Identity card information safety transmission method and system
A technology of information security and transmission method, applied in the field of ID card information security transmission method and system, can solve the problems of vulnerability to attack, waste of time and resources, occupation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
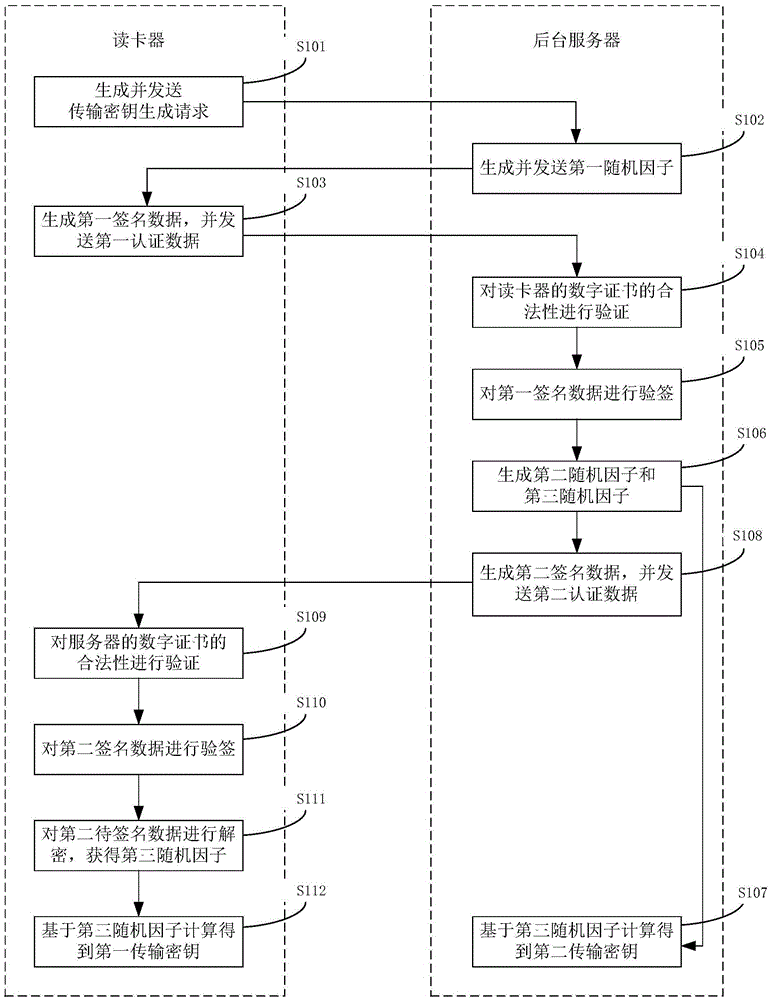
[0053] This embodiment provides a method for securely transmitting ID card information. figure 1 A flow chart of a method for securely transmitting ID card information provided in this embodiment, as shown in figure 1 shown, including the following steps:
[0054] S101. The card reader that is not equipped with a SAM (safety control for identity card verification) module receives the card reading instruction, and sends the transmission key generation request to the background server;
[0055] In this embodiment, the card reader that is not provided with the SAM module can be an ID card reader that is not provided with the SAM module, and is used to read ID card information. For ease of description, it is referred to as a card reader hereinafter. The card reader can have an input device such as a button for receiving a card reading instruction, a touch screen, etc. When the user inputs a card reading instruction, the card reader receives the card reading instruction, and the c...
Embodiment 2
[0089] This embodiment provides an ID card information security transmission system. figure 2 A schematic structural diagram of an ID card information security transmission system provided in this embodiment, as shown in figure 2 As shown, the system includes a card reader 201 and a background server 202 that are not provided with a SAM (resident ID card verification safety control) module, wherein:
[0090] The card reader 201 that is not provided with the SAM (resident identity card verification security control) module is used to receive the card reading instruction and send the transmission key generation request to the background server 202;
[0091] In this embodiment, the card reader that is not provided with a SAM module can be an ID card reader that is not provided with a SAM module, and is used to read ID card information. For ease of description, it is referred to as a card reader hereinafter. The card reader 201 can have input devices such as keys and touch scre...
Embodiment 3
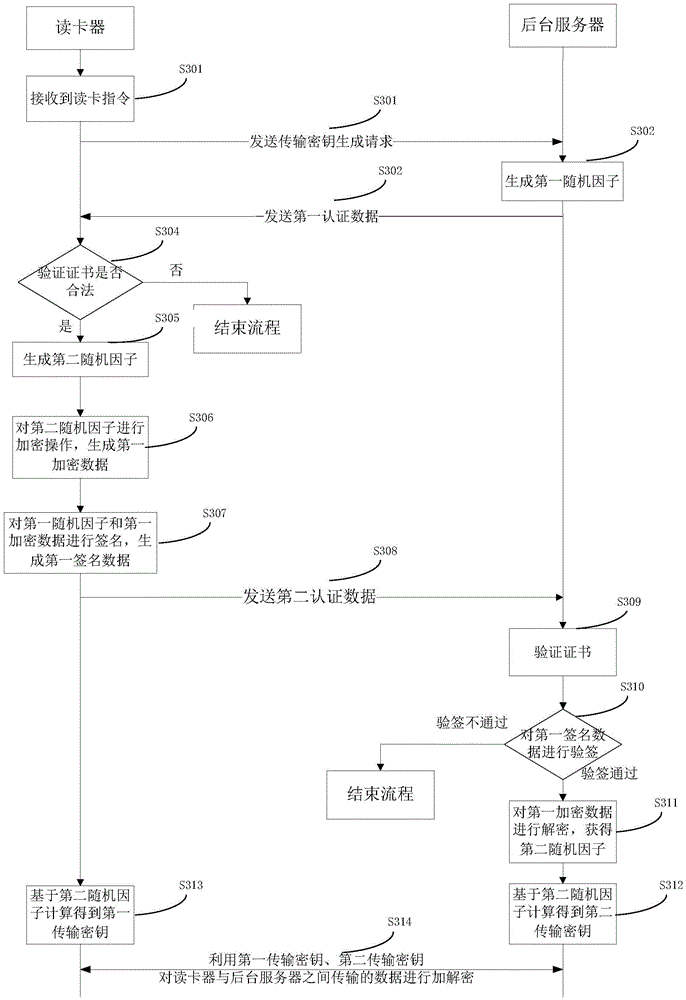
[0123] This embodiment provides a method for securely transmitting ID card information. image 3 A flow chart of a method for securely transmitting ID card information provided in this embodiment, as shown in image 3 shown, including the following steps:
[0124] S301: The card reader not equipped with a SAM (safety control for authentication of resident identity card) module receives the card reading instruction, and sends a transmission key generation request to the background server;
[0125] In this embodiment, the card reader that is not provided with a SAM module can be an ID card reader that is not provided with a SAM module, and is used to read ID card information. For ease of description, it is referred to as a card reader hereinafter. The card reader can have an input device such as a key device and a touch screen for receiving card reading instructions. When the user inputs the card reading instruction, the card reader receives the card reading instruction, and th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com