Method and device for improving safety of network ID authentication
A technology for authentication security and network identity, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as user identity information exposure, security loopholes, user losses, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
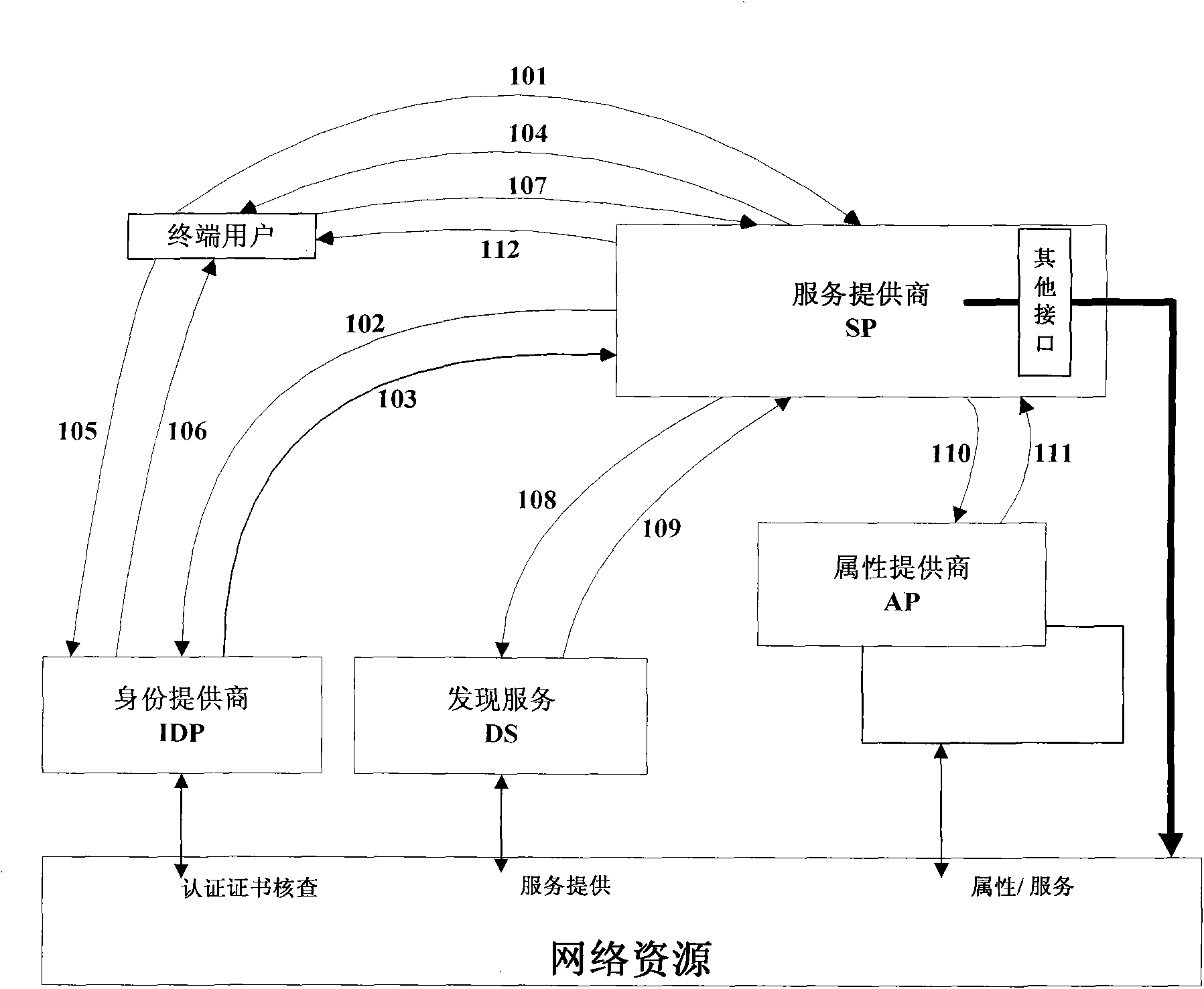
[0067] The embodiment of the present invention provides a method for improving the security of network identity authentication, including: IDP performs network identity authentication on SP and terminal users, and returns the authentication result to SP, the authentication result includes the network identity authentication result of SP and user The network identity authentication result of . see figure 1 , figure 1 The physical devices shown in are located in the circle of trust, and the method specifically includes:
[0068] 101: The terminal user initiates an authentication request to the SP, which carries the terminal user's authentication information, the identification information of the IDP specified by the terminal user, and the identification information that requires the SP to return the SP's network identity authentication result.
[0069] 102: After receiving the authentication request, the SP requests the corresponding IDP to perform network identity authenticat...
Embodiment 2
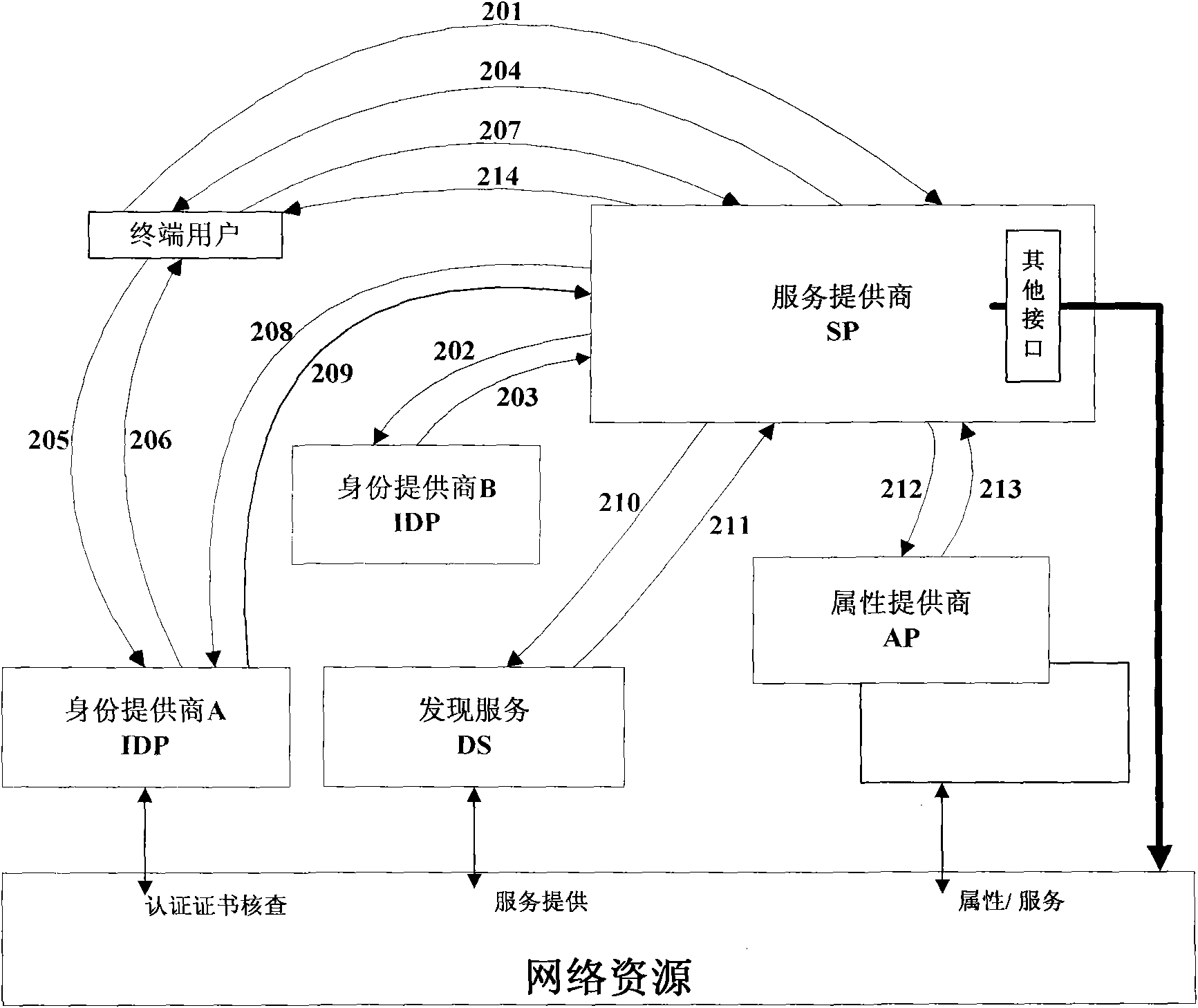
[0087] The embodiment of the present invention also provides a method for realizing seamless switching of the single sign-on process, which is applied to web services, including: when the SP requests the IDP specified by the end user for network identity authentication and obtains the result that the IDP does not support the authentication, The IDP belonging to the SP receives the network identity authentication request sent by the terminal user; after the IDP belonging to the SP performs network identity authentication on the terminal user, it returns the authentication result to the terminal user. see figure 2 , identity provider A is the home IDP of the SP, and identity provider B is the IDP designated by the end user (usually the default), and the end user is both in the trust circle of identity provider A and in the trust circle of identity provider B Within, this embodiment belongs to the application scenario of cross trust circles, and the method specifically includes:...
Embodiment 3
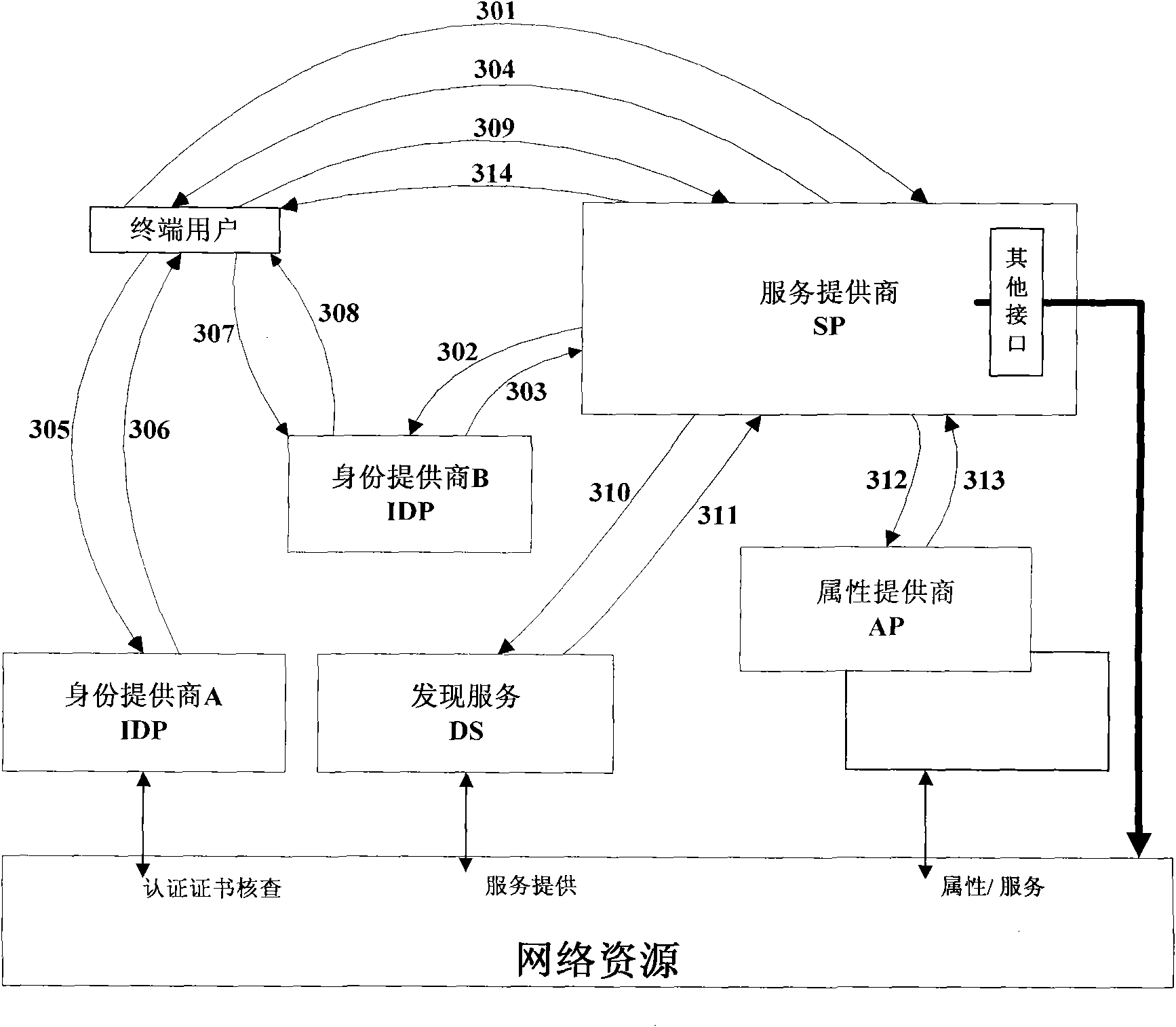
[0107] This embodiment is similar to Embodiment 2, and belongs to the application scenario without cross trust circles, see image 3 , identity provider A is the IDP to which the SP belongs, identity provider B is the IDP designated by the end user (usually the default), the end user is in the trust circle of identity provider B, and the SP is in the trust circle of identity provider A , and the two trust circles do not intersect, the end user cannot complete the authentication at the IDP to which the SP belongs. The embodiment of the present invention also provides a method for realizing seamless switching of the single sign-on process, the method specifically includes:
[0108] Steps 301 to 306 are the same as steps 201 to 206 in Embodiment 2, and will not be repeated here. In this embodiment, since the IDPA to which the SP belongs is not the IDP to which the terminal user belongs, the authentication result returned by the IDPA to the terminal user in 306 is a result of aut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com