Calculable creditworthiness-based access control method under distributed environment of multiple trusting domains
A technology of access control and trust domain, applied in the field of access control based on computable reputation, which can solve the problems of large amount of storage and calculation, too fine-grained, lack of etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] Embodiments of the present invention are described in detail below in conjunction with accompanying drawings: this example is carried out under the premise of technical solution of the present invention, has provided detailed implementation and specific operation process, but protection scope of the present invention is not limited to the following the embodiment.
[0053] This example includes the following steps:
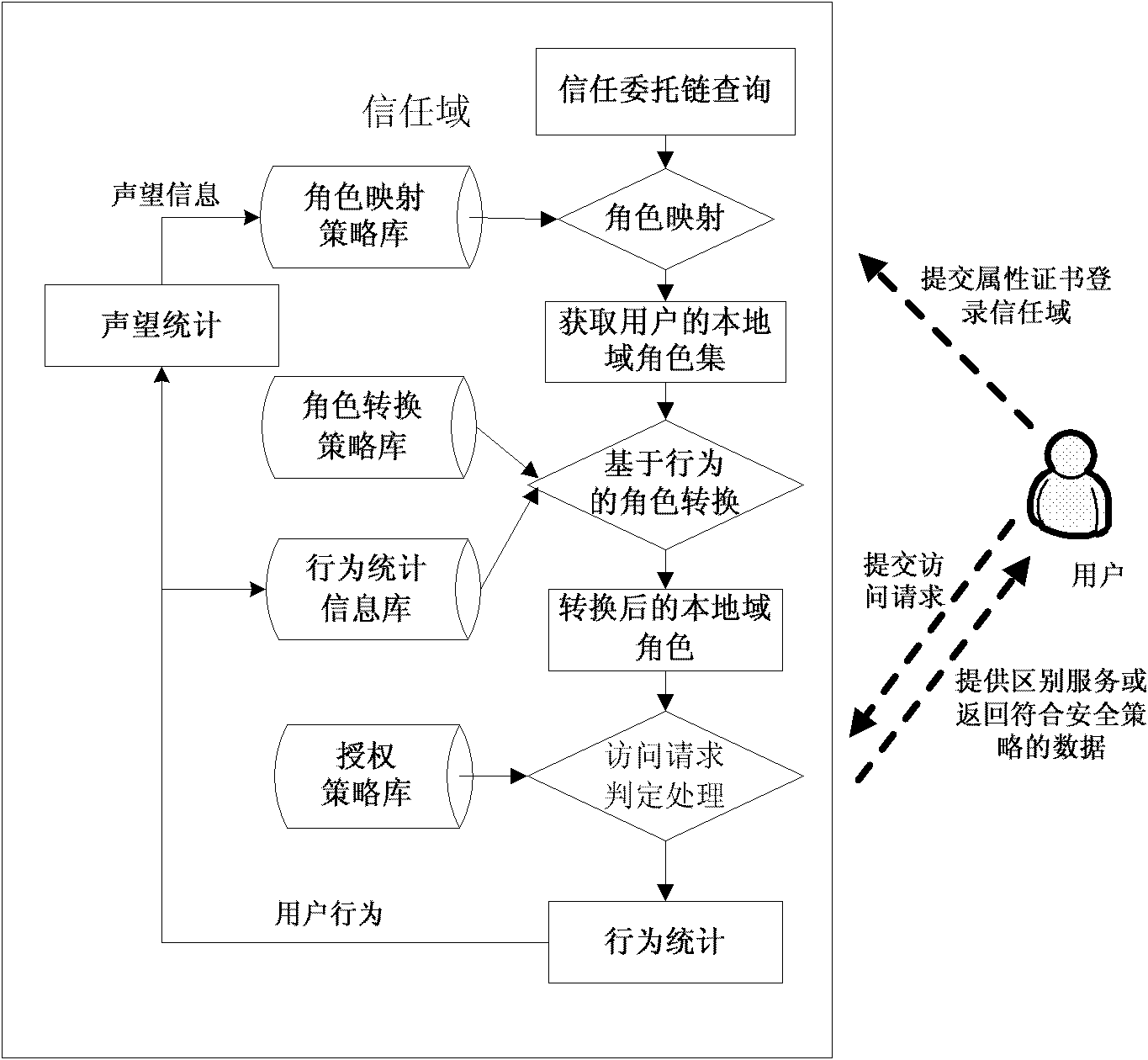
[0054] Step 1: The user logs in to the target trust domain and undergoes role mapping and role conversion to obtain a local role set. Since each role conversion may generate a new target role and delete the old source role, the local role set is based on behavior A dynamically changing collection of .
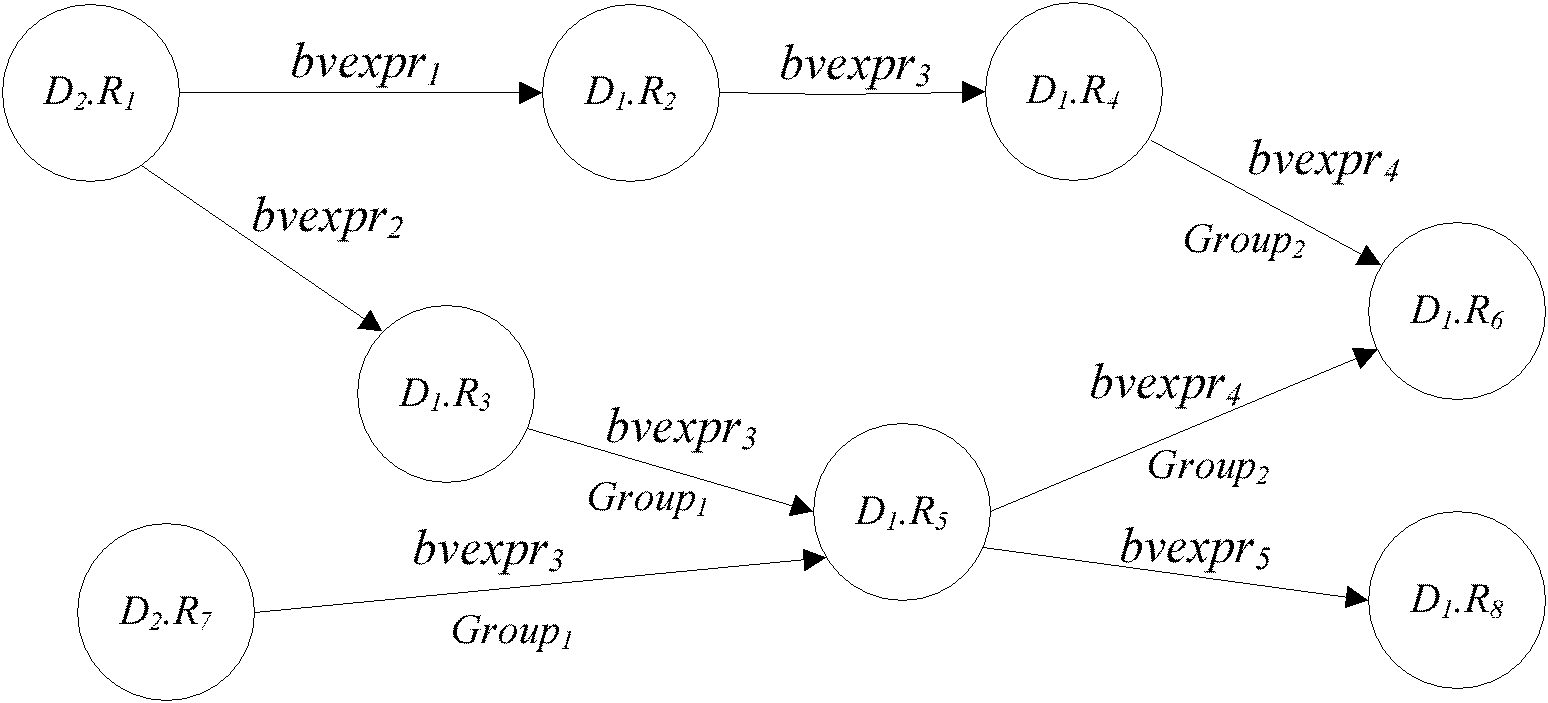
[0055] Such as figure 1 As shown, in this embodiment, the target character is connected to the local character set, and there is a feedback update process. The local role set can contain multiple roles, but after each user action is executed, only one tar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com