Personal information encryption method in logistics system based on two-dimensional codes
A technology of logistics system and private information, applied in the direction of logistics, public key of secure communication, record carrier used by machines, etc. It can solve the problems of confidentiality of customer information and protection of customer information, and achieve the effect of ensuring information and flexible application.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
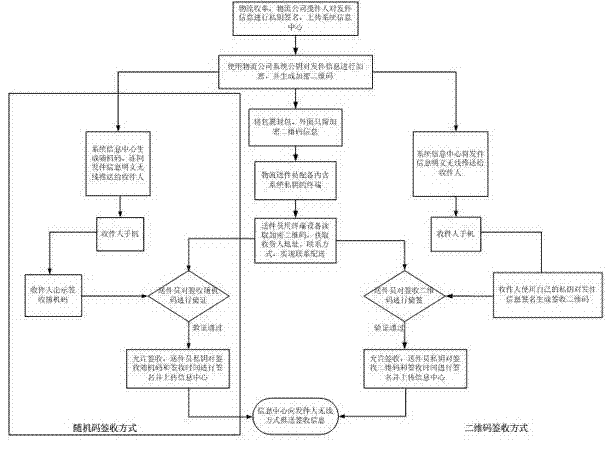
Image
Examples
Embodiment Construction
[0036] Before introducing the embodiments of the present invention in detail, let us first understand the identification authentication technology: the identification-based authentication technology does not need to exchange keys, nor does it require the participation of a trusted third party (even if necessary, the third party generally It is only used to issue a smart card to a user who participates in the system for the first time with the information required for the user's signature and encryption). The key management algorithm uses the elliptic curve cryptography theory to construct public and private key matrices, which can generate a large number of public and private key pairs with a small number of factors; use the user's identity information (ID number, ID number and other unique information) as an identifier, use The mapping algorithm binds the user ID to the public and private key variables, and solves the problem of key management based on ID. Ability to support ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com