RFID random key two-way certifying method accord with EPC C1G2 standard
An EPCC1G2, two-way authentication technology, applied in computer parts, record carriers used by machines, user identity/authority verification, etc., can solve problems such as no secure channel, weak RFID system security protection capability, and security risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
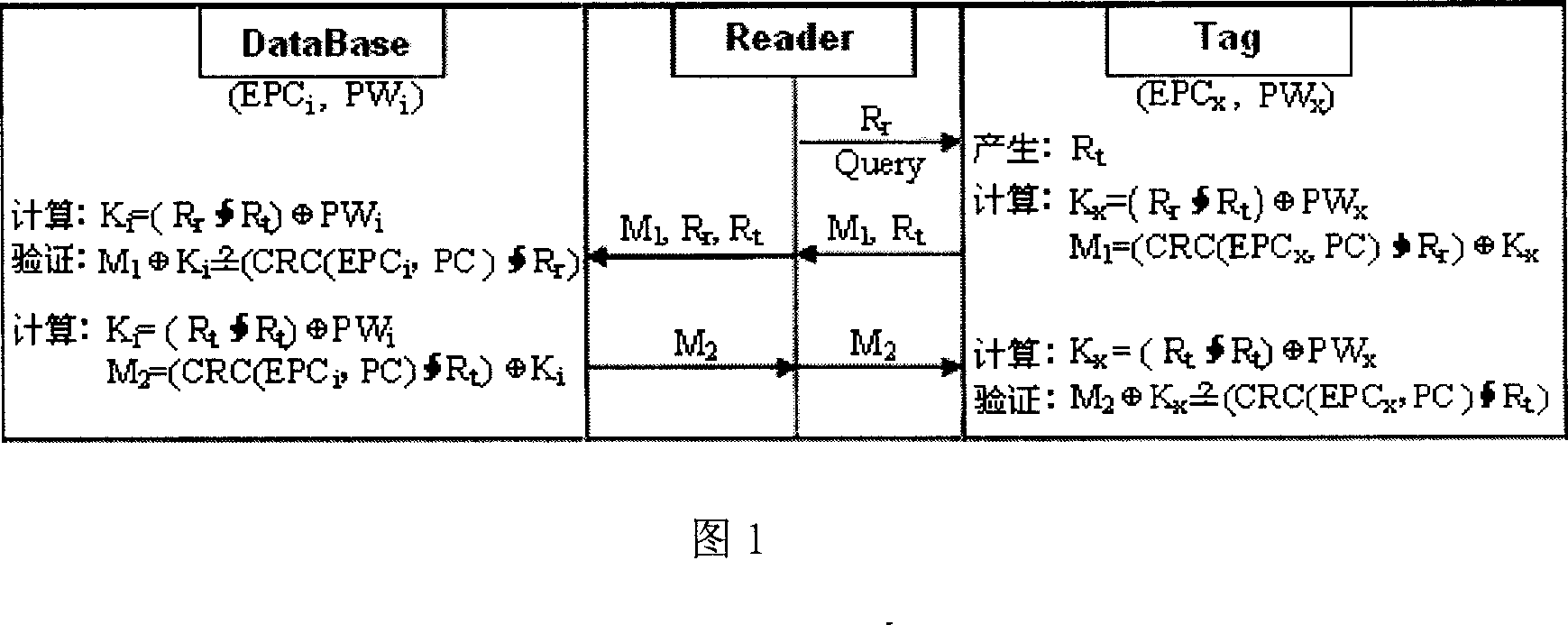
[0036] A kind of RFID randomized key two-way authentication method that meets the EPC C1G2 standard provided by the present invention comprises the following steps:
[0037] (1) Tag reader → tag Tag: the tag reader generates a random number R r , and send a query authentication request to the label, and at the same time R r send to label;
[0038] (2) Tag Tag → Tag Reader → Backend Database DataBase: the tag also generates a random number R t , and calculate K x =(R r ∮R t )PW x and M 1 =(CRC(EPC x , PC)∮R r )K x , the label will be (M 1 , R t ) to the tag reader, the tag reader will (M 1 , R t , R r ) is forwarded to the backend database;
[0039] (3) Back-end database DataBase: Check whether there is an EPC in the back-end database i and PW i , where 1≤i≤n, verify M 1 K i =(CRC(EPC i , PC)∮R r ) is established, where Ki =(R r ∮R t )PW i , if established, the authentication is passed, and go to step 4; otherwise, the authentication fails, and the o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com