Block chain identity system
A block chain and identity technology, applied in the transmission system, digital transmission system, encryption device with shift register/memory, etc., can solve the problems that the general public users are not easy to accept, user personal information leakage, etc., to improve reliability performance and security, and the effect of preventing replay attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
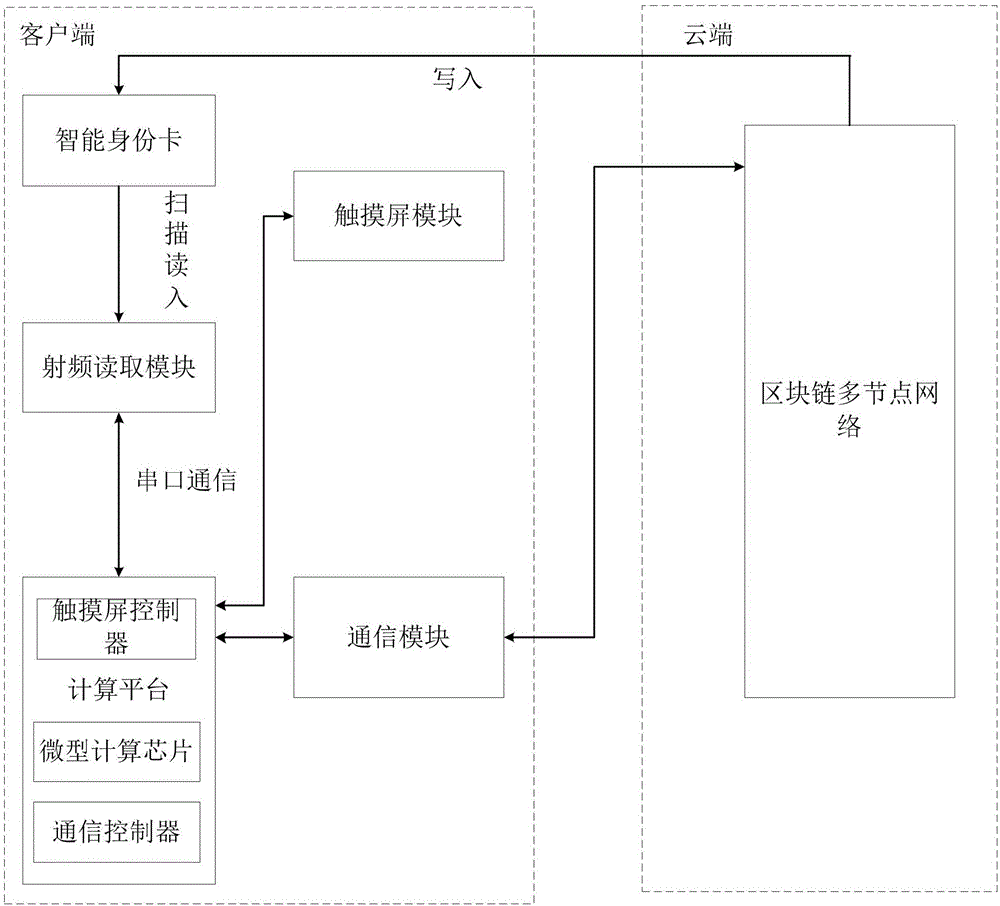
[0039] Example 1: Workflow of the authentication system
[0040] The working process of the authentication system is as follows: the user enters the user name and password on the login window displayed on the touch screen module of the client terminal to log in to the system. After entering the authentication system, the card reading authentication interface is displayed on the touch screen module. The reading module reads the information in the user's smart identity card. After the identity of the smart identity card is read into the computing platform, the processing platform performs corresponding cryptographic operations according to the identity authentication protocol to obtain encrypted authentication request information. , the communication module transmits the encrypted authentication request information to the authentication server in the cloud through network communication, and after a series of authentication interaction processes between the client and the cloud, t...
Embodiment 2
[0041] Embodiment 2: Identity authentication protocol design
[0042] As the key to the security of the identity authentication system, the design of the identity authentication protocol is a key component of the whole system. First introduce the notational conventions used in this article:
[0043] U means user;
[0044] S means a third-party authentication server;
[0045] ID represents the identity information read by the radio frequency reading module;
[0046] UserN and Password respectively represent the user name and corresponding login password;
[0047] KuR and KuS respectively represent the public key and private key of the mobile user;
[0048] KsR and Kss respectively represent the public key and private key of the authentication server;
[0049] EK(m) means to encrypt plaintext m with key k;
[0050] DK(C) means to decrypt the ciphertext c with the key k;
[0051] R1 and N2 are random numbers generated by the system;
[0052] K is used as the session key a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com