Secure guiding system, method, code signature construction method and authentication method
A technology for secure boot and secure system, applied in the field of secure boot system, can solve the problem that elliptic curve cryptography technology is not well applied, and achieve the effects of simplifying key management, protecting operating system security, and preventing user loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
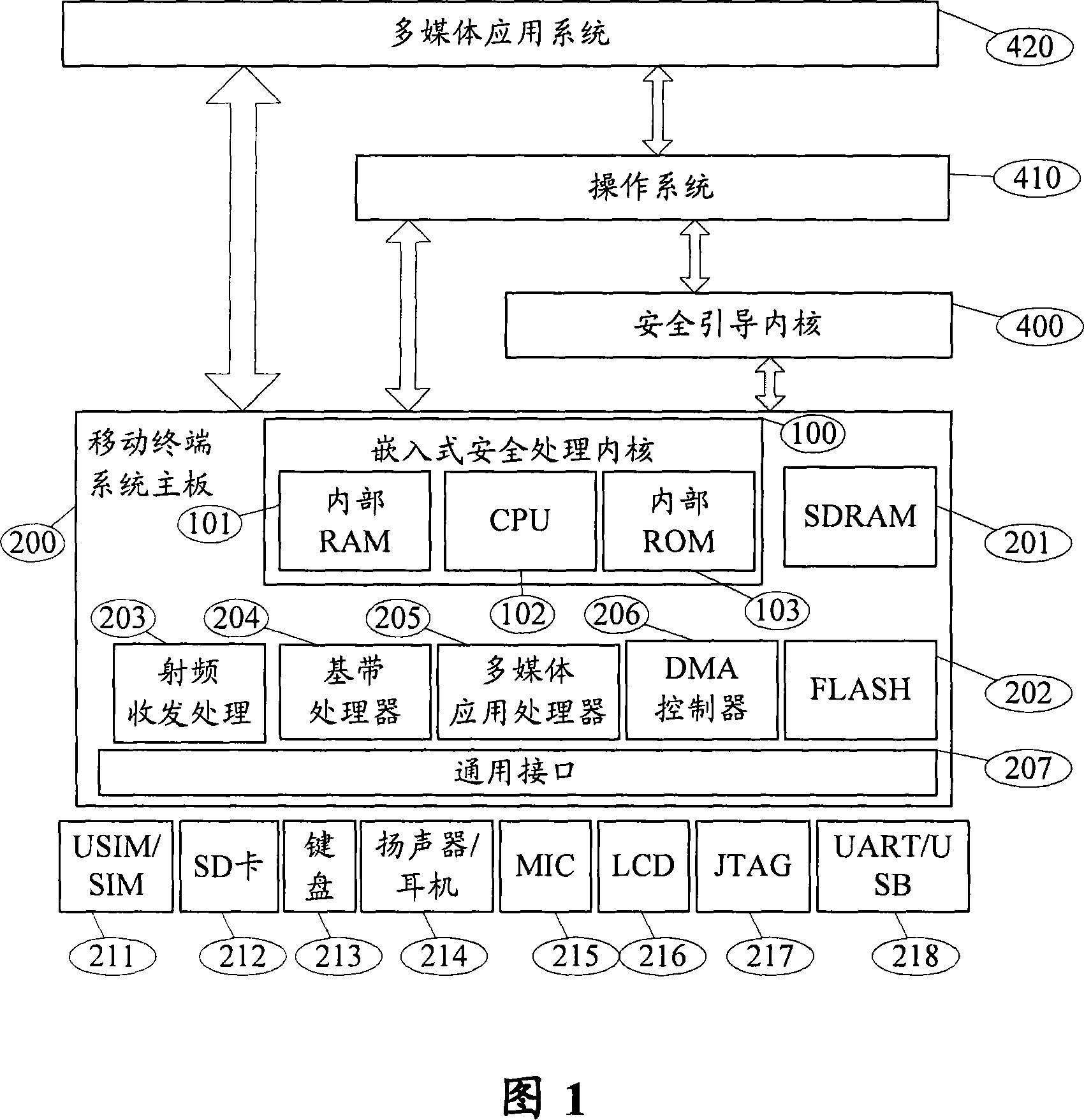
[0038] As shown in Figure 1, the secure boot system of the mobile terminal according to the first embodiment of the present invention mainly includes: a secure processing kernel (preferably, may be an embedded secure processing kernel) 100, including a CPU 102, a RAM 101, and a ROM ( Internal flash) 103 is used to establish a safe boot program, and complete the authentication process to the operating system software image file or application system software image file based on elliptic curve cryptography; the safe operating system 410 is connected with the safe processing kernel, including multimedia applications The processor 205, the baseband processor 204, and the external interface device general interface 207 are used to execute a hardware initialization function.
[0039]In addition, the security guidance system at least includes: a radio frequency signal transceiving module, a baseband signal processing module, a multimedia processor, a terminal flash memory 202, and a g...
no. 2 example
[0047] According to the second embodiment of the present invention, based on the secure boot system of the mobile terminal in the first embodiment, a code signature construction method is provided.
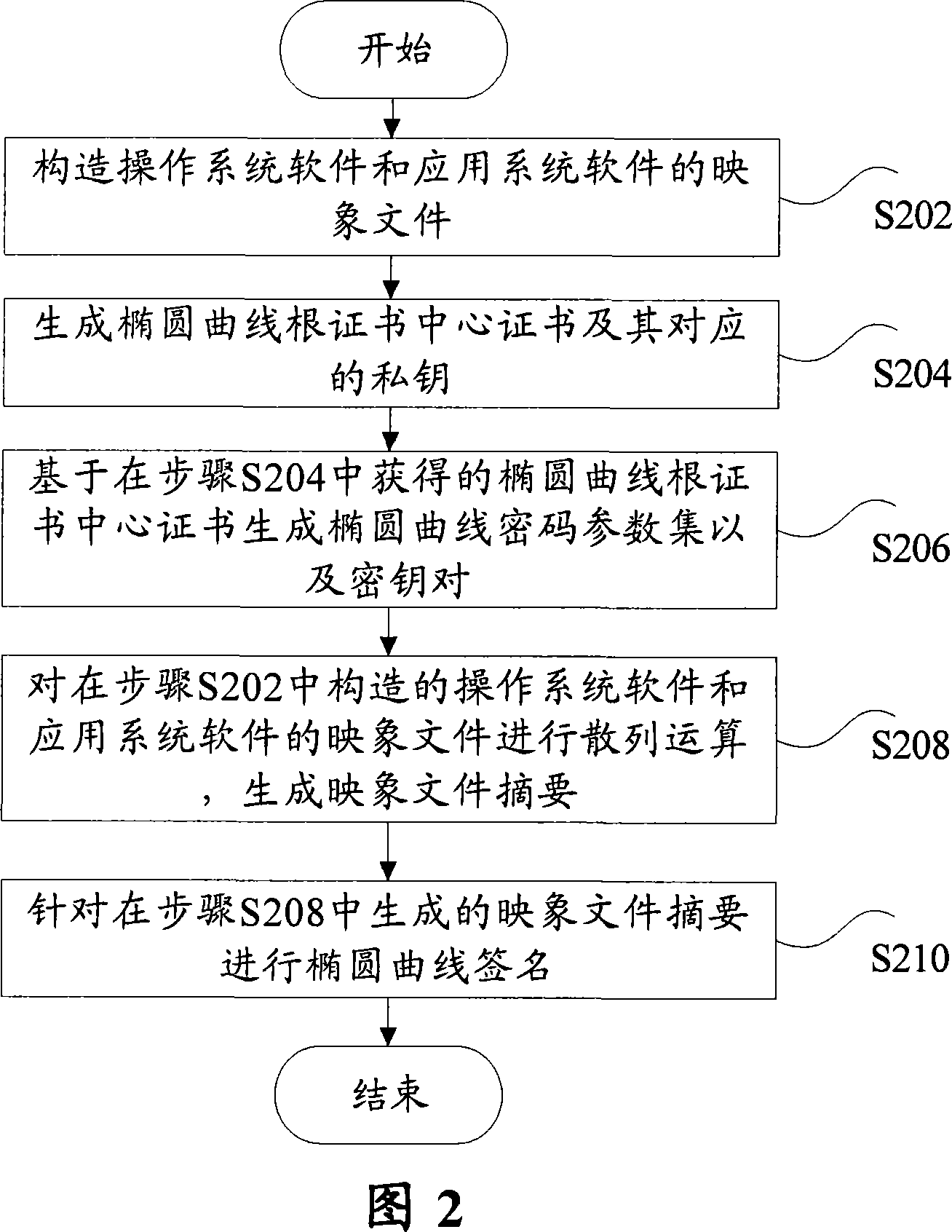
[0048] As shown in Figure 2, the method includes the following steps: Step S202, constructing the image file of operating system software and application system software; Step S204, generating the elliptic curve root certificate center certificate and its corresponding private key; Step S206, based on the The elliptic curve root certificate authority certificate obtained in step S204 generates an elliptic curve cipher parameter set and a key pair; step S208, performs a hash operation on the image files of the operating system software and application system software constructed in step S202 to generate a map Image file digest; and step S210, perform elliptic curve signature on the image file digest generated in step S208.
[0049] Wherein, in step S208, a hash function is used for...
no. 3 example
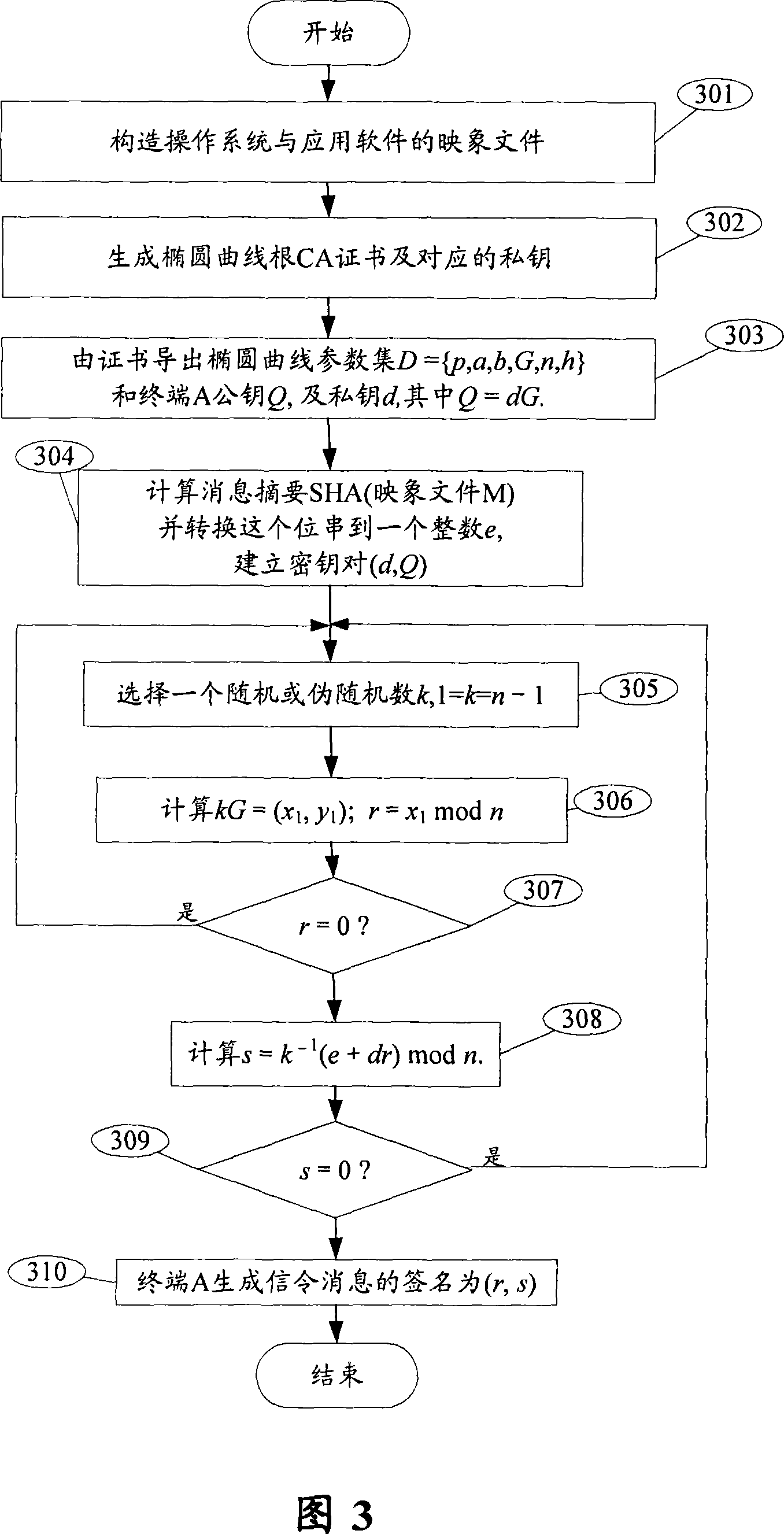
[0062] According to the third embodiment of the present invention, based on the secure boot system of the first embodiment, a code signature authentication method is provided.
[0063] As shown in Figure 4, the method includes the following steps: step S402, securely process the kernel boot program based on the elliptic curve root certificate authority certificate, and obtain a public elliptic curve parameter set and related public keys; step S404, securely process the kernel boot program to verify the image Whether the signature of the file exceeds the scope of the elliptic curve base point group order; wherein, in the case of no verification result, proceed to step S406; step S406, generate the message digest of the image file; step S408, calculate w=s-1 respectively mod n, u1=ew mod n, u2=rw modn, and X=u1G+u2Q=values of (x1, y1); step S410, verify the code signature according to the value of the abscissa of X calculated in step S408.
[0064] Wherein, in step S410, when ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com