Data protection method and device, electronic equipment and readable storage medium
A data protection and login credential technology, applied in the field of communication, can solve security problems, operation and maintenance accidents can not quickly find the cause of the accident, and the person responsible for the accident, server data is vulnerable to attack or stolen, etc., to ensure security , the effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] In order to have a clearer understanding of the technical features, purposes and effects of the present invention, the specific implementation manners of the embodiments of the present invention will now be described in detail with reference to the accompanying drawings.
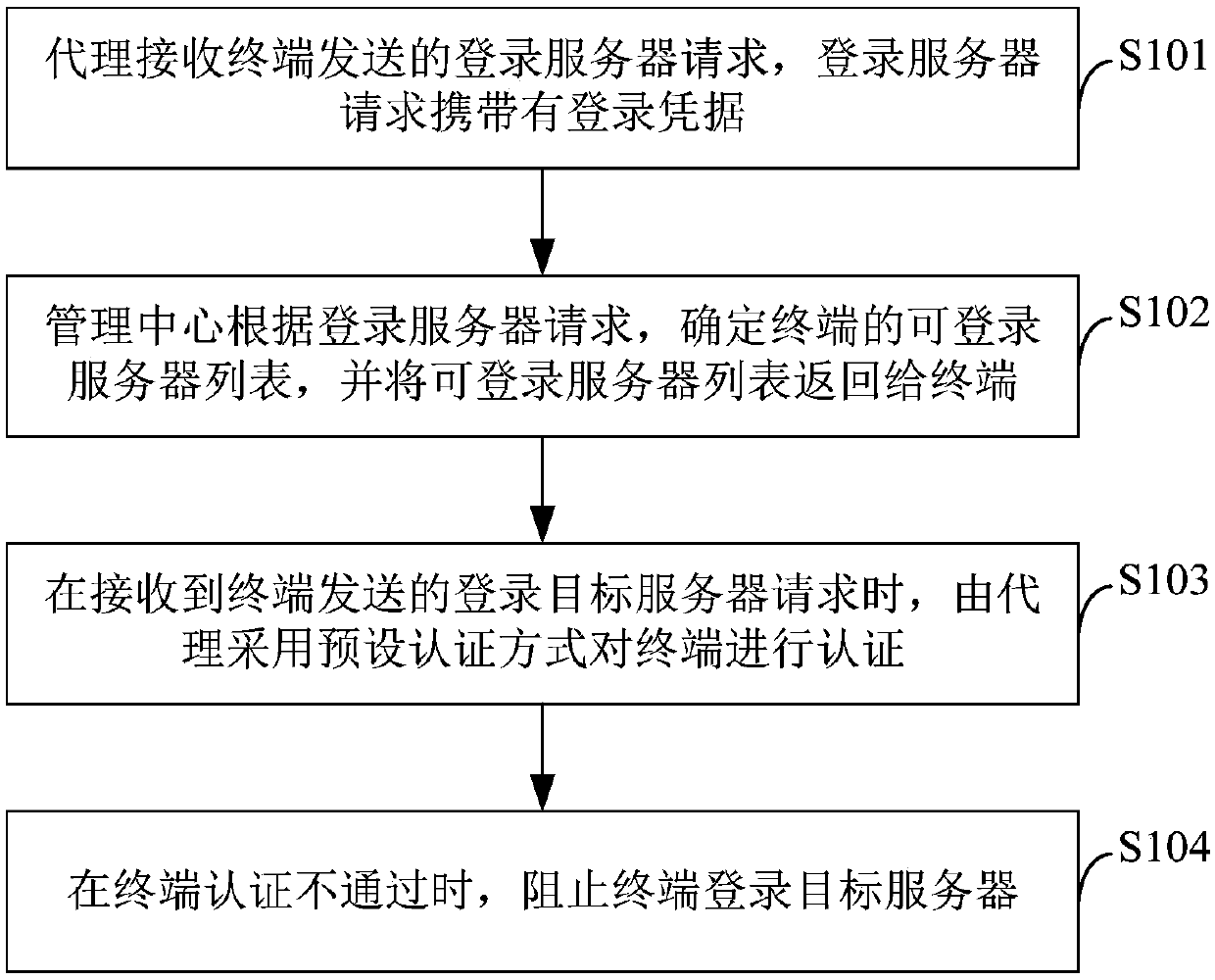
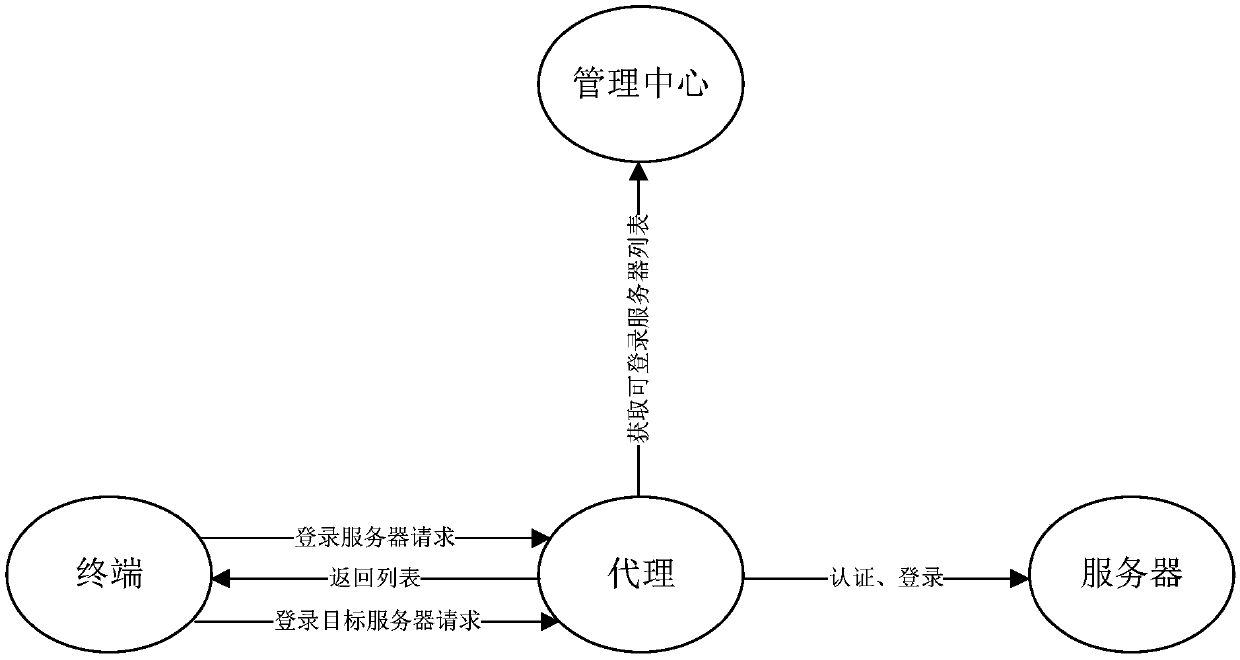
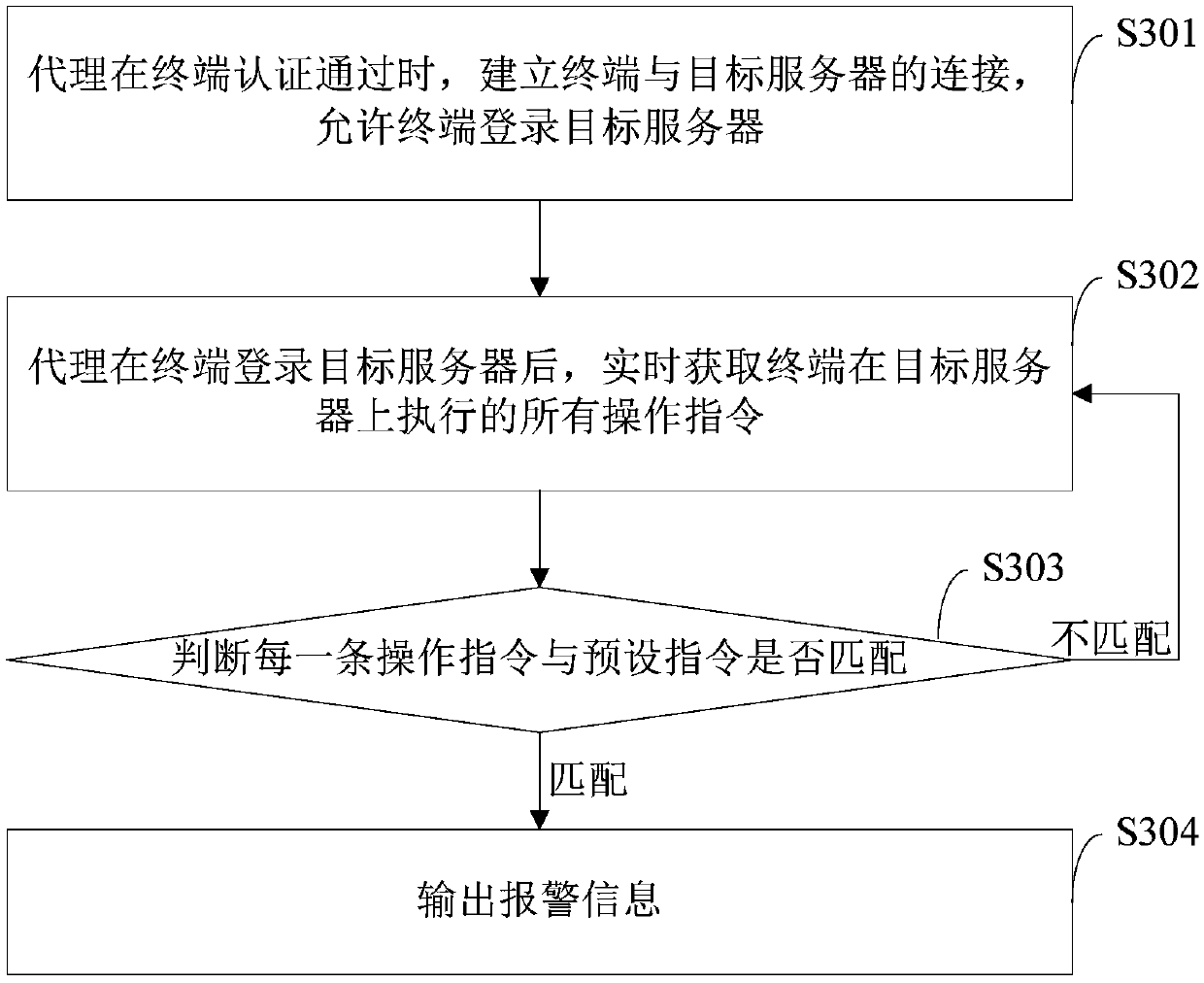
[0049] see figure 1 and figure 2 . The data protection method of this embodiment includes the following steps:
[0050] Step S101 , the proxy receives a login server request sent by a terminal, and the login server request carries login credentials.
[0051] In this step, the login credential carried in the login server request is a credential for the terminal to remotely log in to the server, which means that the terminal carrying the login credential is an authorized user. It should be noted here that the login credentials carried by the terminal are obtained through kerberos authentication. Before the terminal sends a request to log in to the server, it needs to perform an initialization opera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com