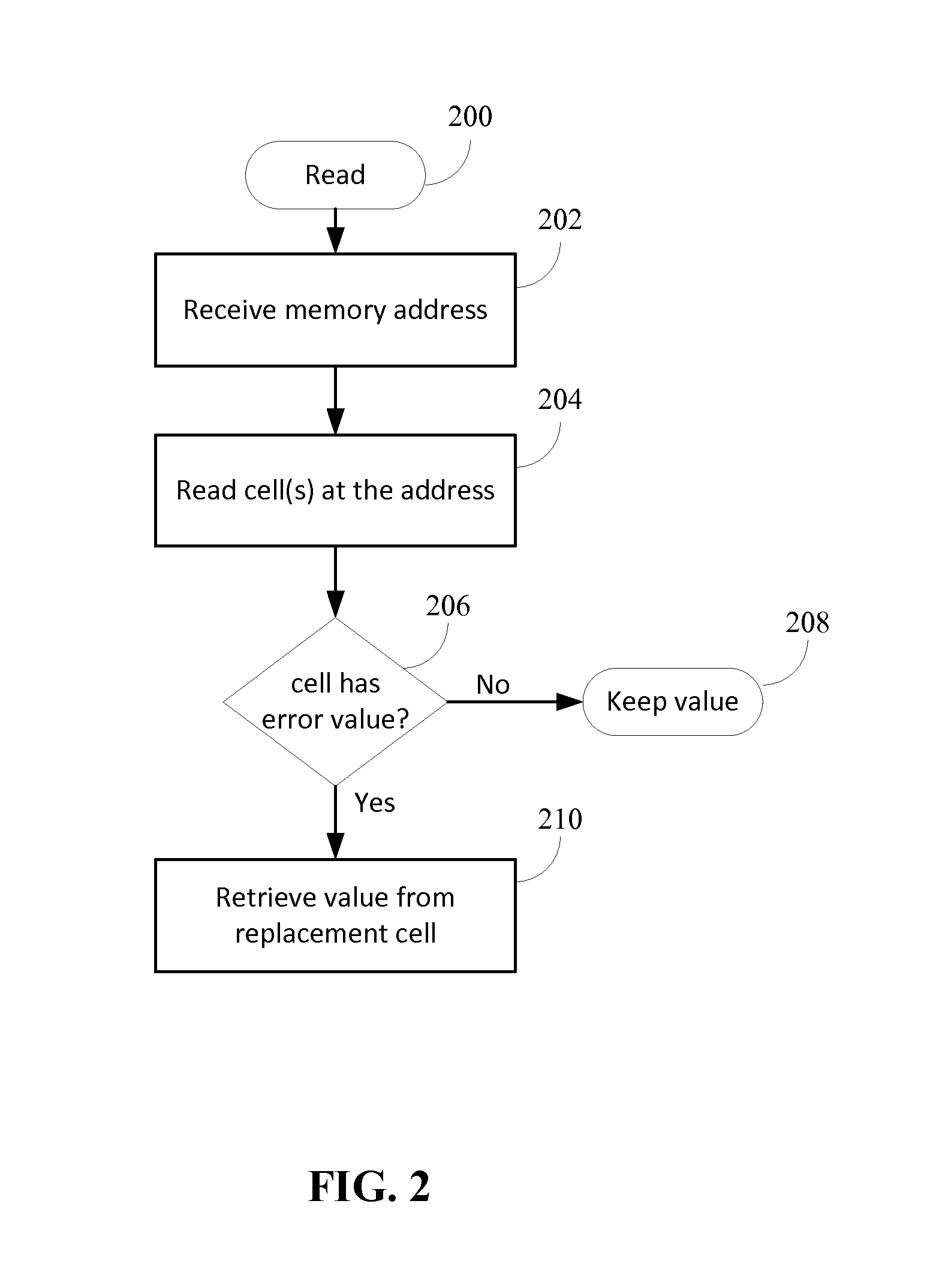
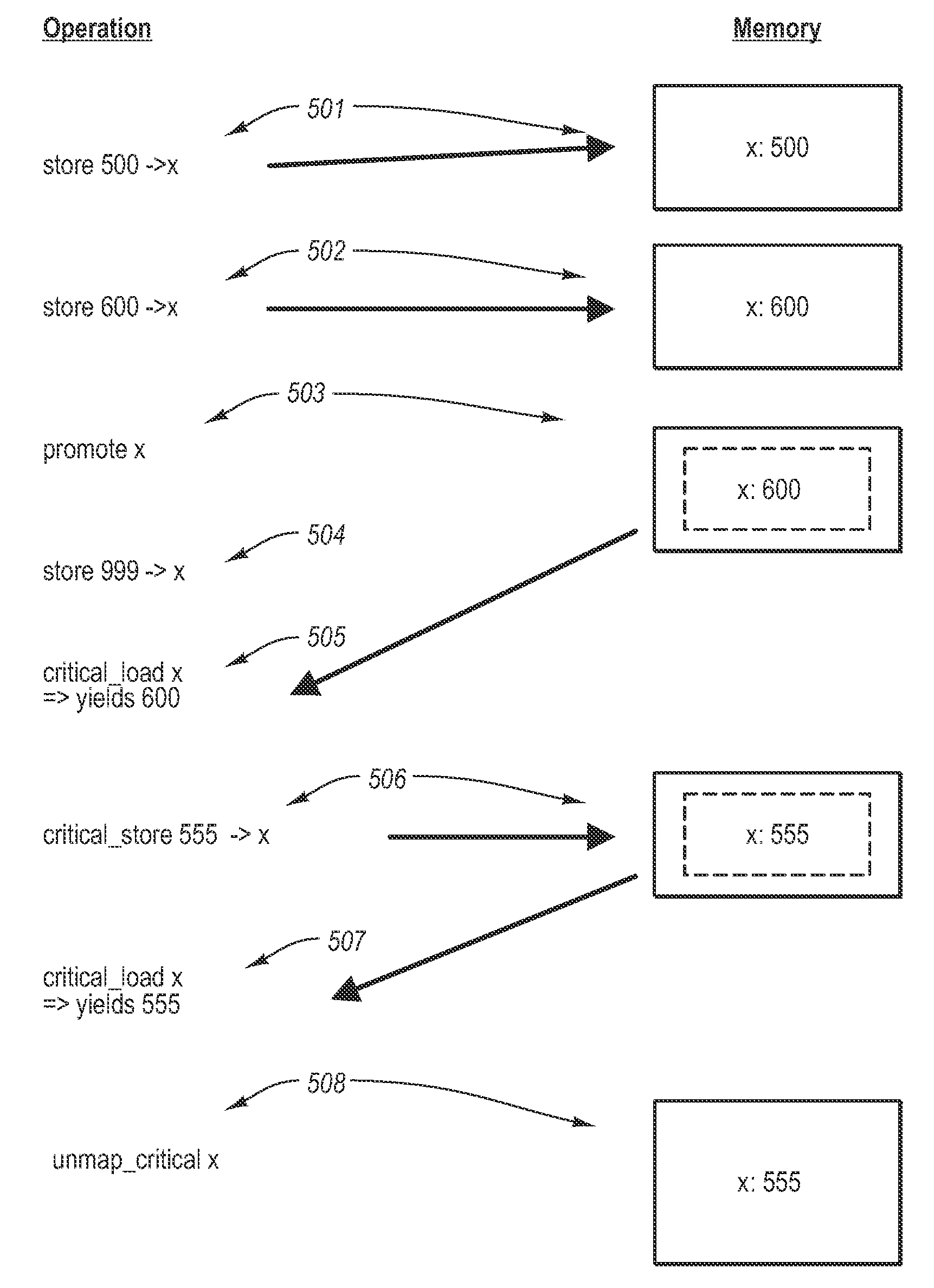
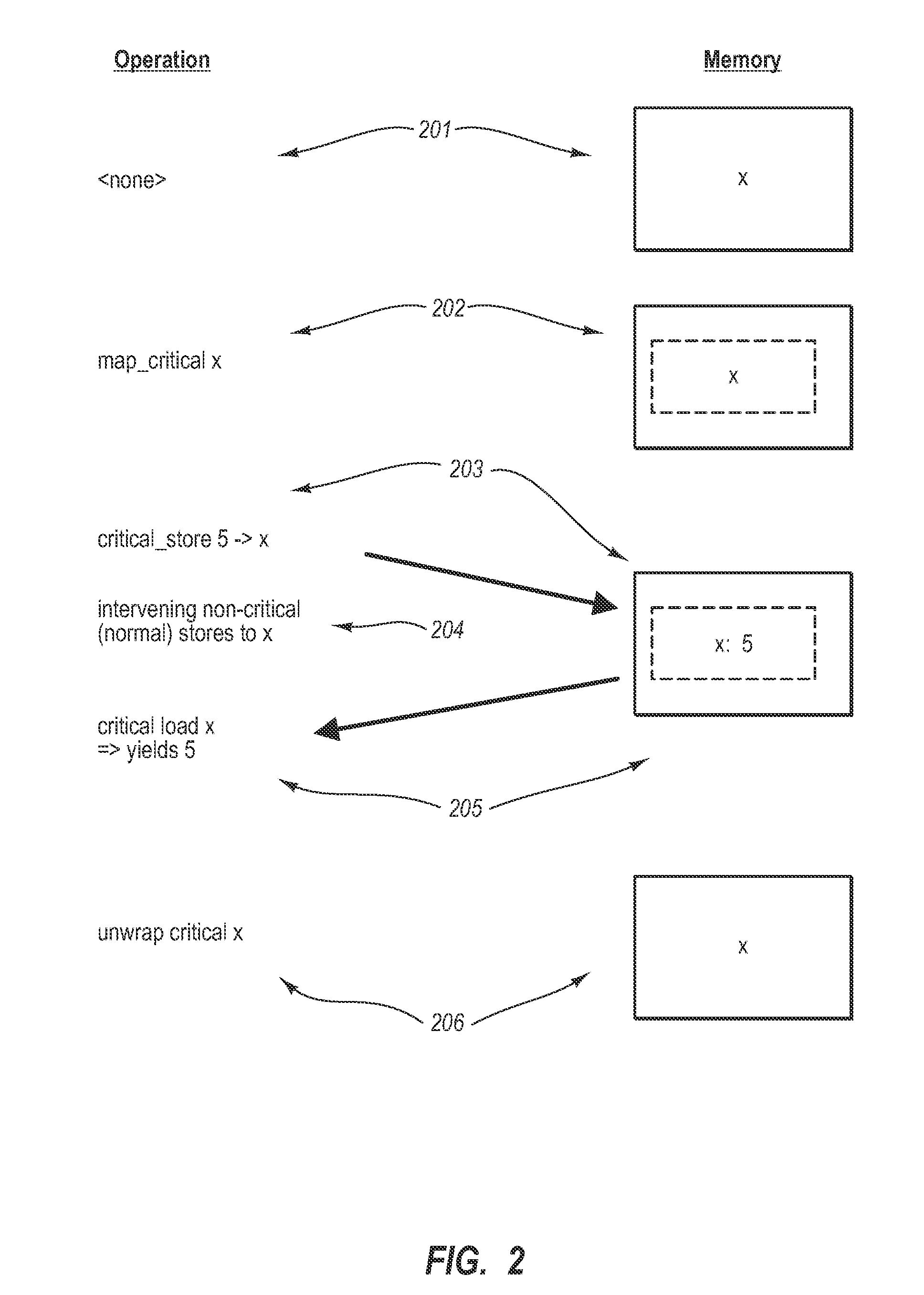
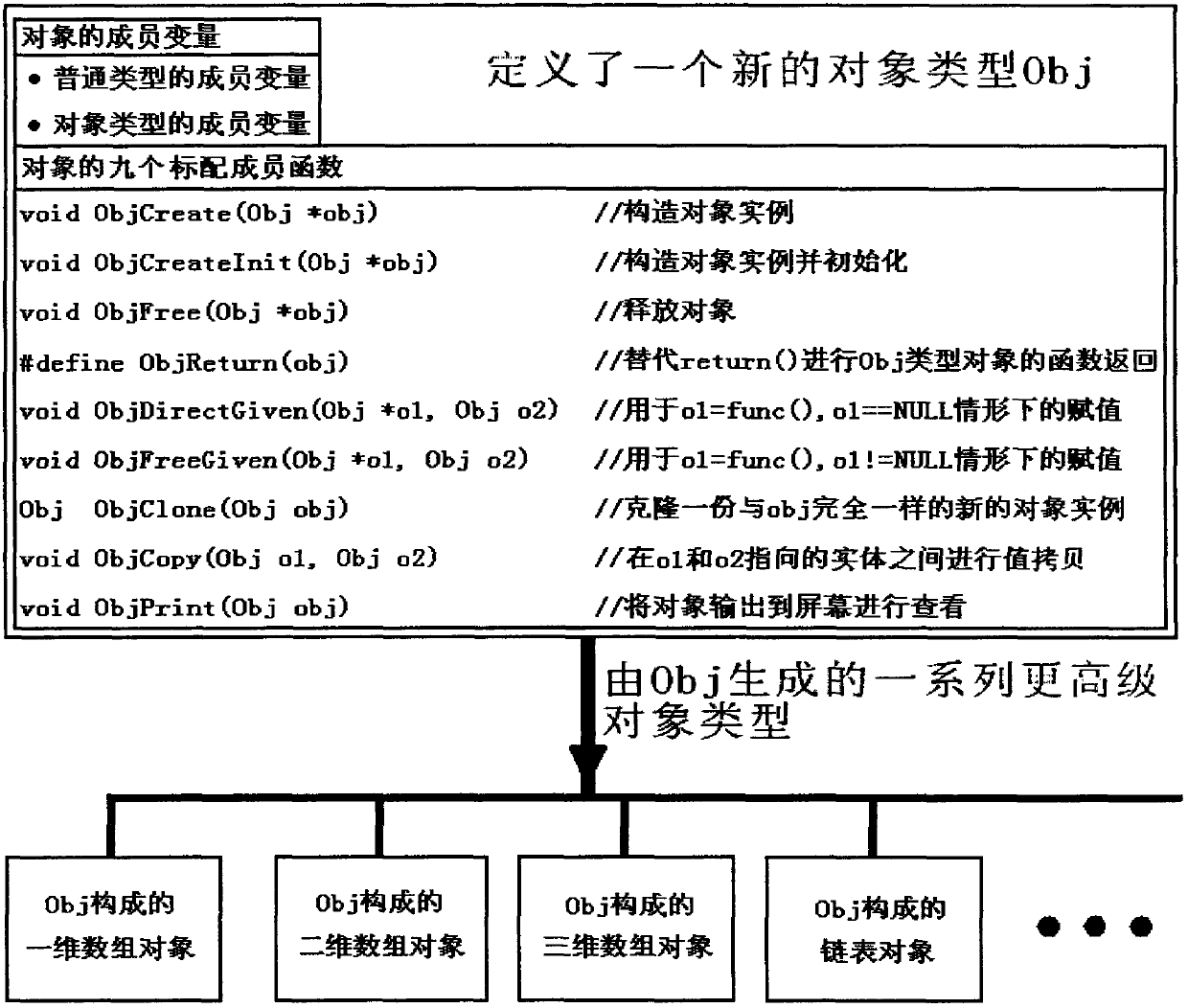
Patents
Literature
173 results about "Bad memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Semiconductor memory and method for operating the same
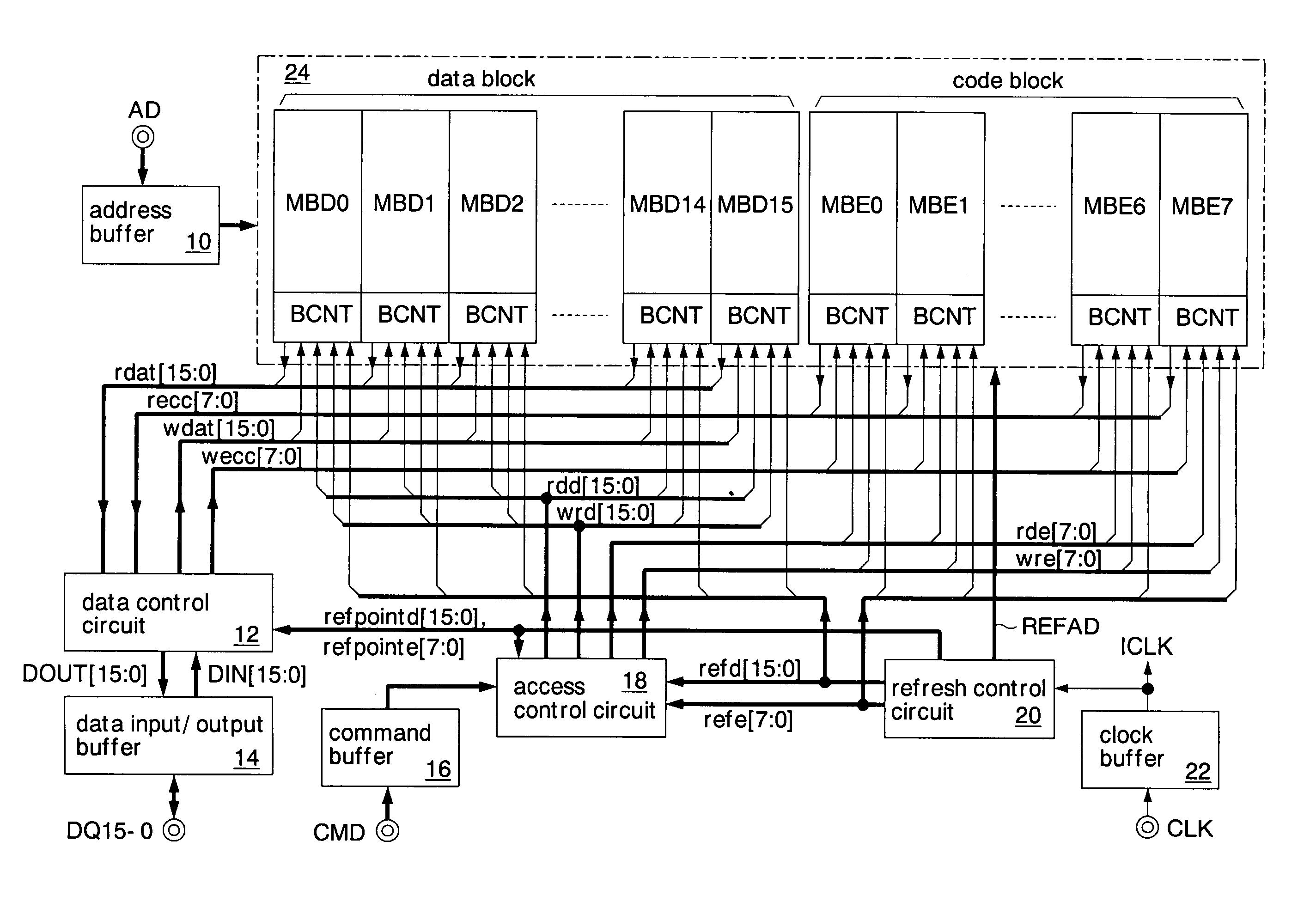
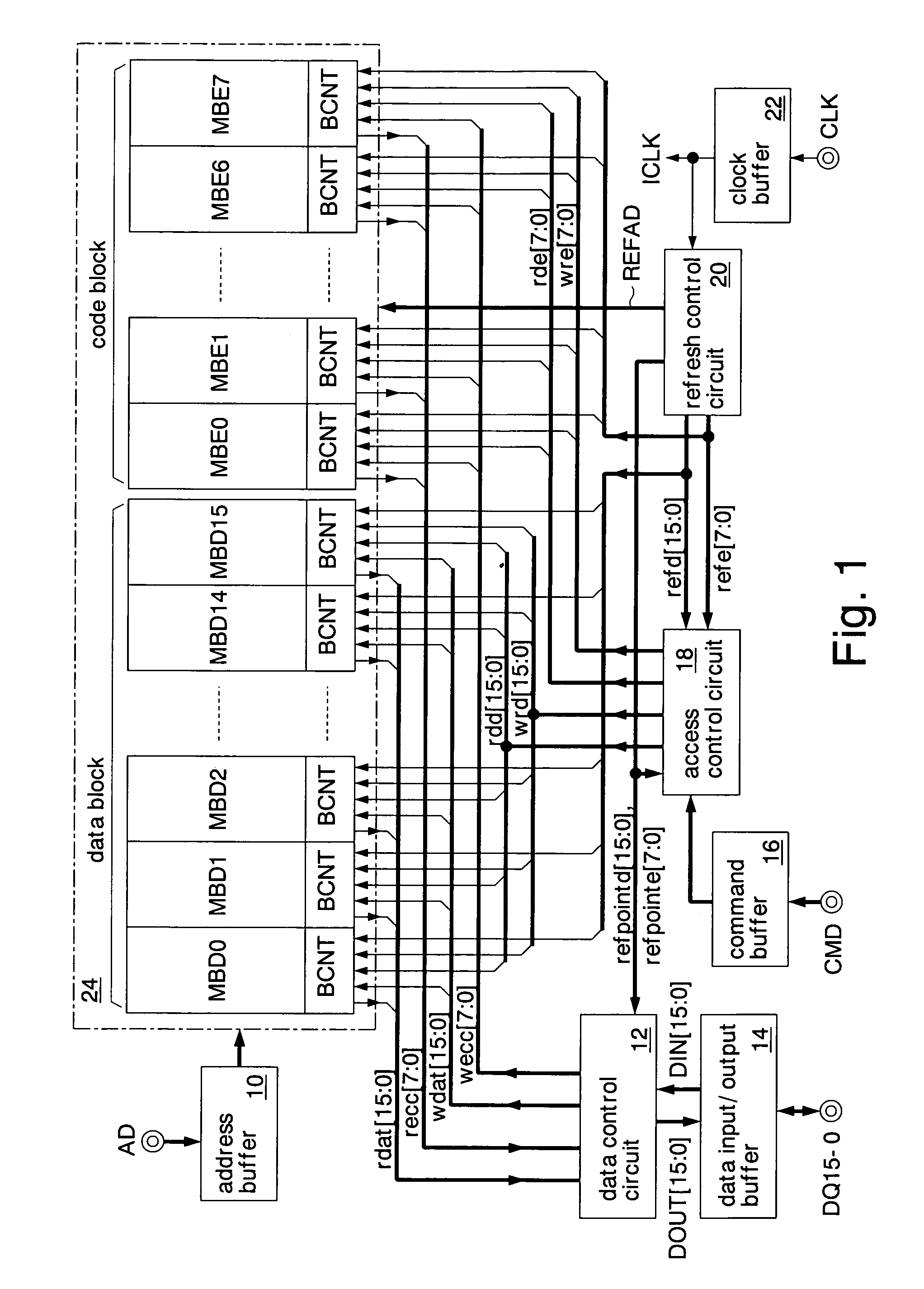
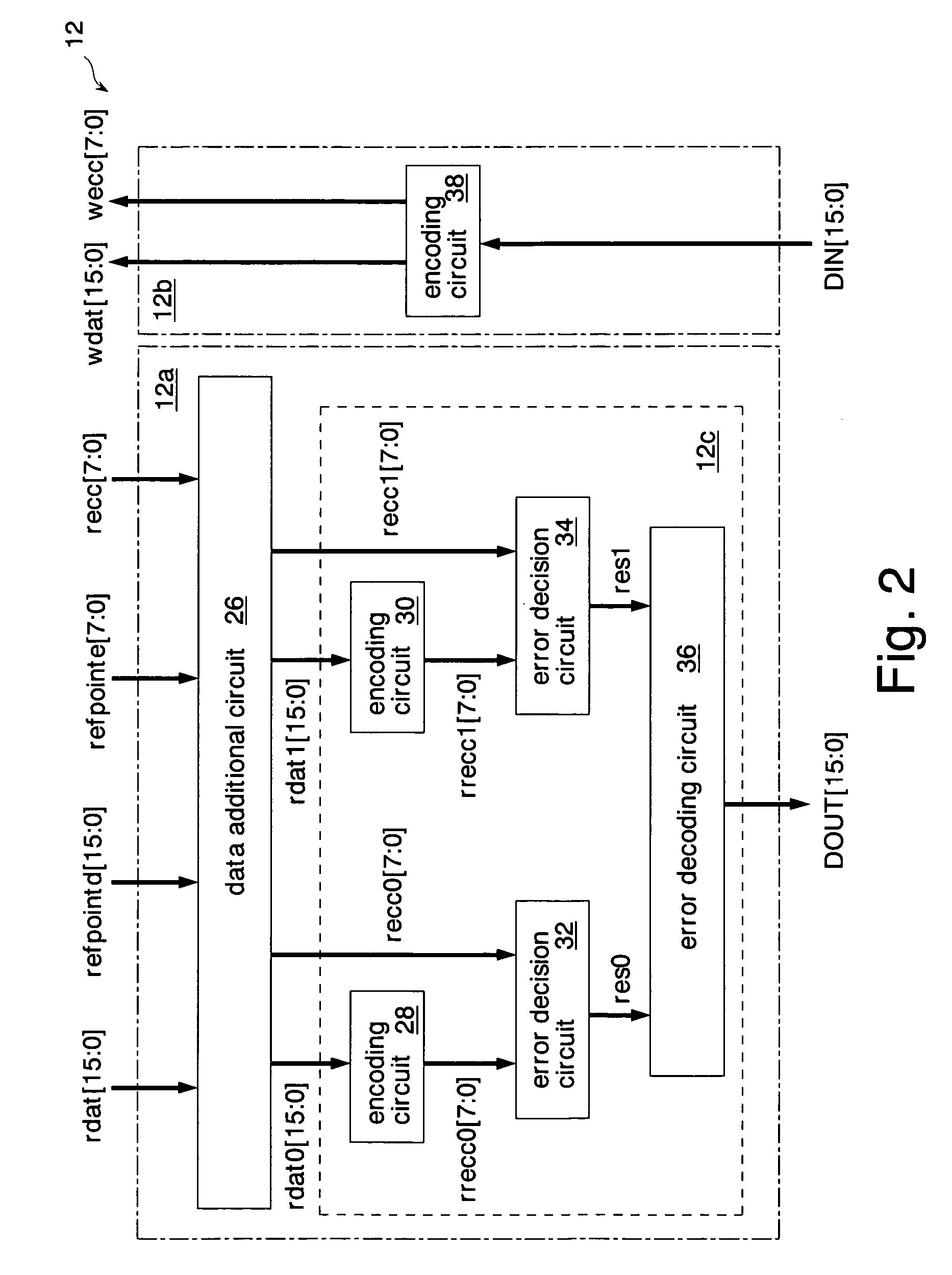
A data additional circuit adds plural types of expectation data to be read from a refresh block to data read from other blocks, respectively, to generate plural read data strings. An error correction circuit detects errors for each read data string, and sets the most reliable result of the error detection results to be true. The error correction circuit decodes data to be read from the refresh block based on a true error detection result. Moreover, the error correction circuit corrects the error of the read data string corresponding to the true error detection result. Consequently, without extending the read cycle time, a refresh operation can be hid, and errors can be corrected simultaneously. By correcting a data error read from a bad memory cell of data retention characteristics, a refresh request interval can be extended, and power consumption during a standby period can be reduced.
Owner:SOCIONEXT INC
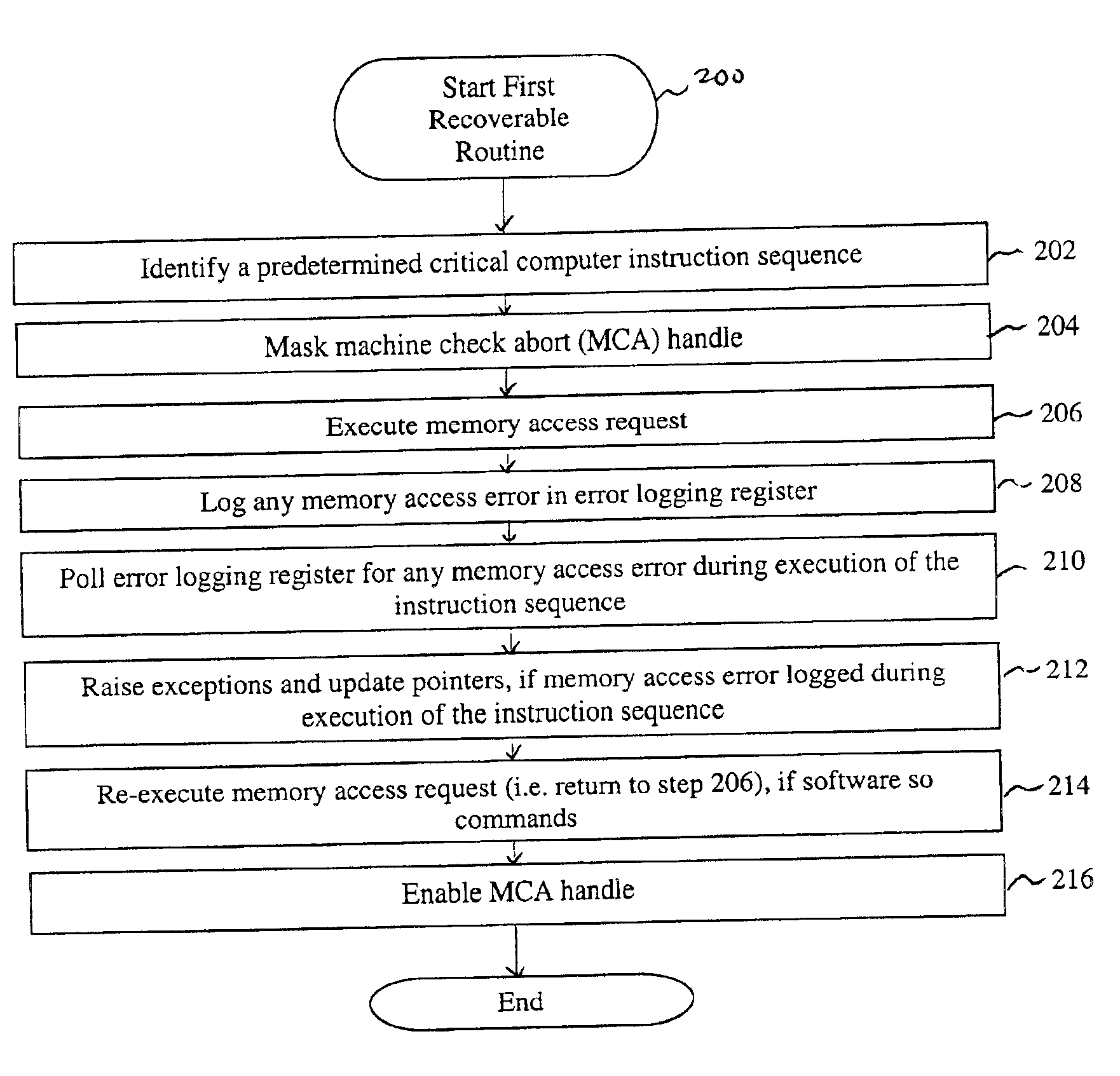
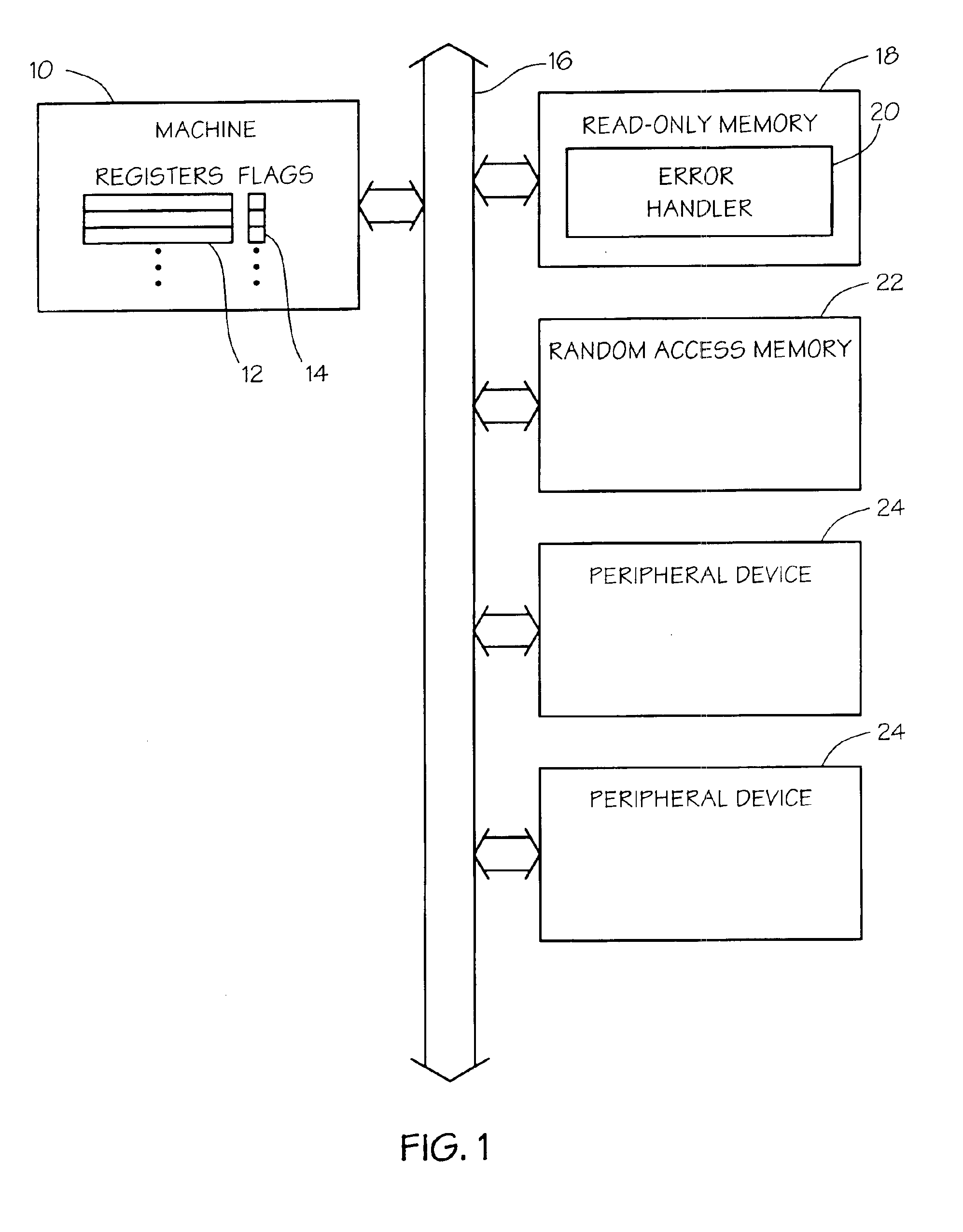
System and method for recovering from memory failures in computer systems
InactiveUS6851074B2Responding to errorRespond effectivelyNon-redundant fault processingRedundant operation error correctionProcessor registerComputerized system
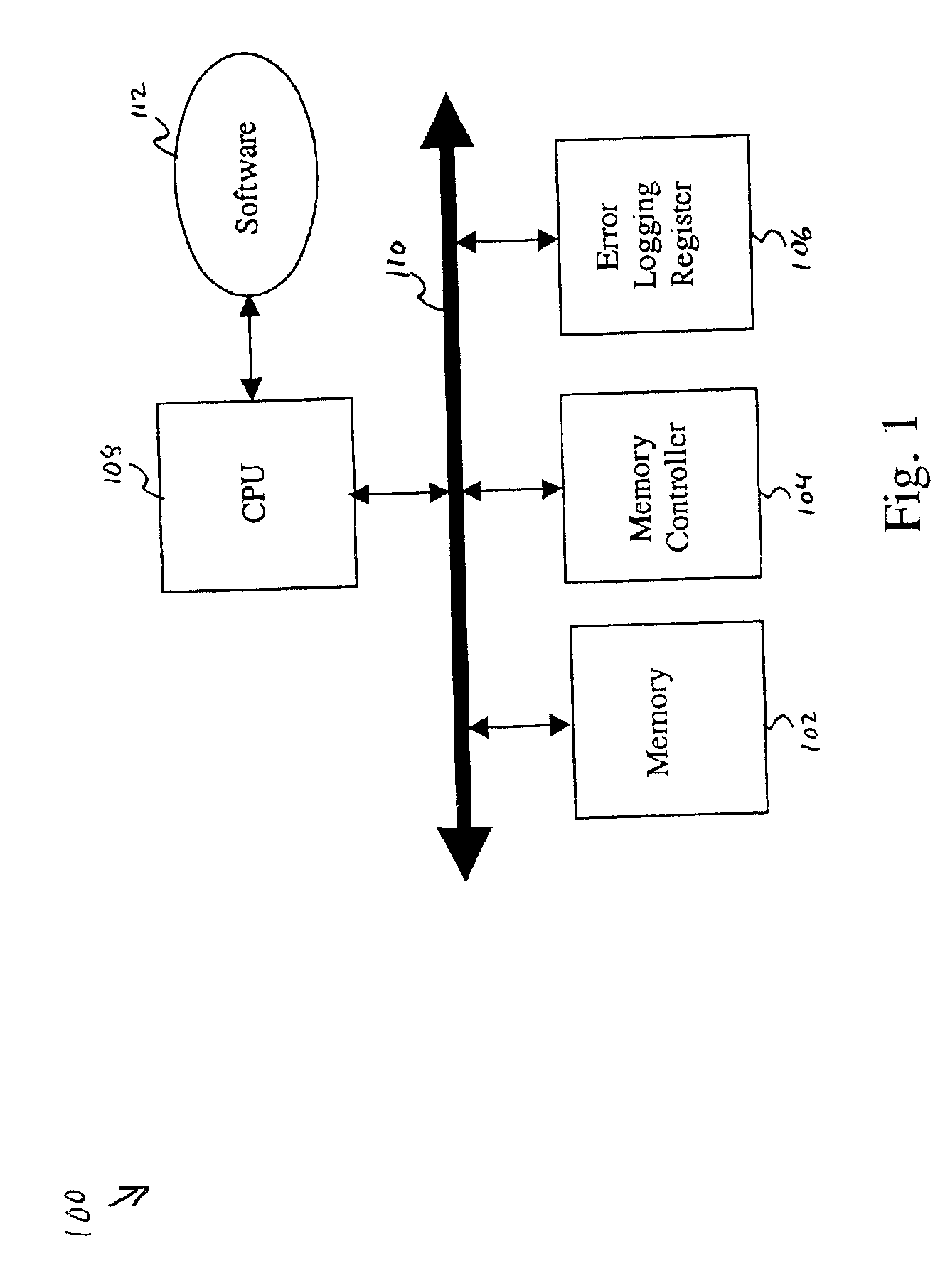
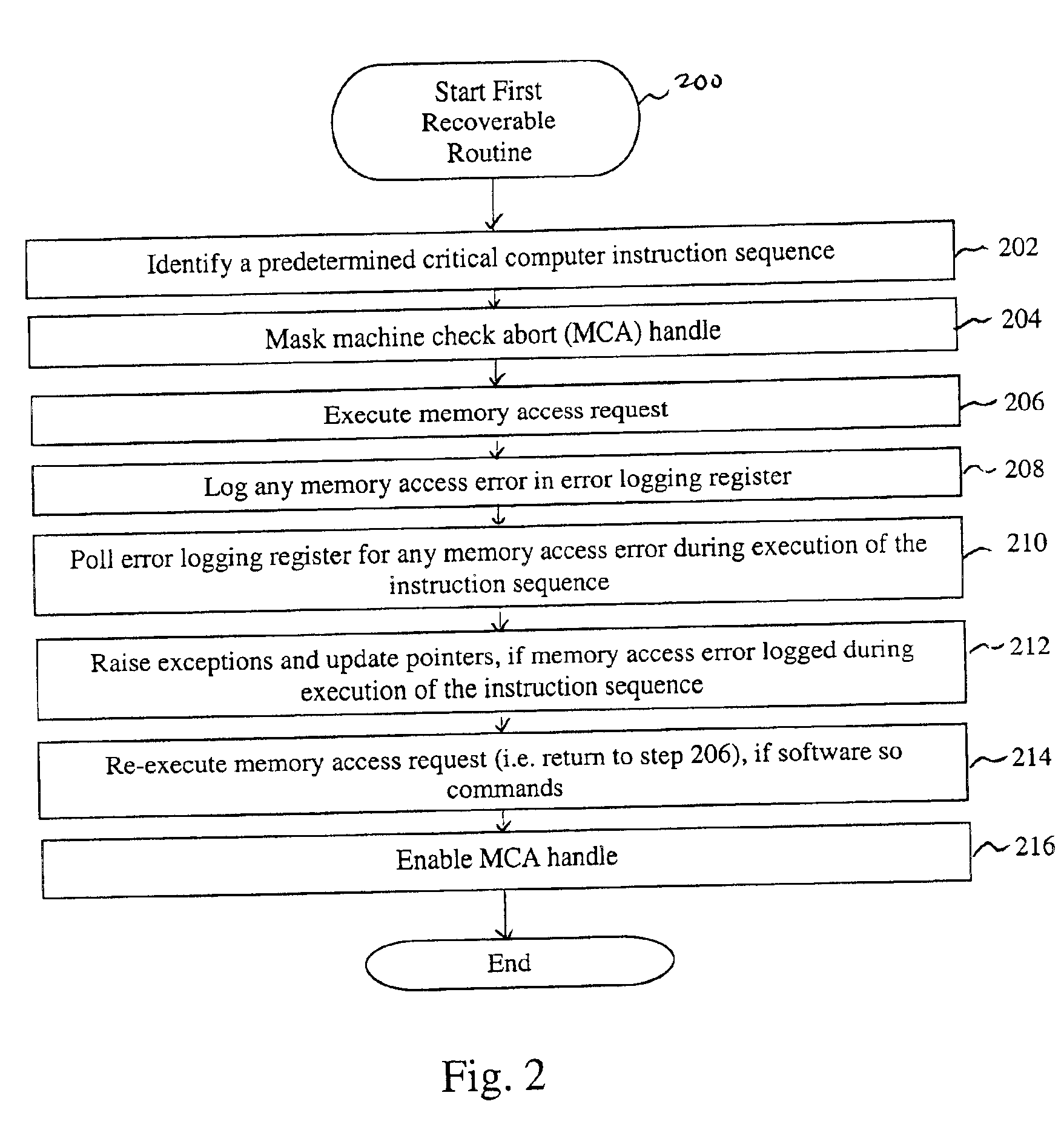
The present invention is a system and method for recovering from memory failures in computer systems. The method of the present invention includes the steps of: identifying a predetermined instruction sequence; monitoring for memory access errors in response to the request; logging a memory access error in an error logging register; polling the register for any logged memory access error during execution of the instruction sequence; and raising exceptions, if the memory access error is logged. Within the system of the present invention, memory access errors are stored in an error logging register, machine check abort handles are masked, and memory controllers are under full control of the software so that memory access errors can be intercepted and responded to without necessitating a system reboot or application restart. The present invention is particularly applicable to O / S code which can not otherwise recover from memory errors except by rebooting.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
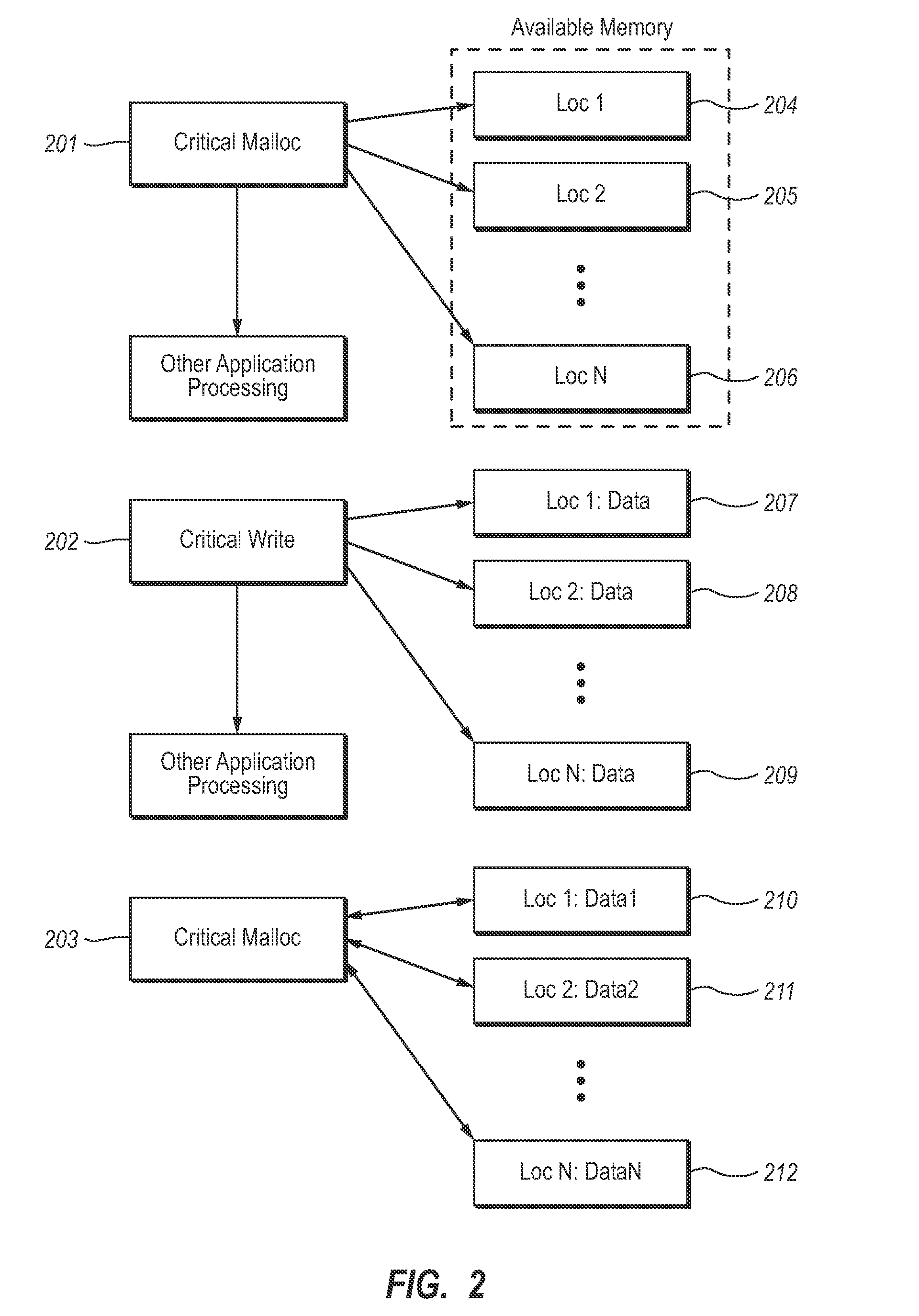
Protection of critical memory using replication
InactiveUS20080140962A1Memory loss protectionUnauthorized memory use protectionThird partyData Corruption
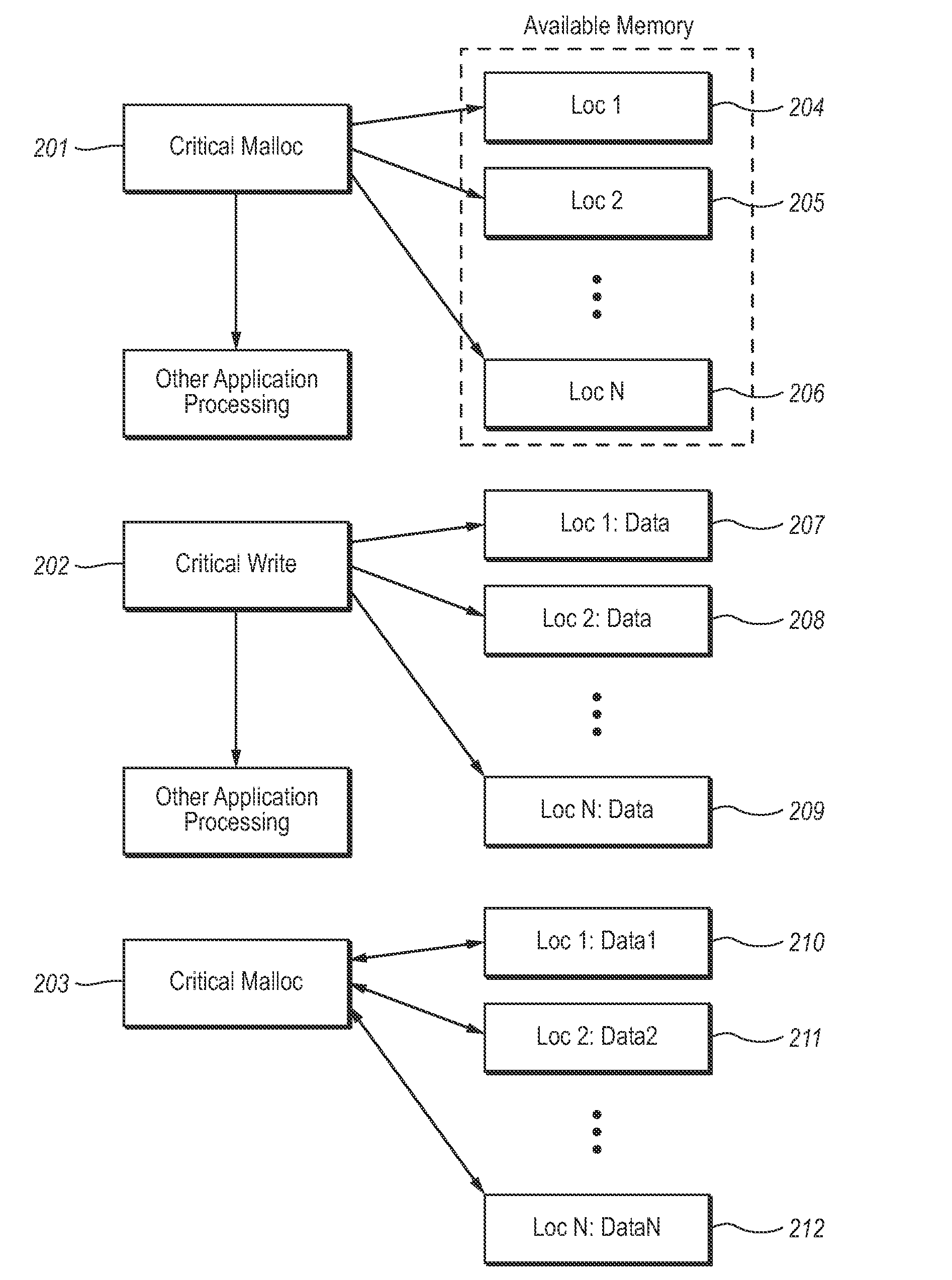
Typical computer programs may incur costly memory errors that result in corrupted data. A new memory model is presented wherein it may be determined that certain data is critical and critical data may be stored and protected during computer application execution. Critical Memory allows that data determined to be critical may be stored and retrieved using functions enabled to increase the reliability of the data. Functions are presented enabling allocation of redundant computer memory; functions are presented enabling consistently writing critical data to redundant locations; and functions are presented enabling reading critical data while ensuring that the data read is consistent with the most recent write of critical data and enabled to repair inconsistent data. The memory model and functions presented are designed to be compatible with existing third-party libraries.
Owner:MICROSOFT TECH LICENSING LLC
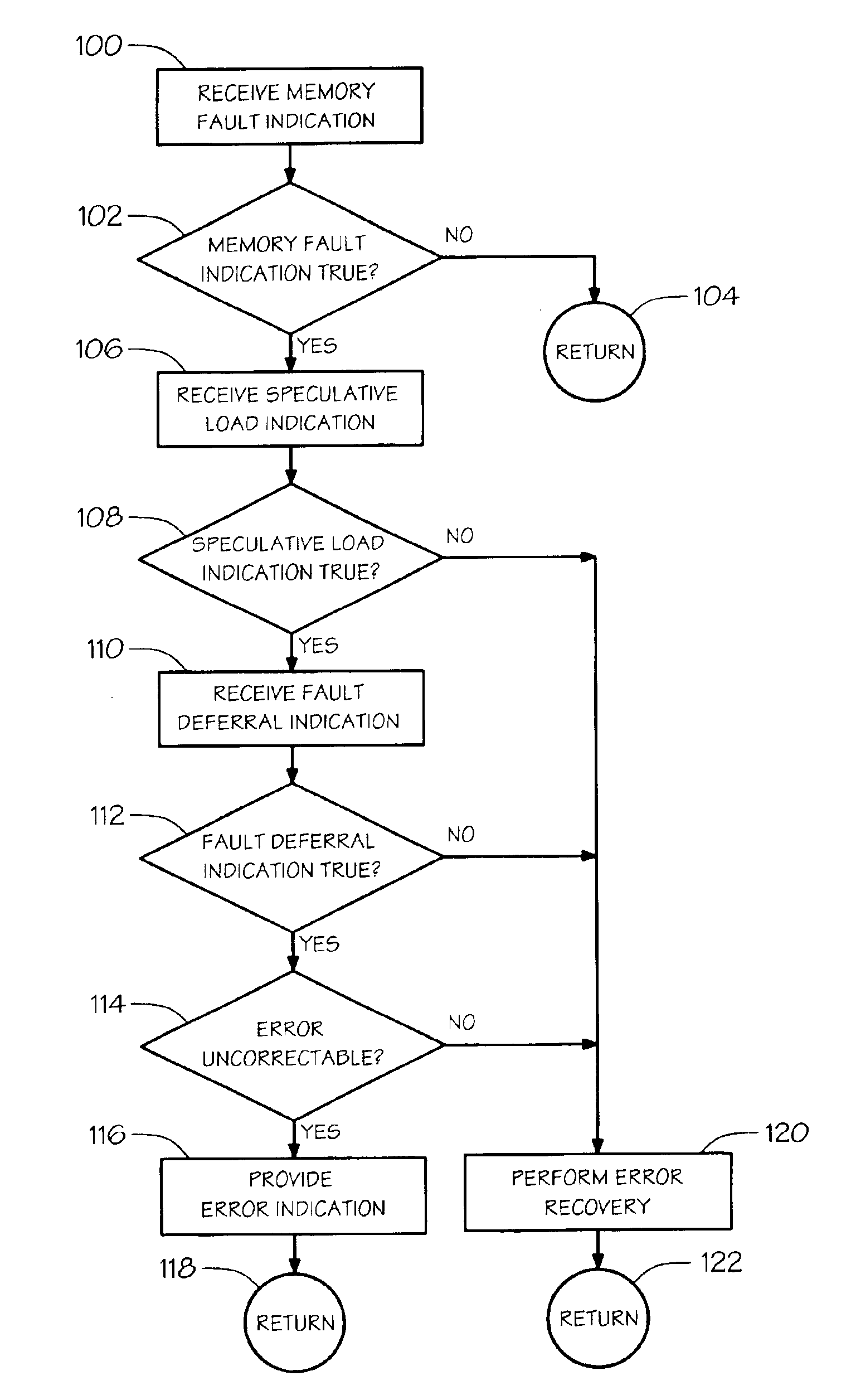
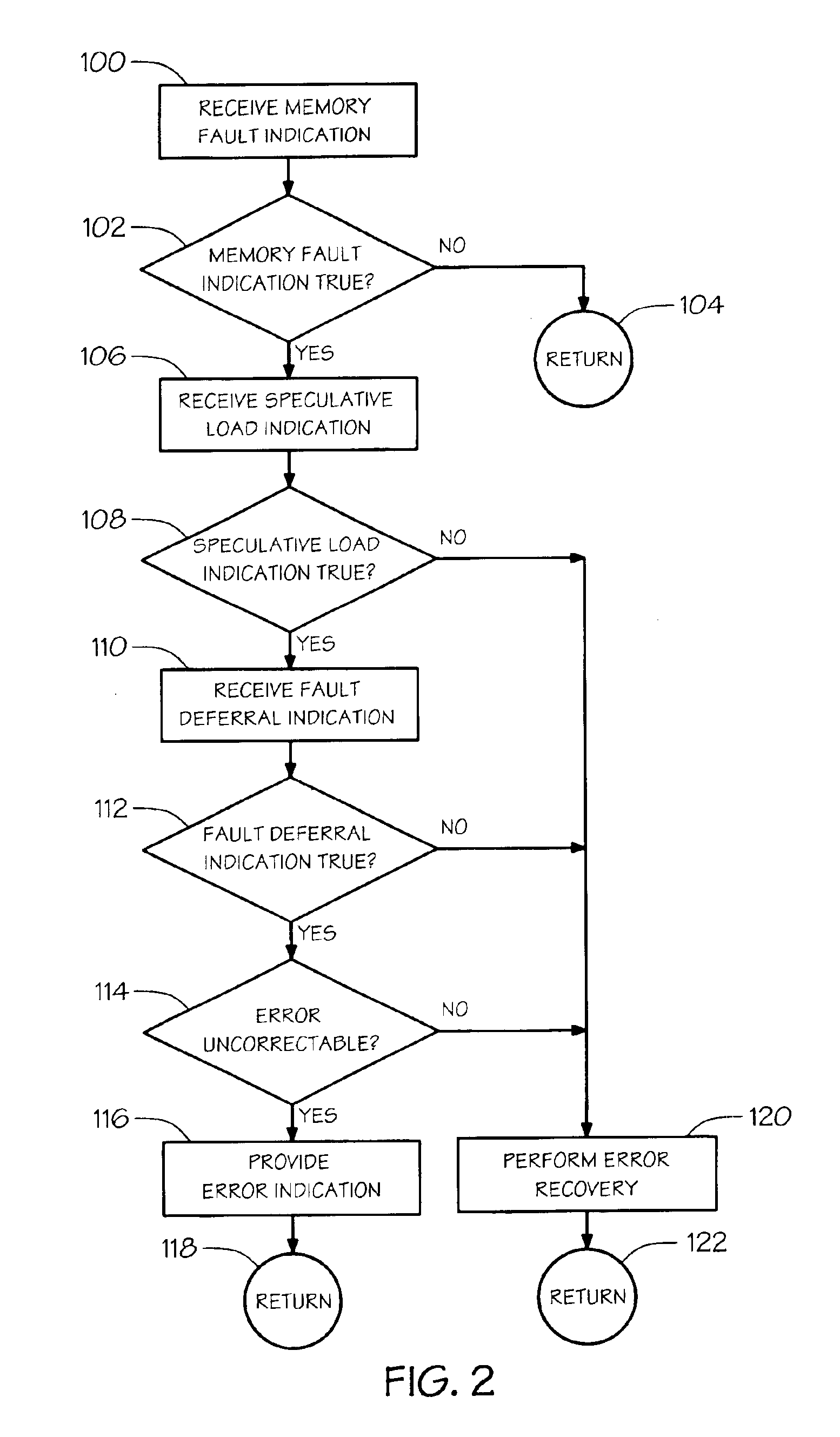
Error recovery for speculative memory accesses
A method of handling memory errors. A memory fault indication is received that is true if an error in the memory is detected while executing a memory load request to retrieve a value from the memory. A speculative load indication is received that is true if the memory load request was issued speculatively. If the memory fault indication is true and the speculative load indication is true, then an error indication that the returned value is invalid is provided, otherwise, error recovery is performed.
Owner:INTEL CORP
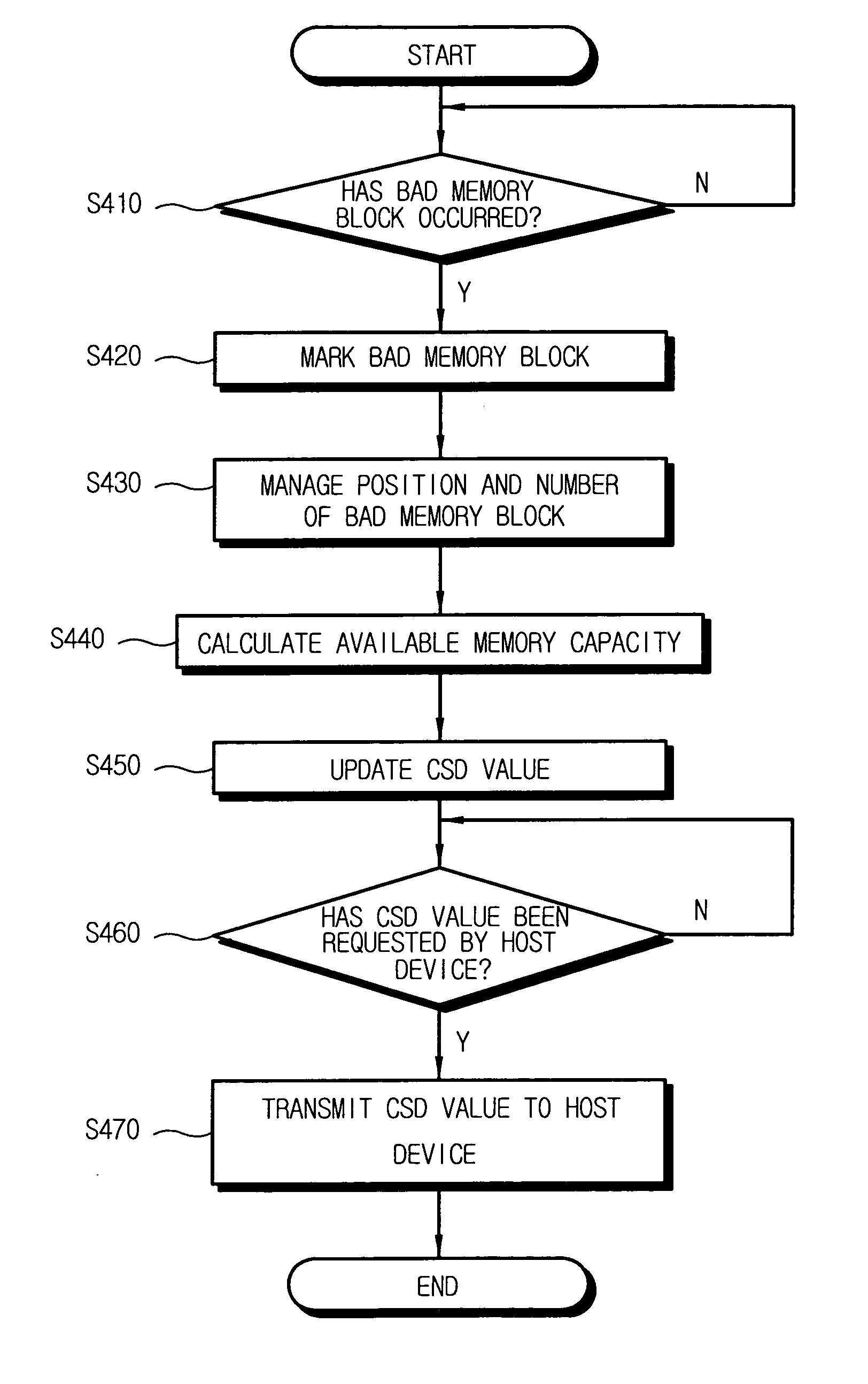
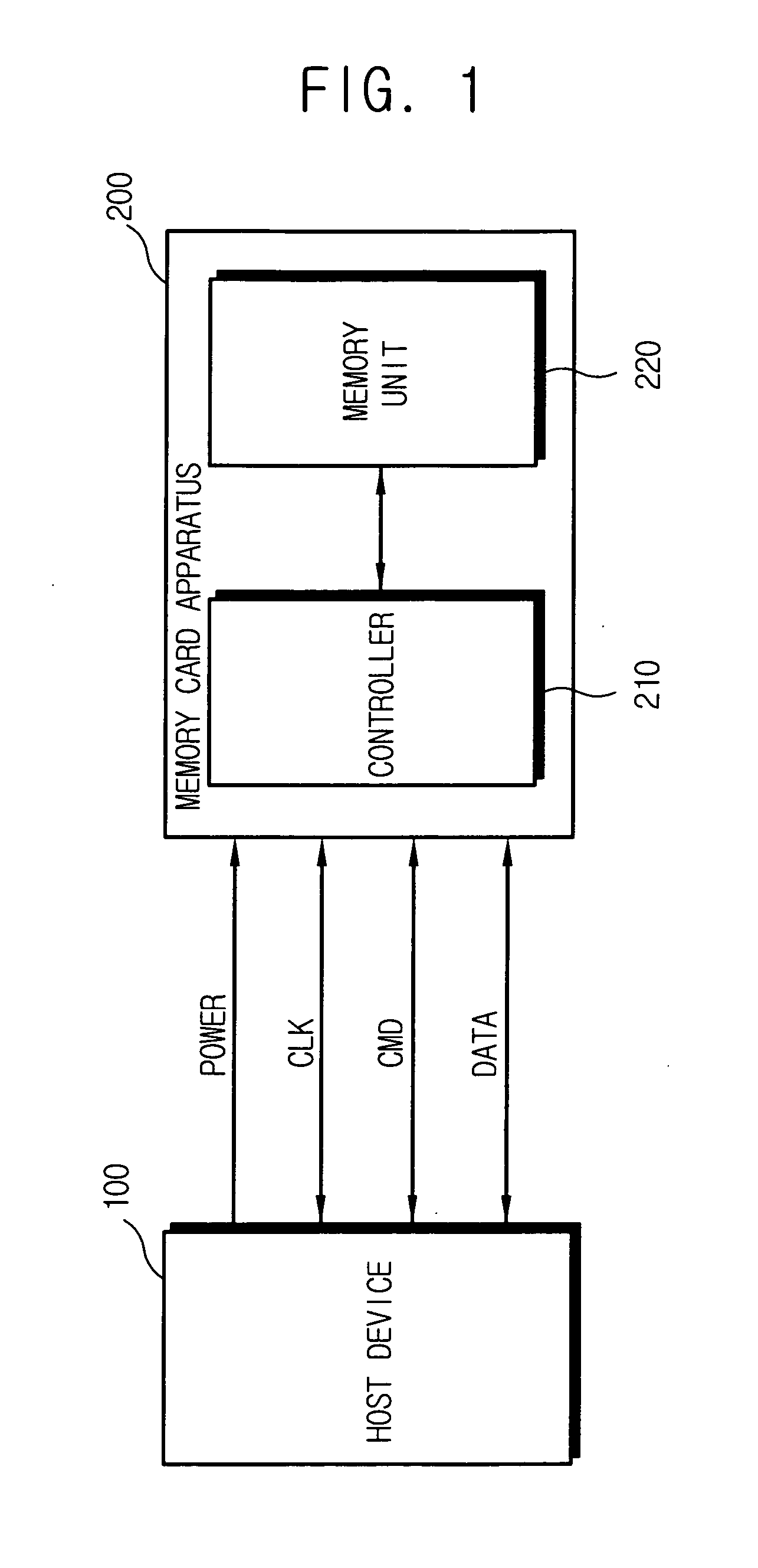
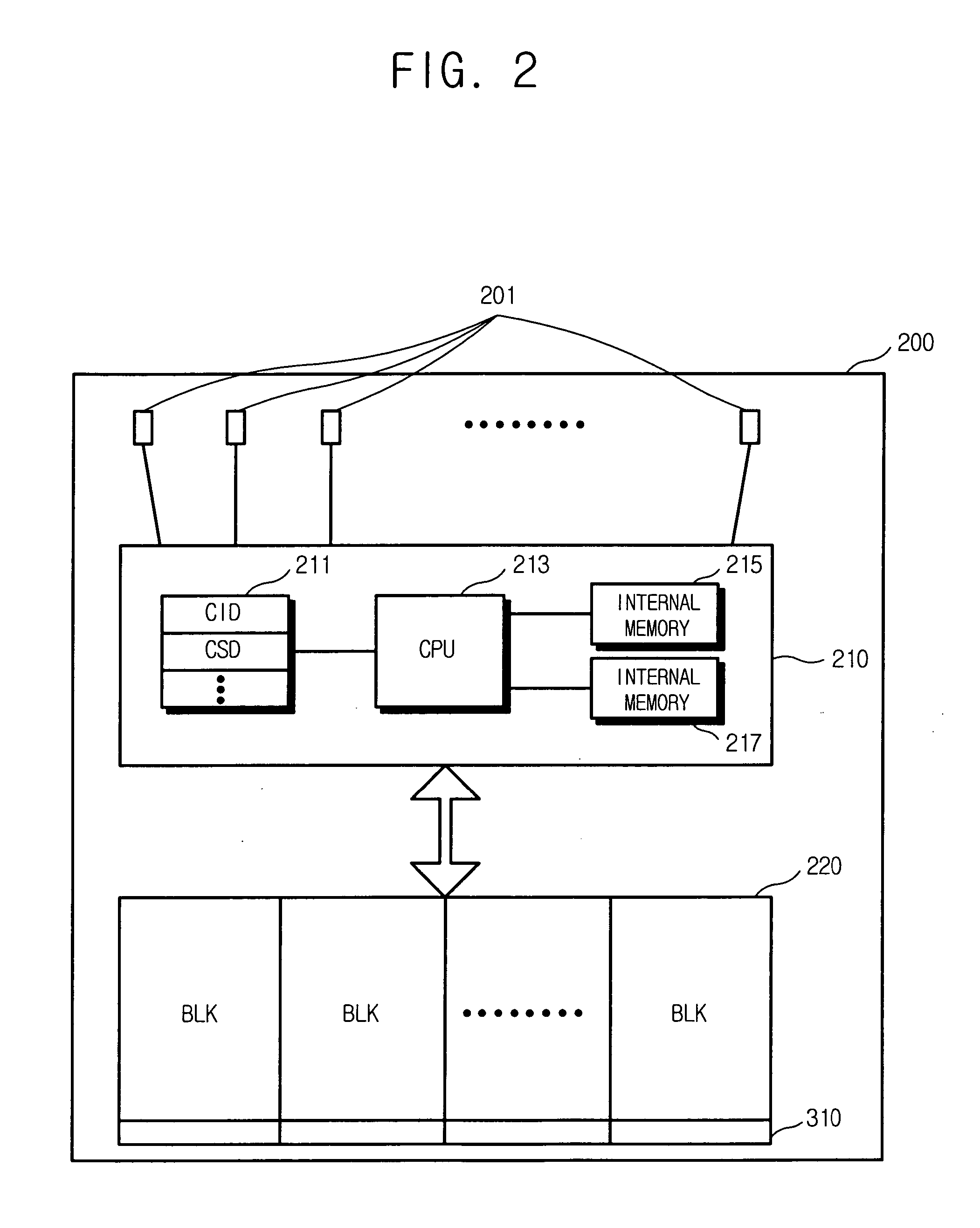
Non-volatile memory card apparatus and method for updating memory capacity information
A memory card apparatus includes a non-volatile memory and a controller configured to control the non-volatile memory and communicating with the host device, wherein the controller updates available memory capacity information according to occurrence of bad memory in the non-volatile memory and transmits the updated memory capacity information to a host device.
Owner:SAMSUNG ELECTRONICS CO LTD
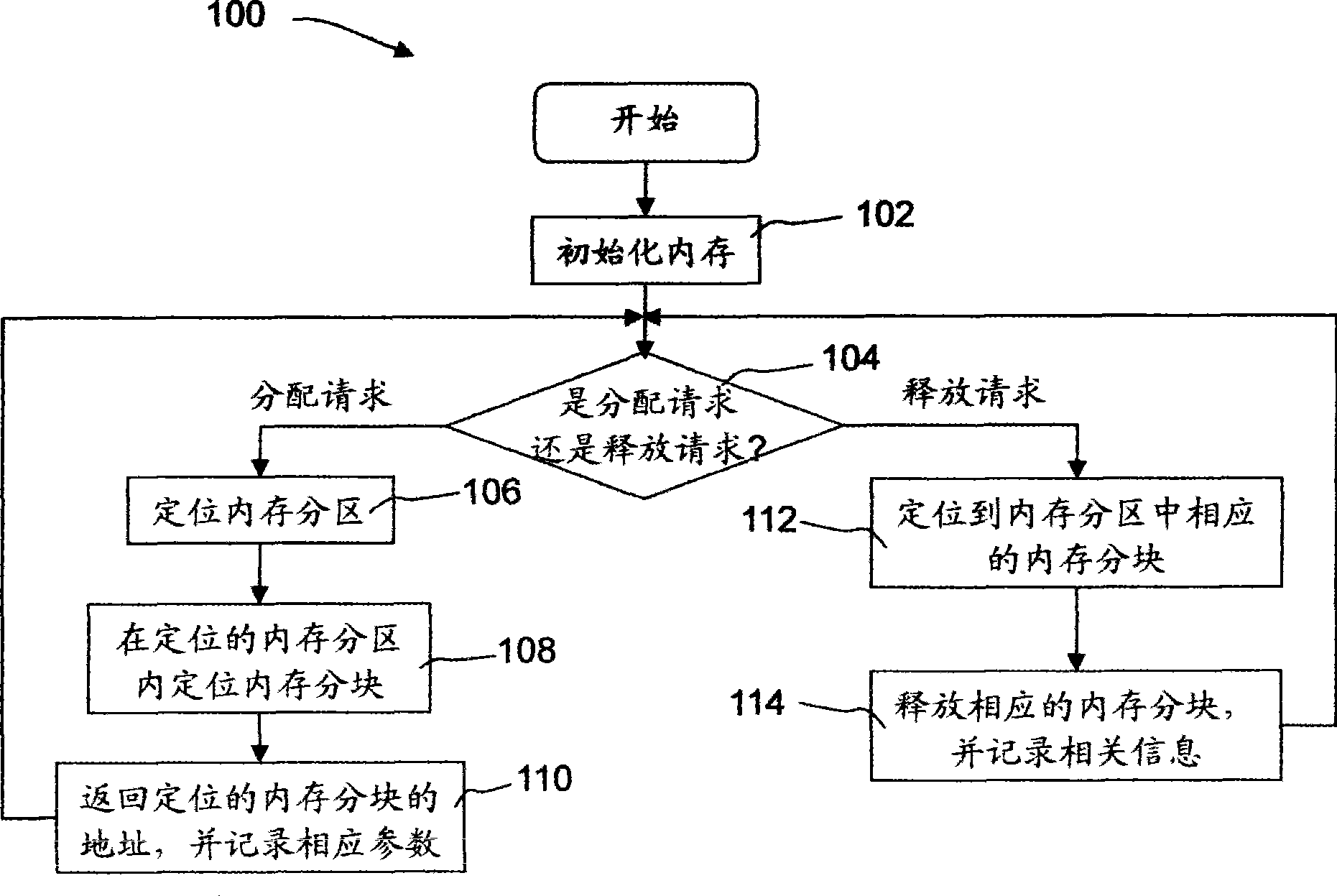
Internal memory management method
InactiveCN101499034AReal-timeAchieve reliabilityMemory adressing/allocation/relocationInternal memoryDistributed memory
The invention discloses a memory management method applicable for an embedded system, comprising steps of: providing a memory area with a certain volume; dividing a memory area into a plurality of memory branch areas and unit memory blocks; when it is necessary to provide memory, distributing the unit memory block greater than needed memory for use. The memory management method related to the invention uses a memory layout aiming at the embedded system, distributing memory via simple algorithm in a high effect manner and detecting whether memory error occurs.
Owner:VIMICRO CORP
Memory error detection reporting
ActiveUS20050132263A1Reduce the impactLower potentialStatic storageRedundant data error correctionCourse of actionMemory controller
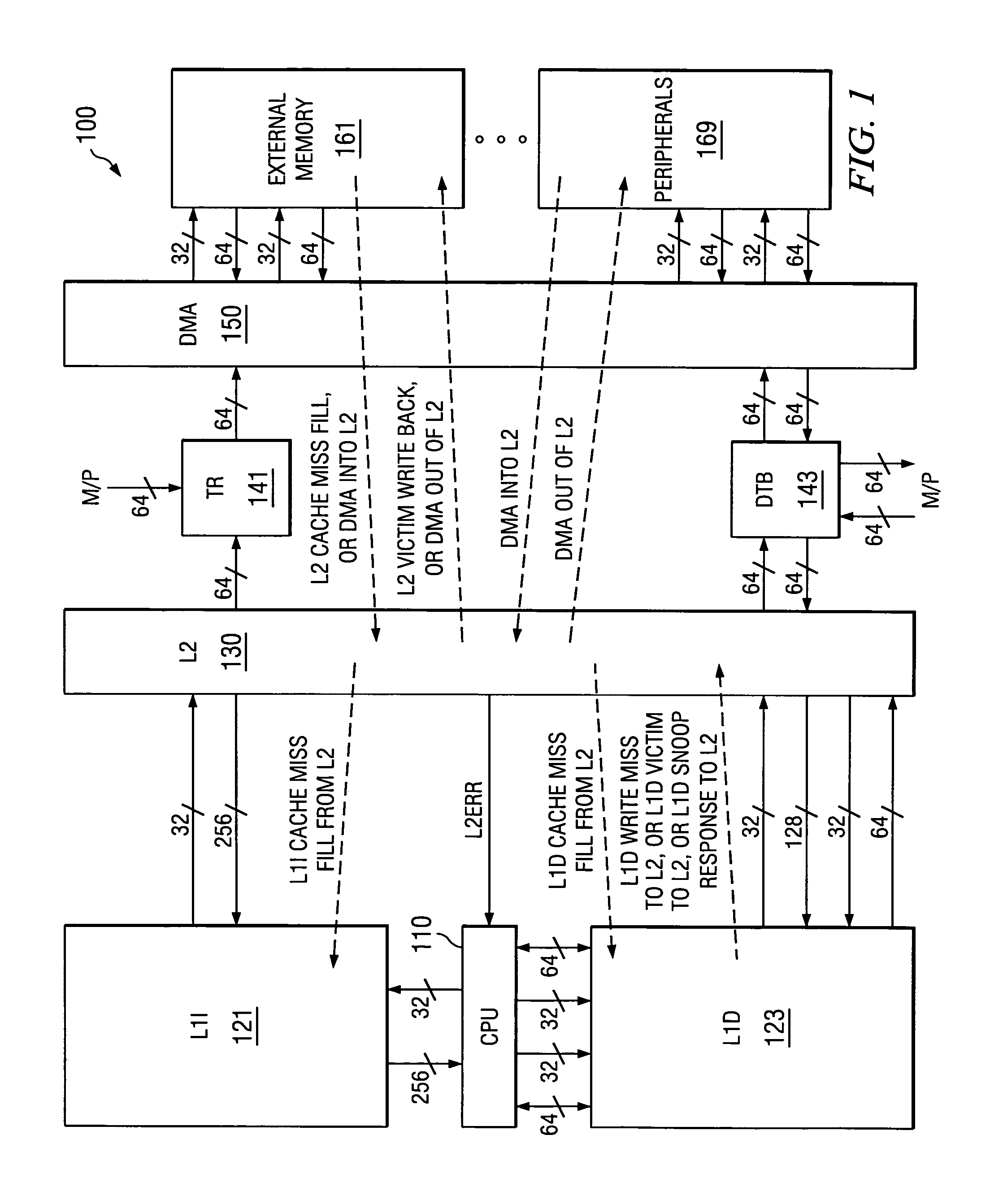
A memory system or a digital signal processor (DSP) includes single-bit-error detection hardware in its level two (L2) memory controller to mitigate the effects of soft errors. Error detection hardware detects erroneous data that is fetched by the central processing unit and signals the central processing unit. The parity is generated and checked only for whole memory line accesses. This technique is especially useful for cache memory. The central processing unit can query the memory controller as to the specific location that generated the error and decide the next course of action based on the type of data affected.
Owner:TEXAS INSTR INC
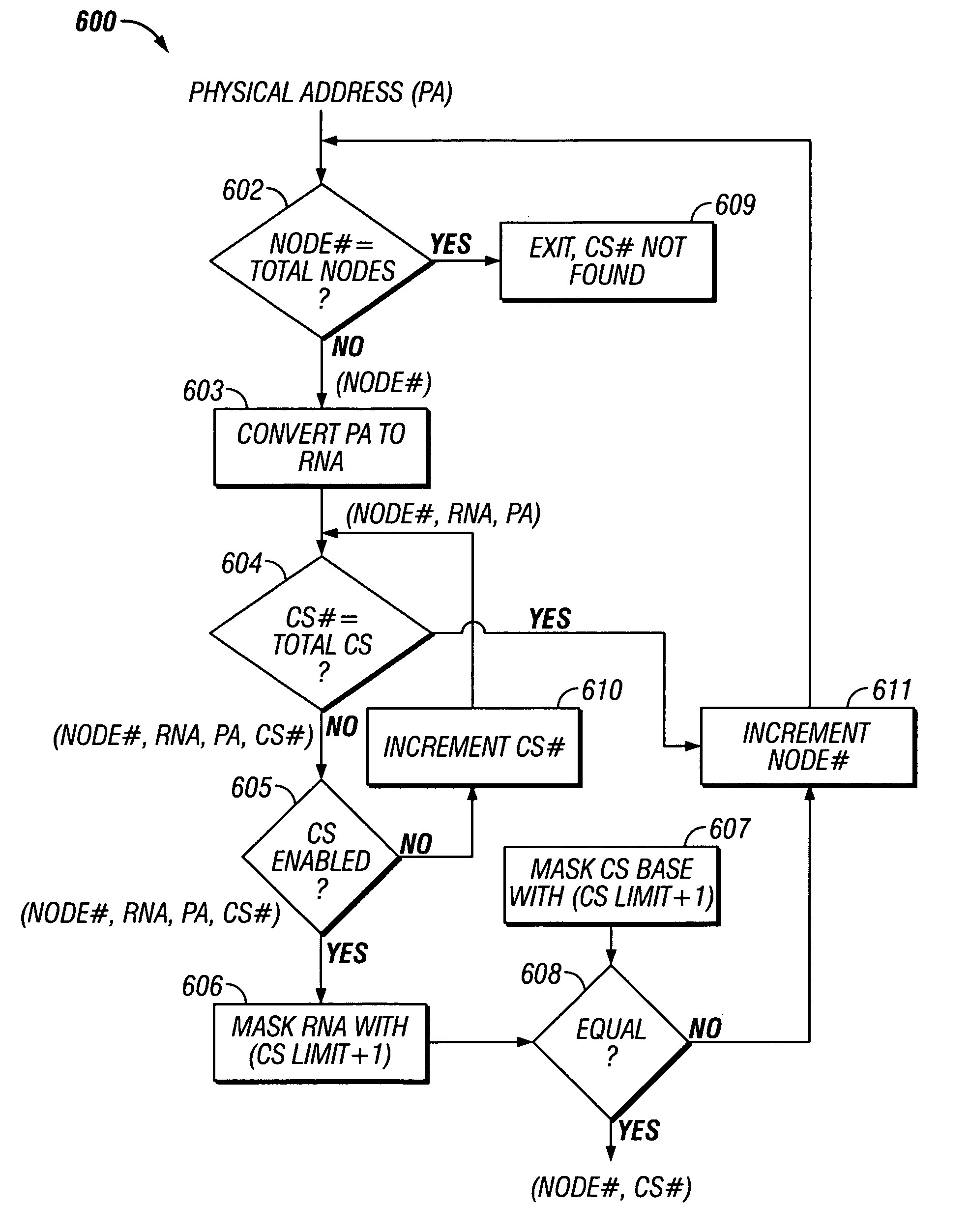
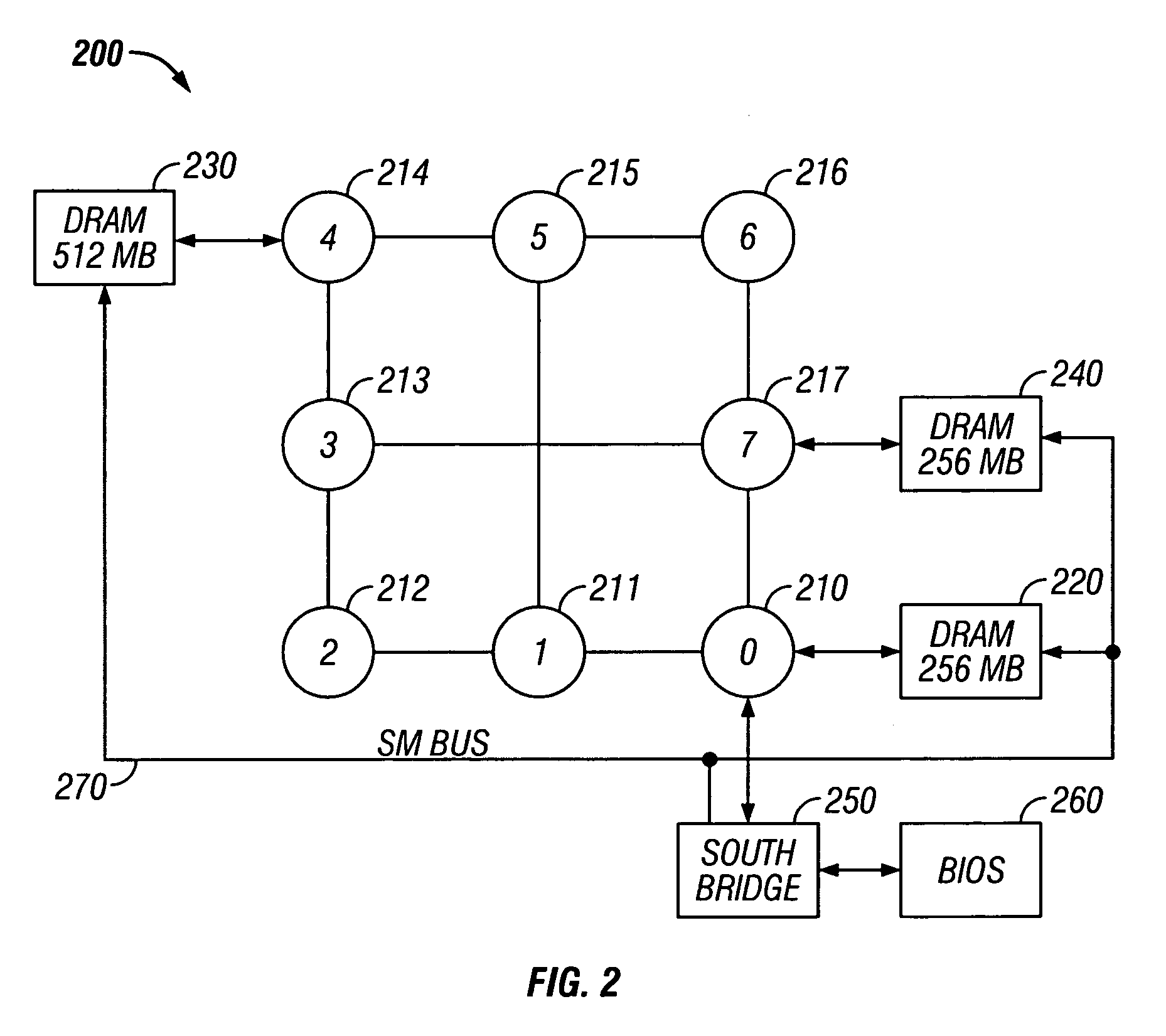
Memory check architecture and method for a multiprocessor computer system
Methods and apparatus are provided for use in testing a memory (220, 230, 240) in a multiprocessor computer system (200). The multiprocessor computer system (200) has a plurality of processing nodes (210-217) coupled in an array wherein each processing node is coupled to at least one other processing node, and a memory (220, 230, 240) distributed among the plurality of processing nodes (210-217). A configuration of the array is determined. An initial configuration of the memory (220, 230, 240) is also determined. The memory (220, 230, 240) is tested over the array according to the initial configuration to identify a bad memory element. The initial configuration is modified to form a revised configuration that excludes the bad memory element.
Owner:ADVANCED MICRO DEVICES INC
Memory error isolation and recovery in a multiprocessor computer system
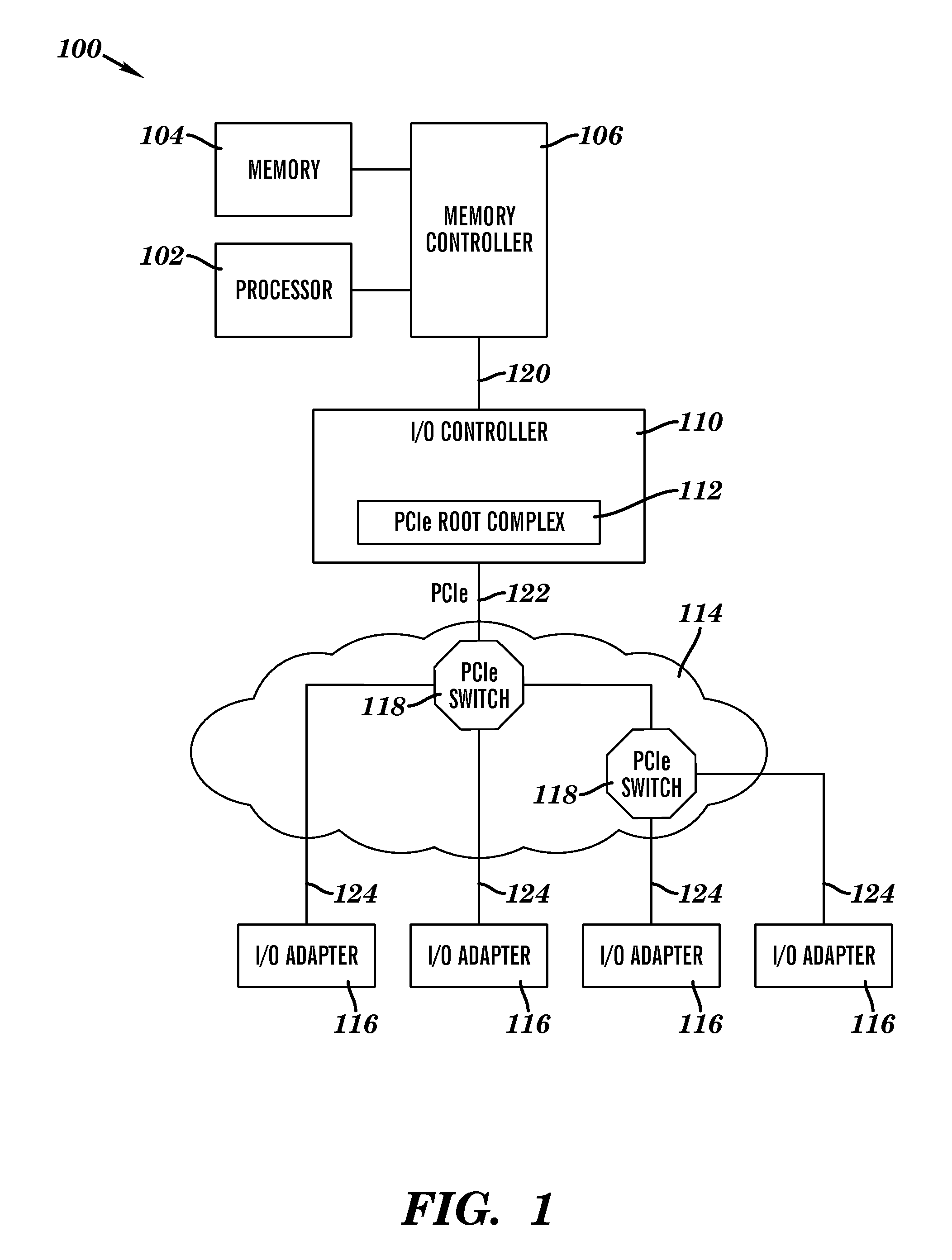
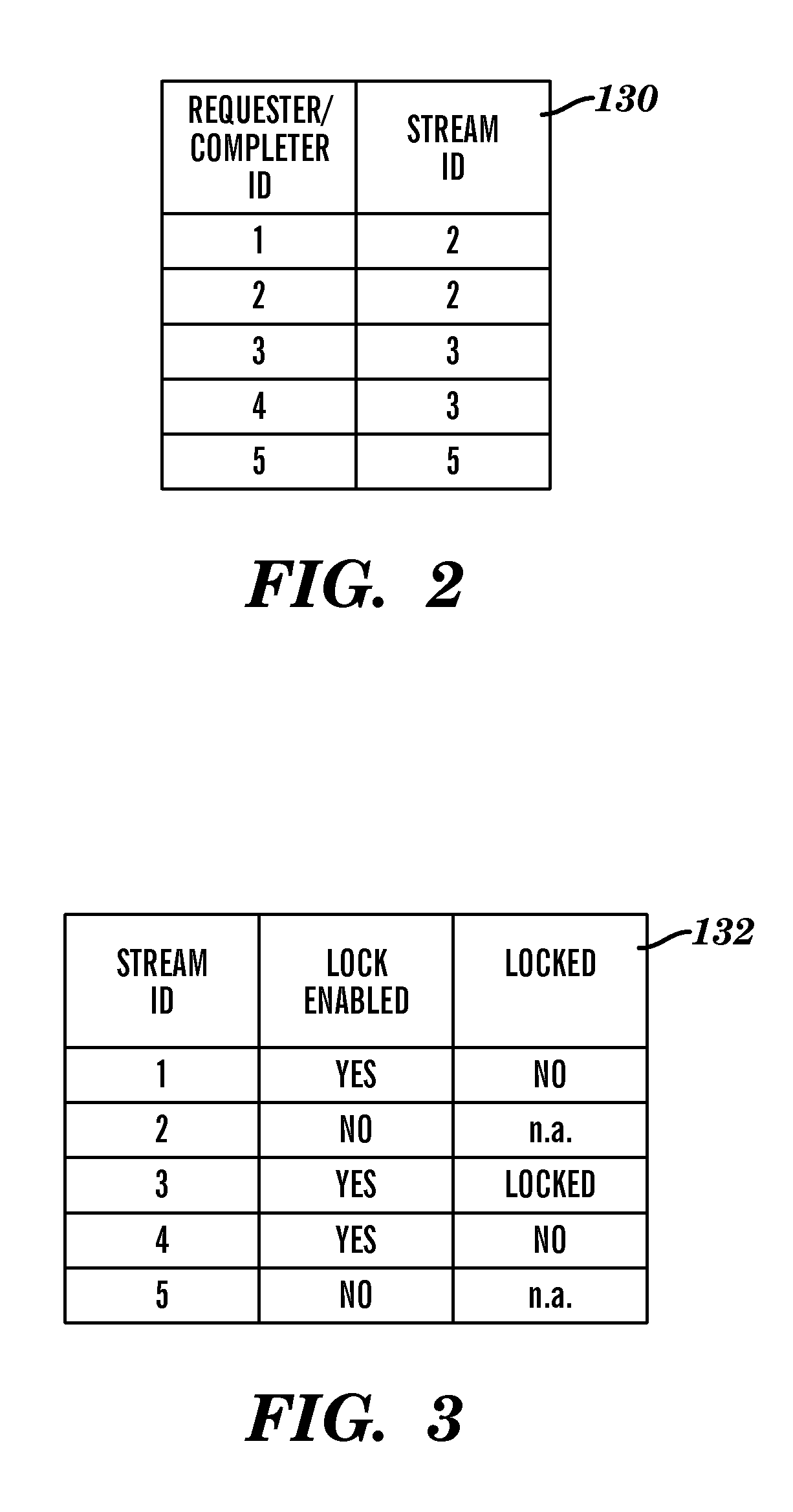
ActiveUS20110320892A1Detecting faulty computer hardwareUnauthorized memory use protectionDirect memory accessMulti processor
A system and computer implemented method for isolating errors in a computer system is provided. The method includes receiving a direct memory access (DMA) command to access a computer memory, a read response, or an interrupt; associating the DMA command to access the computer memory, the read response, or the interrupt with a stream identified by a stream identification (ID); detecting a memory error caused by the DMA command in the stream, the memory error resulting in stale data in the computer memory; and isolating the memory error in the stream associated with the stream ID from other streams associated with other stream IDs upon detecting the memory error.
Owner:IBM CORP
Reducing false positives in configuration error detection for programmable devices
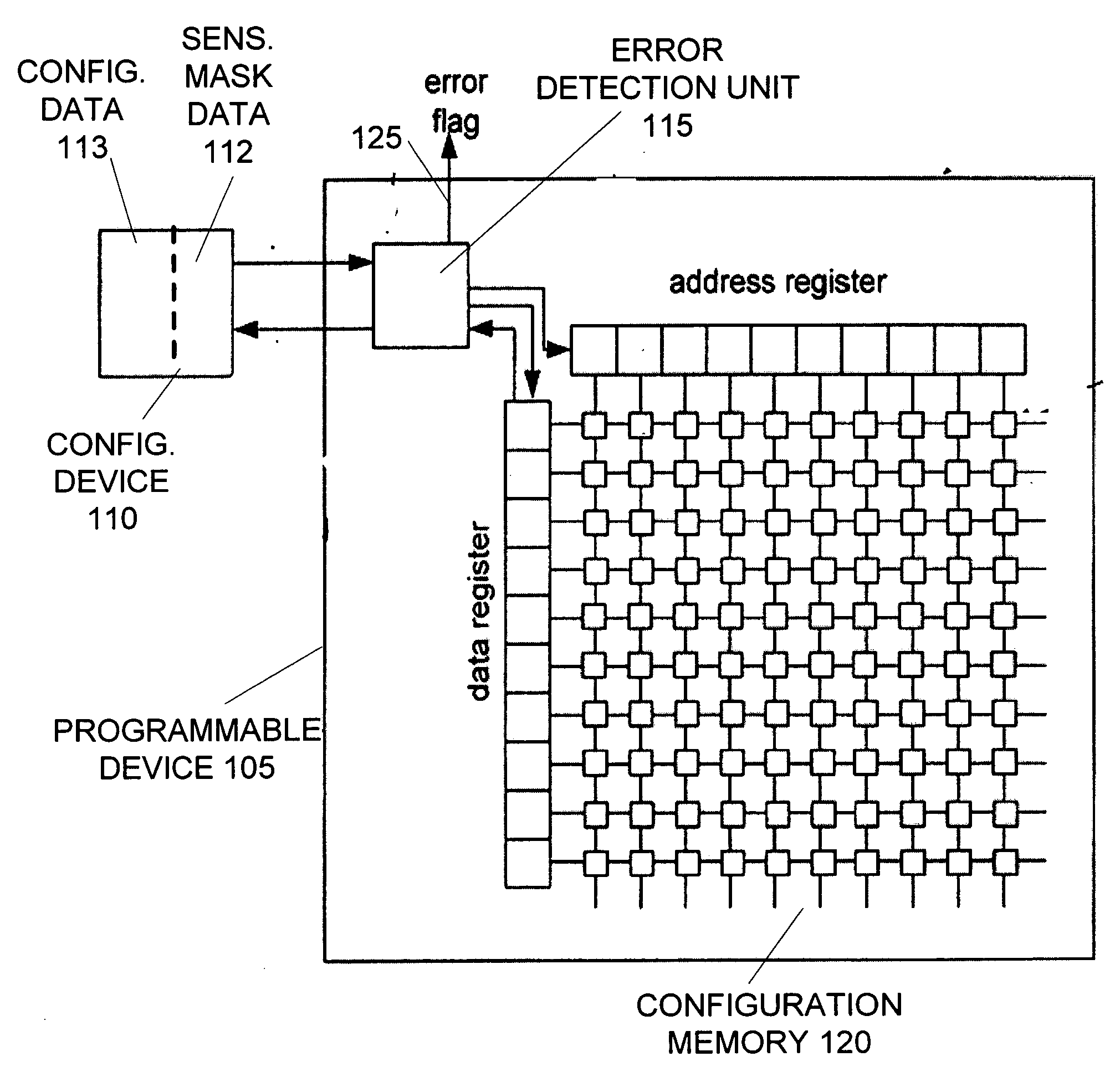
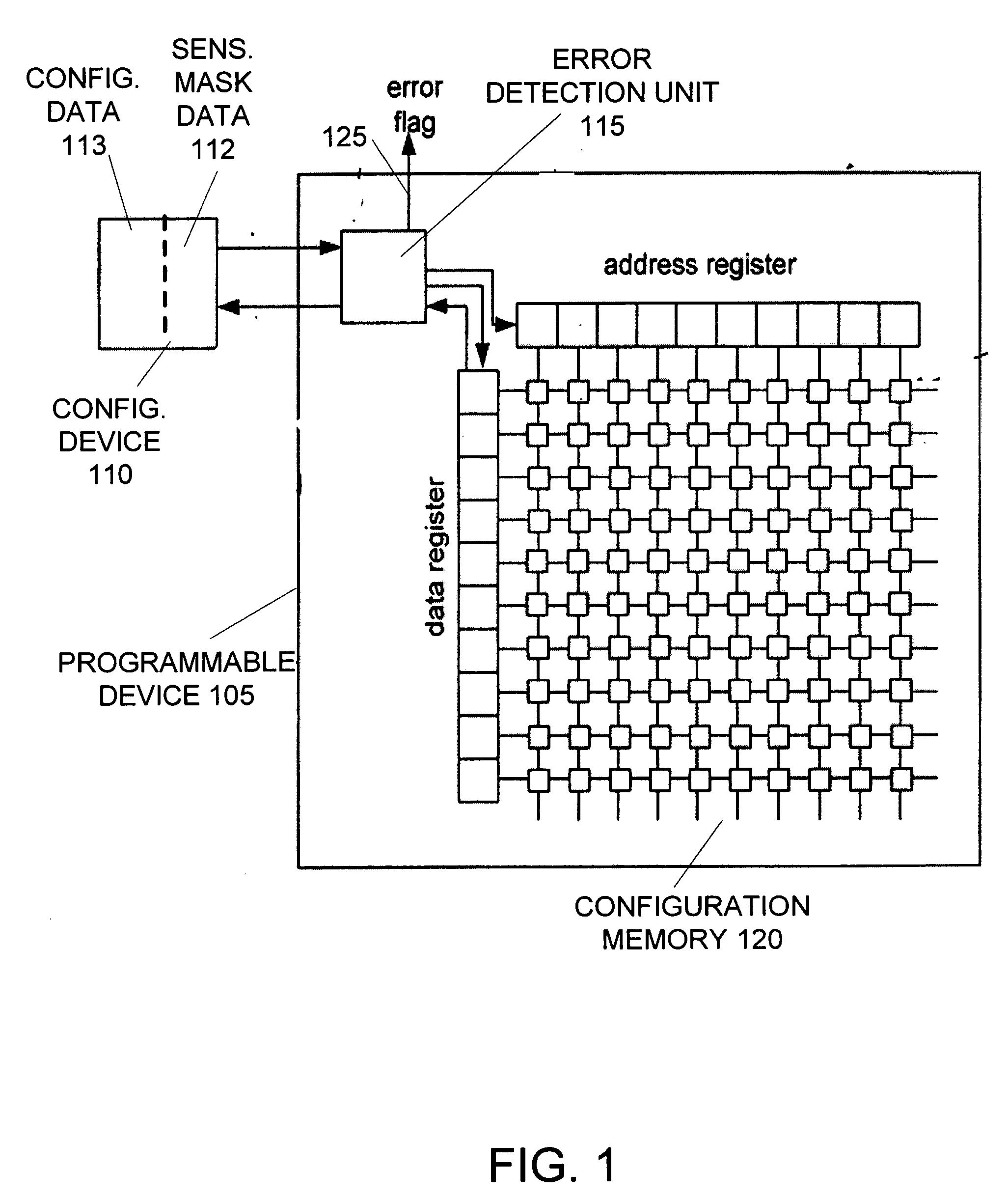
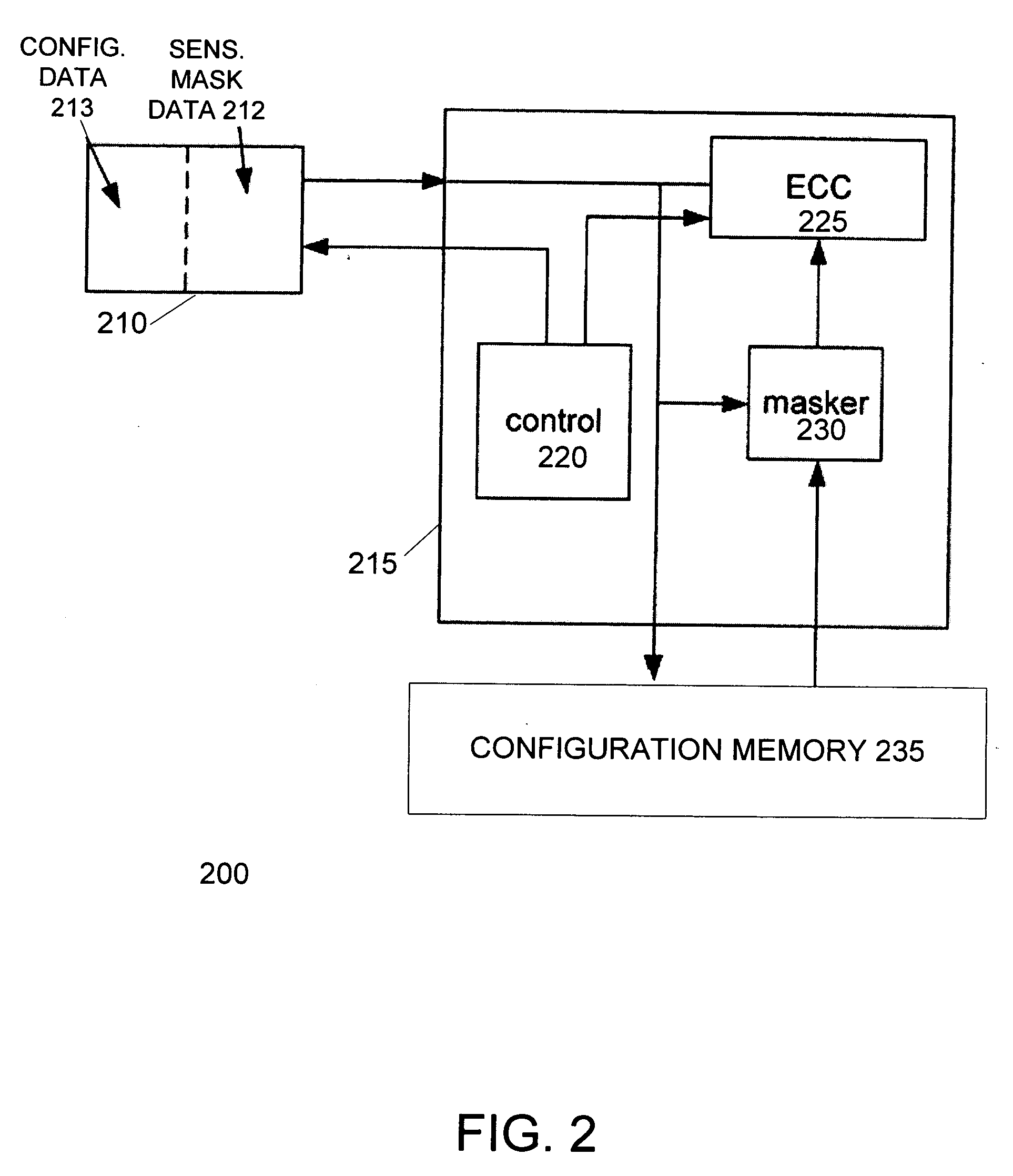
InactiveUS20070011578A1Reduces false positive memory error detectionElectronic circuit testingError detection/correctionData integrityPositive memories
A device reduces false positive memory error detections by using a masking unit and sensitivity mask data to exclude unused portions of the memory from the error detection computations. A device includes an error detection unit to read data from the memory and verify data integrity. The sensitivity mask data indicates unused portions of the memory. Unused portions of the memory may correspond with configuration data for unused portions of a programmable device. Each bit of the sensitivity mask data may indicate the usage of one or more bits of the data from the memory. In response to the mask data, the masking unit sets data from the unused portions of the memory to values that do not change the result of the error detection computations. This prevents any errors in data from the unused portions of the memory from raising an error signal.
Owner:ALTERA CORP
Memory error analysis for determining potentially faulty memory components
ActiveUS7404118B1Easy to identifyError detection/correctionStatic storageComputerized systemBad memory
Accordingly, there has been described a computer system with a plurality of memory components where individual bits from multiple words are distributed among the memory components. An error analyzer is operable to identify a memory component as potentially faulty by accessing a table mapping syndromes to memory components using generated syndromes.
Owner:ORACLE INT CORP
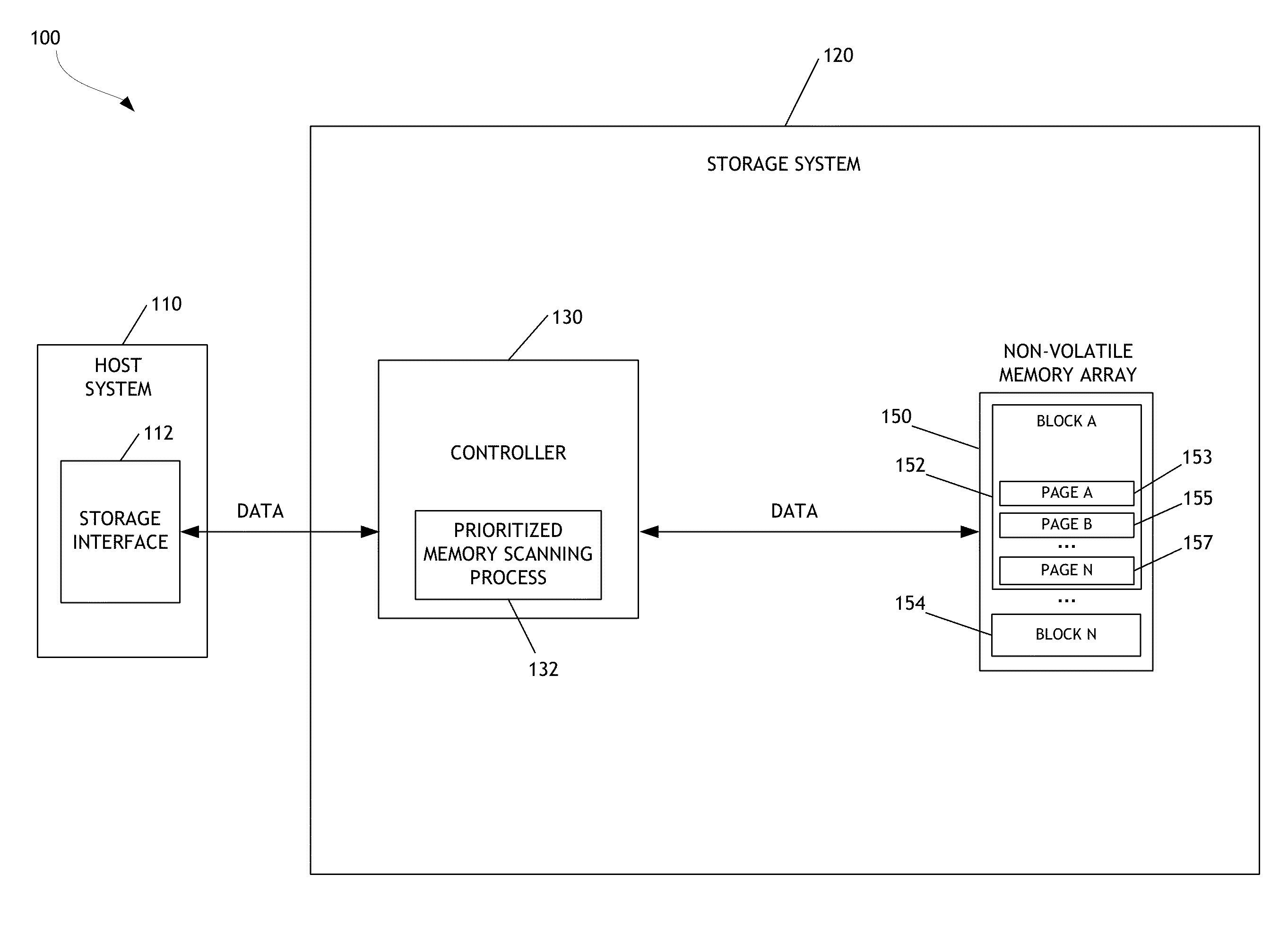
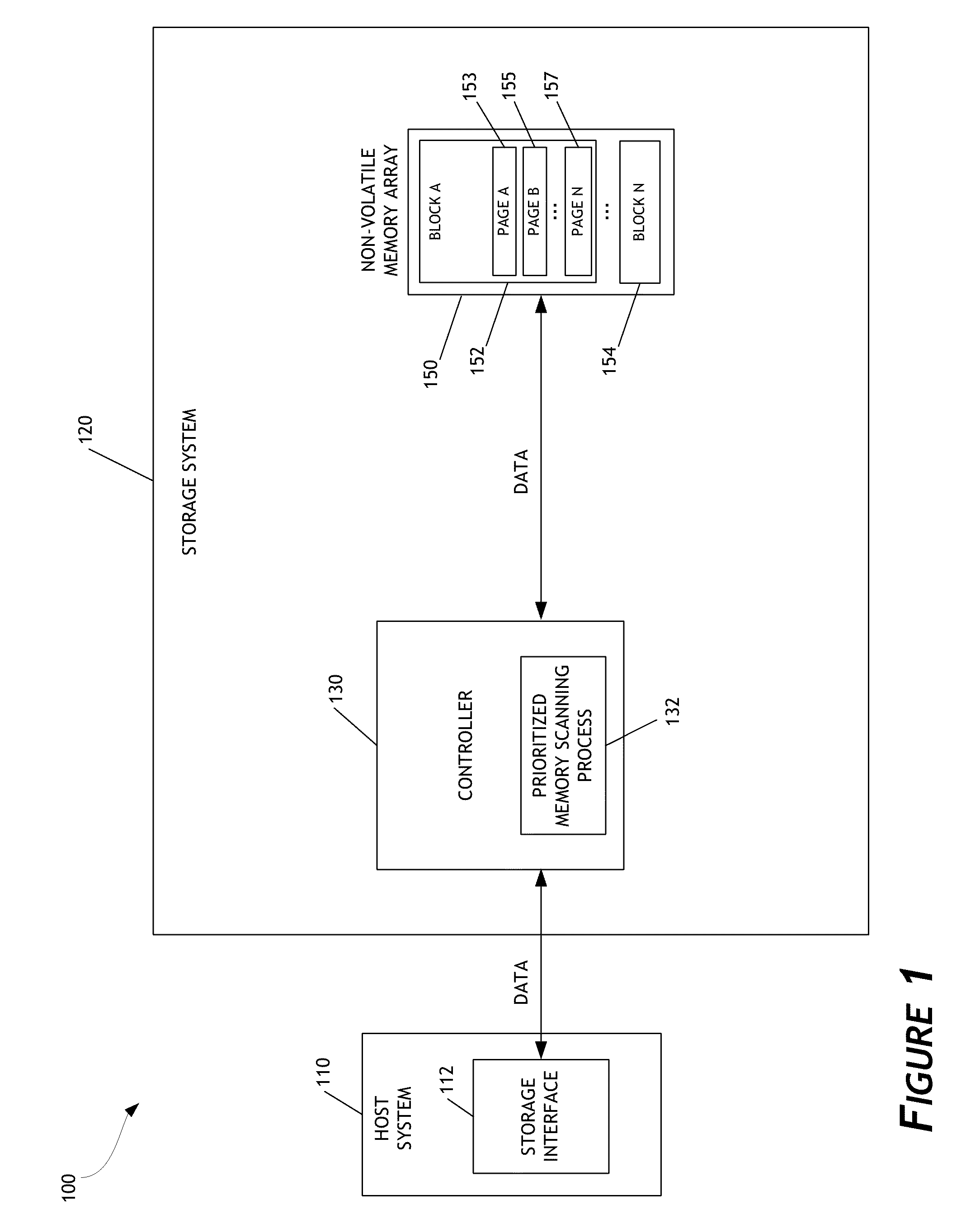
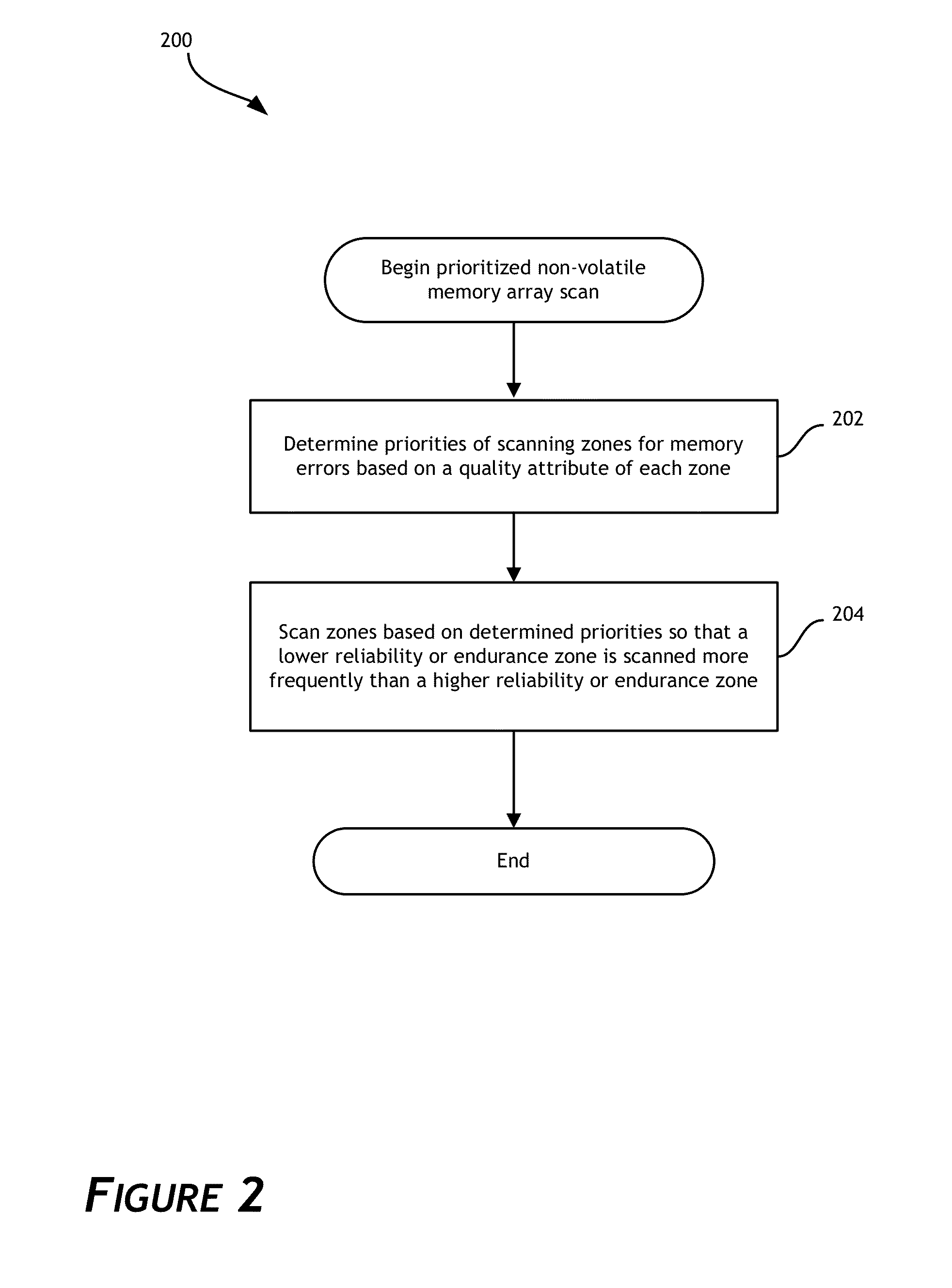
Prioritized memory scanning for data storage systems
A data storage system configured to perform prioritized memory scanning for memory errors is disclosed. In one embodiment, the data storage system prioritizes scanning for memory errors based on a quality attribute of pages or zones of a non-volatile memory array. Pages or zones having quality attributes that reflect a lower level of reliability or endurance than other pages or zones are scanned more frequently for memory errors. When memory errors are discovered, the quality attribute of pages or zones can be adjusted to reflect a lower level of reliability or endurance. In addition, stored data can be recovered before it may become permanently lost and before a host system reads the stored data. Improved performance of the data storage system is thereby attained.
Owner:WESTERN DIGITAL TECH INC
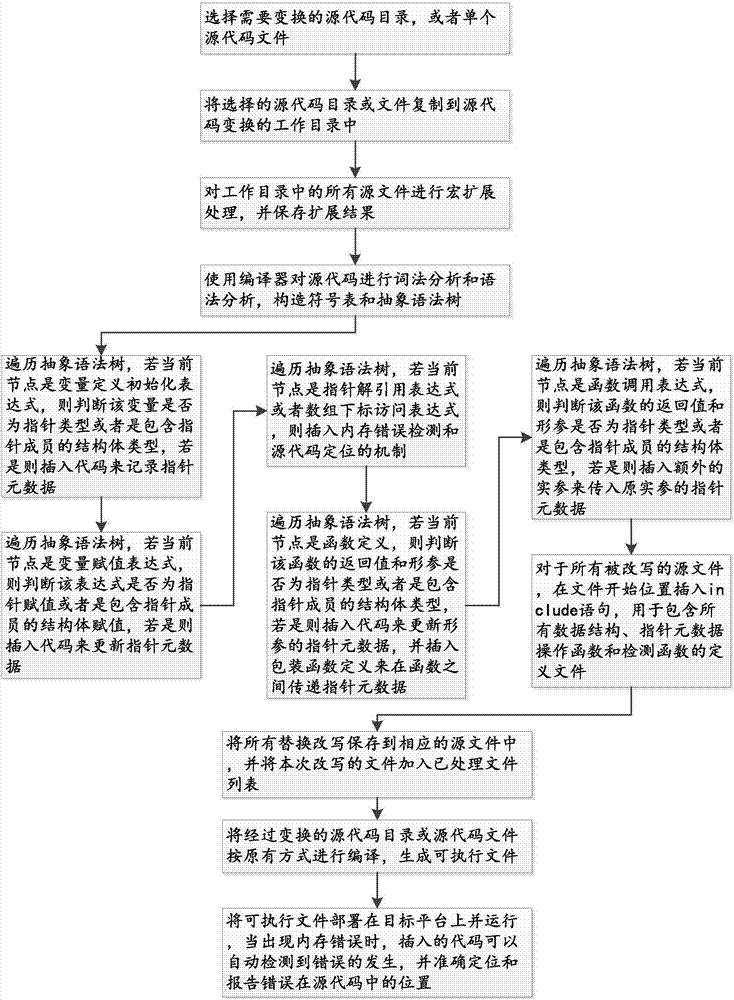
Automatic detection and positioning method for memory error in source code
ActiveCN106940654AEfficient searchImprove universalityProgram controlMemory systemsLexical analysisComputer compatibility
The invention provides an automatic detection and positioning method for a memory error in a source code. The method comprises the steps of firstly using a compiler for carrying out lexical analysis and grammatical analysis on the source code, and constructing a symbol table and an abstract syntax tree; then through traversing the abstract syntax tree, carrying out source code transformation on a node which may produce the memory error, and finally compiling and executing the source code subjected to transformation, wherein a program can automatically judge the occurrence of the memory error, and accurately reports a source code position corresponding to the error. The automatic detection and positioning method for the memory error in the source code provided by the invention can be used for accurately automatically detecting and positioning the memory error so as to realize more comprehensive error detection, better compatibility, better platform universality, more accurate source code positioning, and higher runtime performance and efficiency, so that the quality of software and the efficiency of software maintenance are improved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Method and system for detecting memory problems in user programs
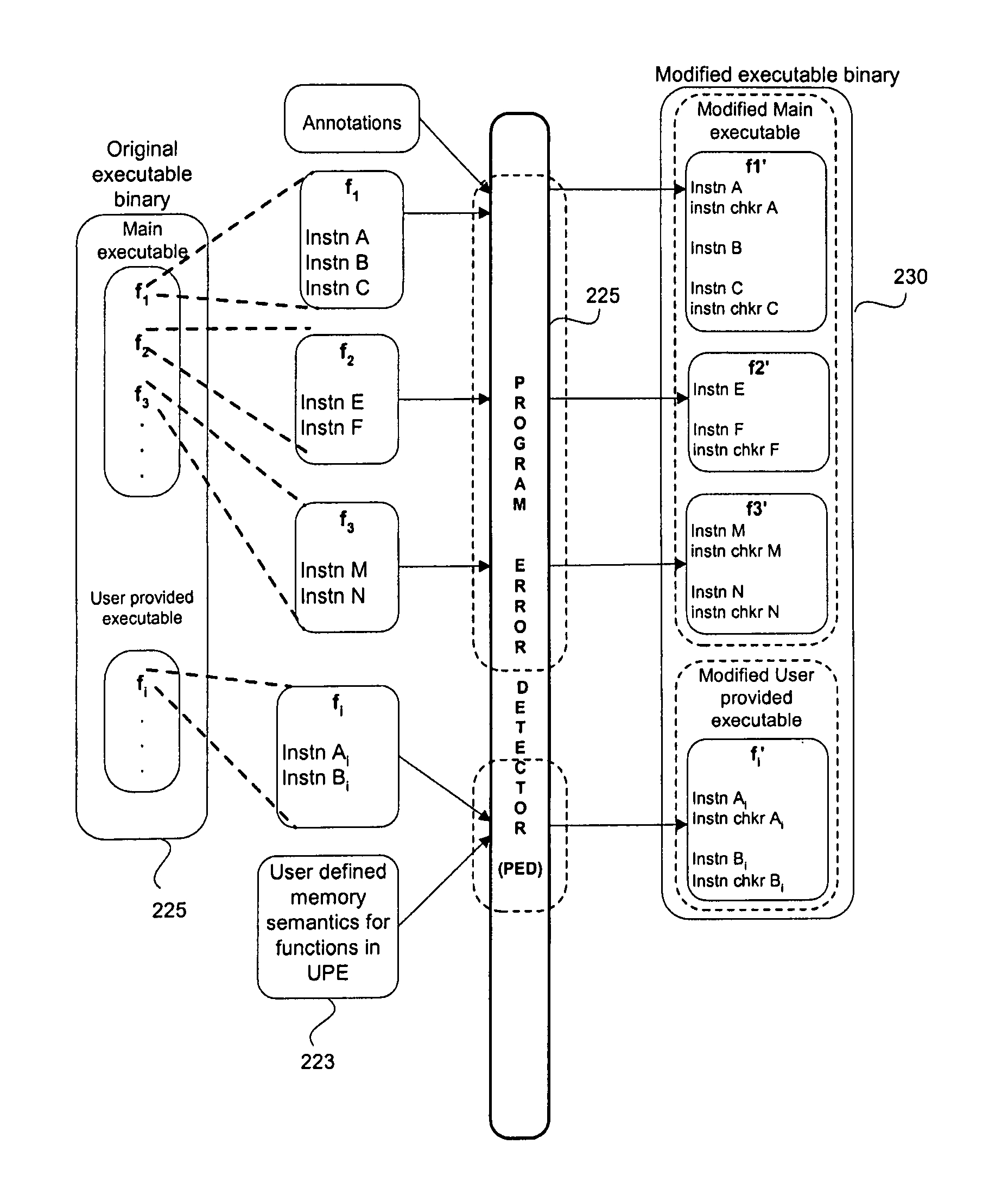
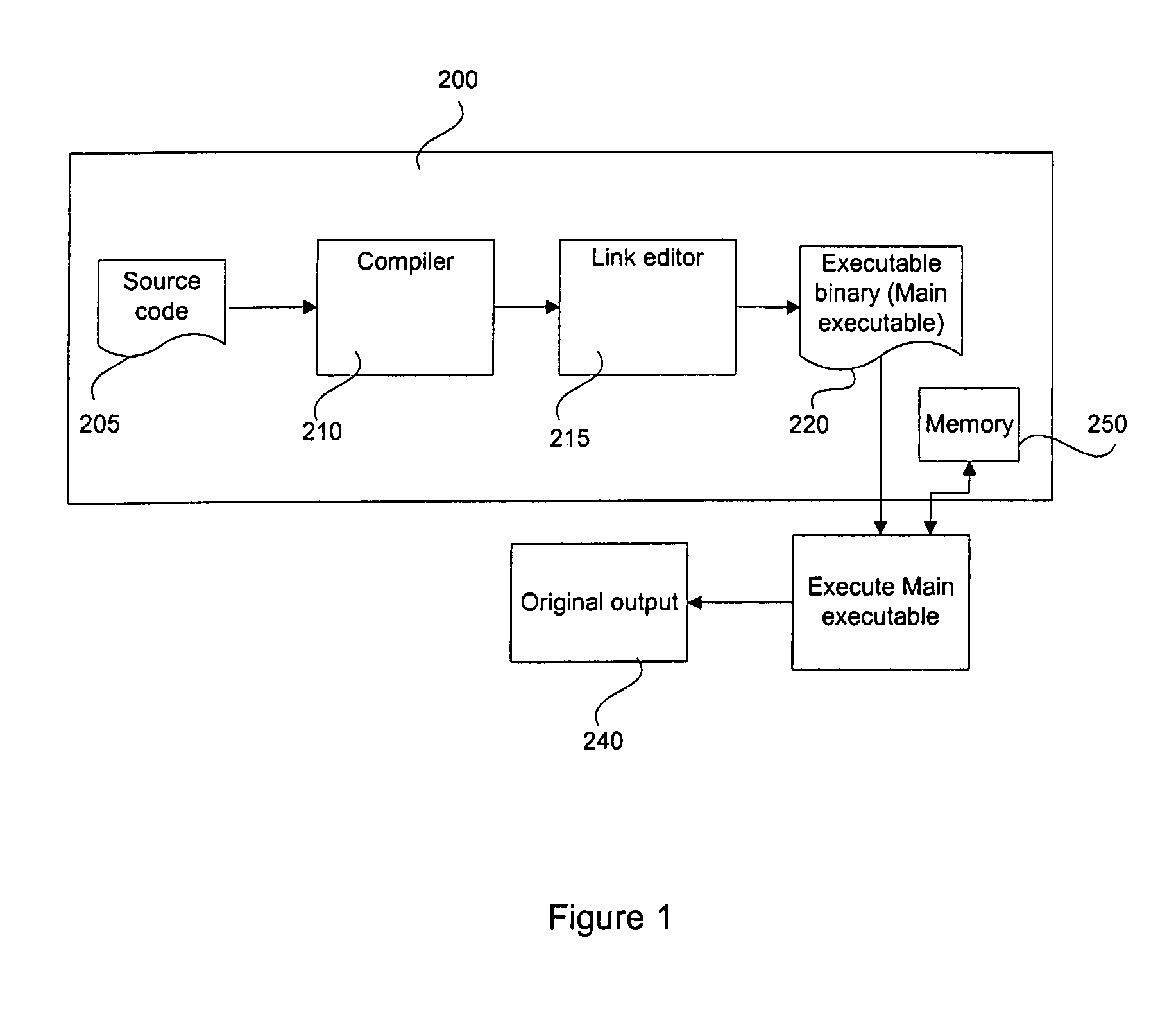
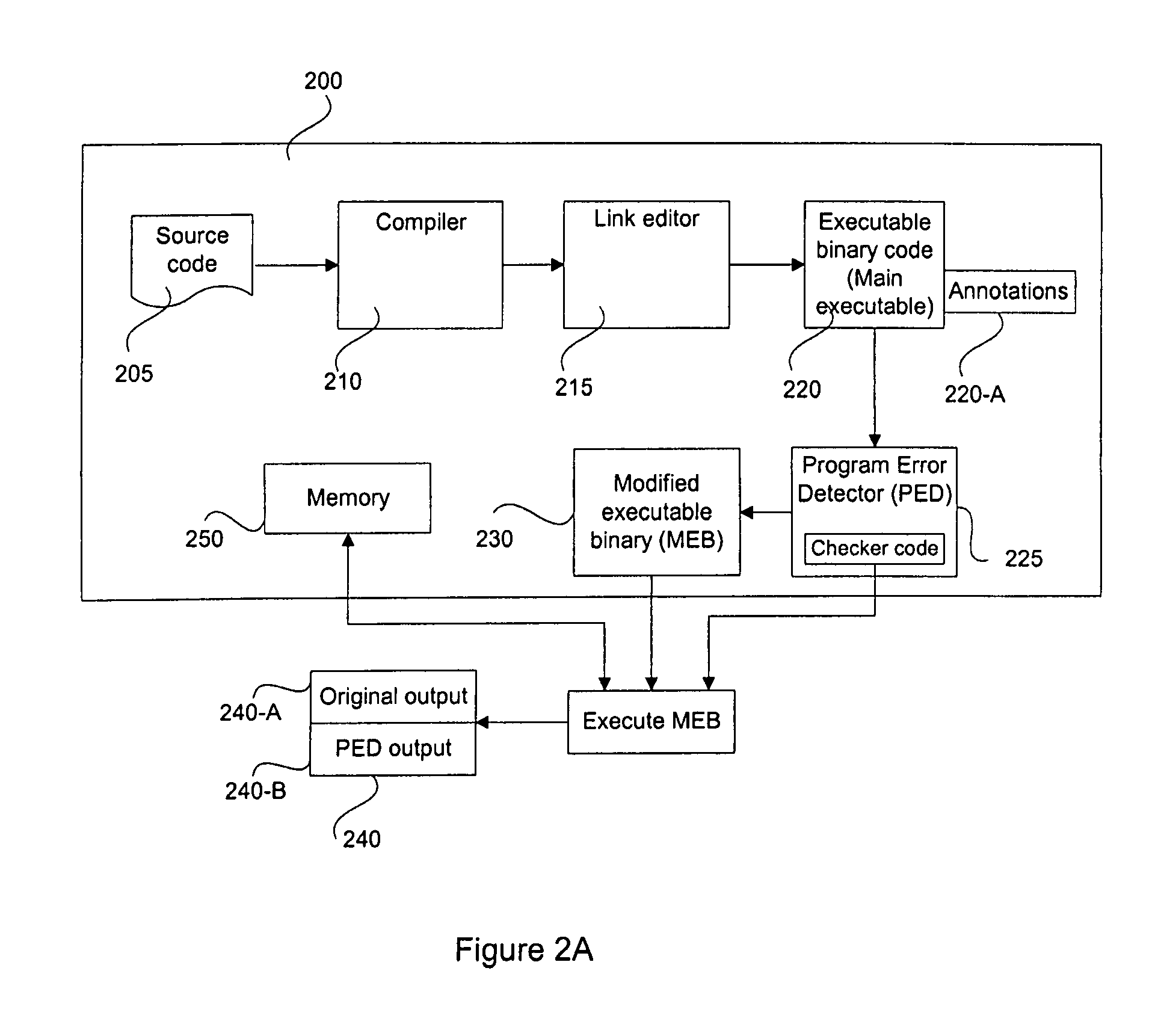
ActiveUS8060869B1Efficient identificationEfficient detectionError detection/correctionMemory adressing/allocation/relocationSoftware bugGuideline
A method and system for providing a binary instrumentation tool to detect memory problems in a runtime application executing on a computer system includes identifying one or more functions or statements in the runtime application. A plurality of compiler annotations defining essential functional characteristic data of each of the plurality of functions is generated by a compiler when compiling the user program from source code to an executable binary code. A program error detector is configured to provide a checker code based on guidelines provided by of the plurality of compiler annotations associated with the function. The program error detector generates a modified function code for the identified function by inserting the checker code into a function code for the corresponding function. A modified executable binary code for the runtime application is then generated by replacing the function code for the function with the corresponding modified function code. When the modified executable binary code is run, the checker code associated with the function invokes a checker. The invoked checker provides performance data analysis that allows identification of program errors including memory errors in the runtime application.
Owner:ORACLE INT CORP
Memory failure recovery method, information processing apparatus, and program
ActiveUS20100318845A1Non-redundant fault processingRedundant operation error correctionRecovery methodInformation processing
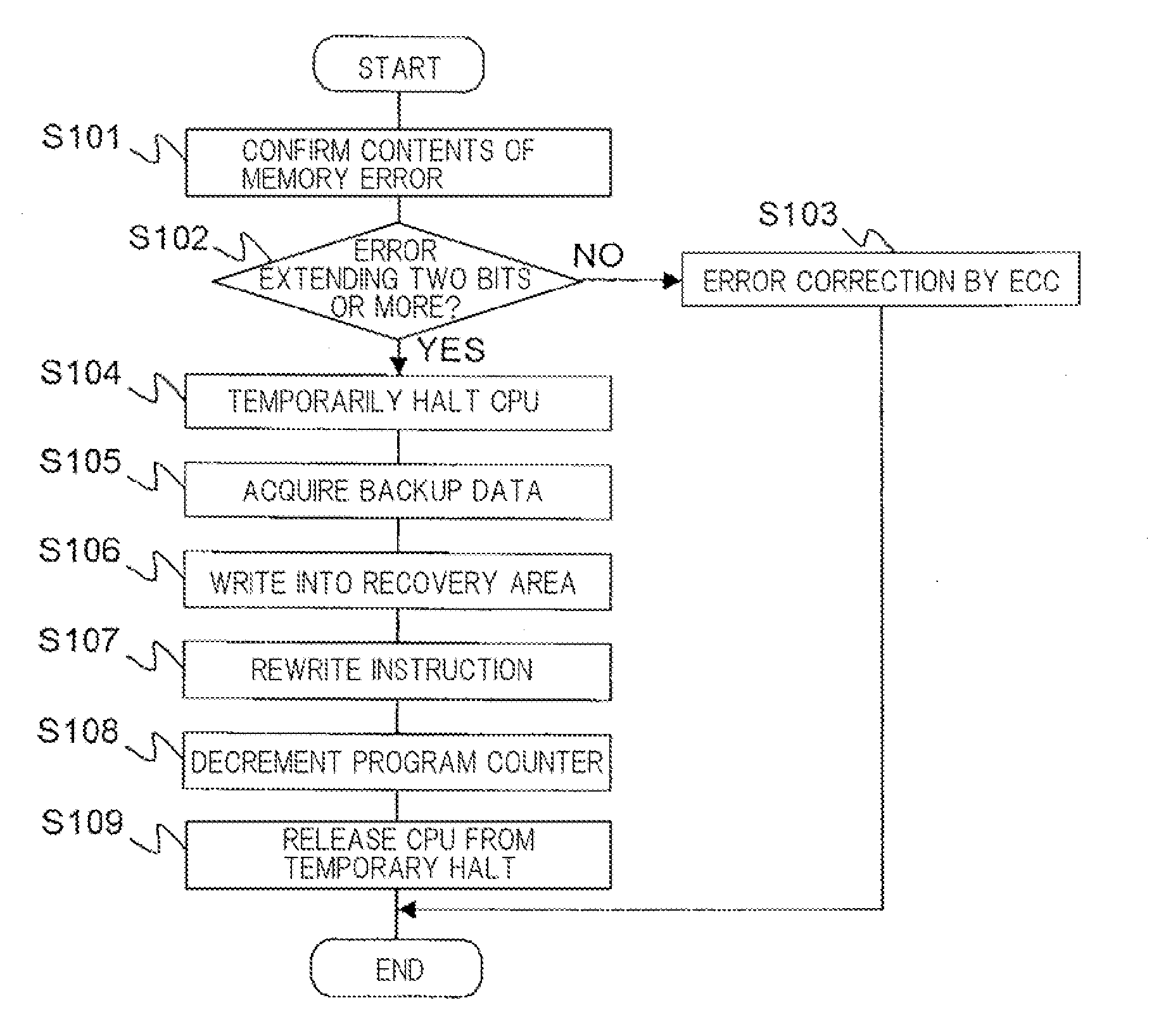
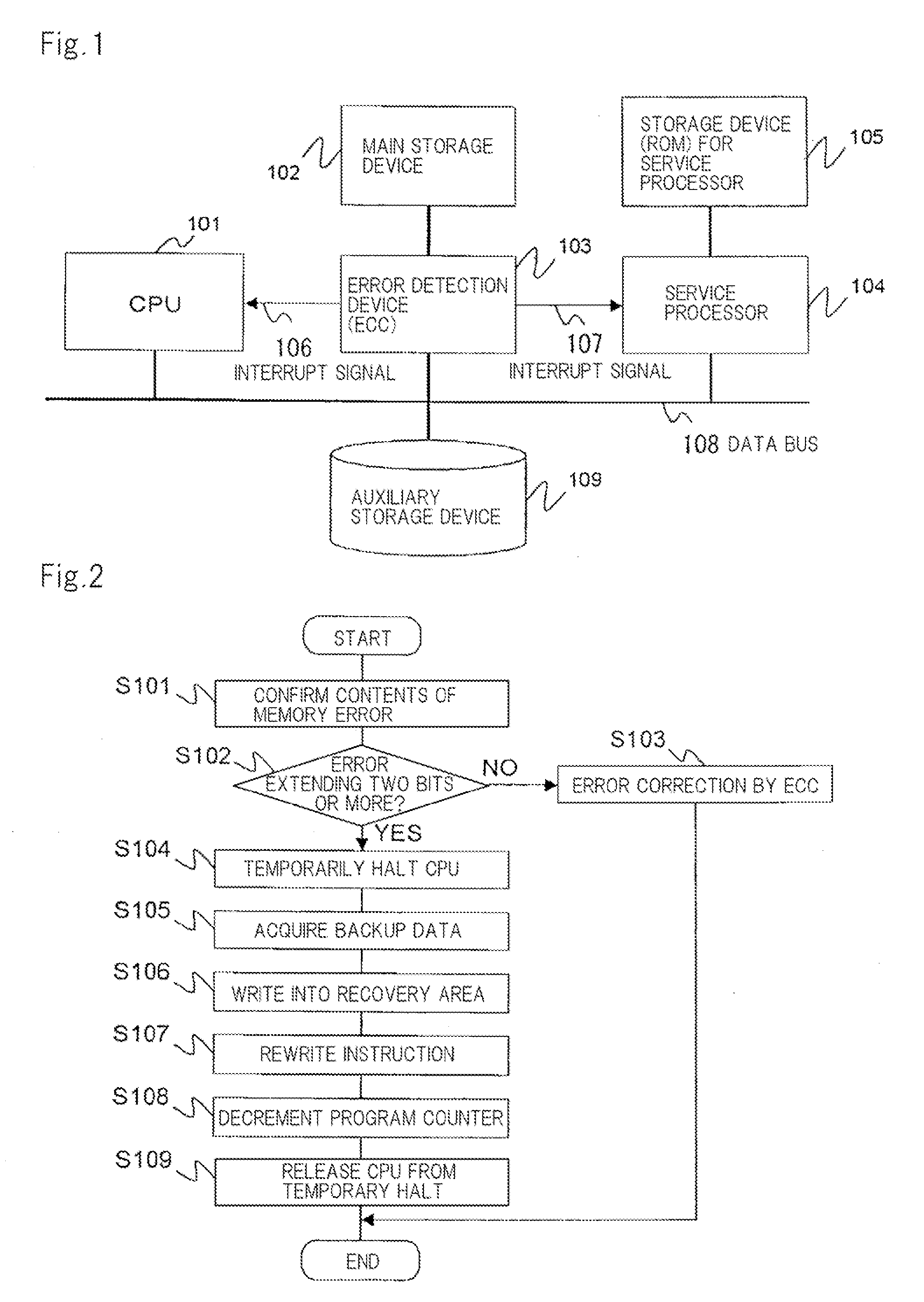
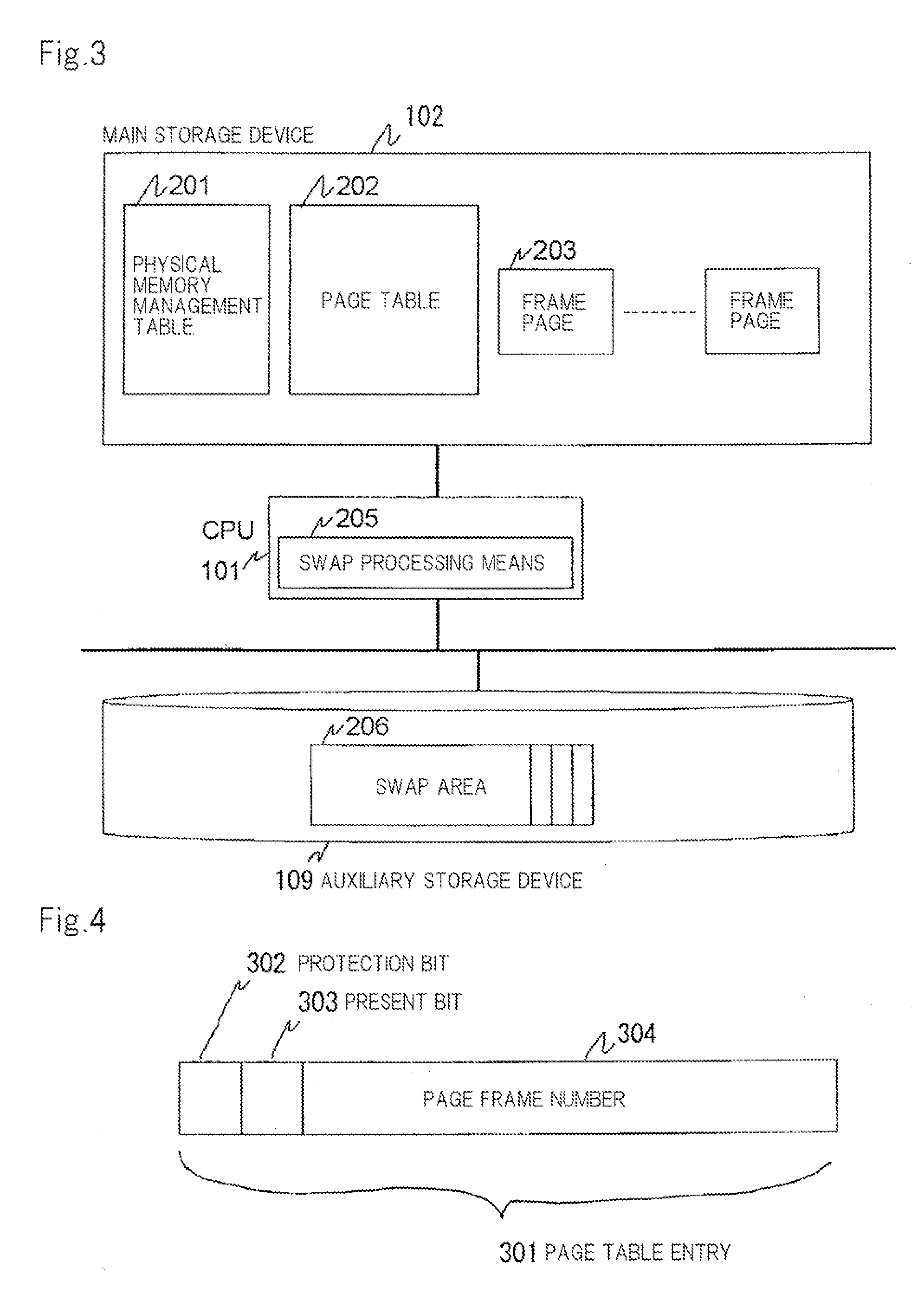
Upon occurrence of a memory error which is difficult to correct, CPU interrupts a process under execution in response to interrupt signal output from error detection device, and transfers the control to the OS. The OS references attributes of a page stored in a page frame which has suffered the memory error. When read-only is indicated, physical memory management table is updated to set the page frame, which has suffered the error, into a disabled state. Then, page table is updated such that a virtual page stored in the page frame which has suffered the error is not assigned to any page frame, followed by resumption of the execution of the process. After execution of the process is resumed, a page fault process is invoked to store the virtual page which has encountered the memory error in another normal page frame.
Owner:NEC CORP
Memory error detection reporting
ActiveUS7240277B2Reduce impactLower potentialMemory adressing/allocation/relocationStatic storageCourse of actionMemory controller
Owner:TEXAS INSTR INC
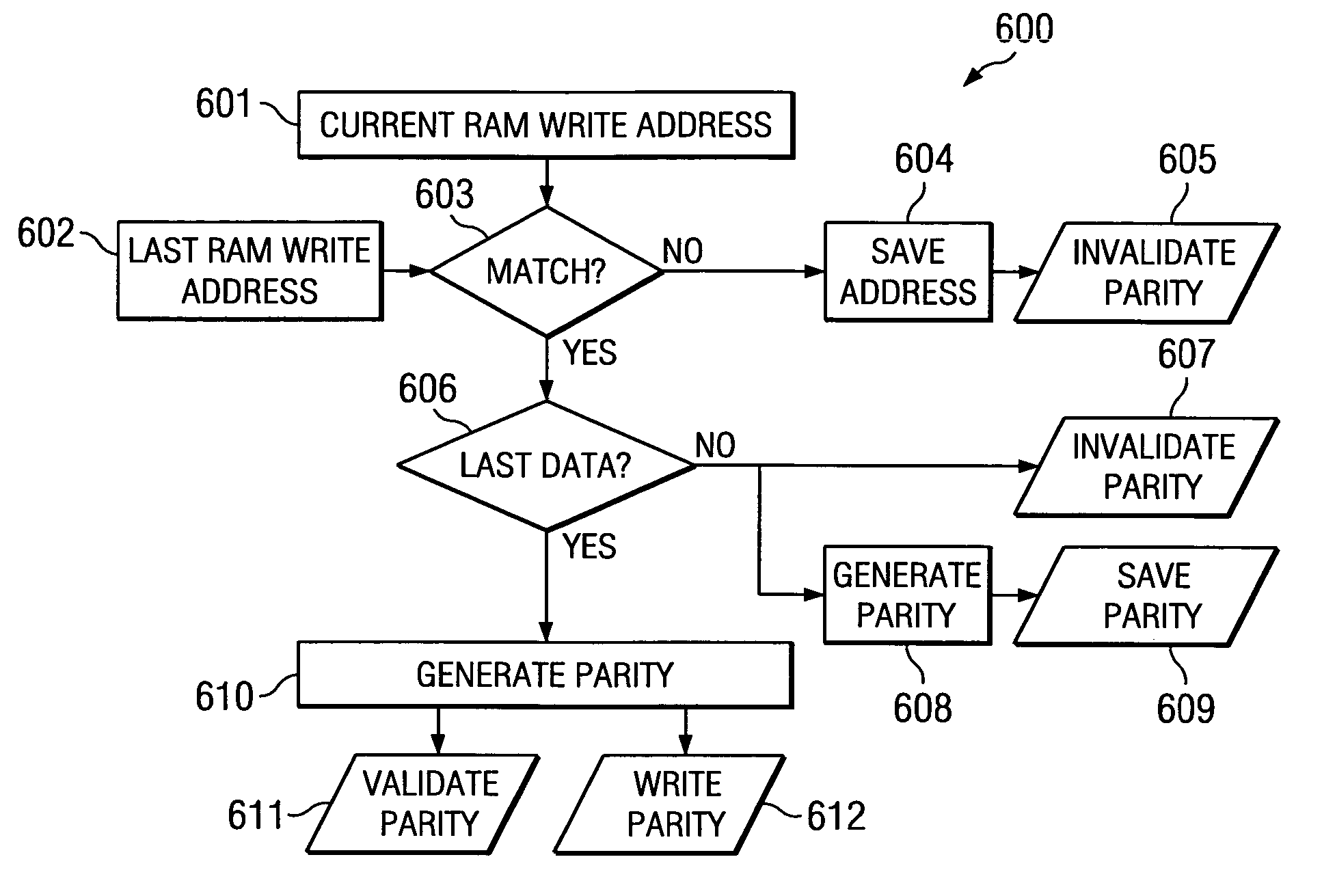
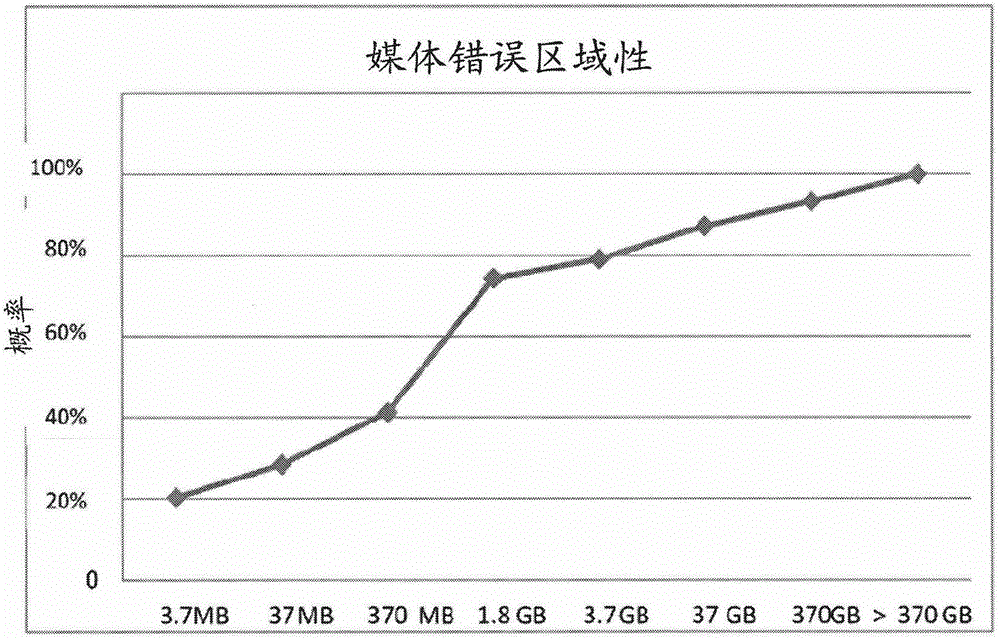
Compression of content entries in storage for replacing faulty memory cells
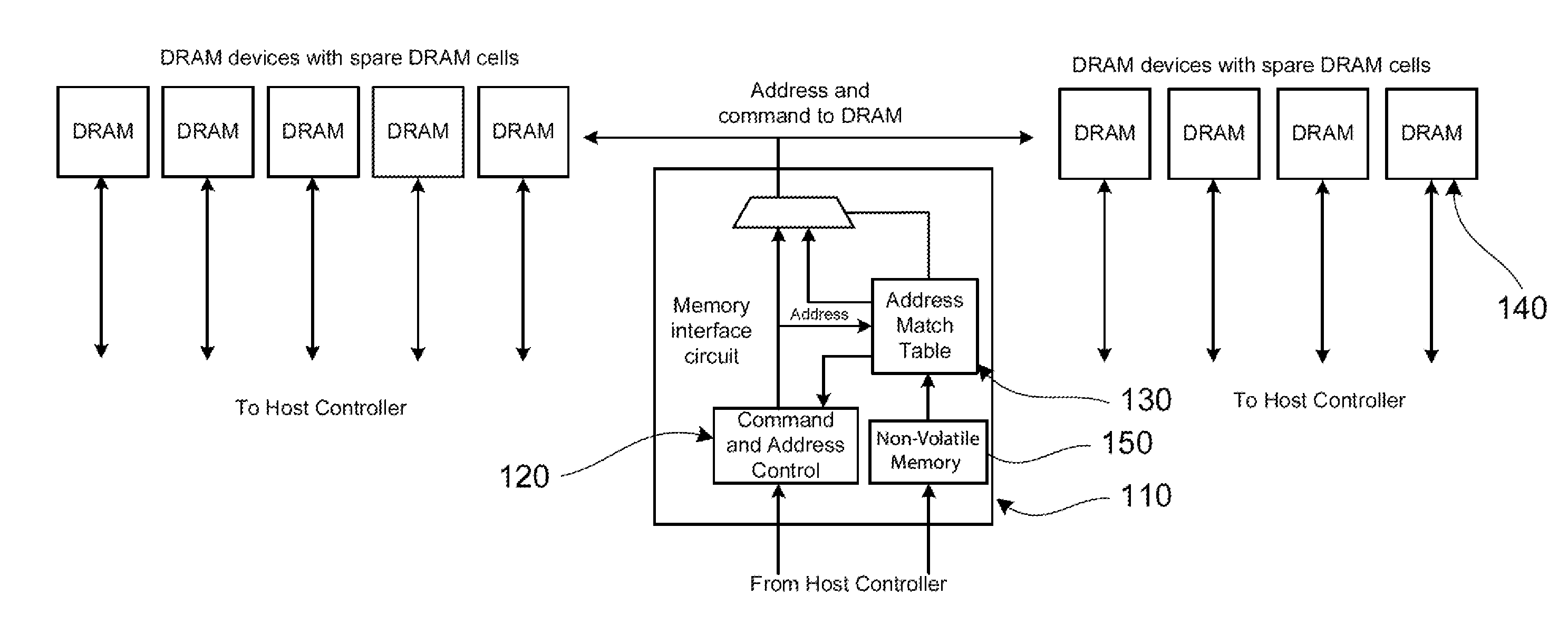
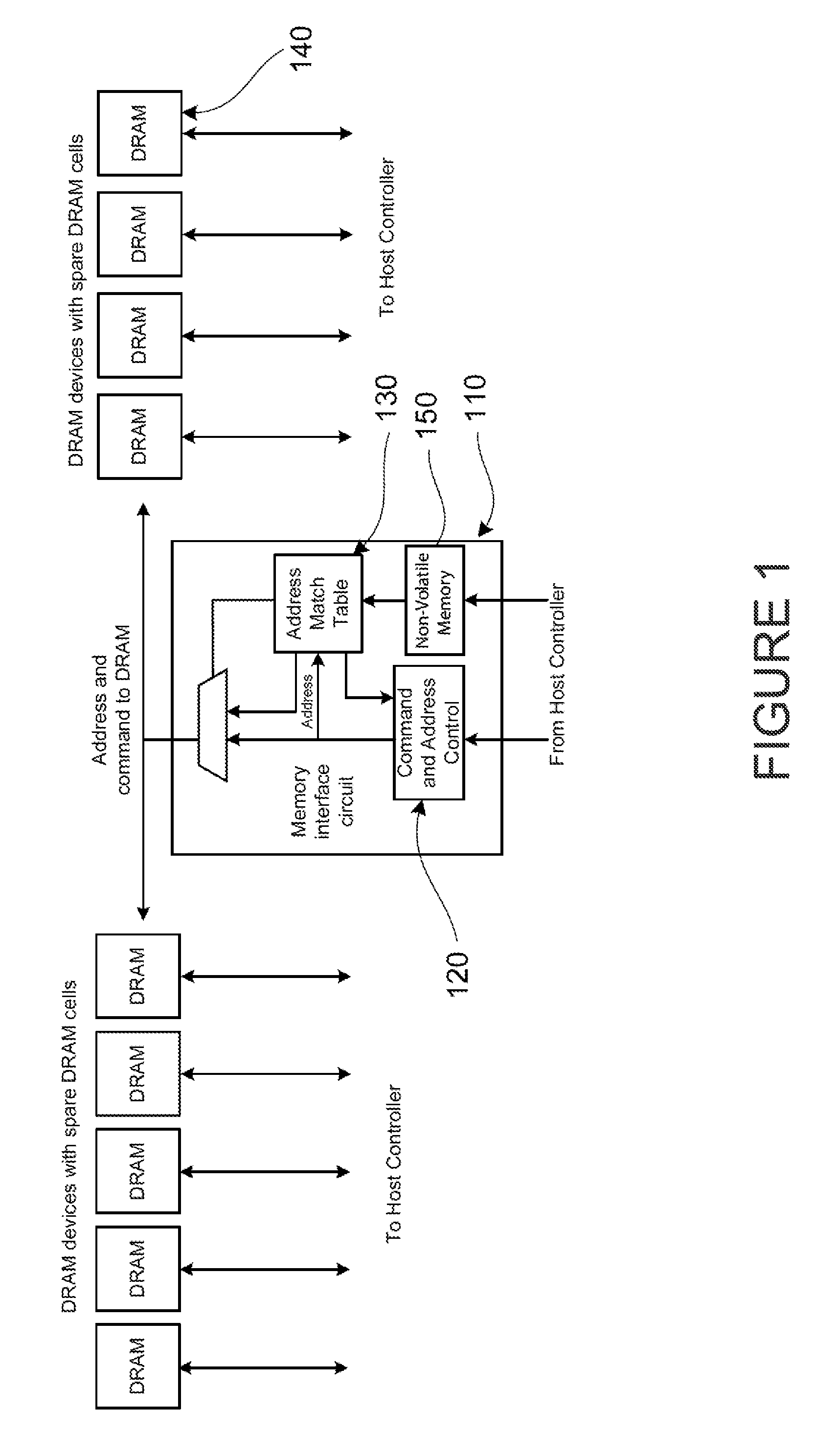
A method of manufacturing a dynamic random access memory device is provided. The method includes testing a DRAM device using a testing process. The method includes identifying, under control by a computing device, a plurality of bad memory cells from the DRAM device and determining a list of addresses associated with the plurality of bad memory cells. The method includes sorting the list of addresses in either ascending or descending order and subjecting the information from the sorted list of address to a compression process, under control by the computing device, to provide a compressed format including a first content entry in the sorted list and a series of off-set values as provided by a recurrence relationship. The method also stores the compressed format into a non-volatile memory.
Owner:RAMBUS INC
Systematic mitigation of memory errors
ActiveUS20120137167A1Mitigating apparent software errorDetecting errorDetecting faulty computer hardwareNon-redundant fault processingComputerized systemBad memory
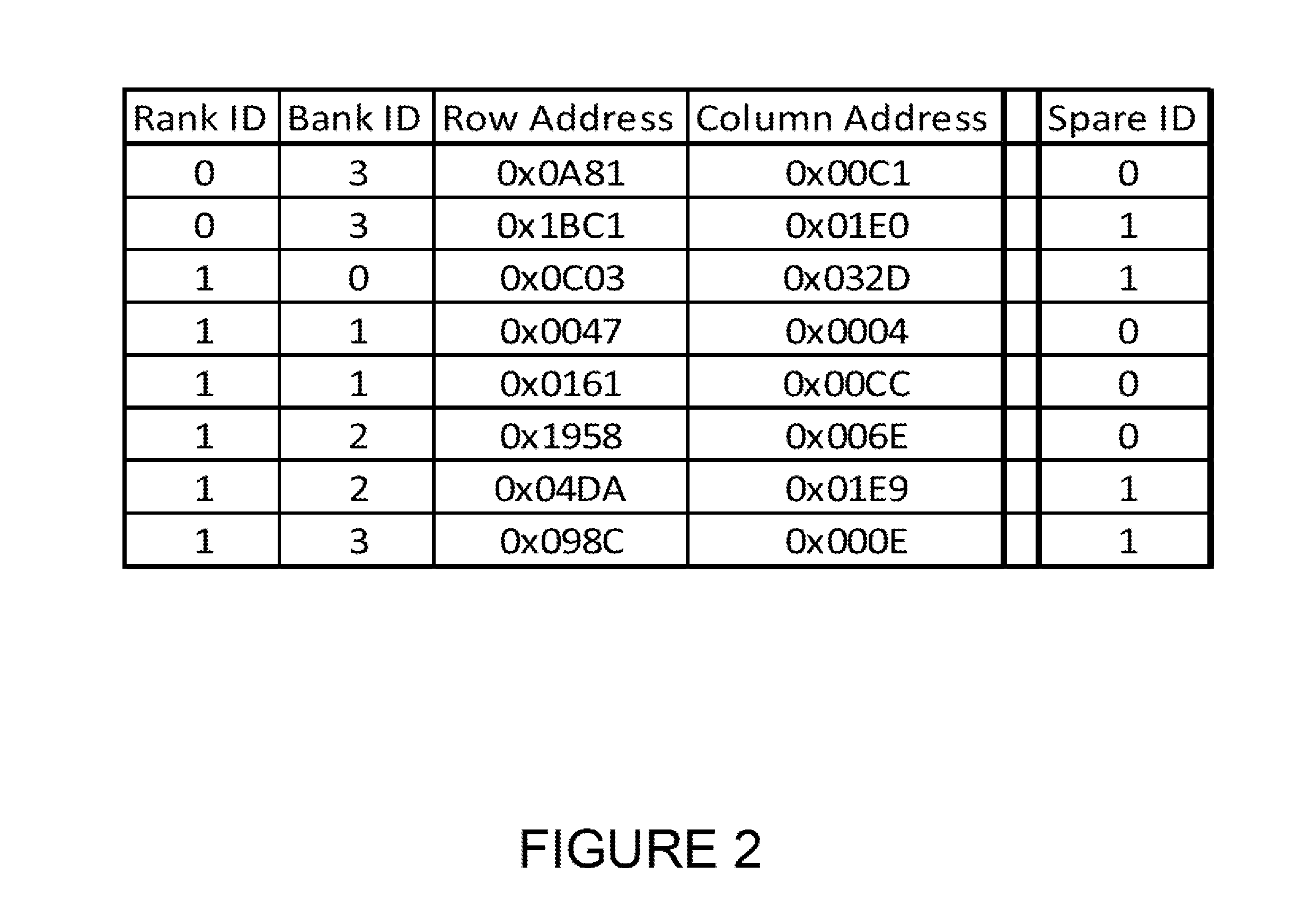
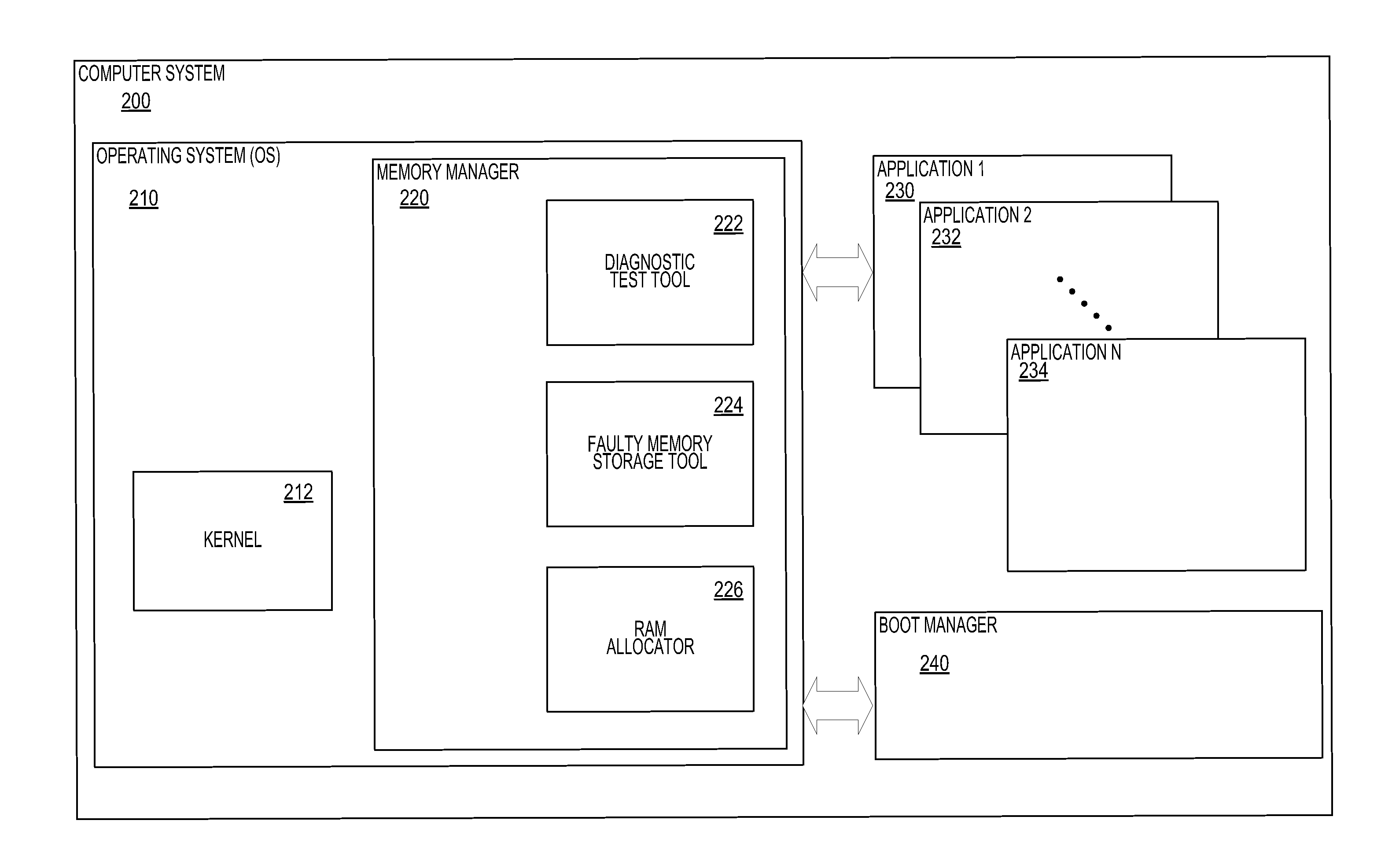
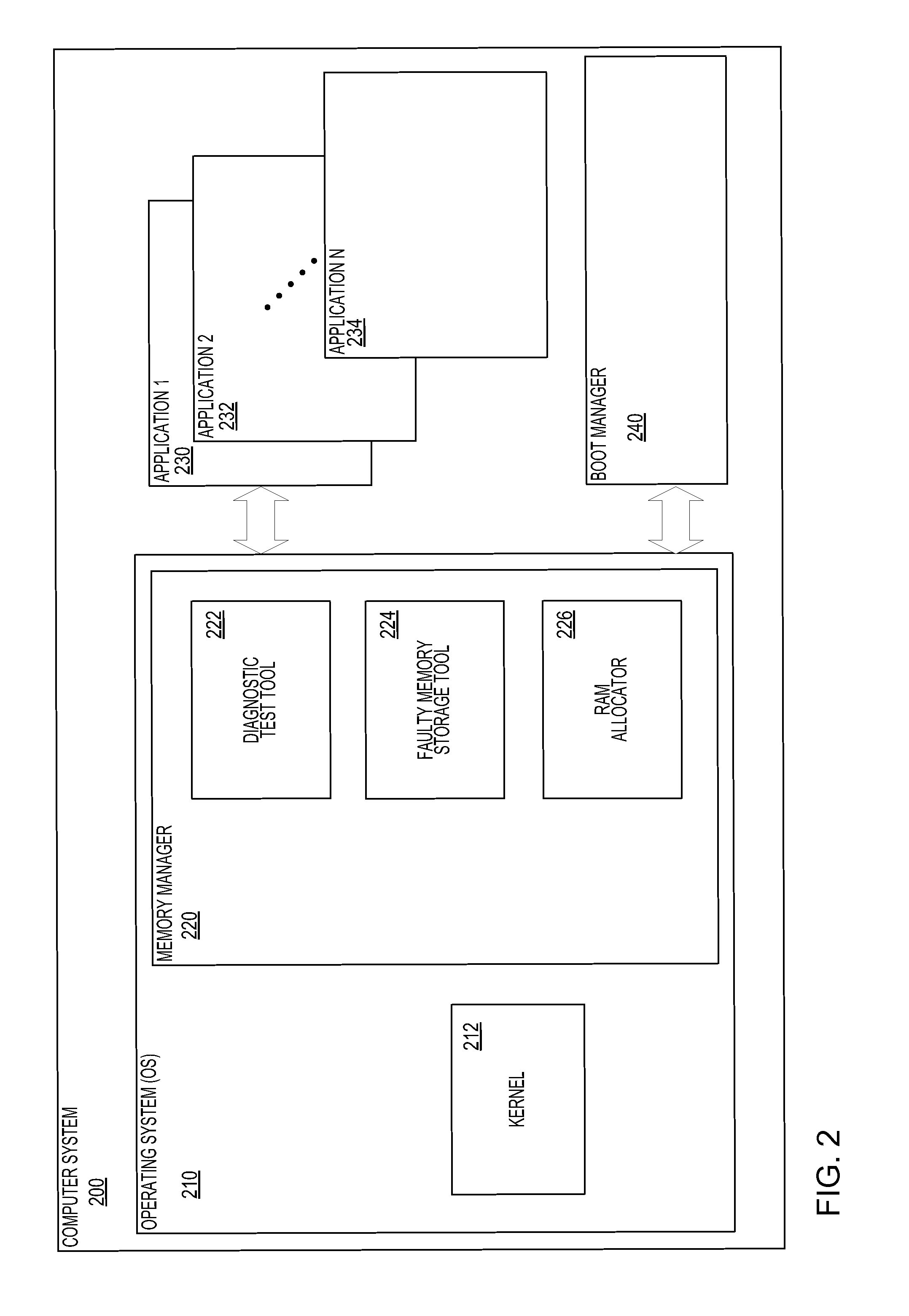
A system and method for mitigating memory errors in a computer system. Faulty memory is identified and tested by a memory manager of an operating system. The memory manager may perform diagnostic tests while the operating system is executing on the computer system. Regions of memory that are being used by software components of the computer system may also be tested. The memory manager maintains a stored information about faulty memory regions. Regions are added to the stored information when they are determined to be faulty by a diagnostic test tool. Memory regions are allocated to software components by the memory manager after checking the stored information about faulty memory regions. This ensures a faulty memory region is never allocated to a software component of the computer system.
Owner:MICROSOFT TECH LICENSING LLC
System and method of recovering from soft memory errors
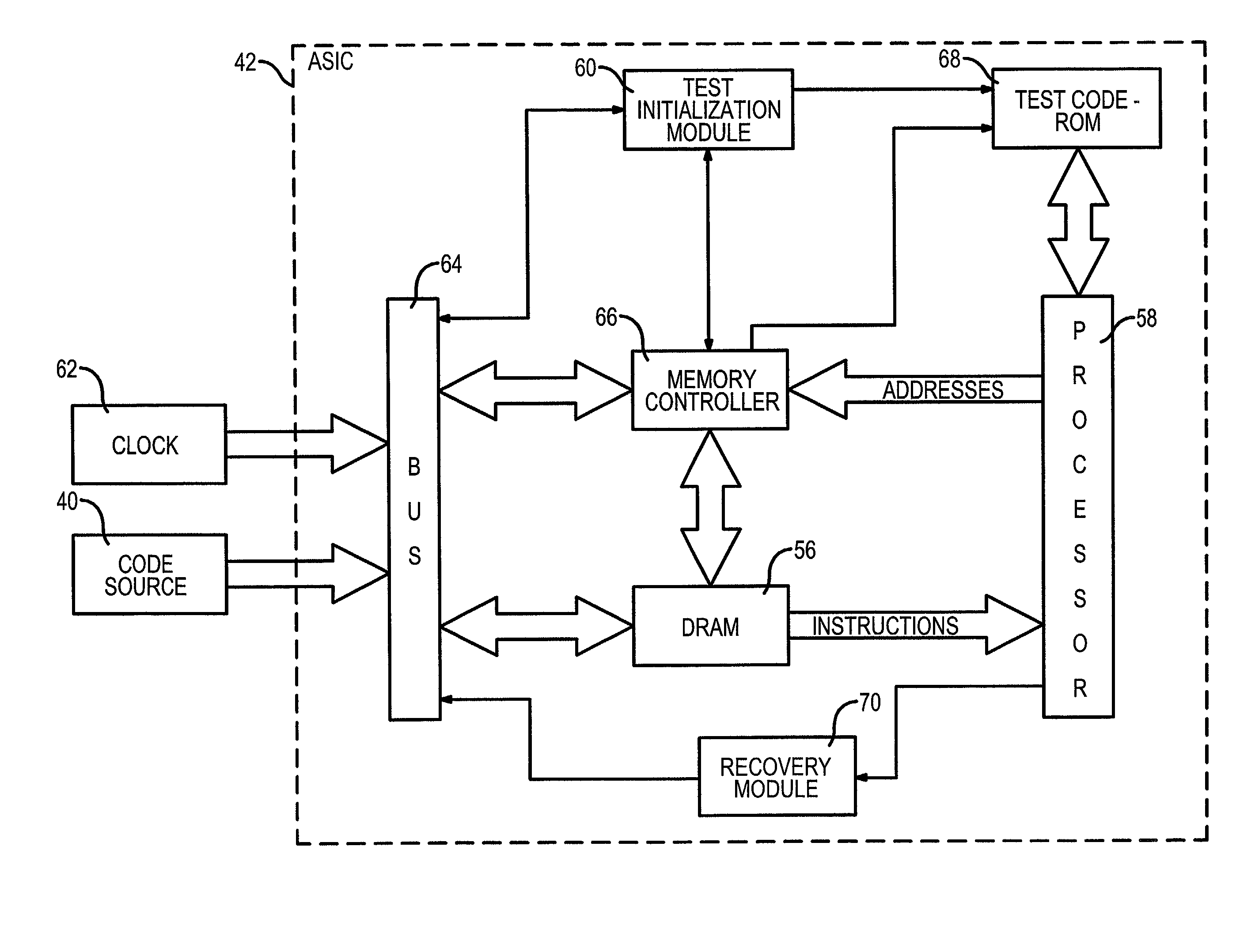
InactiveUS6971051B2Performance penaltyIncreased power consumptionDigital storageApplication-specific integrated circuitBad memory
Managing volatile storage of information, such as executable code within dynamic random access memory (DRAM) embedded within an application specific integrated circuit (ASIC), includes systematically checking the contents of the volatile memory during periods of extended inactivity. Volatile memory checking routines may be initiated on the basis of time, on the basis of a specific event, or on a combination of timing and event occurrences. If a specific error condition is detected, the device in which the volatile memory resides may be automatically reinitialized, so that the corrupt executable code is not used. The information management techniques may be extended to other types of semi-permanent memory i.e., memory that is susceptible to losses in the form of soft errors.
Owner:AVAGO TECH INT SALES PTE LTD
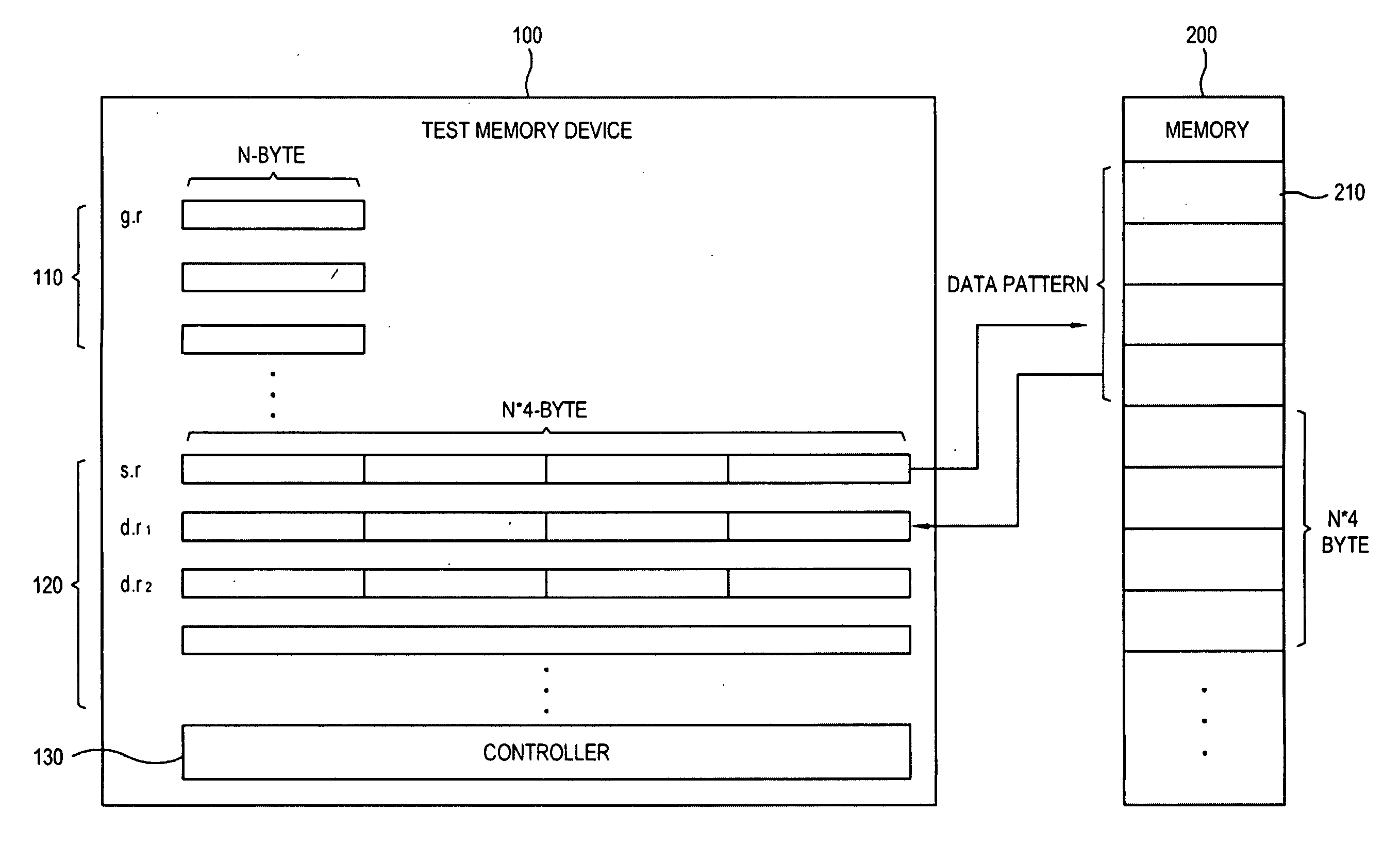
Memory test device and memory test method
InactiveUS20090307544A1Reduce test timeShorten test timeDetecting faulty computer hardwareDigital storageTest fixtureTest facility
A memory test device, including a universal register to conduct an operation by a predetermined universal command language; an extension register having a larger capacity than the universal register and to conduct an operation by a predetermined extension command language; and a controller to write a predetermined test pattern in an external memory using the extension command language, to read the test pattern written in the memory, to determine the identity of the written test pattern and the read test pattern, and to determine a presence of an error in the memory using the universal command language.
Owner:SAMSUNG ELECTRONICS CO LTD
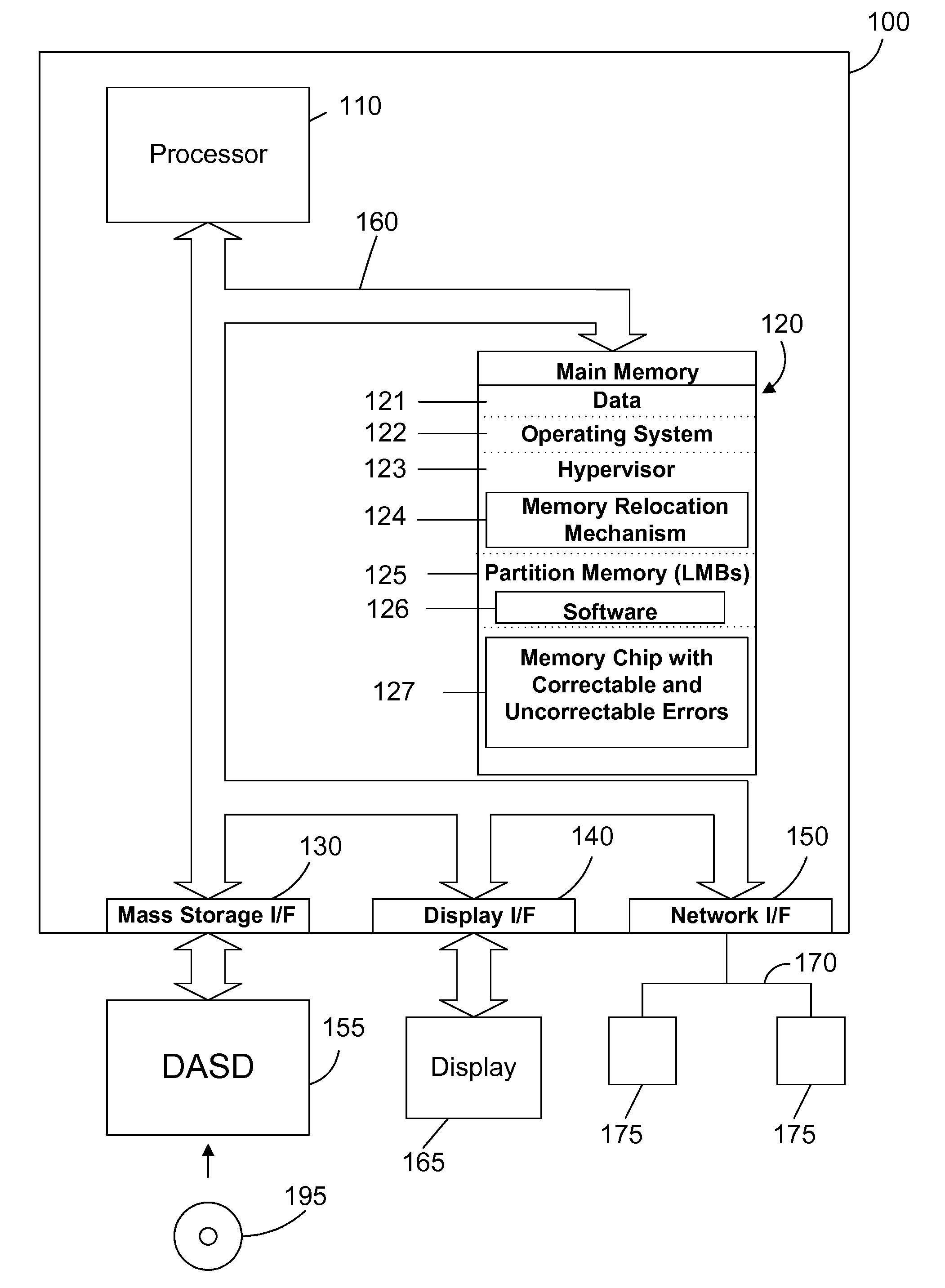
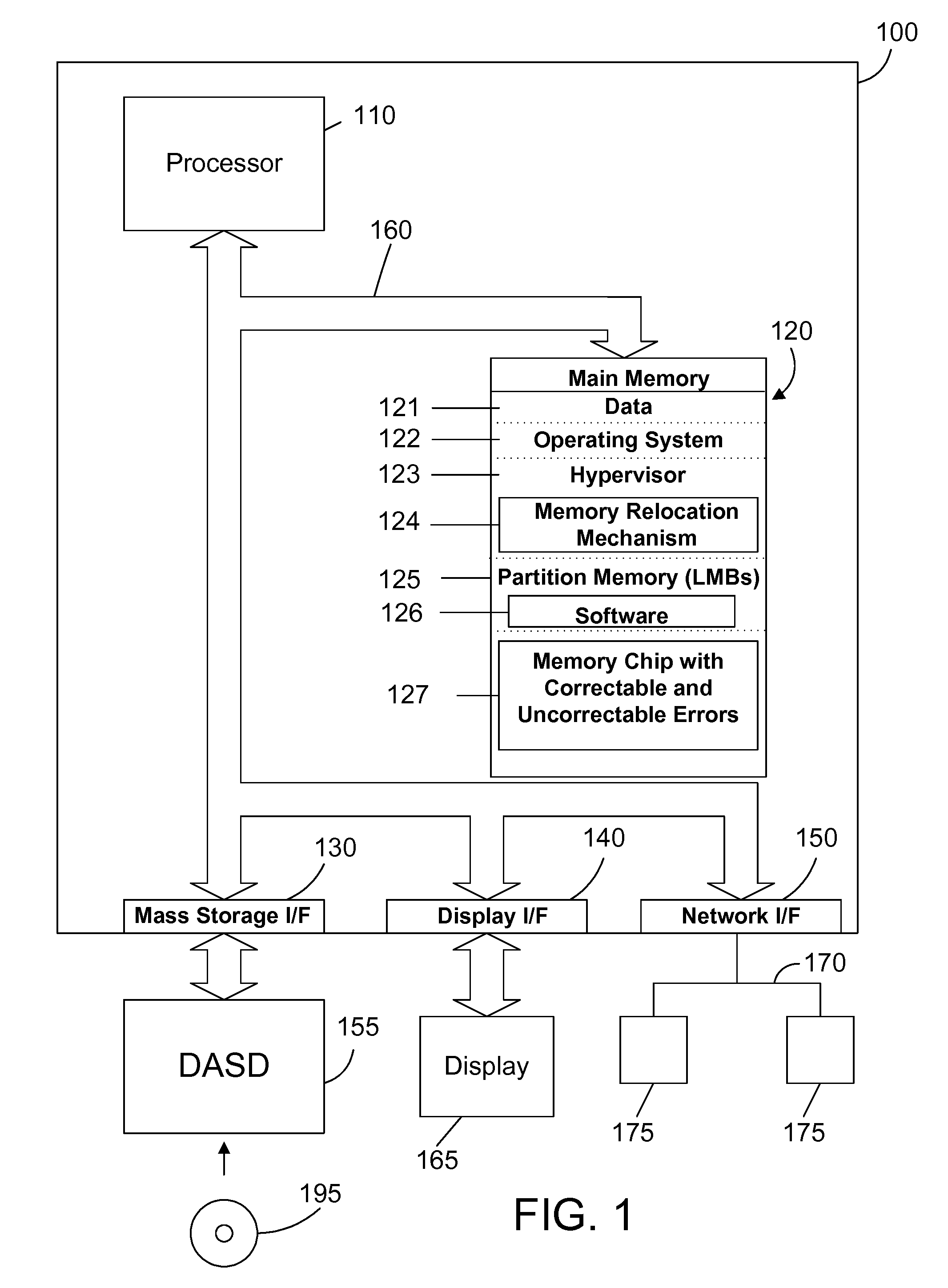
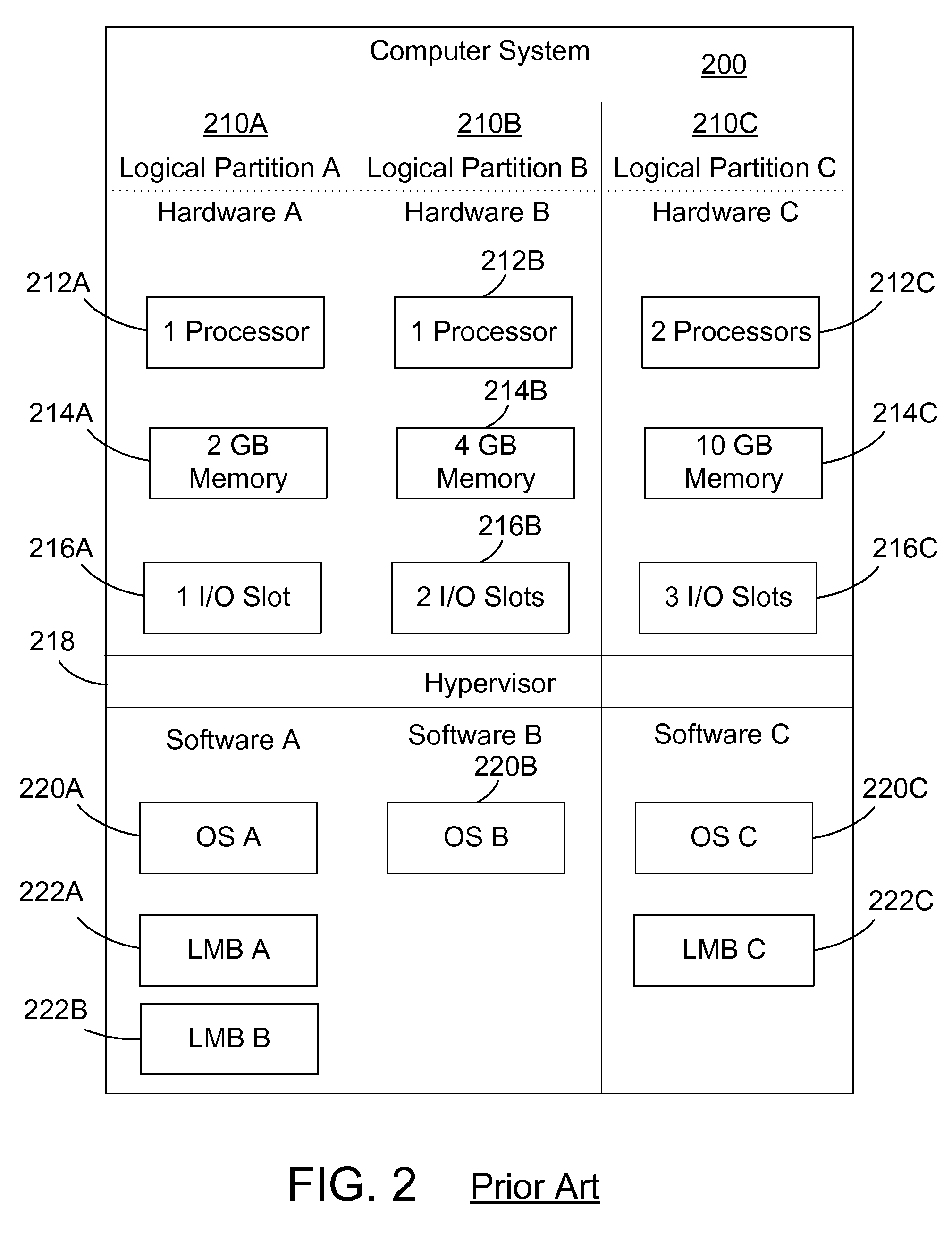
Partition transparent memory error handling in a logically partitioned computer system with mirrored memory
A method and apparatus for transparently handling recurring correctable errors and uncorrectable errors in a mirrored memory system prevents costly system shutdowns for correctable memory errors or system failures from uncorrectable memory errors. When a high number of correctable errors are detected for a given memory location, a memory relocation mechanism in the hypervisor moves the data associated with the memory location to an alternate physical memory location transparently to the partition such that the partition has no knowledge that the physical memory actualizing the memory location has been changed. When a correctable error occurs, the memory relocation mechanism uses data from a partner mirrored memory block as a data source for the memory block with the uncorrectable error and then relocates the data to a newly allocated memory block to replace the memory block with the uncorrectable error.
Owner:INT BUSINESS MASCH CORP
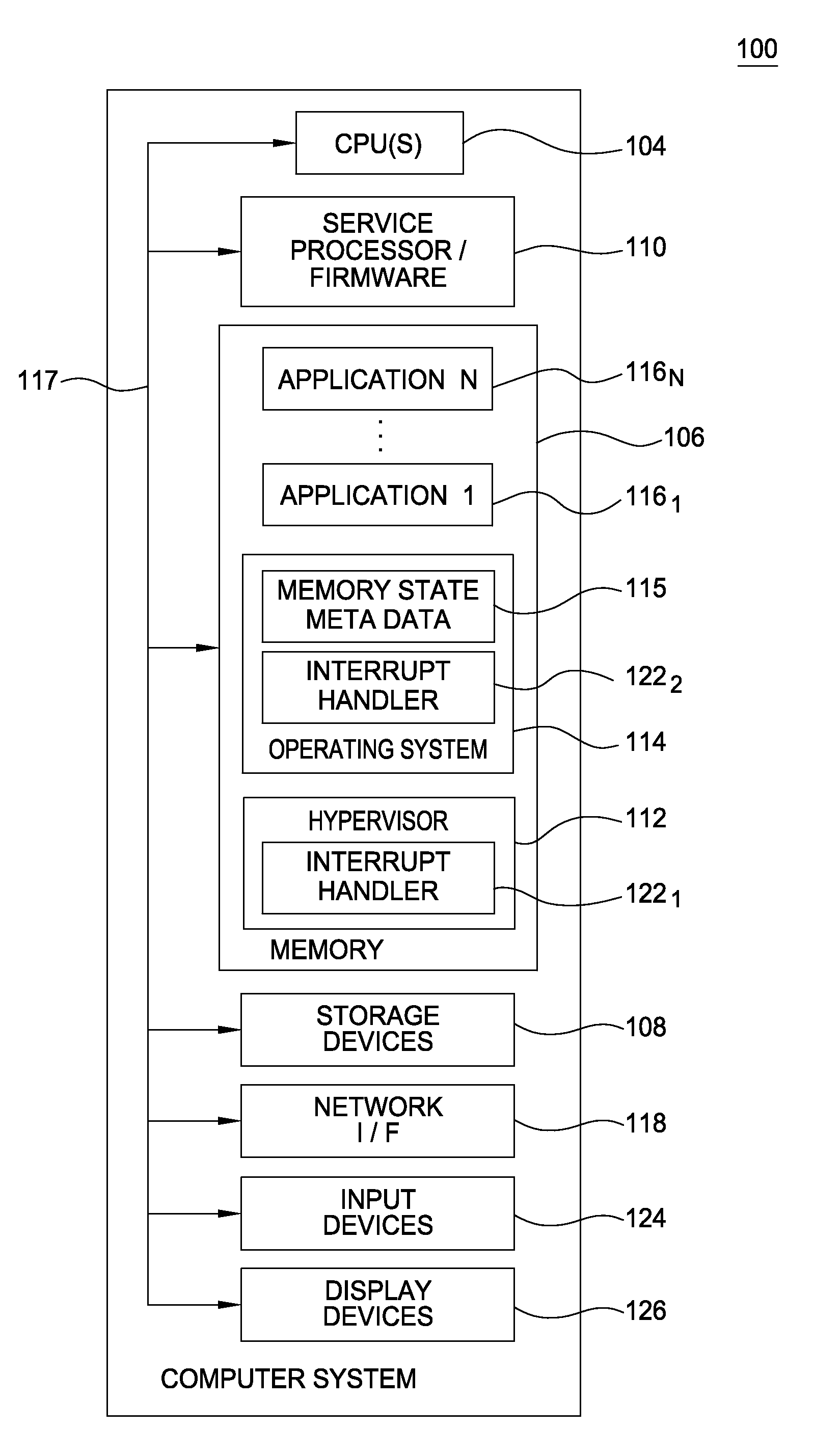
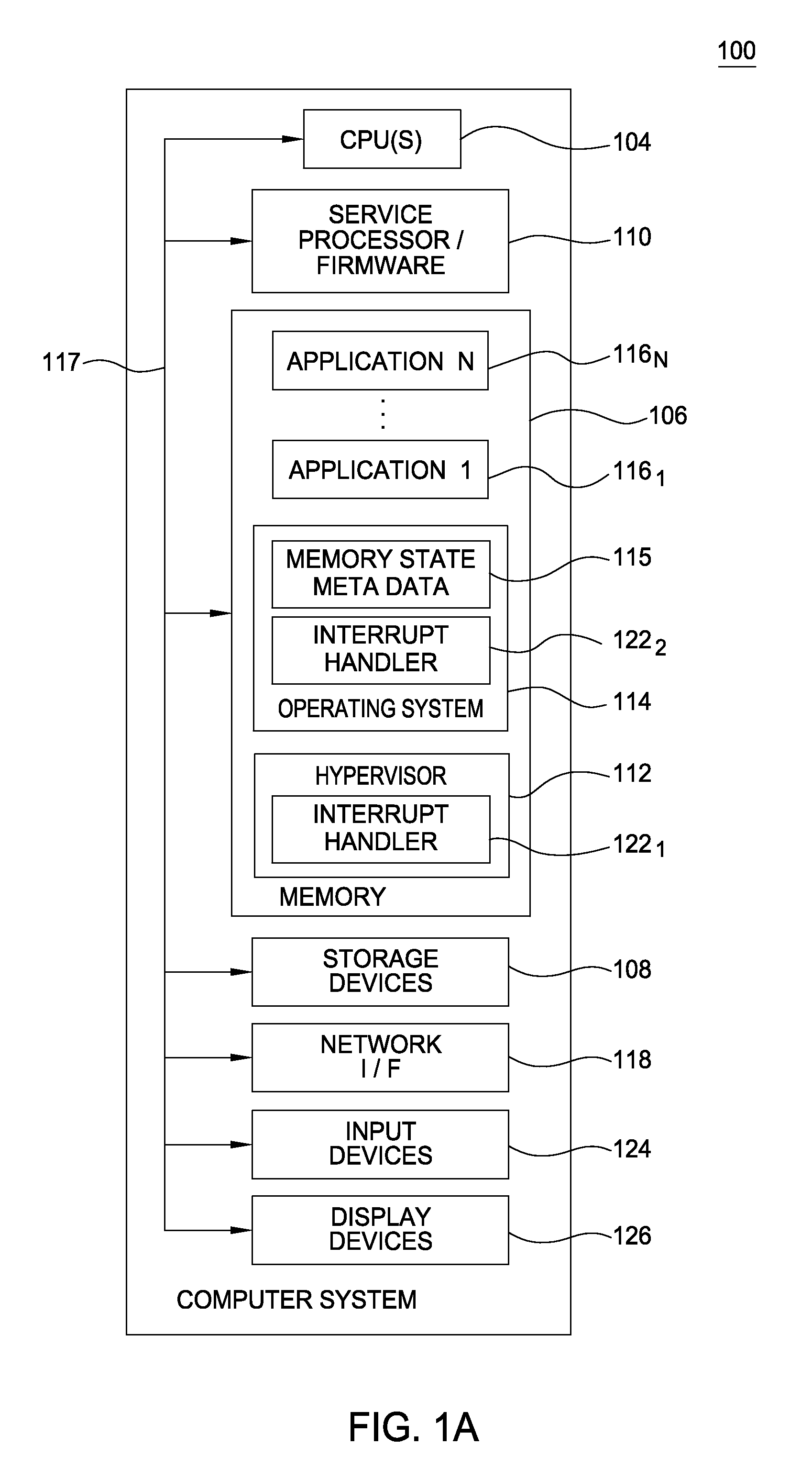
Resilience to Memory Errors with Firmware Assistance
Embodiments of the invention provide an interrupt handler configured to distinguish between critical and non-critical unrecoverable memory errors, yielding different actions for each. Doing so may allow a system to recover from certain memory errors without having to terminate a running process. In addition, when an operating system critical task experiences an unrecoverable error, such a task may be acting on behalf of a non-critical process (e.g., when swapping out a virtual memory page). When this occurs, an interrupt handler may respond to a memory error with the same response that would result had the process itself performed the memory operation. Further, firmware may be configured to perform diagnostics to identify potential memory errors and alert the operating system before a memory region state change occurs, such that the memory error would become critical.
Owner:IBM CORP
Memory monitoring method and apparatus
ActiveCN105975377AAvoid repeated mistakesImprove stabilityHardware monitoringRedundant hardware error correctionParallel computingBad memory
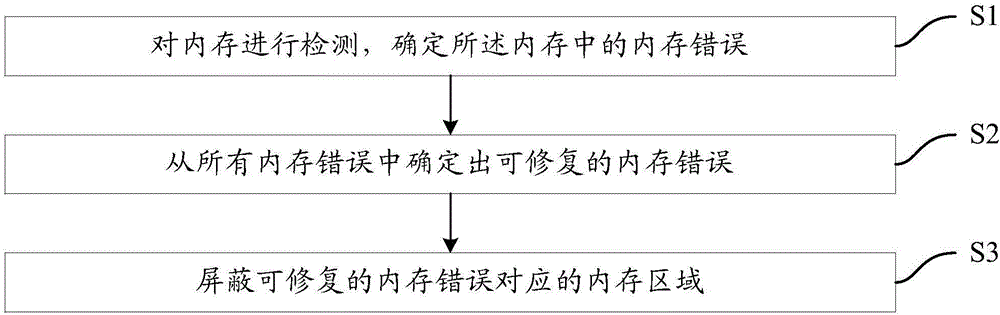
The invention provides a memory monitoring method and apparatus. The method comprises the steps of S1: detecting a memory to determine memory errors in the memory; S2: determining a repairable memory error from all the memory errors; and S3: shielding a memory region corresponding to the repairable memory error. According to the memory monitoring method and apparatus, the stability of a system where the memory is located can be improved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Method and managing bad memory blocks in a nonvolatile memory device, and nonvolatile-memory device implementing the management method
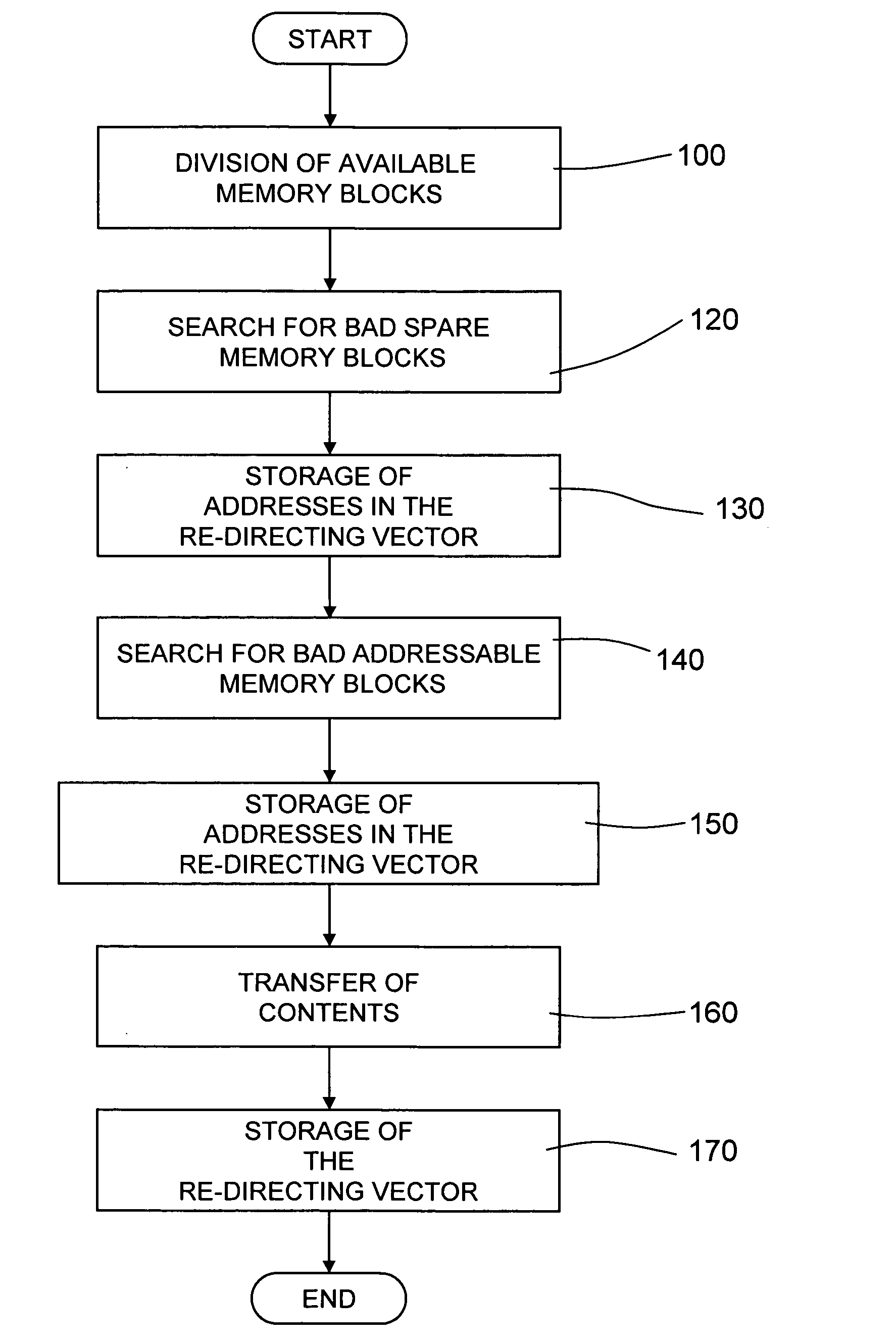
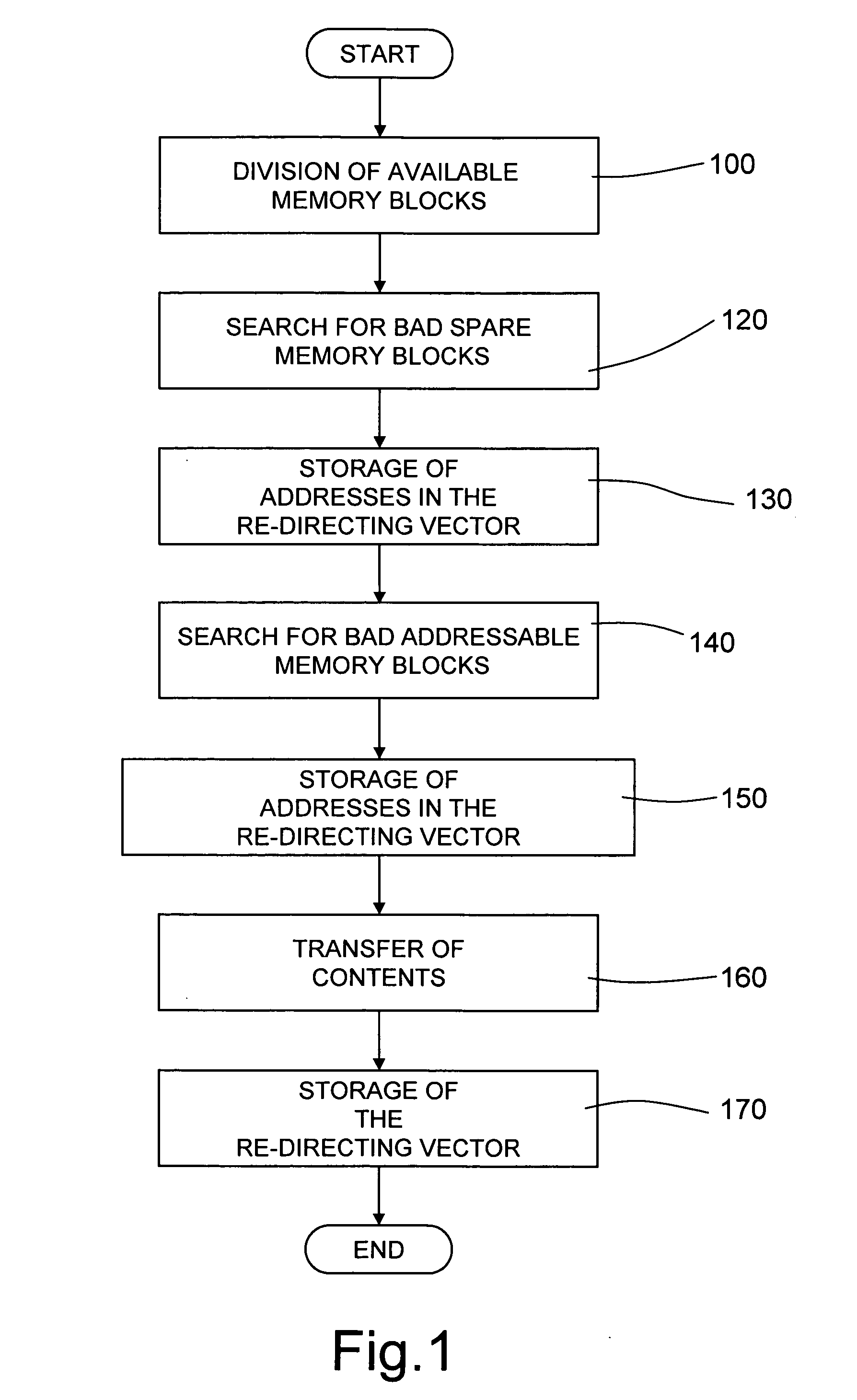
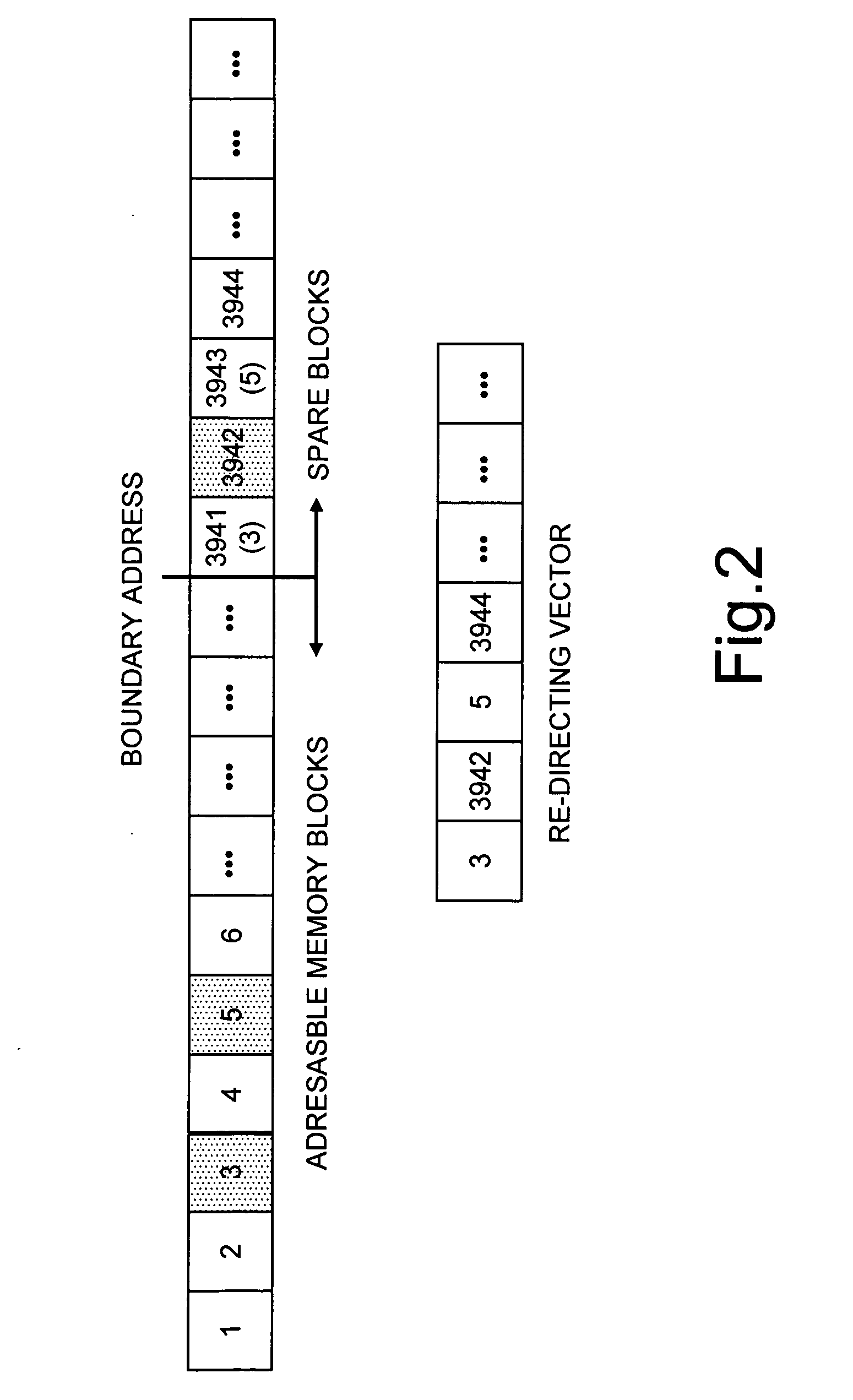
A method for managing bad memory blocks of a nonvolatile-memory device, in which the available memory blocks are divided into a first set, formed by addressable memory blocks that are to be used by a user, and a second set, formed by spare memory blocks that are to replace bad addressable memory blocks, and in which the bad addressable memory blocks are re-mapped into corresponding spare memory blocks. The re-mapping of the bad addressable memory blocks envisages: seeking bad spare memory blocks; storing the logic address of each bad spare memory block in a re-directing vector in a position corresponding to that of the bad spare memory block in the respective set; seeking bad addressable memory blocks; and storing the logic address of each bad addressable memory block in a free position in the re-directing vector.
Owner:MICRON TECH INC
Self-identifying memory errors
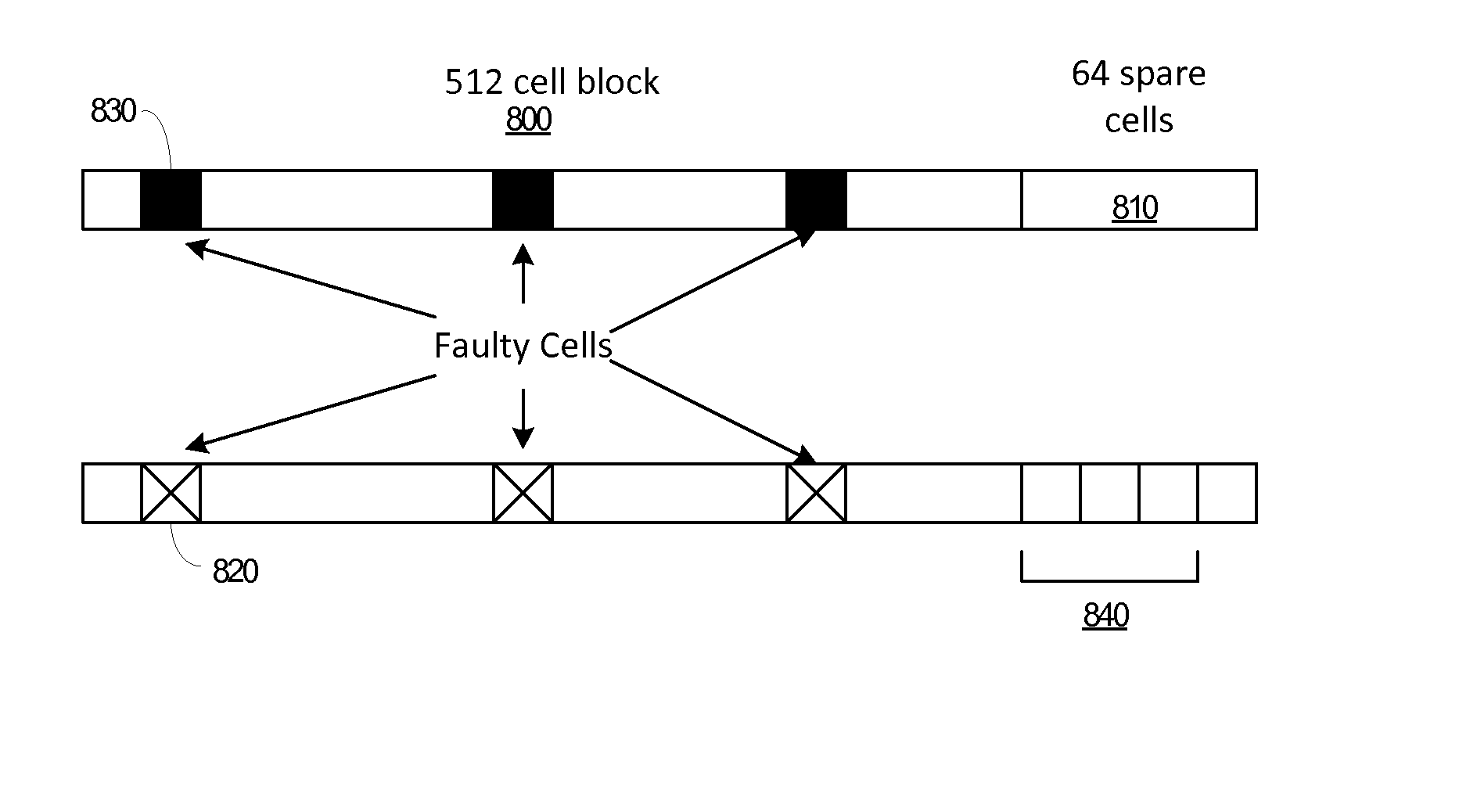
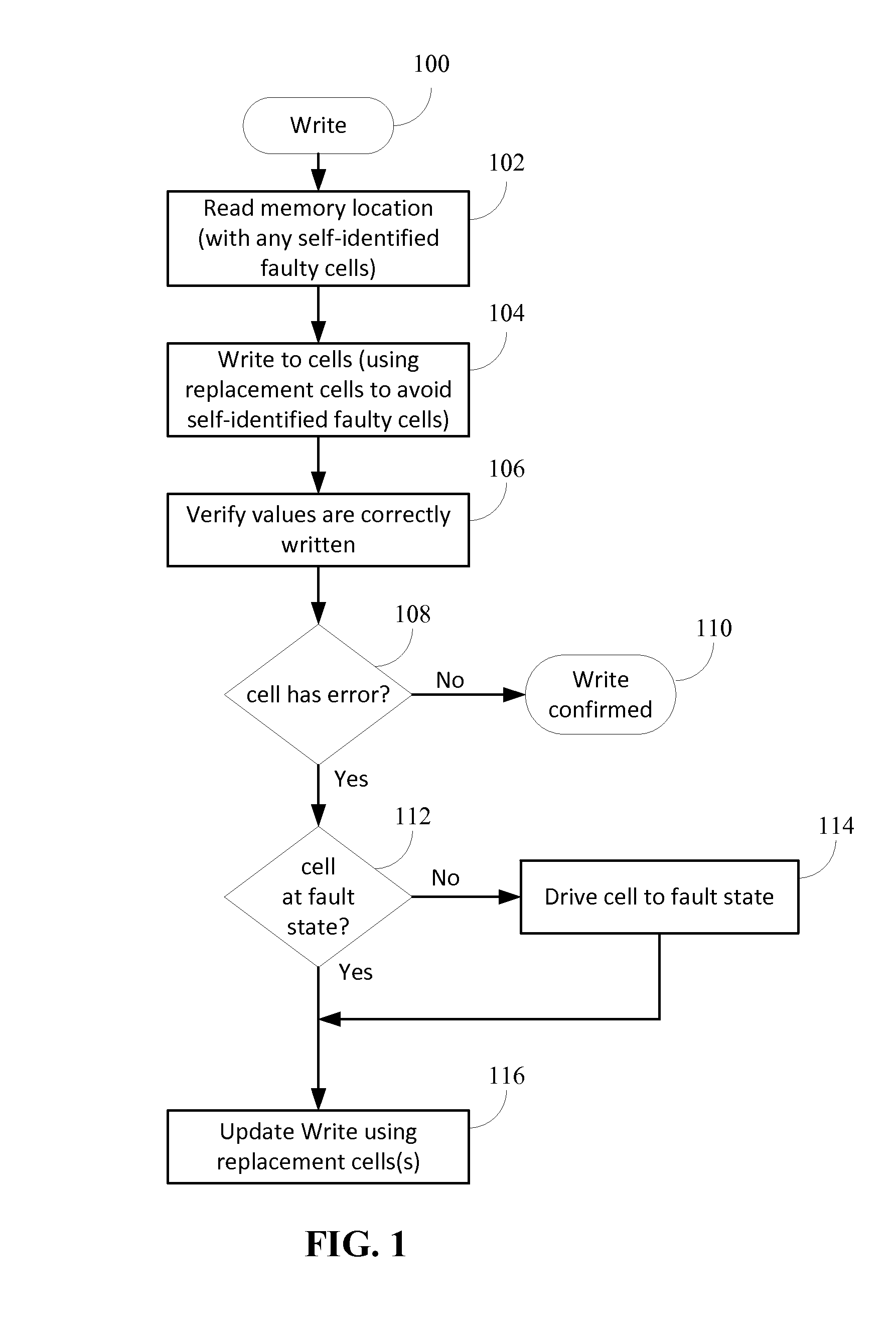
ActiveUS20150033064A1Well formedError detection/correctionRead-only memoriesHigh resistanceMemory faults
A memory region can durably self-identify as being faulty when read. Information that would have been assigned to the faulty memory region can be assigned to another of that sized region in memory using a replacement encoding technique. For phase change memory, at least two fault states can be provided for durably self-identifying a faulty memory region; one state at a highest resistance range and the other state at a lowest resistance range. Replacement cells can be used to shift or assign data when a self-identifying memory fault is present. A memory controller and memory module, alone or in combination may manage replacement cell use and facilitate driving a newly discovered faulty cell to a fault state if the faulty cell is not already at the fault state.
Owner:MICROSOFT TECH LICENSING LLC
Critical memory
ActiveUS20080140957A1Error freeMemory loss protectionError detection/correctionThird partyParallel computing
Typical computer programs may incur costly memory errors that result in corrupted data. A new memory model is presented wherein it may be determined that certain data is critical and critical data may be stored and protected during computer application execution. Critical Memory allows that data determined to be critical may be stored and retrieved using functions enabled to increase the reliability of the data. Critical Memory presents a memory model where a subset of memory designated as critical memory may be used to store a subset of data deemed critical data. Probabilistic guarantees of data value consistency are provided by the employment of the new memory model. The memory model and functions presented are compatible with existing third-party libraries such that third-party libraries may be compatibly called from processes using critical memory.
Owner:MICROSOFT TECH LICENSING LLC
Method and device used for memory equipment management
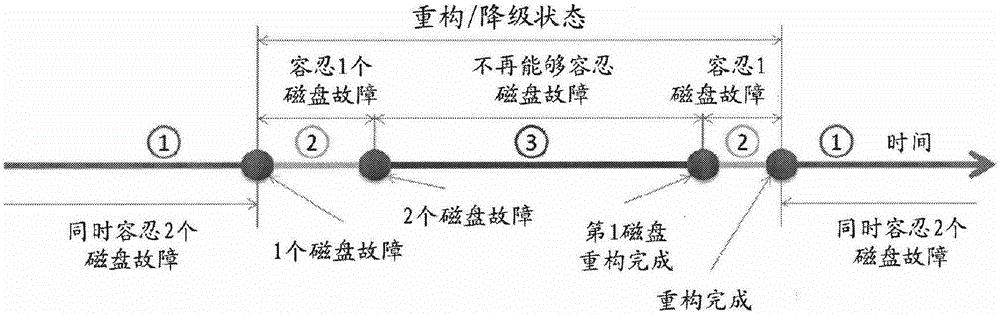
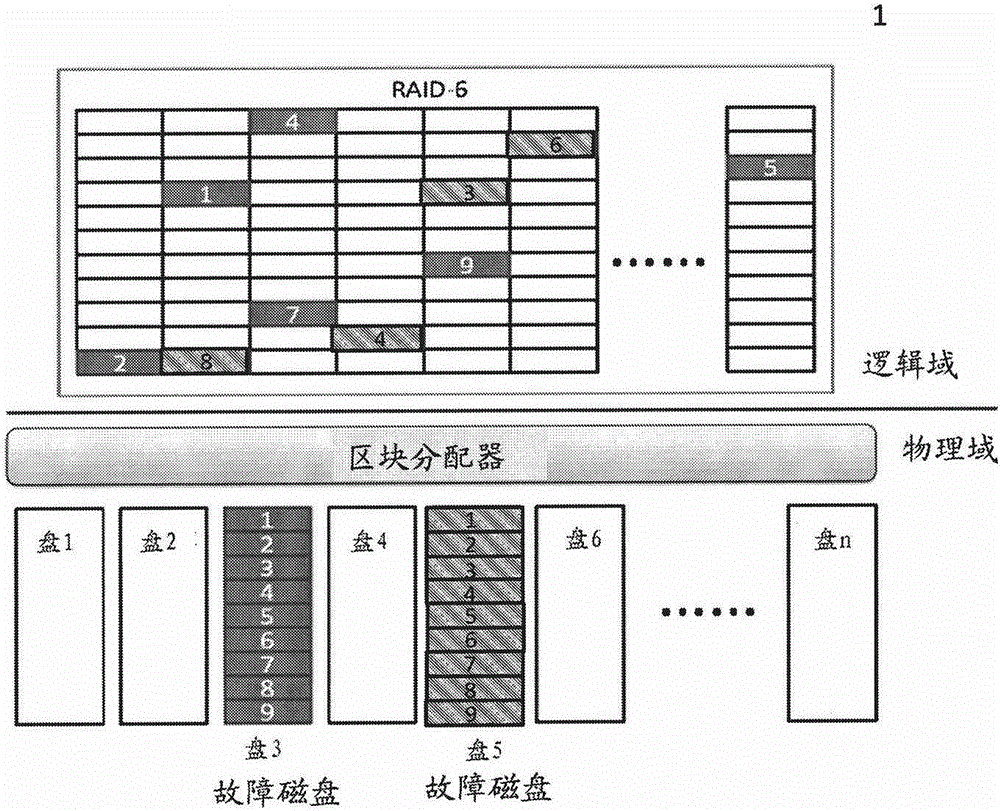
ActiveCN105892934AReduce refactoring timeImprove reliabilityInput/output to record carriersError detection/correctionBad memoryComputer science
Owner:EMC IP HLDG CO LLC
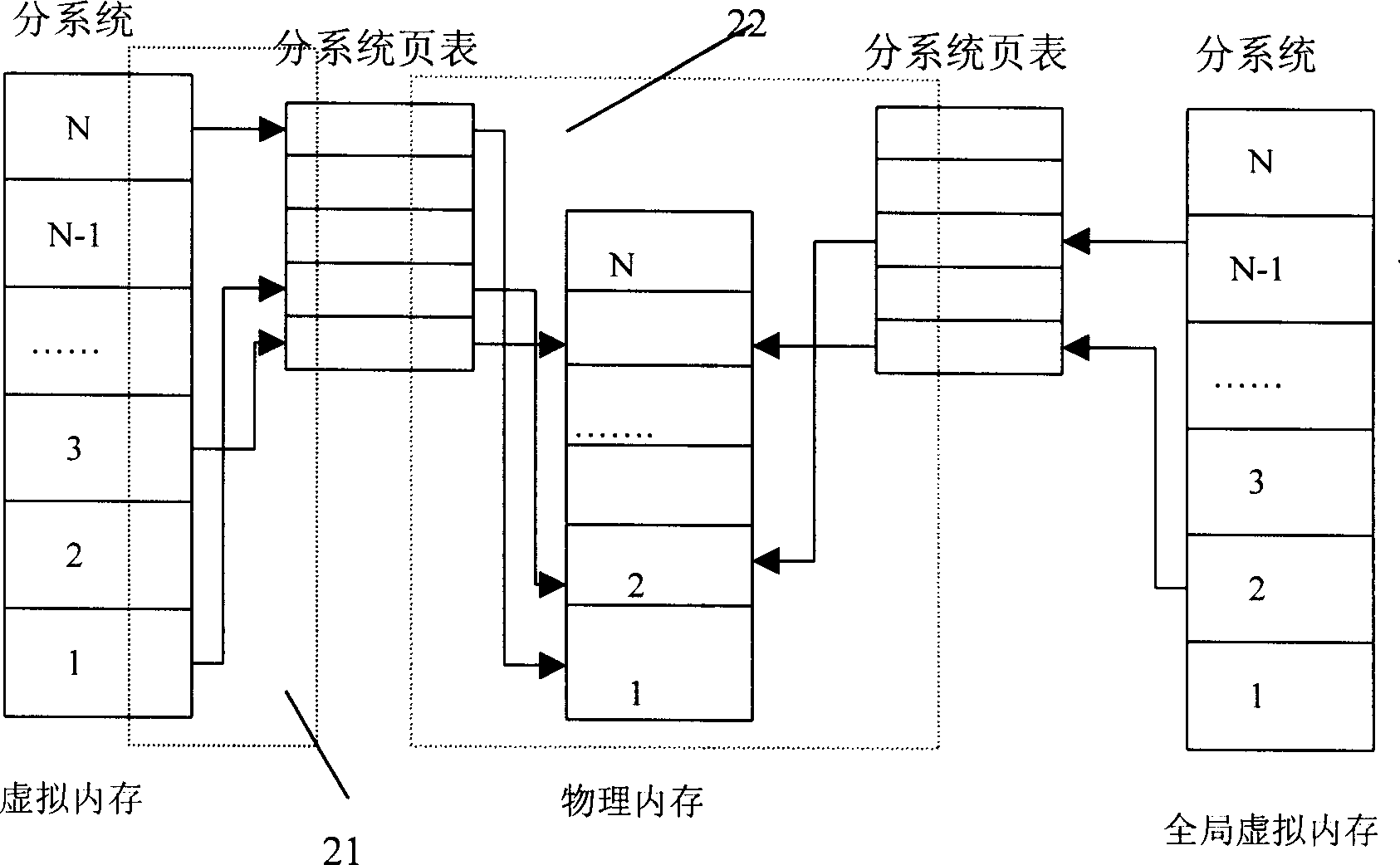
Virtual internal storage allocating and managing method of subsystem in communication system
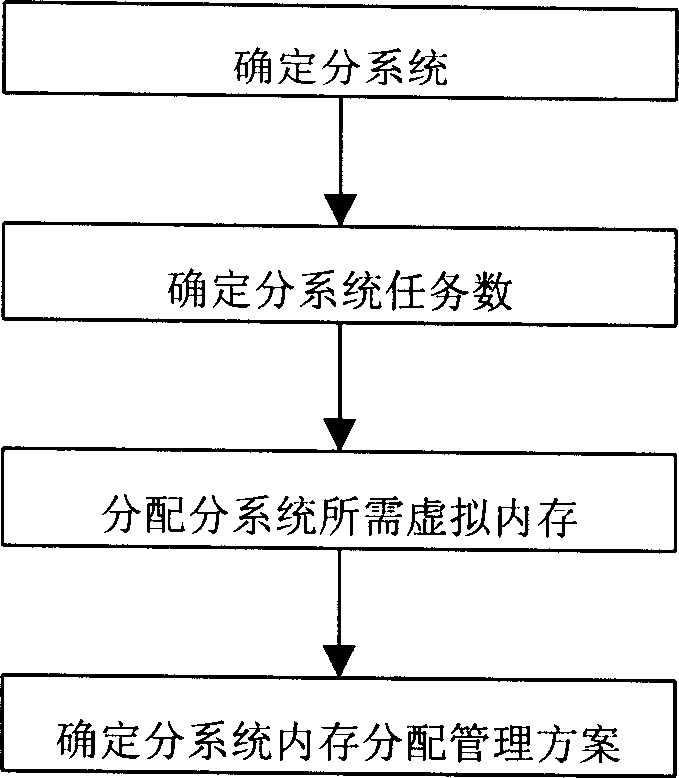
InactiveCN1430150APrevent border crossingControl illegal operationsResource allocationMemory adressing/allocation/relocationVirtual memoryCommunications system
A method for allocating and managing virtual memory between subsystems in communication system includes such steps as analyzing the requirement to communication system to determine all subsystems, determining the number of tasks for each subsystem, allocating the system memory space to all subsystems according to actual requirement pluse a certain redundancy, and determing the allocating and managing scheme for the memory of each subsystem. It can improve the stability and reliability of whole system.
Owner:STATE GRID BEIJING ELECTRIC POWER +2
Object-based programming method and object-based programming system in C language programming
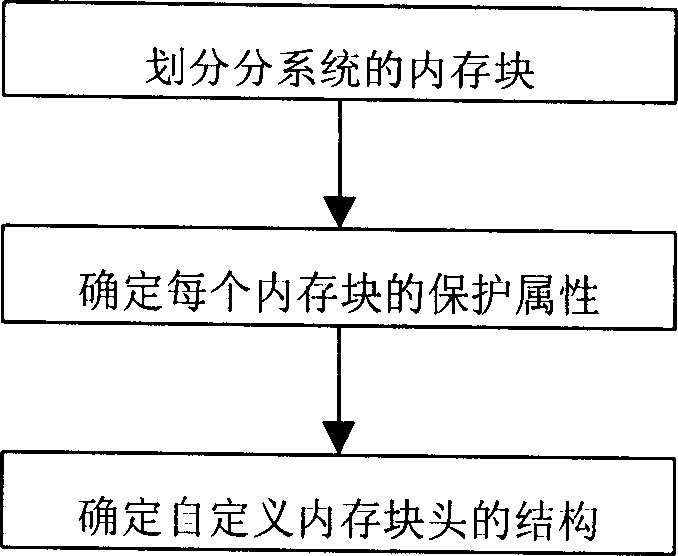
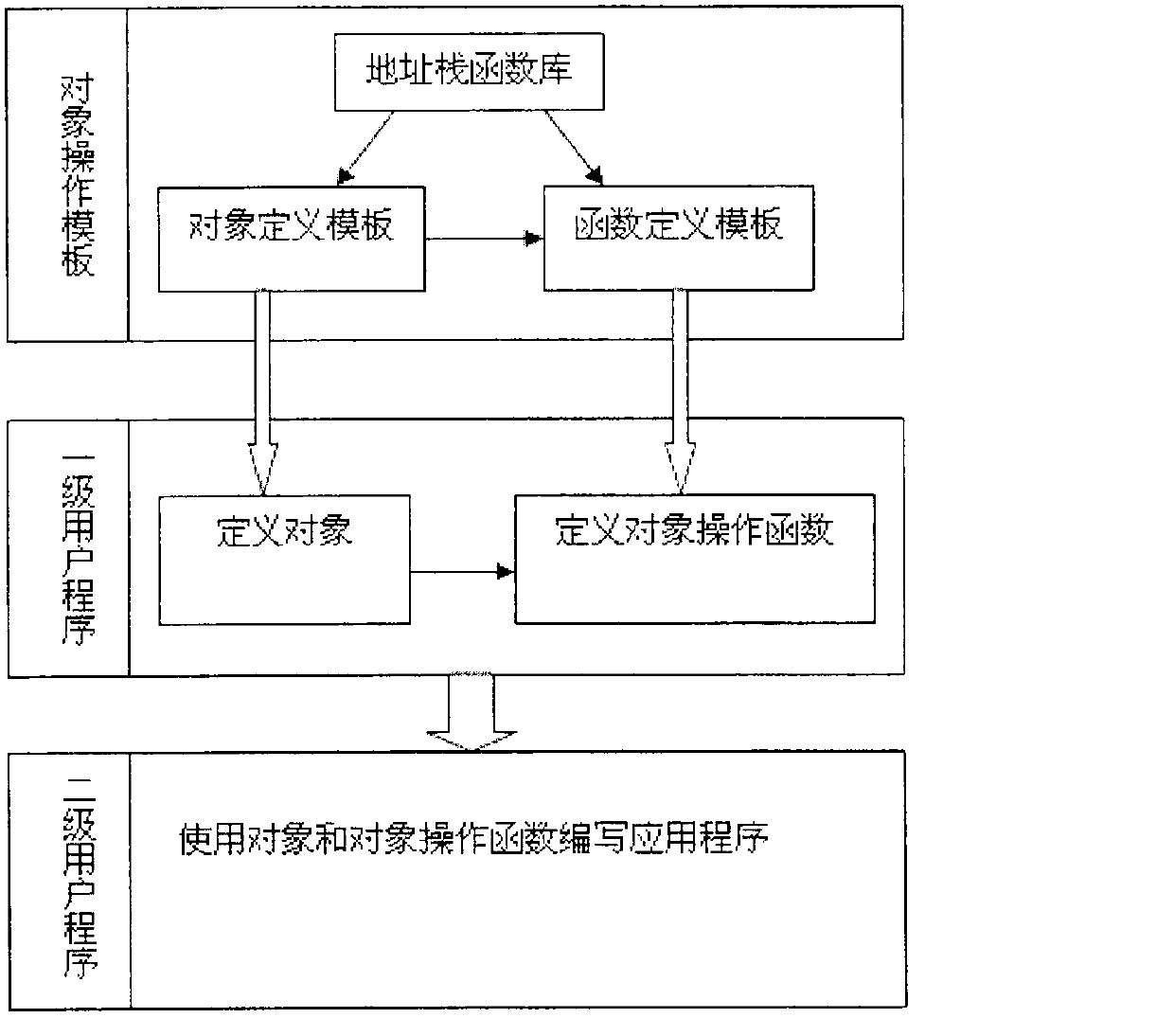
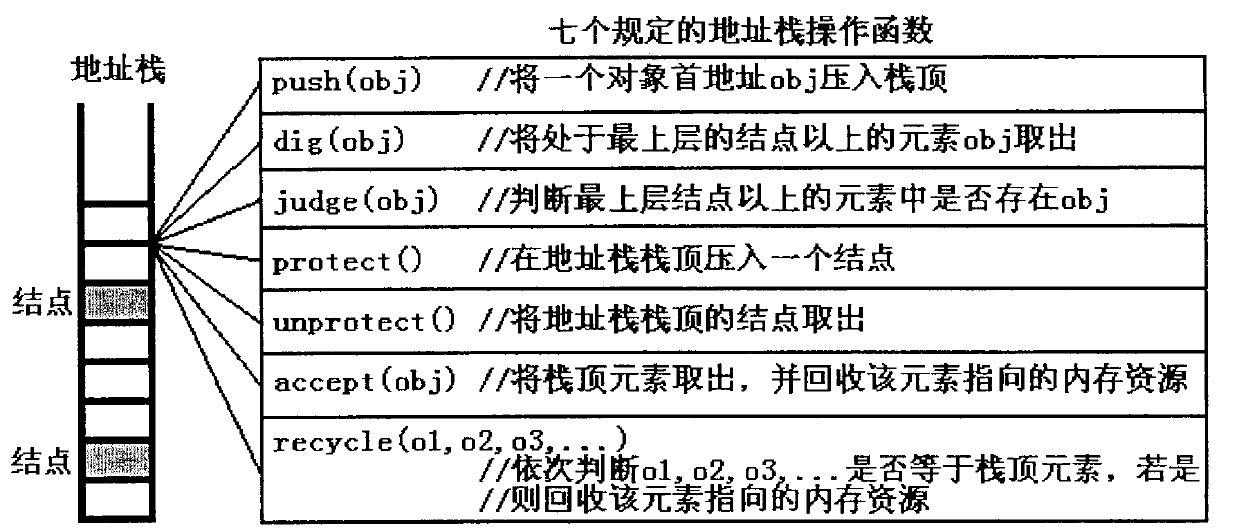
Certain currently popular programming languages (such as C++) are highly efficient but can easily bring about memory errors, and certain currently popular programming languages (such as Java) are safe in memories but lower in efficiency. The invention discloses an object-based programming method and an object-based programming system in C language programming, and the system is a convenient, safe and high-efficiency programming framework. The system utilizes the stack technique to efficiently judge the attribute of an 'object' (i.e. a non-generic type variable), also standardizes assignment and other operations on the object, and can release object resources and optimize the efficiency of object usage (or the efficiency of parameter transfer) simultaneously. The system provides defining templates for objects and object-operating functions, so that programmers can conveniently define the objects and the object-operating functions, the objects and functions defined by the defining templates can be conveniently subjected to recursionrecur and can be conveniently nested, invoked and operated in any other complex ways like generic type variables and functions, and the problems of memory safety and efficiency are automatically processed by the templates.
Owner:INST OF FLUID PHYSICS CHINA ACAD OF ENG PHYSICS
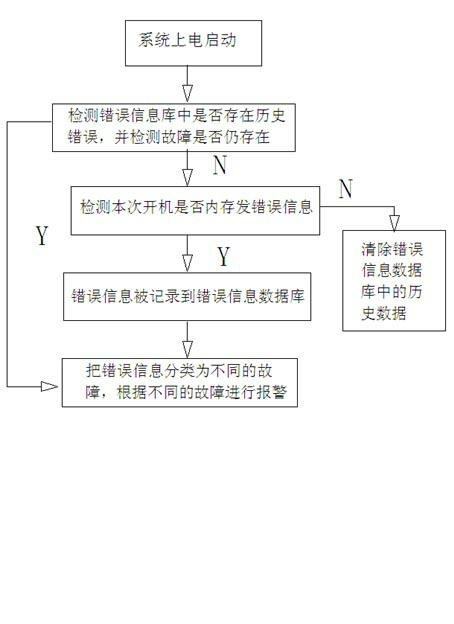
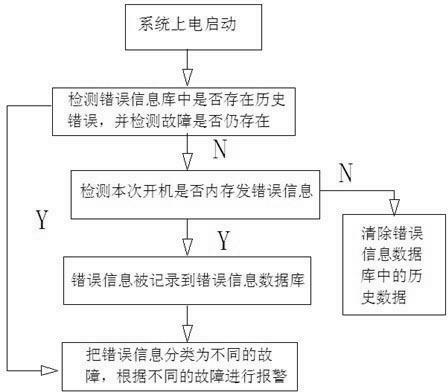
Server memory failure alarm method
InactiveCN102609350AEnhanced reliability featuresEasy maintenanceHardware monitoringDependabilityBad memory
The invention provides a server memory failure alarm method. A software program is used for recognizing memory error messages at a startup stage of a server system, the messages are transmitted to a management chip embedded into a main board and are judged in a classified manner, and alarm is given according to levels. The system comprises a failure information recognition unit, an error message database and an alarm unit, wherein the failure information recognition unit is used for acquiring the error messages sent out by a memory component in the system to provide evidence for judging memory failure, the error message database is used for collecting and transmitting the memory error messages, and the alarm unit is used for selecting different failure alarm modes according to different error messages. By implementing the memory failure alarm method in the server system, reliability of the system can be enhanced to a large extent, maintenance is facilitated, and the total image of the system is improved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com