Patents
Literature
67 results about "Code signing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
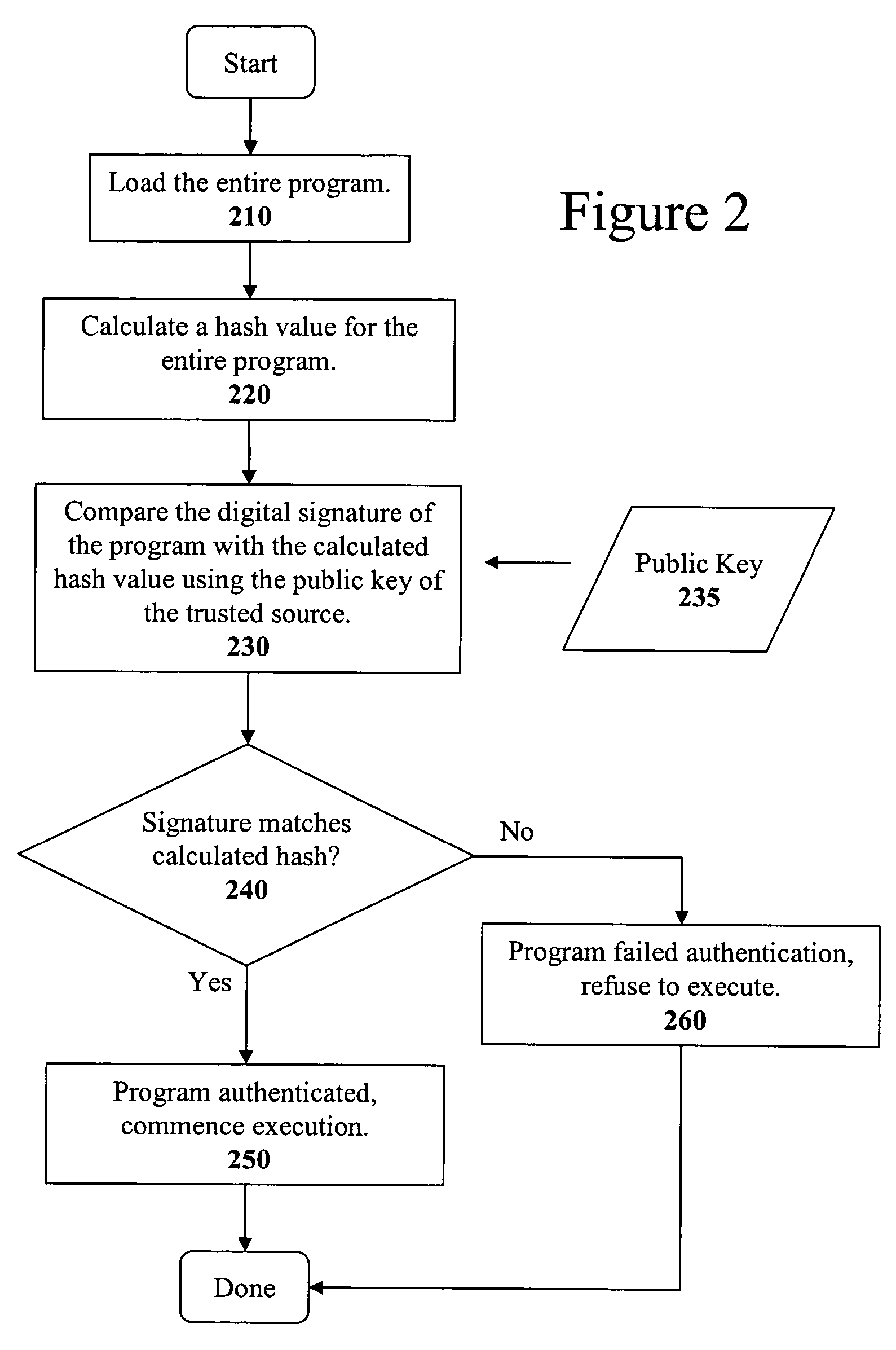
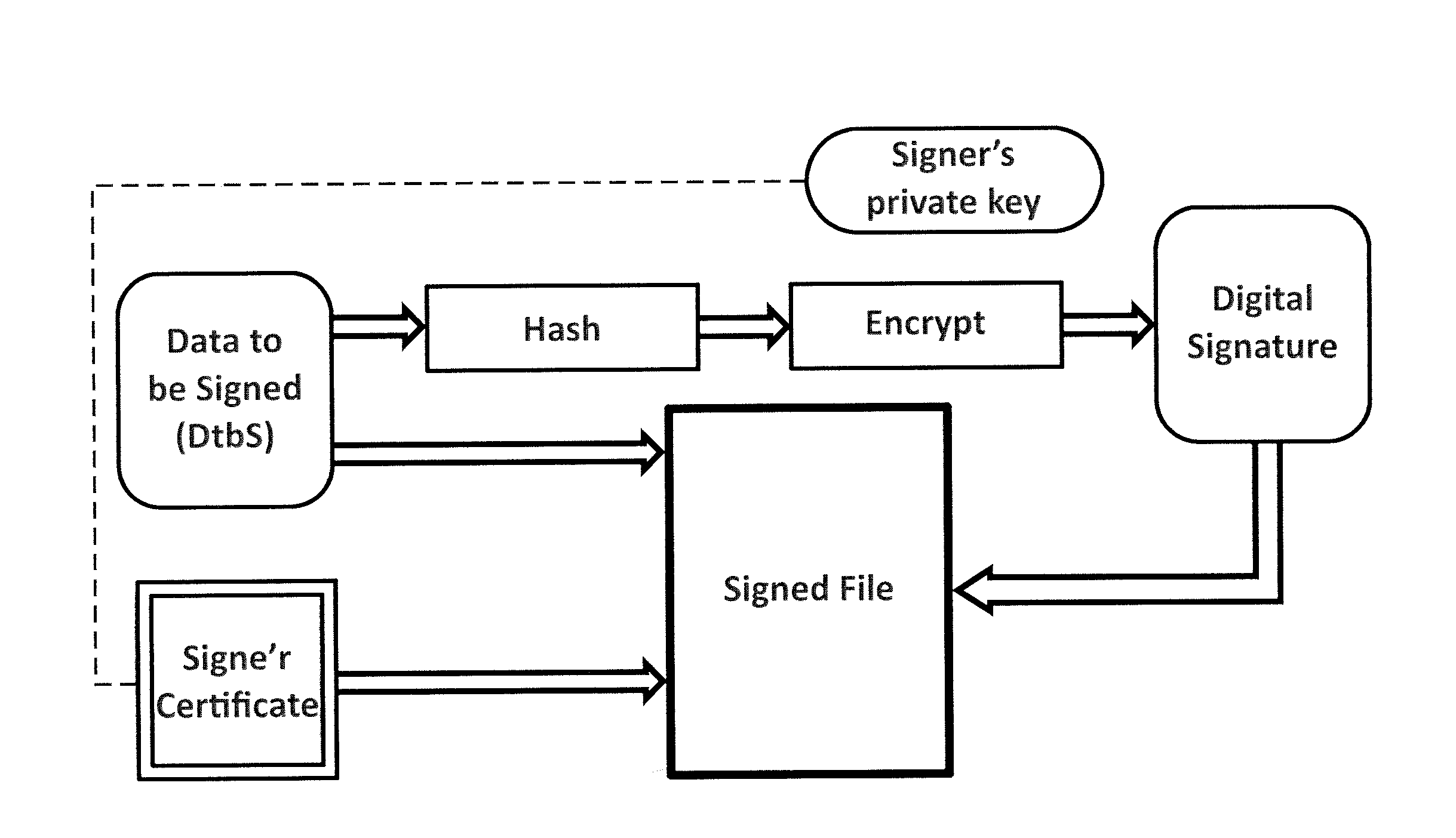
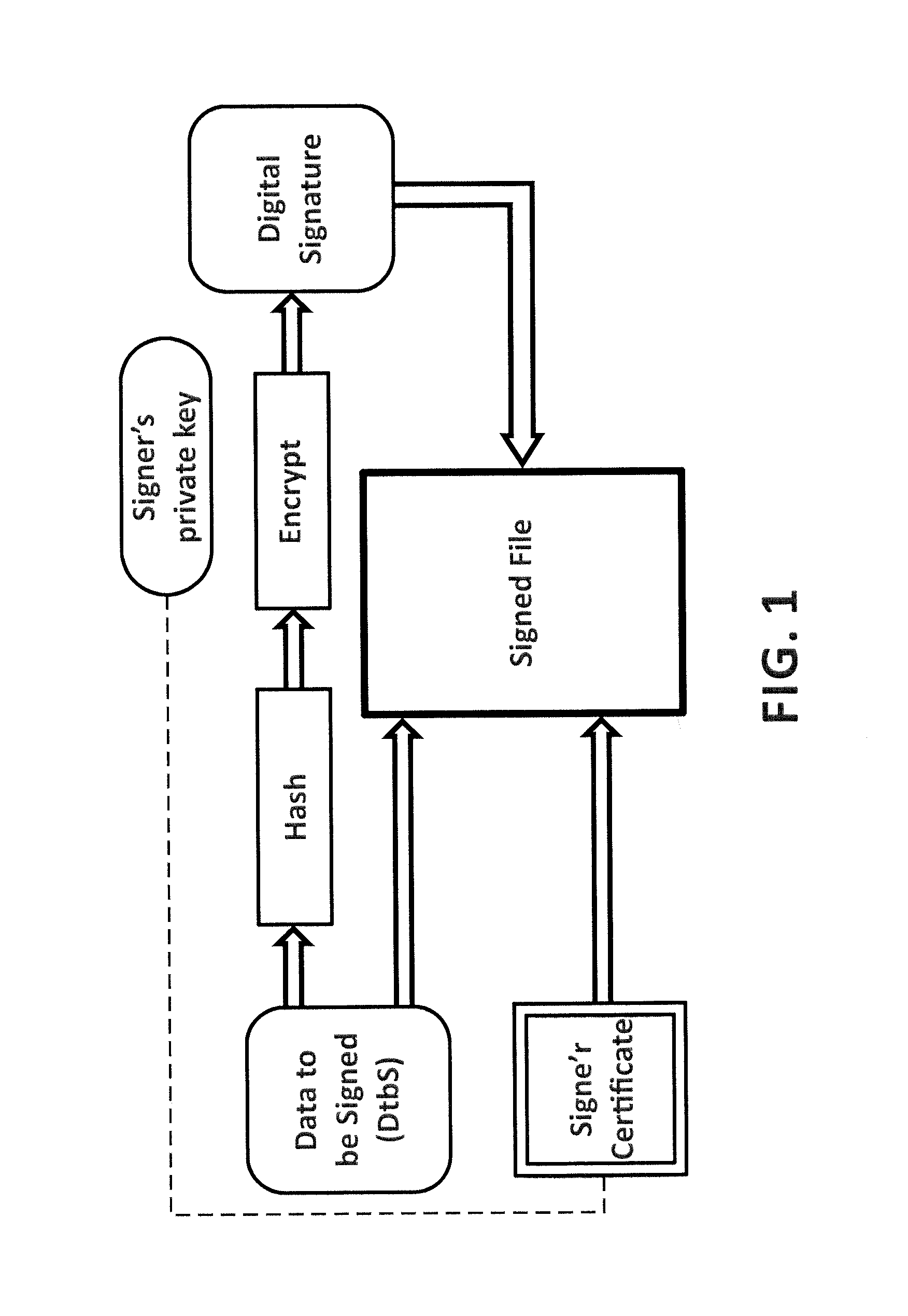
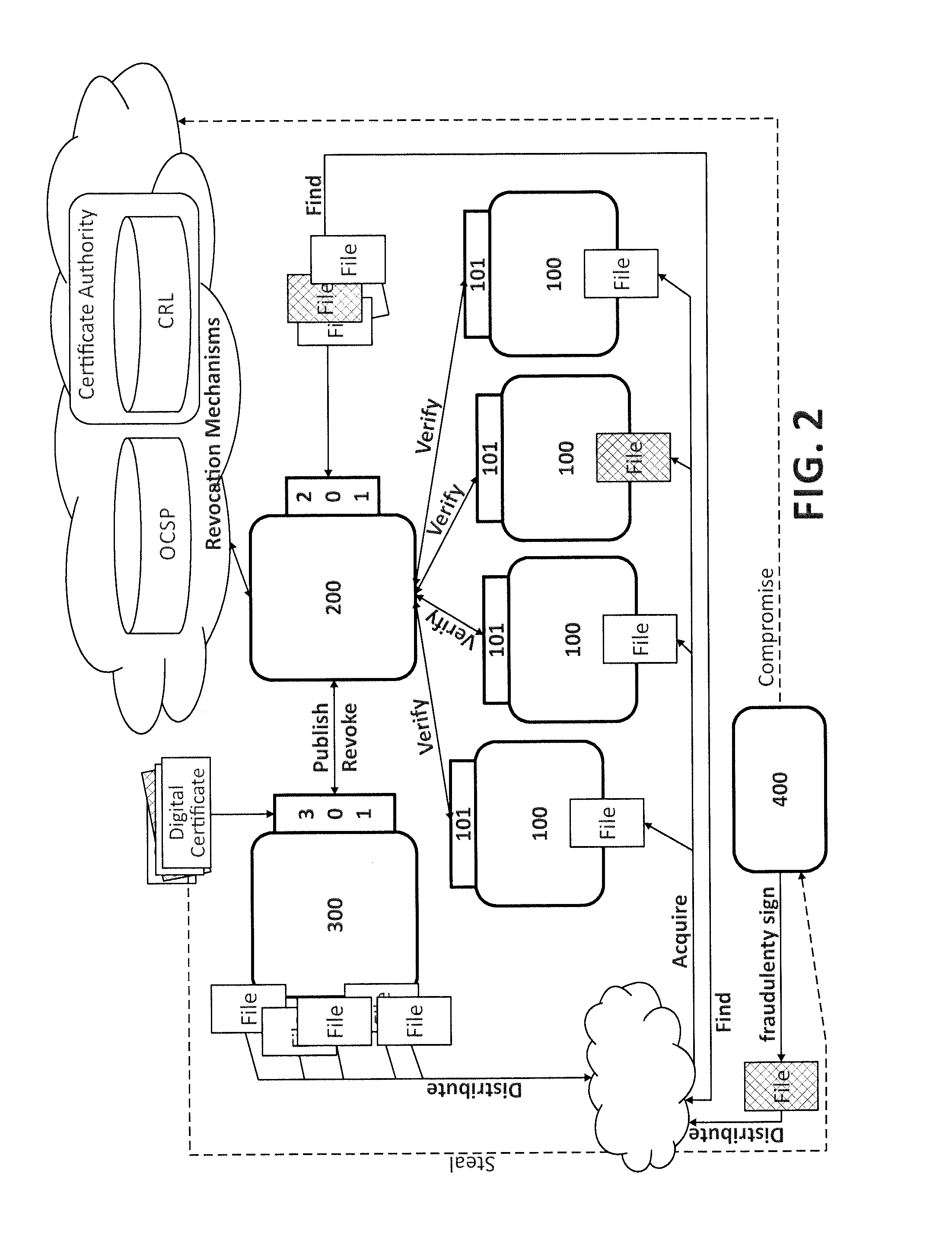
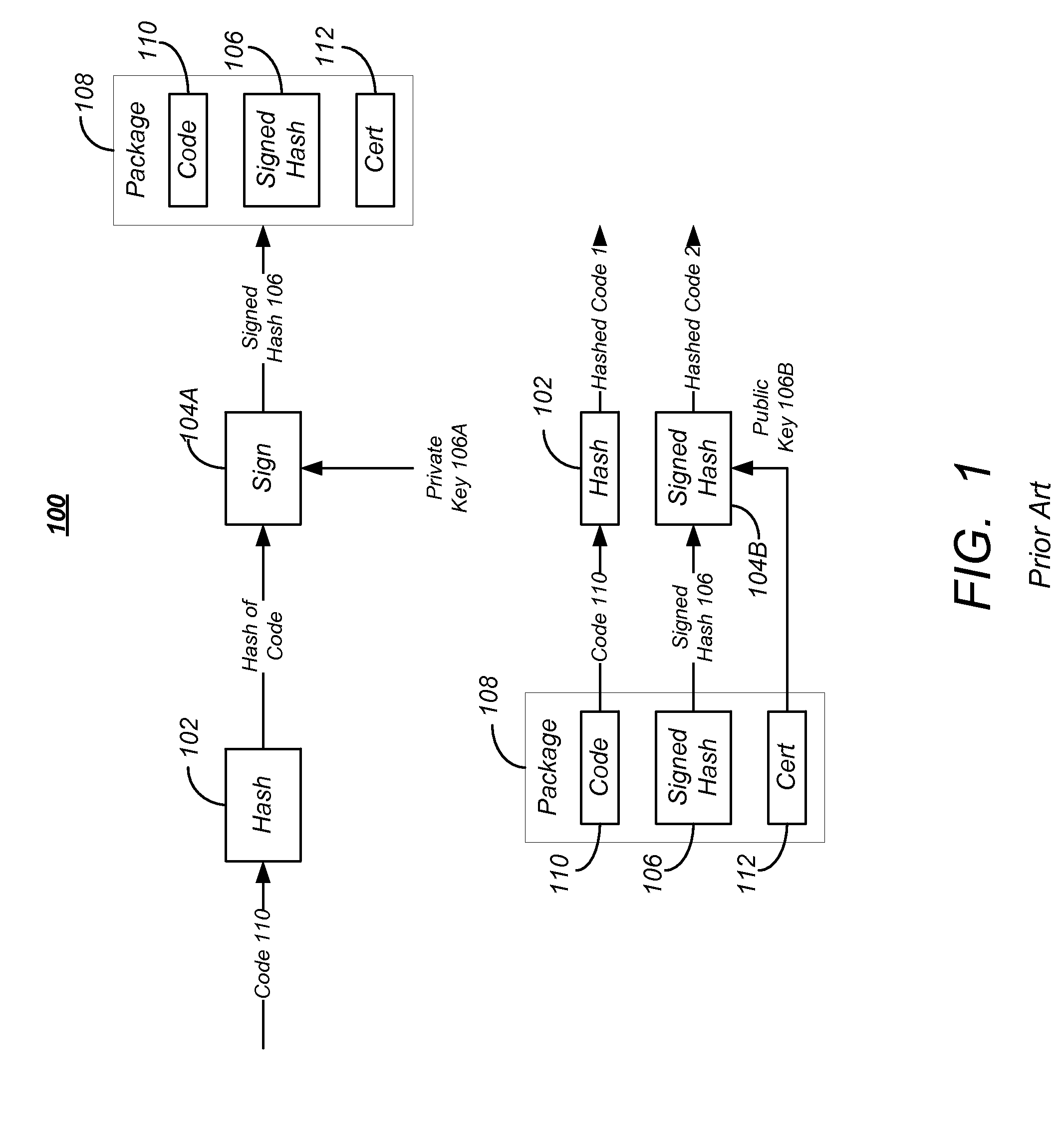
Code signing is the process of digitally signing executables and scripts to confirm the software author and guarantee that the code has not been altered or corrupted since it was signed. The process employs the use of a cryptographic hash to validate authenticity and integrity.
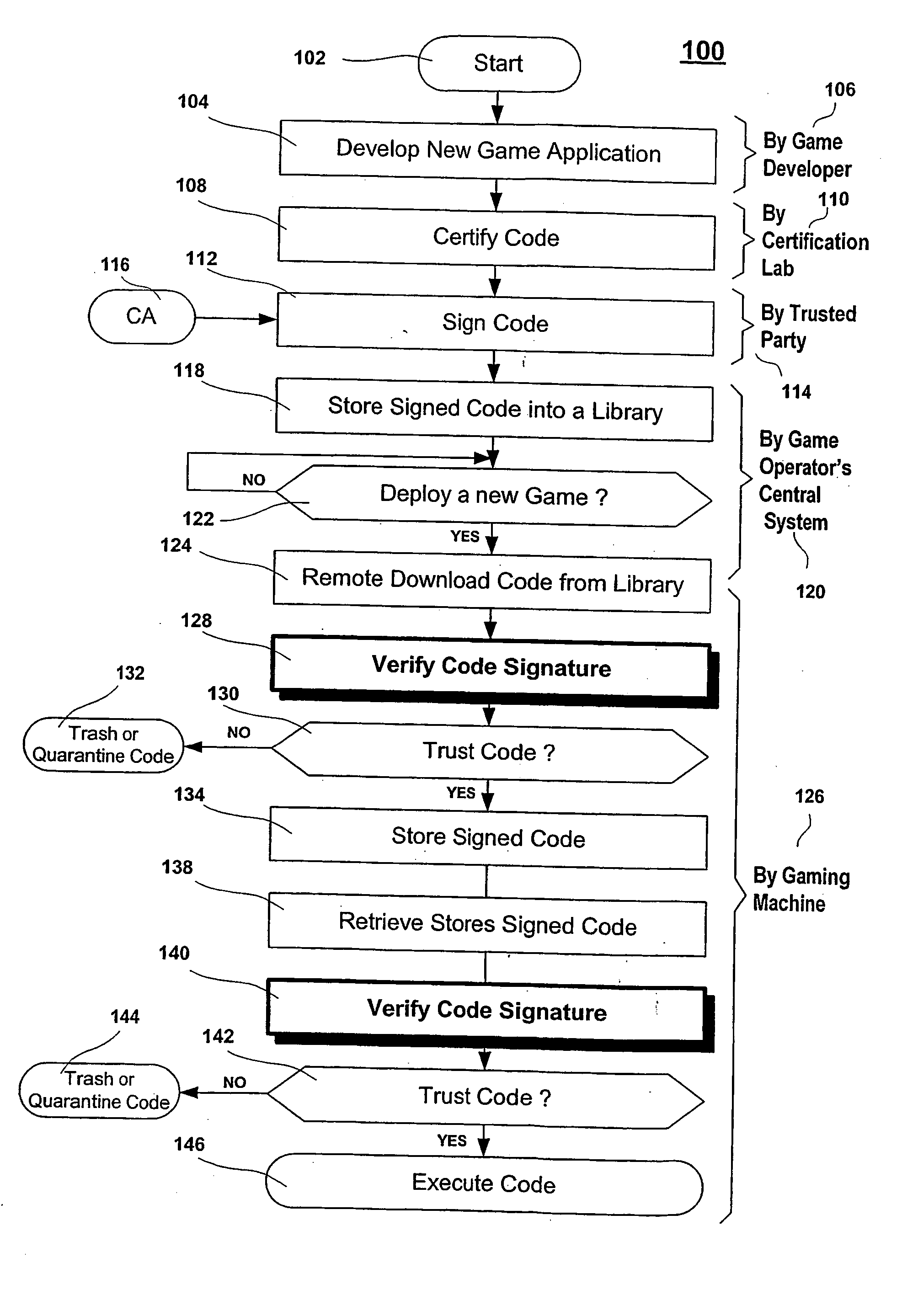
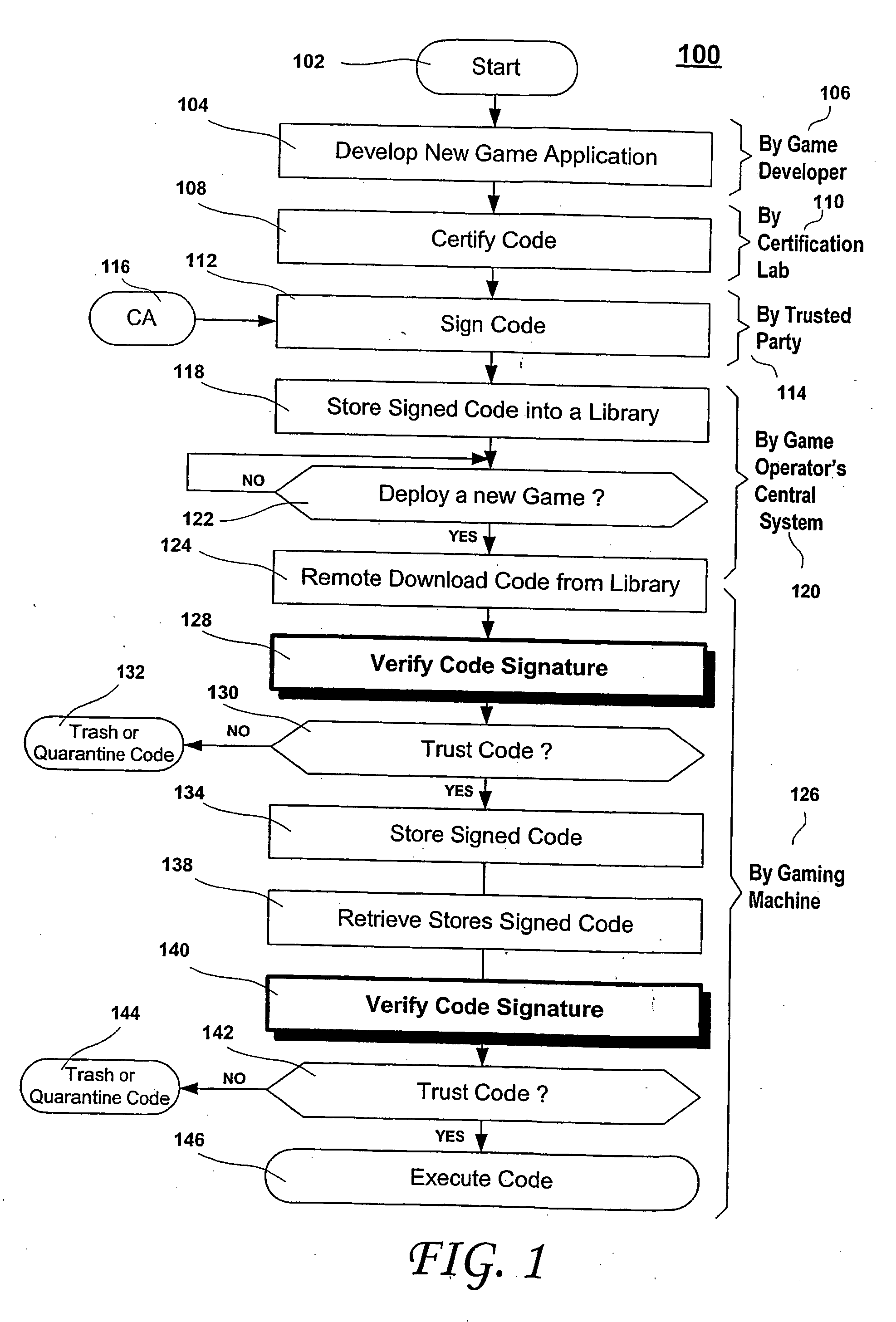
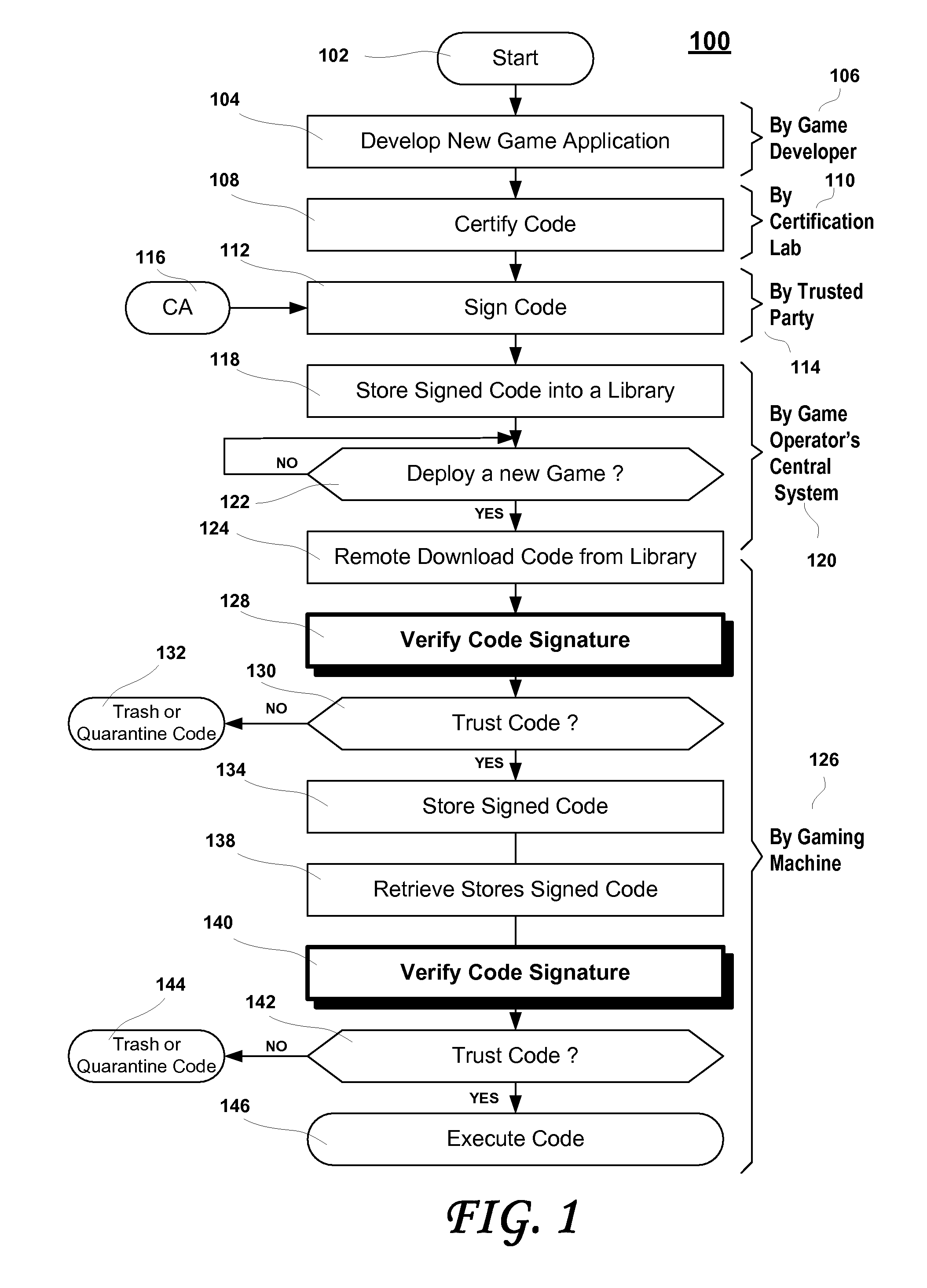
Secure game download
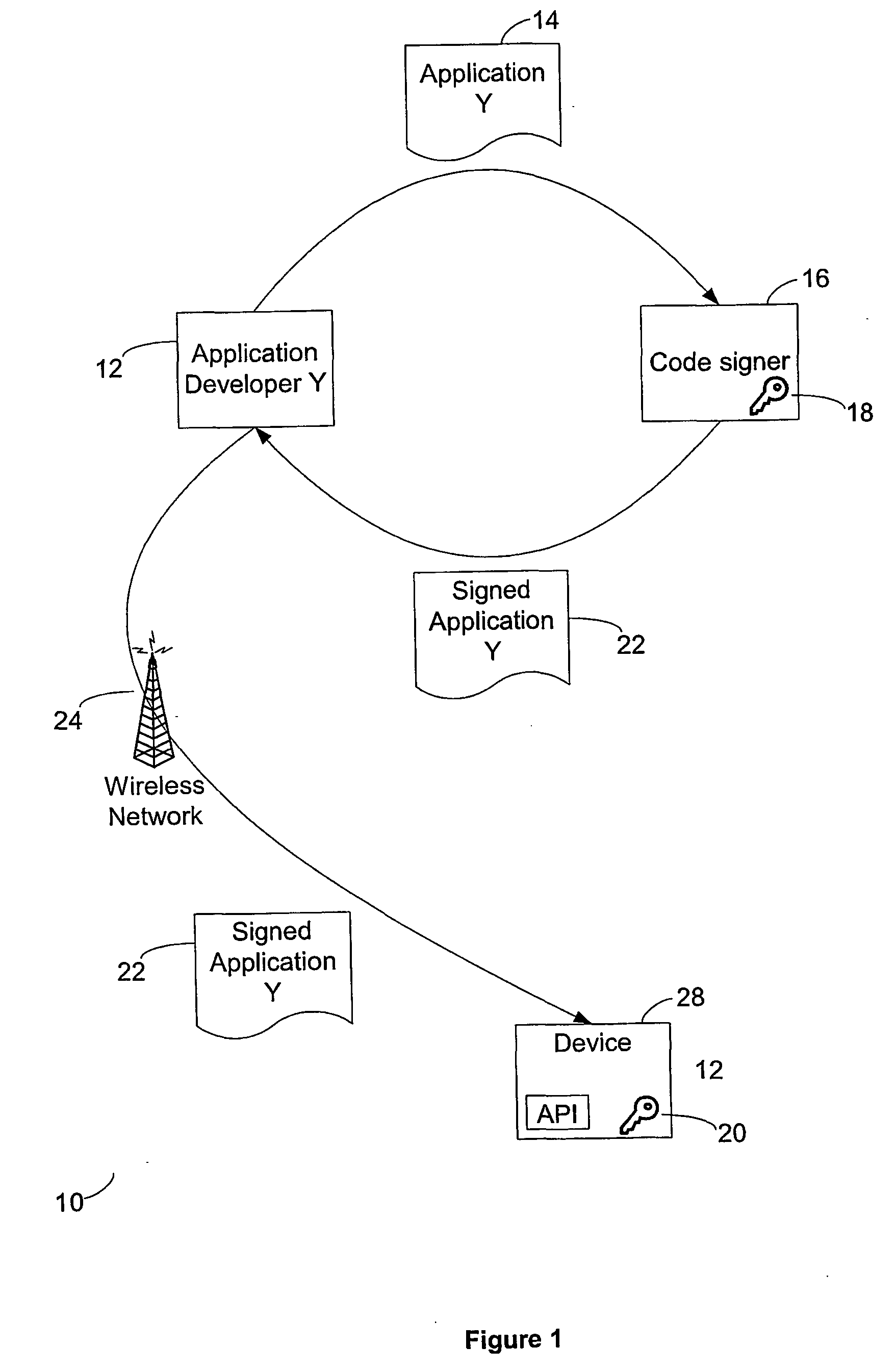
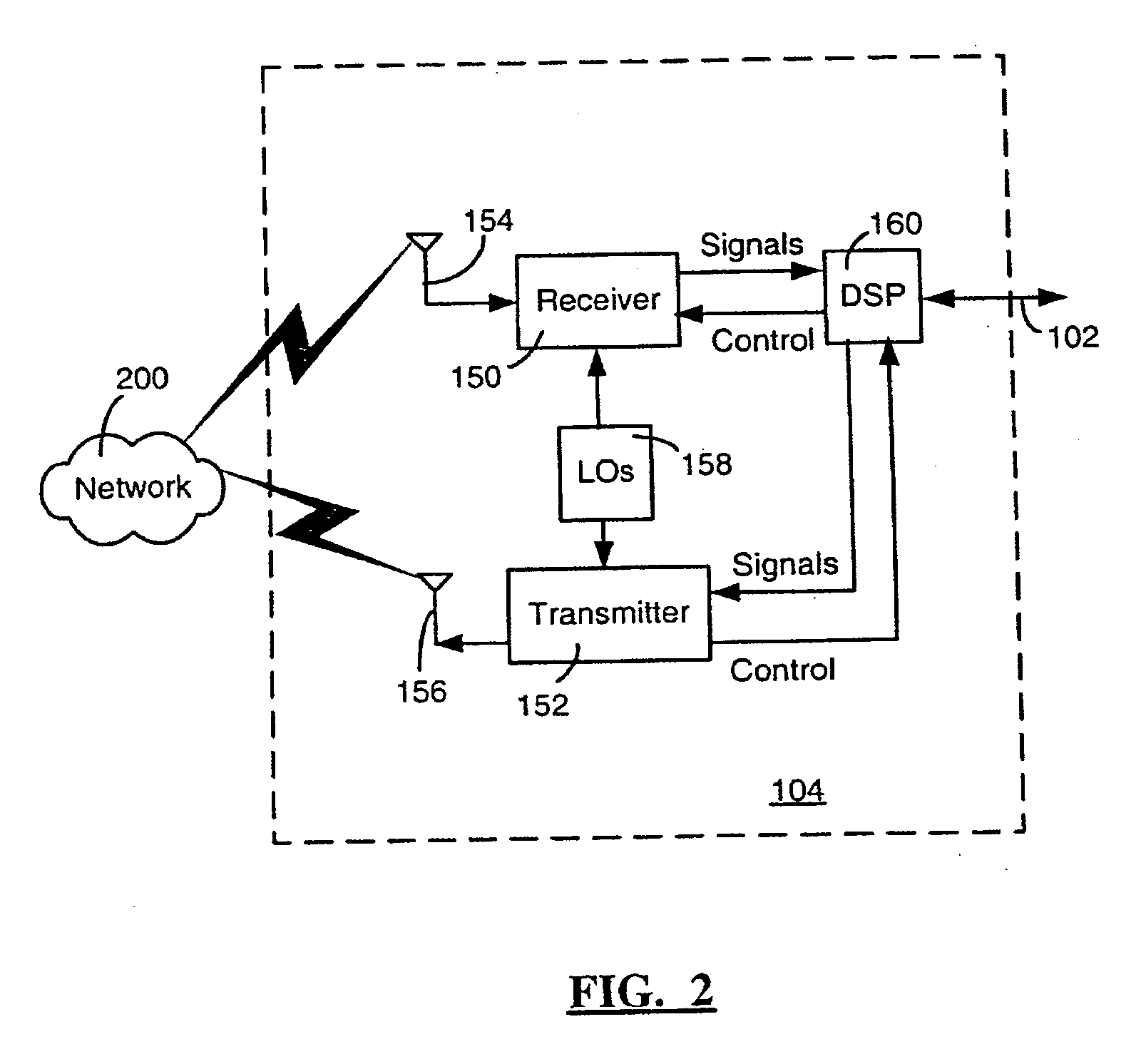
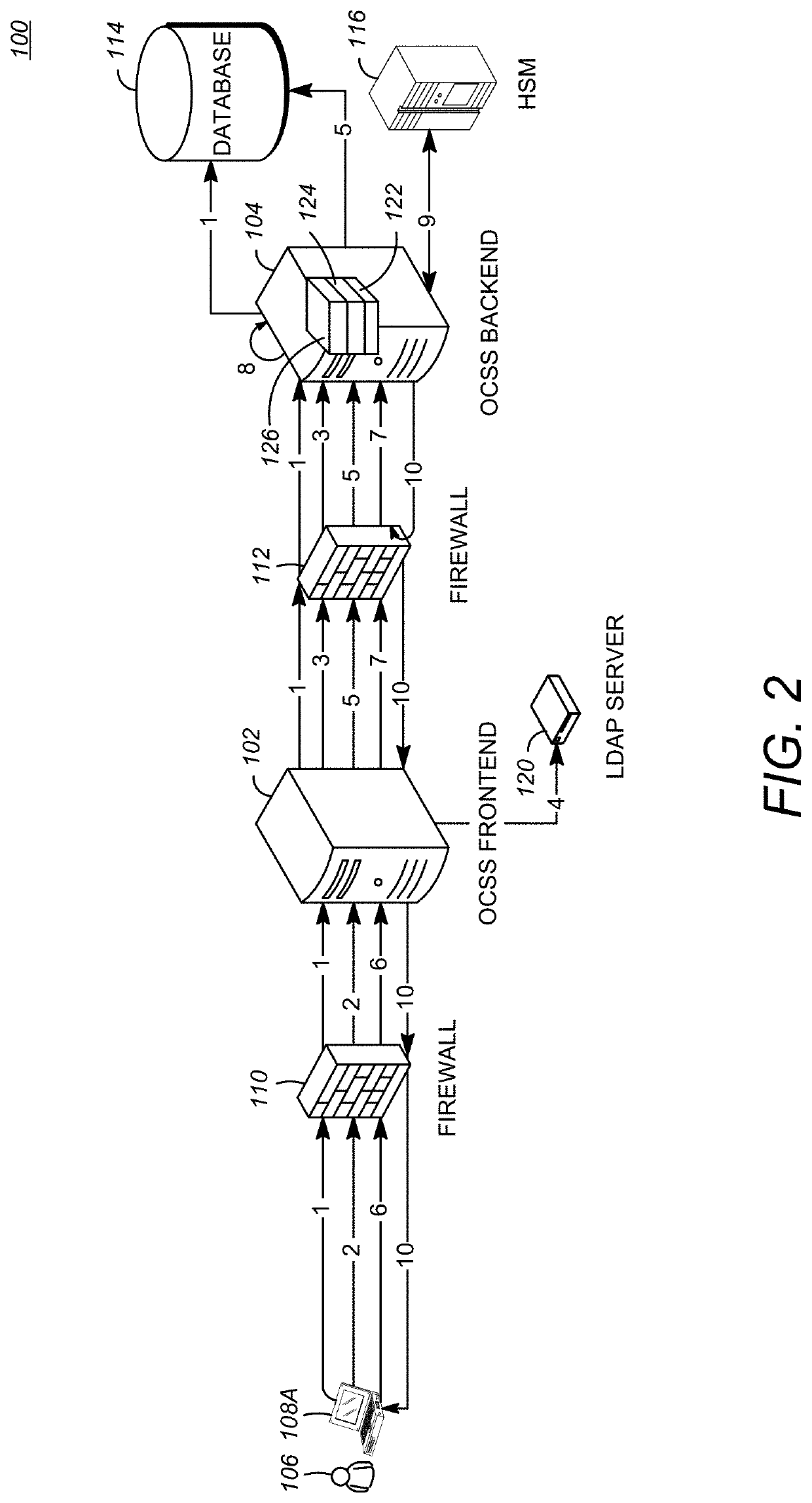
ActiveUS20060100010A1Apparatus for meter-controlled dispensingPlatform integrity maintainanceOperational systemCode signing
A method for gaming terminals, gaming kiosks and lottery terminals to ensure that the code-signing verification process of downloaded game software can be trusted. Drivers independently developed from the operating system supplier are embedded within the operating system kernel to verify that the micro-coded hardware components, the BIOS (808), the operating system components and the downloaded game software can be trusted.
Owner:IGT
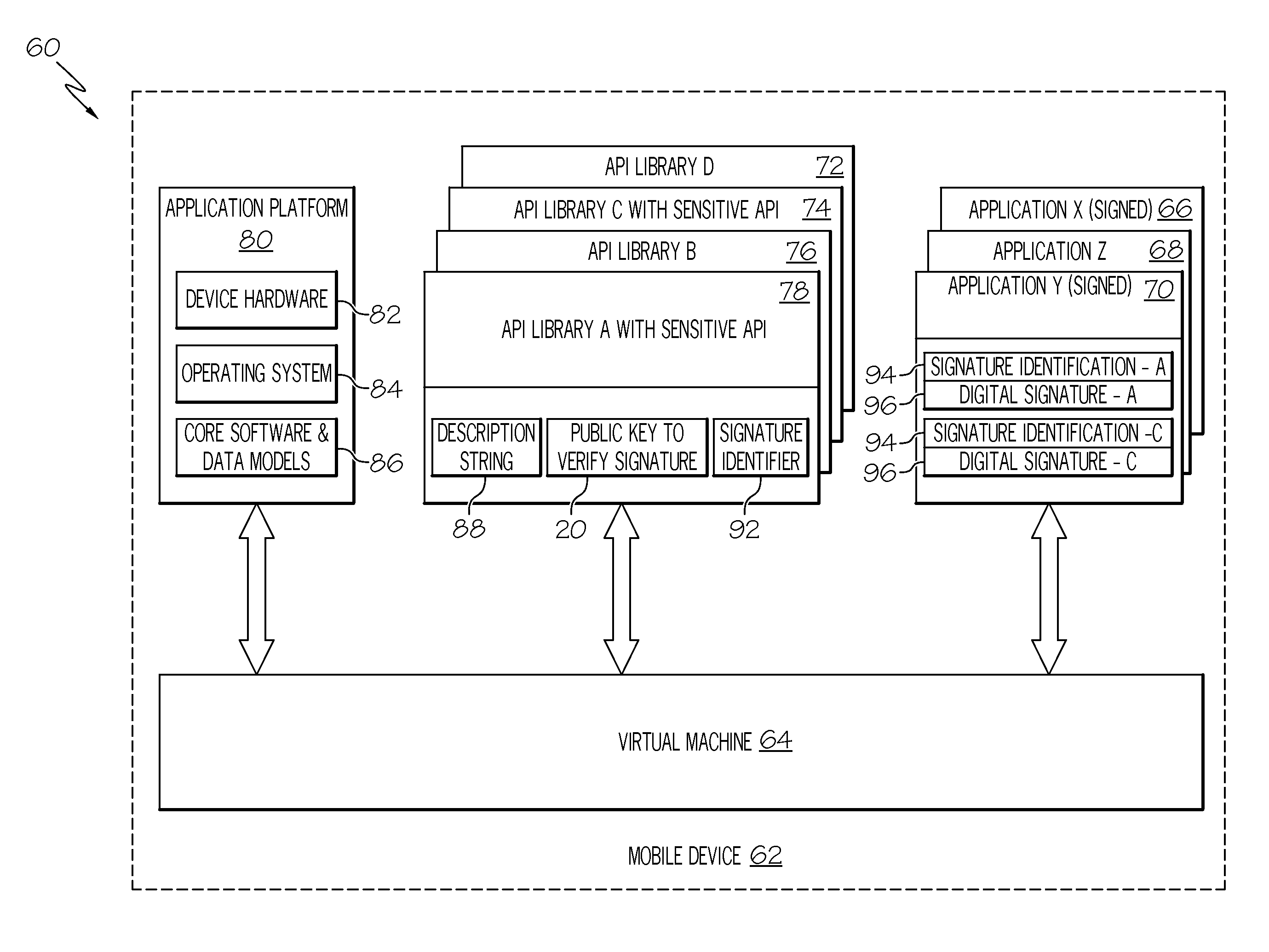
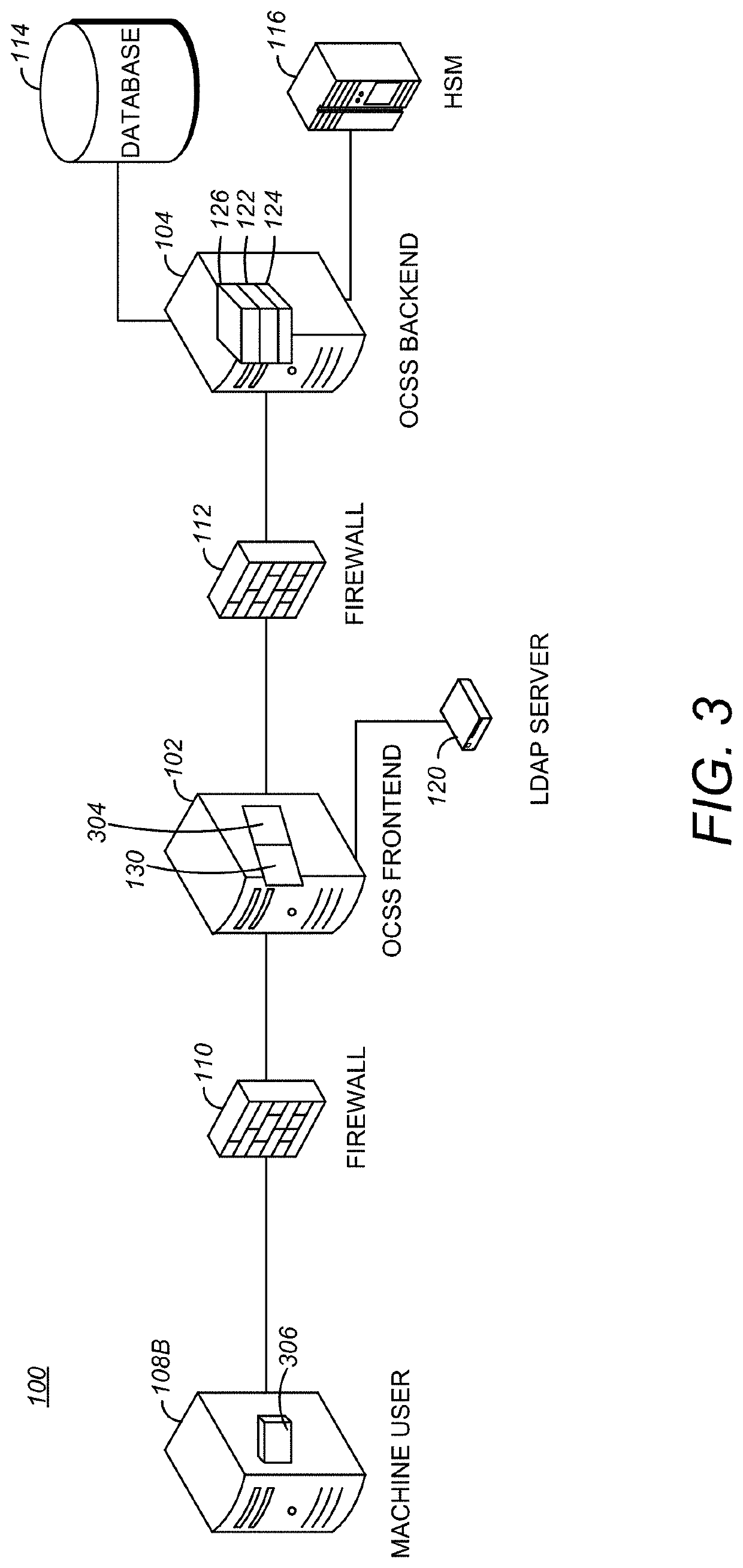
Code signing system and method
ActiveUS20040025022A1Digital data processing detailsUser identity/authority verificationApplication programming interfaceCode signing
A code signing system and method is provided. The code signing system operates in conjunction with a signed software application having a digital signature and includes an application platform, an application programming interface (API), and a virtual machine. The API is configured to link the software application with the application platform. The virtual machine verifies the authenticity of the digital signature in order to control access to the API by the software application.
Owner:BLACKBERRY LTD
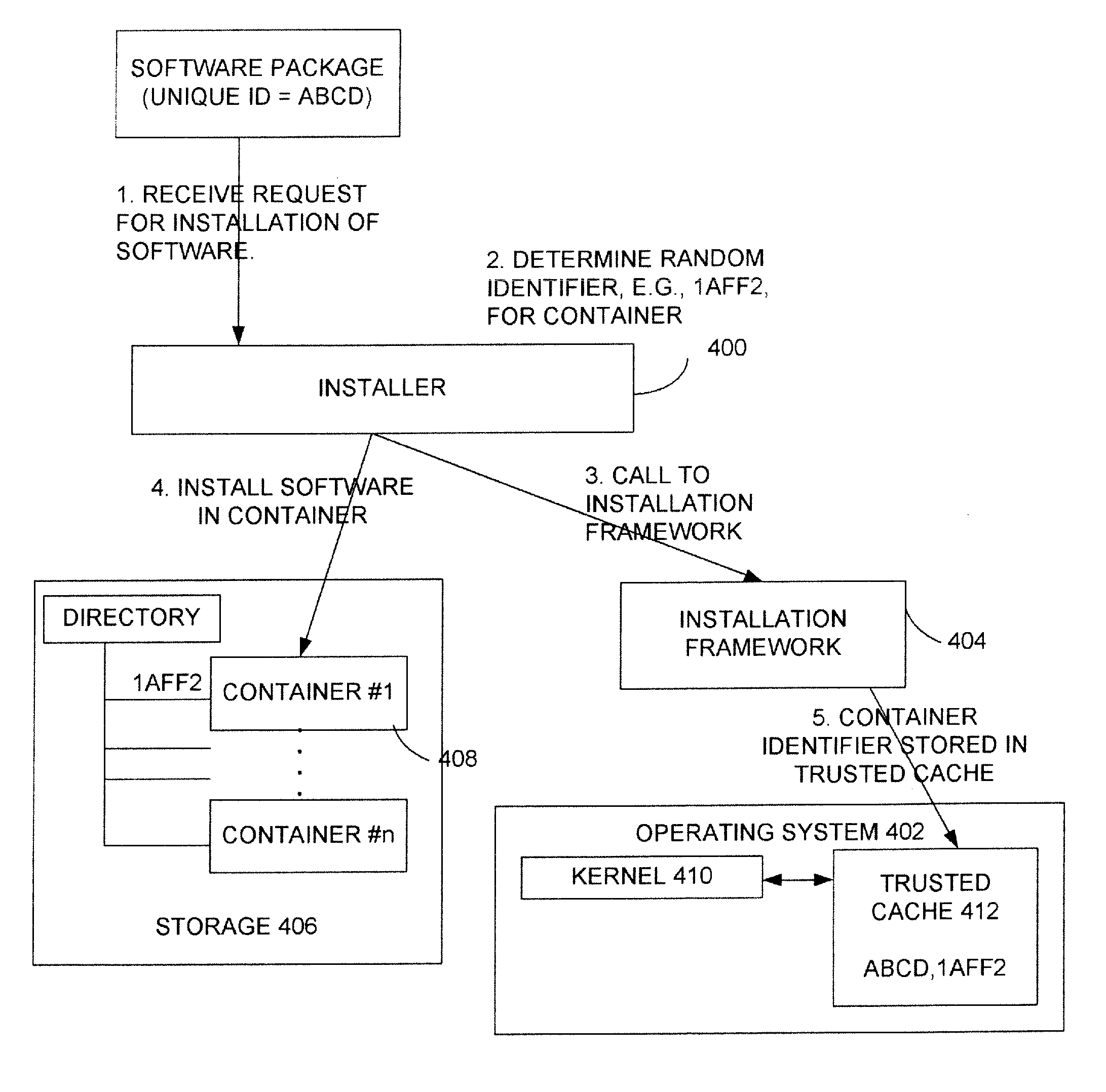
Managing securely installed applications
ActiveUS20100313196A1Memory loss protectionError detection/correctionOperational systemRandom allocation
Embodiments of the present disclosure provide methods and systems for managing securely installed applications. After installation, an installation framework performs a bind process to correlate the randomly assigned identifier with the unique identifier of the application. The installation framework also manages the execution of the application. When an application is launched, the application framework performs a search for that application's randomly assigned identifier and locates the application's container. The application is then allowed to execute within its container. During execution, the software application may also be restricted in various ways by the installation framework to its dynamic containers. The installer may also work with a trusted operating system component, such as the kernel, to help enforce the container restrictions. In addition, if desired, the use of random identifiers for containers may be used in conjunction with other security mechanisms, such as the use of code signing.
Owner:APPLE INC
Personal information encryption method in logistics system based on two-dimensional codes
InactiveCN103177220AGuaranteed confidentialityEnsure safetyPublic key for secure communicationDigital data protectionPlaintextLogistics management
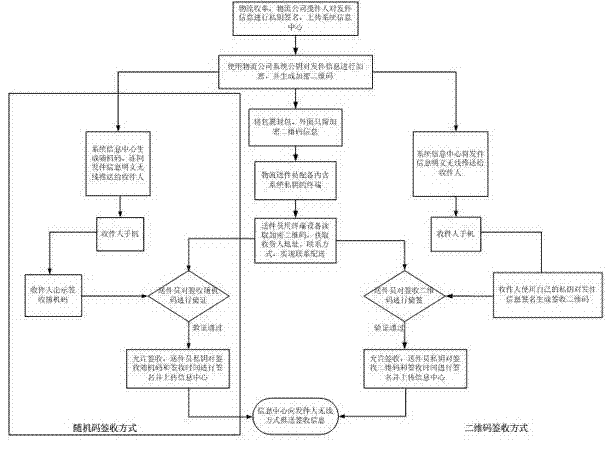
The invention discloses a personal information encryption method in a logistics system based on two-dimensional codes. The personal information encryption method in the logistics system based on two-dimensional codes is characterized by comprising the following steps that: step 1. object sending information is encrypted: the encryption is finished by senders, or collectors in the field, or objects are sent back to a logistics company and are encrypted; step 2. object sending information is encrypted by utilizing a system public key of a logistics company, and encryption two-dimensional codes are generated and are printed; packages are packed, encryption two-dimensional codes are only reserved externally, and no plaintext information is reserved; and step 3. signing is carried out after receiving. According to the invention, two signing modes are selectable, one is a two-dimensional code signing mode, and the other one is a random code signing mode; and if the two-dimensional signing mode is adopted, a receiver needs to have an ID number and public and private key pairs in the system. The personal information encryption method in the logistics system based on two-dimensional codes provided by the invention has the advantages that the encryption and safety of the user private information are ensured; packages are protected from being falsely received by other people, and denying of receiving is avoided after signing; off-line check can be realized, network support is not required, and the application is much flexible; and identity theft is also avoided.
Owner:CHENGDU EHENGXIN TECH
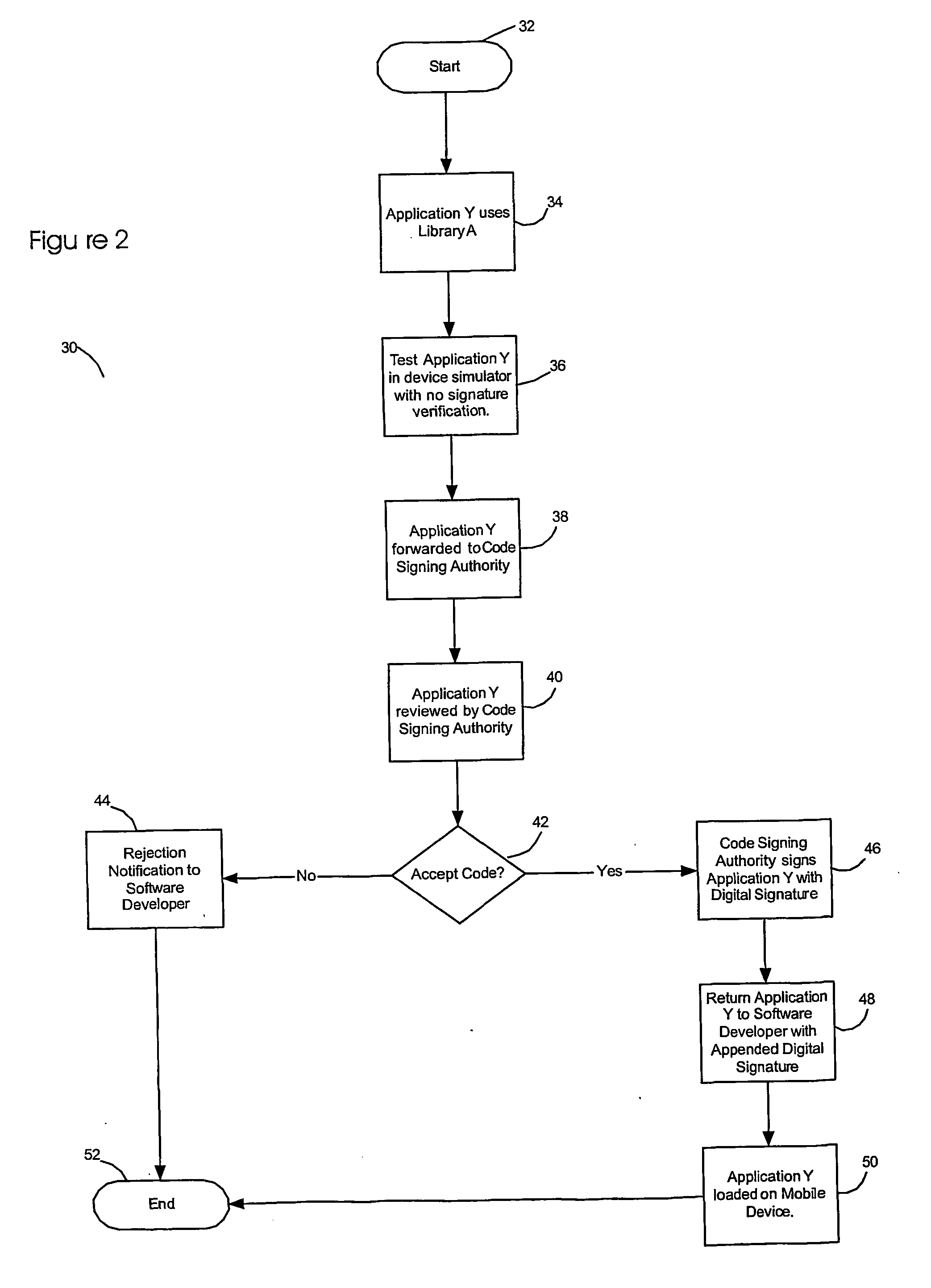
Method and apparatus for incremental code signing
ActiveUS7103779B2Memory loss protectionUser identity/authority verificationArray data structureCode signing
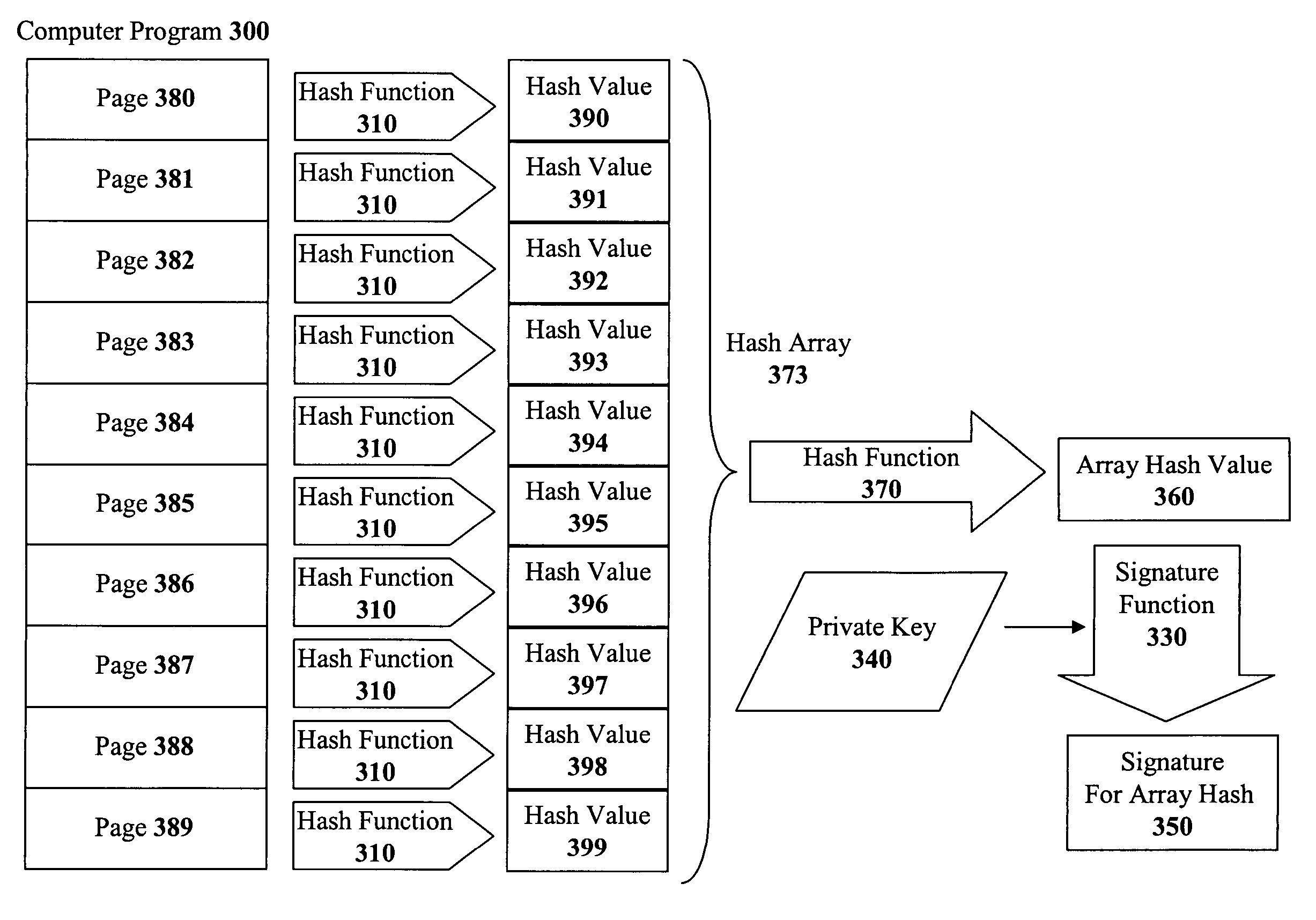
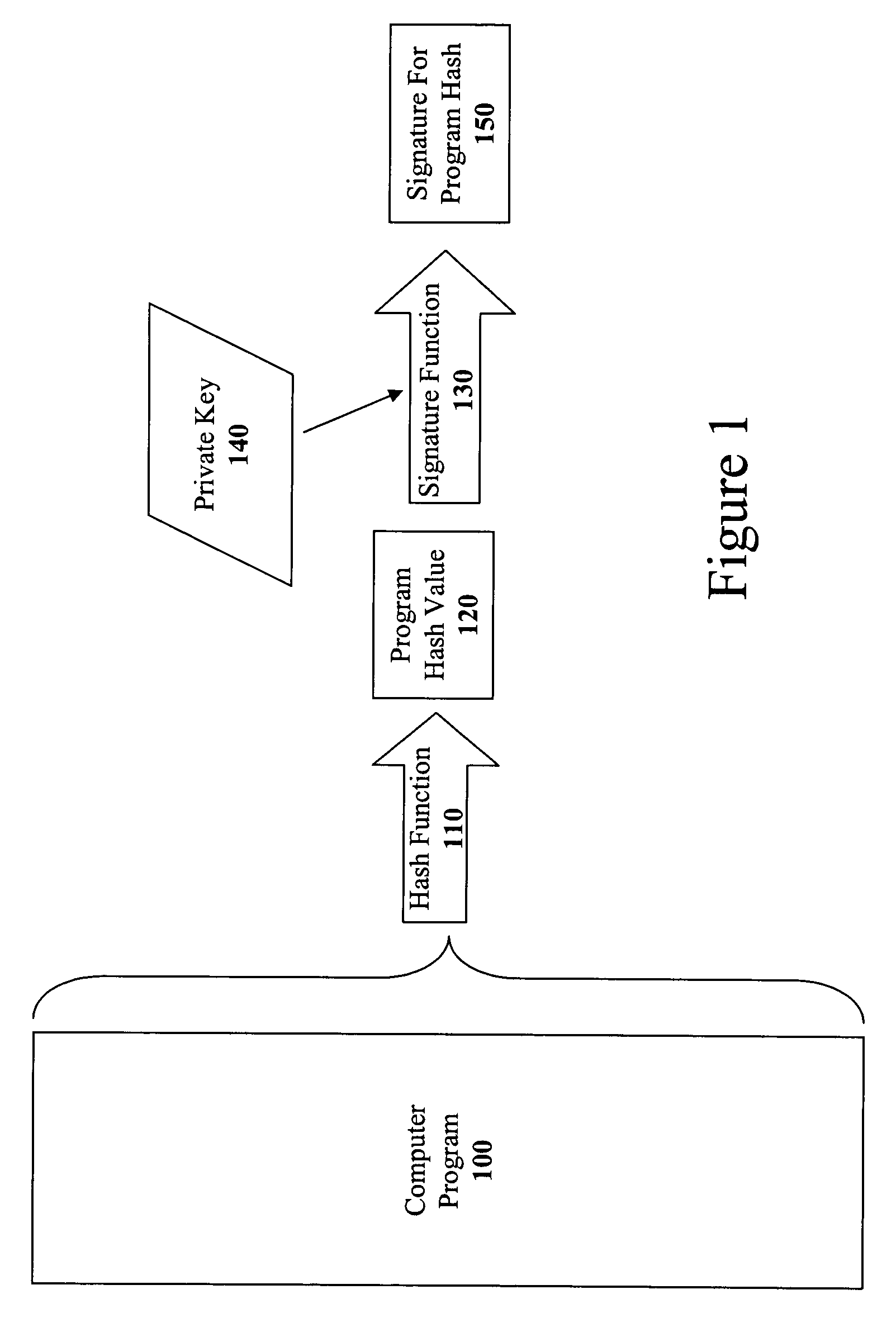
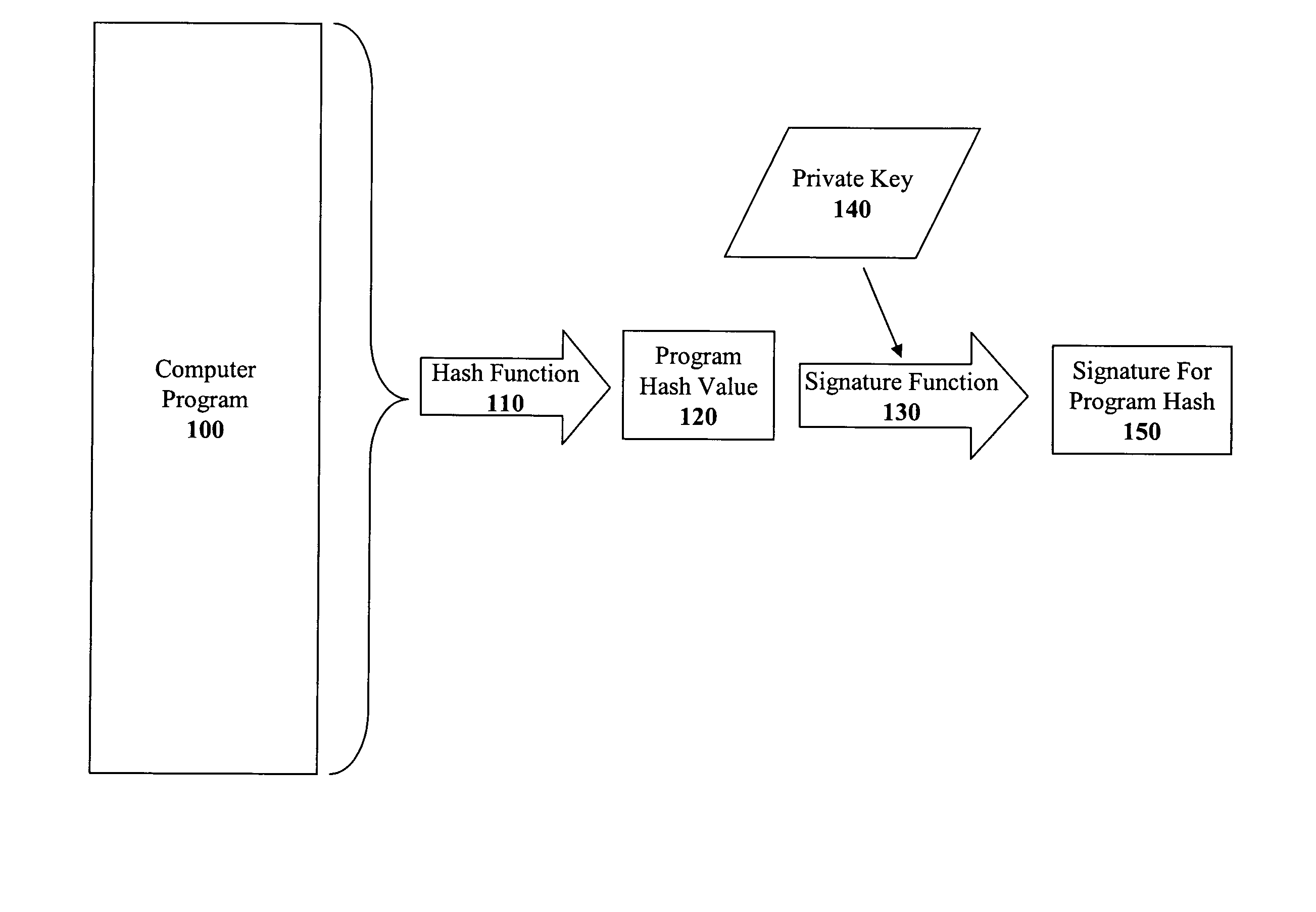
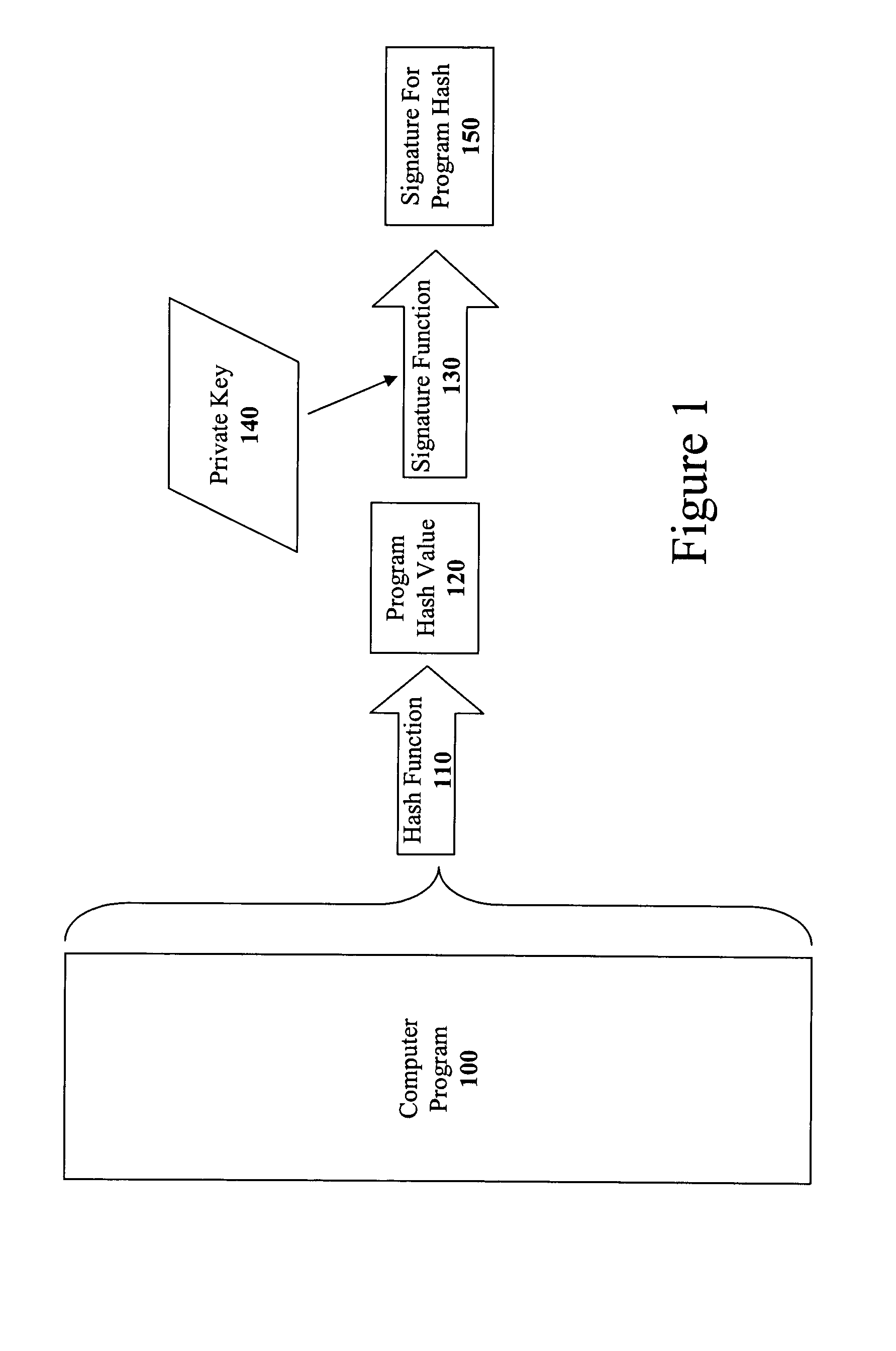
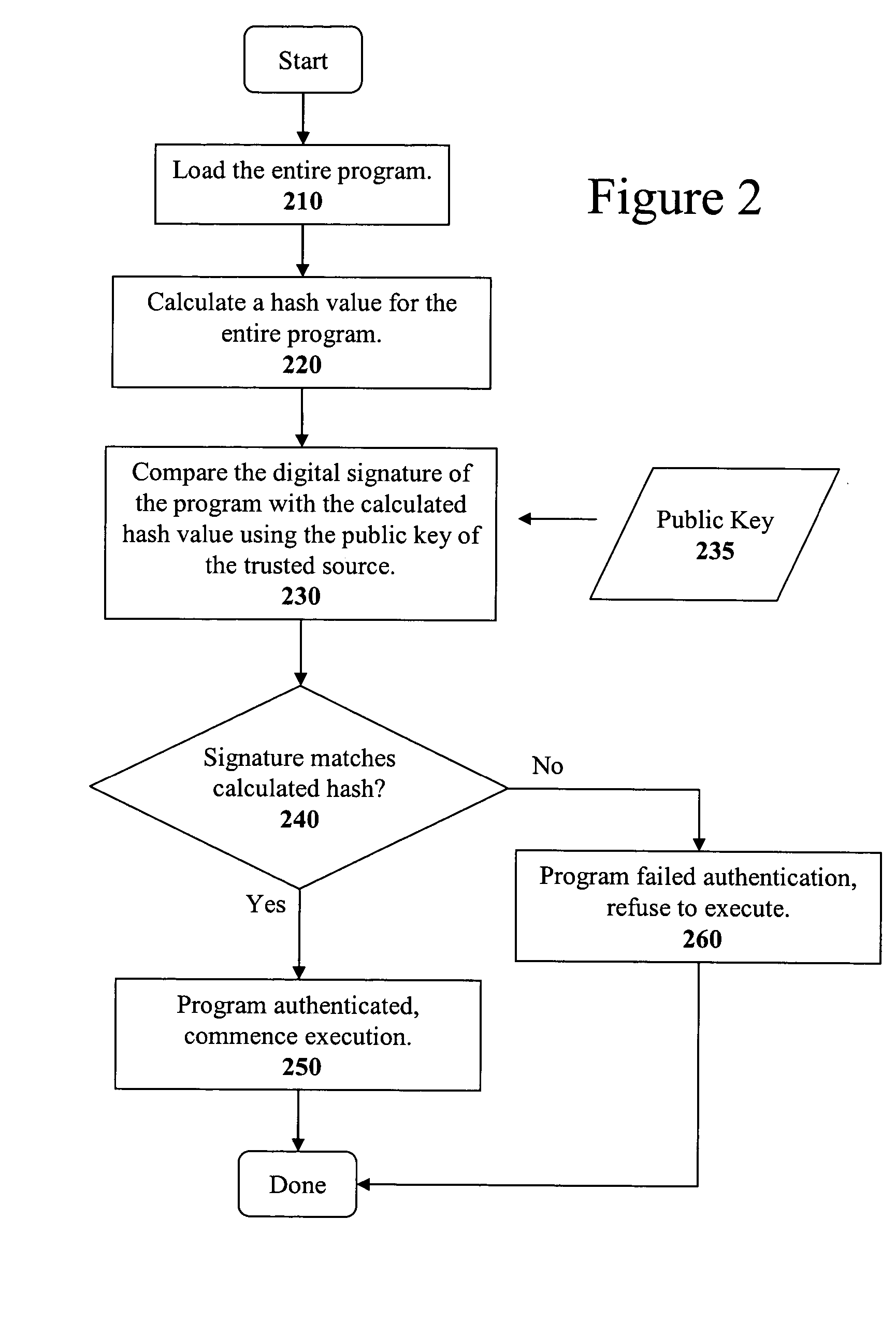
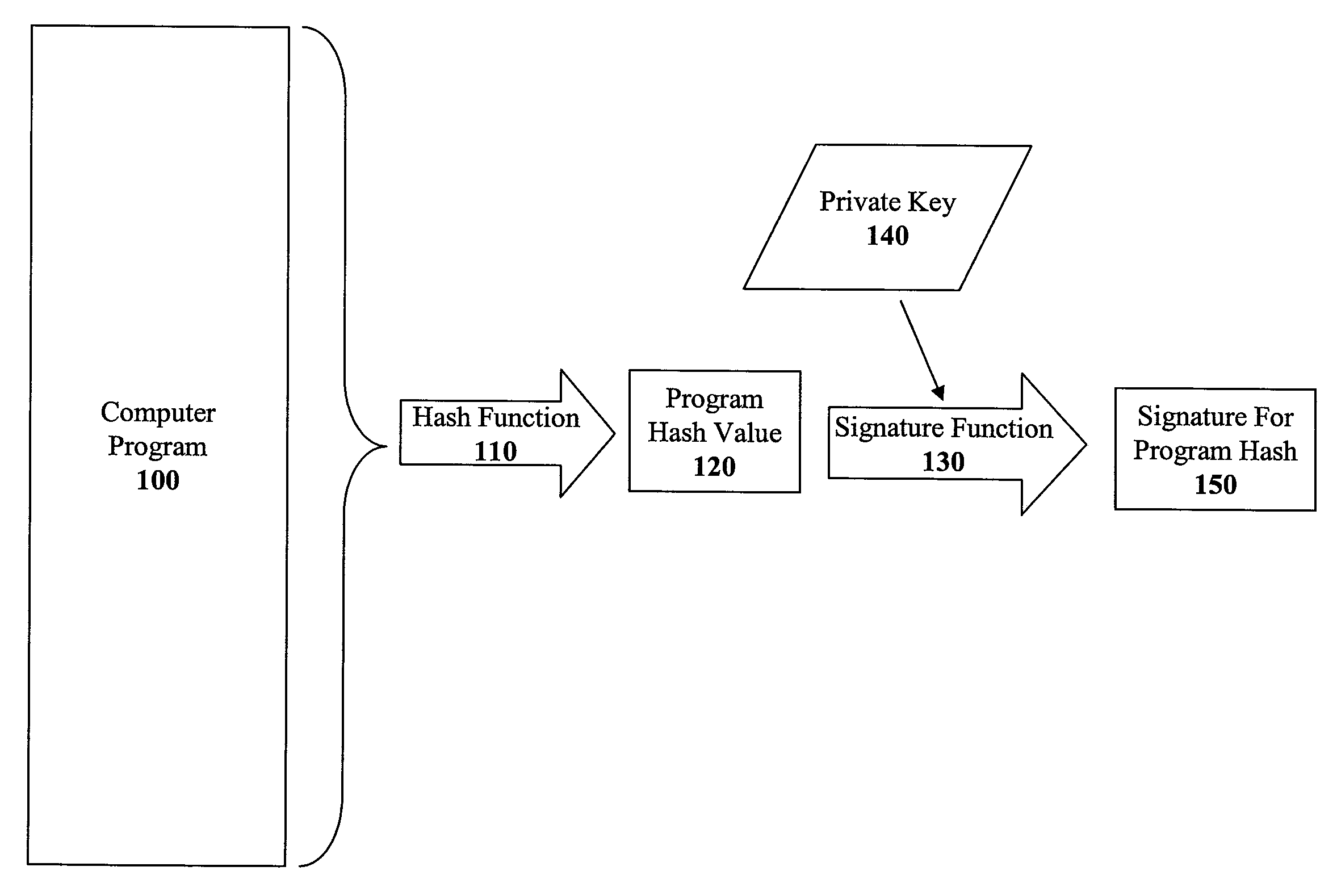
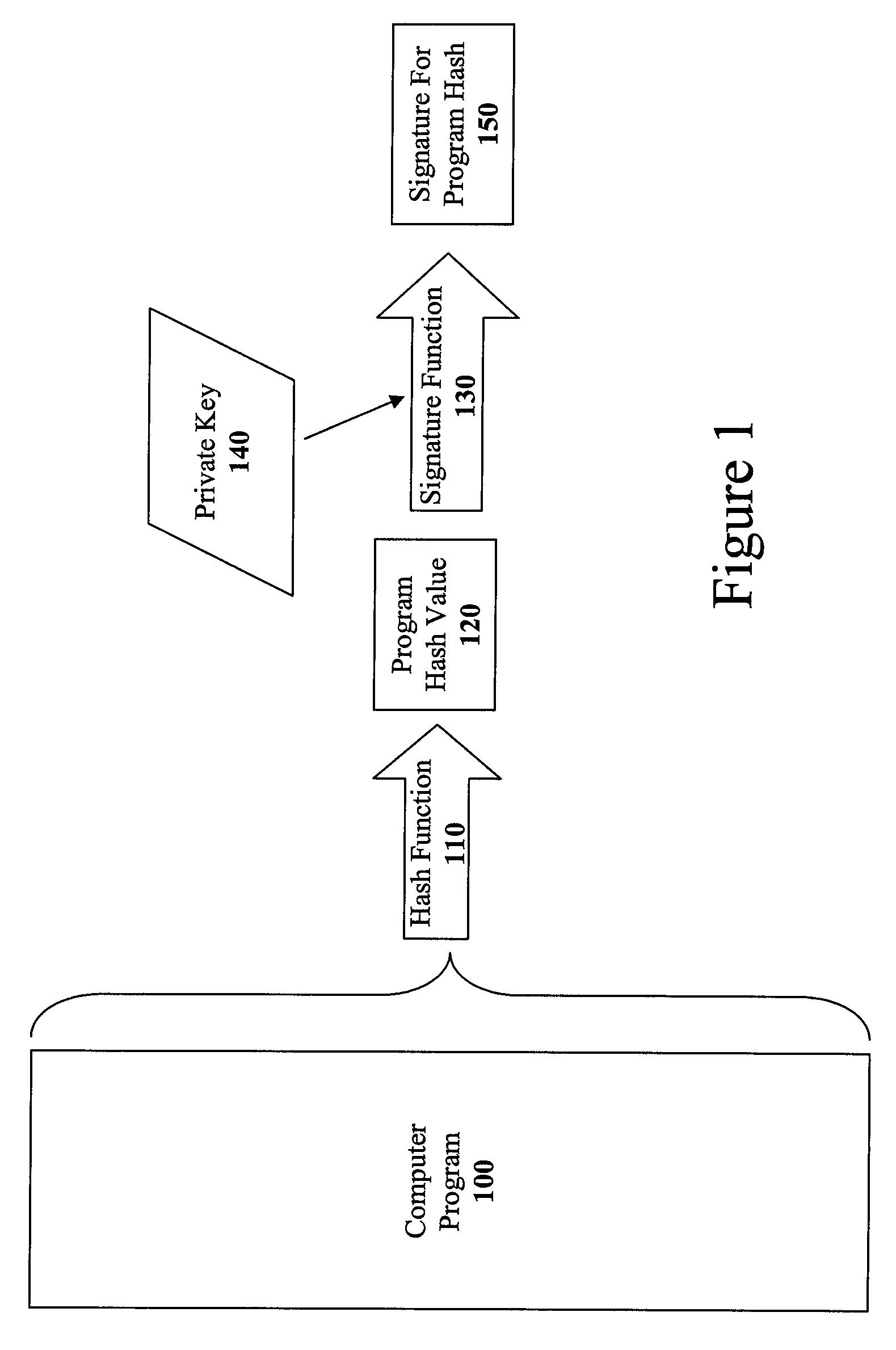
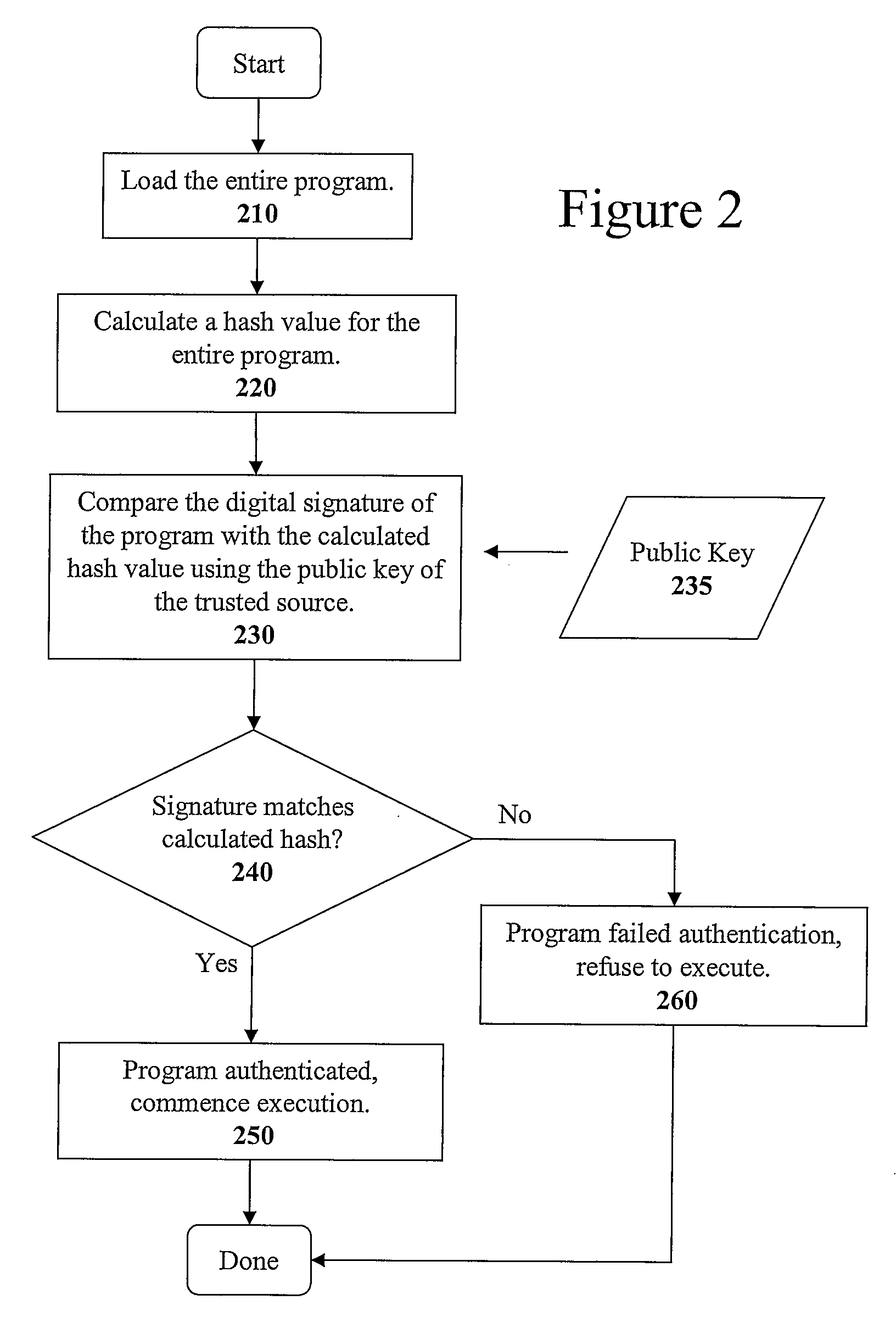
The present invention discloses a method for quickly and easily authenticating large computer program. The system operates by first sealing the computer program with digital signature in an incremental manner. Specifically, the computer program is divided into a set of pages and a hash value is calculated for each page. The set of hash values is formed into a hash value array and then the hash value array is then sealed with a digital signature. The computer program is then distributed along with the hash value array and the digital signature. To authenticate the computer program, a recipient first verifies the authenticity of the hash value array with the digital signature and a public key. Once the hash value array has been authenticated, the recipient can then verify the authenticity of each page of the computer program by calculating a hash of a page to be loaded and then comparing with an associated hash value in the authenticated hash value array. If the hash values do not match, then execution may be halted.
Owner:APPLE INC
Rollback-Resistant Code-Signing
InactiveUS20080195868A1Prevent rollbackSign be incorrectUser identity/authority verificationDigital data protectionCode signingSoftware upgrade
A code signature methodology that allows recovery from incorrectly signed software while preventing rollbacks is described herein. When software is signed, the code signature is based not only on the current version of executable code and information corresponding to the current version of executable code, but also includes a history value based on a previous version of the executable code. Each history value is unknown until each version of the software is validly signed. Thus, the code signature technique allows a signing entity to continue using the same signing key even after recovering from an attack, can be used with and without pre-configured trust roots, and allows a device to upgrade from one version of software to another version of the software while skipping intermediate versions.
Owner:NOKIA CORP
Method and apparatus for incremental code signing
ActiveUS20050066169A1Quickly and easily authenticatingMemory loss protectionUser identity/authority verificationArray data structureCode signing
The present invention discloses a method for quickly and easily authenticating large computer program. The system operates by first sealing the computer program with digital signature in an incremental manner. Specifically, the computer program is divided into a set of pages and a hash value is calculated for each page. The set of hash values is formed into a hash value array and then the hash value array is then sealed with a digital signature. The computer program is then distributed along with the hash value array and the digital signature. To authenticate the computer program, a recipient first verifies the authenticity of the hash value array with the digital signature and a public key. Once the hash value array has been authenticated, the recipient can then verify the authenticity of each page of the computer program by calculating a hash of a page to be loaded and then comparing with an associated hash value in the authenticated hash value array. If the hash values do not match, then execution may be halted.
Owner:APPLE INC
Secure game download
ActiveUS20070150937A1Apparatus for meter-controlled dispensingPlatform integrity maintainanceOperational systemCode signing
A method for gaming terminals, gaming kiosks and lottery terminals to ensure that the code-signing verification process of downloaded game software can be trusted. Drivers independently developed from the operating system supplier are embedded within the operating system kernel to verify that the micro-coded hardware components, the BIOS, the operating system components and the downloaded game software can be trusted.
Owner:IGT
System and method for enhanced layer of security to protect a file system from malicious programs
InactiveUS20060236100A1Minimize successful attacks by malicious programsEnhance layeringUser identity/authority verificationComputer security arrangementsFile systemCode signing
A system and method for providing an enhanced layer of security to protect the file system from malicious programs are provided. An additional layer of security for protecting data and to minimize successful attacks by malicious programs is provided. This additional layer uses the feature of code signing to verify that the code is from a source which the code claims to be from, and also that the code has not been tampered with by a malicious party. The file system provides a feature by which certificates are mapped to portions of a file system, e.g., files / directories, such that only programs that are certified by those certificates are able to read / modify those portions of the file system.
Owner:IBM CORP
Safe, secure resource editing for application localization
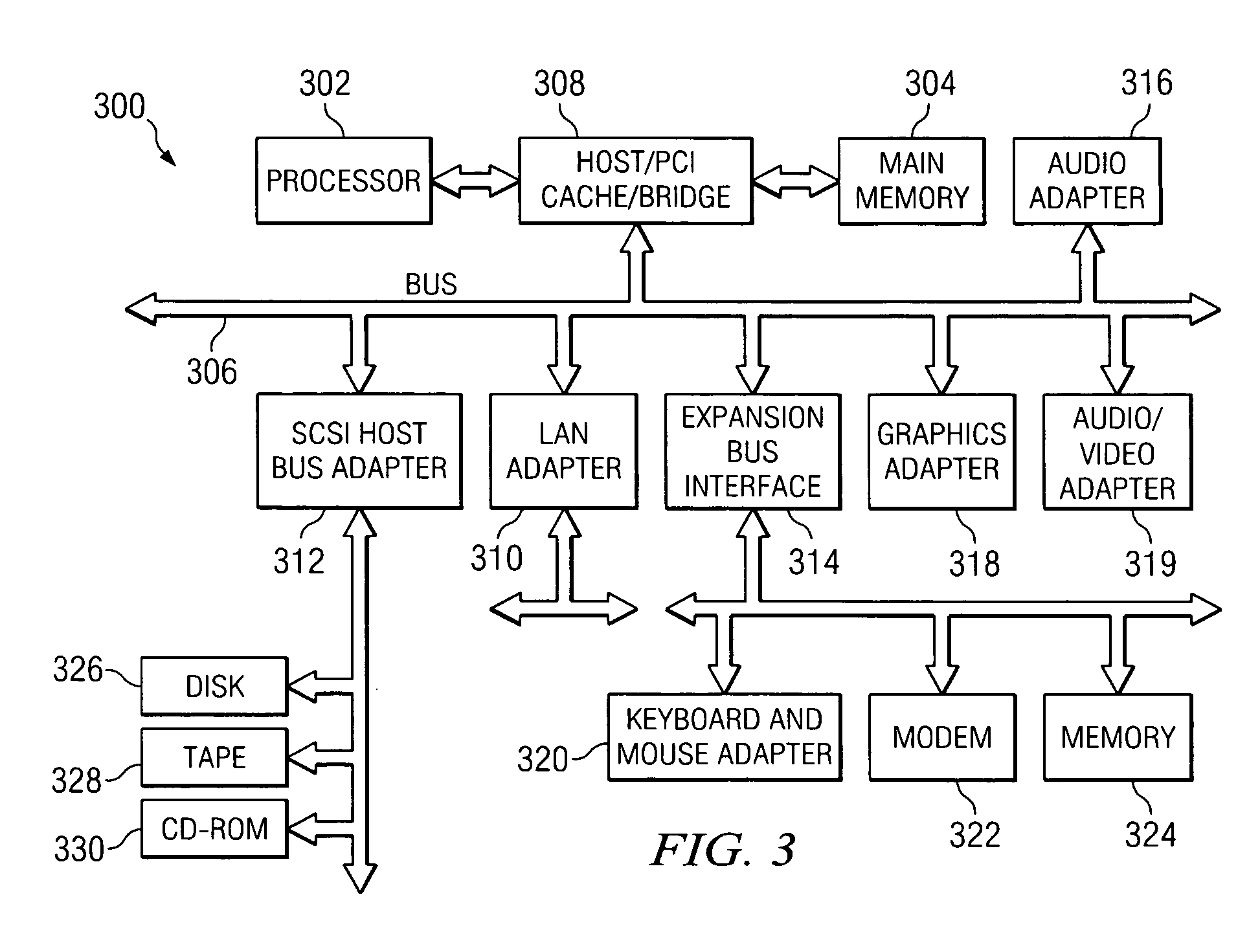
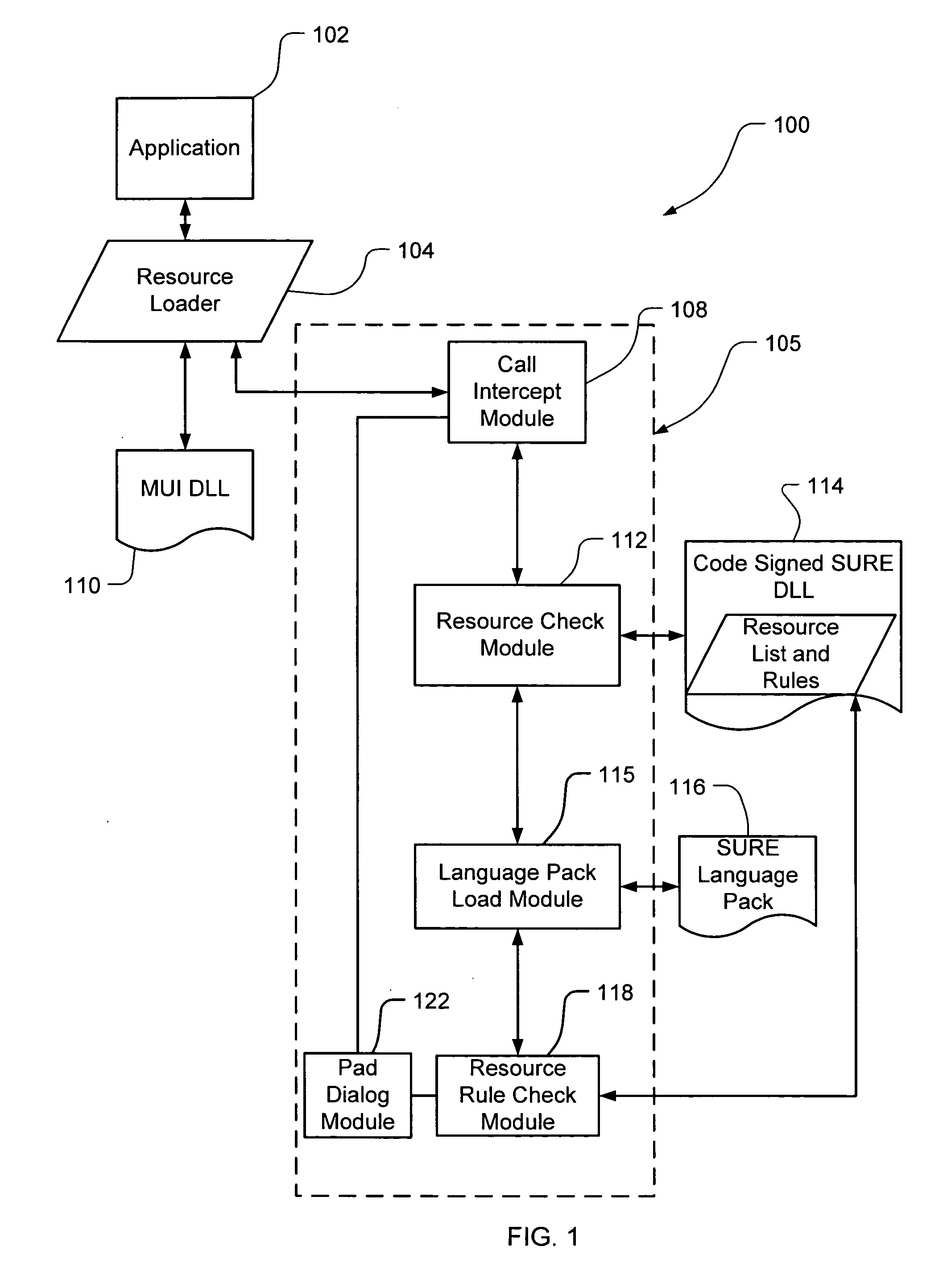
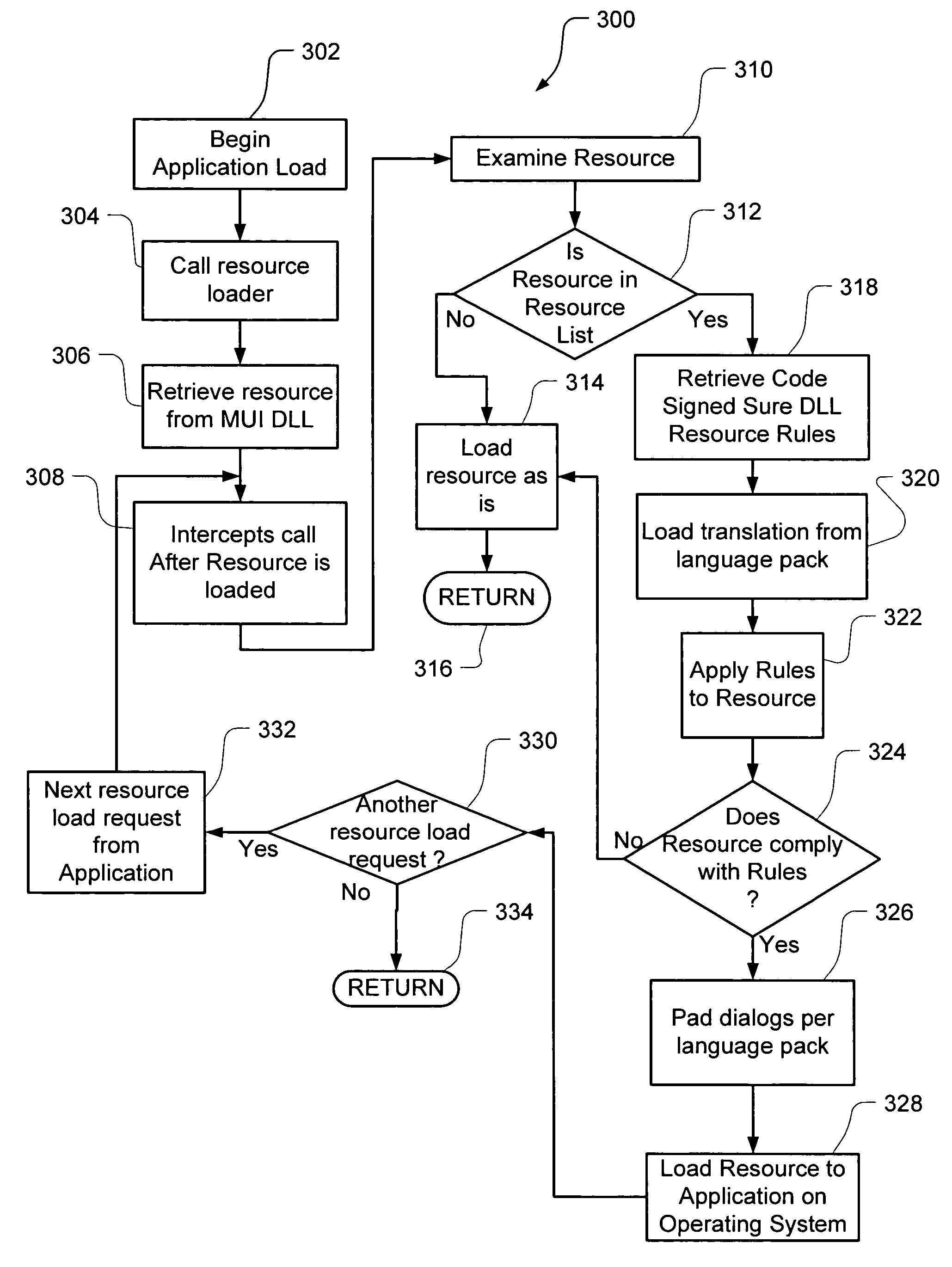
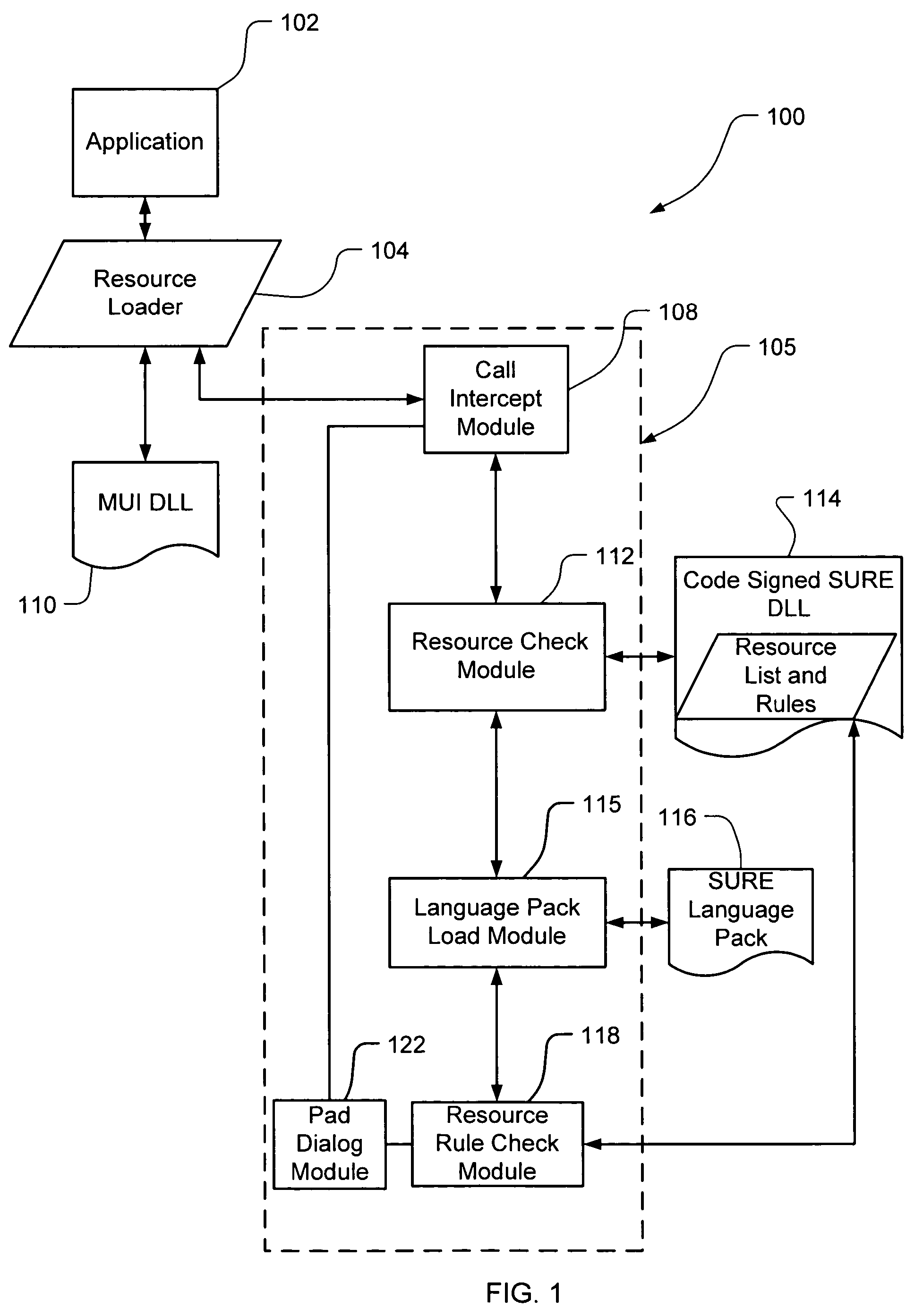
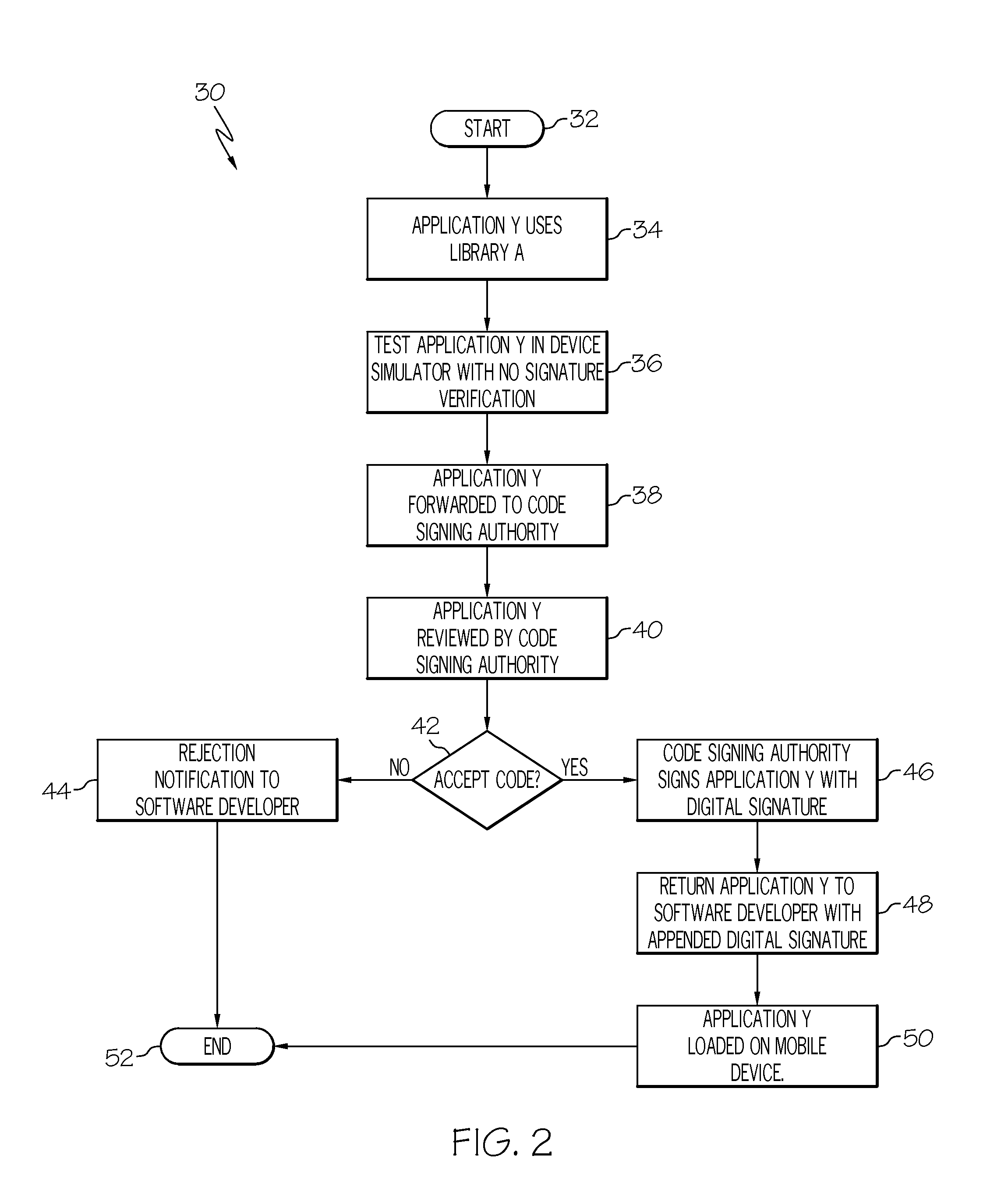
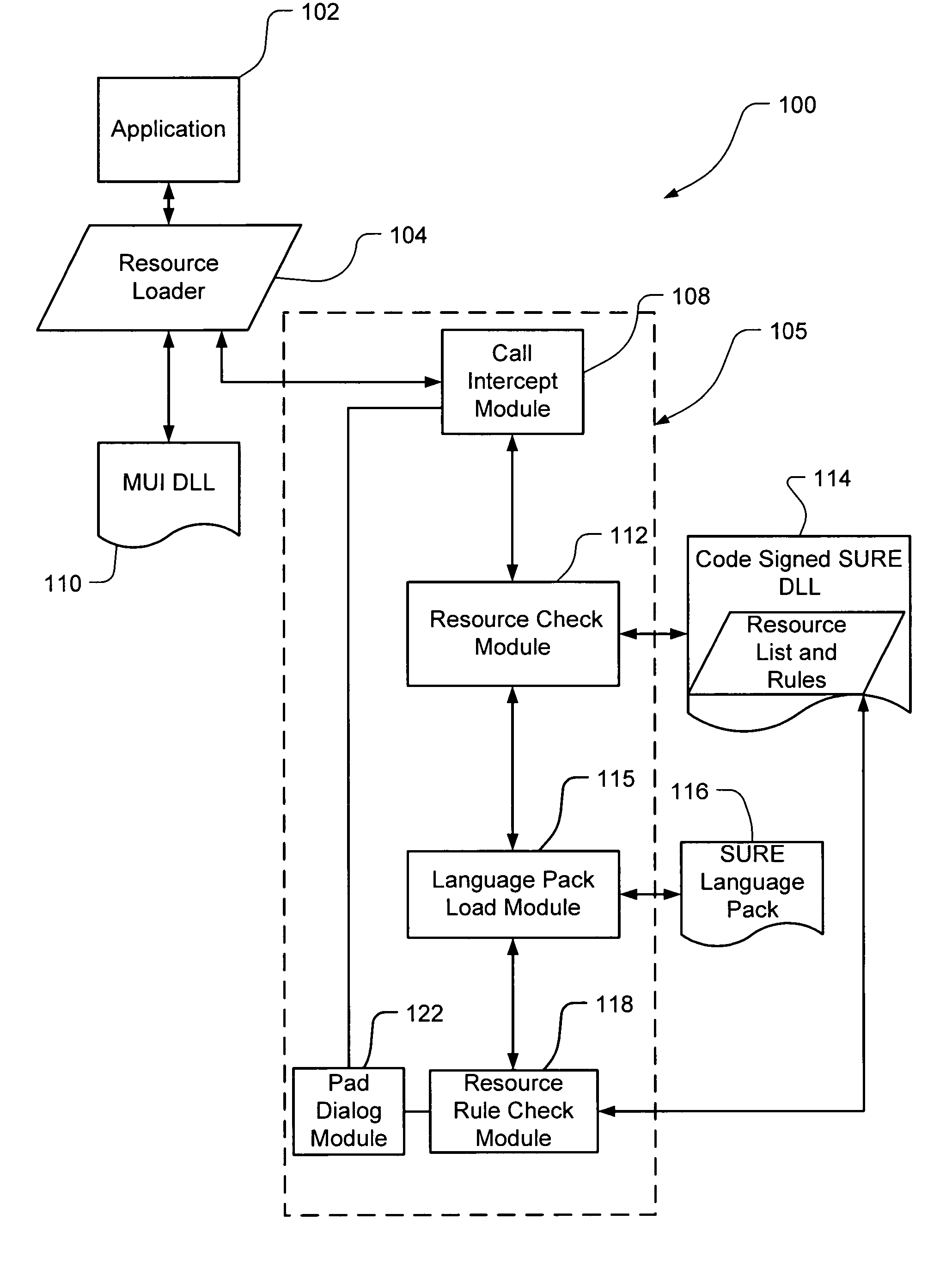
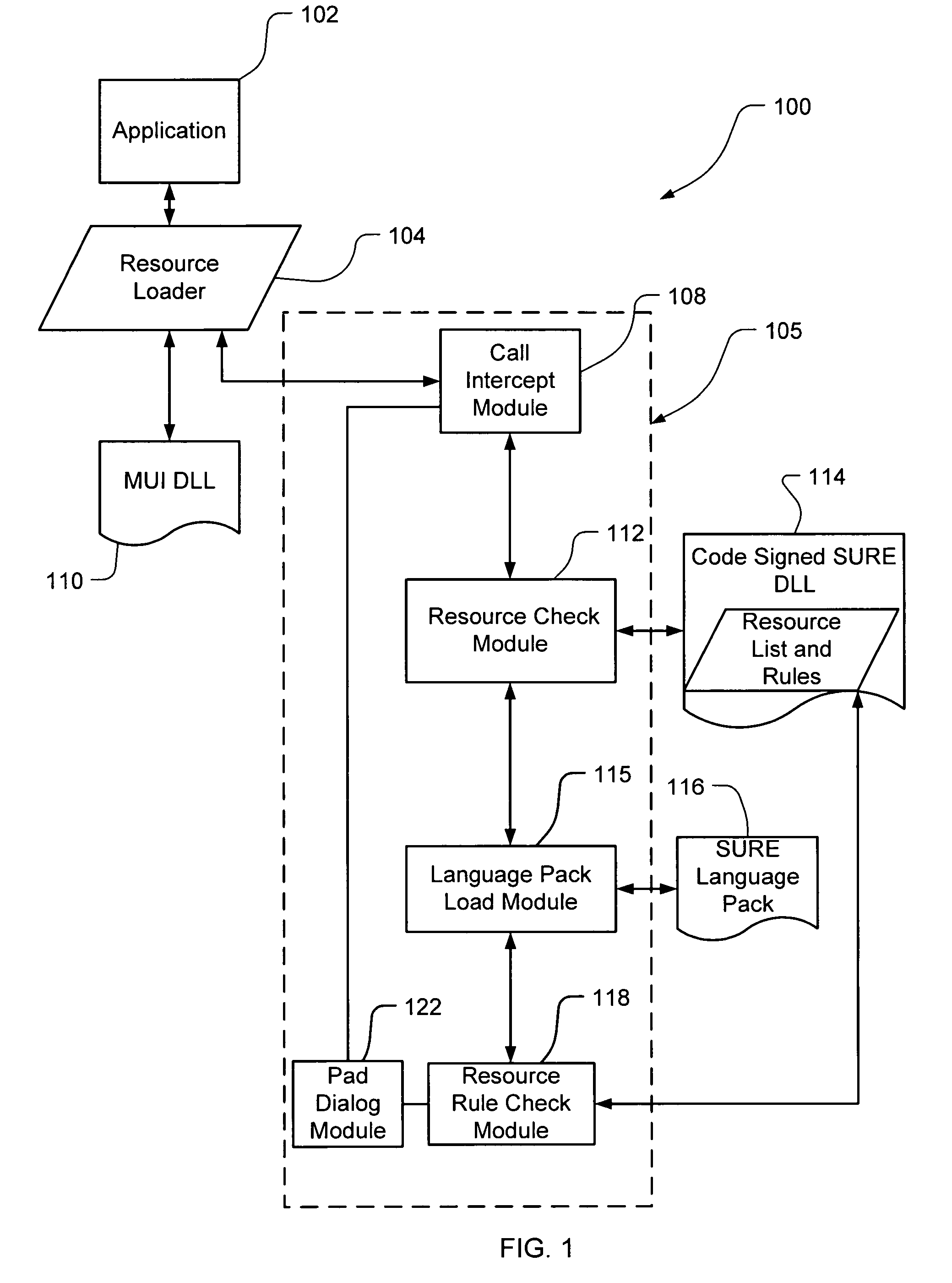
InactiveUS20060150173A1Natural language translationSpecial data processing applicationsData setOperational system
Embodiments of the present invention relate to methods, systems and computer-readable media for external localization of a software product. This external localization involves loading a base product having one or more calls to an operating system (or an API) to load language specific data. The calls are intercepted after the resource is loaded into a Resource loader, and queried whether the resource is identified in a restricted resource list such as a code signed dynamic linked library. If so, the translated resource is loaded from a specified language package. The loaded, and translated, resource is then checked against validation rules (which are also protected in a code signed resource list) to see if it is safe to use. If the resource is not on the list or the translated resource is not safe to use, the original resource is simply transferred to the application without modification from the resource loader, i.e., loaded from the base language file. This generates a localized product using a limited set of language specific data covering most situations.
Owner:MICROSOFT TECH LICENSING LLC
Method and Apparatus for Incremental Code Signing
ActiveUS20060288223A1Memory loss protectionUser identity/authority verificationArray data structureCode signing
The present invention discloses a method for quickly and easily authenticating large computer program. The system operates by first sealing the computer program with digital signature in an incremental manner. Specifically, the computer program is divided into a set of pages and a hash value is calculated for each page. The set of hash values is formed into a hash value array and then the hash value array is then sealed with a digital signature. The computer program is then distributed along with the hash value array and the digital signature. To authenticate the computer program, a recipient first verifies the authenticity of the hash value array with the digital signature and a public key. Once the hash value array has been authenticated, the recipient can then verify the authenticity of each page of the computer program by calculating a hash of a page to be loaded and then comparing with an associated hash value in the authenticated hash value array. If the hash values do not match, then execution may be halted.
Owner:APPLE INC
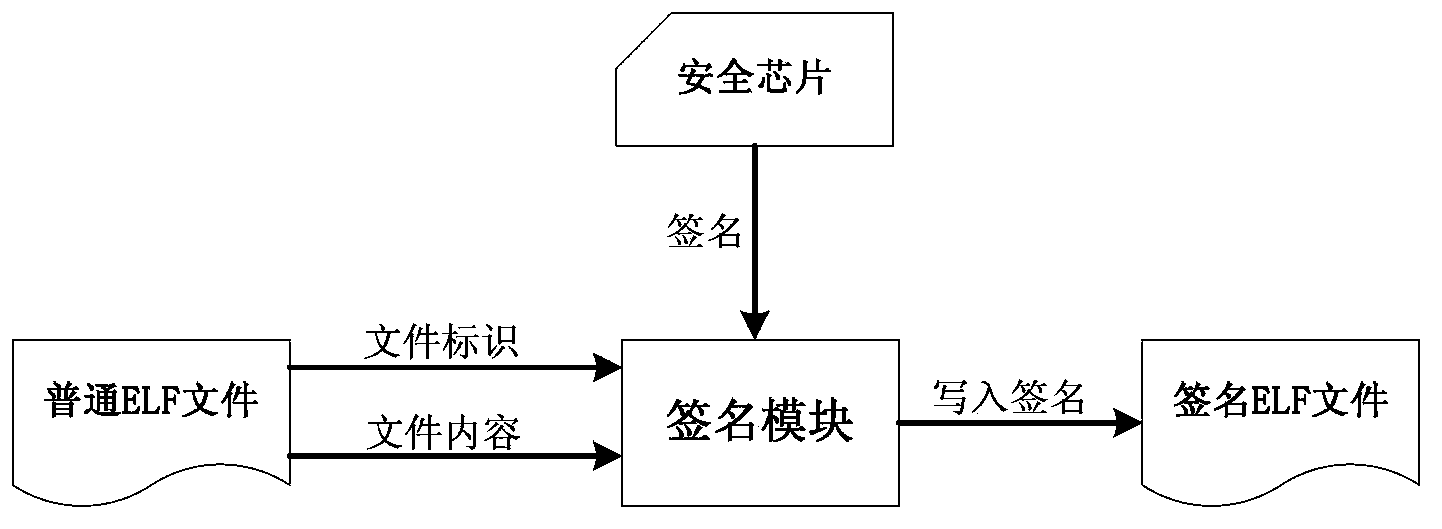
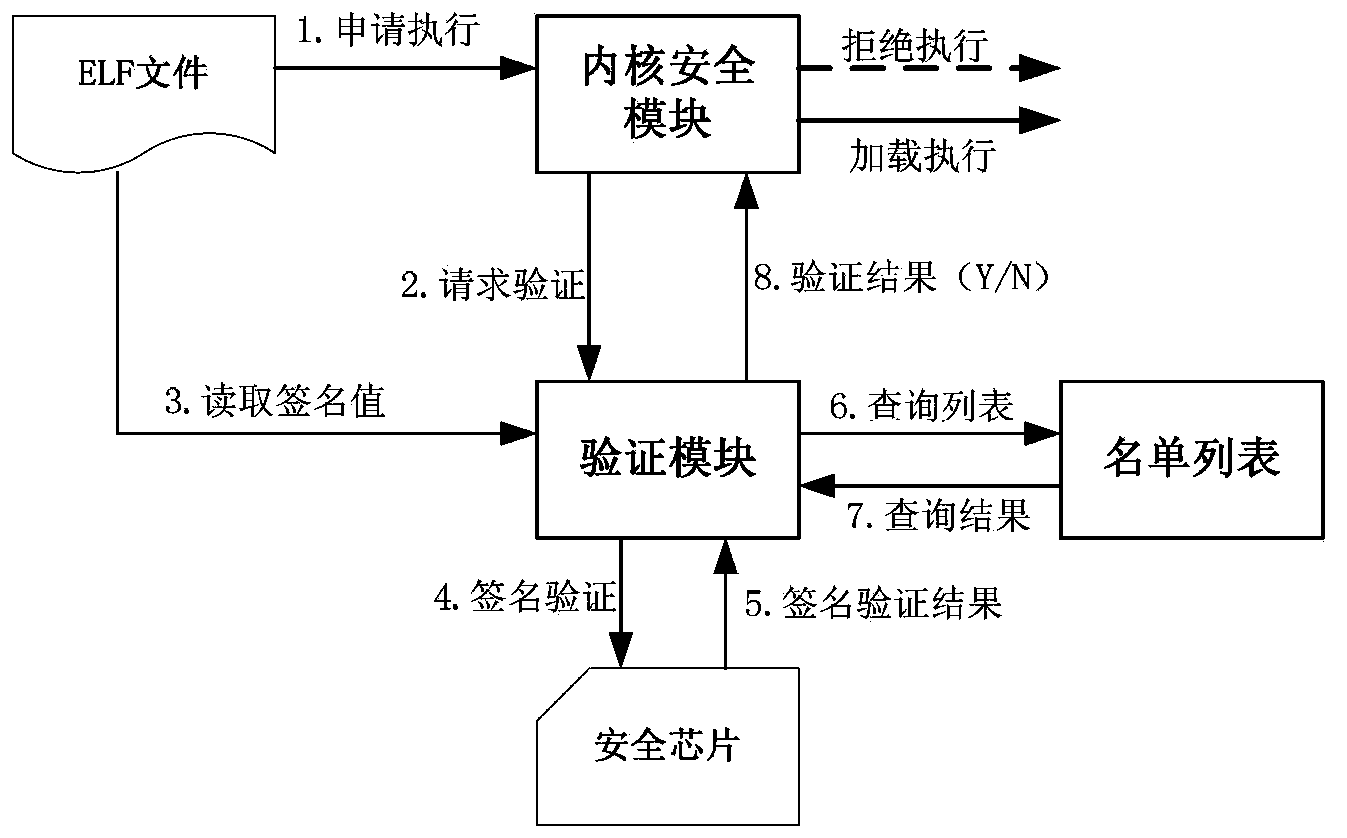
ELF file identification method and device based on code signature
InactiveCN104283860AAvoid destructionGuaranteed operational safetyDigital data protectionTransmissionOperational systemCode signing
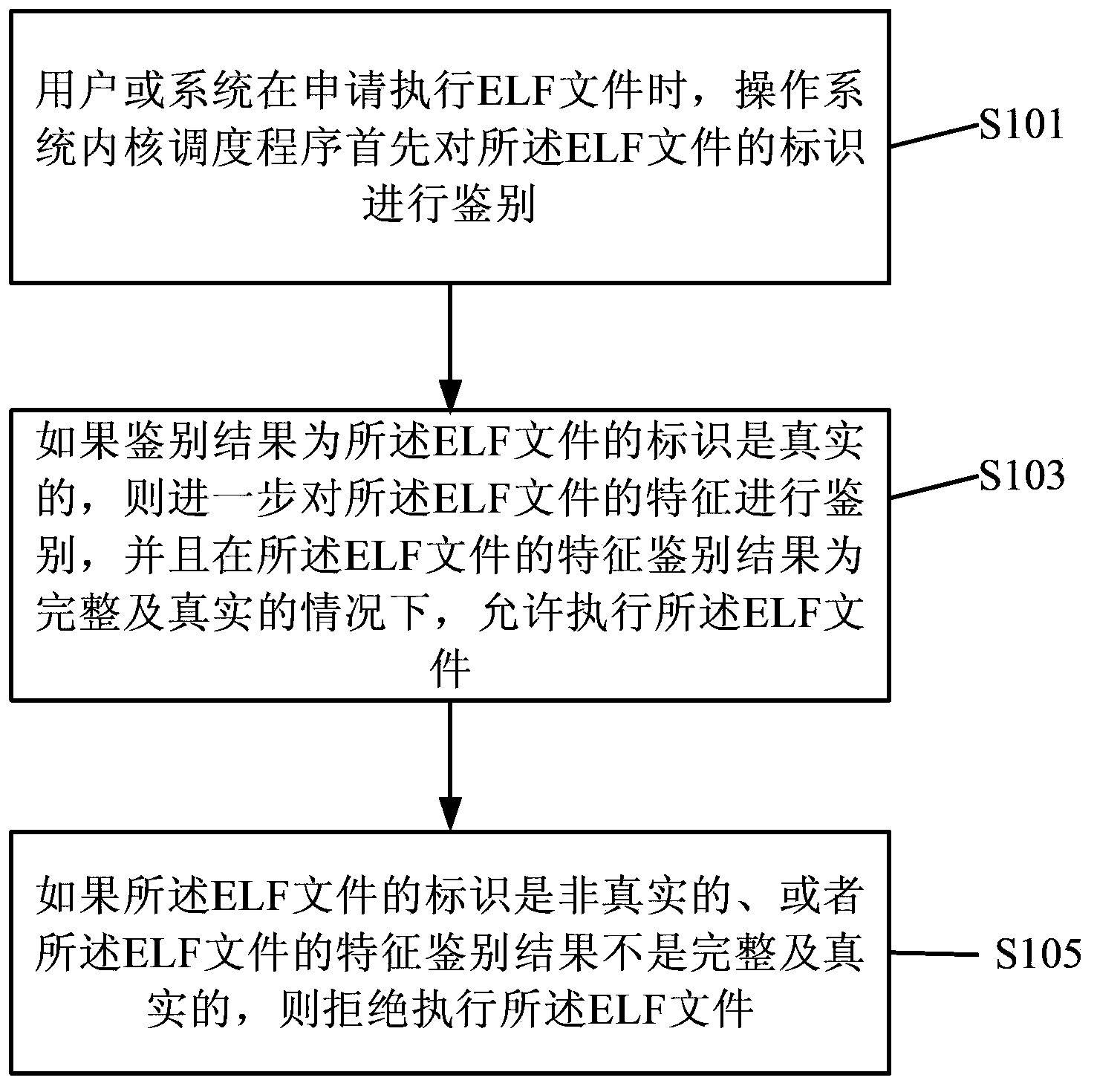
The invention discloses an ELF file identification method based on a code signature. According to ELF file identification, an issuer provides evidence, and a caller (an operating system) verifies the evidence. The evidence of the issuer is the file signature of the issuer, and the signature is made in two steps that firstly, the issuers signs for the file identification, and secondly, the issuer signs for file features. The caller carries out verification in two steps that firstly, the caller extracts the signature of the file identification to verify the file identification and judges whether a file is loaded or not, and secondly, the caller extracts the signature of the file features to verify the file features and judges whether the file is executed or not, wherein the first step is named as admissibility verification, and the second step is named as acceptance verification. By means of the ELF file identification method, identification authentication and feature authentication of the ELF file are achieved, damage caused by illegal invasion and malicious software can be effectively prevented, the operational safety of a computer is ensured, and the optimal balance between the efficiency and safety of the operating system is achieved.
Owner:全联斯泰克科技有限公司
Managing securely installed applications
Embodiments of the present disclosure provide methods and systems for managing securely installed applications. After installation, an installation framework performs a bind process to correlate the randomly assigned identifier with the unique identifier of the application. The installation framework also manages the execution of the application. When an application is launched, the application framework performs a search for that application's randomly assigned identifier and locates the application's container. The application is then allowed to execute within its container. During execution, the software application may also be restricted in various ways by the installation framework to its dynamic containers. The installer may also work with a trusted operating system component, such as the kernel, to help enforce the container restrictions. In addition, if desired, the use of random identifiers for containers may be used in conjunction with other security mechanisms, such as the use of code signing.
Owner:APPLE INC
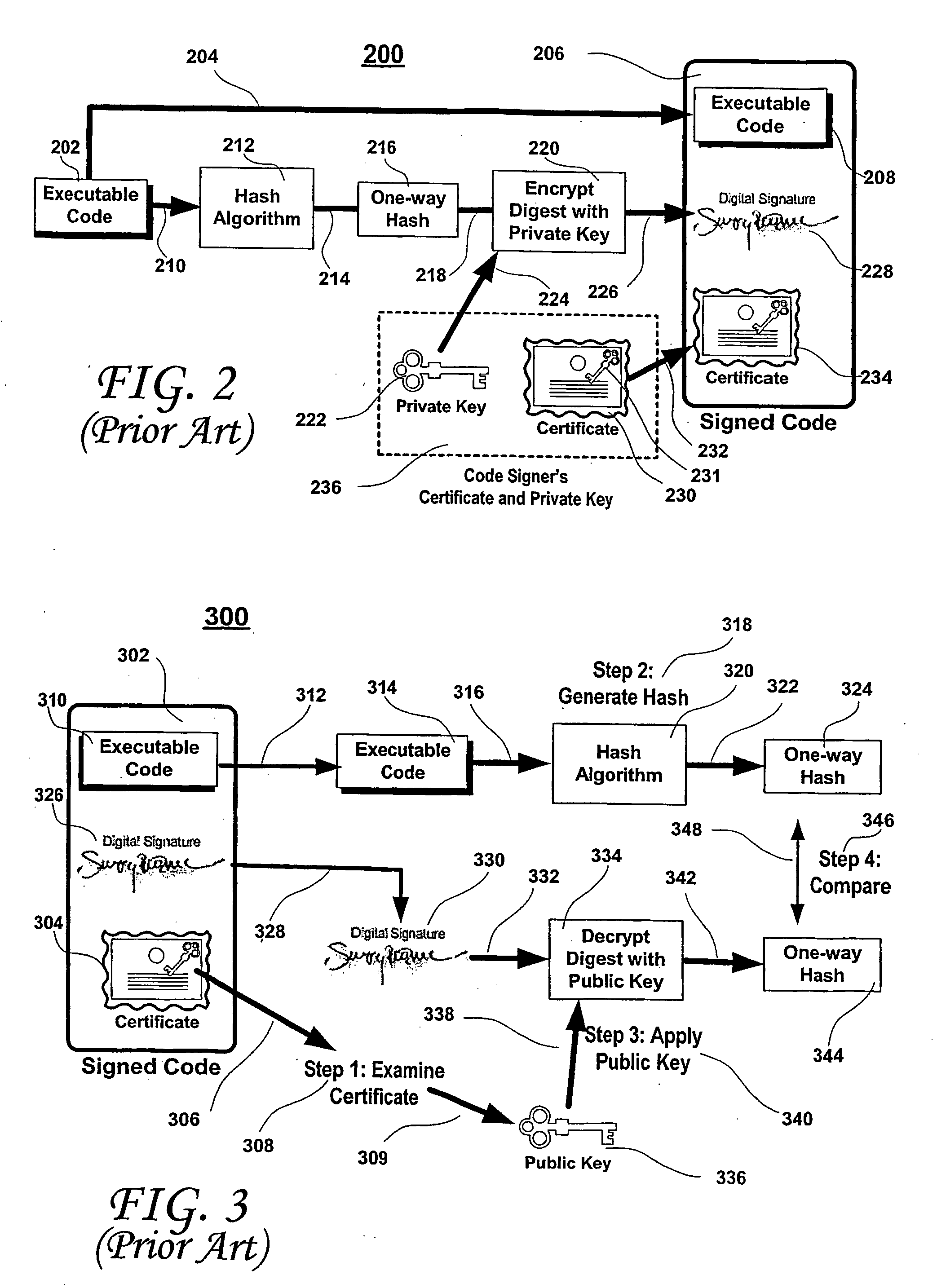
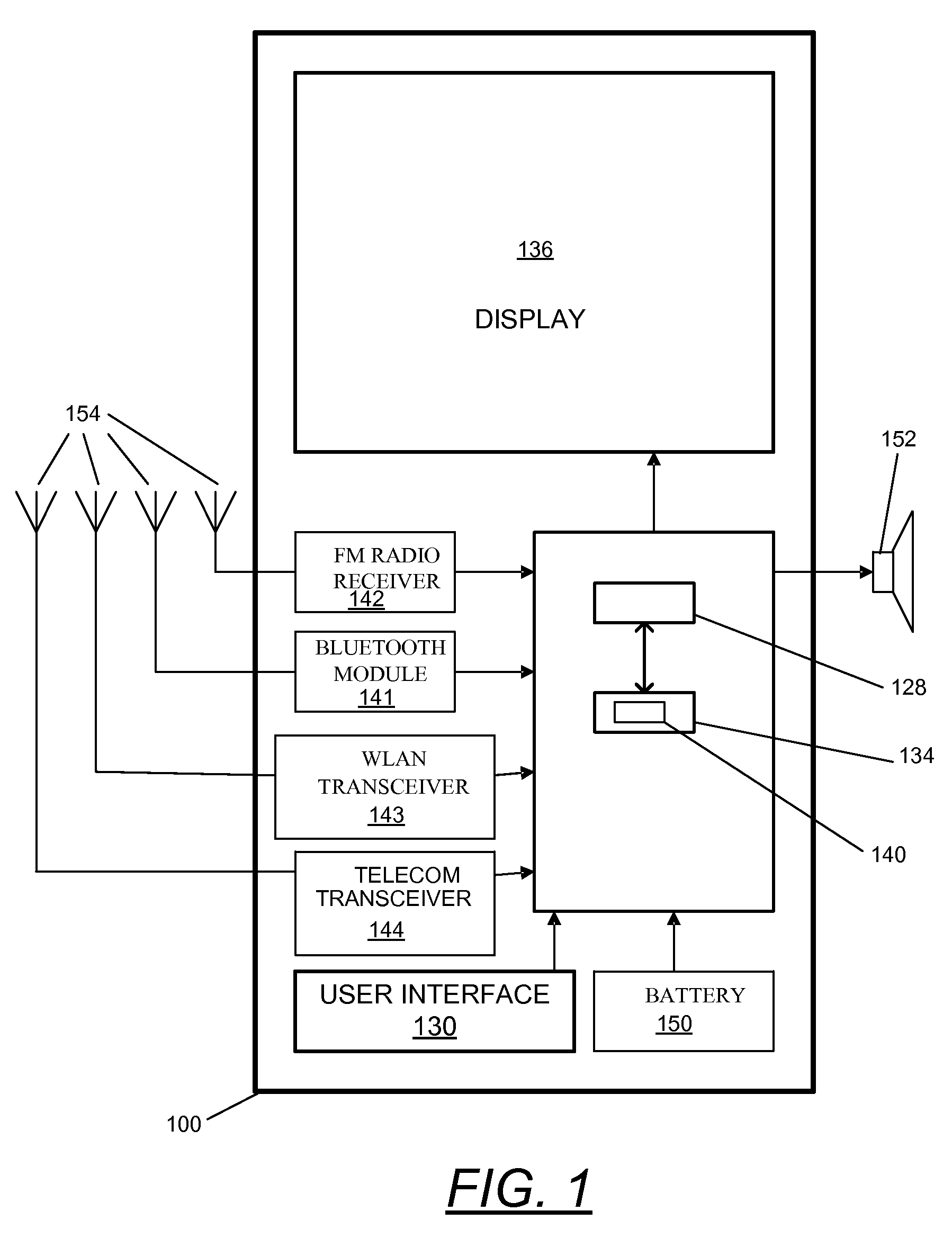
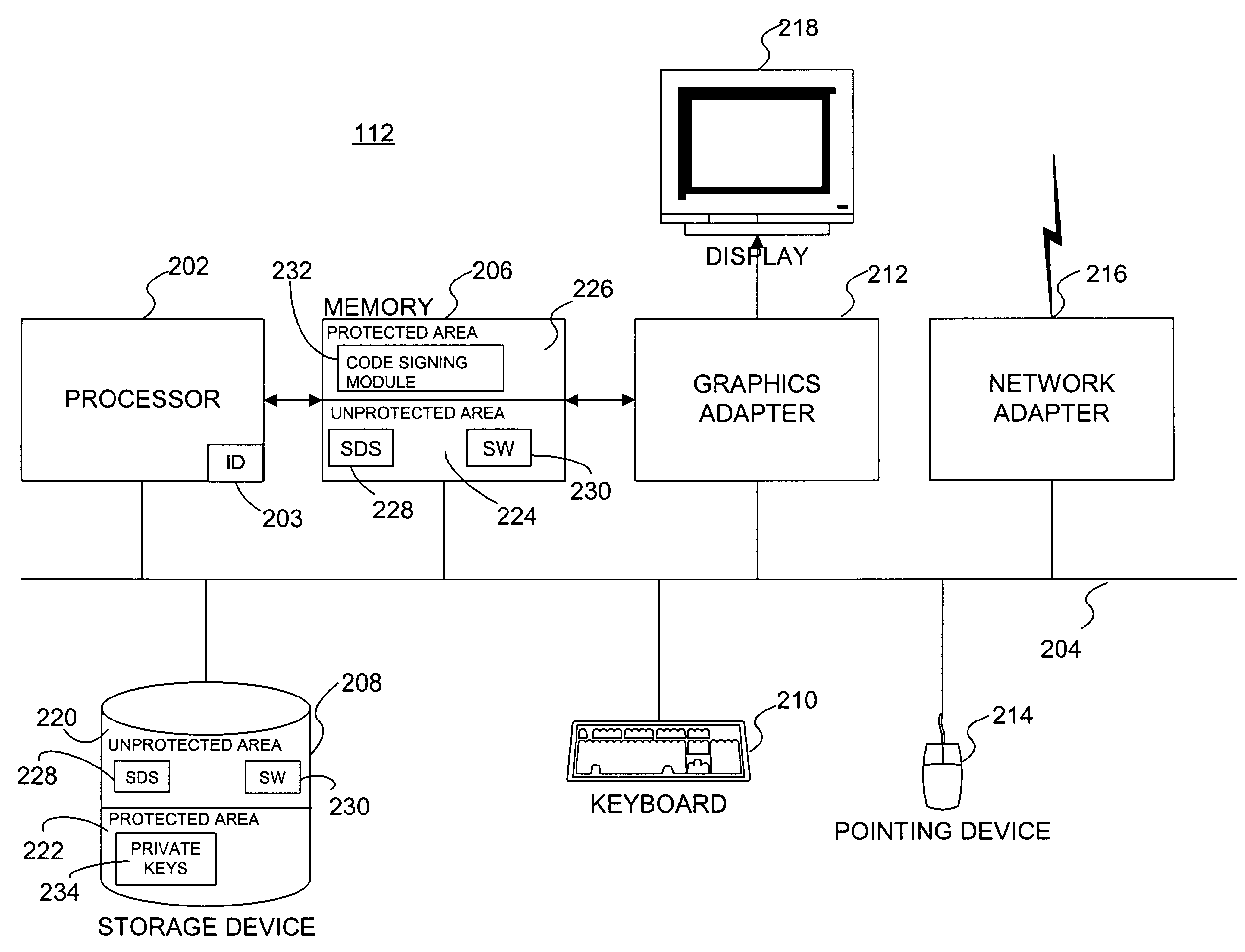
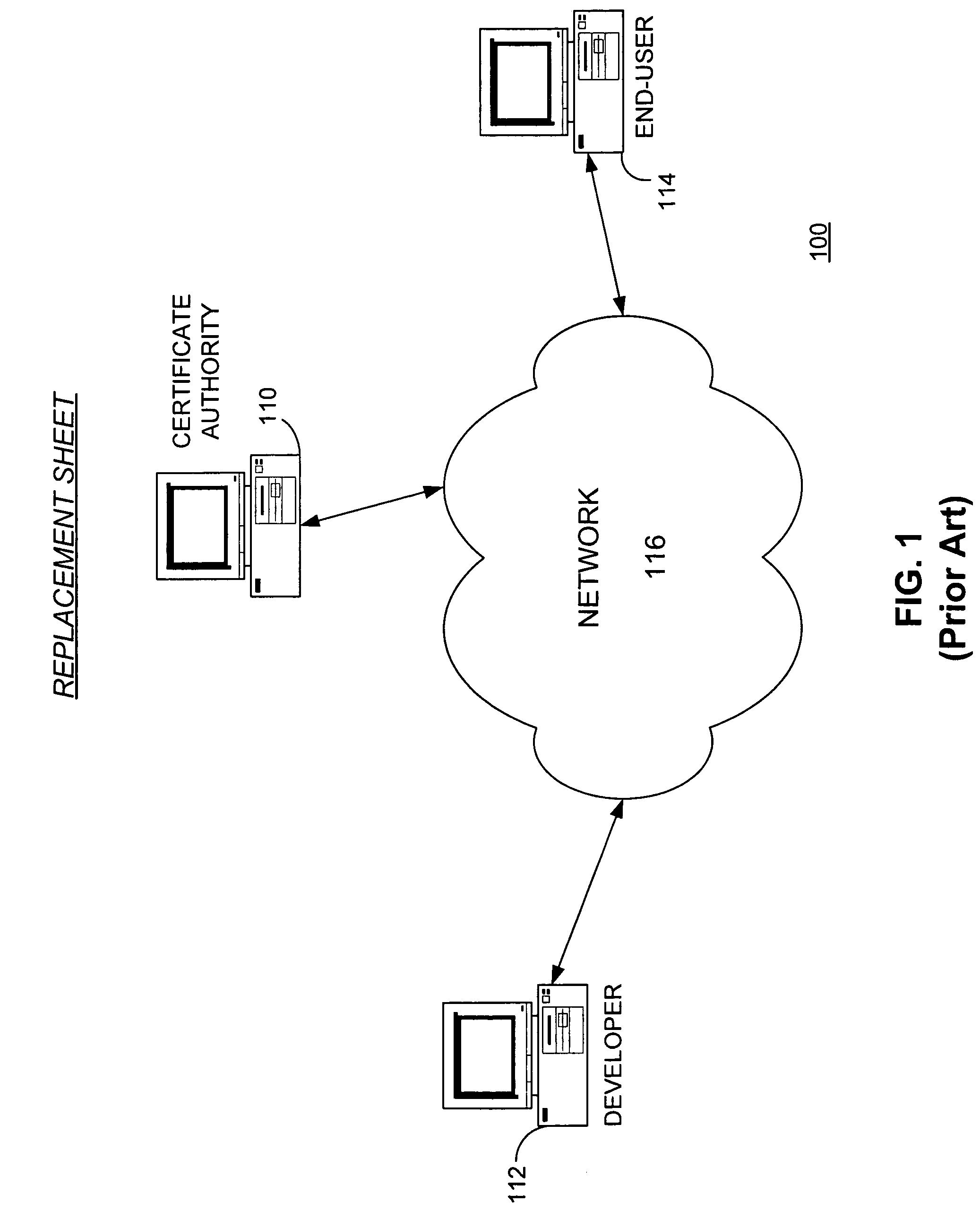
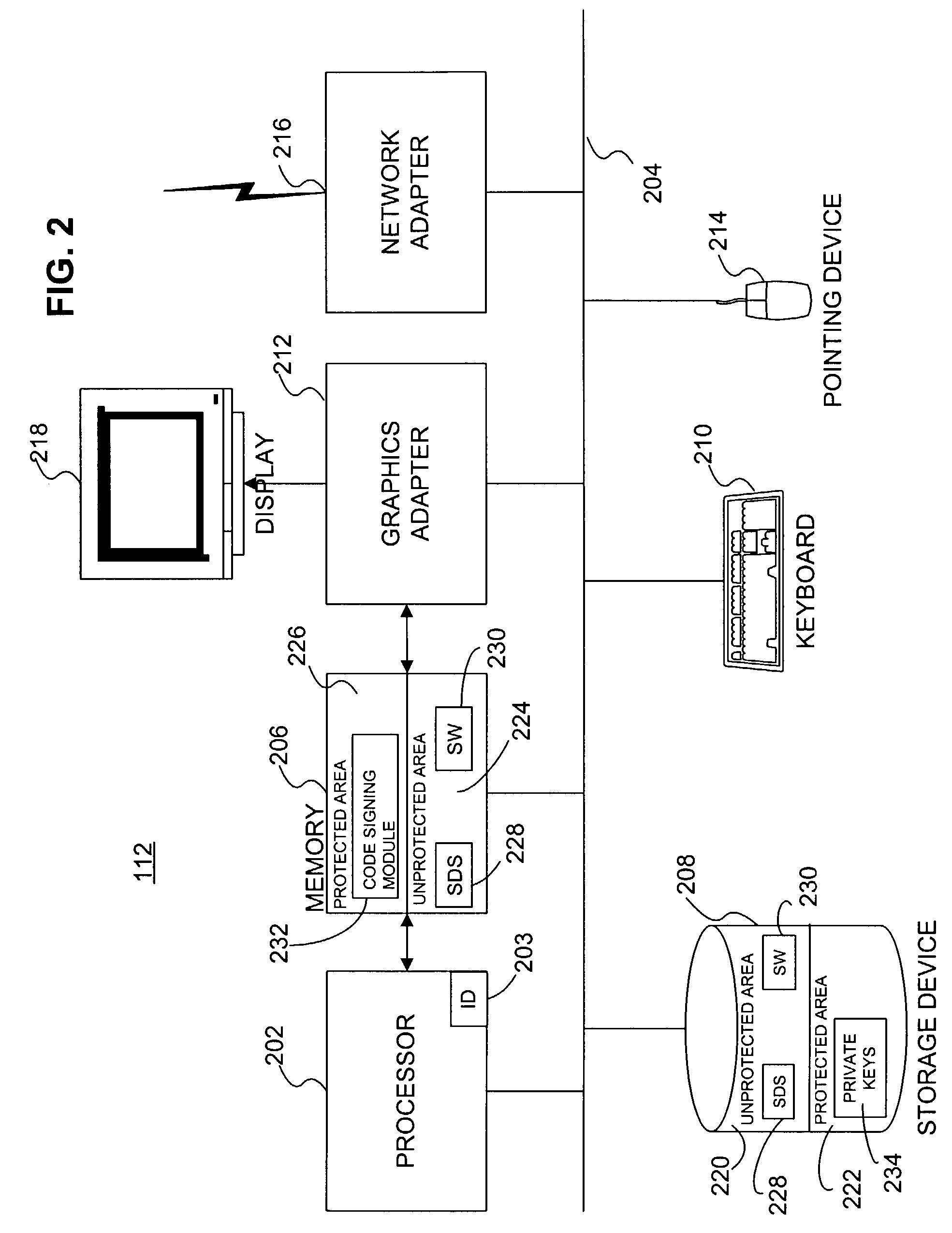
Securing executable content using a trusted computing platform
InactiveUS7694139B2Reduce riskIncrease probabilityUser identity/authority verificationComputer security arrangementsComputerized systemTrusted Computing
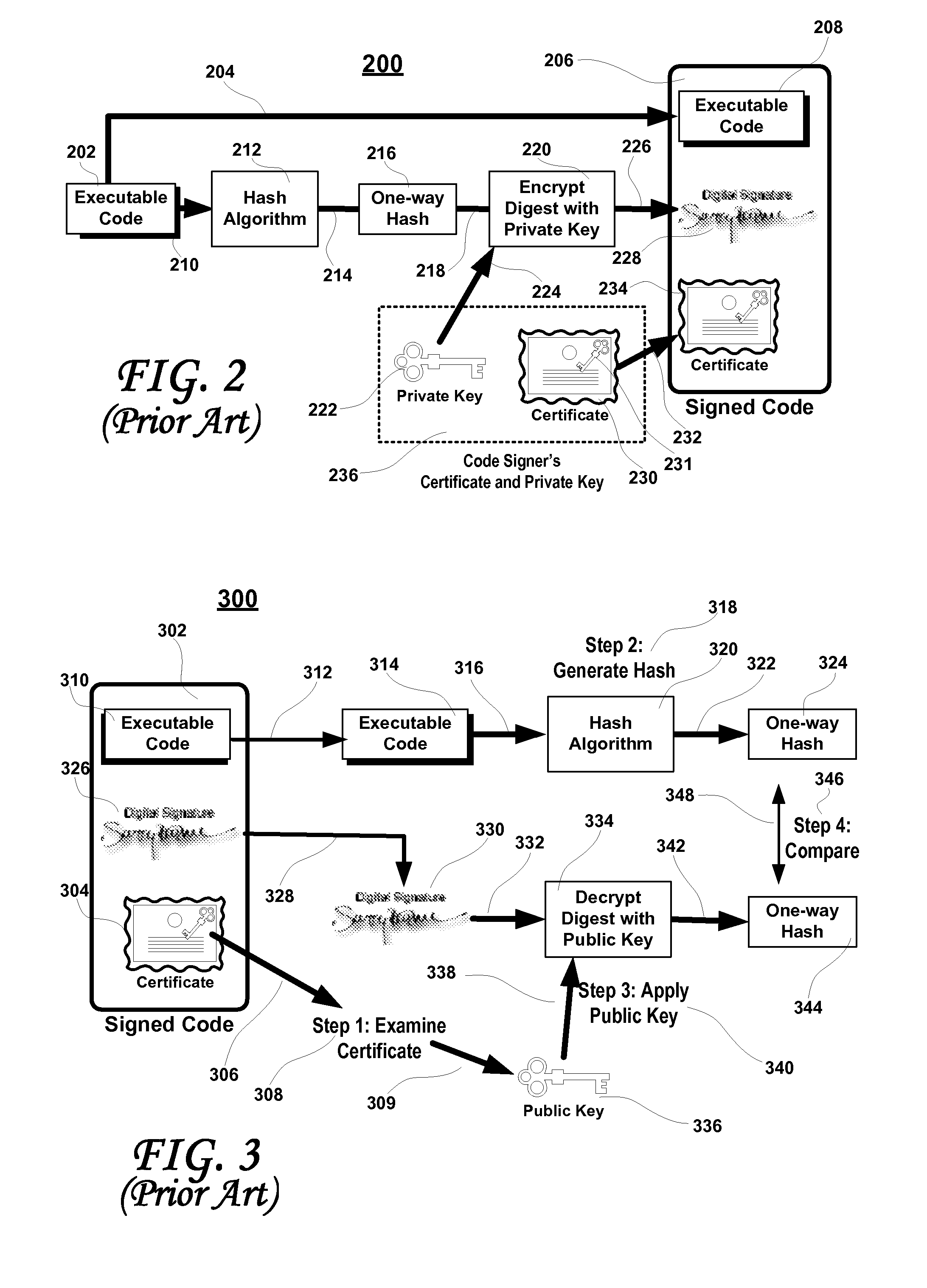
A software development system (SDS) (228) digitally signs software (230) developed on the system. The SDS (228) executes on a computer system (112) having a trusted computing platform. The platform includes protected areas (220, 226) that store data and cannot be accessed by unauthorized modules. A code signing module (232) executing in a protected area (226) obtains a private / public key pair and a corresponding digital certificate. The SDS (228) is configured to automatically and transparently utilize the code signing module (232) to sign software (230) produced by the system. End-user systems (114) receive the certificate with the software and can use it to verify the signature. This verification will fail if a parasitic virus or other malicious code has altered the software (230). Accordingly, the SDS (228) greatly reduces the risk of malicious code executing on the end-user computer system (114).
Owner:CA TECH INC
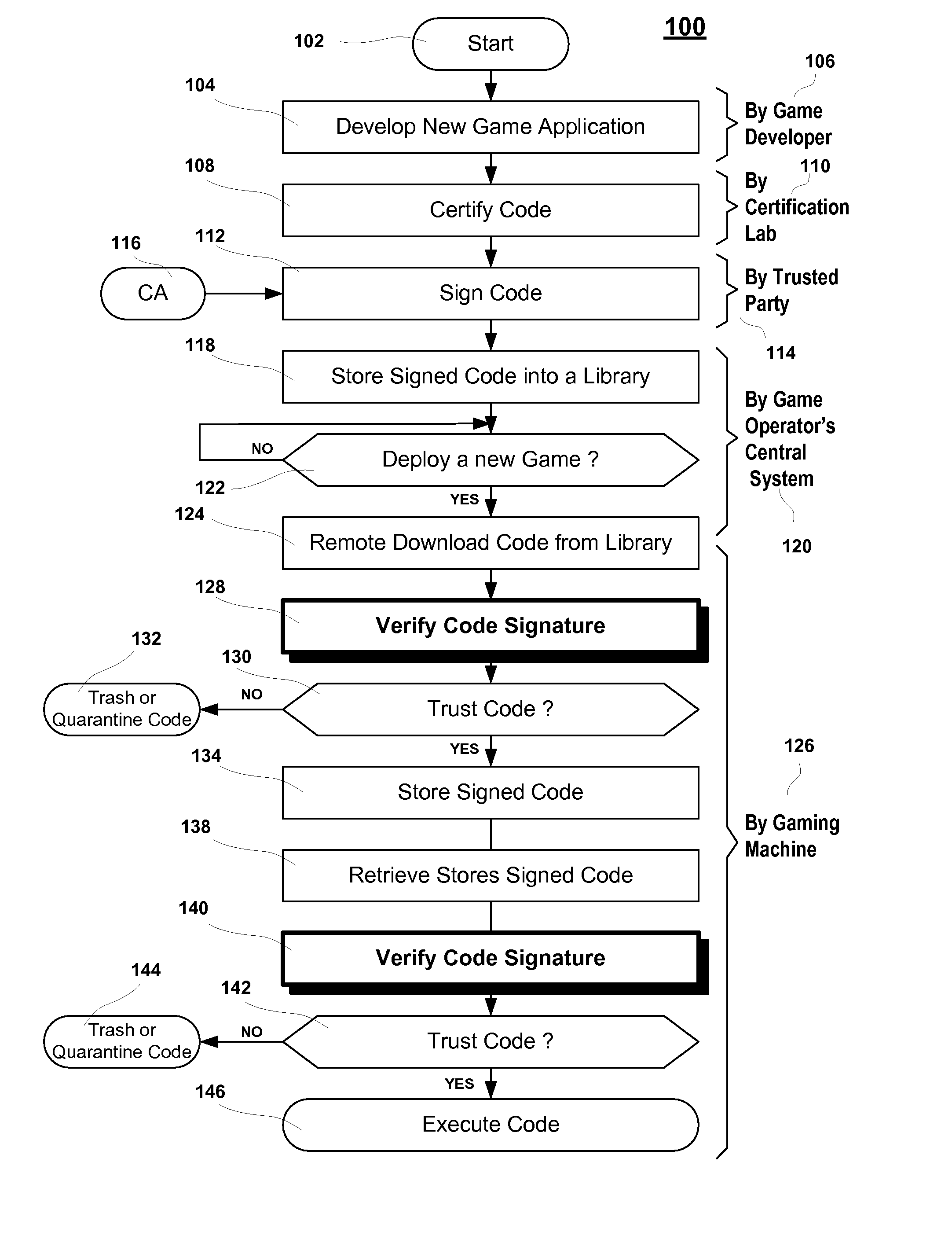
Universal method for submitting gaming machine source code software to a game certification laboratory
InactiveUS7802087B2User identity/authority verificationDigital computer detailsOperational systemGeneral purpose computer
A universal computer-implemented method for submitting source code to an authorized game certification laboratory. Initial source code and subsequent source code patches may be transferred from the manufacturer's software development environment into the laboratory's software development environment in a controlled fashion using packaging installation technology normally used for deploying software applications. The packaging technology contains automation actions for automating the synchronization and / or management of the source code and related files between the two software development environments. The entirety of the source code or any source code patch sequence may be removed by executing the corresponding uninstall function. The package containing the original source code or the source code patch sequences and related files may be code signed such as to provide persistent proof of origin which may be verified at any time. The method may be implemented under any operating system such as Microsoft Windows, Linux, UNIX and Apple Mac OS without the laboratory having to learn a complex source code configuration management software.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
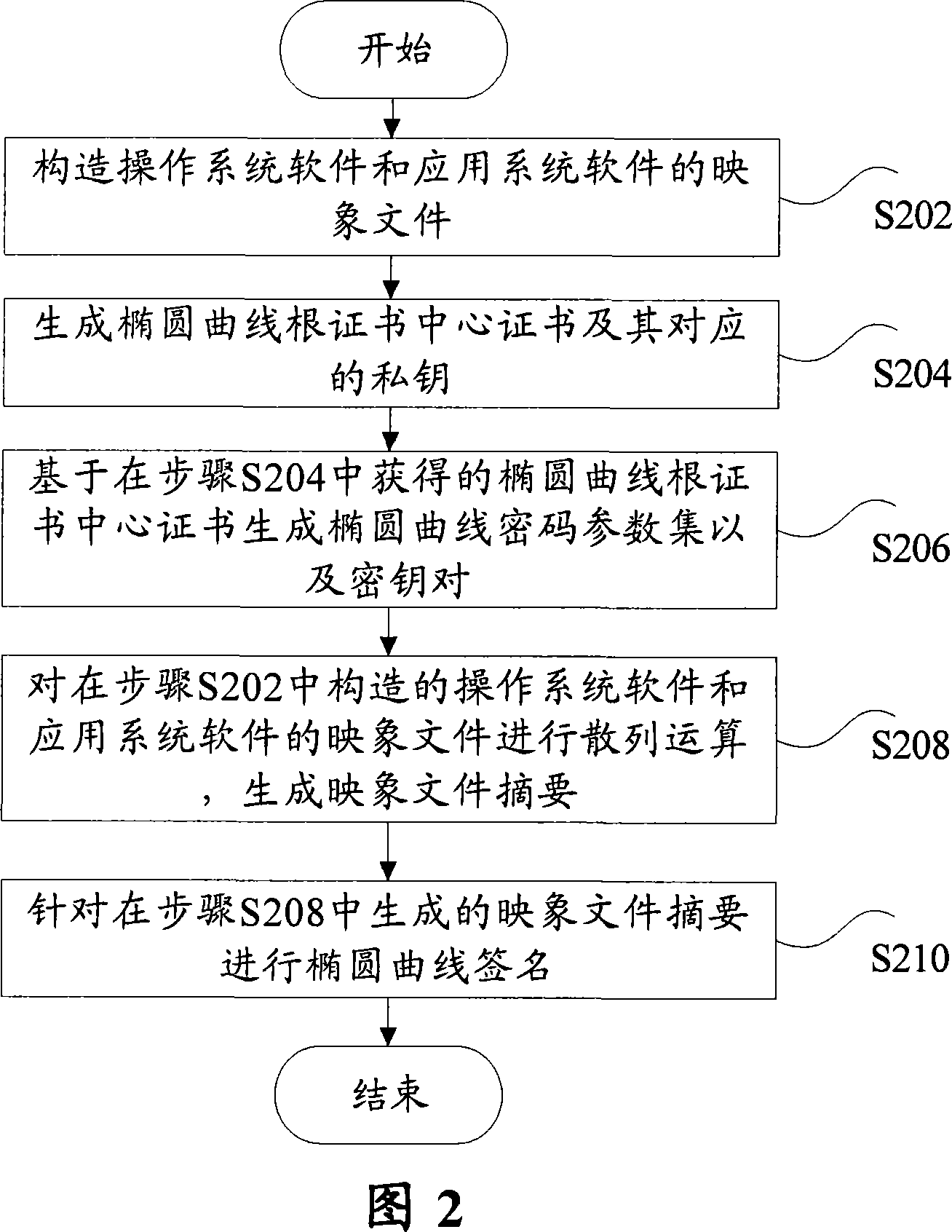
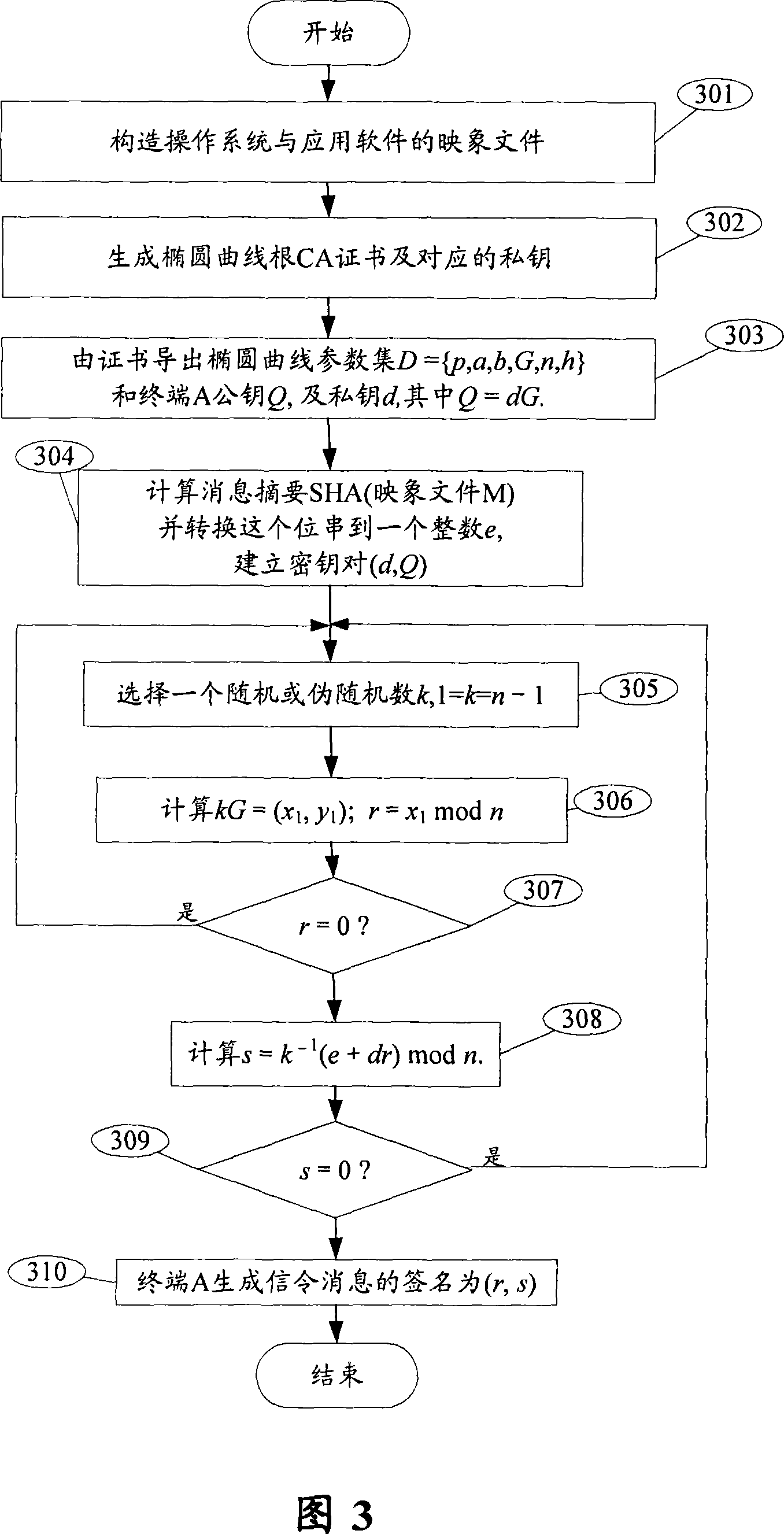
Secure guiding system, method, code signature construction method and authentication method
ActiveCN101034991AEnsure safetyAvoid churnPublic key for secure communicationUser identity/authority verificationOperational systemCode signing
The invention is a mobile terminal safe booting method, comprising the steps of: 1. safe booting program builds an interrupt vector list in the internal RAM of a safe processing kernel; 2. initializing the internal RAM; 3. the safe processing kernel boots program to build access to the internal RAM and makes hardware initialization, where the hardware comprises flash memory out of safe processing kernel chip; 4. loading and processing configuration data in the flash memory; 5. loading operating system software mapping file and completing authentication on the operating system software mapping file based on ECC (Elliptic Curve Cryptography); 6. loading application system software mapping file and completing authentication on the application system software mapping file based on ECC; and 7. after the application system software mapping file passes the authentication, transmitting the control to the application system. And the invention also discloses a mobile terminal safe booting system, and a code signing constructing method and a code signing authentication method.
Owner:BEIJING SHENZHOU ANFU TECH CO LTD
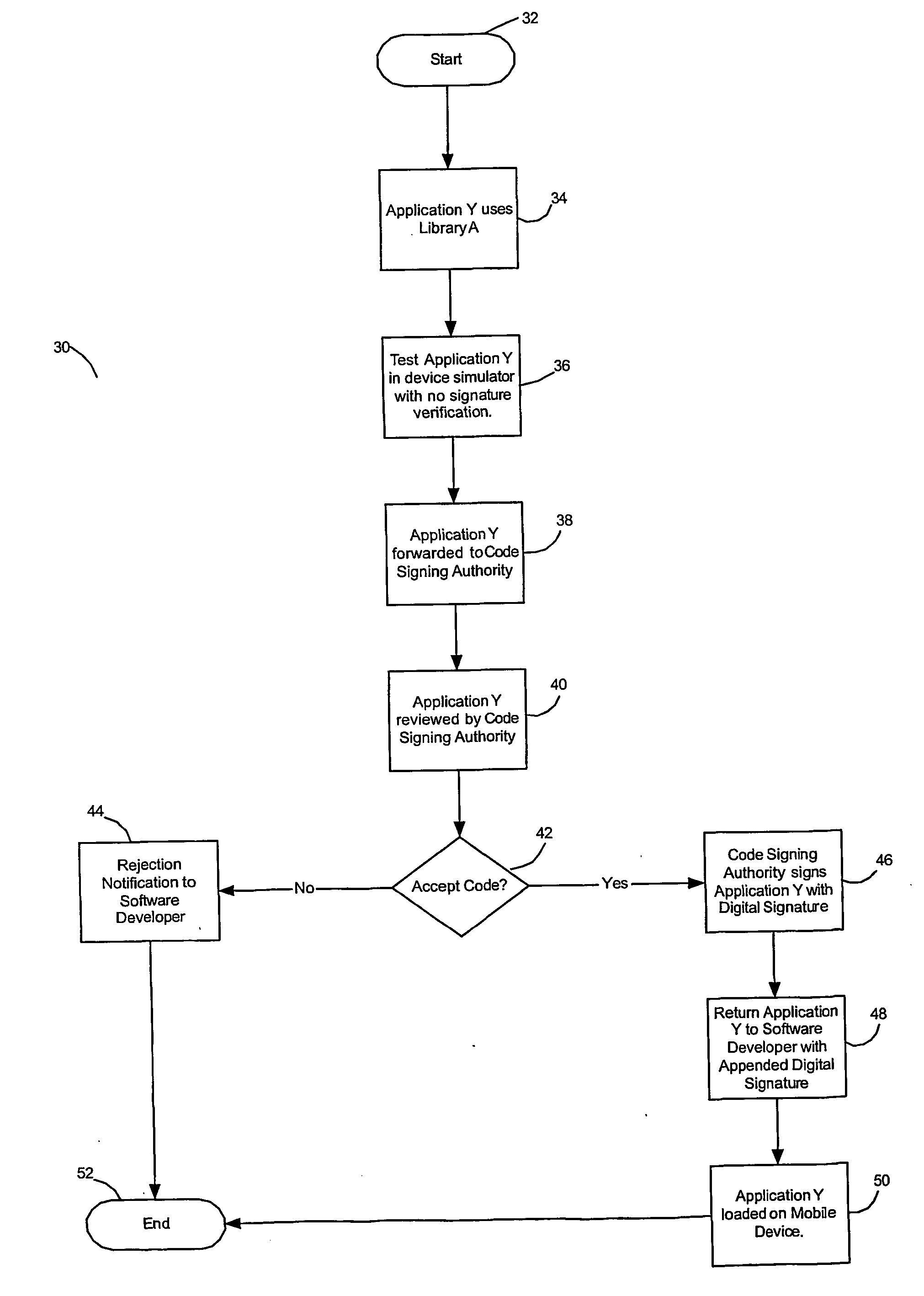
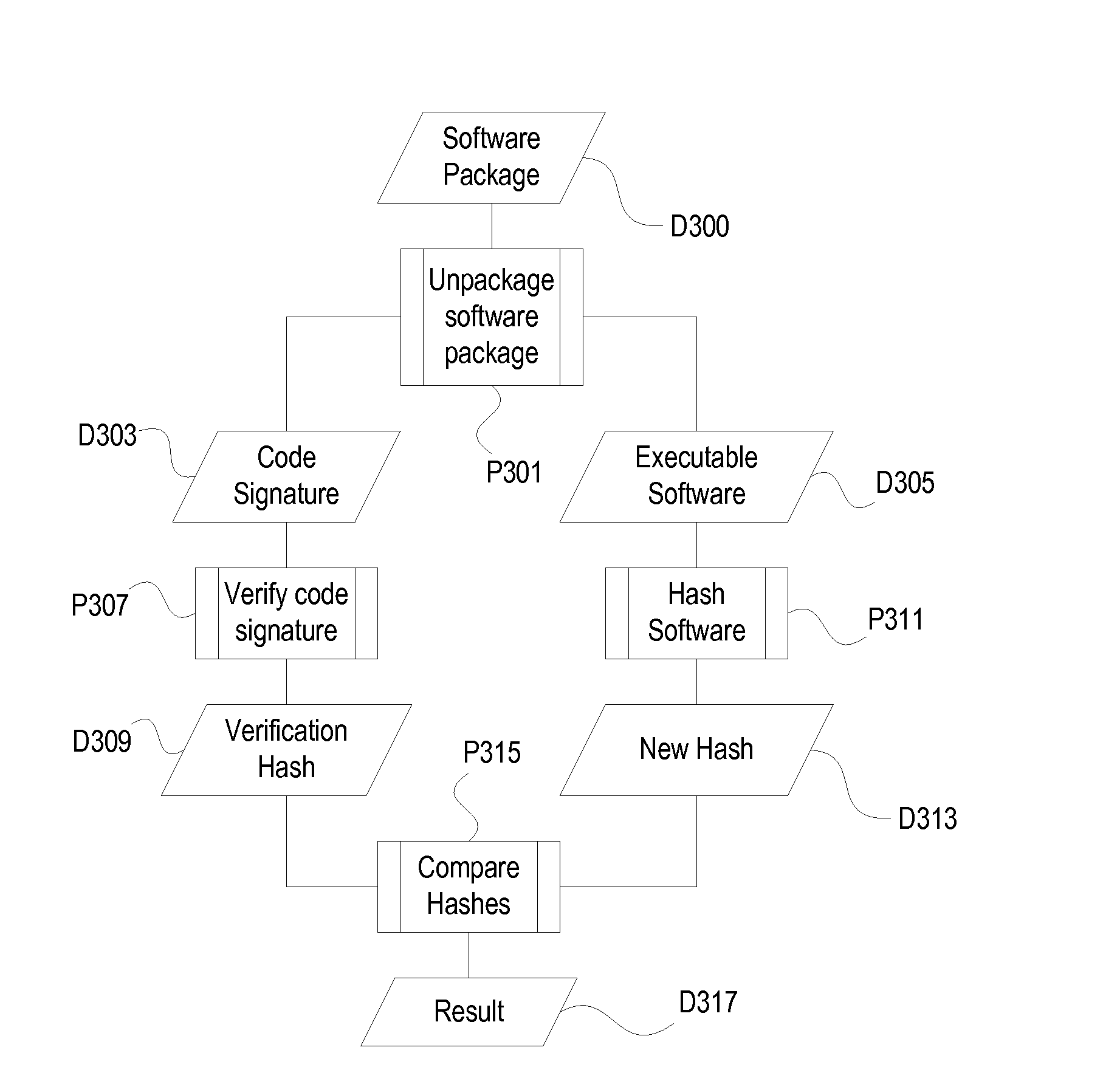
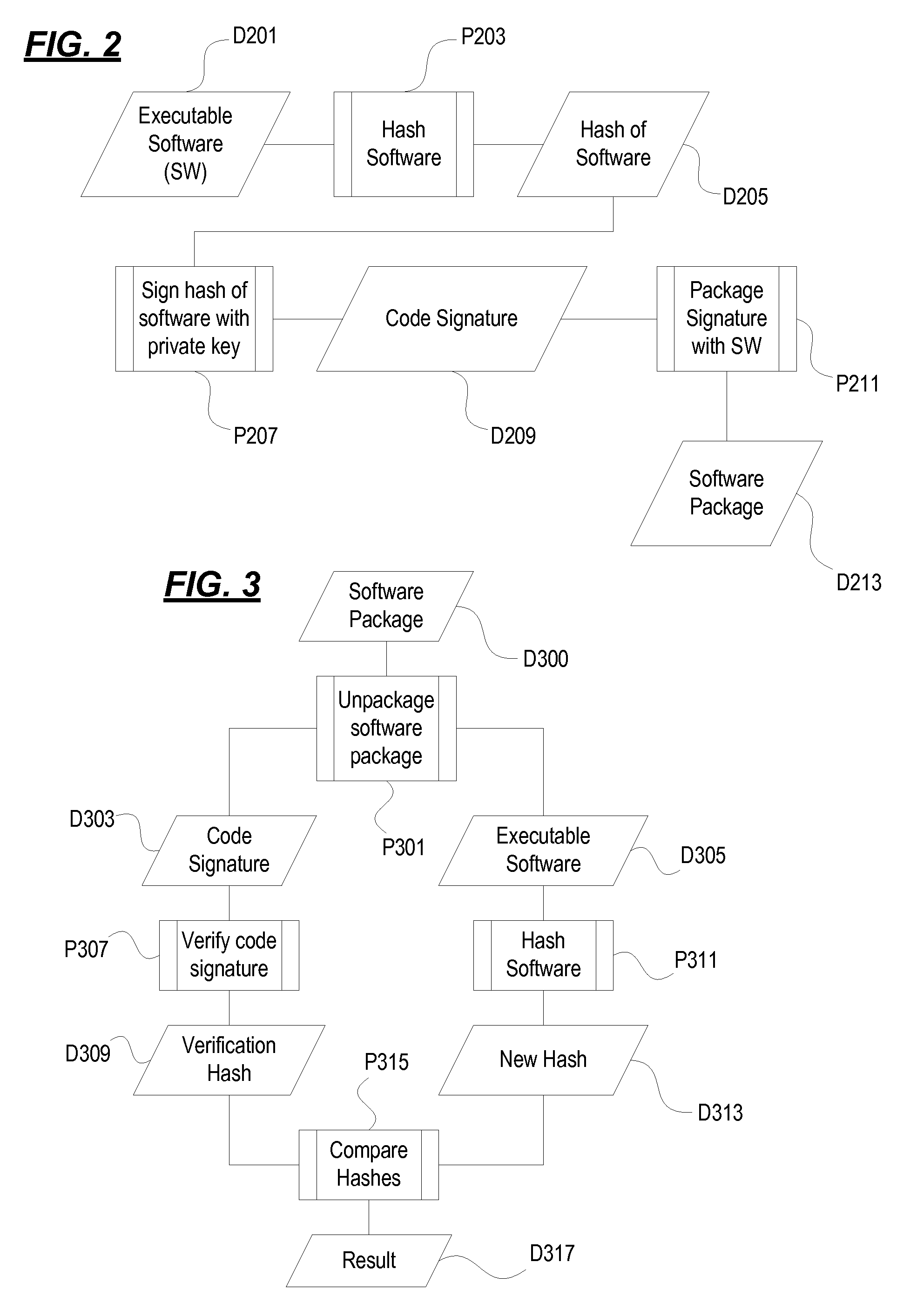
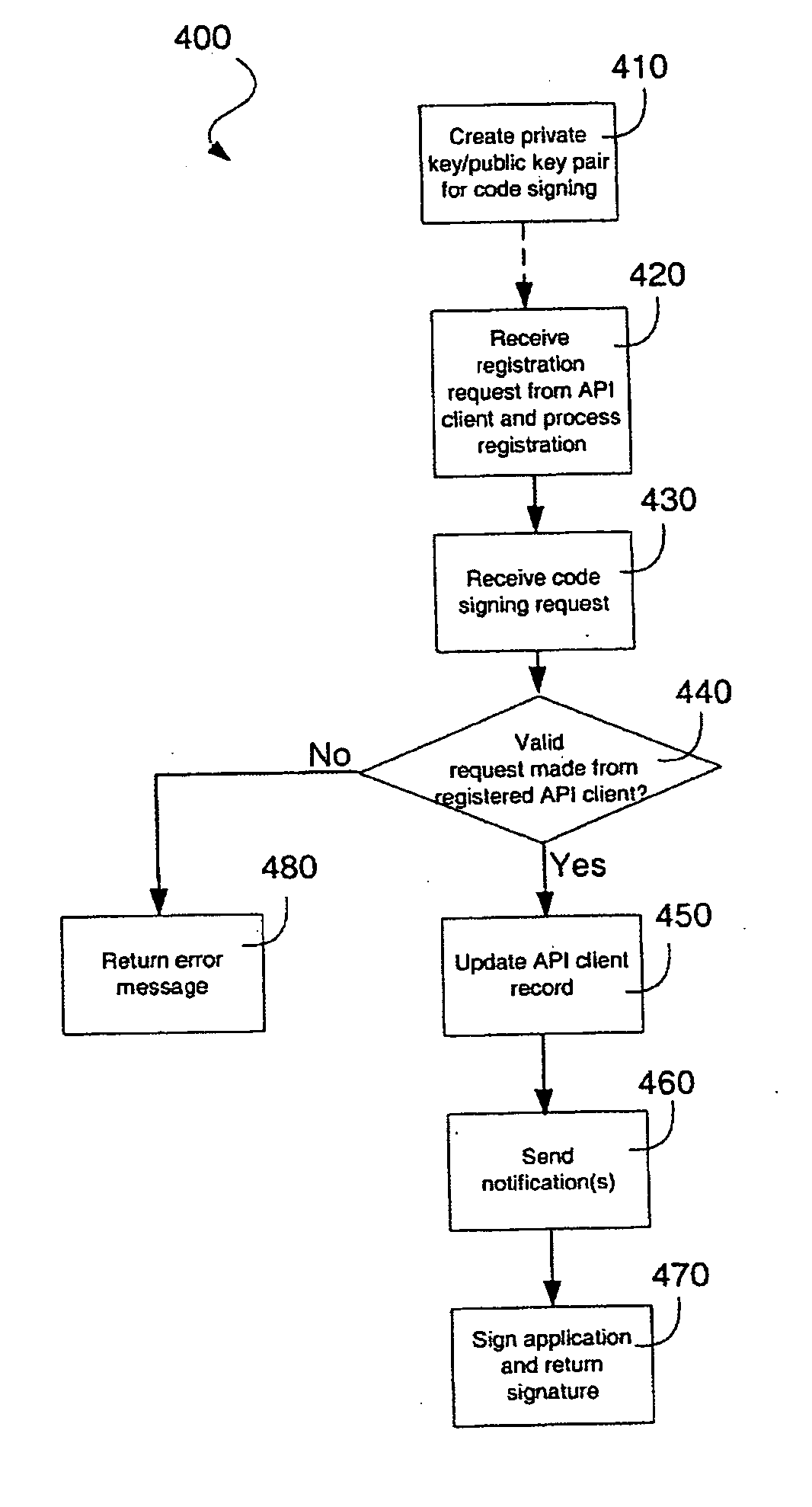
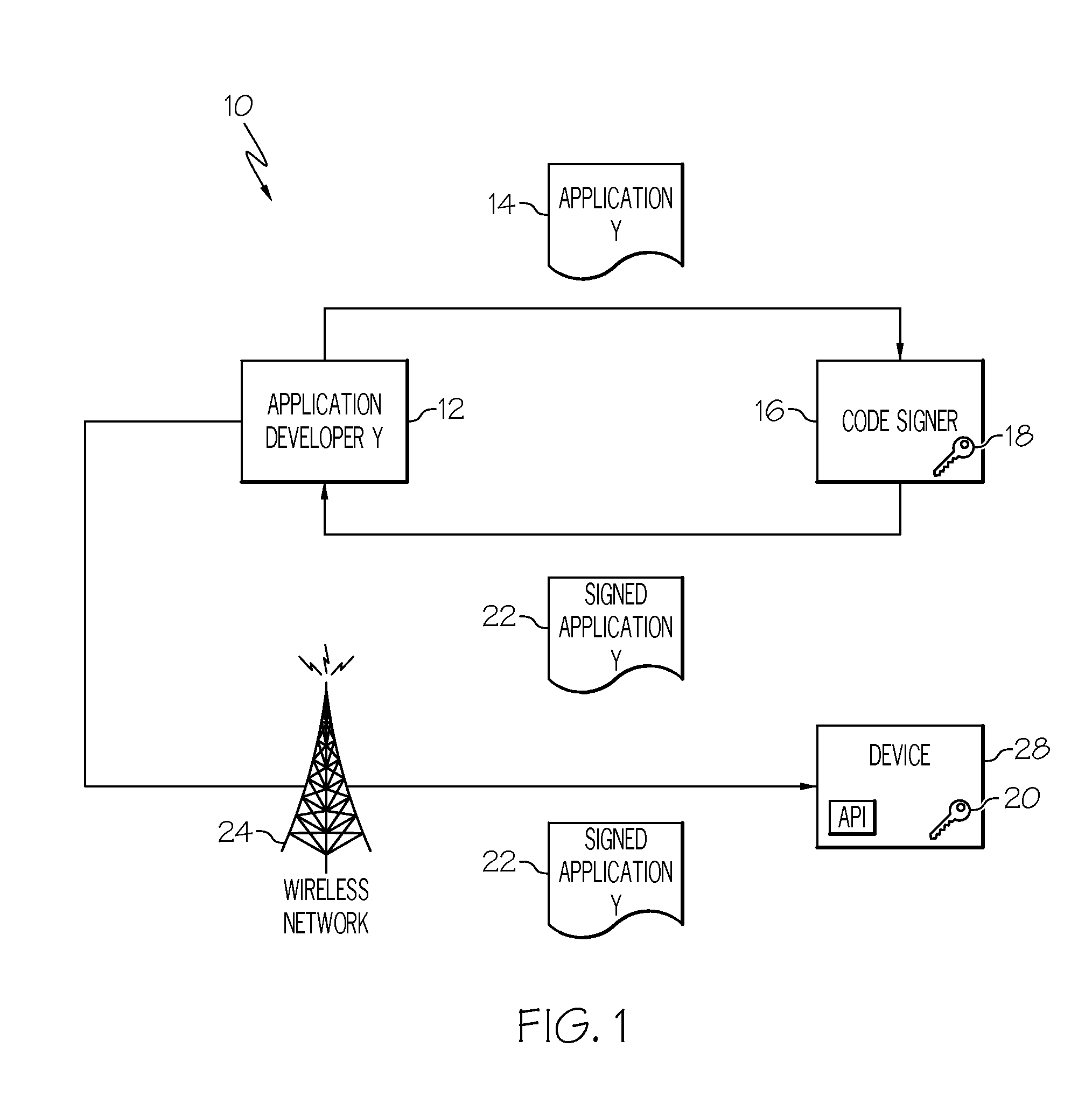
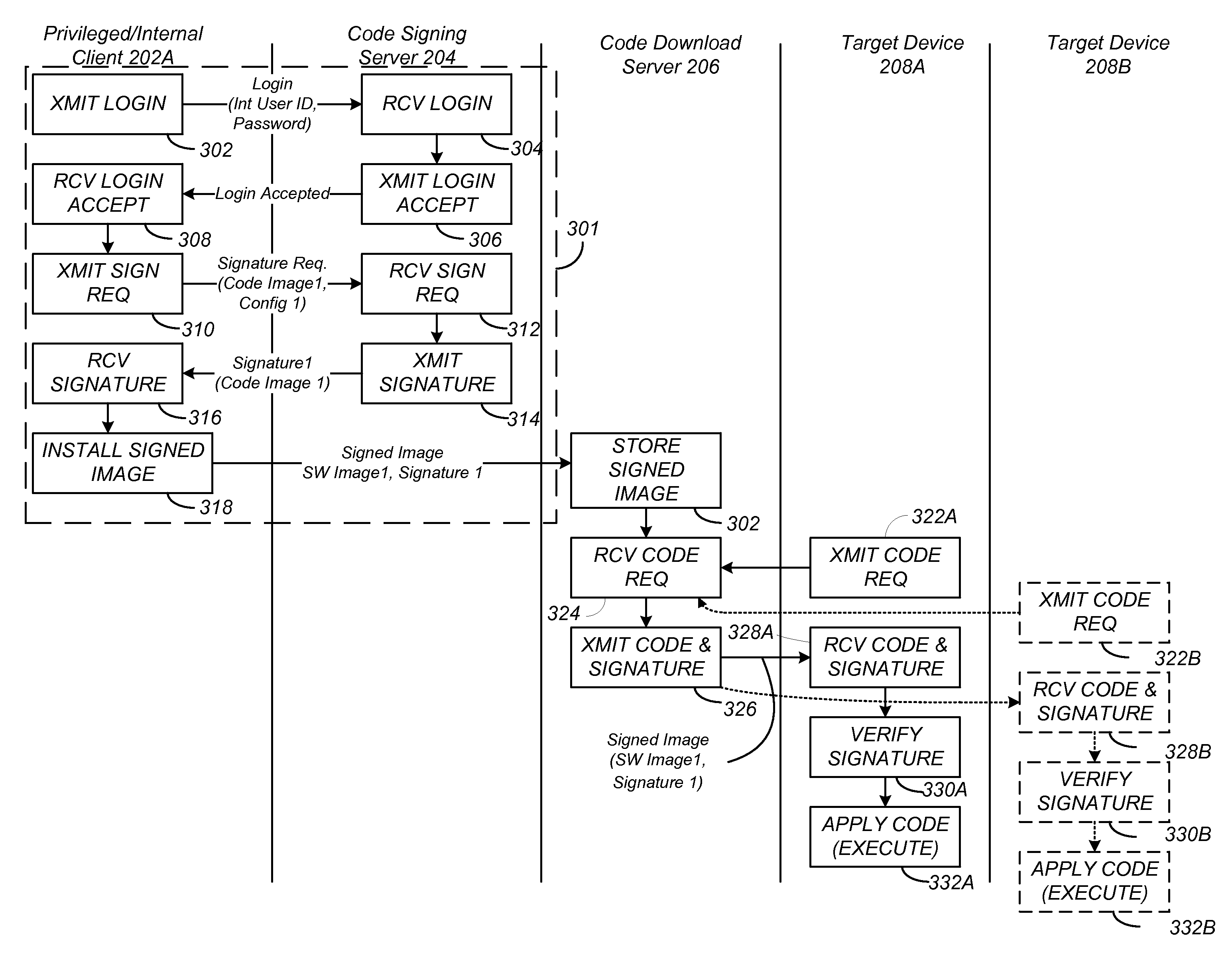
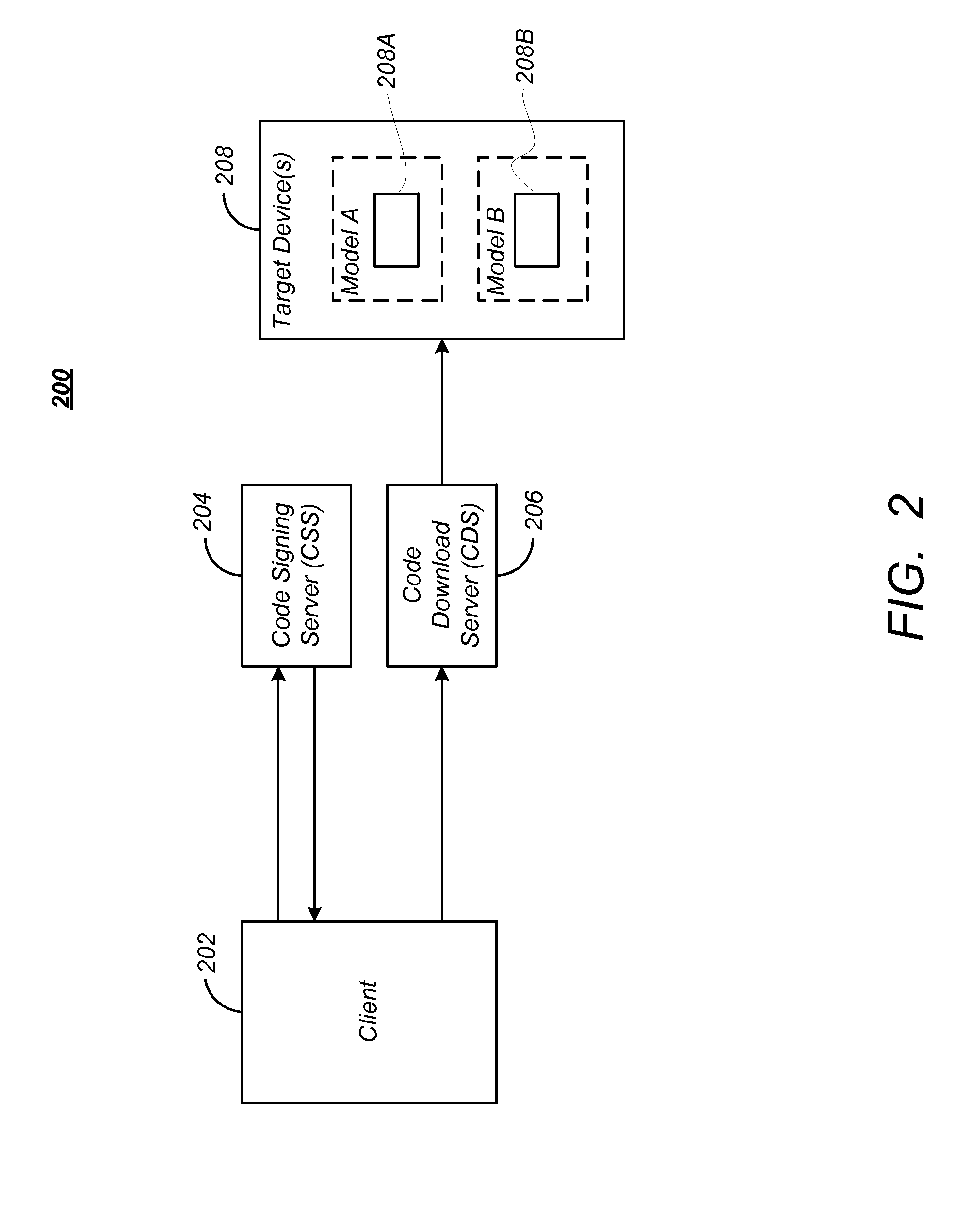
Remote hash generation in a system and method for providing code signing services
InactiveUS20070074032A1User identity/authority verificationComputer security arrangementsCode signingApplication software
A system and method for providing code signing services to software application developers or to other individuals or entities that wish to have applications digitally signed. Signing of the applications may be required in order to enable the applications to access sensitive APIs and associated resources of a computing device when the applications are executed on the computing device. In one embodiment, a hash of an application is generated by a requestor of code signing services. The hash of the application, and not the application itself, may then be received in a code signing request to be digitally signed.
Owner:MALIKIE INNOVATIONS LTD
Safe, secure resource editing for application localization with language fallback
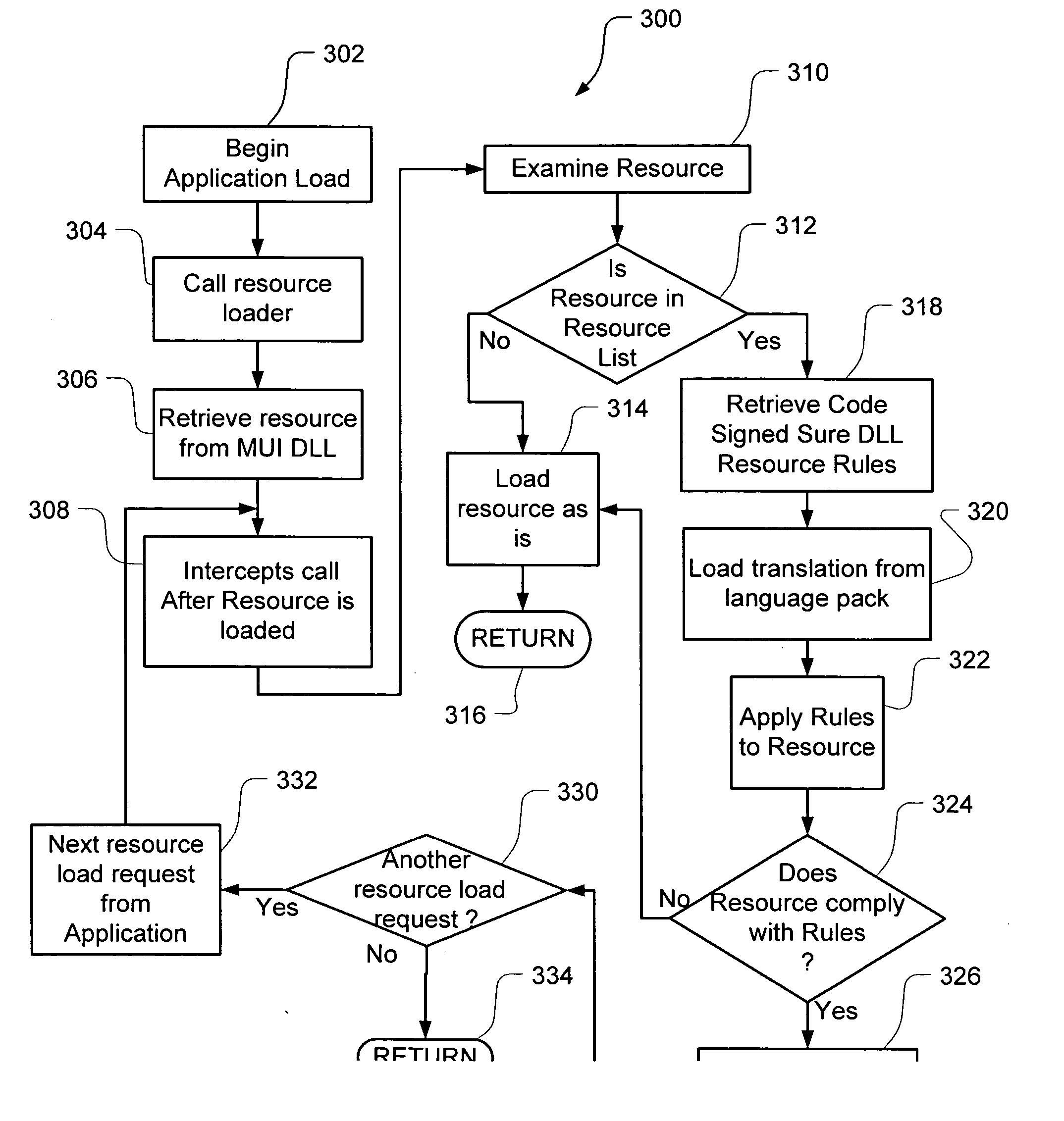
InactiveUS20060130032A1Natural language translationProgram loading/initiatingBasic languageOperational system
Embodiments of the present invention relate to methods, systems and computer-readable media for external localization of a software product. This external localization involves loading a base product having one or more calls to an operating system (or an API) to load language specific data. The calls are intercepted after the resource is loaded into a Resource loader, and queried whether the resource is identified in a restricted resource list such as a code signed dynamic linked library. If so, the translated resource is loaded from a specified language package. The loaded, and translated, resource is then checked against validation rules (which are also protected in a code signed resource list) to see if it is safe to use. If the resource is not on the list or the translated resource is not safe to use, the original resource is simply transferred to the application without modification from the resource loader, i.e., loaded from the base language file. This generates a localized product using a limited set of language specific data covering most situations and falls back to the base language automatically when no specific translated resource is available.
Owner:MICROSOFT TECH LICENSING LLC
Computer implemented method and a computer system to prevent security problems in the use of digital certificates in code signing and a computer program product thereof
ActiveUS20150156024A1Process safetyUser identity/authority verificationComputer security arrangementsSoftware distributionSoftware engineering
A computer implemented method including a software distributor signing via a first server at least one software file using a digital certificate with a digital signature and at least one user via a computing device acquiring a copy of the signed software file. The digital certificate to be used is previously recorded in a second server in communication with the first server, the digital certificate to be recorded being provided by the software distributor upon a registration of the latter in the second server and including information obtained from a trust certificate chain associated to the digital certificate when performing the registration. The second server generates, upon a request made by the software distributor, a hashstamp of the signed software file.
Owner:TELEFONICA CYBERSECURITY TECH SL
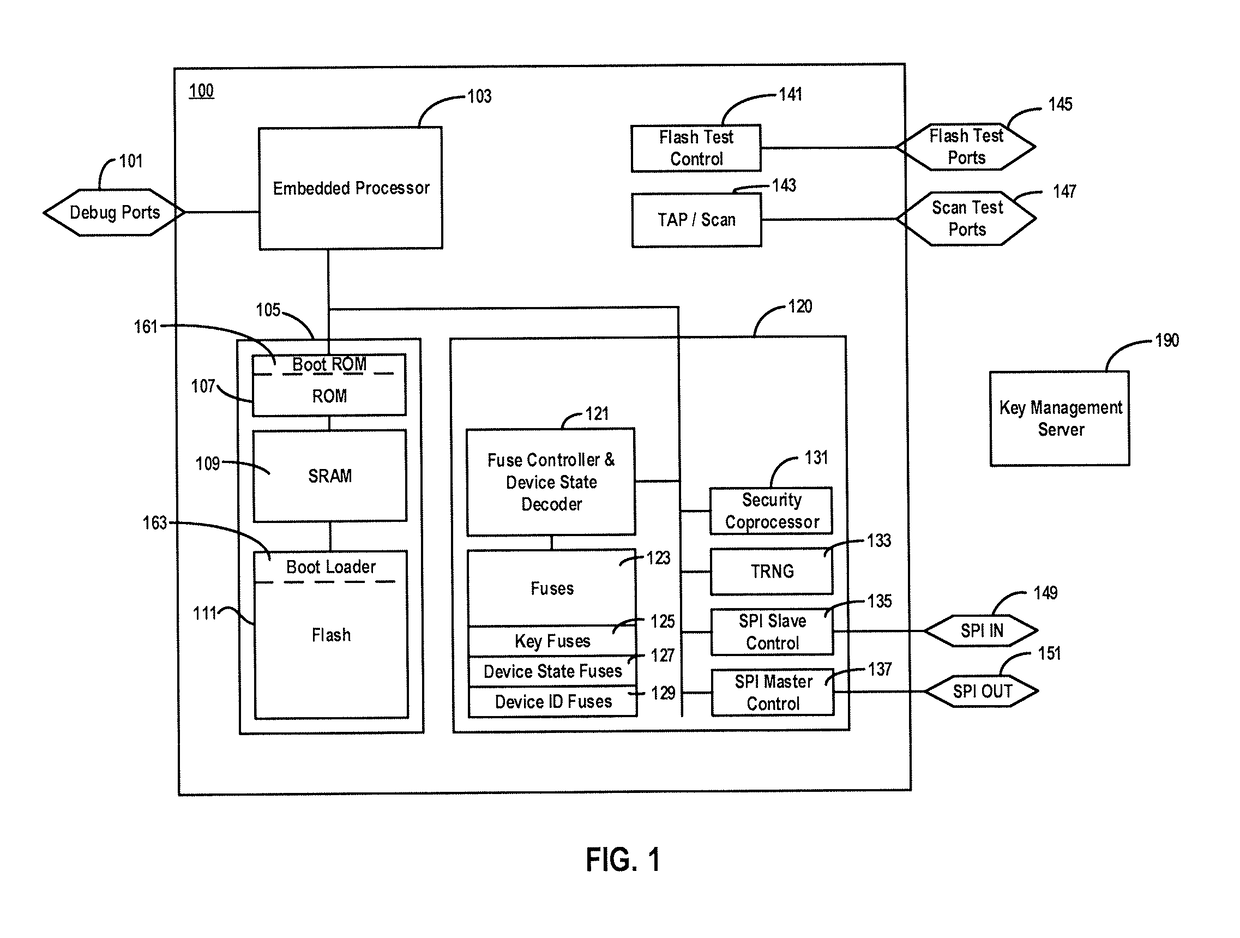
Verification of code signature with flexible constraints
ActiveUS20180241568A1User identity/authority verificationInternal/peripheral component protectionComputer hardwareParallel computing
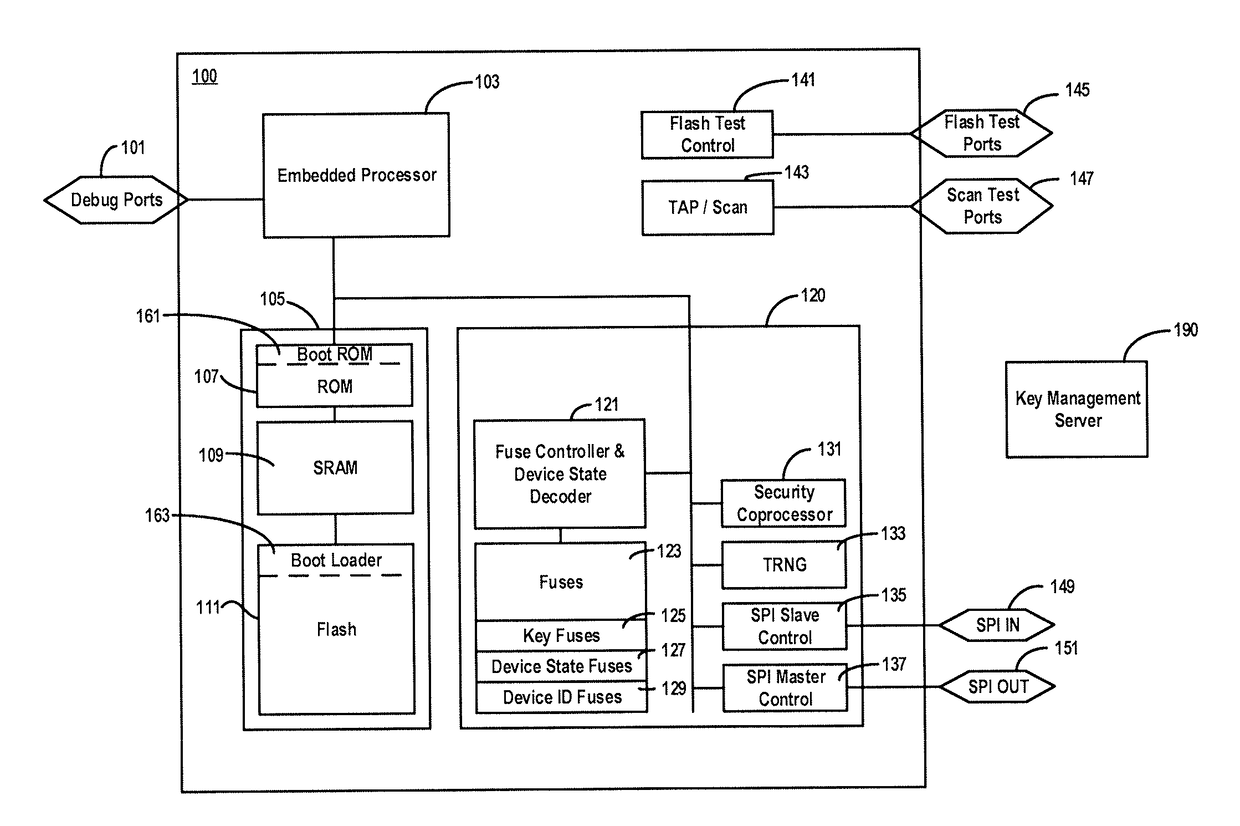
Systems, apparatuses, and methods for signing, and verifying the signature of, code to be executed by a target device. An example method of determining a verification hash of a code image to be executed by a target device comprises receiving a header and code image, determining an image hash based on metadata and the code image, determining a fuses hash based on values of hardware fuses of the target device, determining an information hash based on information stored in memory, determining a verification hash based on the image hash, the fuses hash, and the information hash, verifying the verification hash against a code signature in the header, obtaining an unlock constant based on the verification hash, comparing the unlock constant with a stored predetermined value to unlock a memory region of the target device, and executing the code in the code image on the target device.
Owner:GOOGLE LLC
Code signing system and method
InactiveUS20120179917A1Digital data processing detailsUnauthorized memory use protectionApplication programming interfaceCode signing
A code signing system and method is provided. The code signing system operates in conjunction with a signed software application having a digital signature and includes an application platform, an application programming interface (API), and a virtual machine. The API is configured to link the software application with the application platform. The virtual machine verifies the authenticity of the digital signature in order to control access to the API by the software application.
Owner:BLACKBERRY LTD
Load time bullet proofing for application localization
InactiveUS20060130031A1Natural language translationSpecific program execution arrangementsOperational systemLoad time
Embodiments of the present invention relate to methods, systems and computer-readable media for external localization of a software product. This external localization involves loading a base product having one or more calls to an operating system (or an API) to load language specific data. The calls are intercepted after the resource is loaded into a Resource loader, and queried whether the resource is identified in a restricted resource list such as a code signed dynamic linked library. If so, the translated resource is loaded from a specified language package. The loaded, and translated, resource is then checked against validation rules (which are also protected in a code signed resource list) to see if it is safe to use. If the resource is not on the list or the translated resource is not safe to use, the original resource is simply transferred to the application without modification from the resource loader, i.e., loaded from the base language file. This generates a localized product using a limited set of language specific data covering most situations.
Owner:MICROSOFT TECH LICENSING LLC
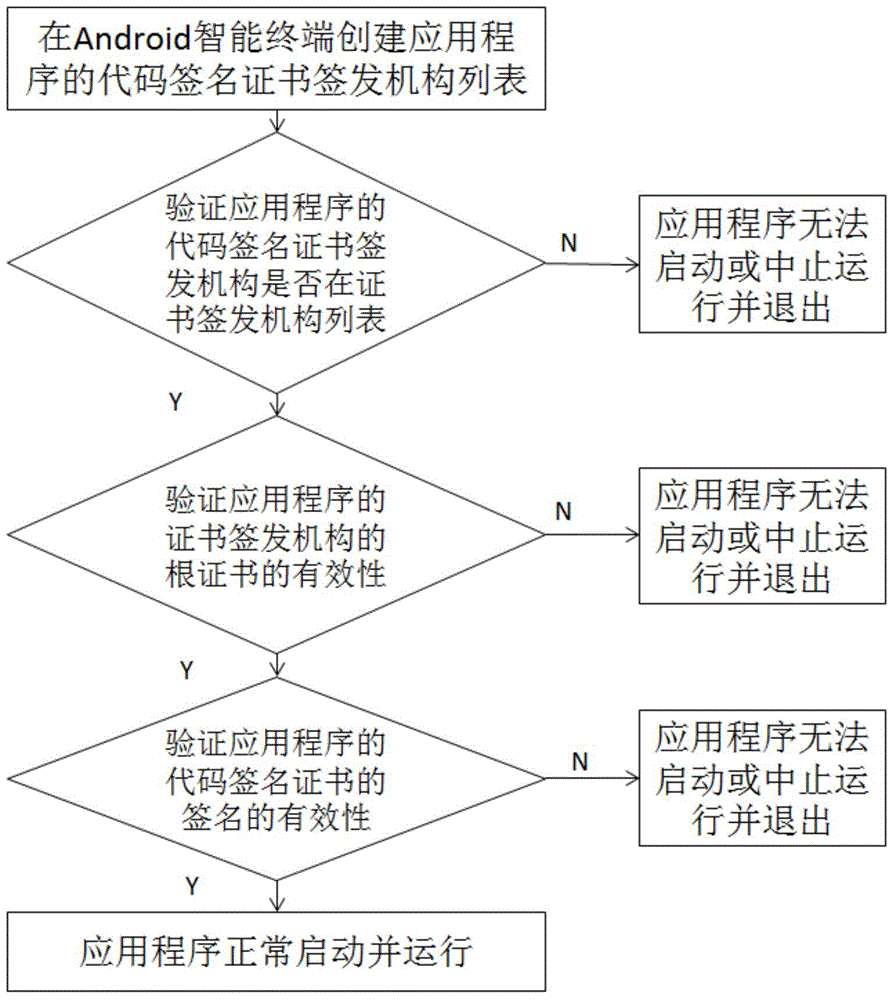
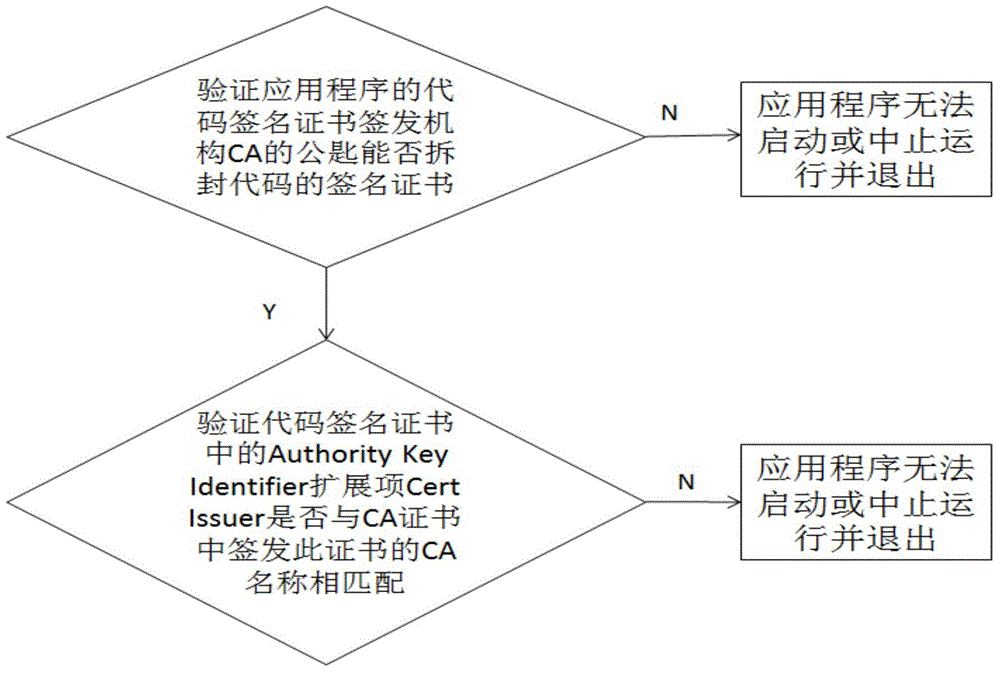
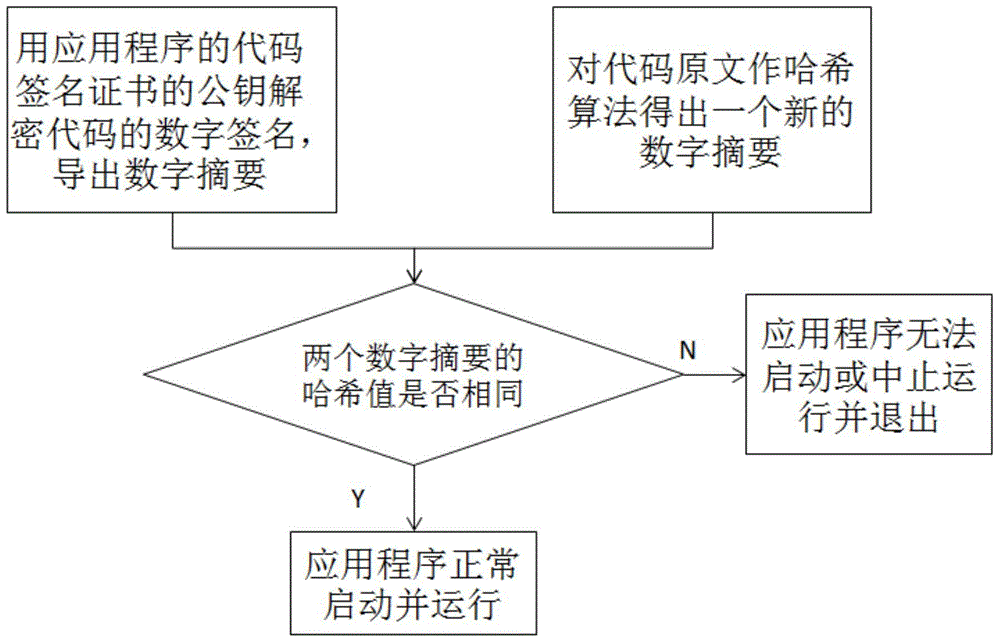
Method and system for verifying code signing during startup of application in Android environment
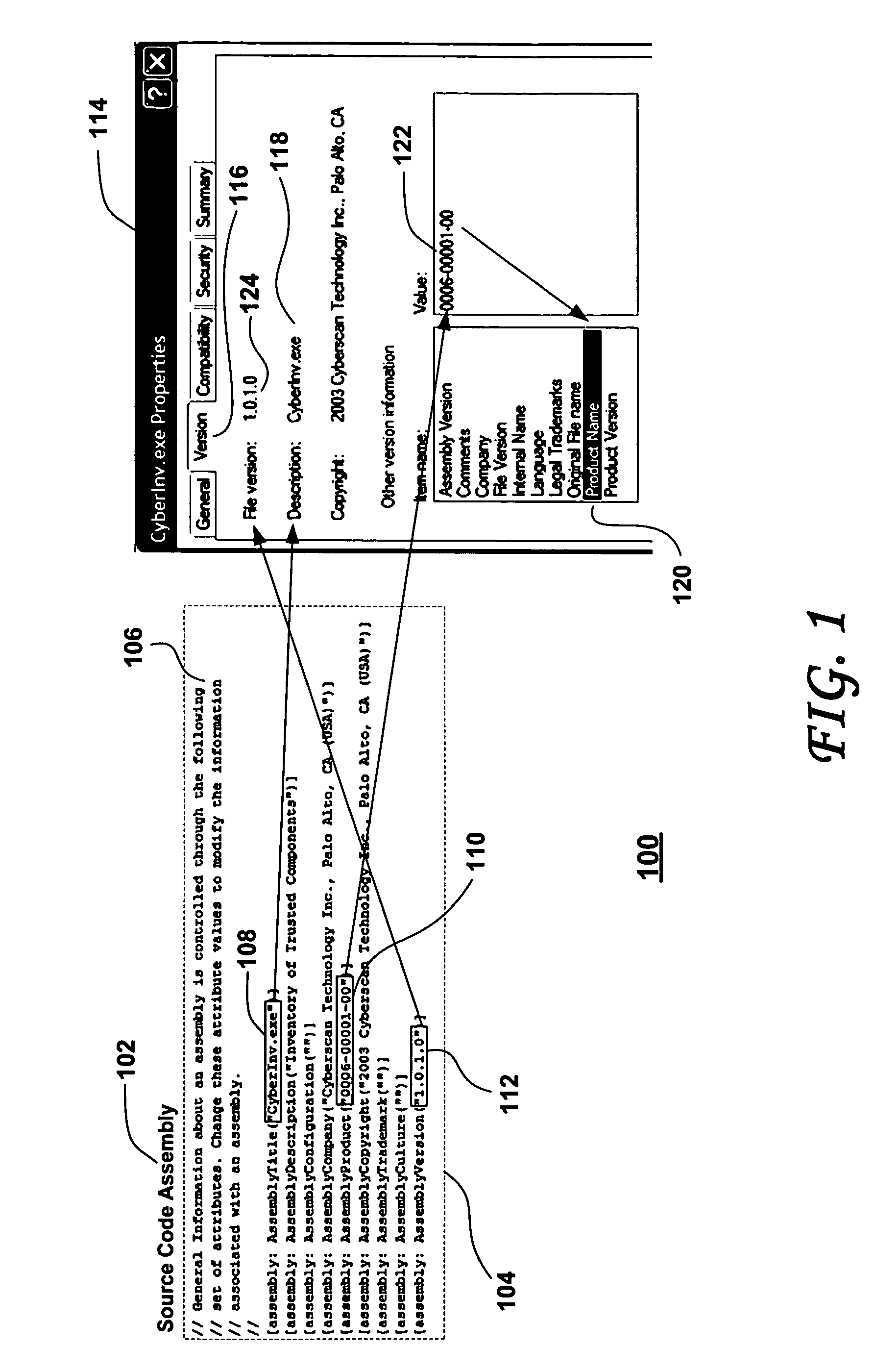
InactiveCN104680061AProtection securityProtect communication securityComputer security arrangementsCode signingApplication software
The invention relates to a method and system for verifying code signing during startup of an application in an Android environment. The method comprises the following steps: creating a code signing certificate issuing institute list of the application on an Android intelligent terminal, wherein one or more credible code signing certificate issuing institutes of the application are stored in the code signing certificate issuing institute list; verifying whether or not the code signing certificate issuing institutes of the application are in the code signing certificate issuing institute list during startup of the application, if not, judging that code signing verification is not passed, and stopping startup of the application or terminating running and exiting, if so, verifying the validity of the code signing certificate issuing institutes of the application, and judging that code signing verification is not passed, and stopping startup of the application or terminating running and exiting if the code signing certificate issuing institutes are invalid; if the code signing certificate issuing institutes are valid, verifying the validity of a code signing certificate sign of the application, normally starting and running the application if the code signing certificate sign is valid, otherwise, stopping startup of the application or terminating running and exiting. By adopting the method and system, attacks to the application in the Android environment can be prevented, and safe startup of the application is ensured.
Owner:GODIN CYBER SPACE SECURITY TECH CO LTD
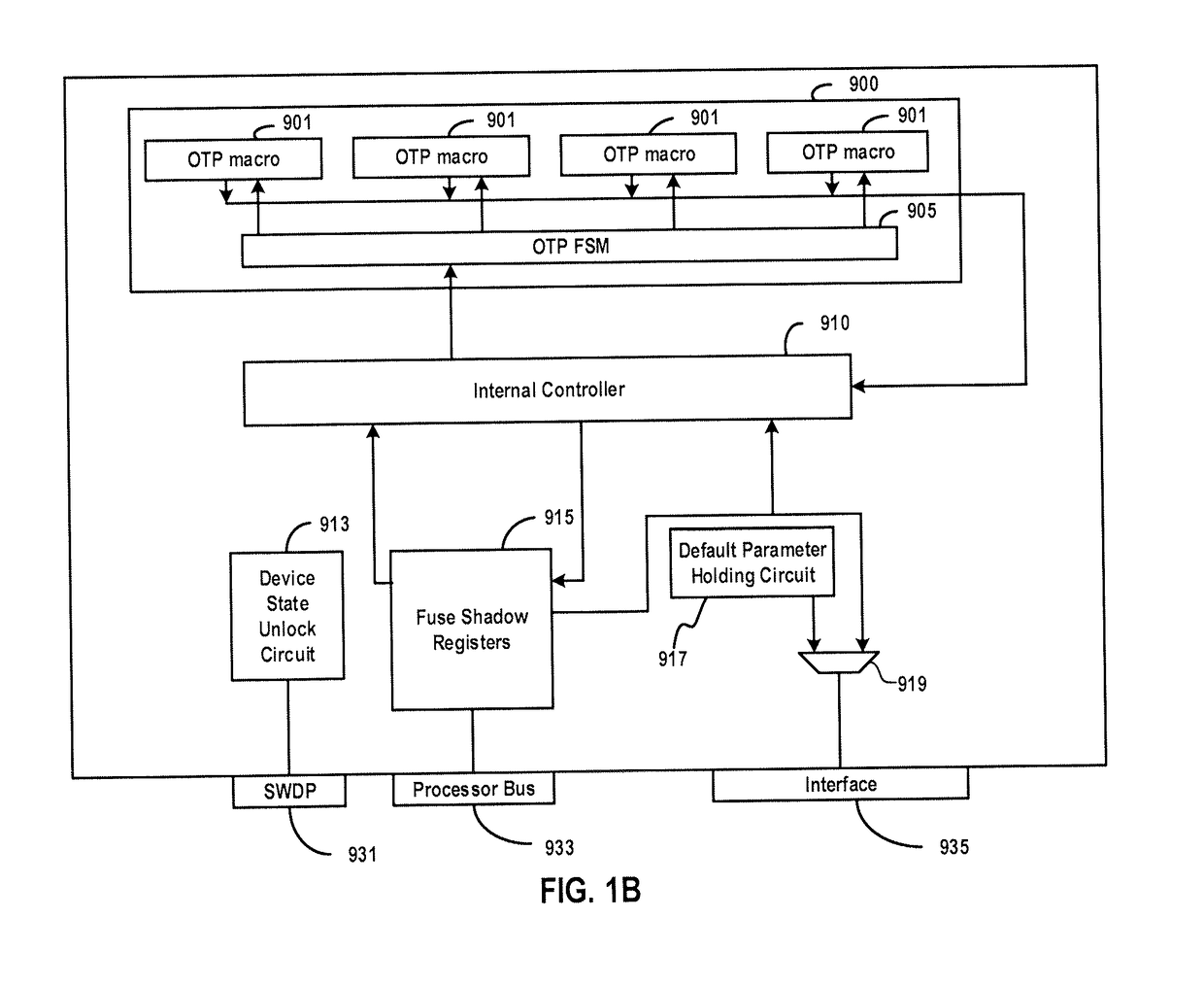
Restricted Code Signing
ActiveUS20150363576A1Digital data processing detailsUser identity/authority verificationSystem configurationCode signing
A method and system is provided for signing data such as code images. In one embodiment, the method comprises receiving, from a requestor, a request to sign the data according to a requested configuration selected from a first configuration, in which the data is for use with any of the set of devices, and a second configuration in which the data is for use only with a subset of a set of devices; modifying the data according to the requested configuration; generating a data signature using the modified data; and transmitting the generated data signature to the requestor. Another embodiment is evidenced by a processor having a memory storing instructions for performing the foregoing operations.
Owner:ARRIS ENTERPRISES LLC
Layered mobile application security system
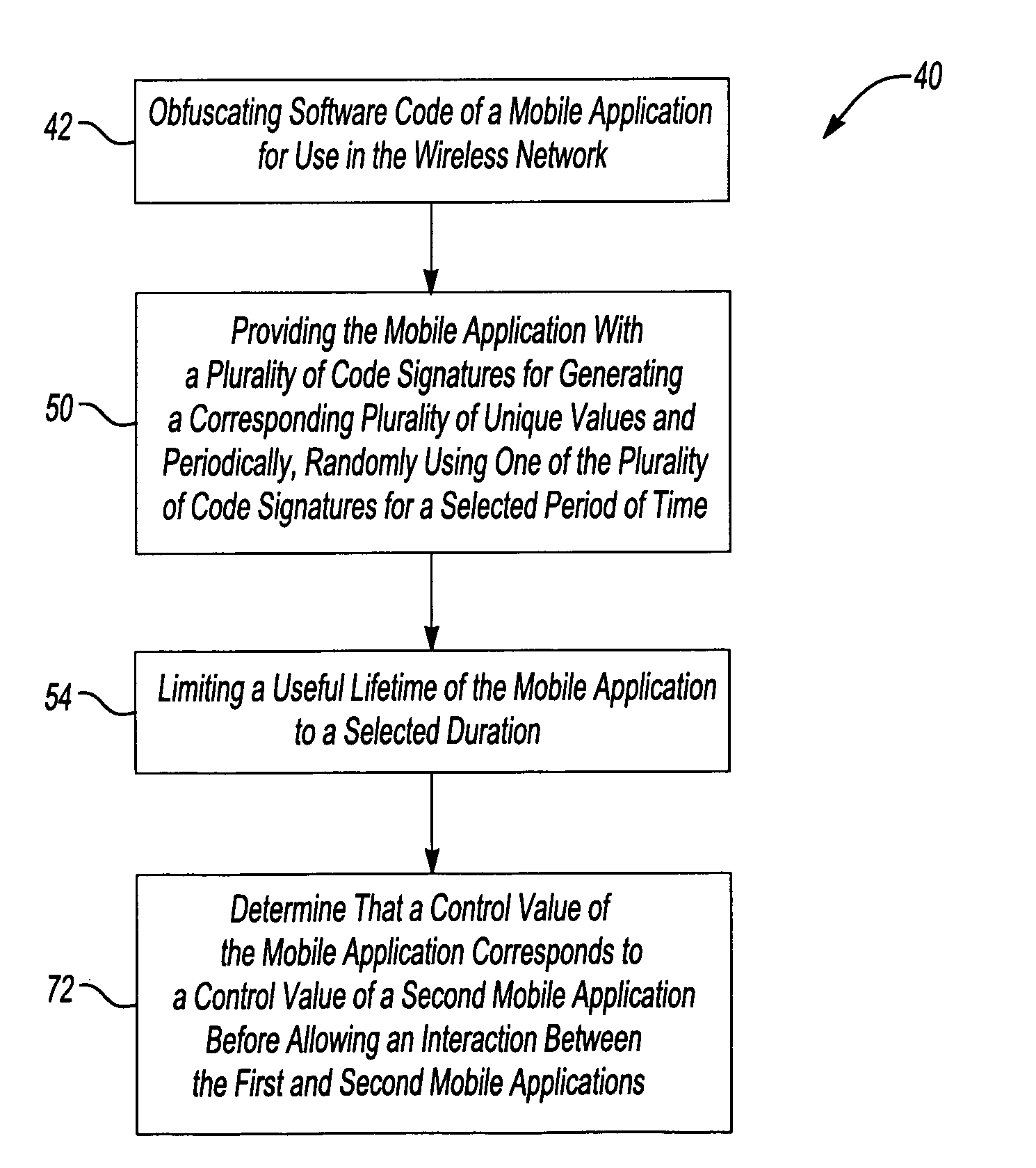
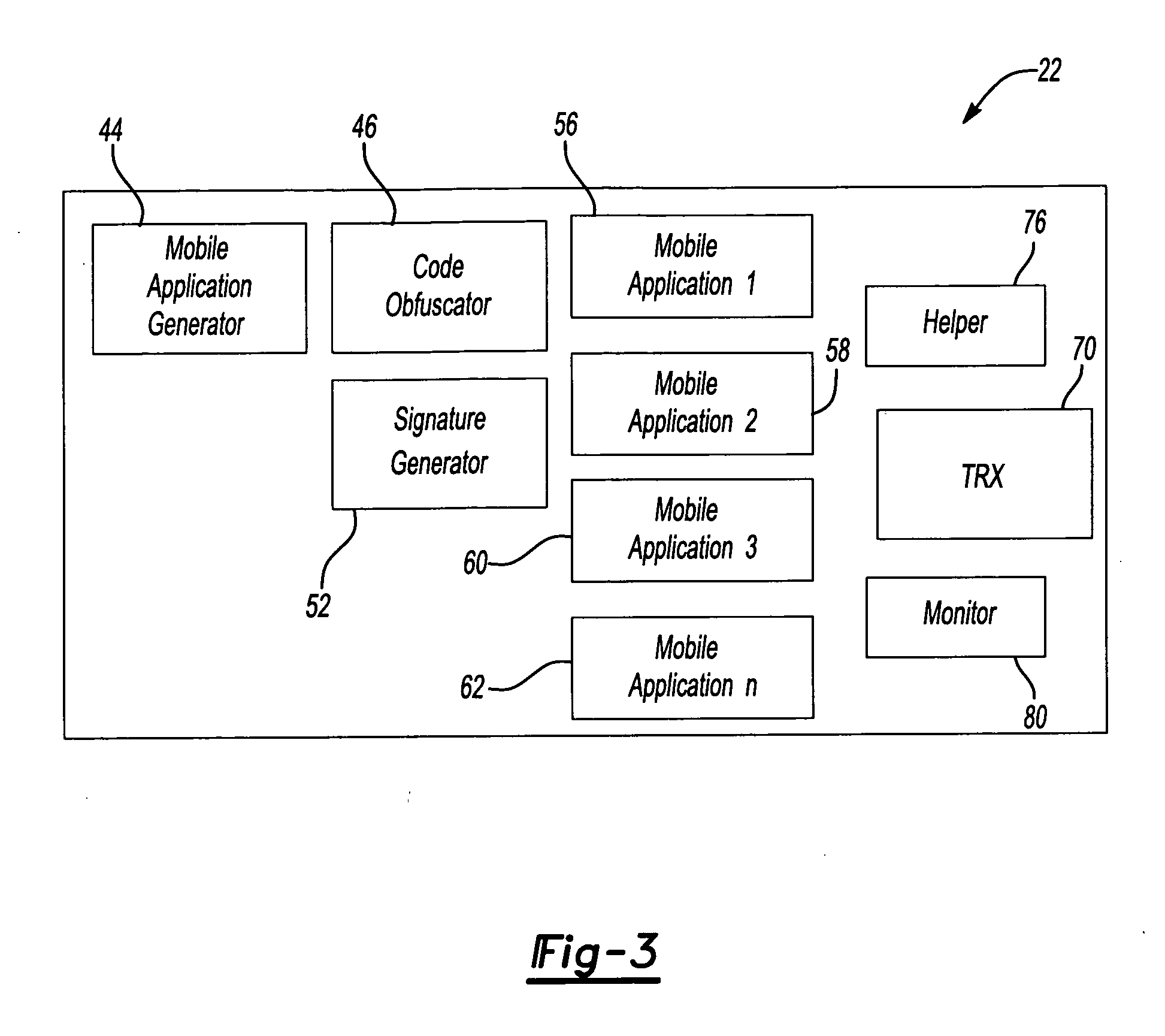
ActiveUS20070135111A1Improve integrityLimit useful lifetimeDigital data processing detailsMultiple digital computer combinationsEngineeringCode signing
A wireless communication network (20) including mobile applications (56-62) includes a security approach that uses a combination of at least two techniques (42, 50, 54, 72). One disclosed example includes a combination of all four techniques. The combined, layered approach greatly reduces the probability that an unauthorized individual will be able to masquerade as a valid application within the network so that network security is improved. Disclosed techniques include obfuscating software code of a mobile application, providing a mobile application with a plurality of code signatures for generating a corresponding plurality of unique control values, limiting the useful lifetime of a mobile application and determining that a control value of a mobile application corresponds to the control value of another application before the two applications are allowed to interact in a manner that could compromise either application or the network.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
System and Method for Enhanced Layer of Security to Protect a File System from Malicious Programs
InactiveUS20080256625A1Minimize successful attacks by malicious programsEnhance layeringDigital data processing detailsUnauthorized memory use protectionFile systemCode signing
A system and method for providing an enhanced layer of security to protect the file system from malicious programs are provided. An additional layer of security for protecting data and to minimize successful attacks by malicious programs is provided. This additional layer uses the feature of code signing to verify that the code is from a source which the code claims to be from, and also that the code has not been tampered with by a malicious party. The file system provides a feature by which certificates are mapped to portions of a file system, e.g., files / directories, such that only programs that are certified by those certificates are able to read / modify those portions of the file system.
Owner:IBM CORP
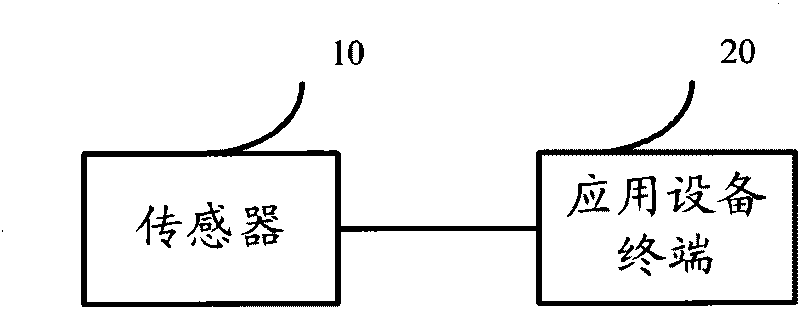
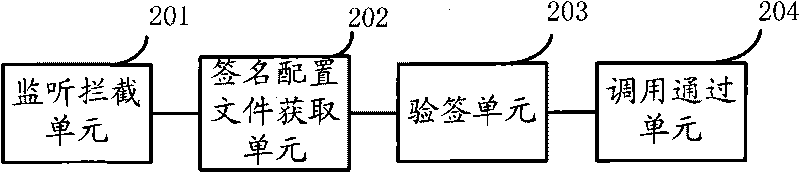
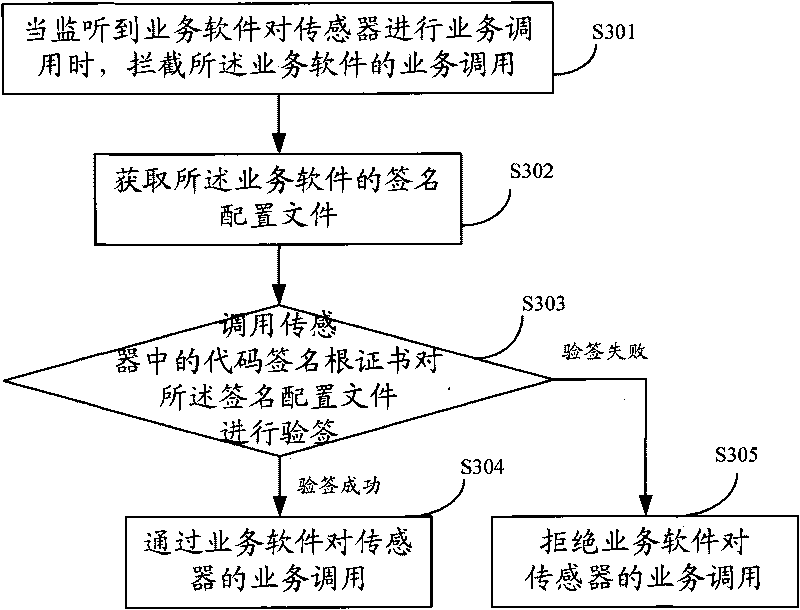
Safety access method for sensor, sensor and safety access system
InactiveCN101729565AImplement secure access managementAvoid safety hazardsUser identity/authority verificationAccess methodCiphertext
The embodiment of the invention discloses a safety access method for a sensor. The method comprises the following steps: when monitoring that service software calls service of the sensor, intercepting the service calling of the service software; acquiring a signature configuration file of the service software, wherein the signature configuration file comprises a program file and a signature ciphertext; calling a code signing certificate in the sensor to authenticate and sign the signature configuration file; and when the signature configuration file is authenticated and signed successfully, calling the service of the sensor through the service software. Correspondingly, the embodiment of the invention also provides a sensor, an application equipment terminal of the sensor and a safety access system. The implementation of the safety access method can realize the safety access management of sensor equipment, and avoids potential safety hazard caused by calling the sensor by various malicious software or a Trojan program.
Owner:卓望数码技术(深圳)有限公司
Generic code signing client with downloadable modules
ActiveUS20200186359A1User identity/authority verificationSoftware deploymentProgramming languageProcess module
A method for signing data such as software images is provided that uses modules executable by a generic client to sign hashes of the software images rather than the images themselves. The method avoids both the requirement for new or updated client software and the uploading of full software images to the signing system. This approach uses a generic client that requests and downloads processing modules from the signing system to perform the pre-processing operations in signing software images, as well as optionally for post-processing operations.
Owner:ARRIS ENTERPRISES LLC
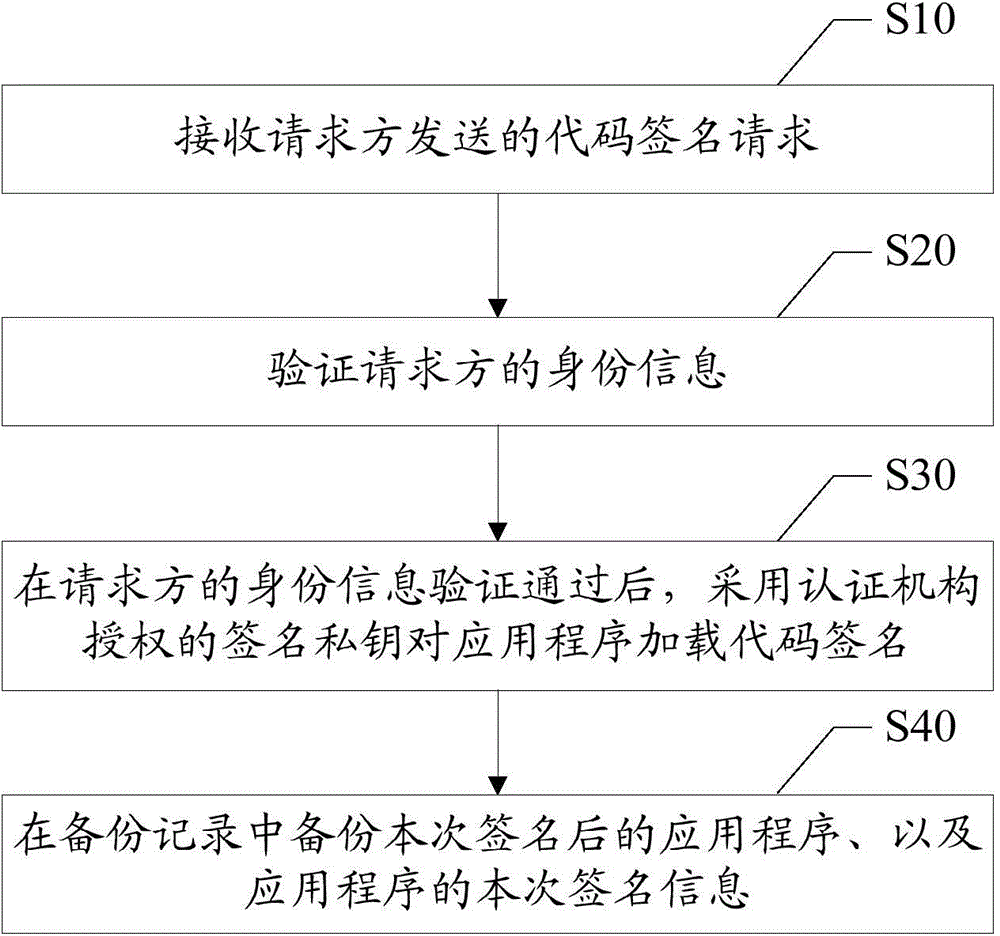
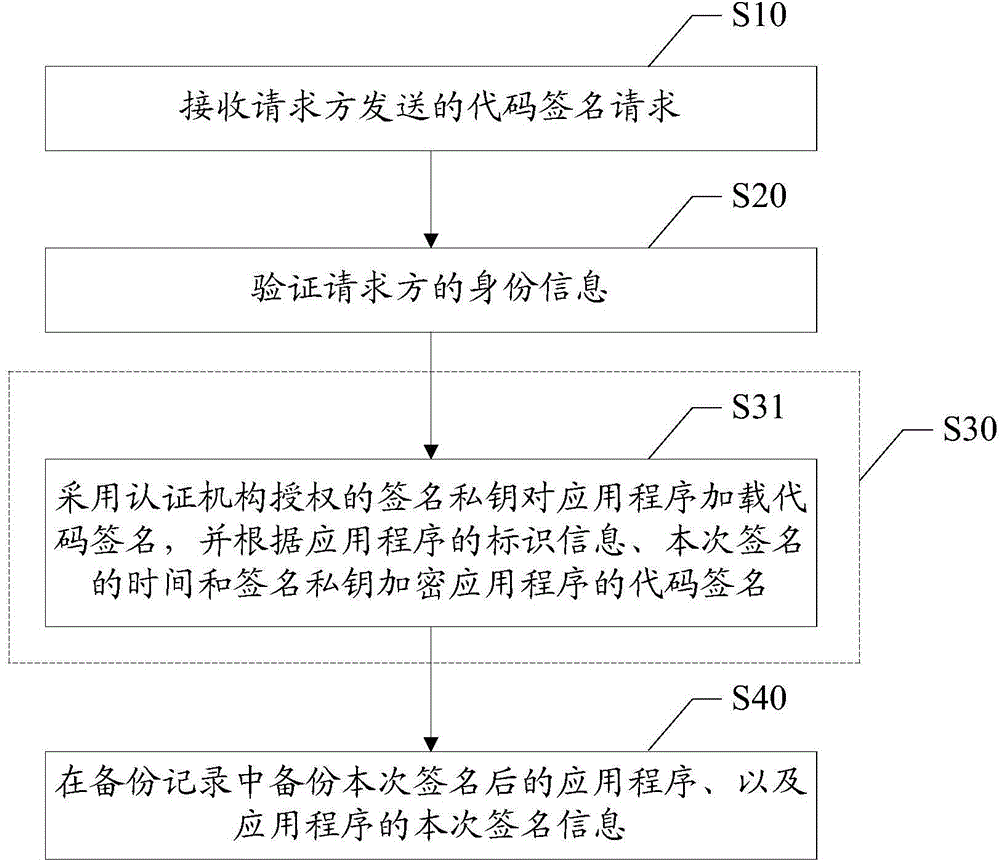
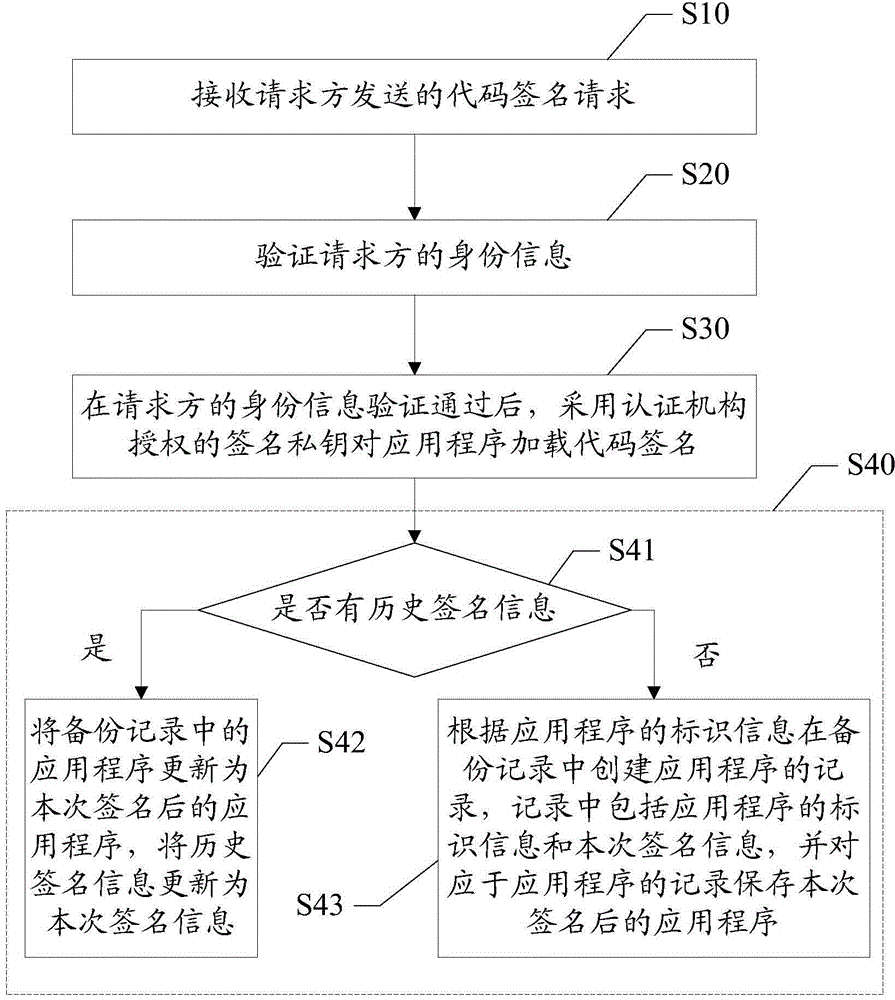
Method and device for loading code signatures to applications
InactiveCN106155663APrevent leakageImprove securityProgram/content distribution protectionSpecific program execution arrangementsCode signingApplication software
The invention discloses a method for loading a code signature to an application. The method includes the steps that a code signature request sent by a requester is received, wherein the code signature request comprises identity information of the requester and the to-be-signed application; the identity information of the requester is verified; after the identity information of the requester passes verification, a signature private key authenticated by a certification mechanism loads the code signature to the application; the application obtained after the signature and signature information of the application are backed up in a backup record. The invention further discloses a device for loading the code signature to the application. The private key authenticated by the certification mechanism is stored in a server, code signatures are loaded to applications needing signatures in a unified mode through the server, the situation that the code signatures are maliciously tampered or stolen by illegal users is avoided, leakage of the private key is avoided, unified management of the code signatures is promoted, the security of the signatures is further improved, and security propagation and use of the applications are guaranteed.
Owner:ZTE CORP
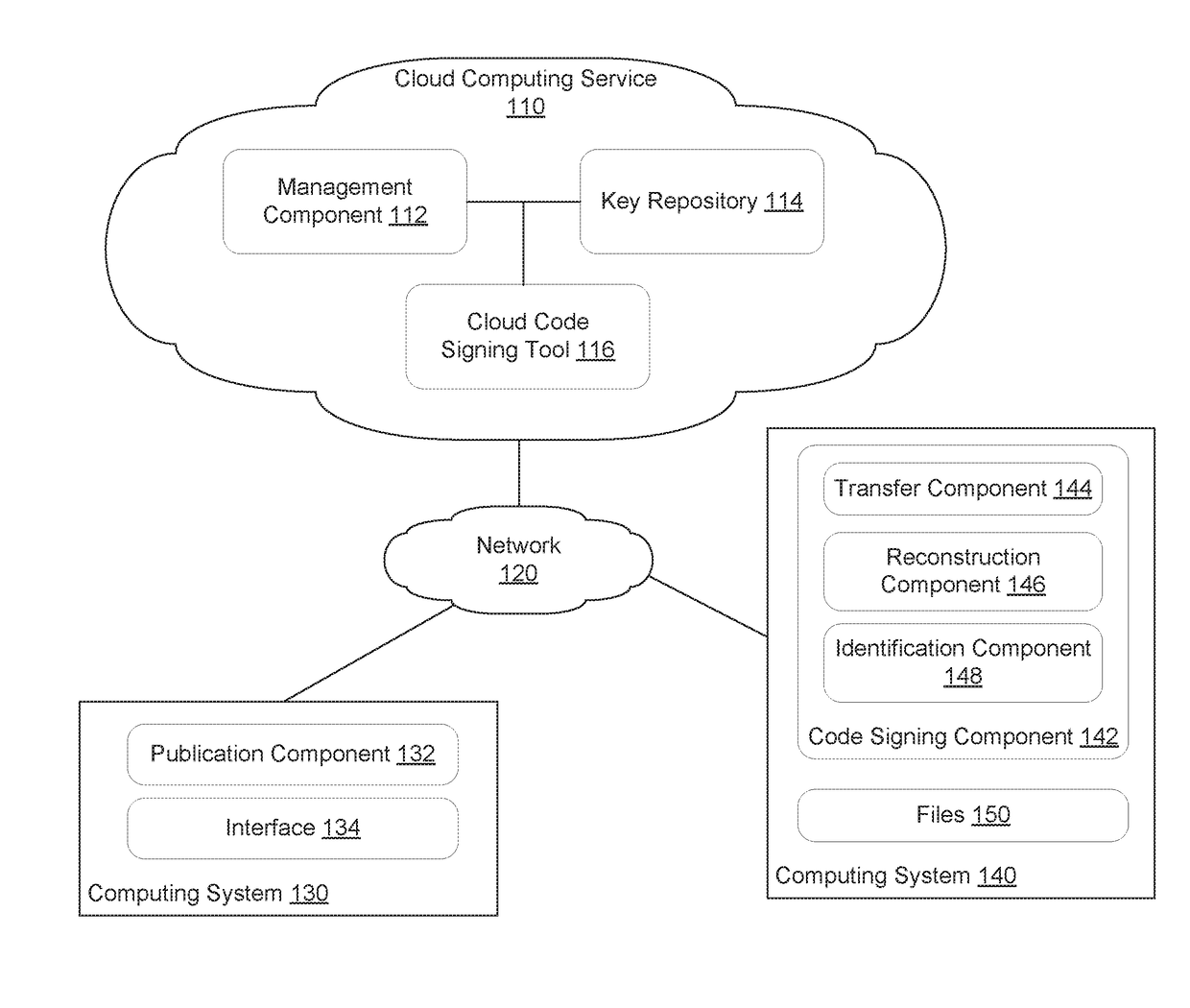
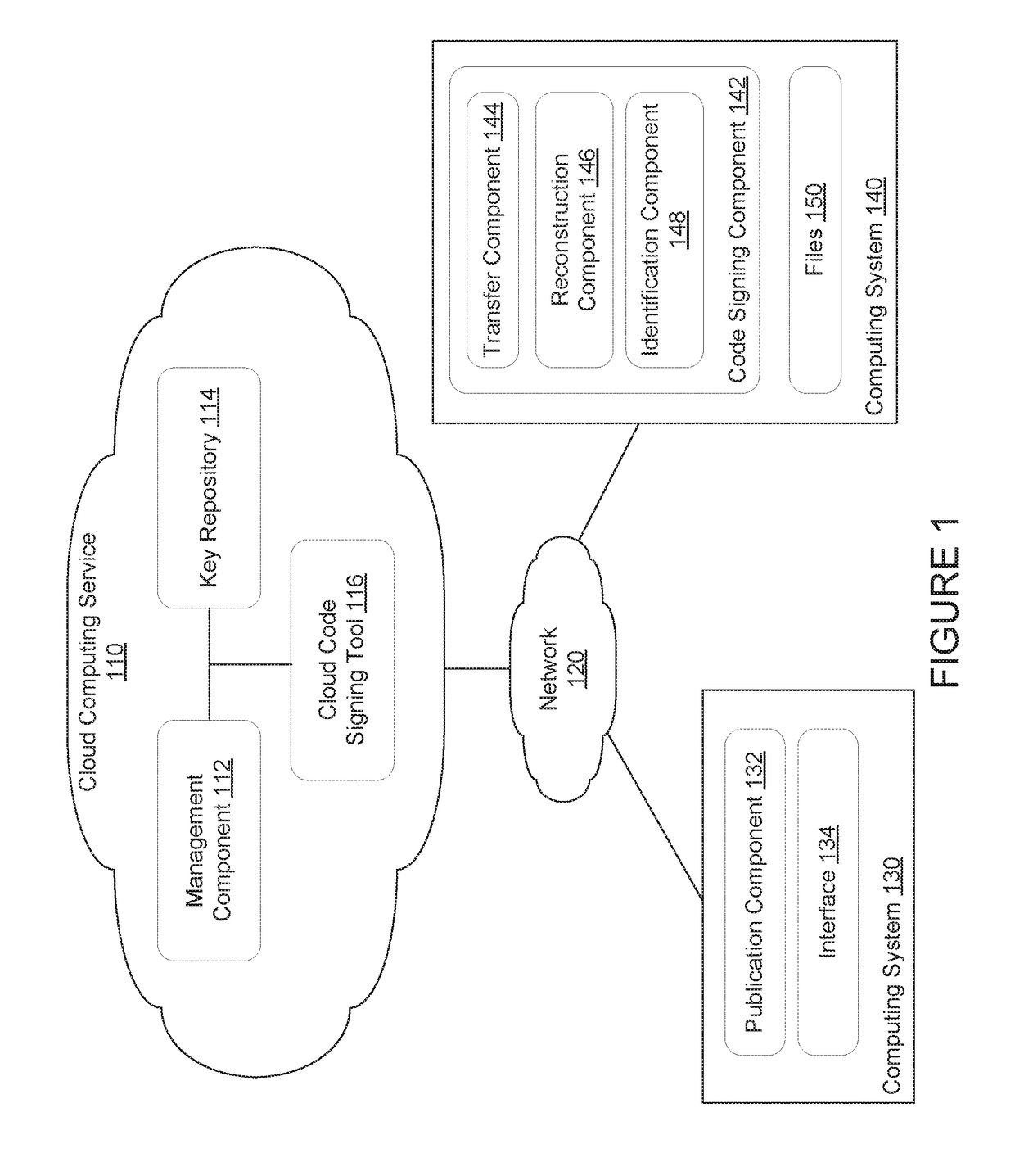
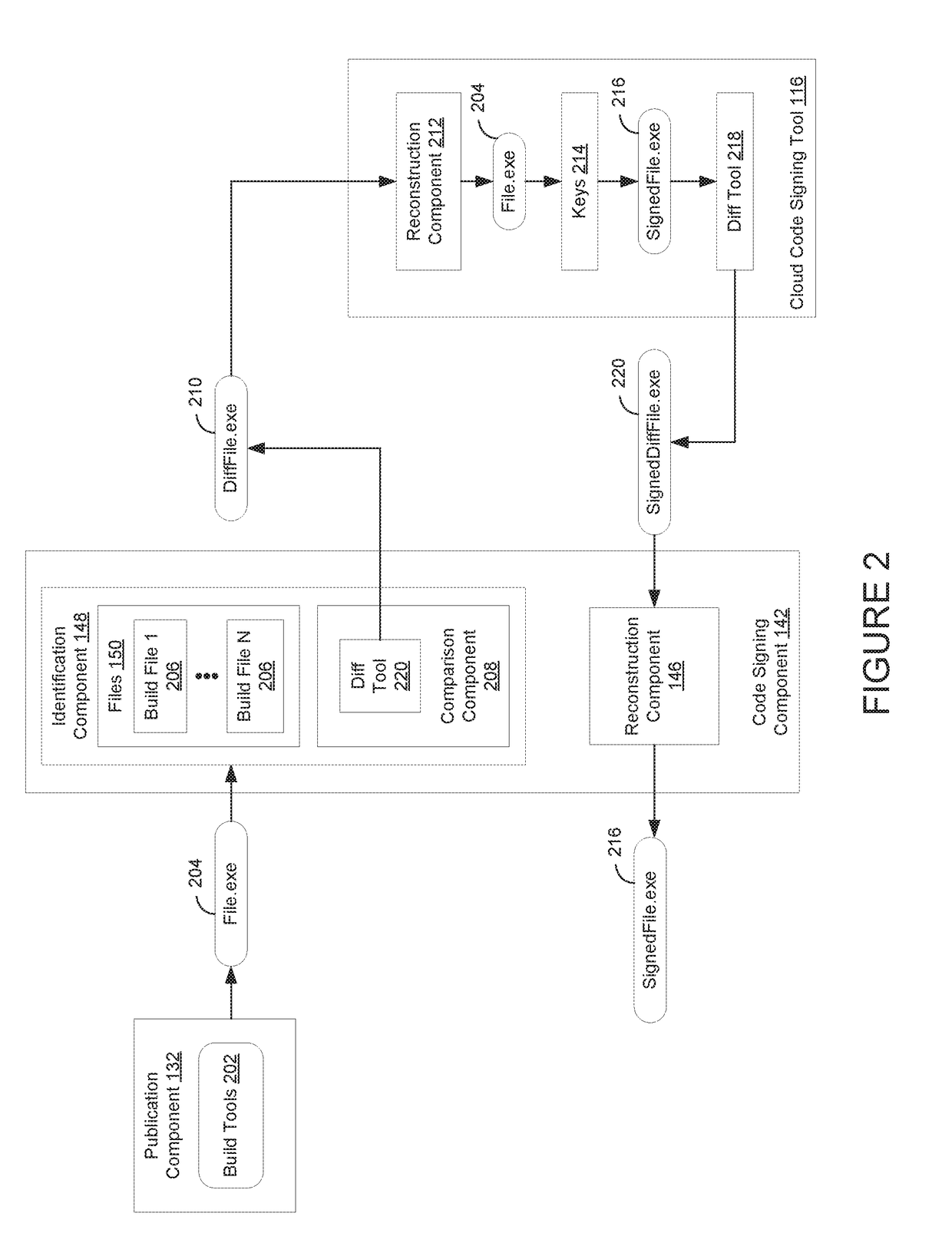
Cloud-based code signing service - hybrid model to avoid large file uploads
ActiveUS20170279615A1Reduce amountUser identity/authority verificationDigital data protectionSignature fileCloud base
Techniques are disclosed for reducing the amount of data associated with code signing files in a cloud-based computing environment. In one embodiment, a cloud-based code signing component receives a request to sign a current version of a file. The request includes differences between the current version of the file and a previous version of the file. The cloud-based code signing component reconstructs the current version of the file based on the differences between the current version of the file and the previous version of the file. The cloud-based code signing component signs the reconstructed file, and determines differences between the signed file and the reconstructed file. The cloud-based code signing component transfers the differences between the signed file and the reconstructed file to a user.
Owner:DIGICERT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com