Patents
Literature
119results about How to "Prevent login" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
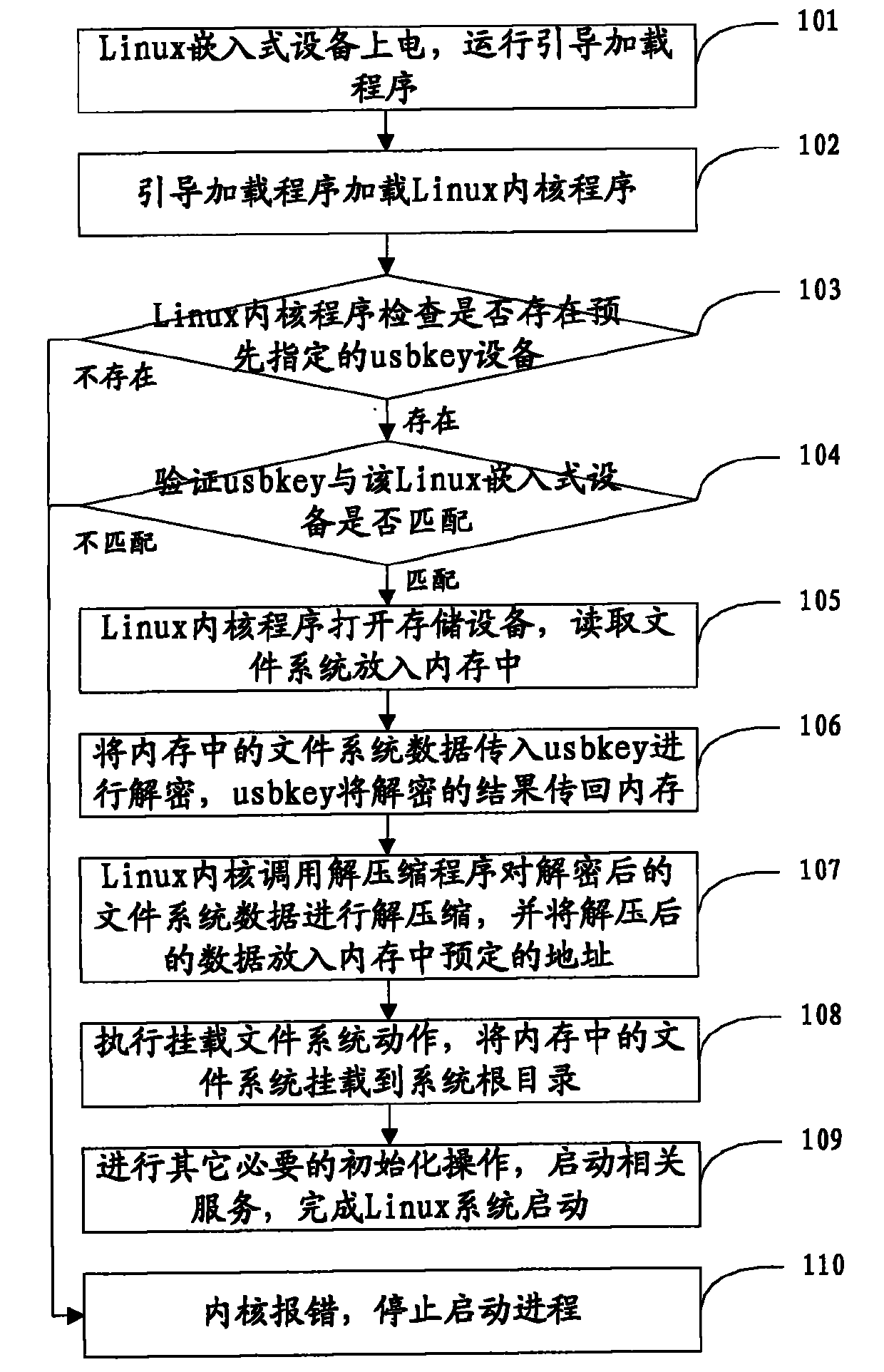
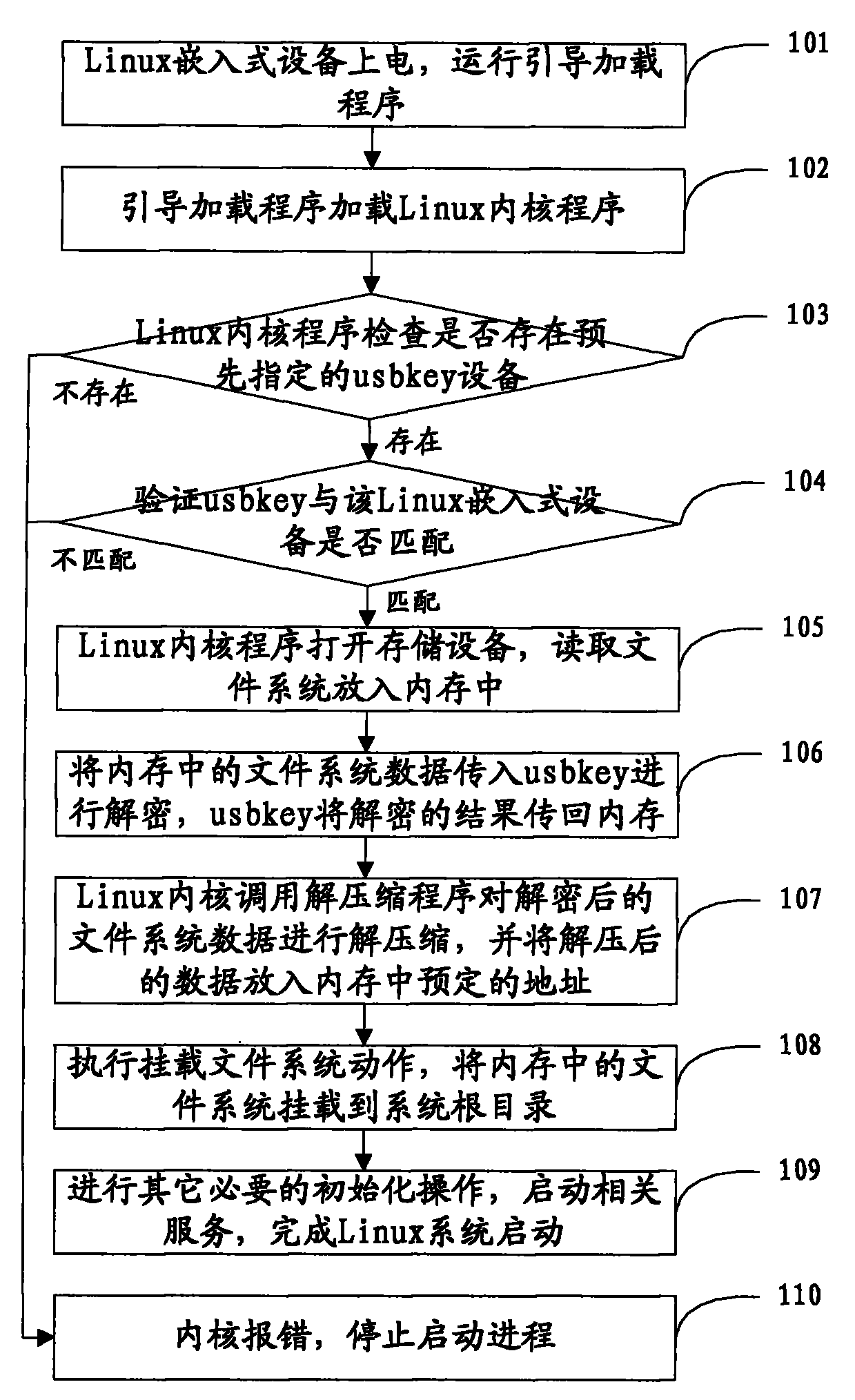
Safe startup method for Linux embedded system
ActiveCN101770386AImprove securityGuaranteed confidentialityProgram loading/initiatingPlaintextInternal memory
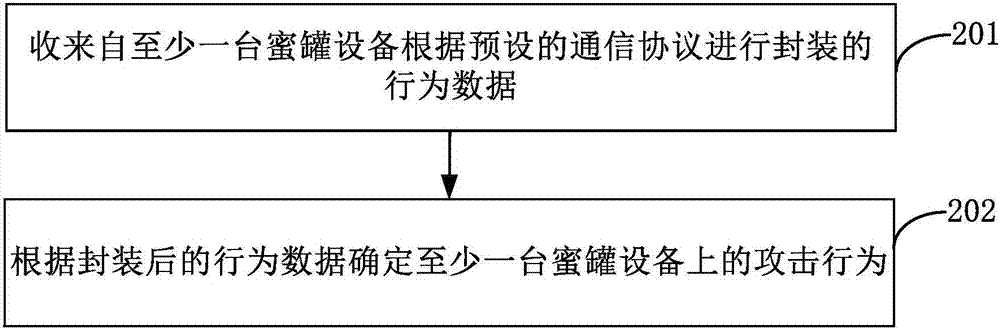
The invention discloses a safe startup method for a Linux embedded system and belongs to the field of information safety. The safe startup method for the Linux embedded system comprises that: a bootstrap loader is operated in a Linux embedded device to load Linux kernel; the Linux kernel checks whether predetermined encryption / decryption equipment is connected to the Linux embedded device; if thepredetermined encryption / decryption equipment is connected to the Linux embedded device, a cipher text of the Linux file system data is transmitted to the encryption / decryption equipment for decryption, the decrypted clear text of the Linux file system data is transmitted to an internal memory, a system root directory is mounted, and other operations for starting up the Linux embedded system are continuously executed; and if the predetermined encryption / decryption equipment is not connected to the Linux embedded device, the operation for starting up the Linux embedded system is stopped so as to guarantee the information safety of the Linux file system data.
Owner:北京坚石诚信科技有限公司
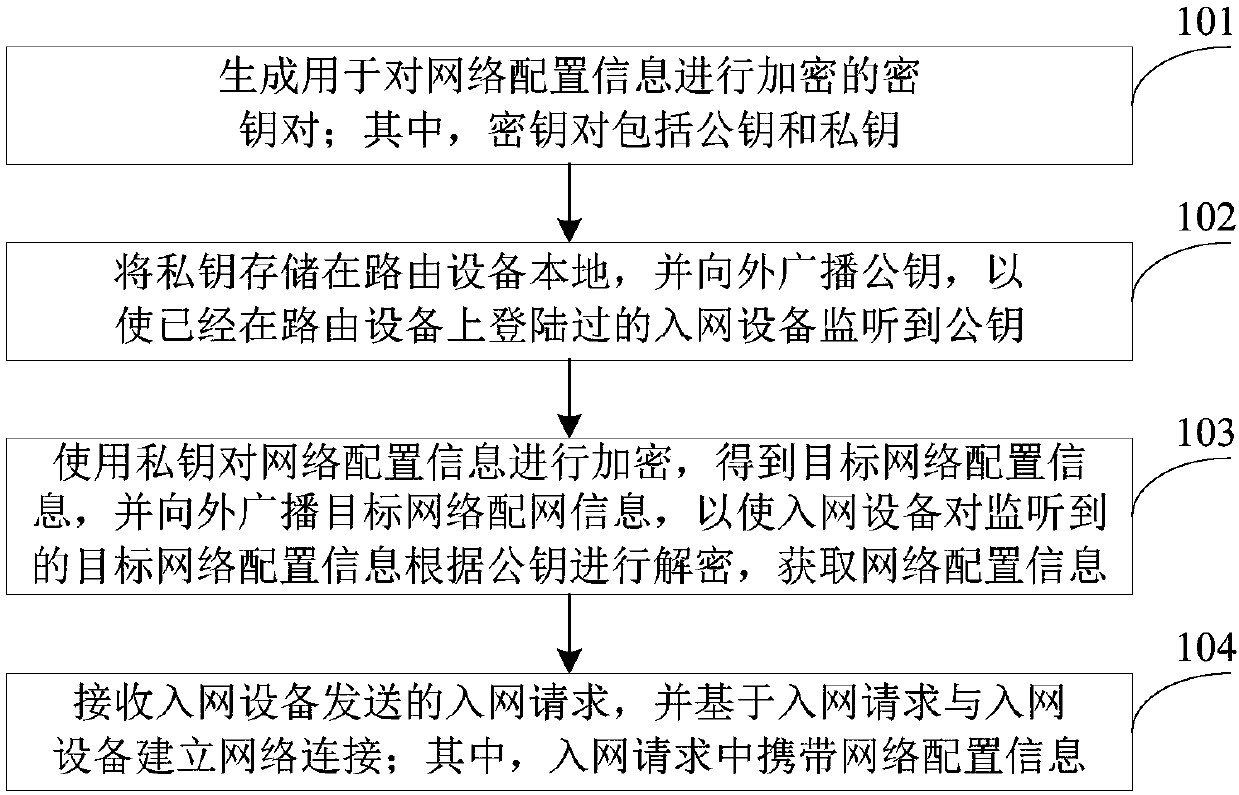
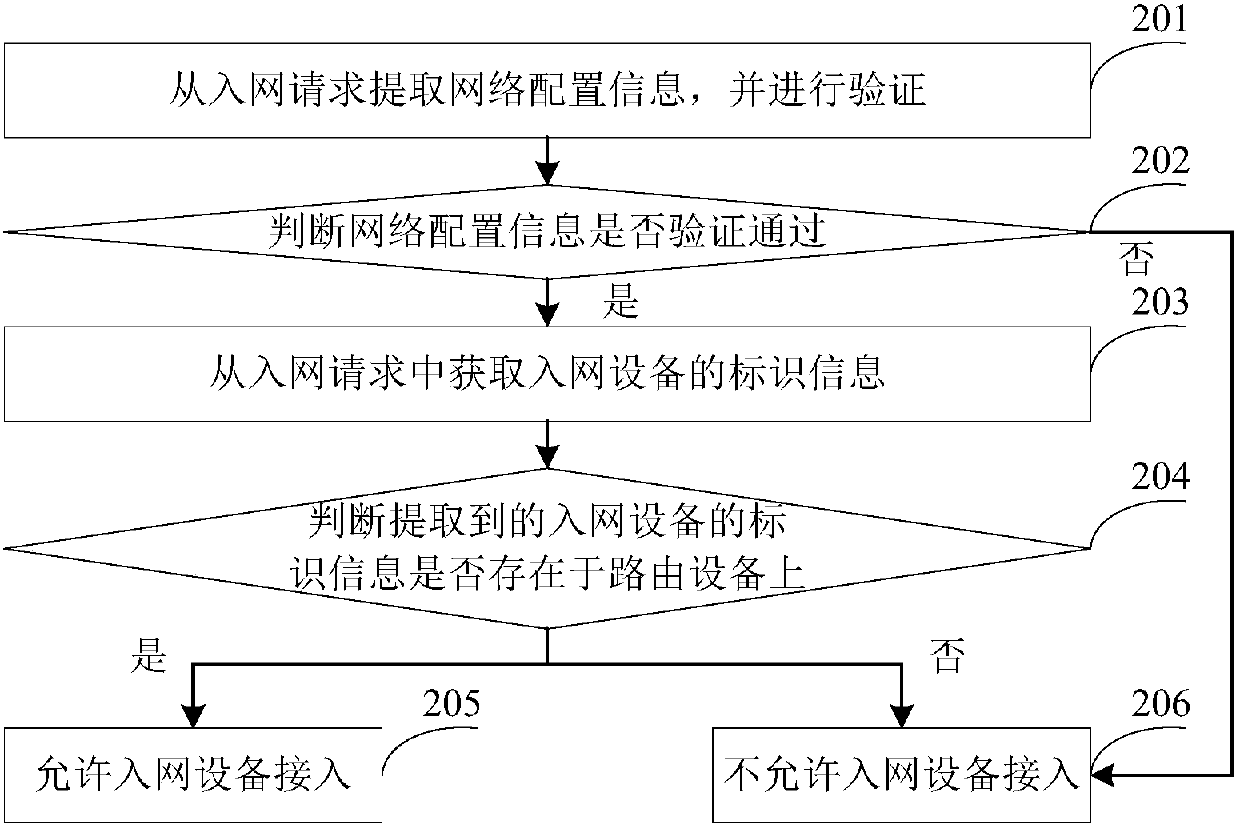
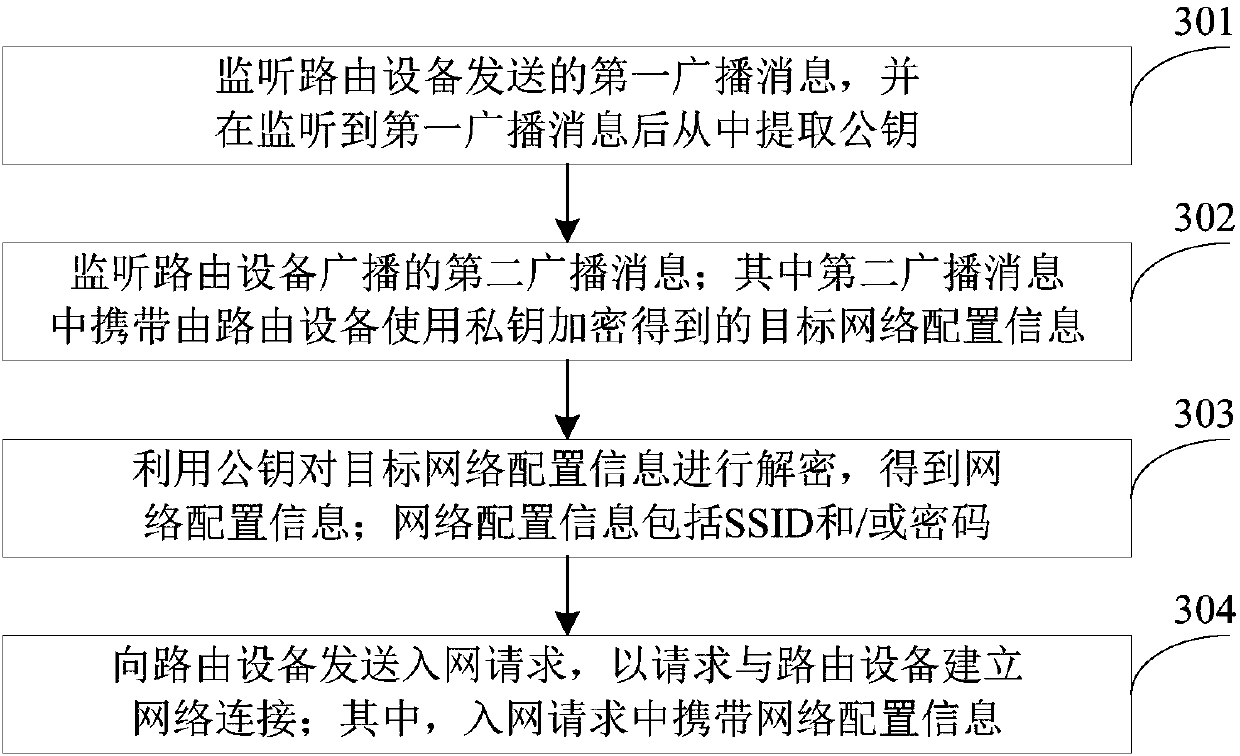
Network configuration method and system, routing equipment and network access equipment
ActiveCN107645725AEasy to operateEnsure safetyAssess restrictionData switching networksNetwork connectionNetwork access point
The invention provides a network configuration method and system, routing equipment and network access equipment. The method comprises the steps that a key pair used for encrypting network configuration information is generated; a private key is locally stored in the routing equipment and a public key is broadcasted to the outside so that the network access equipment logging in the routing equipment is enabled to monitor the public key; the network configuration information is encrypted by using the private key so that target network configuration information is obtained and the target networkconfiguration information is broadcasted to the outside, and the network access equipment is enabled to decrypt the monitored target network configuration information according to the public key to acquire the network configuration information; and the network access request transmitted by the network access equipment is received, and network connection with the network access equipment is established based on the network access request. According to the method, the network access equipment which previously logs in the routing equipment can automatically establish network connection with therouting equipment after the network configuration information of the routing equipment is modified so that the network access equipment does not need to perform network configuration again and then establish network connection with the routing equipment and the operation steps can be simplified.
Owner:GD MIDEA AIR-CONDITIONING EQUIP CO LTD
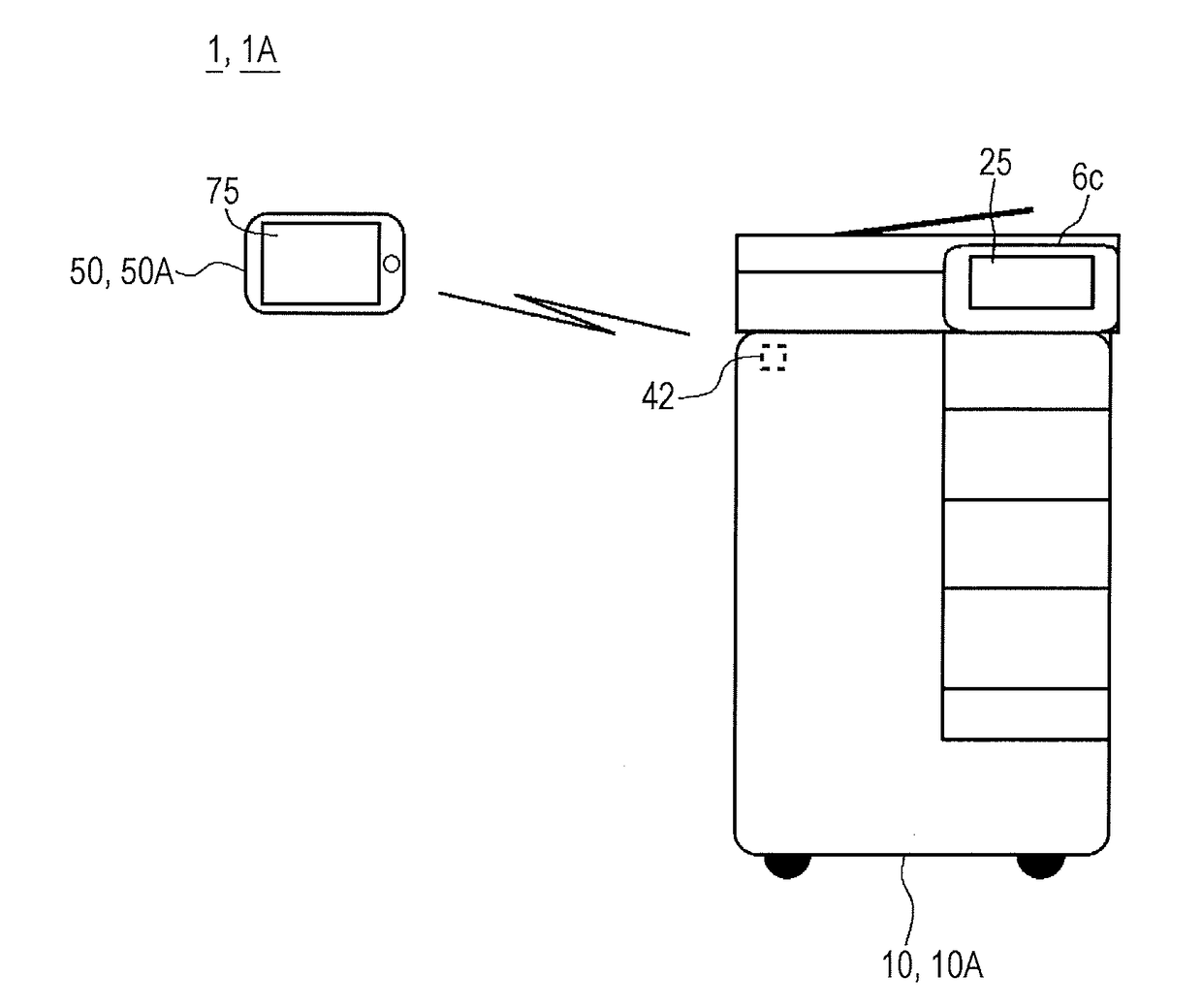
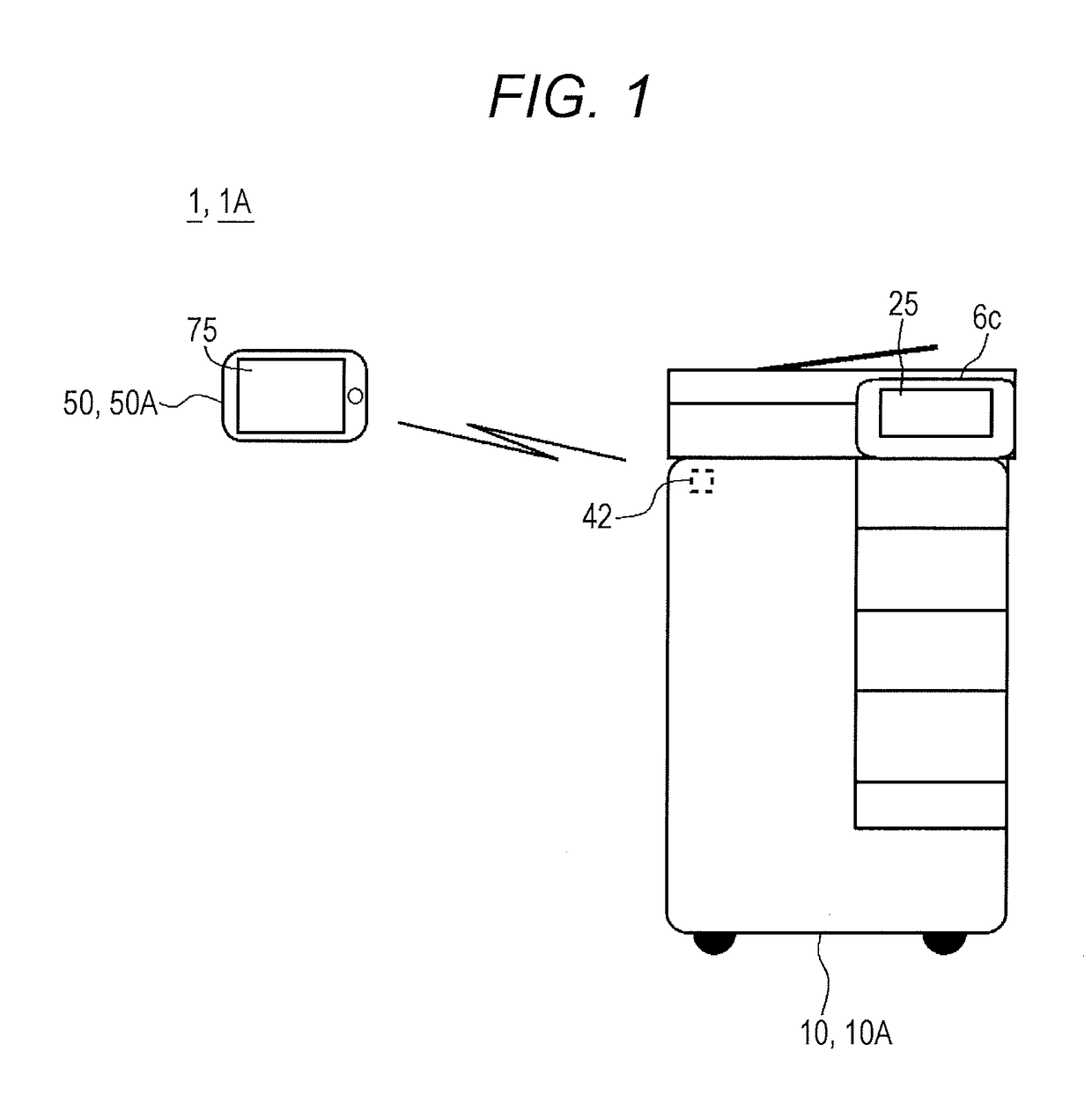
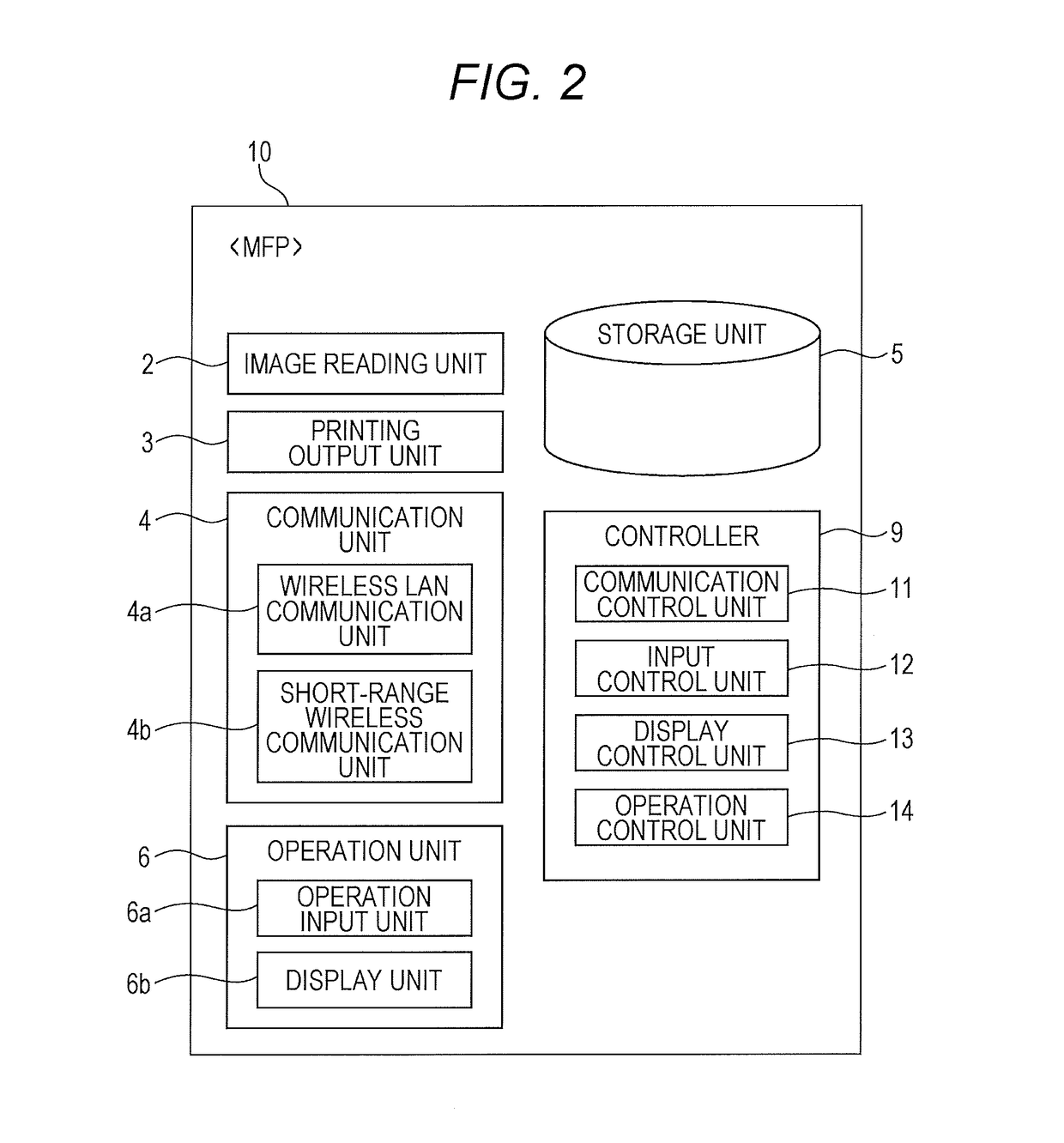
Image forming system and program
ActiveUS20170102903A1Prevent unauthorized accessPrevent loginNear-field transmissionPictoral communicationComputer hardwareImage formation
A non-transitory recording medium storing a computer readable program causes a computer included in a portable terminal to communicate with an image forming device to execute: a) a step of acquiring communication information from the image forming device via first wireless communication, the communication information being information for executing second wireless communication; b) a step of executing processing of confirming existence of a user who possesses the portable terminal in the vicinity of the image forming device; and c) a step of, on condition that existence of the user in the vicinity of the image forming device is confirmed in the step b), permitting registration processing of registering the communication information in the portable terminal in order to execute the second wireless communication, the communication information being communication information for the second wireless communication with the image forming device and being acquired in the step a).
Owner:KONICA MINOLTA INC
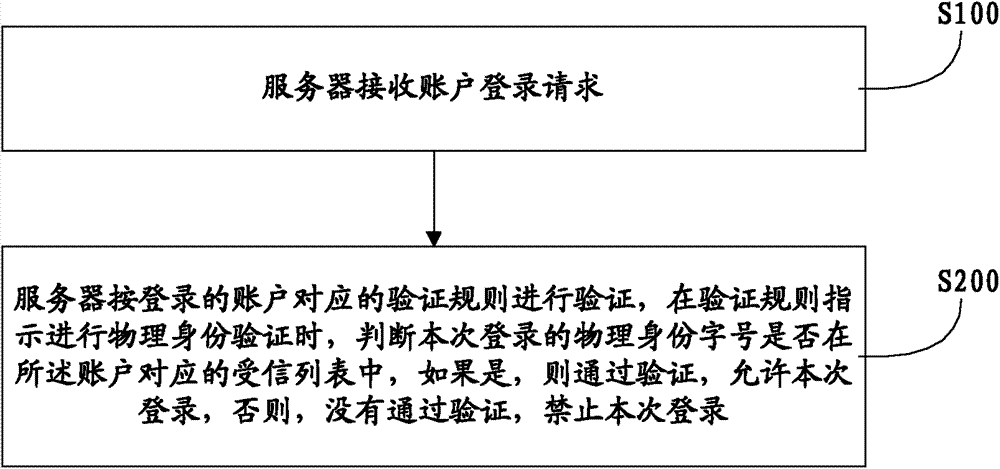
Account login method and system in internet
The invention discloses an account login method and a system in an internet. The method comprises: step 1, an account login request is received by a server; and step 2, the login request is verified through the server according to corresponding verifying rules of the logged in account, when the verifying rules indicate to conduct physical identification verification, the server judges whether a logged in physical identification word size is in a corresponding credit receiving list of the account or not, and if so, verification is passed, the login is permitted, otherwise, the verification is not passed, and the login is forbidden. The account login method and the system in the internet can avoid an unauthentic login and improve safety of the account.
Owner:ULTRAPOWER SOFTWARE
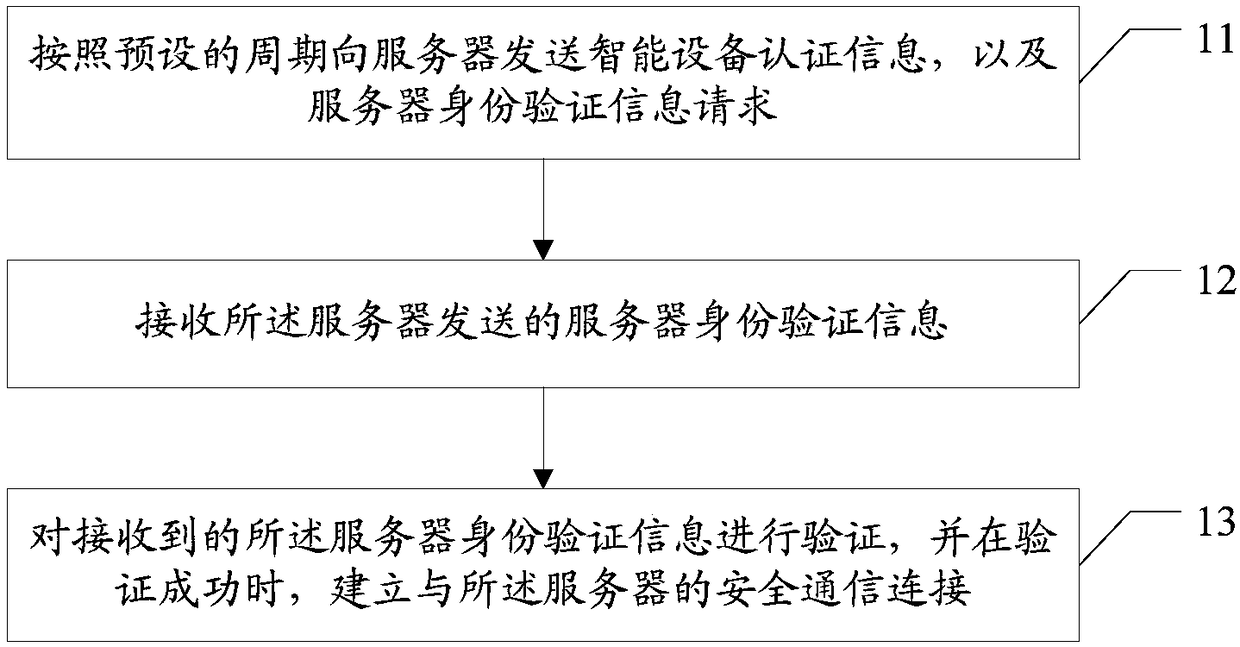
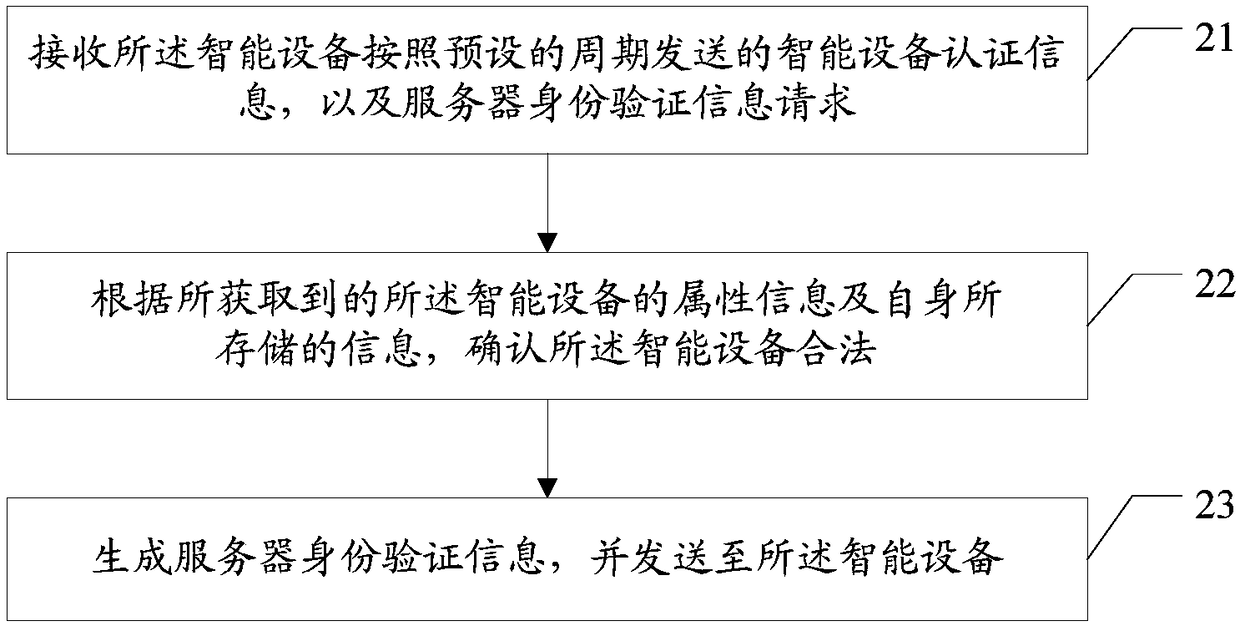
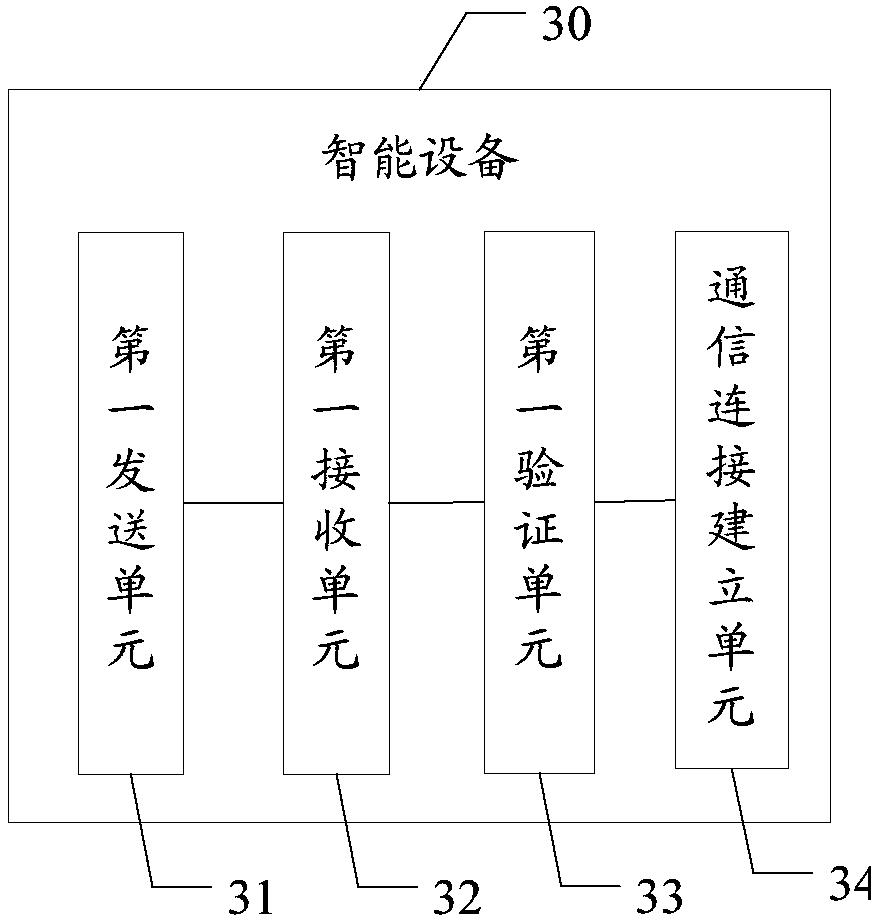
Data safety protection method, intelligent device, server and readable storage medium
InactiveCN109286599AFacilitate communicationAvoid attackKey distribution for secure communicationUser identity/authority verificationSecure communicationIntelligent equipment
The invention provides a data safety protection method, an intelligent device, a server and a readable storage medium. The data safety protection method comprises the steps of when over-the-air firmware updating is required, transmitting intelligent device authentication information and a server identity verification information request to a server according to a preset period, wherein the intelligent device authentication information comprises the attribute information of the intelligent device; receiving server identity verification information transmitted from the server, wherein the serveridentity verification information is generated by the server in confirming validity of the intelligent device according to the obtained attribute information of the intelligent device and the storedinformation itself after receiving the server identity verification information request; verifying the received server identity verification information, and when verification succeeds, establishing asafe communication connection with the server. The data safety protection method, the intelligent device, the server and the readable storage medium can improve communication safety in the system upgrading process of the intelligent device.
Owner:BEIJING SPREADTRUM HI TECH COMM TECH CO LTD
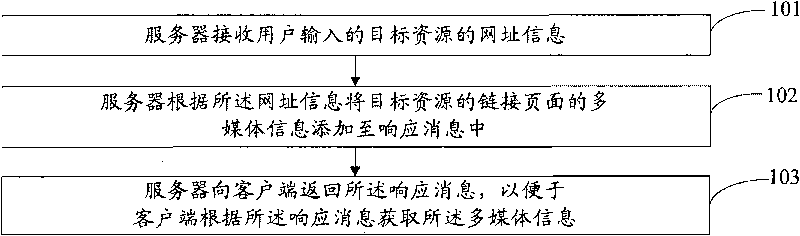
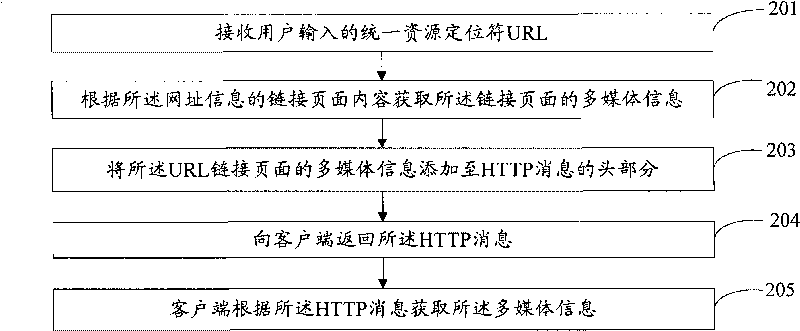
Method and device for acquiring information of target resources
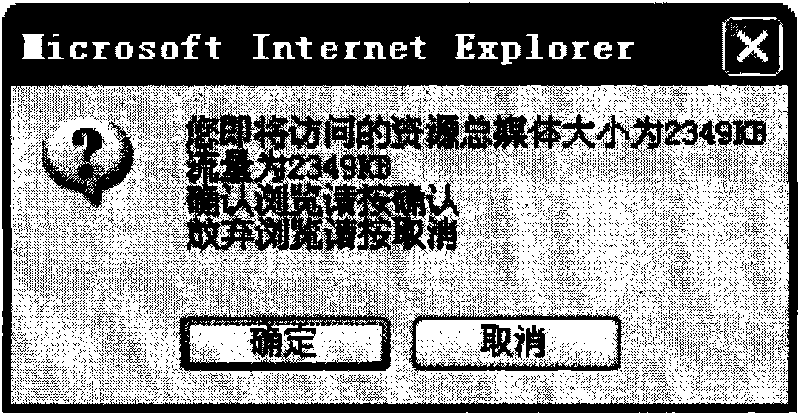
InactiveCN101741872AImprove login experiencePrevent loginTransmissionSpecial data processing applicationsUser inputClient-side
The embodiment discloses a method and a device for acquiring information of target resources. The method comprises the steps of: receiving the website information of the target resources input by users at first; adding the multimedia information of pages linked with the target resources to a response message in accordance with the website information, and returning the response message to a user terminal so that the user terminal can acquire the multimedia information in accordance with the response message. By the embodiment of the invention, the user terminal can acquire the multimedia information of the target resources in accordance with the response message returned by a server, and know the multimedia information of the target resources before browsing the target resources so that the user terminal can determine whether to continue to browse the target resources or not in accordance with the multimedia information, and the website access experience of users can be greatly improved.
Owner:HUAWEI SOFTWARE TECH
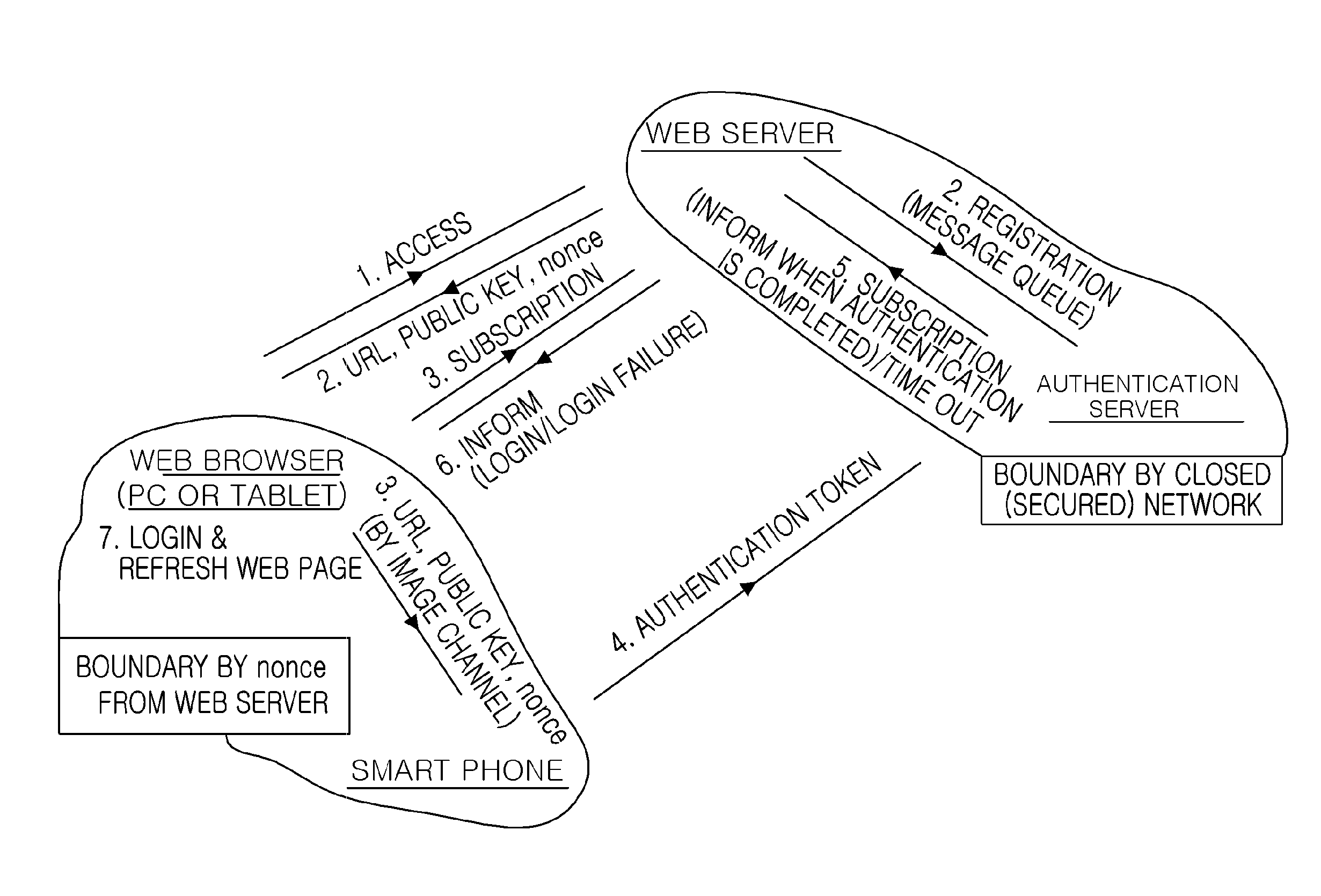
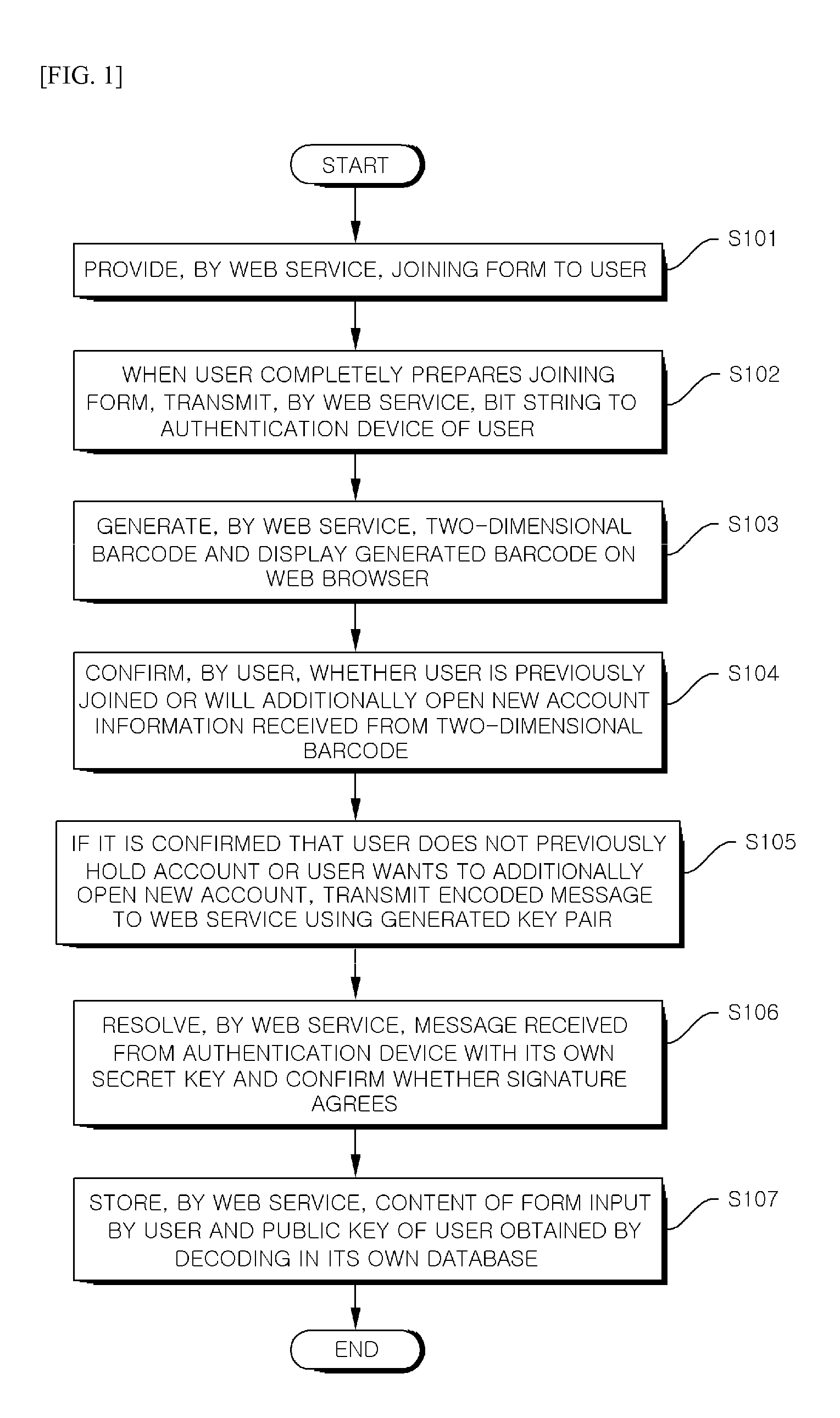
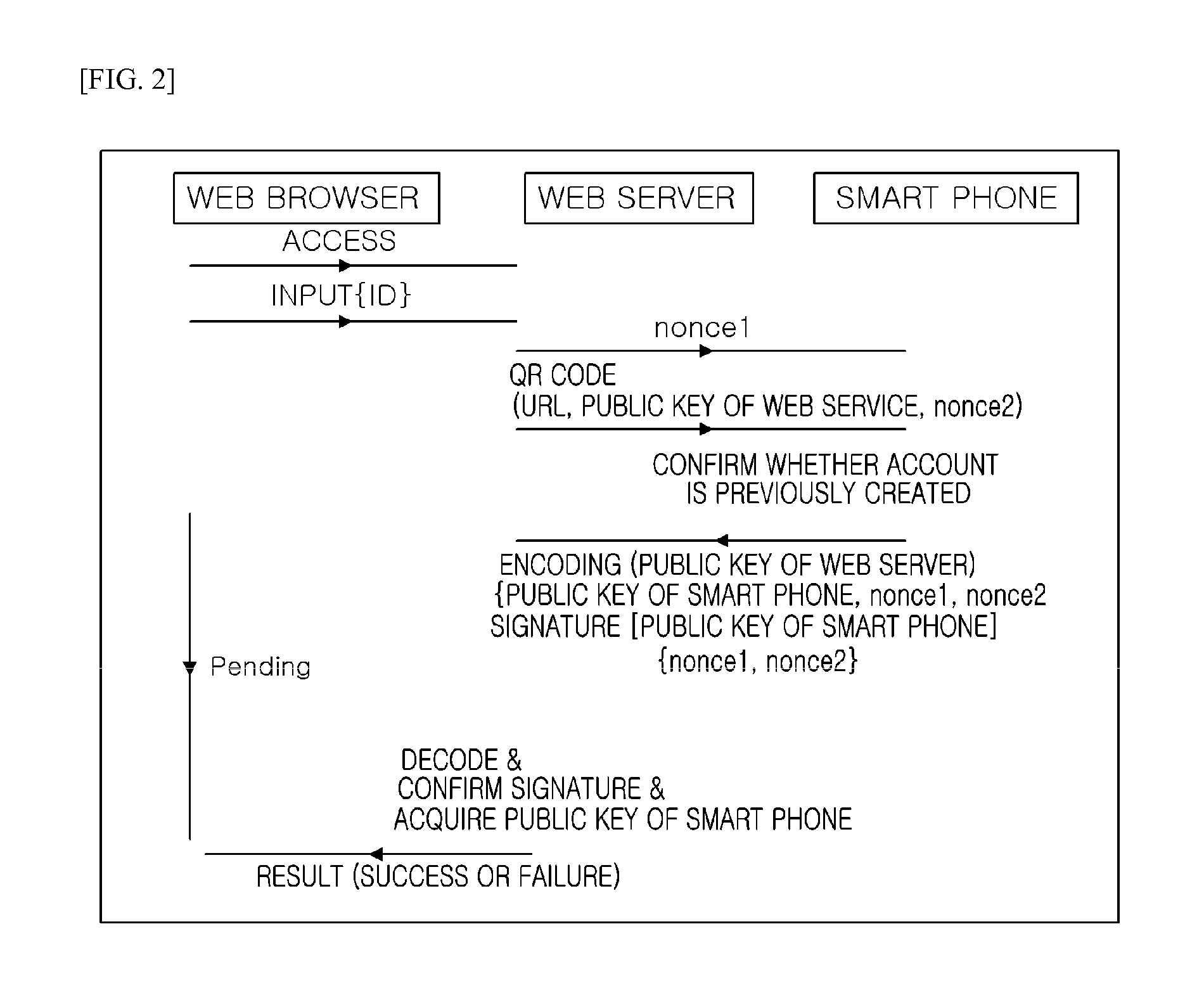
Method for web service user authentication
ActiveUS20150220718A1Ensure safetyConveniently performedDigital data processing detailsUser identity/authority verificationWeb servicePassword
Disclosed is a method for web service user authentication capable of increasing convenience while providing high security strength. The present invention has been made in an effort to provide a technique for conveniently performing user authentication by alleviating a user inconvenience of a memory of a password, storing a user password in a device which is carried by him / her at all times so as to use a powerful password, and using the password.
Owner:AJOU UNIV IND ACADEMIC COOP FOUND
Credible computer platform
InactiveCN101976320AControl accessPrevent tamperingInternal/peripheral component protectionElectricityTrusted Computing
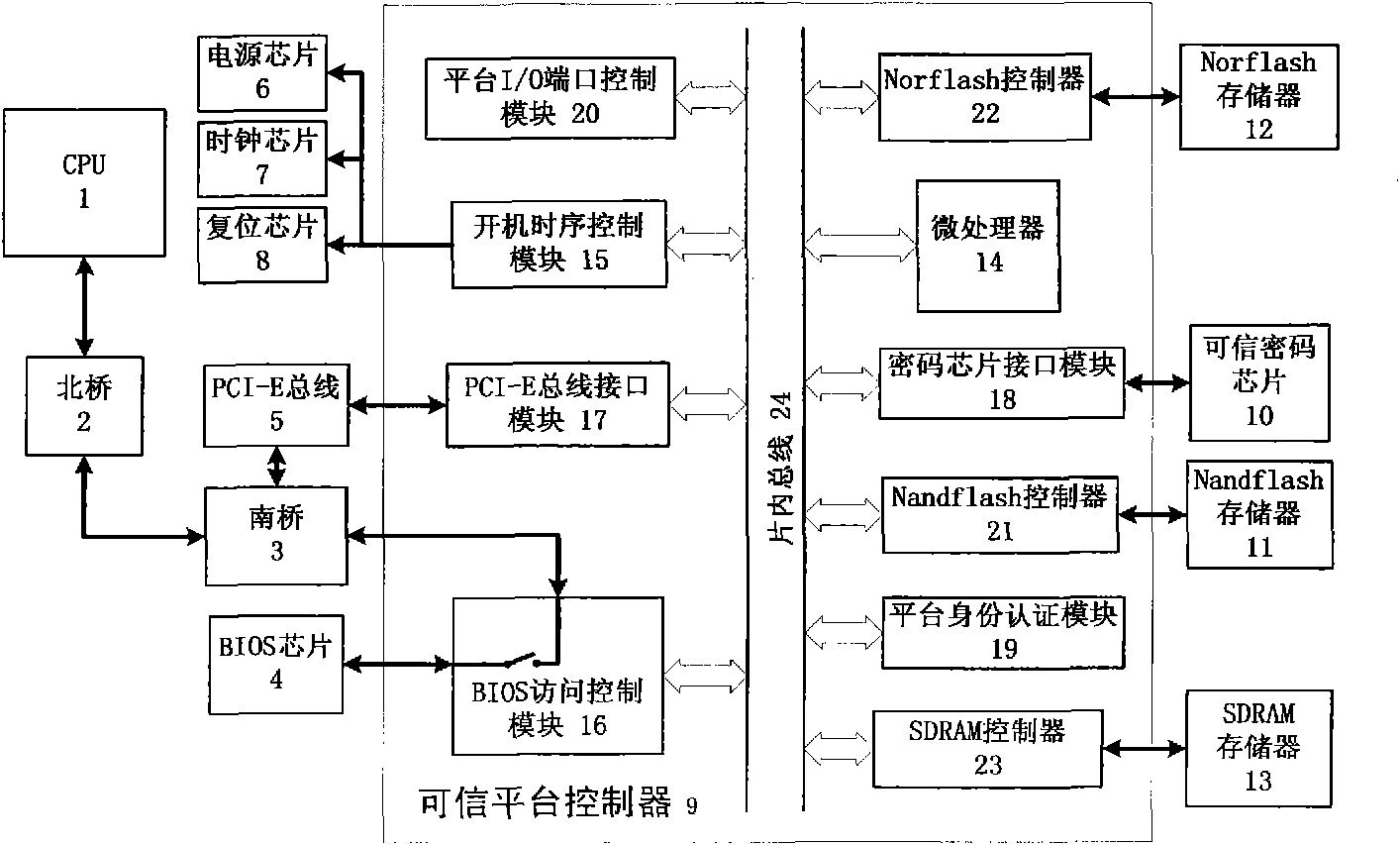
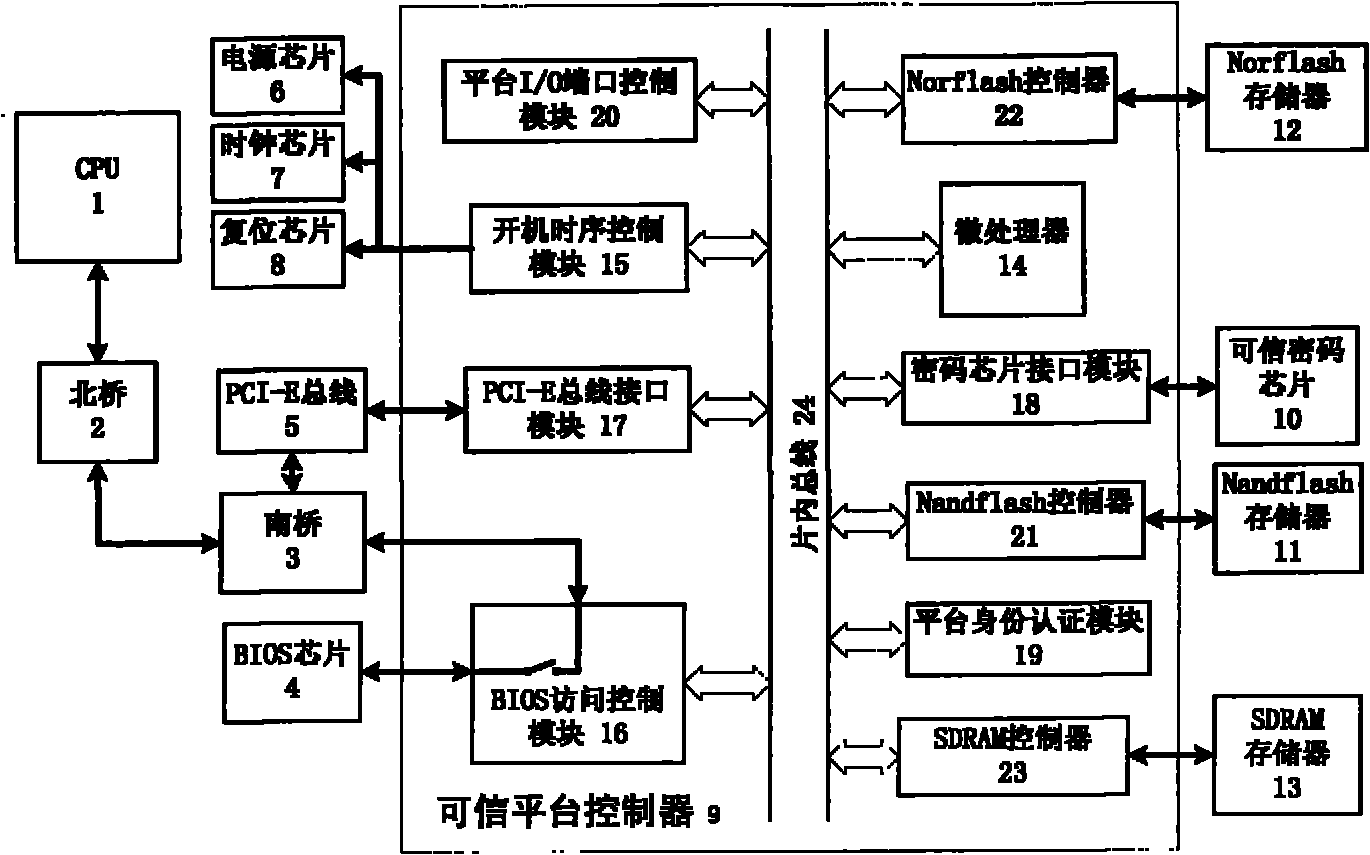
The invention discloses a credible computer platform, comprising a CPU (1), a North bridge (2), a South bridge (3), a credible platform controller (9), a credible crypto chip (10), a Nandflash storage (11), a Norflash storage (12) and a SDRAM (Synchronous Dynamic Random Access Memory) storage (13). The CPU (1) is bidirectionally connected with the North bridge (2), the North bridge (2) is bidirectionally connected with the South bridge (3), and buses are mutually connected inside the credible platform controller (9). The credible platform controller (9) isolates the South bridge (3) and a BIOS (Basic Input / Output System) chip (4) physically, and when being electrified, the credible platform controller (9) can be used for measuring and recovering BIOS completeness, verifying user identity, controlling the opening and closing of an I / O (Input / Output) port, and performing high-speed encryption / decryption on key data. The invention can be used for effectively controlling malicious codes from entering a computer system and preventing BIOS from falsification and illegal users from logging in, and thus, information safety protection capability of the system is improved.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
Honeypot deployment method, device and cloud server
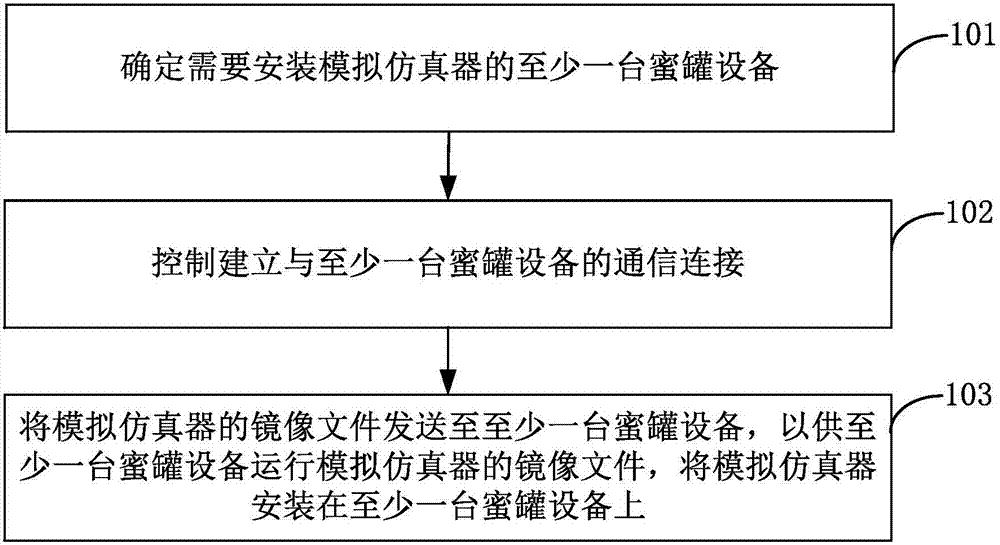
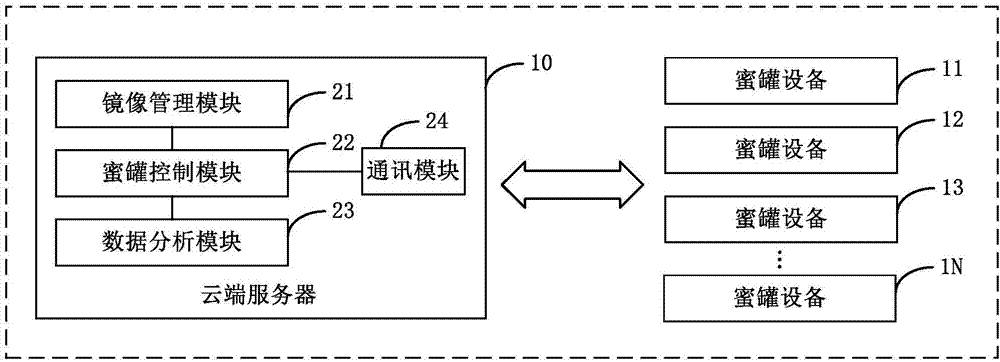
The invention provides a honeypot deployment method, device and a cloud server. The method comprises the following steps: determining at least one honeypot equipment which needs to be equipped with an analog simulator; controlling to establish a communication connection with the at least one honeypot equipment; and transmitting a mirror image of the analog simulator to the at least one honeypot equipment, so that the at least one honeypot equipment can run the mirror file of the analog simulator and install the analog simulator on the at least one honeypot equipment. The technical scheme of the invention greatly improves the efficiency of deploying the honeypot equipment in batches, realizes the deployment of the honeypot equipment in an automatic way, avoids logining the honeypot equipment manually on the honeypot device, and reduces the deployment cost of the honeypot equipment.
Owner:ALIBABA GRP HLDG LTD
Team organizing video method, device and system used in team organizing game
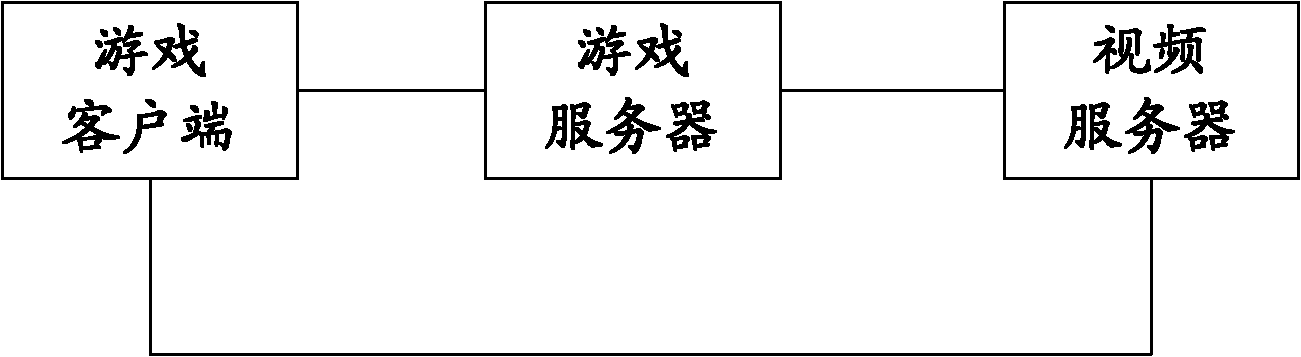
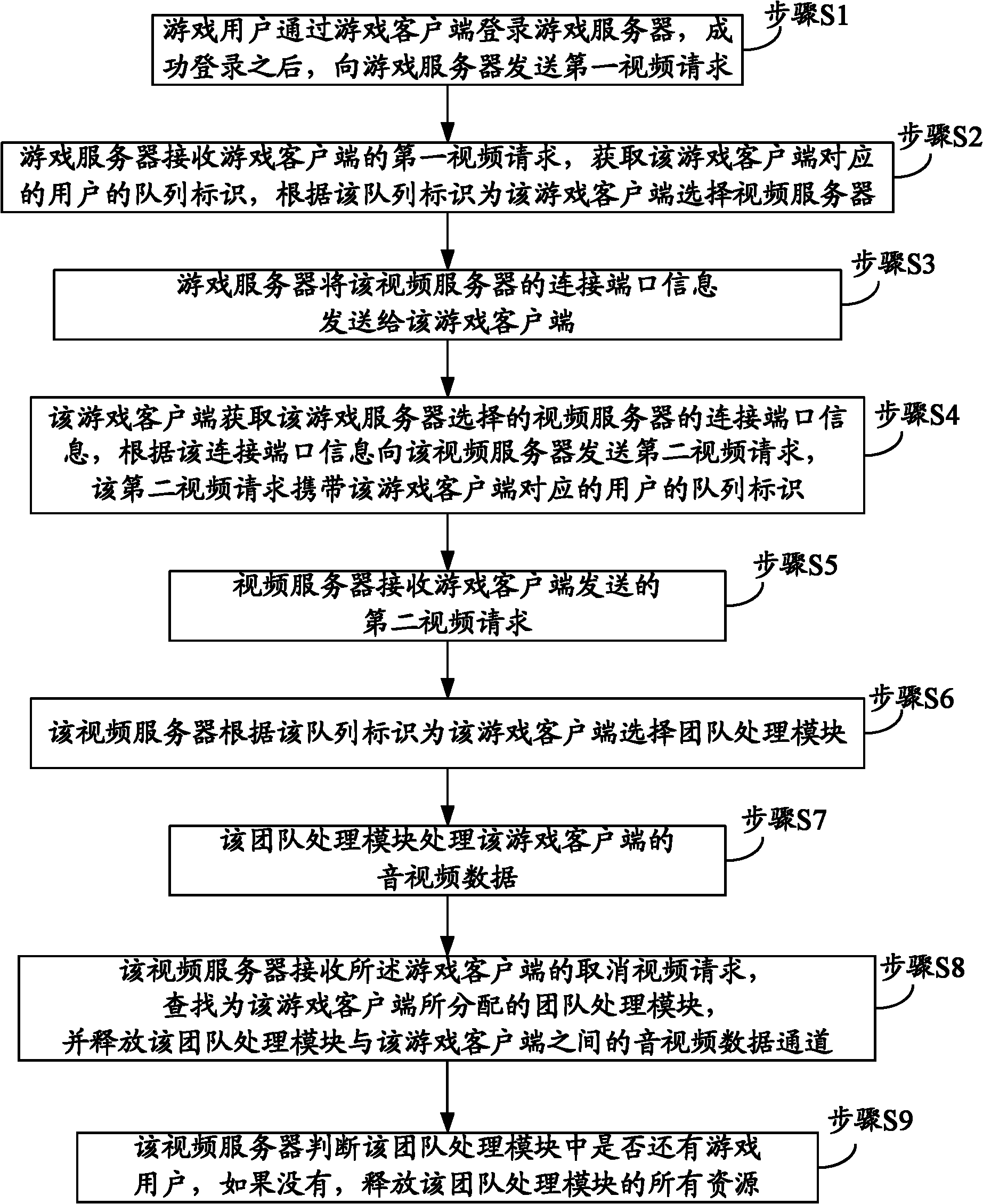
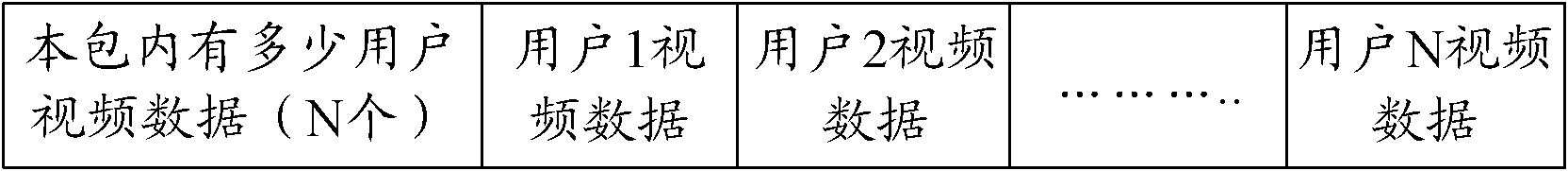
ActiveCN102185856AImprove interactivityTroubleshoot game interruptionsTransmissionSelective content distributionClient-sideGame server
The invention discloses a team organizing video method, a team organizing video device and a team organizing video system used in a team organizing game, aiming at reducing the waste of network resources and facilitating management. The team organizing video system used in the team organizing game comprises a game client terminal, a game server and a video server, wherein the game client terminal is used for sending a first video request to the game server, obtaining connecting port information of the video server selected by the game server, and sending a second video request to the video server according to the connecting port information; the second video request carries the queue identification of a user corresponding to the game client terminal; the game server is used for receiving the first video request of the game client terminal, obtaining the queue identification of the user corresponding to the game client terminal, and selecting the video server for the game client terminal according to the queue identification; and the video server is used for receiving the second video request sent by the game client terminal, and selecting a team processing module for the game client terminal according to the queue identification to process audio / video data of the game client terminal.
Owner:贵阳语玩科技有限公司
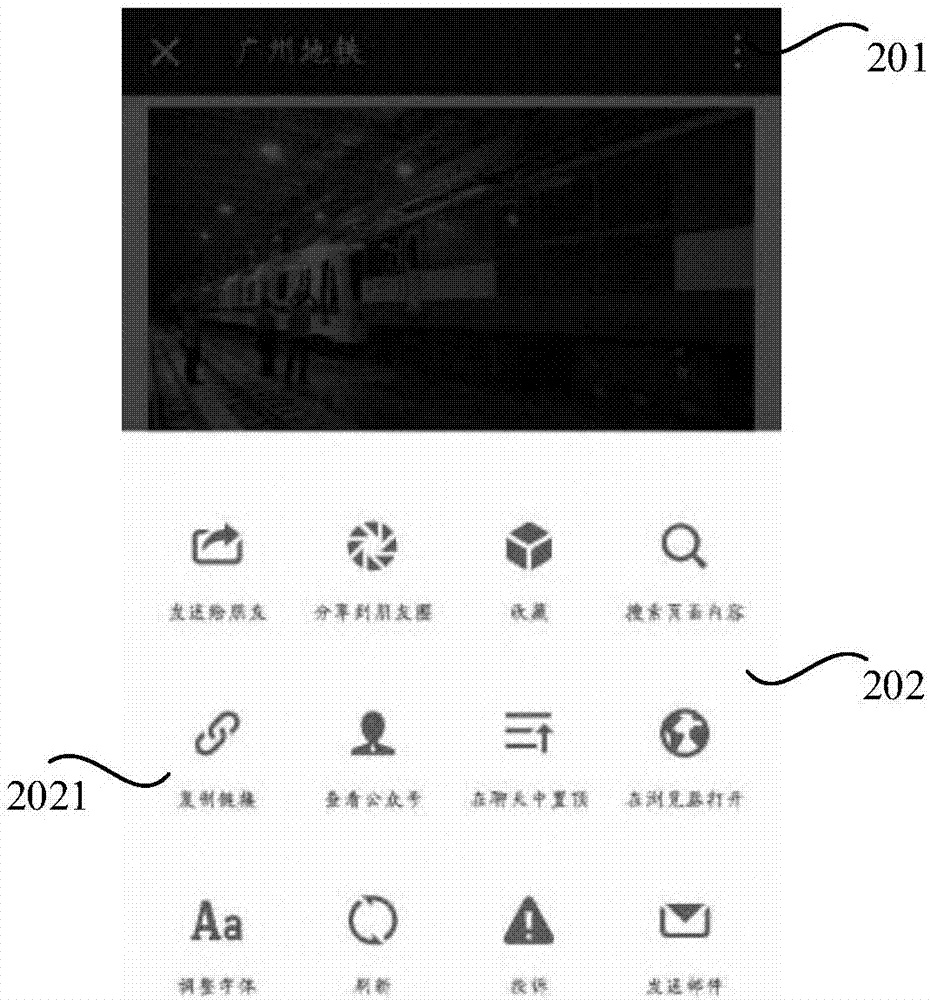
Collecting method and device of pages and mobile terminal
ActiveCN107329985ACollection operations to avoidCollection realizedSubstation equipmentSpecial data processing applicationsDatabaseComputer terminal
The embodiment of the invention provides a collecting method and device of pages and a mobile terminal. The method comprises the steps that collection operations aiming at loaded pages in first applications are detected; according to the collection operations, page information of the pages is obtained; according to the page information, favorite information is aggregated in second applications. On one hand, the pages of different first applications are collected in the second applications, it is avoided that users log in accounts and collect the pages in different first applications, the number of accounts is reduced, the convenience of management processing is improved, the number of confused collected pages is reduced, and the first applications are prevented from being started repeatedly for searching; on the other hand, additional collection functions can be provided for the first applications which do not support the collection functions, so that page collection is achieved, additional recording by using modes such as bookmarks is avoided, and the probability of the collected pages being forgotten by the users is reduced.
Owner:BEIJING ANYUNSHIJI TECH CO LTD
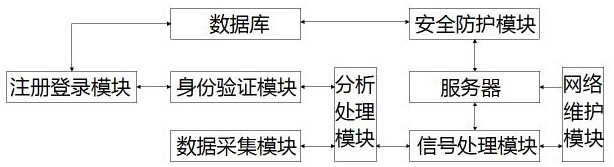
Network security protection method for Internet of Things equipment
The invention discloses a network security protection method for Internet of Things equipment. After the user logs in, the registration and login module sends the user information to the identity verification module to verify the login information of the user through the identity verification module; information of a webpage is collected through the data collection module; the data acquisition module is used for acquiring information of a website, the analysis processing module is used for analyzing and processing the information, the signal processing module is used for processing corresponding signals and sending generated processing signals to the server, and the network maintenance module is used for receiving network maintenance signals and maintaining a network. Security maintenancemeasures is performed on the server through the security protection module, the security maintenance measures are recorded and the security maintenance measures are sent to the database for storage; the system has strong safety performance, and daily safety maintenance is performed on the server so that the network invasion probability is enabled to be lower.
Owner:杭州优云科技有限公司
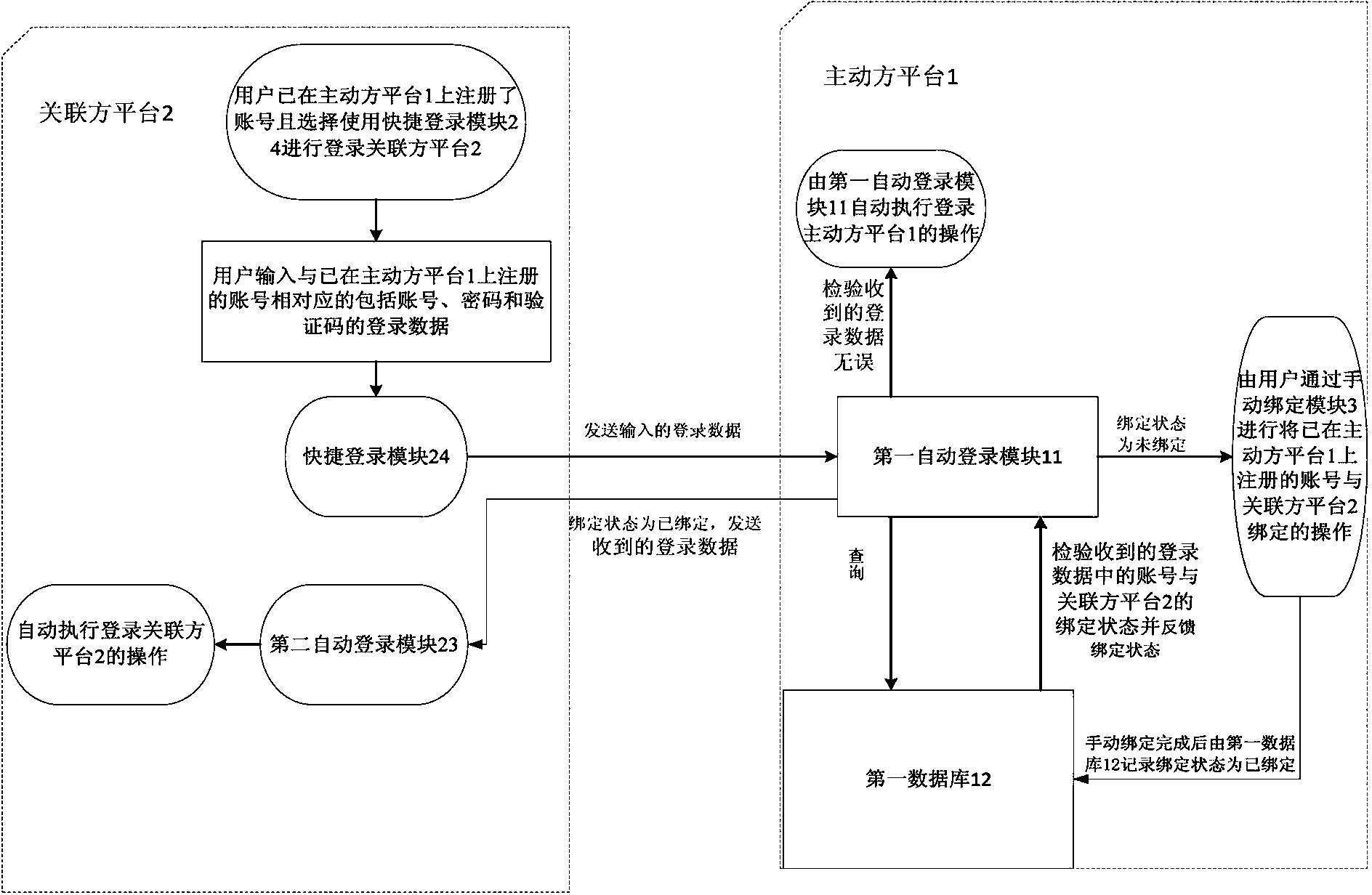
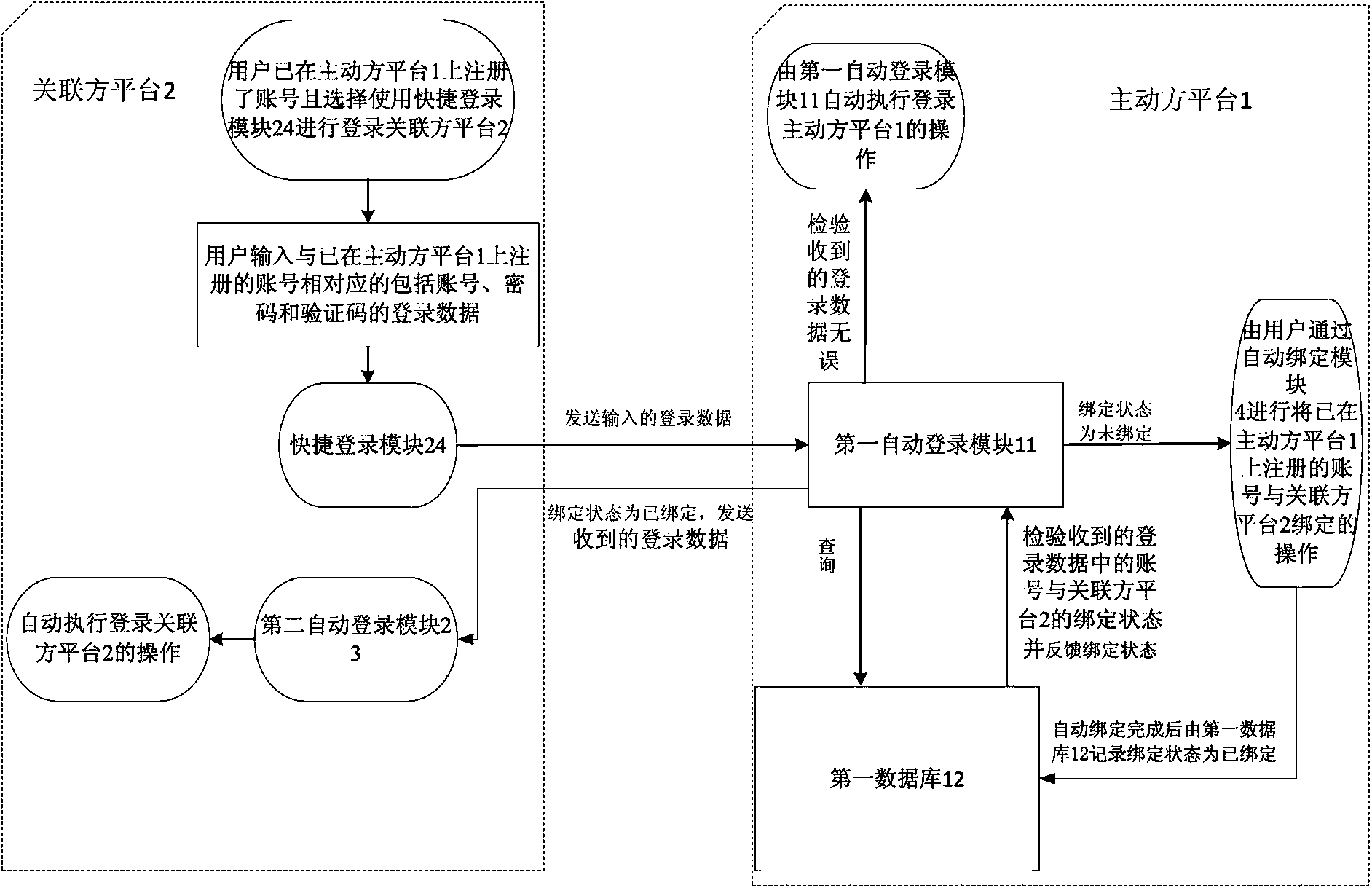
Method for synchronously logging in to double platforms
InactiveCN103595537AImprove conveniencePrevent loginUser identity/authority verificationData synchronizationTransaction data
Owner:NINGBO ZHIXIANG NETWORK TECH SERVICE
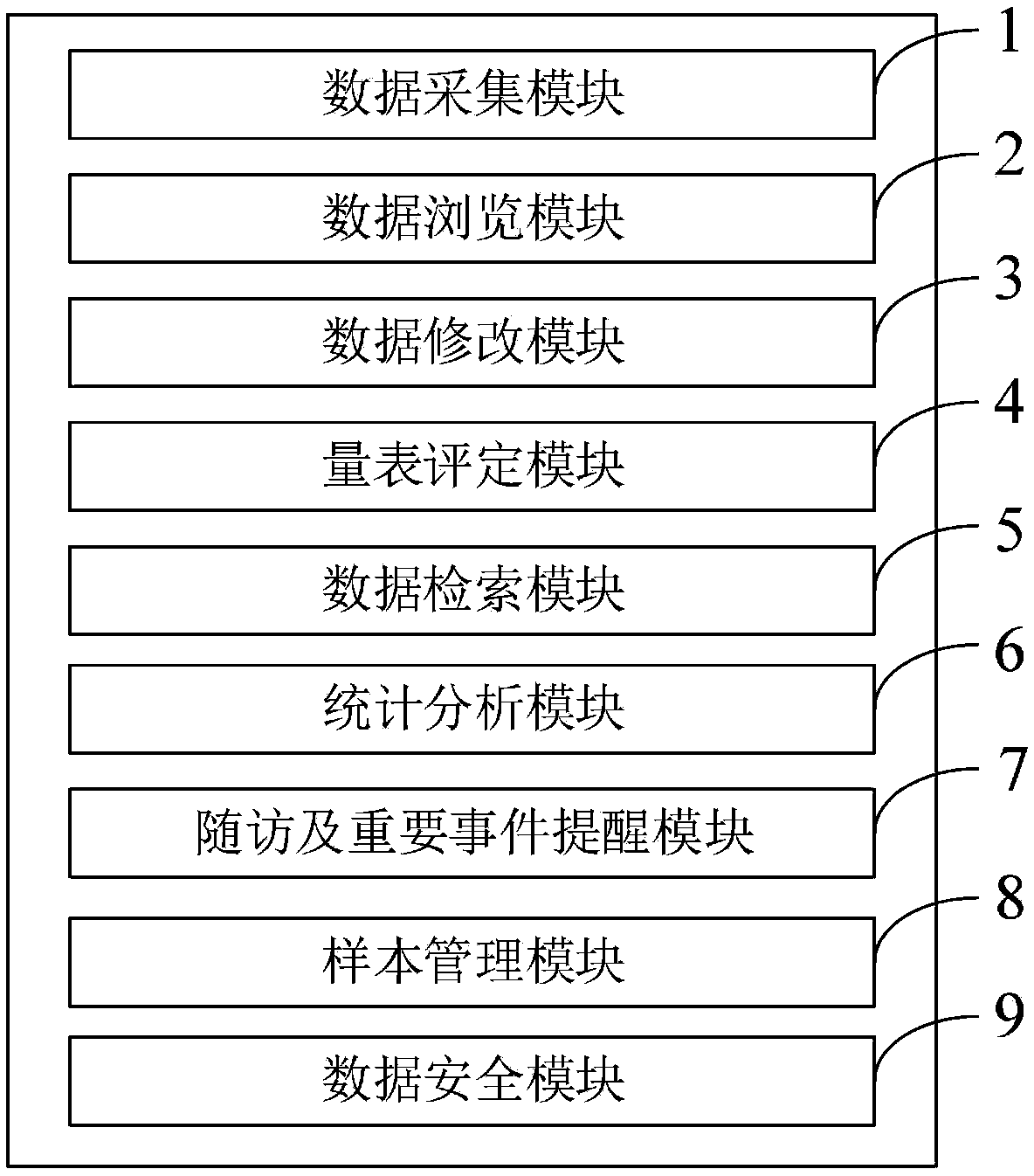
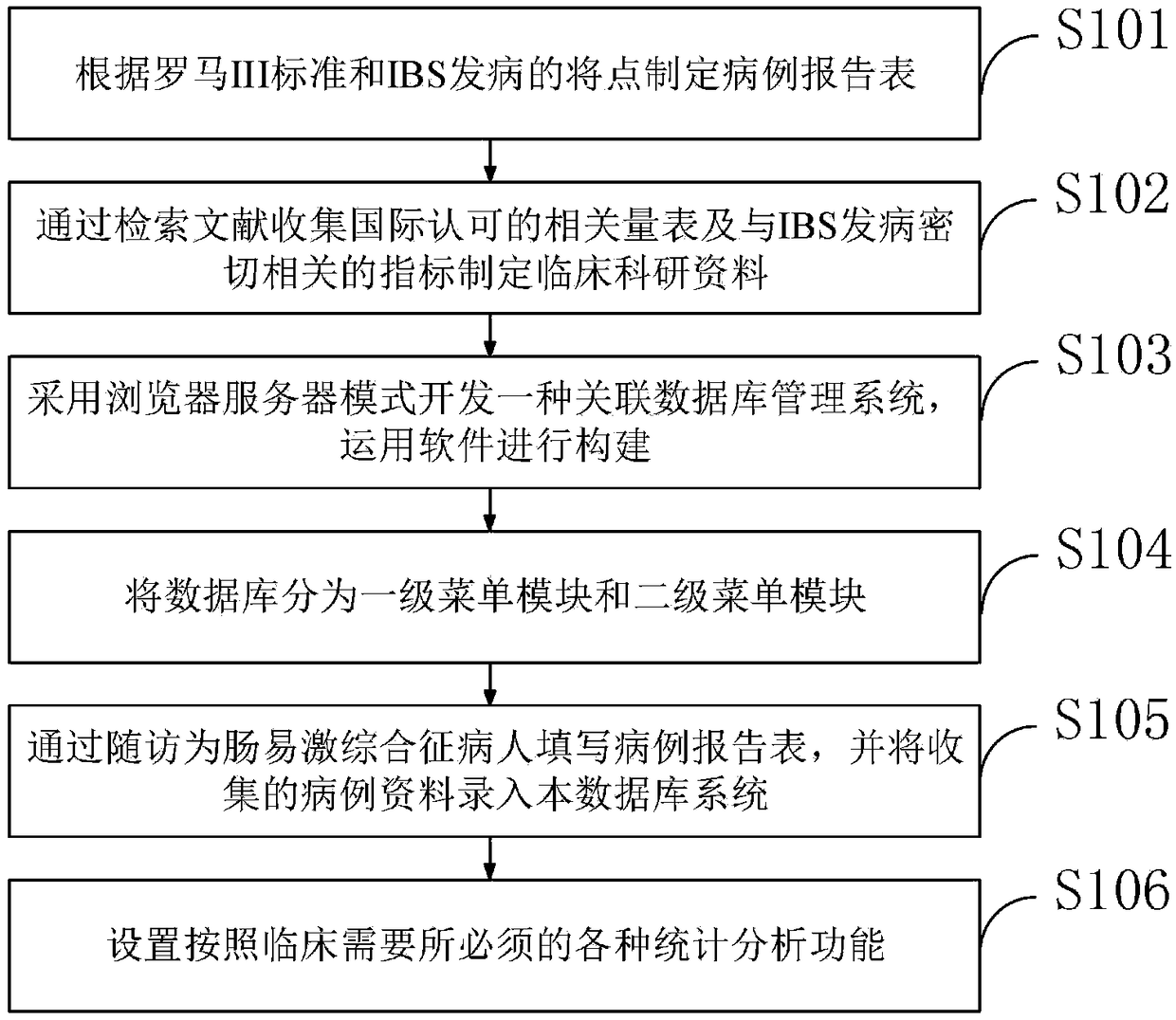
Clinical data platform design method of irritable bowel syndrome
InactiveCN109036539AEnsure consistencyIntegrity guaranteedMedical data miningMedical automated diagnosisWestern medicineComputer Aided Design
The invention belongs to the technical field of computer auxiliary design, and discloses a clinical data platform design method of an irritable bowel syndrome. The method includes following steps: establishment of clinical data, scientific research data and a database system, module design of a database, case collection, and data statistics and analysis. According to the method, data acquisition is performed according to a pre-designed complete and standard CRF table, the integrated database with wide coverage and high practical value is established through input of a background language stepby step according to the requirement for establishing the database, functions of the database system can be modified or added by entering the database from a server, the functions of the database system can be extended according to a specific condition, the maintenance and the extension are convenient, the database not only collects conventional diagnosis and treatment data of western medicine, but also collects diagnosis and treatment data of traditional Chinese medicine syndrome differentiation and traditional Chinese medicine treatment in an emphasized manner, and a platform is provided forexploration of the optimal Chinese and western diagnosis and treatment scheme of the treatment of the irritable bowel syndrome.
Owner:GUANGDONG HOSPITAL OF TRADITIONAL CHINESE MEDICINE
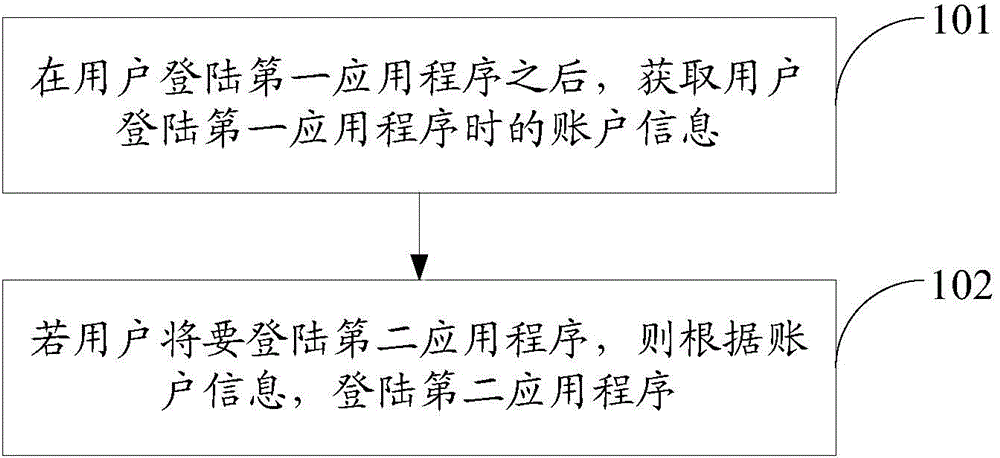
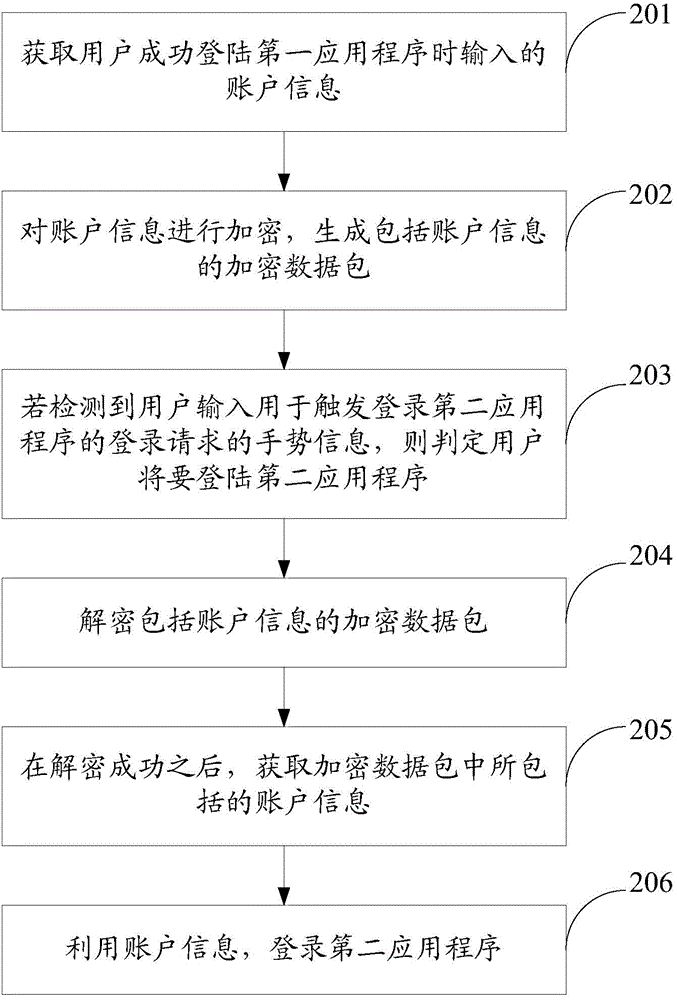
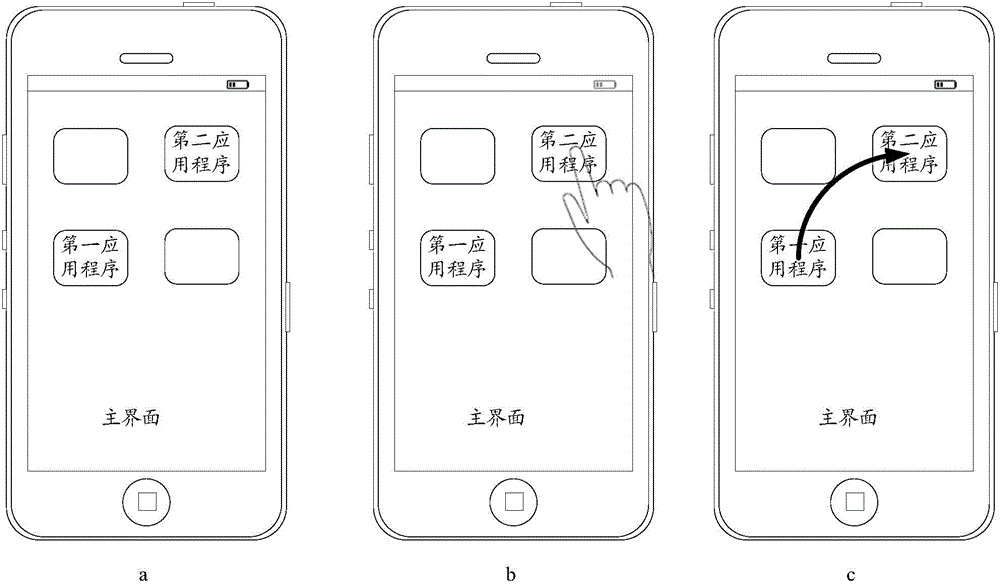
Mobile terminal application program login method and equipment
InactiveCN104951366APrevent loginImprove experienceProgram initiation/switchingSoftware engineeringApplication software
An embodiment of the invention provides a mobile terminal application program login method and equipment and belongs to the field of communication. The mobile terminal application program login method comprise steps as follows: acquiring account information of a user after the user logs in the first application program; logging in a second application program according to the account information if the user logs in the second application program, wherein the account information of the first application program is the same as that of the second application program. After the user logs in the first application program, the second application program with the account information the same as the first application program is logged in according to the account information of the first application program, the user does not need to manually input the account information to log in the second application program, the application program login procedure is simplified, the application program login efficiency is improved, and the user experience is improved.
Owner:SHANGHAI YIWAN NETWORK SCI & TECH
Big data cluster host management method and management system as well as server
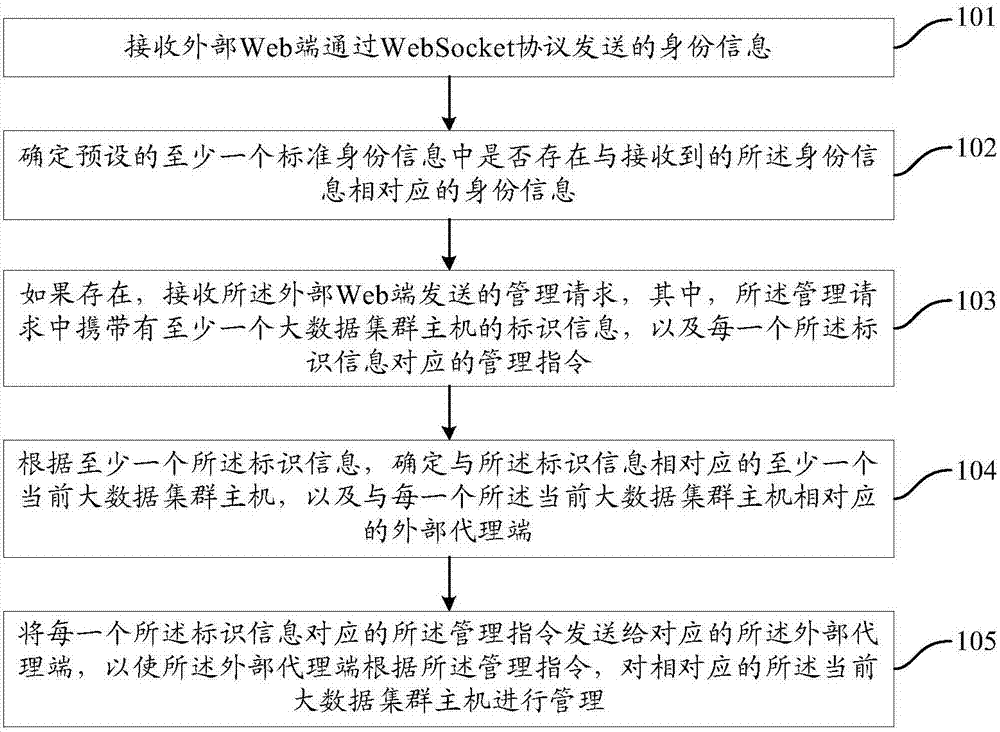
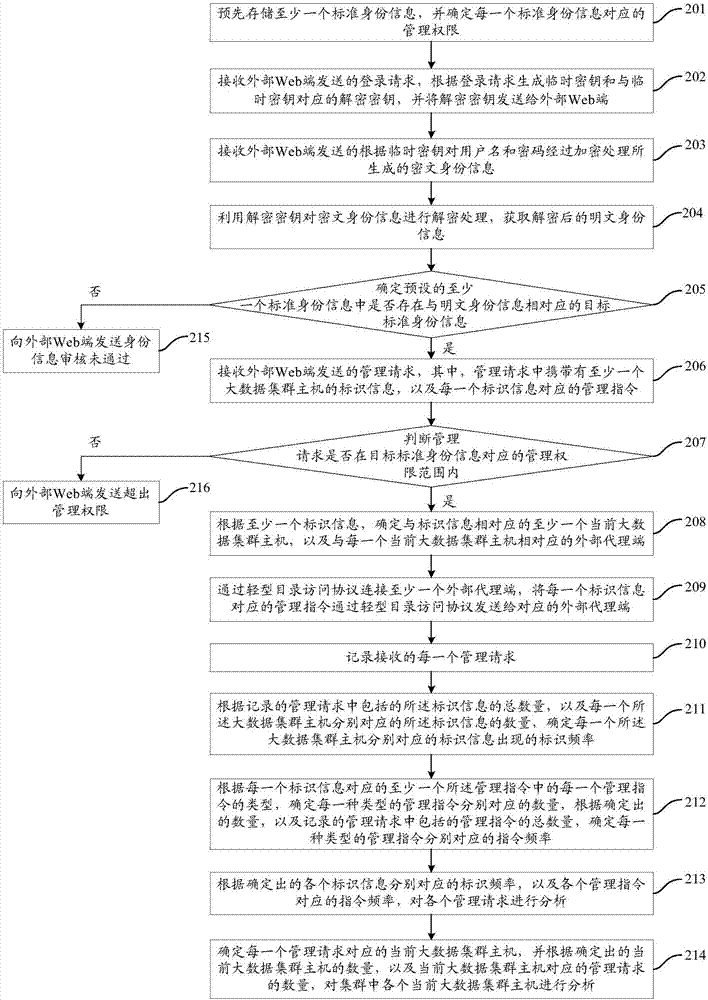
The invention provides a big data cluster host management method and management system as well as a server. The big data cluster host management method, applied to the server, comprises the steps of receiving identity information sent by an external Web end through a WebSocket protocol; determining whether identity information corresponding to the received identity information exists in the preset at least one piece of standard identity information; if so, receiving a management request sent by the external Web end, determining at least a current big data cluster host which corresponds to the identifier information and an external agent end which corresponds to each current big data cluster host based on the identifier information in the at least one management request; and sending a management command which corresponds to each piece of the identifier information to the corresponding external agent end so as to enable the external agent end to manage the corresponding current big data cluster host based on the management command. The scheme can simplify the management operation of a worker when managing the host.
Owner:INSPUR SOFTWARE CO LTD
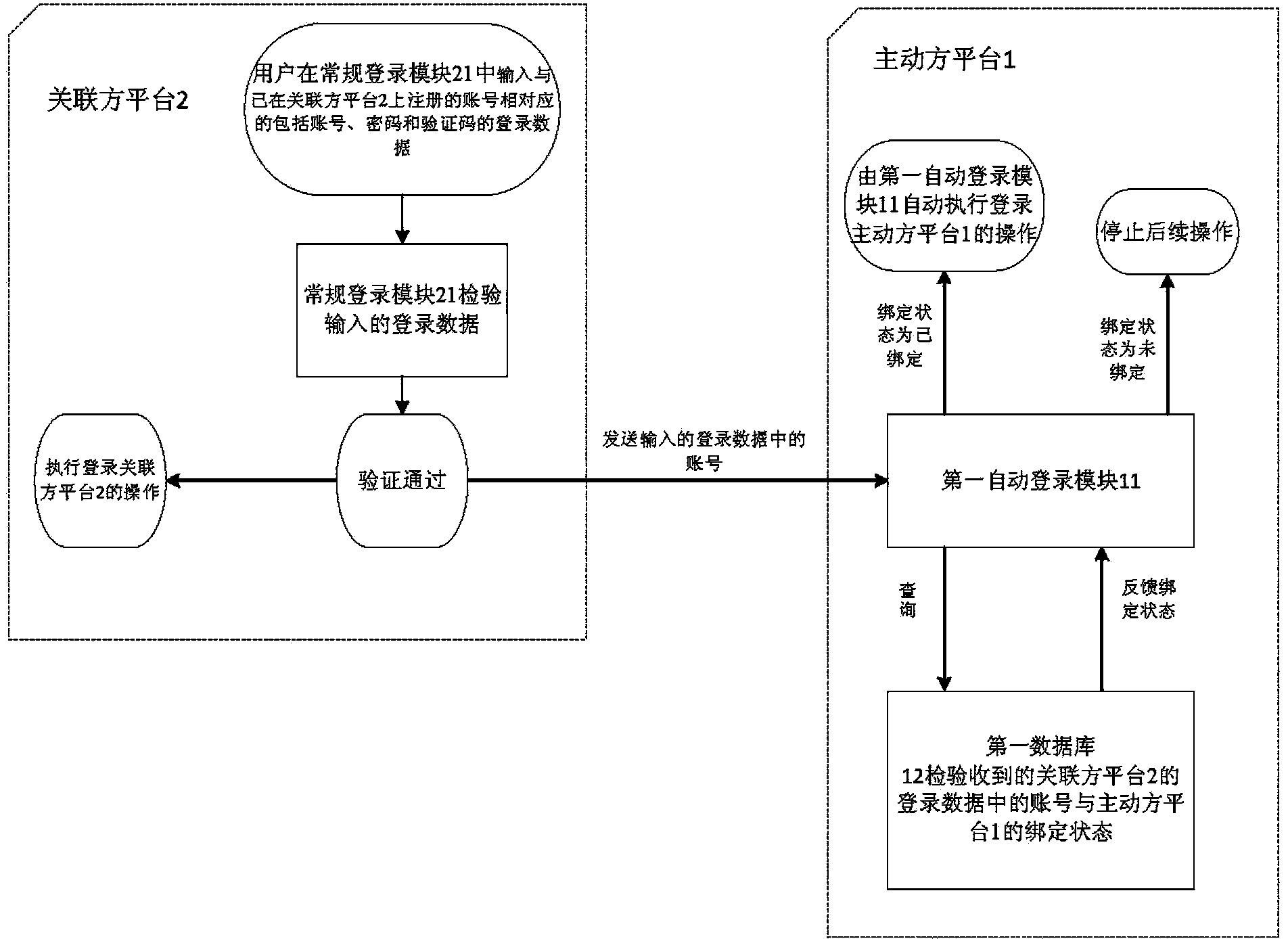
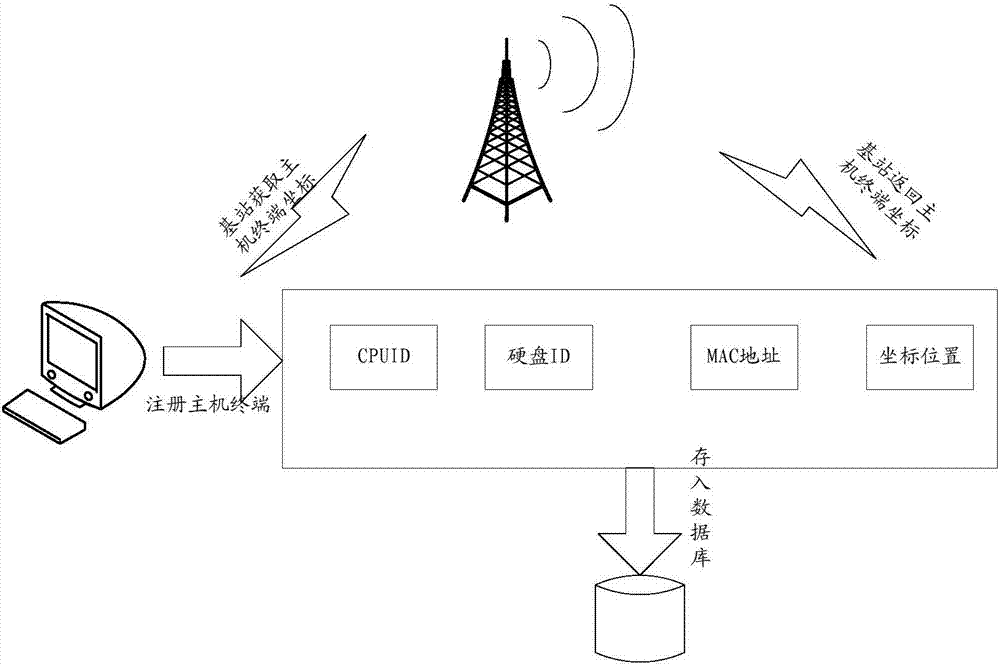
Internet site login system based on intelligent equipment monitoring and user identity recognition
ActiveCN110611685AImprove identityIdentity theftInternal/peripheral component protectionDigital data authenticationFull life cycleIdentity recognition
The invention provides an Internet site login system based on intelligent equipment monitoring and user identity recognition. The system comprises a cloud server and clients, and the clients comprisea user client, a maintenance client and a production client. The invention relates to an integrated system for controlling a user to log in an internet site through user identity recognition and binding of hardware features of intelligent equipment and the user identity recognition. Hardware characteristics of the intelligent equipment, all stages of the full life cycle of the intelligent hardware, ownership of a user to the intelligent equipment, login and query states of the user in a cloud server through the equipment, login and use of an internet site and other links can be tracked.
Owner:NANNING ZHISOU INFORMATION TECH
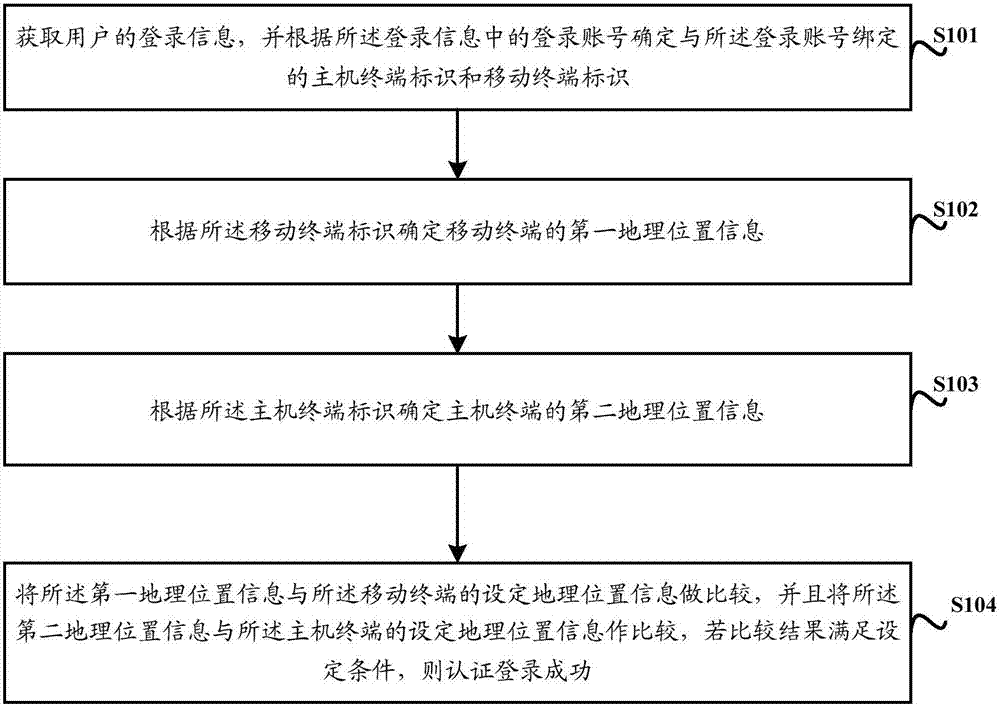
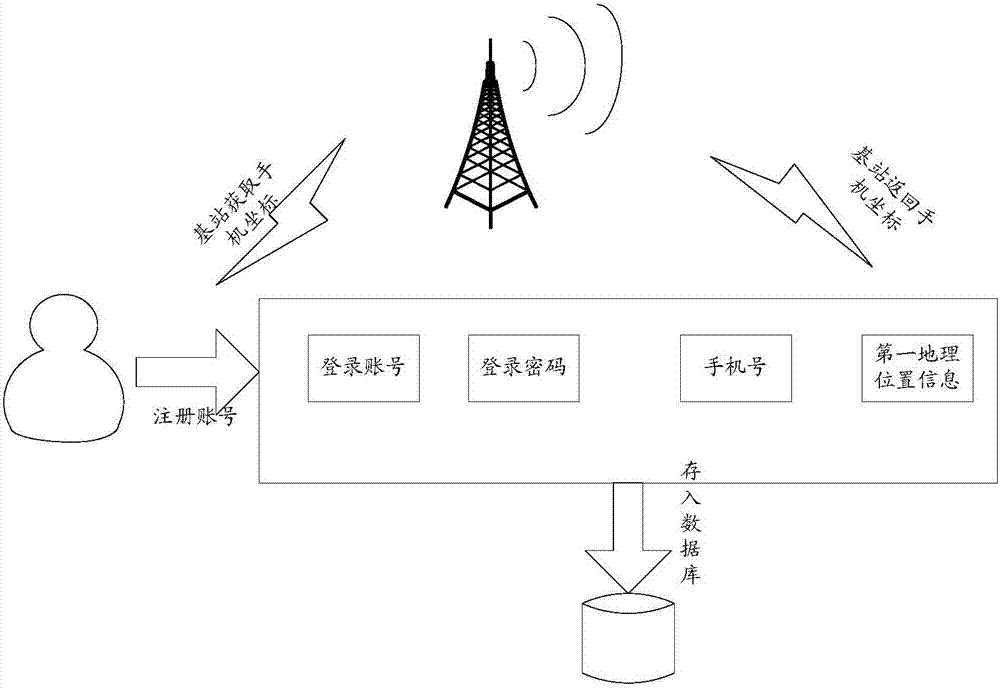
Secure login method and device
The invention discloses a secure login method and device. The method comprises the steps of: obtaining login information of a user, and determining a host terminal identifier and a mobile terminal identifier bound with a login account according to the login account in the login information; according to the mobile terminal identifier, determining the first geographical position information of a mobile terminal; according to the host terminal identifier, determining the second geographical position information of a host terminal; and, comparing the first geographical position information with the set geographical position information of the mobile terminal, furthermore, comparing the second geographical position information with the set geographical position information of the host terminal, and, if a comparison result satisfies a set condition, authenticating that login is successful. The problem of sensitive information leakage or the sensitive information tampering risk due to illegal remote login in the prior art can be solved.
Owner:CHINA MOBILE GROUP JIANGSU
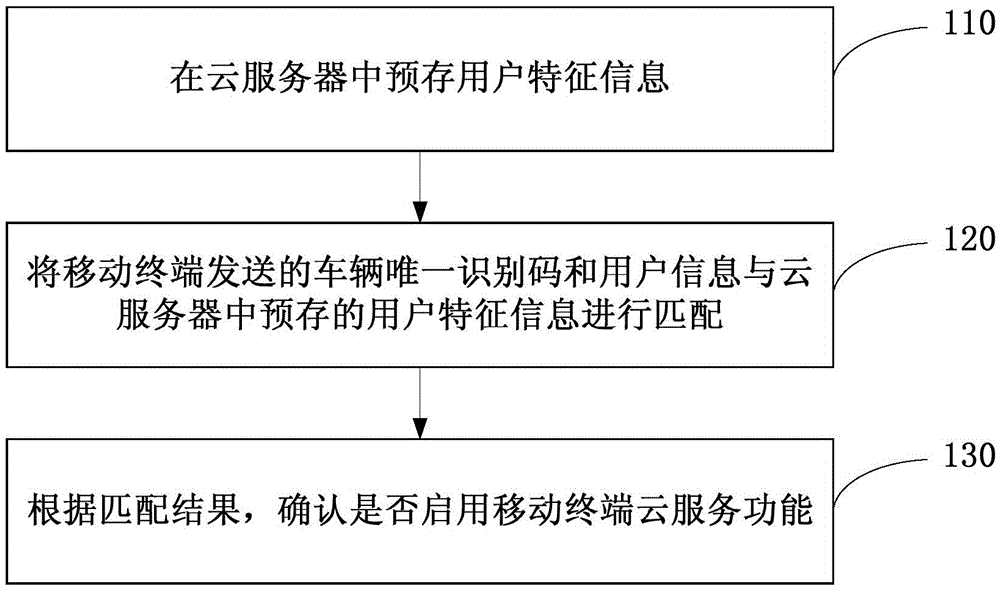
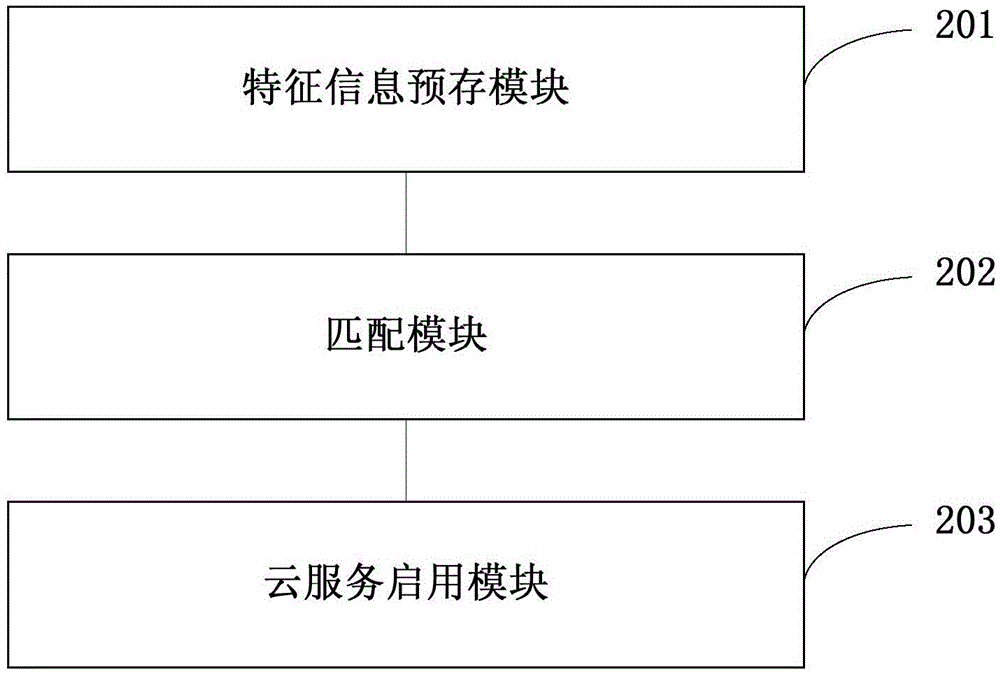
Method and system for enabling on-board cloud service
The invention discloses a method and a system for enabling an on-board cloud service. The method comprises the following steps: pre-storing user feature information in a cloud server; matching a vehicle unique identification code and user information transmitted by a mobile terminal with user feature information pre-stored in the cloud server; and determining whether to enable a cloud service function of the mobile terminal or not according to a matching result. Through adoption of the method, logging into an on-board cloud service function through a unique account and a unique password can be avoided; users can enable cloud service function by successfully matching the user feature information pre-stored in the cloud server through different mobile terminals; and a plurality of users can use the cloud service function through different mobile terminals on the premise of preventing the cloud service function from being used by irrelevant people.
Owner:KUNSHAN YINGTAI ELECTRONICS TECH CO LTD
Method for preventing website login by illegal user
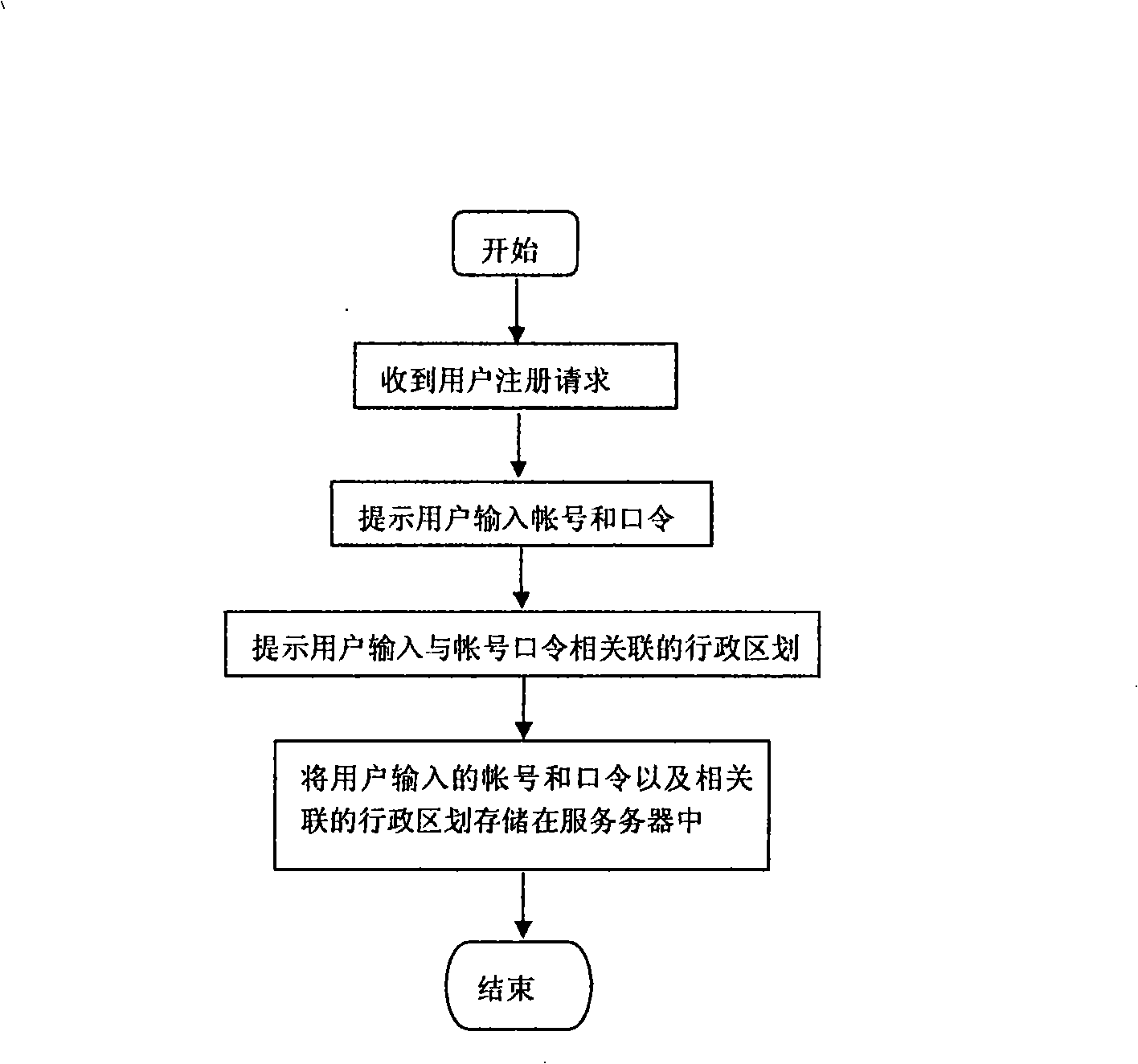
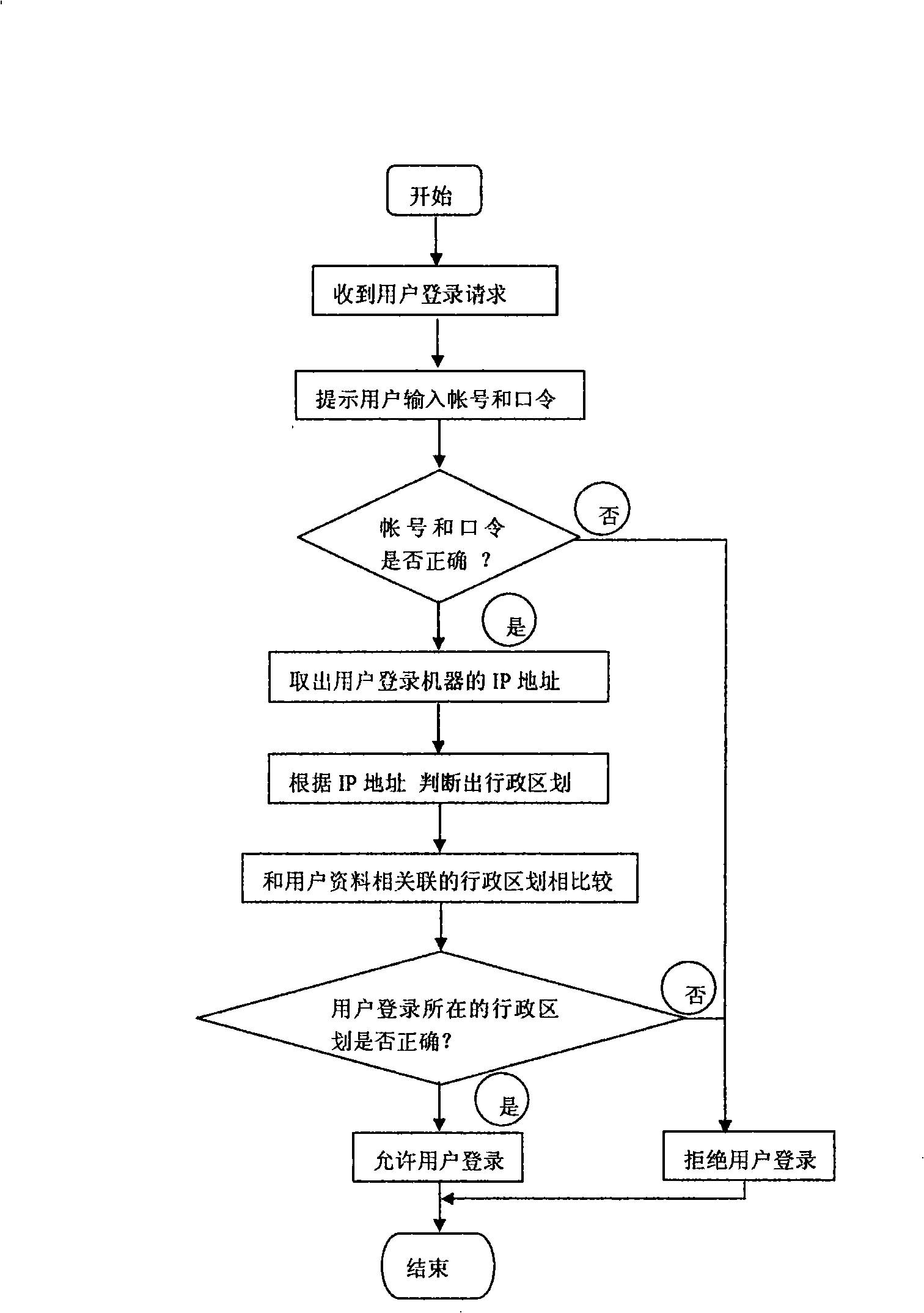
InactiveCN101340332AReduce lossesPrevent loginUser identity/authority verificationData switching by path configurationIp addressWorld Wide Web
The invention provides a method for preventing an illegal user from logging in a website by the user login information of a real user. In the invention, the user material and a administrative district of a user are caused to be associated, after the user login information input by the user is received, the computer IP address where the user logs in is taken out and is compared with the IP section in which the administrative district associated with the user is located, if the IP section is not in any IP section that the administrative district associated with the user belongs to, then the user is an illegal user, login can be rejected. In the invention, the IP address of the login computer is adopted as the basis of judgment, and the objective of preventing login by most of illegal users can be realized, thus avoiding that the illegal user logs in the website by using the user login information of the real user and steals the network information which can only be owned by the real user.
Owner:郑志豪
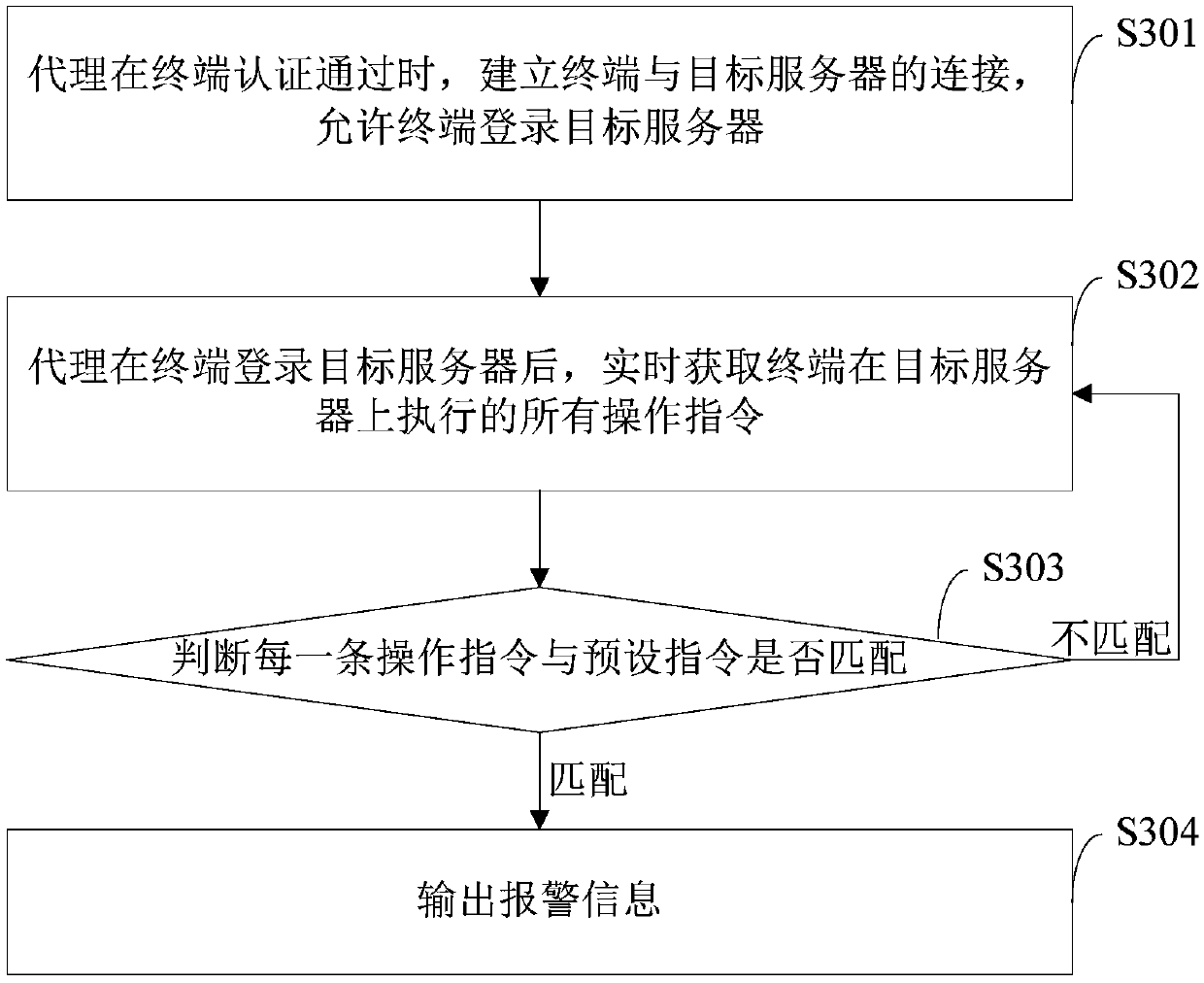
Data protection method and device, electronic equipment and readable storage medium
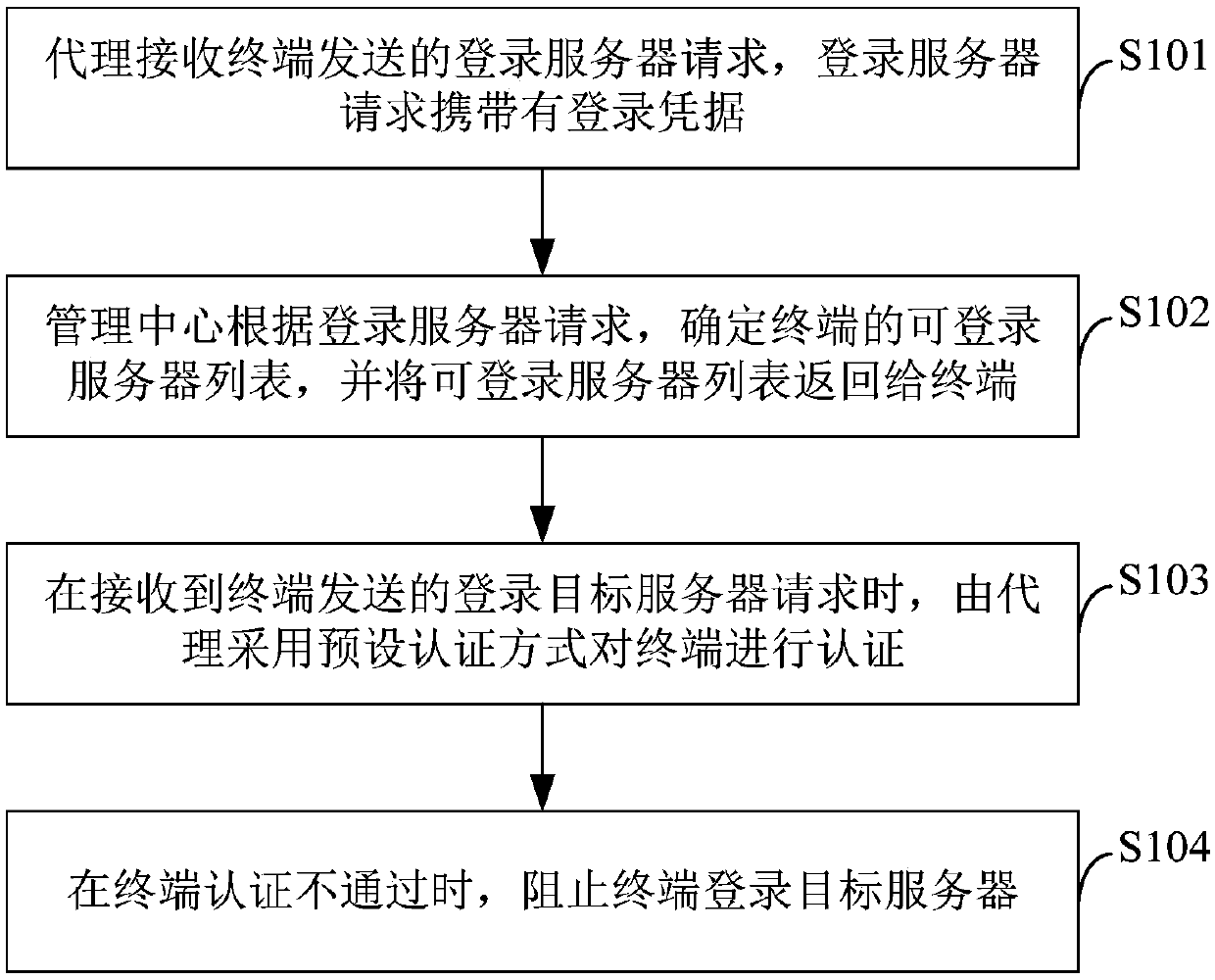
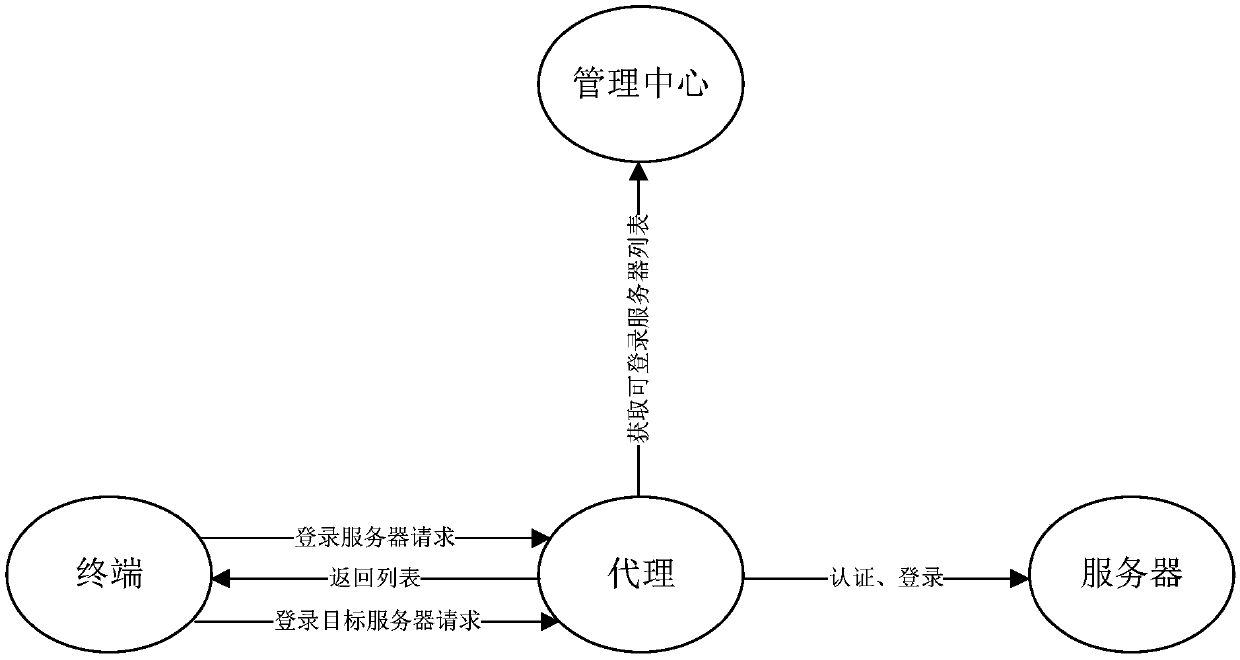
The invention relates to a data protection method and device, electronic equipment and a readable storage medium. The method includes: receiving a server login request, which is sent by a terminal, bya proxy, wherein the login server request carries login credentials; determining a list of servers, which can be logged in, of the terminal by a management center according to the server login request, and returning the list of the servers, which can be logged in, to the terminal; adopting a preset authentication manner to authenticate the terminal by the proxy when a target server login requestsent by the terminal is received; and preventing the terminal from logging in a target server when terminal authentication is unsuccessful. Through the above manner, the method prevents terminals, which are illegal or have no authorized authority, from logging in the servers, and ensures security of server data. In addition, the method can carry out real-time monitoring and auditing on all operations of terminals on the servers. The security of the server data is guaranteed, and operation and maintenance accident causes and related responsible persons can also be quickly determined.
Owner:上海格物致远网络科技有限公司
Secure communication method and system based on secure communication module
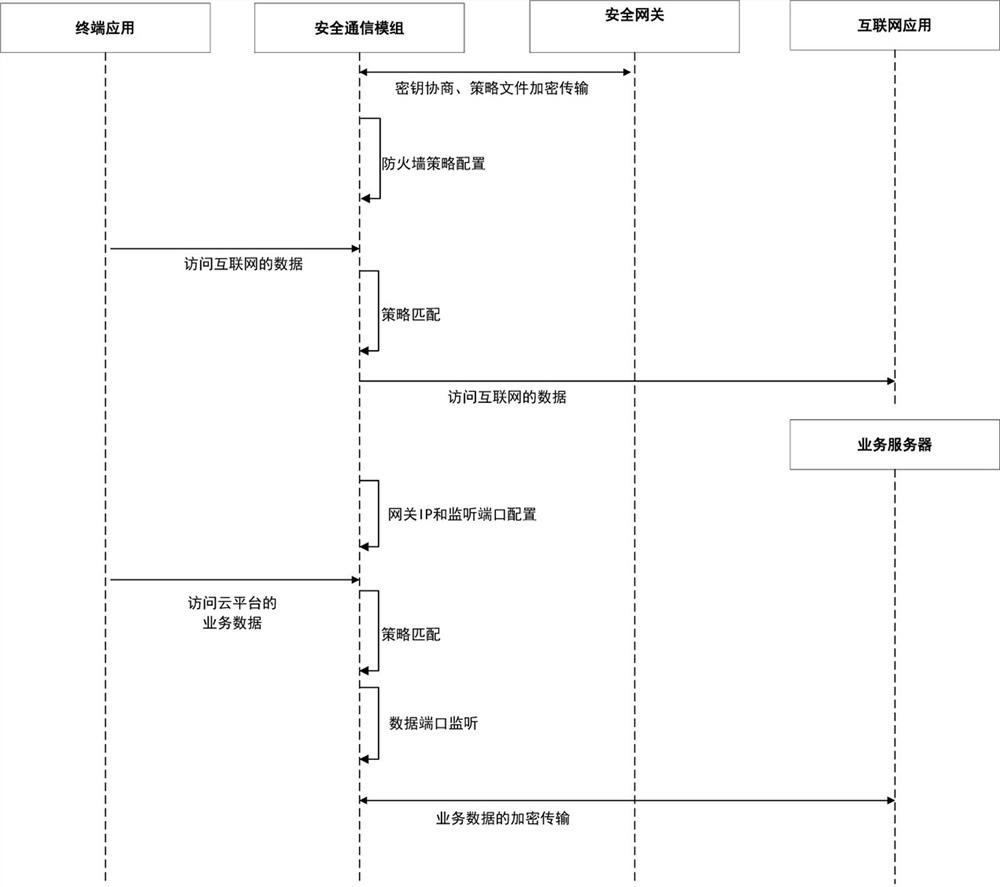
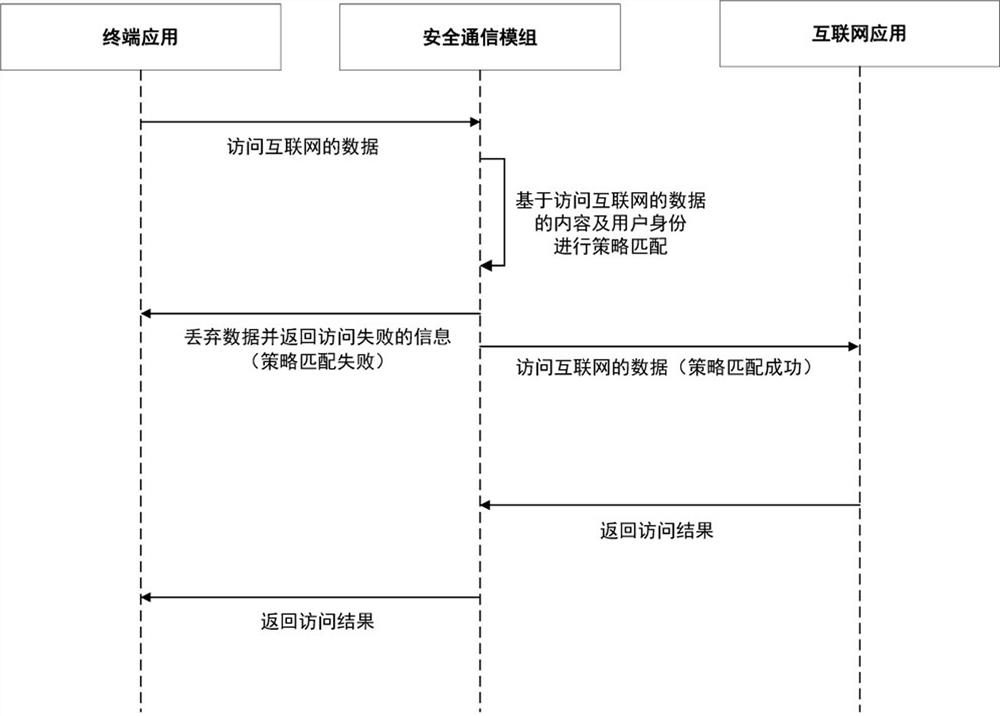
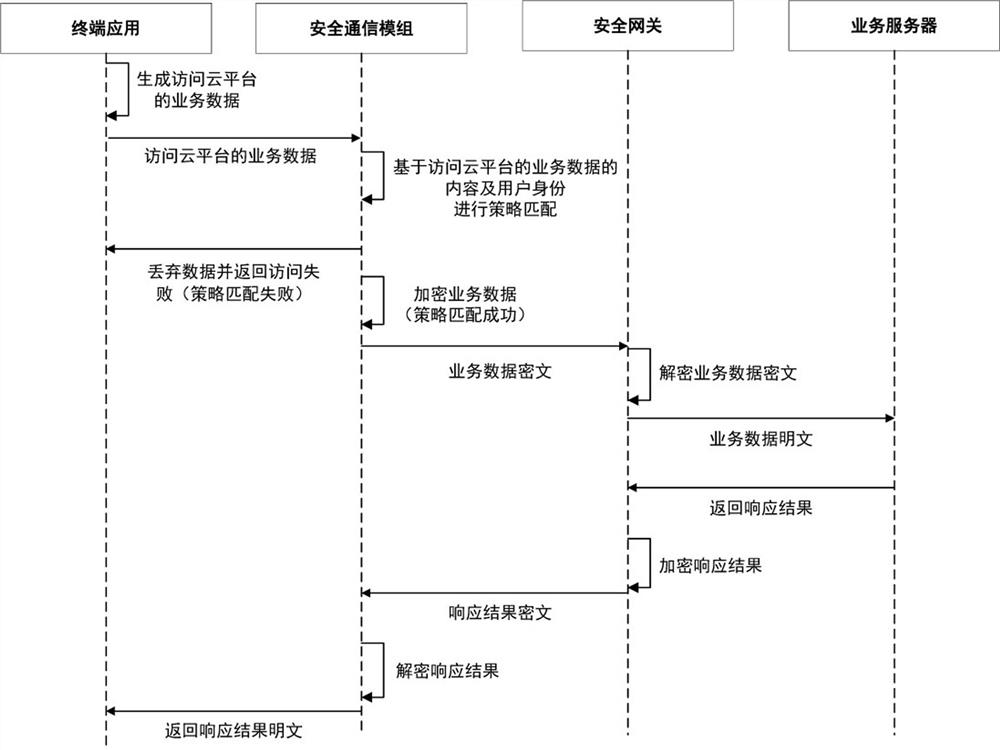
ActiveCN111918284AGuaranteed encrypted transmissionEasy accessKey distribution for secure communicationUser identity/authority verificationSecure communicationInternet privacy
The invention provides a secure communication method and system based on a secure communication module, and the method comprises the steps that a secure mobile terminal obtains a session key after carrying out the key negotiation with a security gateway of a cloud platform through the secure communication module, and carries out the encryption transmission of a strategy file; the security communication module performs firewall policy configuration according to the policy file; when the internet application is accessed, the terminal application sends data for accessing the internet to the safety communication module for strategy matching; if the first strategy is successfully matched, the security communication module sends the data of accessing the Internet to the Internet application fornetworking processing; when the cloud platform service is accessed, the security communication module performs gateway IP and monitoring port configuration according to the strategy file, and sends the service data accessing the cloud platform to the security communication module to perform policy matching and the like with a second policy file. And thus, the secure mobile terminal is ensured to securely access the Internet application or the cloud platform through the secure communication module.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Terminal two-factor secure login protection method
InactiveCN104735085ATo log in securelyPrevent theftUser identity/authority verificationPersonal identification numberPassword
The invention discloses a terminal two-factor secure login protection method. An audit center is installed in a server; a host sensor is installed in a client; the audit center issues login supervision rules to the client and enables login supervision; the client automatically enables USB (universal serial bus) key certification; a USB key writes in user information and an initial PIN (personal identification number) code during mass production; after the USB key is plugged to a computer, a PIN code is entered before verification is passed. The method using terminal two-factor secure login protection has the advantages that the USB key certification with a password is used as a startup login verification, the drive-level encryption technique is utilized, illegal operations such as illegally visiting a computer and stealing or revising confidential files are effectively prevented, and safety of a personal computer is improved.
Owner:上海汉邦京泰数码技术有限公司
A user account login method and device
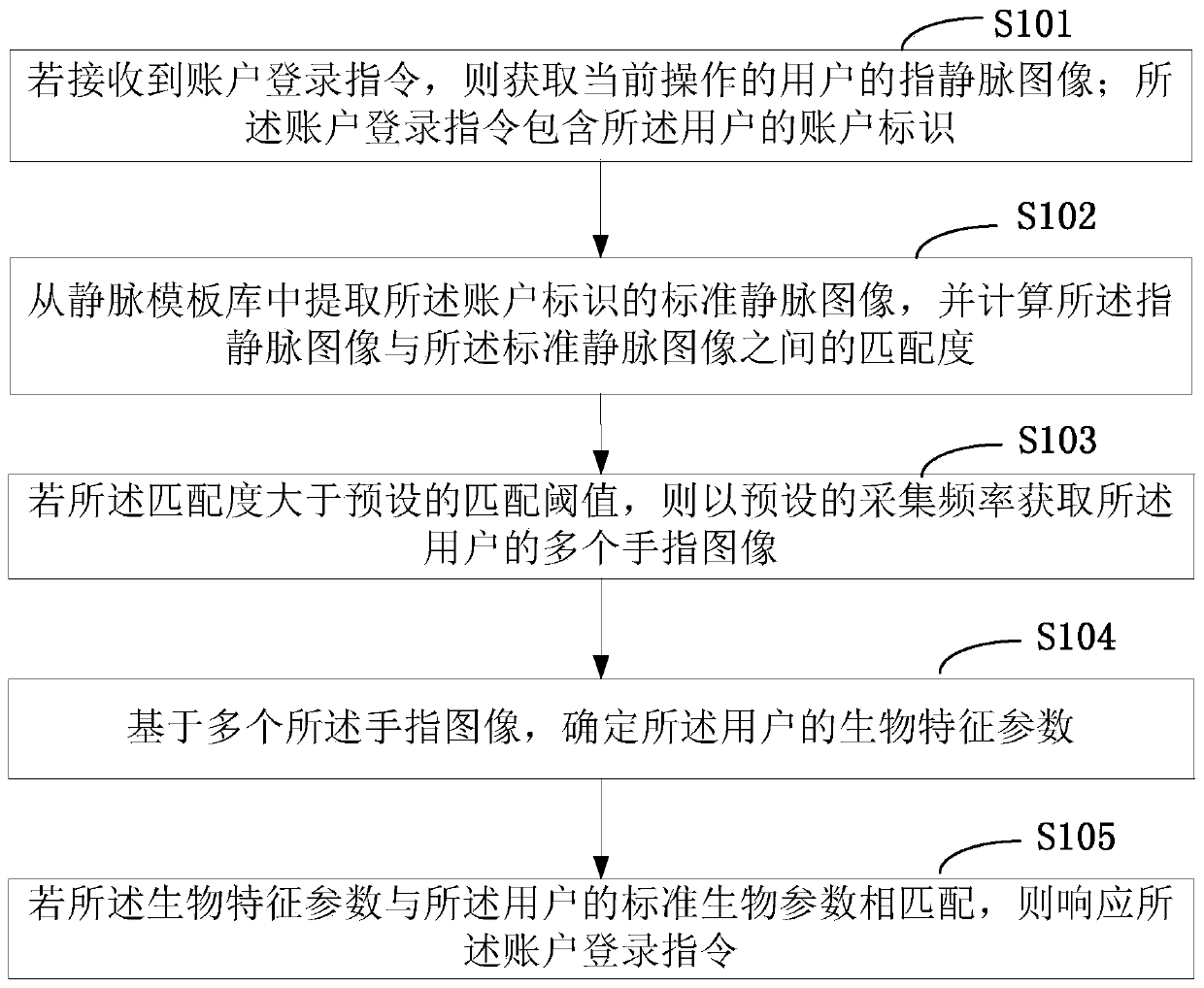
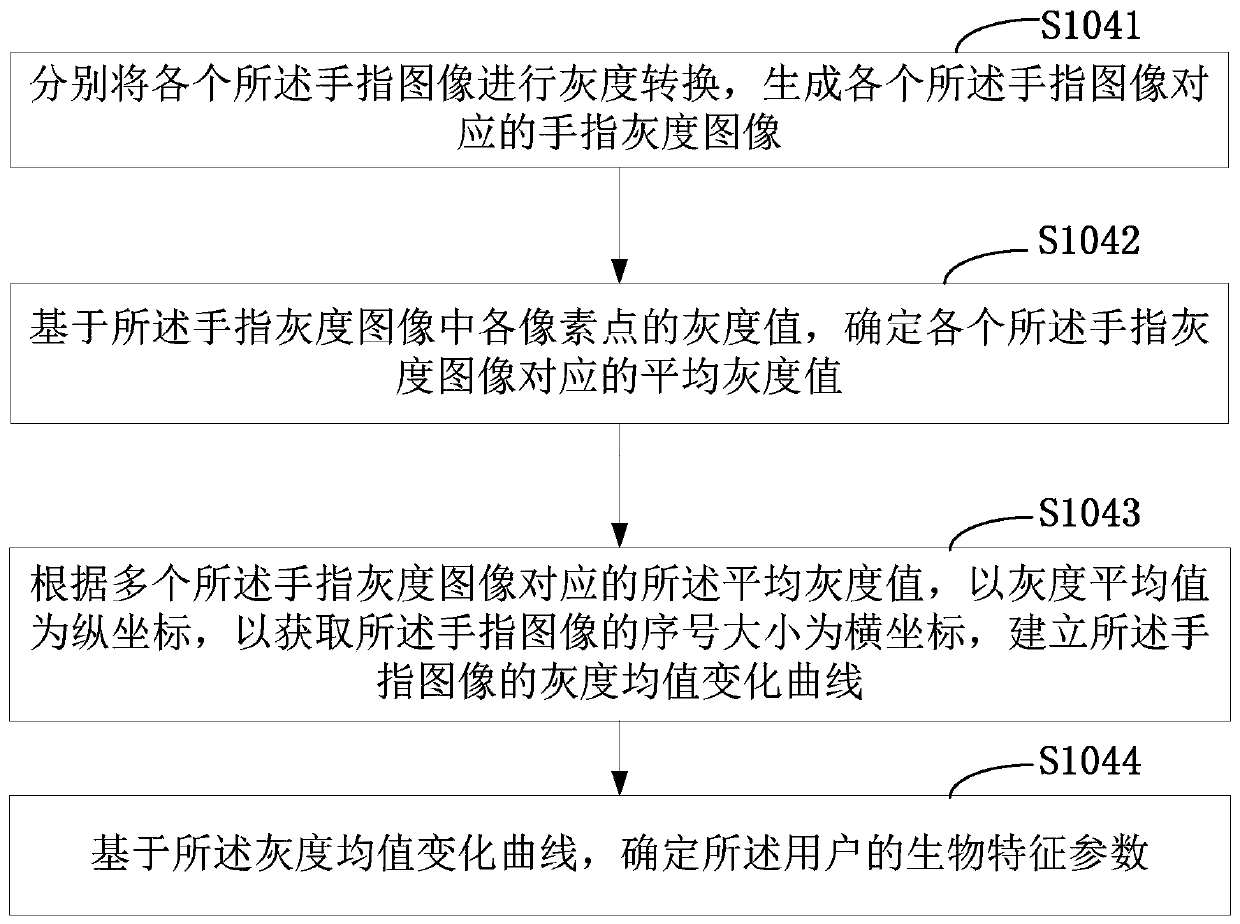
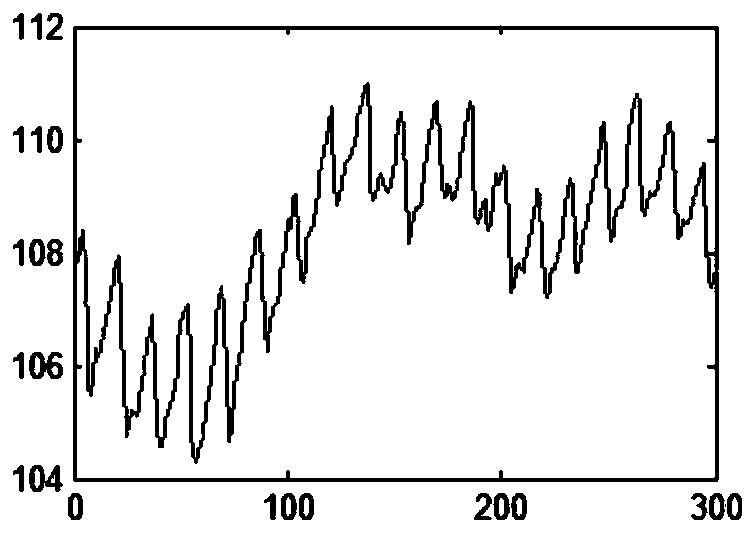
The invention is applicable to the technical field of data processing, and provides a user account login method and device, and the method comprises the steps: obtaining a finger vein image of a current operation user if an account login instruction is received; Extracting a standard vein image of the account identifier from the vein template library, and calculating a matching degree between thefinger vein image and the standard vein image; If the matching degree is greater than a preset matching threshold, acquiring a plurality of finger images of the user at a preset acquisition frequency;Determining biological characteristic parameters of the user based on the plurality of finger images; And if the biological characteristic parameters are matched with the standard biological parameters of the user, responding to the account login instruction. A vein image in a finger of a user is collected; According to the invention, the fingerprint sleeve cannot be counterfeited by wearing thefingerprint sleeve, so that the reliability of account verification can be improved, the biological characteristic parameters of the user can be collected, the current authenticated user is subjectedto living body detection, and the user is further prevented from illegally charging a legal user for account login through a counterfeiting tool.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Method for online updating of token ID
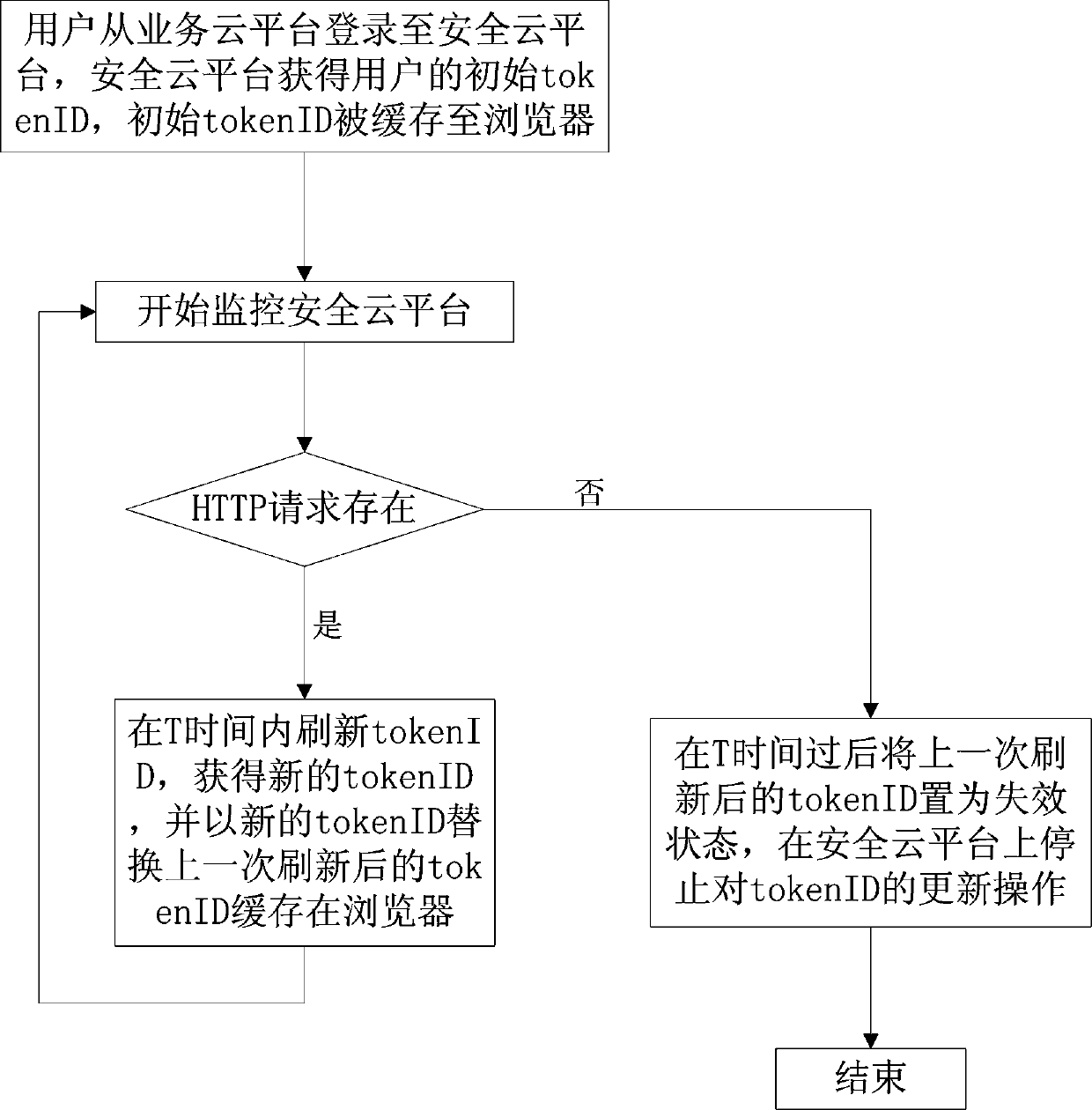
The invention relates to a method for online updating of a token ID. A user logs in a safety cloud platform from a service cloud platform; the safety cloud platform obtains an initial token ID and caches the ID; if an HTTP request exists continuously, the token ID is refreshed within a token ID expiration time defined by the service cloud platform and carries out replacement of the cached token ID; and otherwise, after T time, the token ID is set to be invalid, the updating operation of the token ID is stopped and the operation is ended. If the execution time of a single API is too long, a token ID is obtained again by using a preset API for restoration based on user information authentication. According to the invention, security of third-party data and resources is ensured; a phenomenonthat the current operation of the user is terminated for re logging in is avoided; a failure problem of a token ID invoked by the API is solved; the re authentication and logging in caused by the token ID failure are avoided; and the user experience is improved while the safety is ensured.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Game data intercommunicating method, game data intercommunicating system, terminals and servers
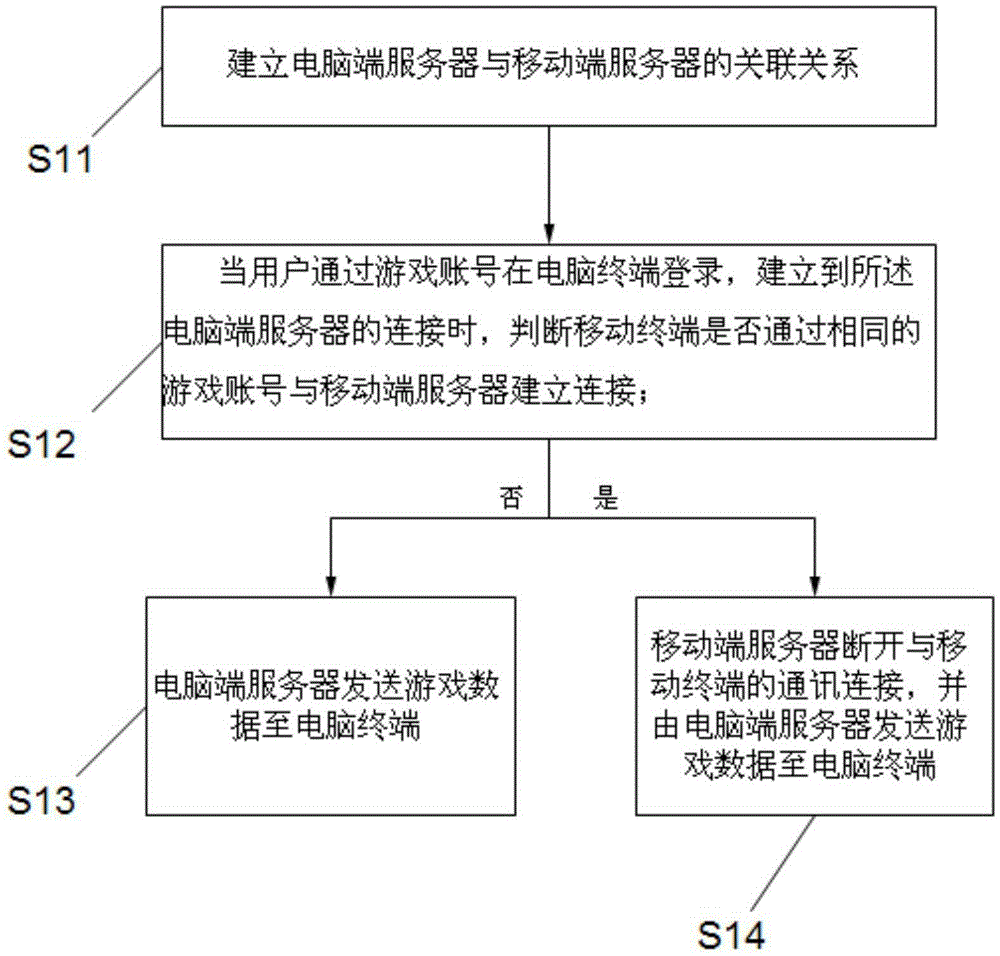
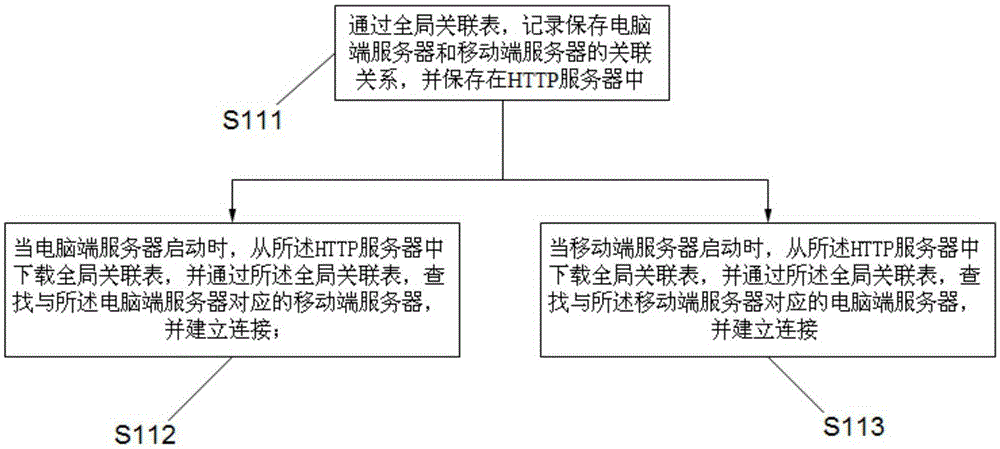
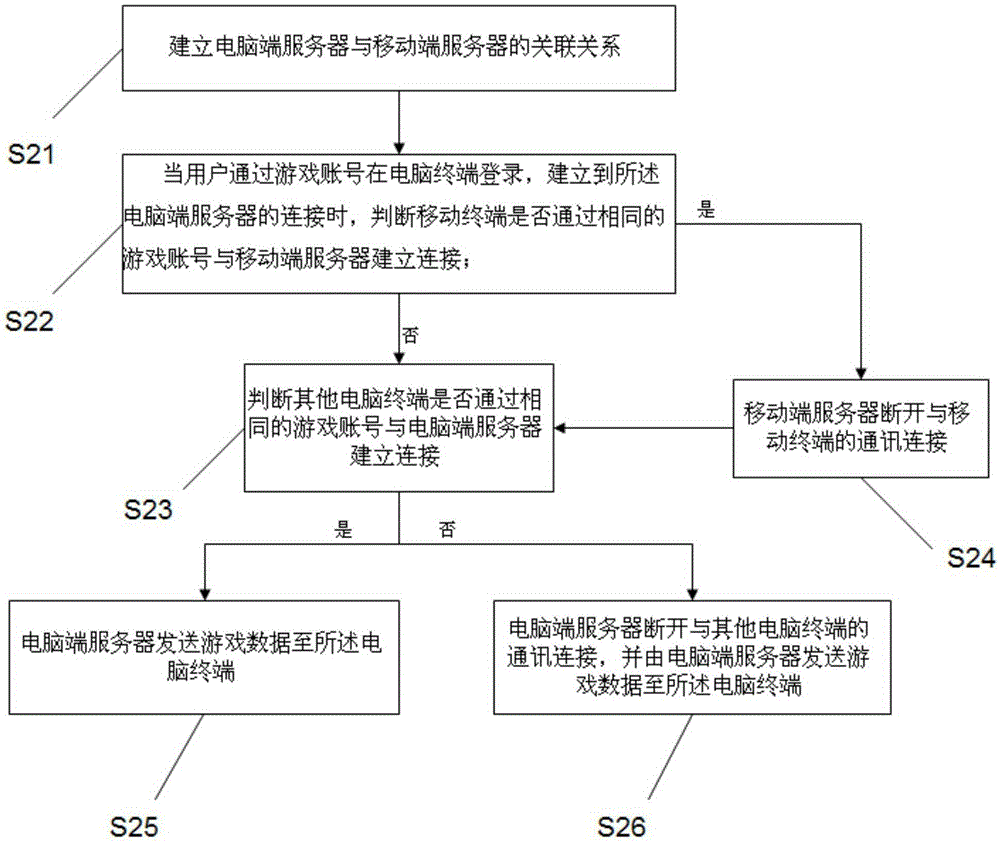
ActiveCN106606865ASolve defects that cannot be operated in real timePrevent loginVideo gamesTerminal serverComputer terminal
The invention relates to a game data intercommunicating method and system for a computer terminal and a mobile terminal. The method comprises the steps that the association relationship of a computer terminal server and a mobile terminal server is built; when a user logs in the computer terminal through a game account to build the connection with the computer terminal server, whether the mobile terminal builds the connection with the mobile terminal server through the same game account or not is judged; if the mobile terminal does not build connection with the mobile terminal server, the computer terminal server sends game data to the computer terminal; and if the mobile terminal and the mobile terminal server build connection, the mobile terminal server disconnects the communication with the mobile terminal, and the computer terminal server sends game data to the computer terminal. Meanwhile, the invention also provides the game data intercommunicating system for realizing the method.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Dynamic password configuration based mobile communication method and system
InactiveCN101895878APrevent loginEncryption apparatus with shift registers/memoriesSecurity arrangementAuthentication systemCommunications software
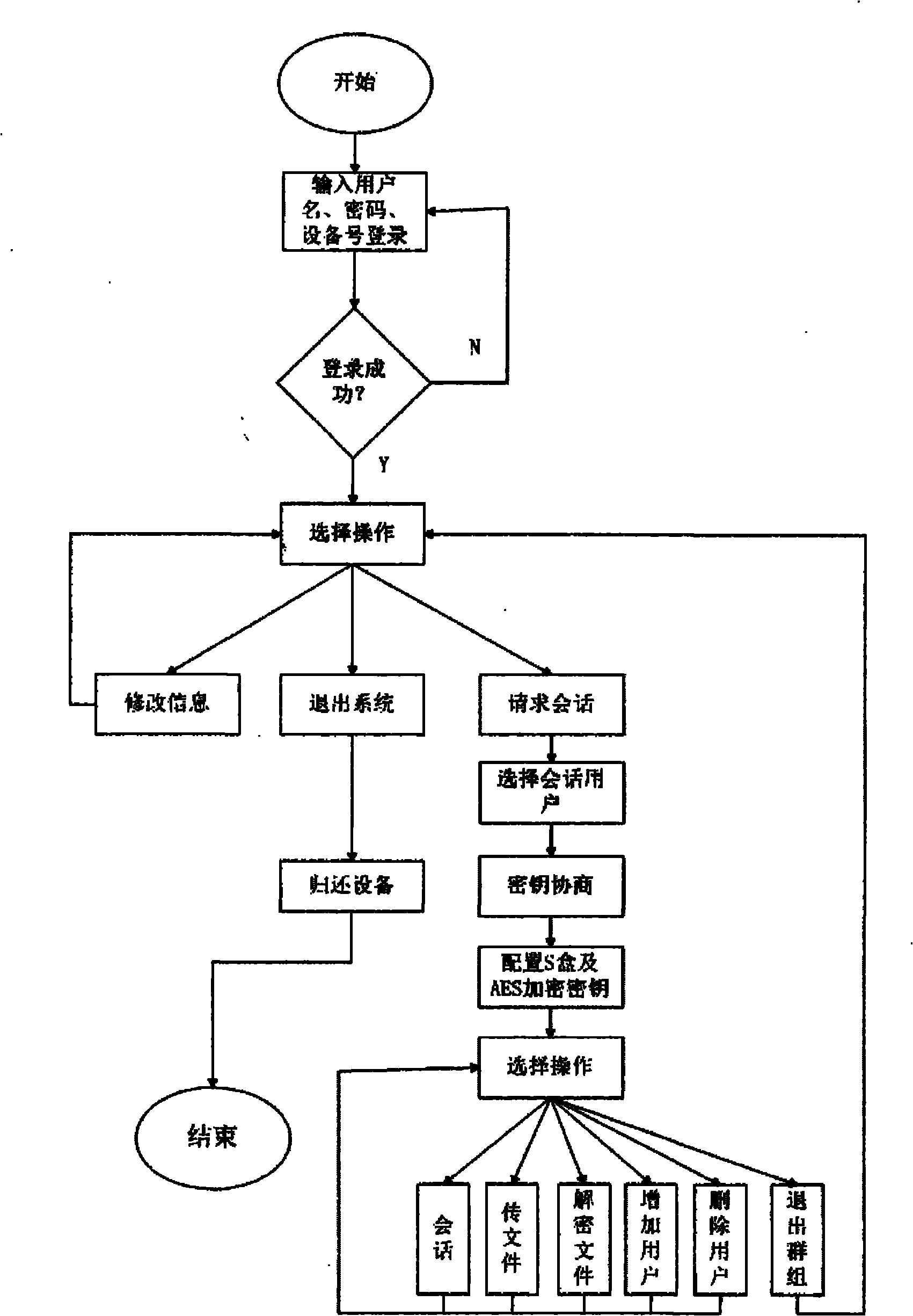
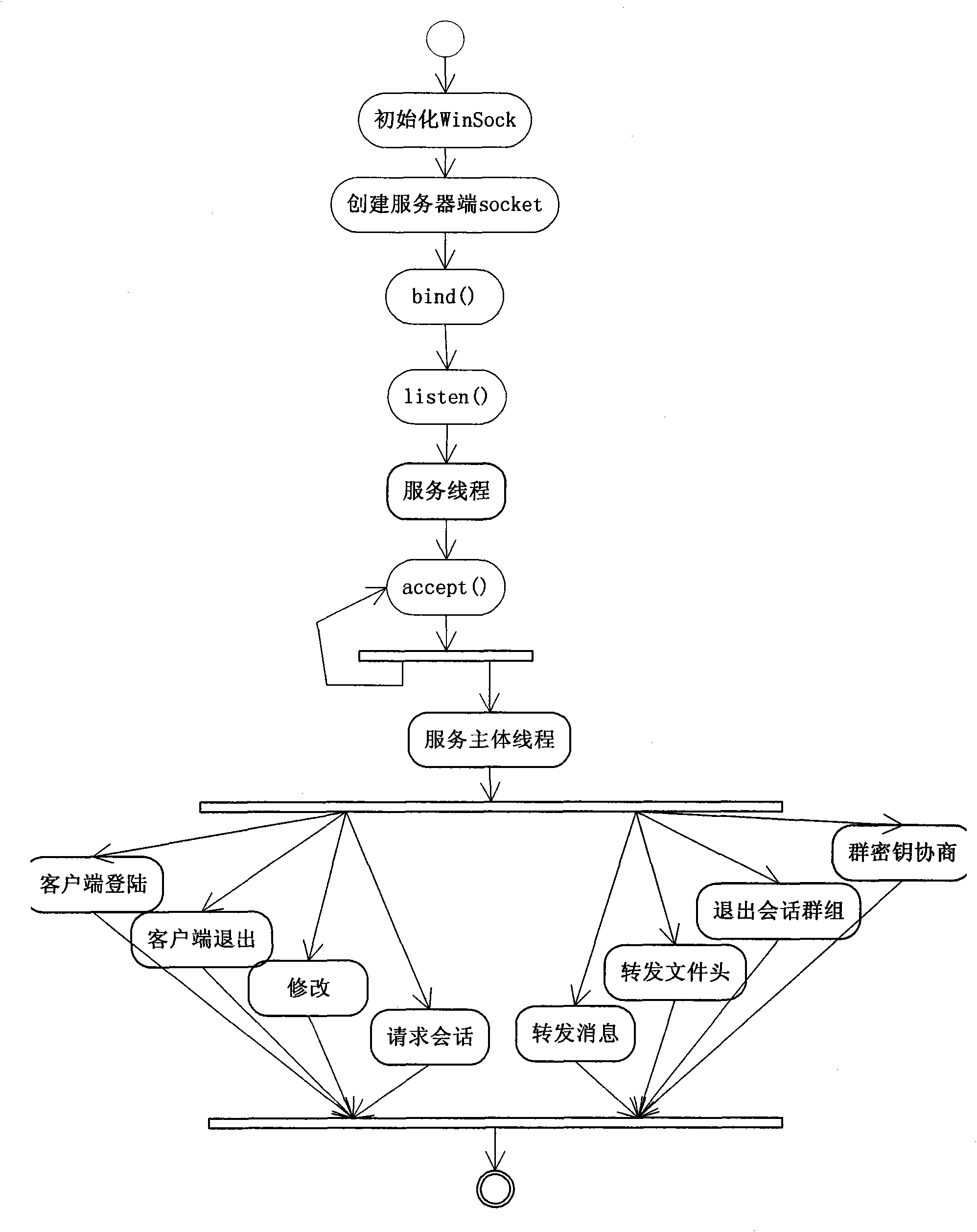
The invention relates to the technical field of mobile communication information safety, in particular to dynamic password configuration based mobile communication method and system. In the invention, a dynamic password algorithm is applied to communication with higher requirement on secrecy so as to ensure the safety of conversions and file content; and an application program is implanted to embedded equipment, thereby achieving convenient use and strong mobility and better facilitating an access network and other equipment. In the invention, a dynamic S-box generation algorithm based on evolution calculation and an AES algorithm are combined to encrypt message content and large transmitted files in a communication process; an identity authentication system is applied to prevent lawless persons from logging in the system; and the establishment of a software communication platform is completed based on the communication protocol of a TCP protocol, which has positive and beneficial technical effects as communication software.
Owner:WUHAN UNIV
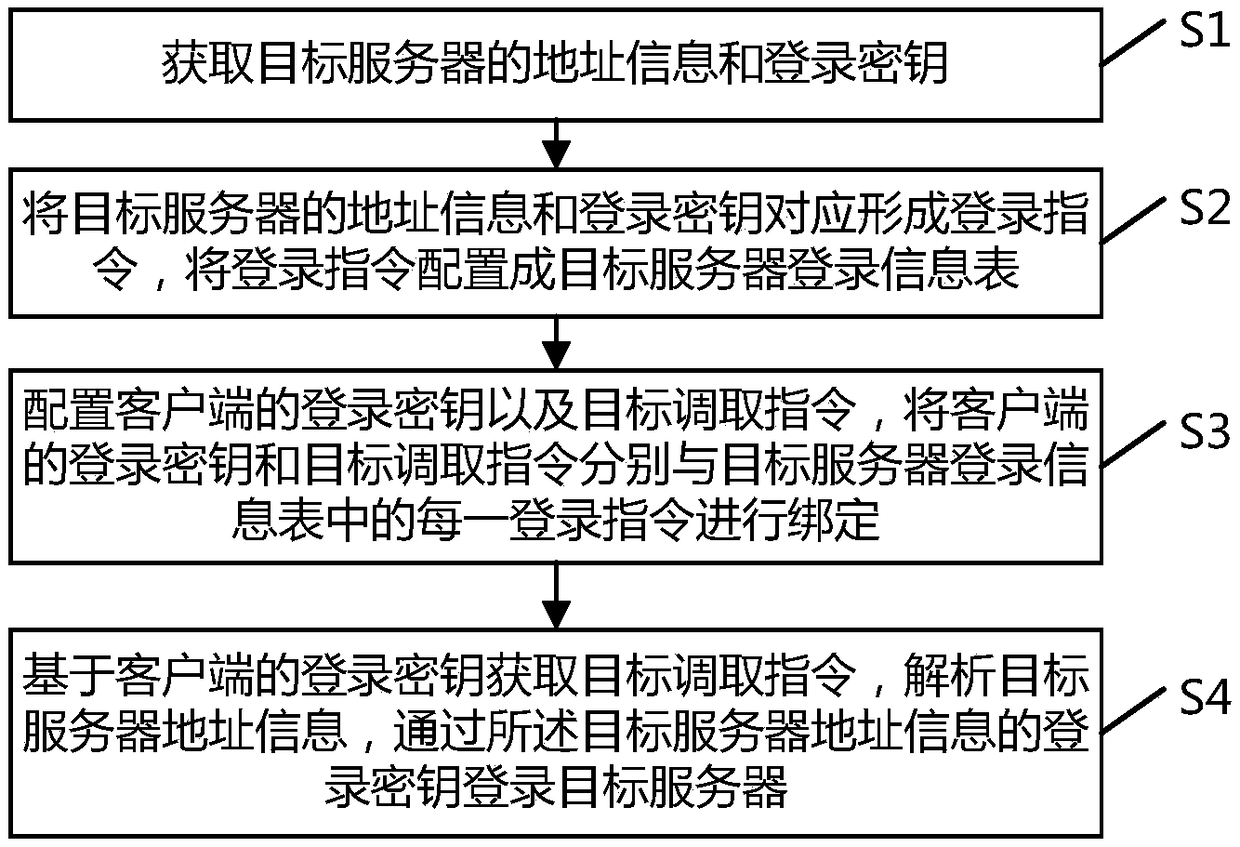
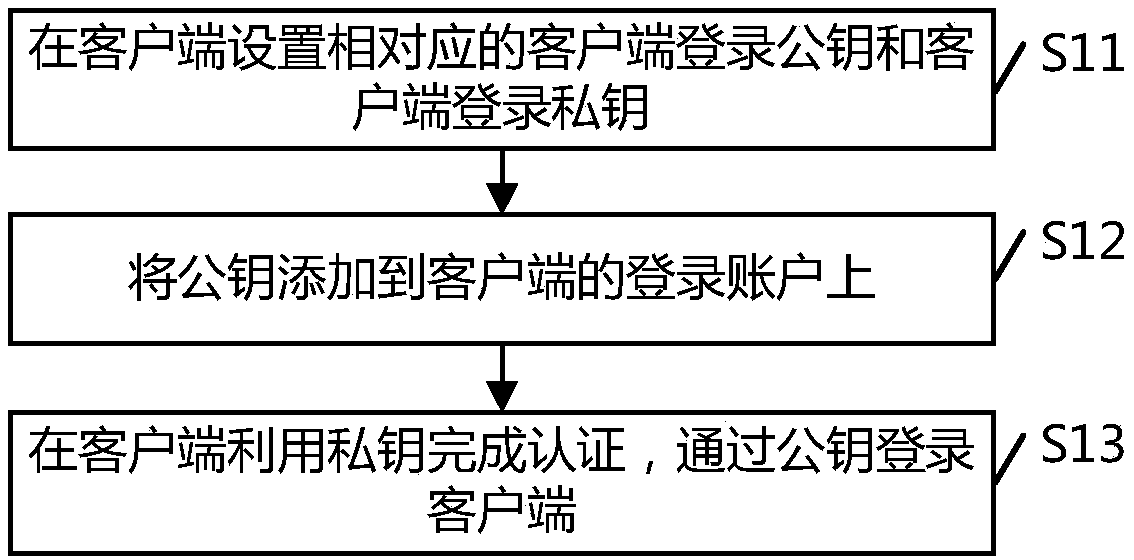
Remote password-free login method and system
The invention provides a remote password-free login method and system. The method comprises the steps that address information and login keys of target servers are acquired; the address information and the login keys of the target servers correspondingly form login instructions, and the login instructions are configured into a target server login information table; login keys and target calling instructions of a client are configured and bound with the login instructions in the target server login information table respectively; and the target calling instructions are acquired on the basis ofthe login keys of the client, the address information of the target servers is parsed, and the target servers are logged in through the login keys of the address information of the target servers. Thelogin keys of multiple target servers needing to be logged in are integrated in the client, and when a user switches login of the target servers, password input can be avoided, so that the login convenience is increased.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Method, device and system for preventing illegal subscriber log-on
InactiveCN1881877APrevent loginPrevent theftUser identity/authority verificationInternet privacyEngineering
The invention relates to a method for avoiding illegal user to access into one on-line application with the access information of real user, wherein the invention relates to the user access information with the number of personal communication device appointed by user; when receiving the user access information input by user, searching for the number of personal communication device related to said user access information, and sending one message to the number, to inform user about the access operation; if not receiving the confirm message of user, rejecting said user access information to access on the on-line application. The invention uses external personal communication device as mobile phone to avoid illegal user to access, to avoid the illegal user to theft the network resource of real user.
Owner:INT BUSINESS MASCH CORP
Computer network monitoring system using chip TMS320F2812
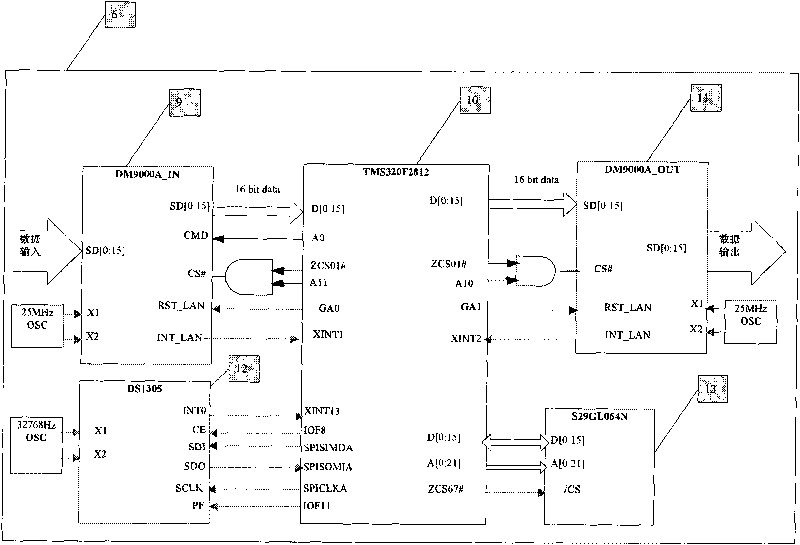
InactiveCN101741636AGuaranteed circulationAchieve viewData switching networksComputer network technologyThe Internet
The invention discloses a computer network monitoring system using a chip TMS320F2812 and relates to a network monitoring system, belonging to the technical field of computer networks. The invention aims to solve the problem of providing the computer network monitoring system using the chip TMS320F2812. The computer network monitoring system comprises a personal computer 5, a computer network supervision system 6, an internet interface 7 (such as an ADSL (asymmetrical digital subscriber loop) modem) and an internet 8; the input end of the computer network supervision system 6 is connected with the personal computer 5; the output end of the computer network supervision system 6 is connected with the input end of the internet interface 7; and the output end of the internet interface 7 is connected with the internet 8. The invention can ensure normal flow of network data, provide the identity authentication function, can control net play time, record access websites and provide the blacklist function.
Owner:CHANGCHUN INST OF OPTICS FINE MECHANICS & PHYSICS CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com