Access control method and system for virtual machine system
An access control and virtual machine monitor technology, applied in the field of resource access, can solve problems such as uncertainty, and achieve the effect of preventing attacks between virtual machines
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
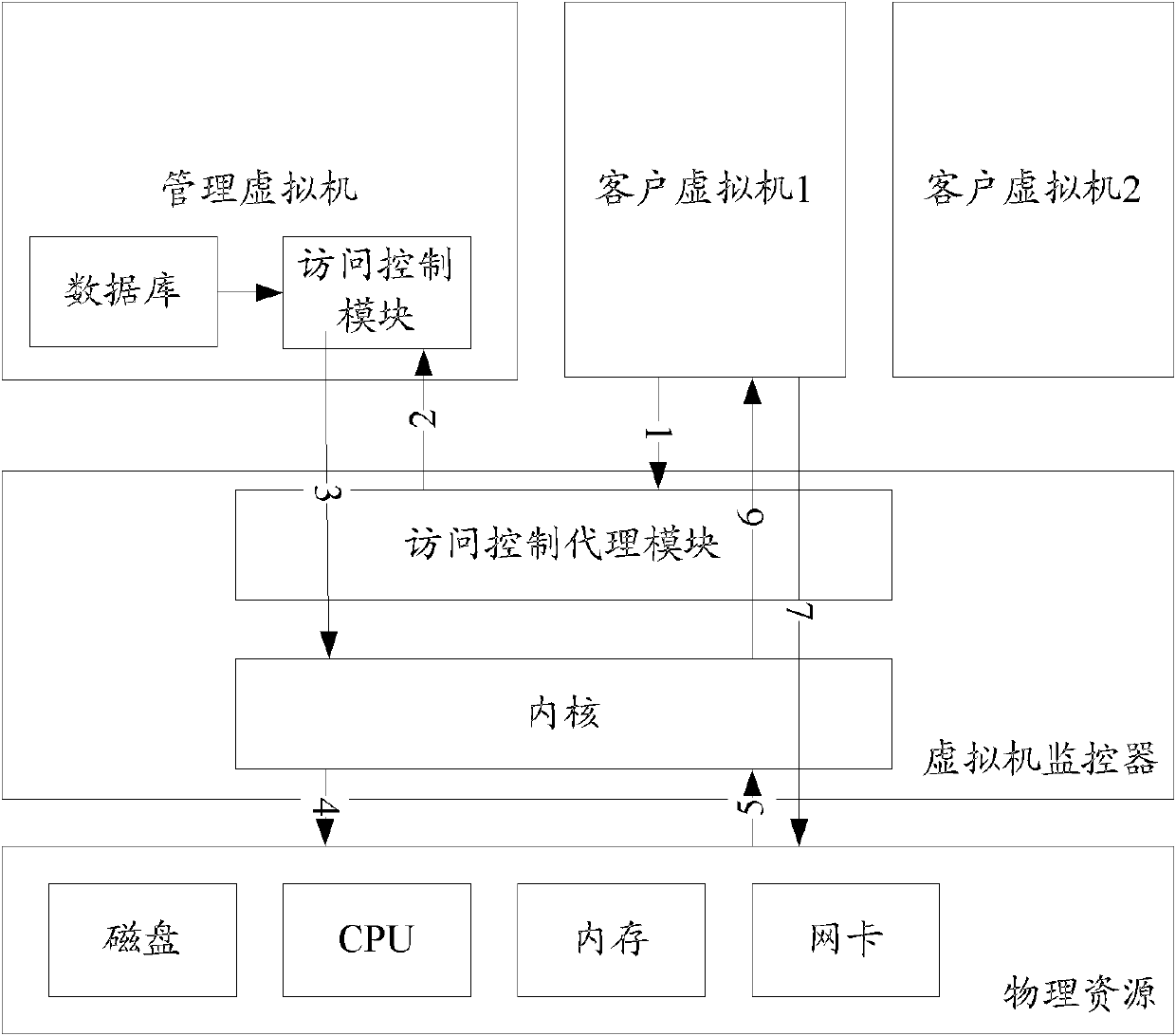
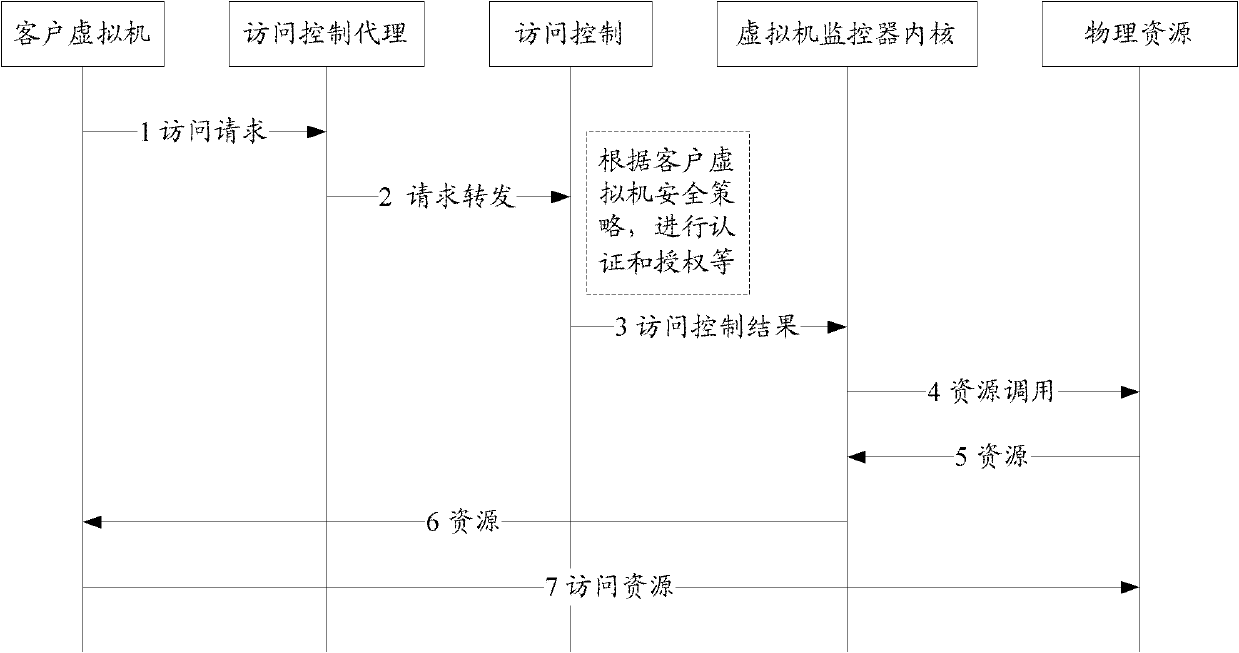
[0040] The basic idea of the present invention is, by dividing the virtual machine into a management virtual machine and a client virtual machine, and setting an access control agent module in the virtual machine monitor, so that the virtual machine monitor receives the resource access request or After accessing other customer virtual machine requests, the resource access request is forwarded to the management virtual machine, and the management virtual machine performs authentication and authorization operations on the customer virtual machine, and allows access to other customer machines after the authentication is passed, or according to the security policy The information and the like determine the corresponding resource access rights for the client virtual machine, and send the information to the virtual machine monitor, and the virtual machine monitor performs corresponding resource access management on the client virtual machine.
[0041] In a virtual machine system, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com