Credible computer platform
A computer and trusted technology, applied in computer security devices, computing, internal/peripheral computer component protection, etc., can solve the problems of data encryption protection, insufficient user identity authentication, etc., to improve information security protection capabilities, prevent BIOS from being tampered with, The effect of preventing illegal user login
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
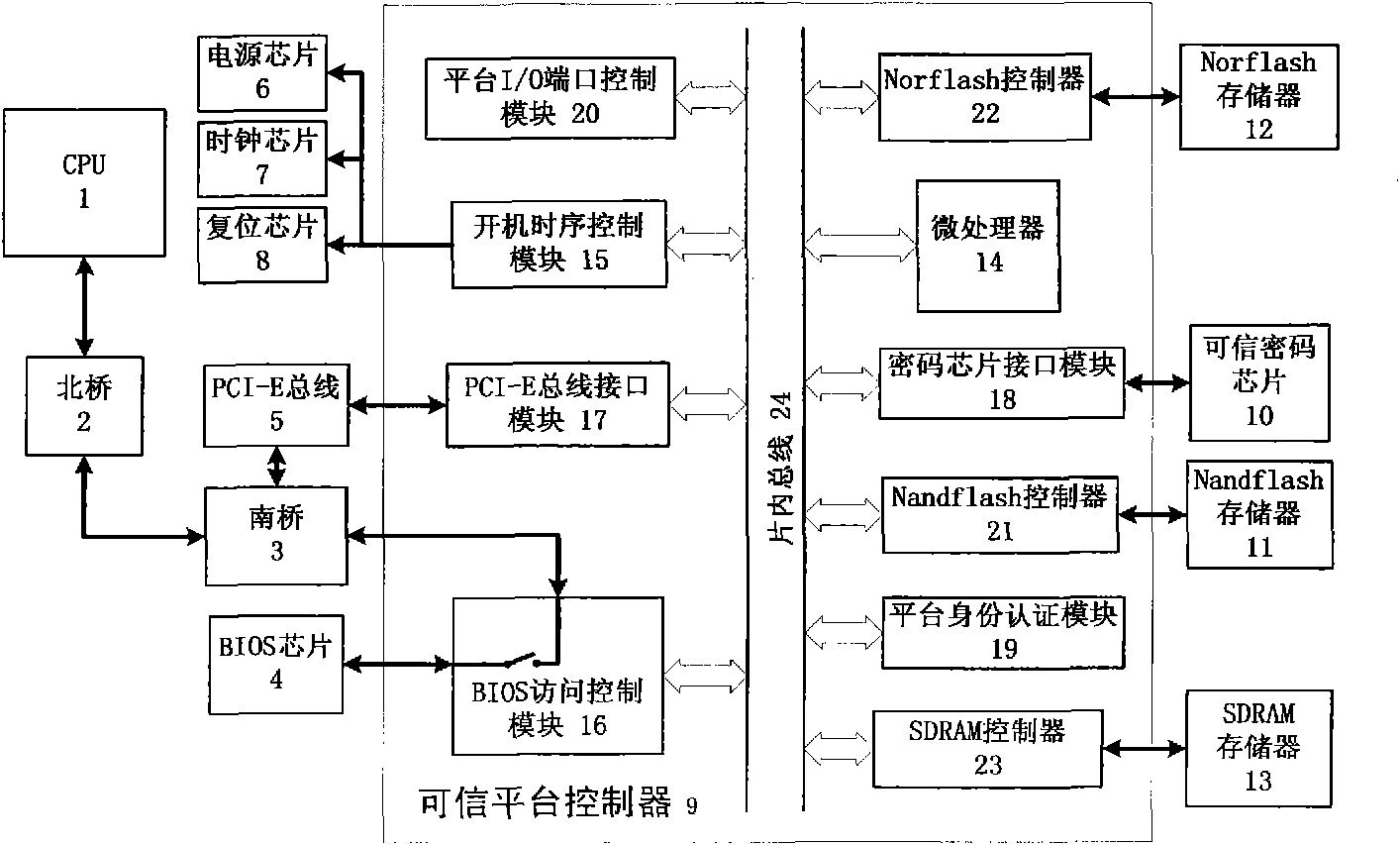
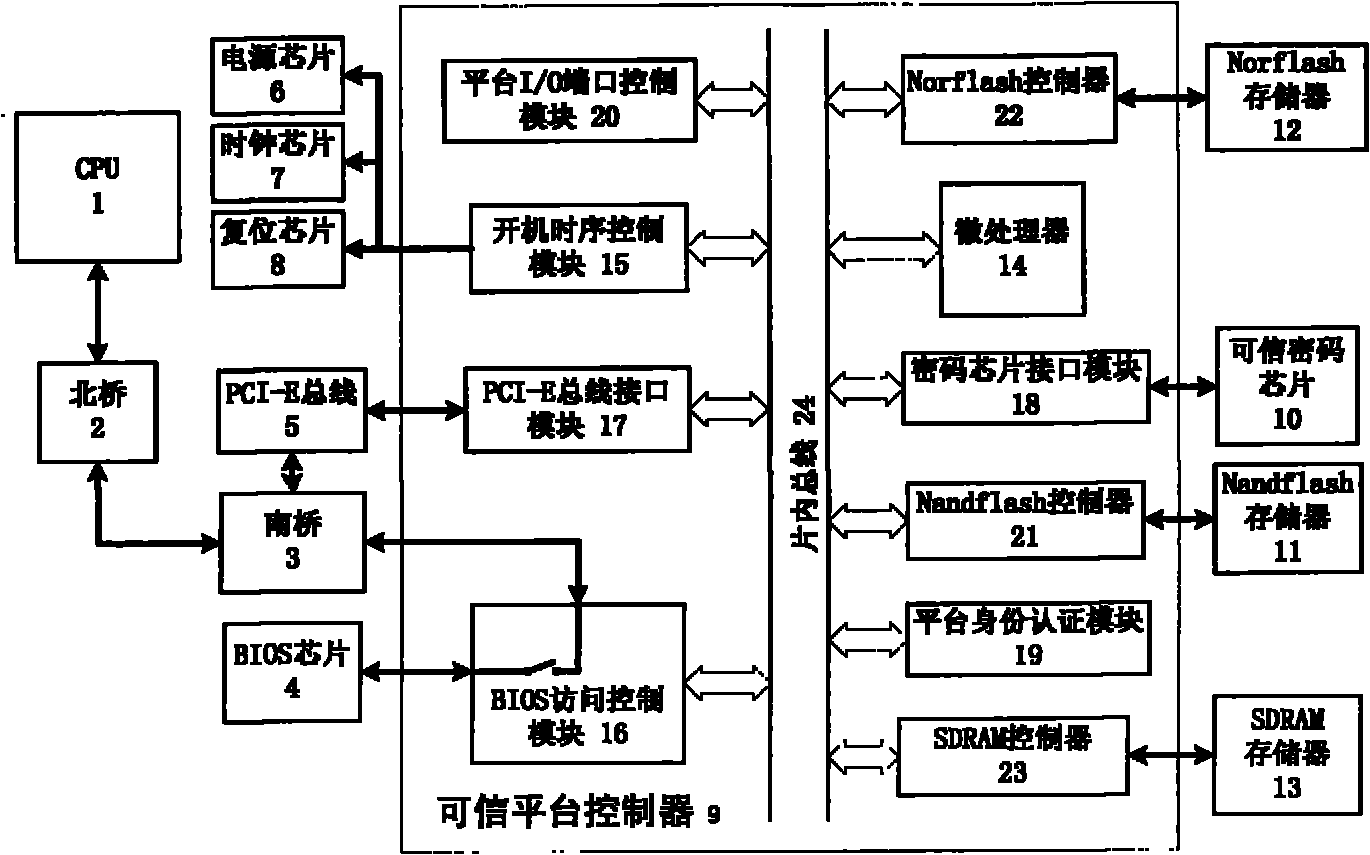
[0010] A trusted computer platform, comprising: CPU1, Northbridge 2, Southbridge 3, BIOS chip 4, PCI-E bus 5, power supply chip 6, clock chip 7 and reset chip 8, also includes: Trusted platform controller 9, Trusted cryptographic chip 10, Nandflash memory 11, Norflash memory 12 and SDRAM memory 13; wherein, trusted platform controller 9 includes: microprocessor 14, boot sequence control module 15, BIOS access control module 16, PCI-E bus interface Module 17, cryptographic chip interface module 18, platform identity authentication module 19, platform I / O port control module 20, Nandflash controller 21, Norflash controller 22, SDRAM controller 23 and on-chip bus 24.
[0011] Two-way connection between CPU1 and North Bridge 2, two-way connection between North Bridge 2 and South Bridge 3, bus interconnection in Trusted Platform Controller 9, microprocessor 14, boot sequence control module 15, BIOS access control module 16, PCI-E bus interface module 17 , cryptographic chip interfa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com