Method for BIOS authentication prior to BIOS execution
a bios and authentication technology, applied in the field of bios authentication prior to bios execution, can solve the problems of unauthorized memory use protection, mechanism is still vulnerable to component or device replacement, and can easily be circumvented by password-based security mechanisms and other current security mechanisms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
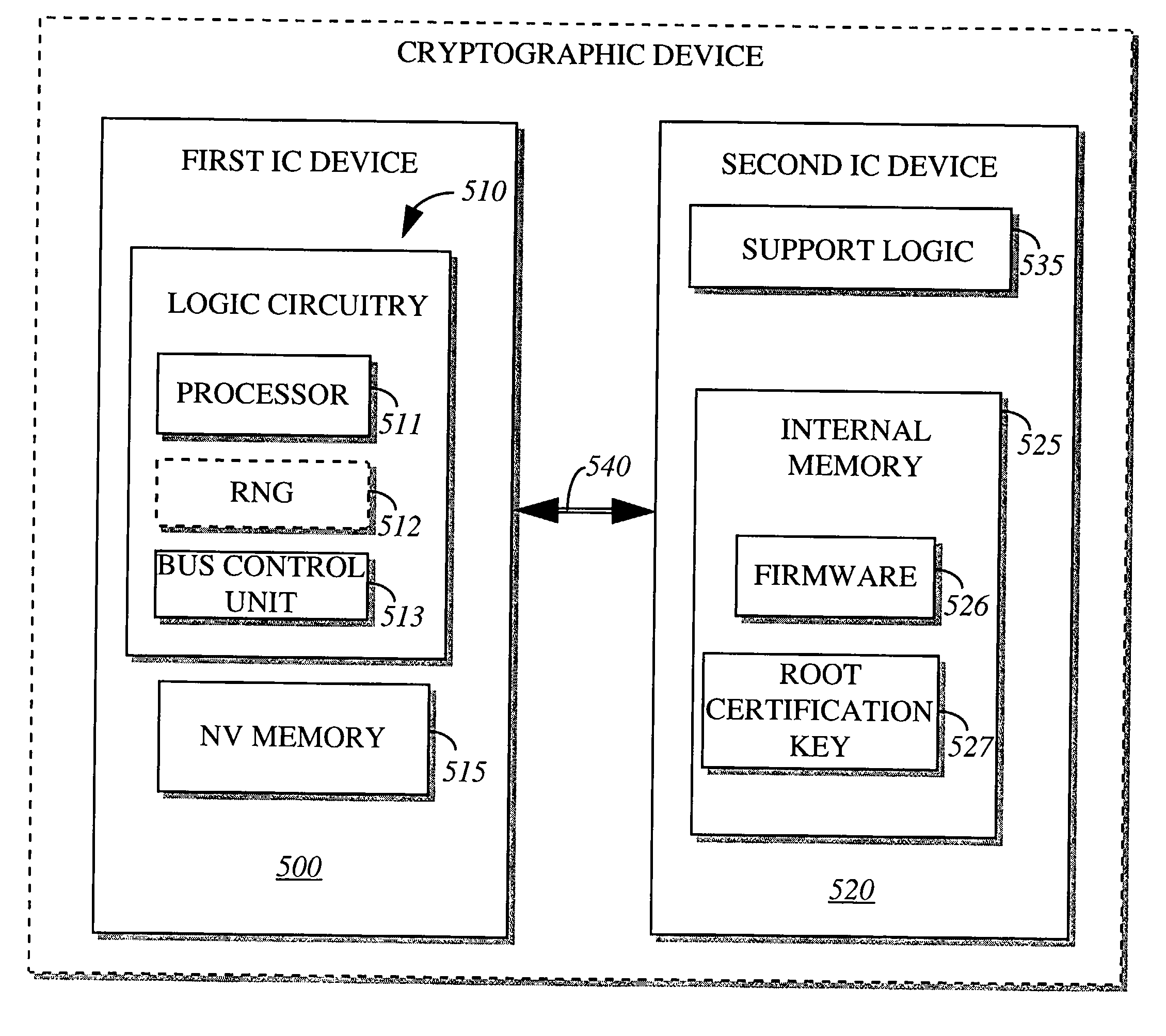
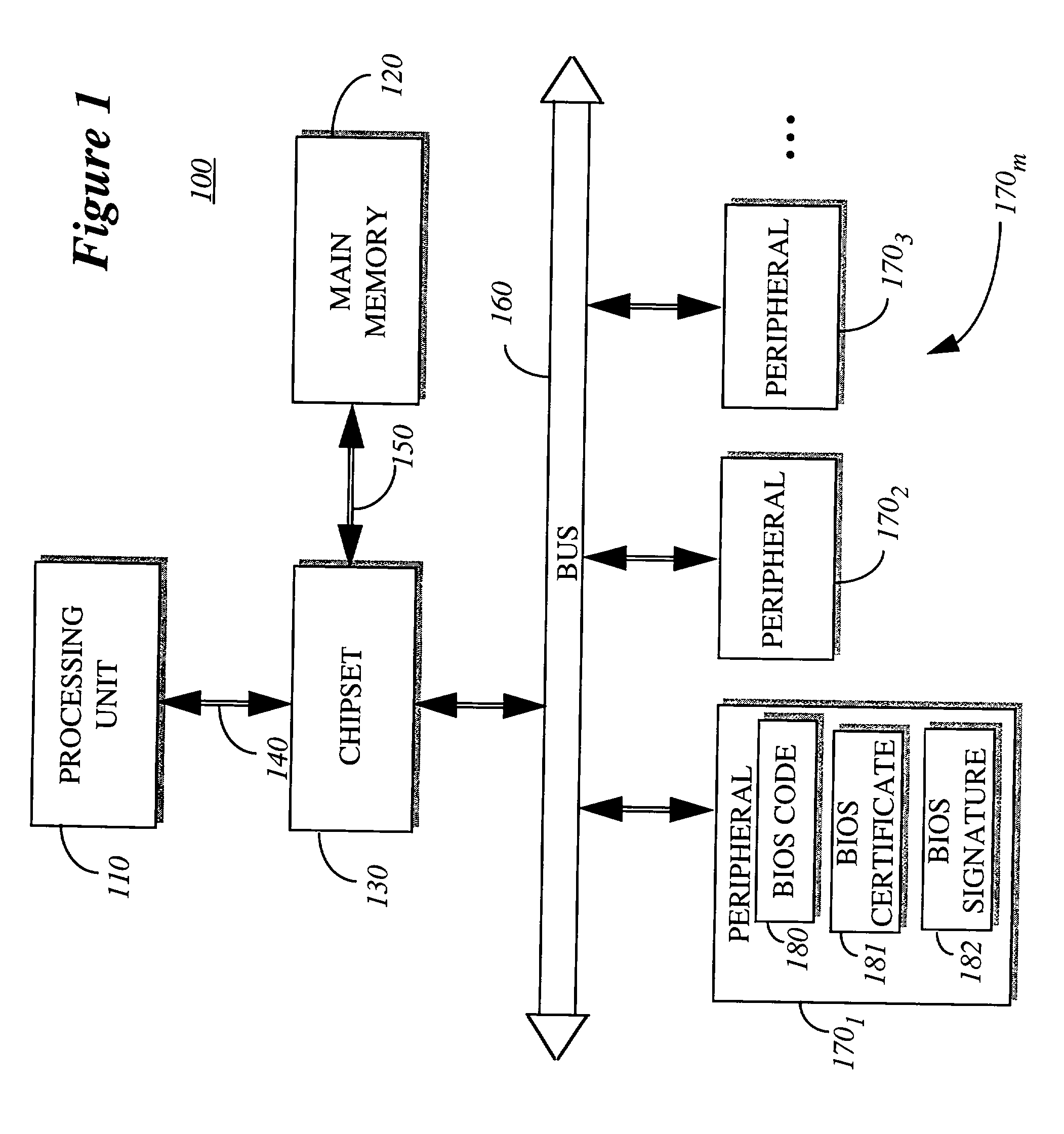
[0018] The present invention relates to an electronic system and method for authenticating software code before execution by the host processor. Herein, certain examples of hardware and methods of operation are described in an illustrative sense, and should not be construed in a restrictive sense.
[0019] To clarify various qualities of the present invention, certain terminology set forth below is used to describe hardware or cryptographic-related terms. In particular, an "electronic system" is defined as any hardware with processing and internal data storage capability. Examples of electronic systems include computers (e.g., laptops, desktops, hand-held, servers, etc.), imaging equipment (e.g., printers, facsimile machines, scanners, etc.), wireless communication equipment (e.g., cellular phones, pagers, etc.), automated teller machines and the like. "Information" is defined as one or more bits of data, address, control or any combination thereof. A "bus" is any medium used to transf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com