Security system implementation method based on virtual security element in trusted execution environment
A virtual security element and execution environment technology, applied in computer security devices, internal/peripheral computer component protection, instruments, etc. It is difficult to achieve a balance with the effectiveness of the system architecture, etc., to achieve the effects of improving ease of use and portability, improving system security, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
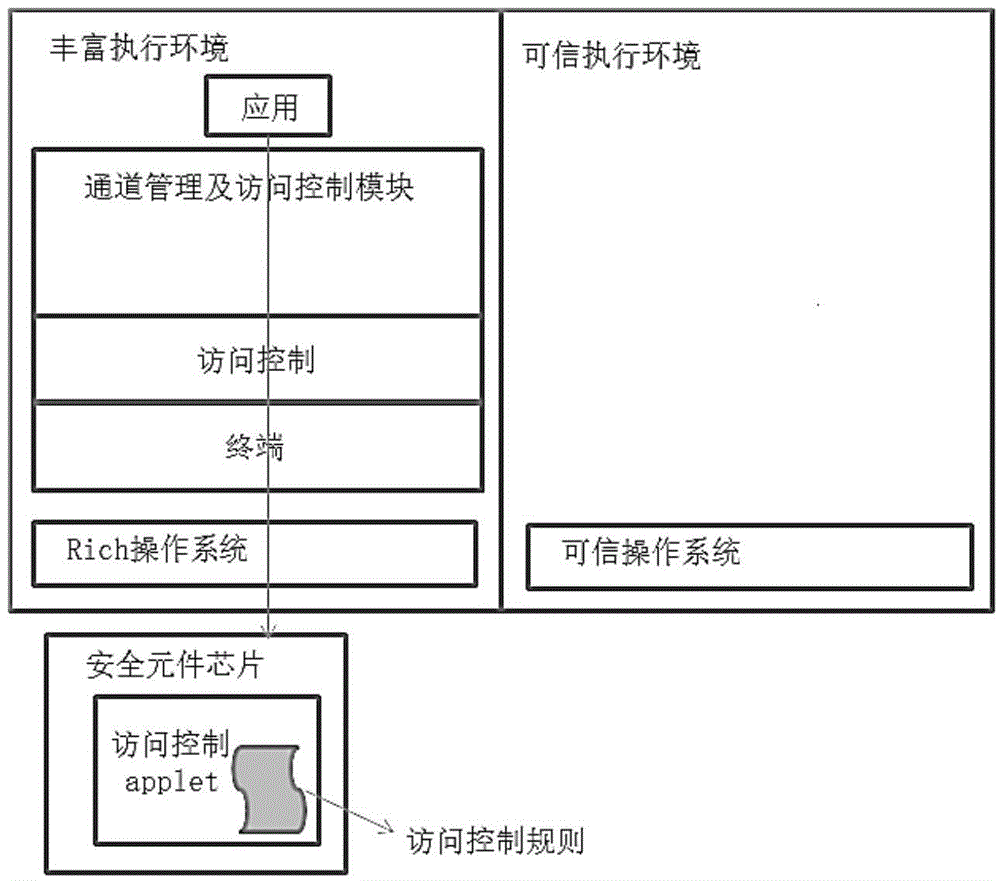
[0041] Such as figure 2 As shown, in this embodiment, the access request is directed to the security application in the virtual secure element in the feasible execution environment.
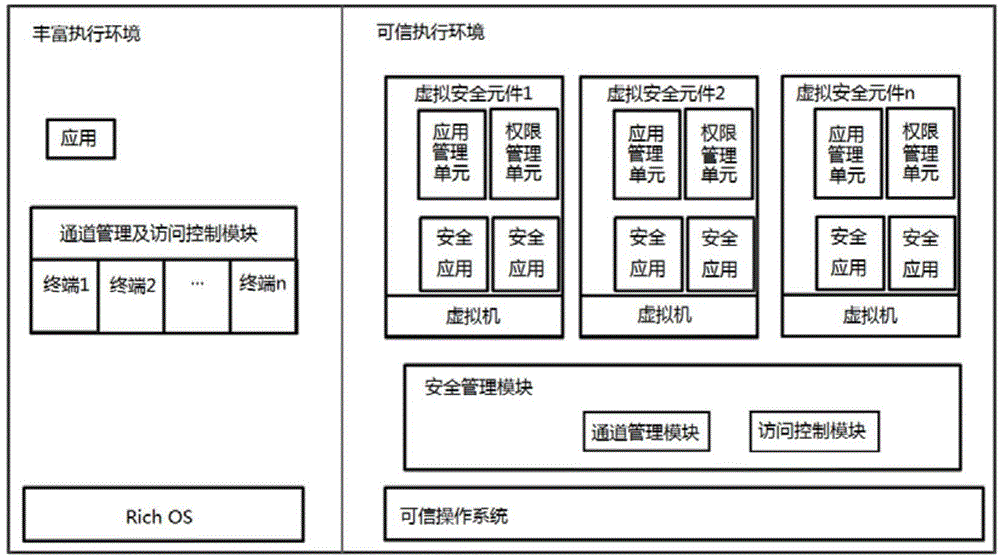
[0042] In this embodiment, the terminal for accessing the trusted execution environment is added to the channel management and access control module built in Rich OS, and the access control processing for accessing the trusted execution environment is removed, and then a direction to the trusted execution environment is set in the trusted execution environment. Applications in the Rich OS provide a security management module with a unified access interface and at least one virtual security element, and receive all access requests from applications in the Rich OS through the security management module.
[0043] The security management module receives an access request from an application in the Rich OS to the virtual security element, and the access request is sent to the security management modu...
Embodiment 2
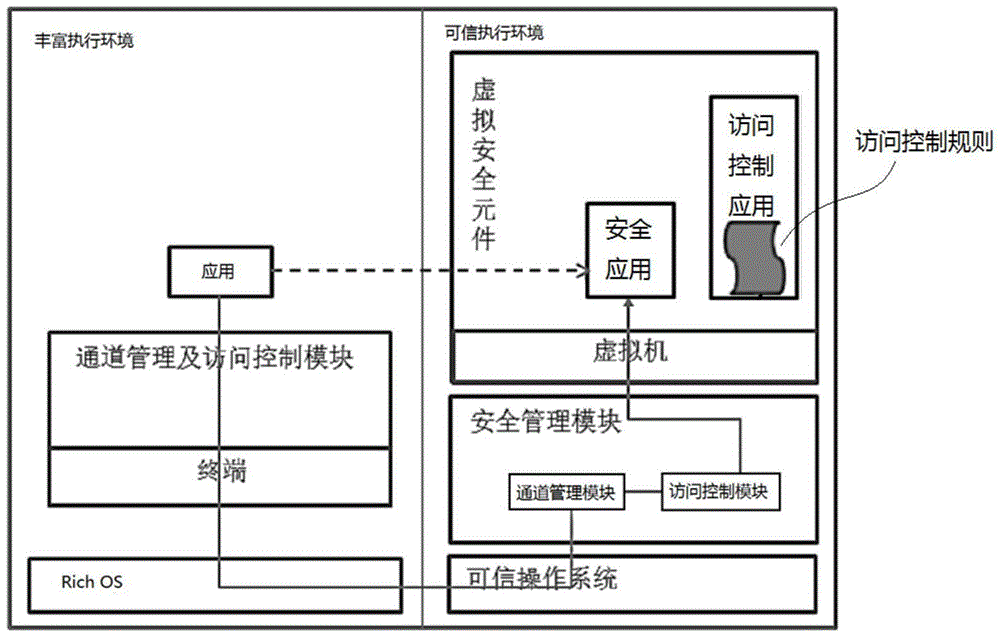
[0062] Such as Figure 6 As shown, the difference between this embodiment and Embodiment 1 is that the access request is directed at the security application in the secure element chip. Similarly, in this embodiment, all access requests from applications in the Rich OS are received by the security management module , connect the secure element chip with the trusted execution environment, when the application in the Rich OS sends a request to access the secure application in the secure chip, the access request is first transmitted to the security management module in the trusted execution environment, and the security management module passes the judgment Whether the access request matches the access control rules to accept or deny the request.
[0063] The initialization of the access rules in this embodiment is also read from the source data by the security management module when the trusted execution environment is initialized or when an initial request is received.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com