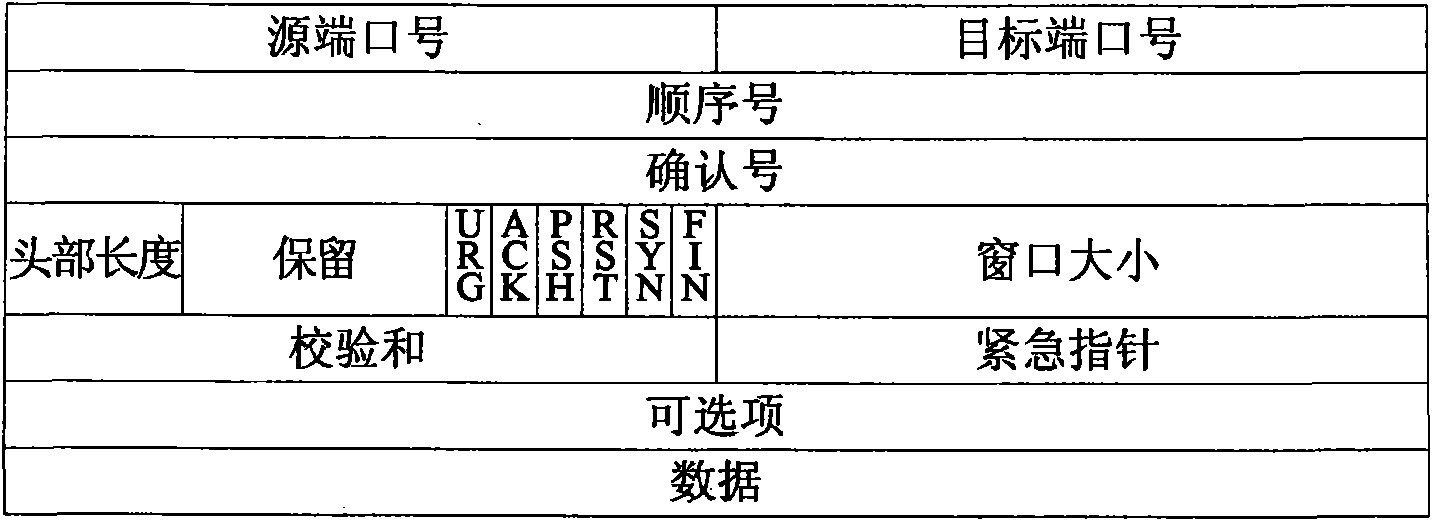
[0056] Taking the header field of the selected type of message as an item, in the received selected type of network message, find all frequent item sets that meet the minimum support;
[0057] First sort all the found frequent item sets in descending order of arity, and then sort the frequent item sets with the same arity in descending order of support; from the sorted frequent item sets, select a group of items that meet the packet filtering ratio threshold in turn. The minimum set of frequent item sets is the attack message characteristic of the selected type of message.
[0058] Wher...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com