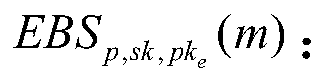Patents
Literature
85results about How to "Prevent getting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
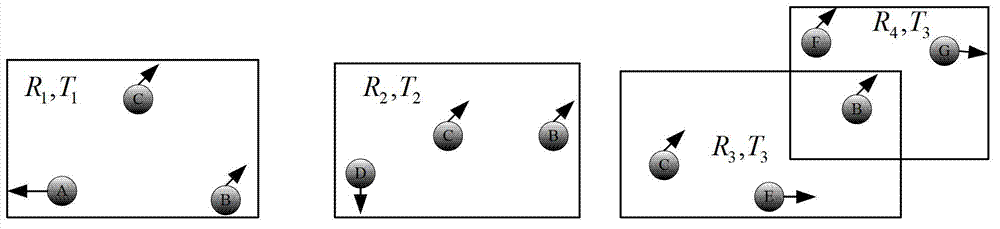
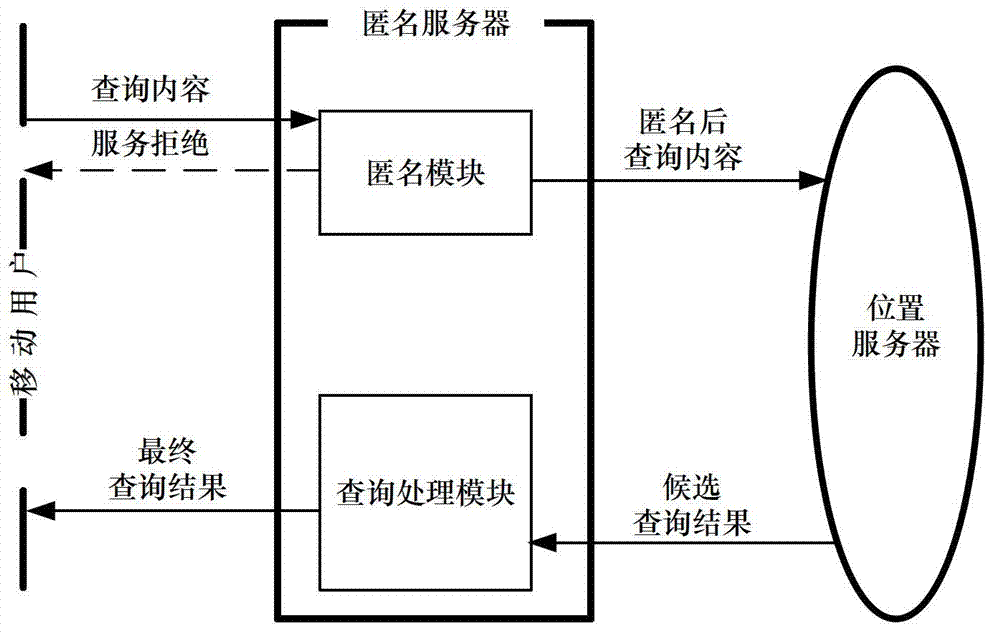
Continuous query oriented location anonymizing method applicable to location service system
InactiveCN102892073AFix the leakSufficiently diverseLocation information based serviceTransmissionPersonalizationPrivacy protection
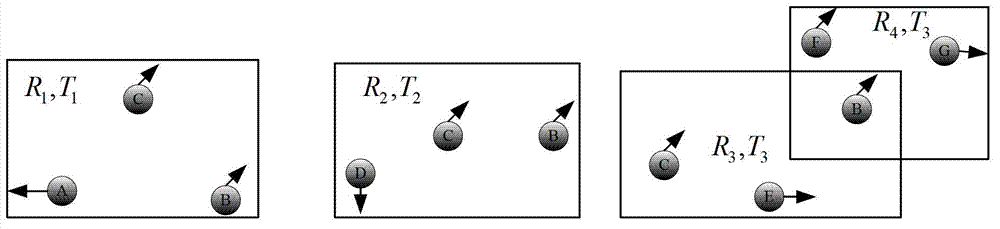
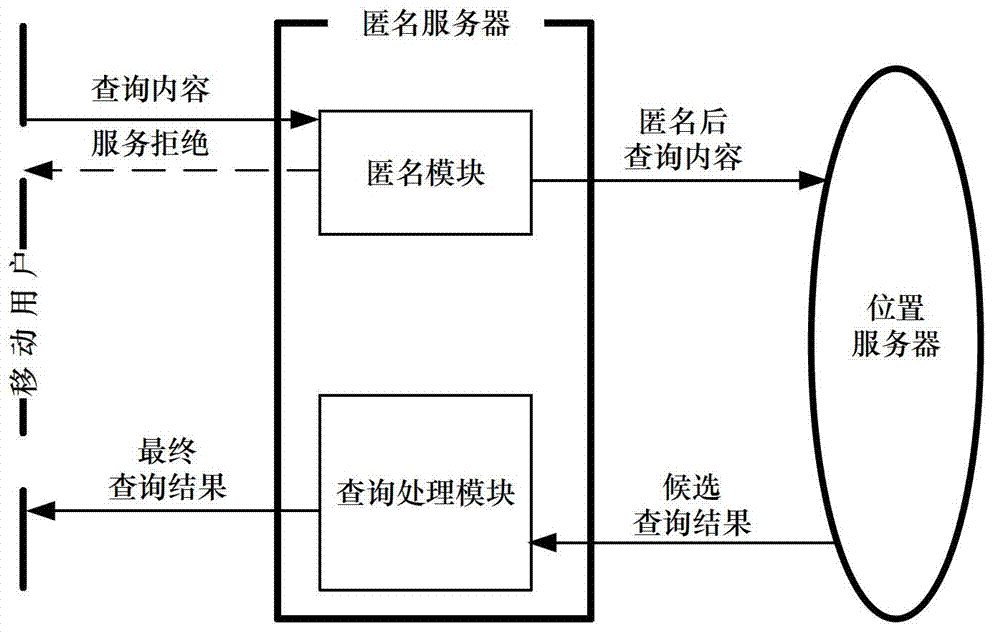
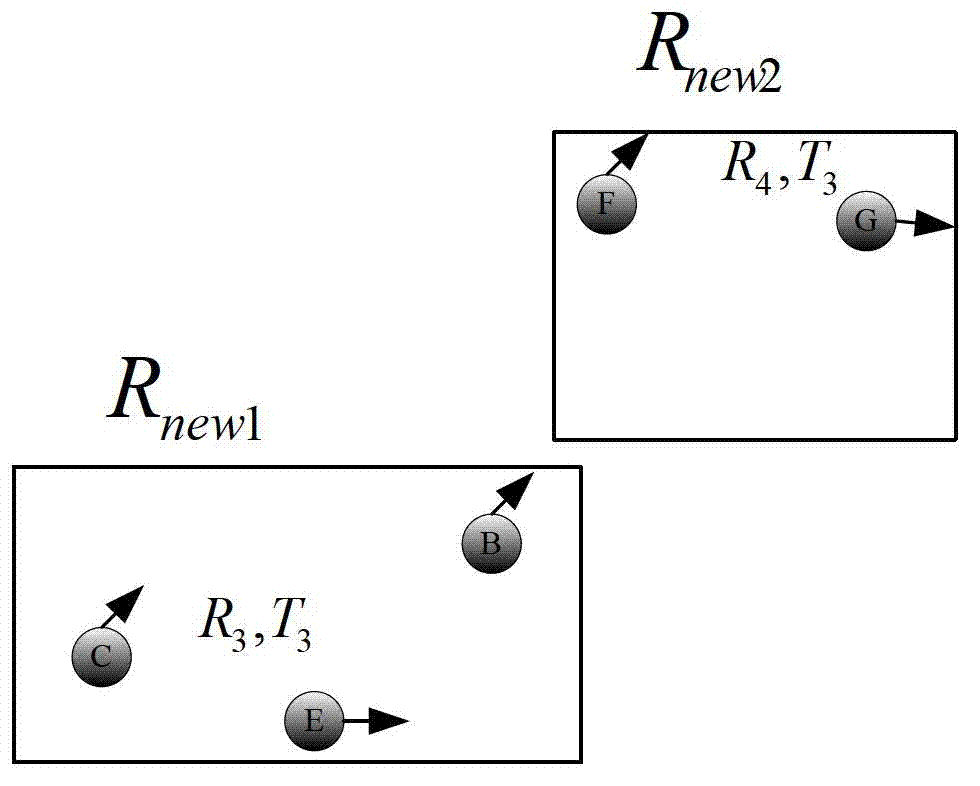
The invention discloses a continuous query oriented location anonymizing method applicable to a location service system, belonging to the technical field of privacy protection of location service, which comprises the steps of: proposing an anonymizing request by a mobile user; anonymizing the request by an anonymizing module in an anonymizing server, and sending the anonymized request to a location server; processing the request by the location server, integrating query results and sending to the anonymizing server; integrating and filtering received candidate results by a query processing module of the anonymizing server, and sending a precise result to the corresponding mobile user. According to the anonymizing method, personalized customization of privacy protection parameters of the user is permitted. The anonymizing module operates in the anonymizing server, and is used for calculating by the anonymizing method provided by the invention depending on the privacy protection parameters of the mobile user, to guarantee that all anonymizing regions of the mobile user include an identical number of queries in a query valid period and the anonymizing space is shared by the mobile users in the space; and the query privacy of the mobile user who proposes a continuous query in the location service is effectively protected.
Owner:BEIHANG UNIV
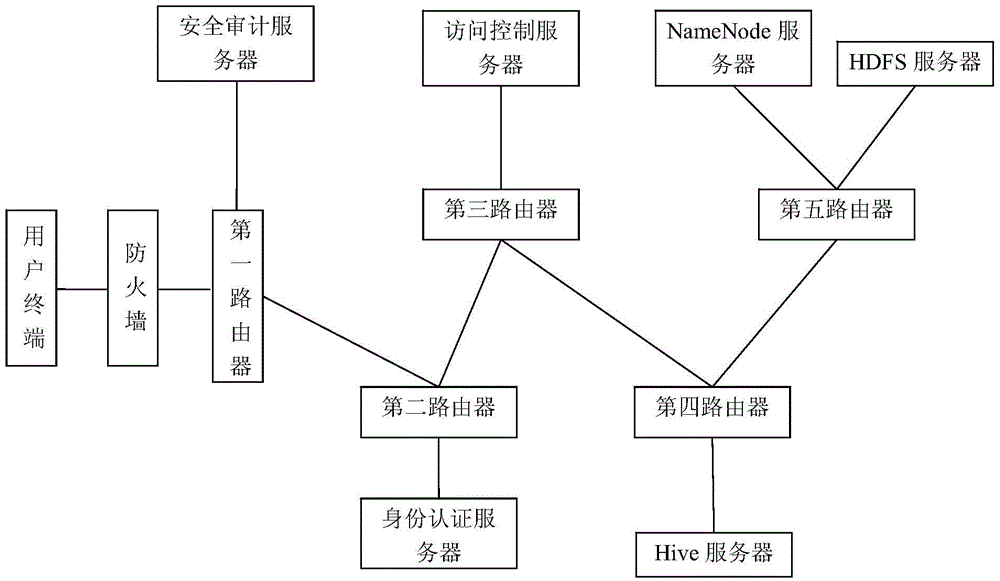
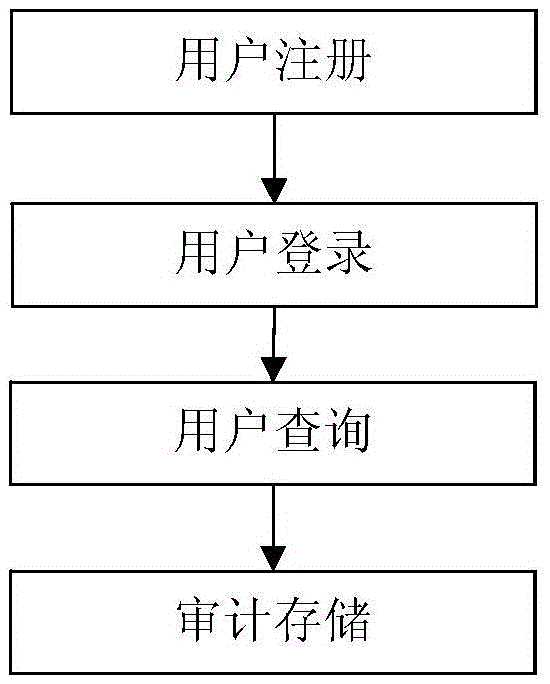
Hive platform user safety management system and application
InactiveCN105656903AMeet safety requirementsAvoid the shortcomings of intertwined functions and reduced business efficiencyTransmissionSafety management systemsData query
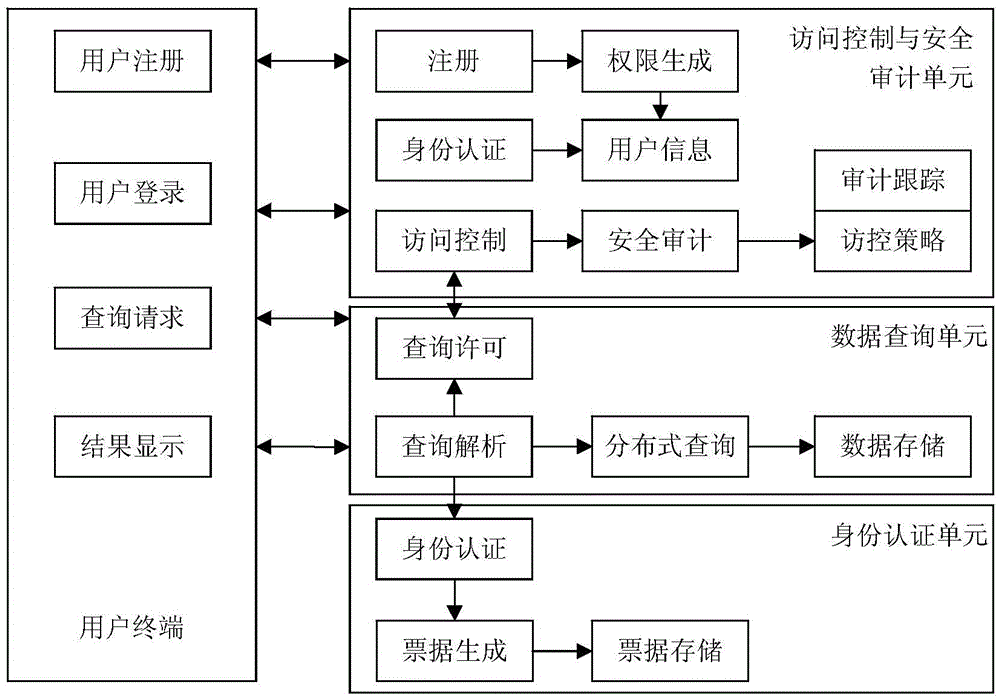
The invention discloses a Hive platform oriented user safety management system. The Hive platform oriented user safety management system comprises an access control and safety audition unit, a data query unit and an identify authentication unit, wherein the access control and safety audition unit comprises a safety audition server and an access control server, the data query unit comprises an HDFS server, a NameNode server and a Hive server, and the identify authentication unit comprises an LDAP server. A Hive platform oriented user safety management method comprises four steps, including user registration, user login, user query and audition storage. According to the Hive platform oriented user safety management system and method, an exceed authority access action of the traditional user to a large-scale storage system is prevented, data leakage due to the fact that a data storage device is stolen can be safely and effectively prevented, and problems that data packets are captured illegally and private data is obtained after the traditional storage system is invaded by external personnel are prevented.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
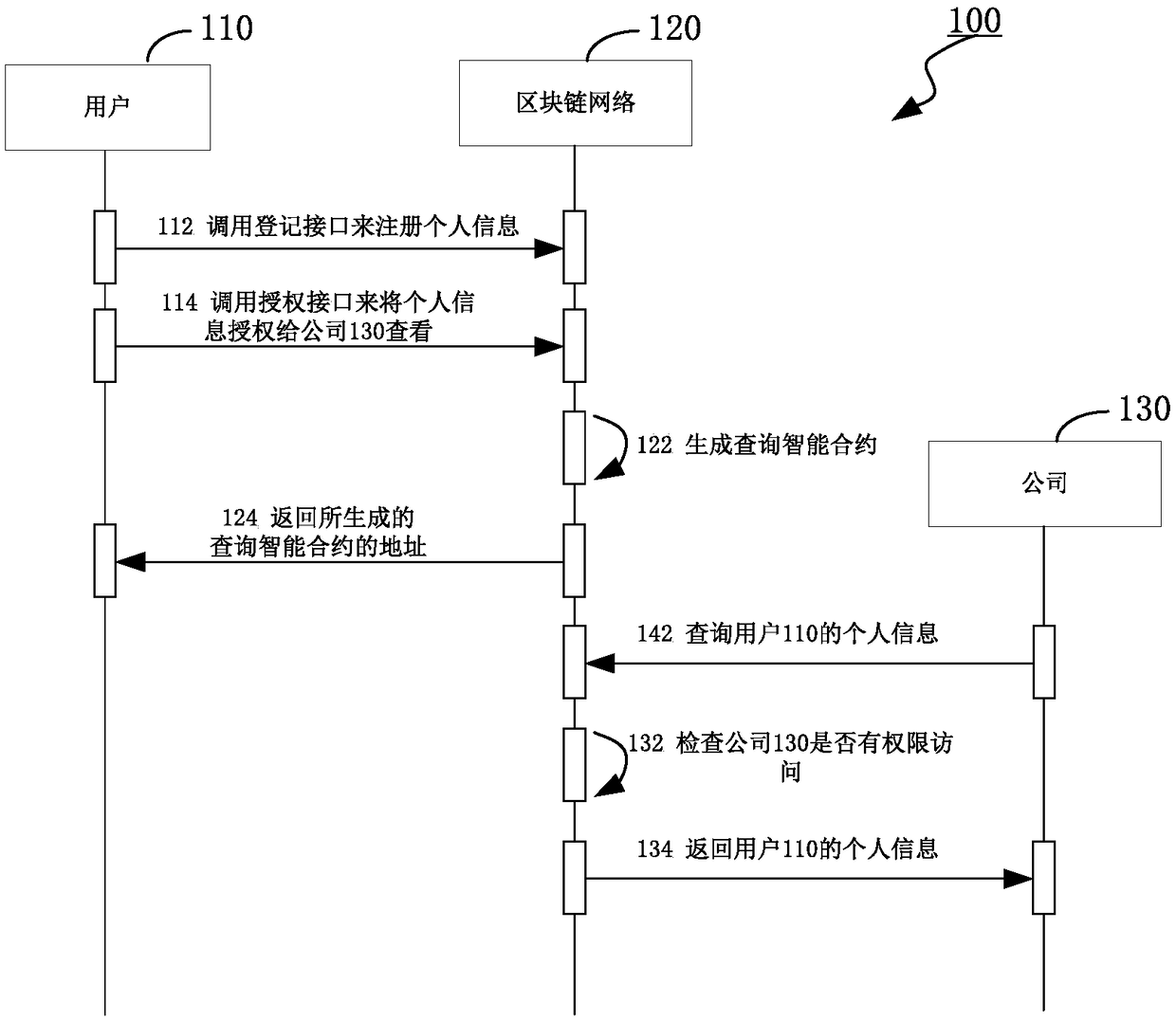
Method, apparatus and storage medium for processing privacy data based on block chain
ActiveCN109214197ARealize strict protectionPrevent gettingDigital data protectionAuthorizationInternet privacy
Embodiments of the present invention provide a method for processing privacy data based on a block chain. The method includes receiving an authorization request including an address of an authorized account on the block chain, a public key of the authorized account, and a privacy data identifier. Obtaining encrypted first privacy data associated with the privacy data identification from the ledgerof the block chain; decrypting the encrypted first privacy data and obtaining second privacy data by encrypting at least a portion of the decrypted first privacy data using the public key; generatinga query intelligent contract for querying the second privacy data according to at least the address of the authorized account and the second privacy data; and returning an address of the query smartcontract. The method according to the embodiment of the invention can precisely control the privacy data in the account book of the block chain, so as to ensure that the privacy data will not be obtained by an unauthorized individual or an organization, and the privacy of the data is ensured.
Owner:SHANGHAI DIANRONG INFORMATION TECH CO LTD
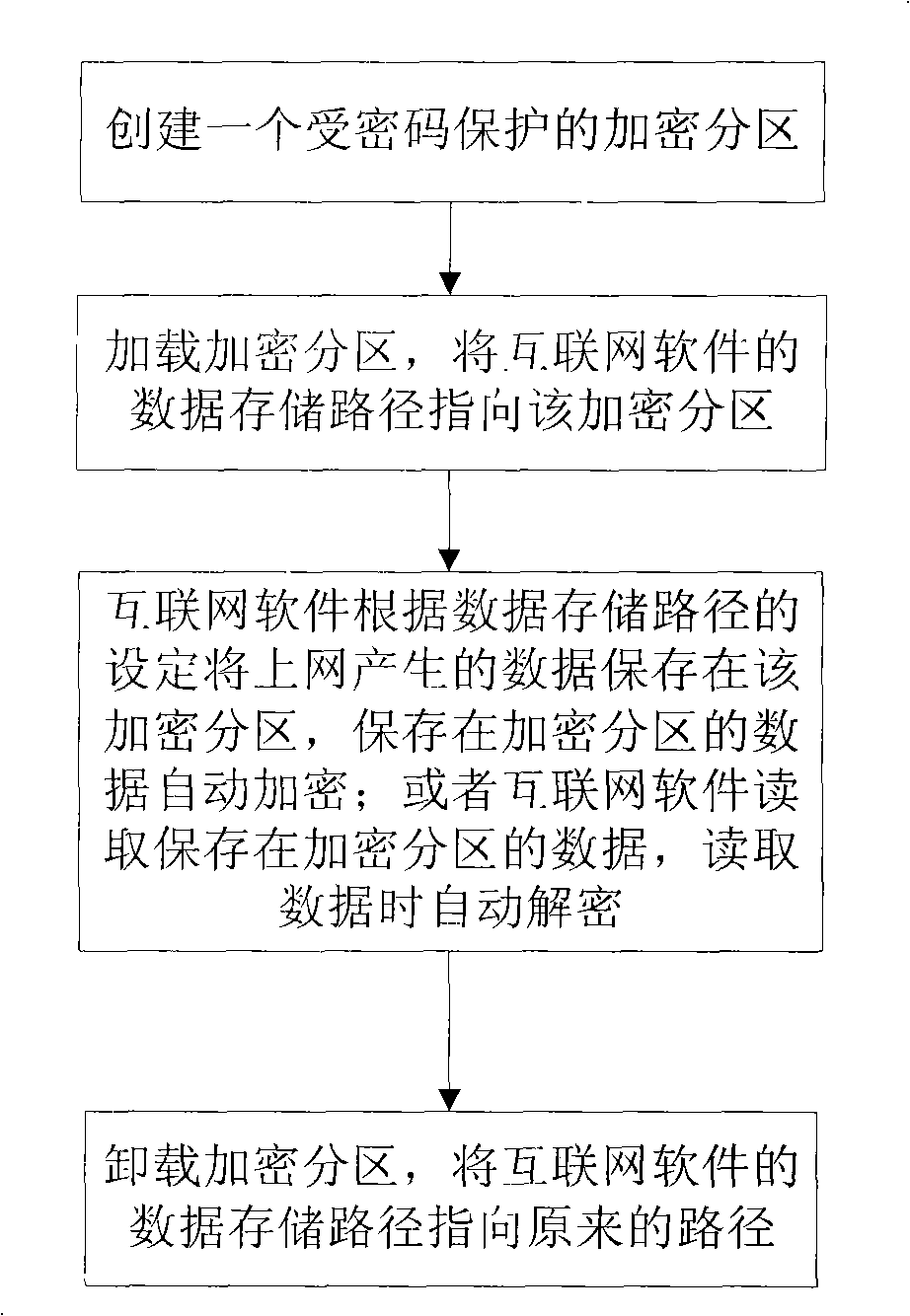
Internet software internet privacy protection method
InactiveCN101408916APrevent gettingProtect online privacyDigital data protectionInternal/peripheral component protectionPasswordThe Internet
The invention provides an online privacy protection method by internet software. The method comprises the following steps: (1) creating an encryption partition protected by a password; (2) loading the encryption partition: causing the data storage path of the internet software to point to the encryption partition; (3) the internet software automatically storing the data generated online in the encryption partition according to the setting of the data storage path and automatically encrypting the data stored in the encryption partition; and the internet software being capable of further reading the data stored in the encryption partition and automatically decrypting the data when being read; and (4) unloading the encryption partition: causing the data storage path of the internet software to point to the original path. The online privacy protection method can ensure users to completely utilize the convenient functions provided by the internet software, and can effectively protect the online privacy of the user.
Owner:SHANGHAI SECOND POLYTECHNIC UNIVERSITY
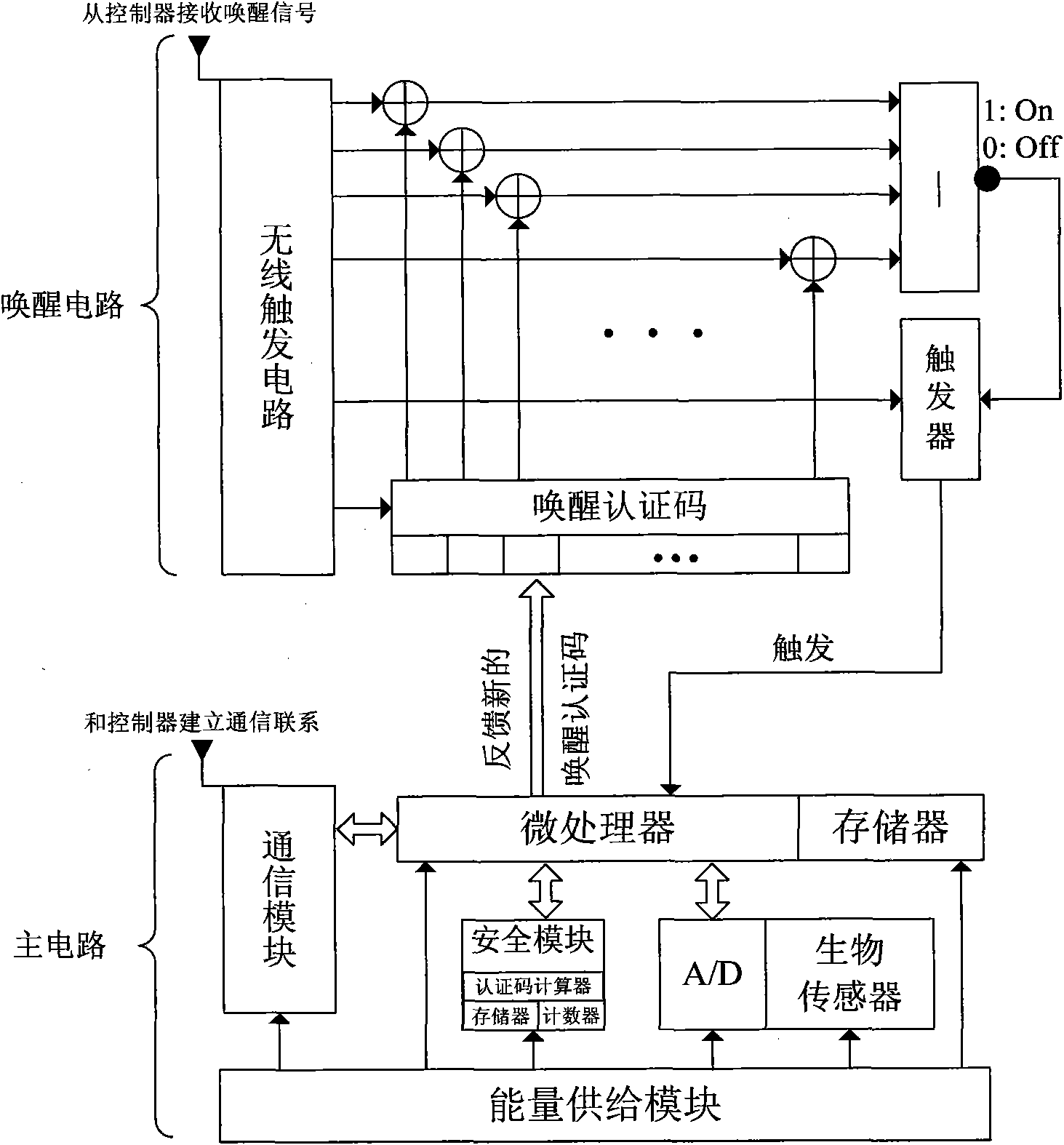
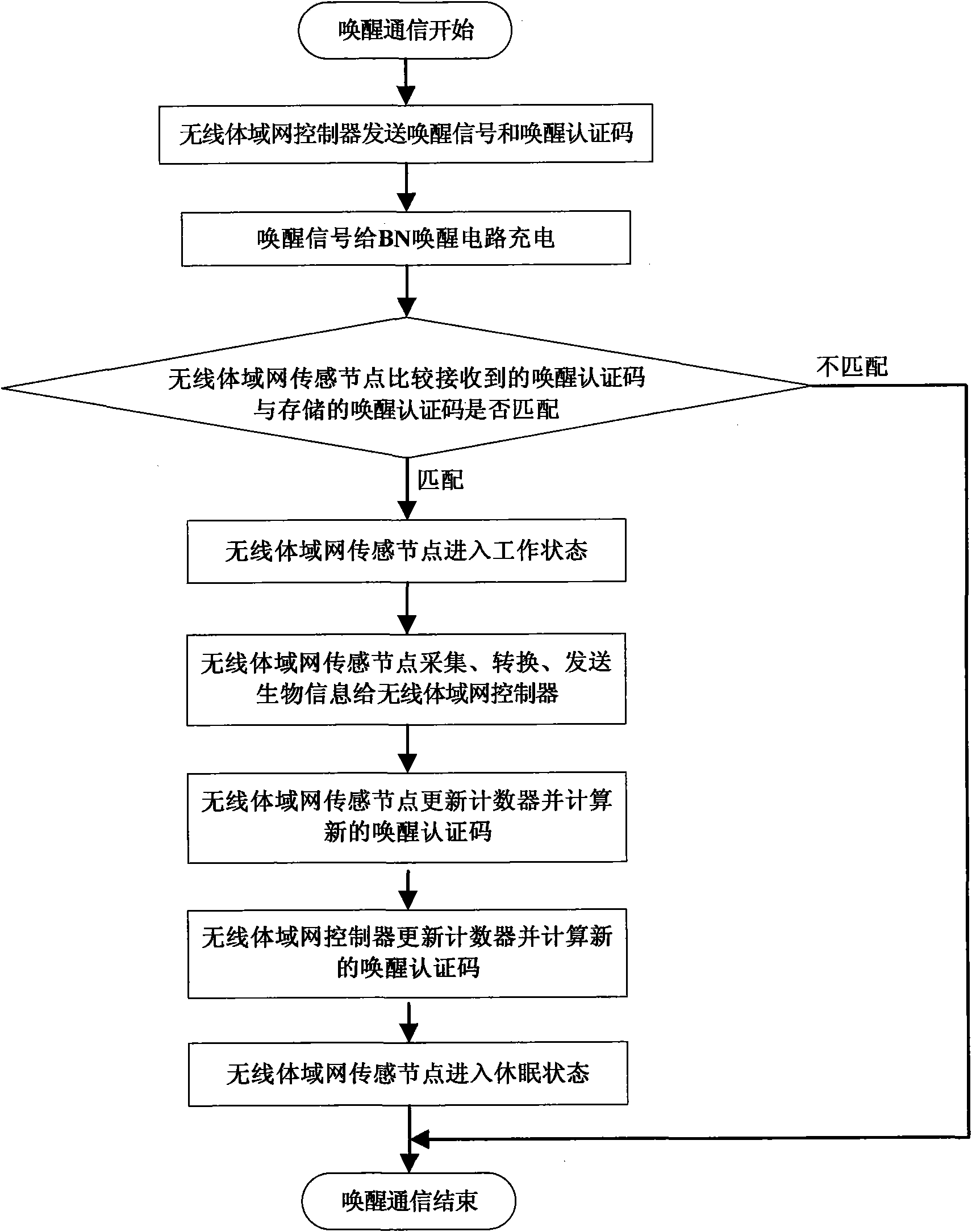
Security awakening device and method for wireless body area network sensing node
InactiveCN101674573AExtend your lifePrevent gettingEnergy efficient ICTNetwork topologiesBody area networkEnergy consumption
The invention discloses security awakening device and method for a wireless body area network sensing node, which mainly solve the problems of large energy consumption and poor security of the prior wireless body area network sensing node. The security awakening device comprises a wireless trigger circuit, an awakening authentication code comparing circuit and a main circuit, wherein the wirelesstrigger circuit obtains energy from an awakening signal transmitted by a wireless body area network controller and respectively transmits the energy to the awakening authentication code comparing circuit and the main circuit; the awakening authentication code comparing circuit compares an awakening authentication code in the awakening signal with the awakening authentication code stored in the wireless body area network sensing node and judges whether the main circuit is triggered or not; and the main circuit receives a trigger signal of the wireless trigger circuit to establish data communication with the wireless body area network controller and feeds back a new awakening authentication code to the awakening authentication code comparing circuit for use during awakening at next time. Theinvention has the advantages of less energy consumption and high security and can be used for awakening the sensing node in a wireless body area network.
Owner:XIDIAN UNIV
Holographic display system and holographic display method
The invention discloses a holographic display system and a holographic display method, relates to the technical field of display, and can prevent other persons from obtaining holographic three-dimensional image information and ensure the safety of user information when providing the holographic three-dimensional image information for a user. The holographic display system comprises a display device and a pair of peep-proof spectacles, wherein the display device comprises backlight for generating laser beams, a data processor and a first spatial light modulator, wherein the data processor is used for generating holographic coding data according to to-be-displayed holographic three-dimensional image information, and dividing the holographic coding data into first sub-holographic coding data and second sub-holographic coding data; and the first spatial light modulator comprises multiple first pixels and is used for modulating the laser beams emitted into each first pixel according to the first sub-holographic coding data. The pair of peep-proof spectacles comprises a second spatial light modulator, wherein the second spatial light modulator is connected with the data processor, comprises multiple second pixels and is used for modulating the laser beams emitted into the each second pixel according to the second sub-holographic coding data. The holographic display system and the holographic display method provide safe holographic three-dimensional information for the user.
Owner:BOE TECH GRP CO LTD
System and method for multiple laser triggering
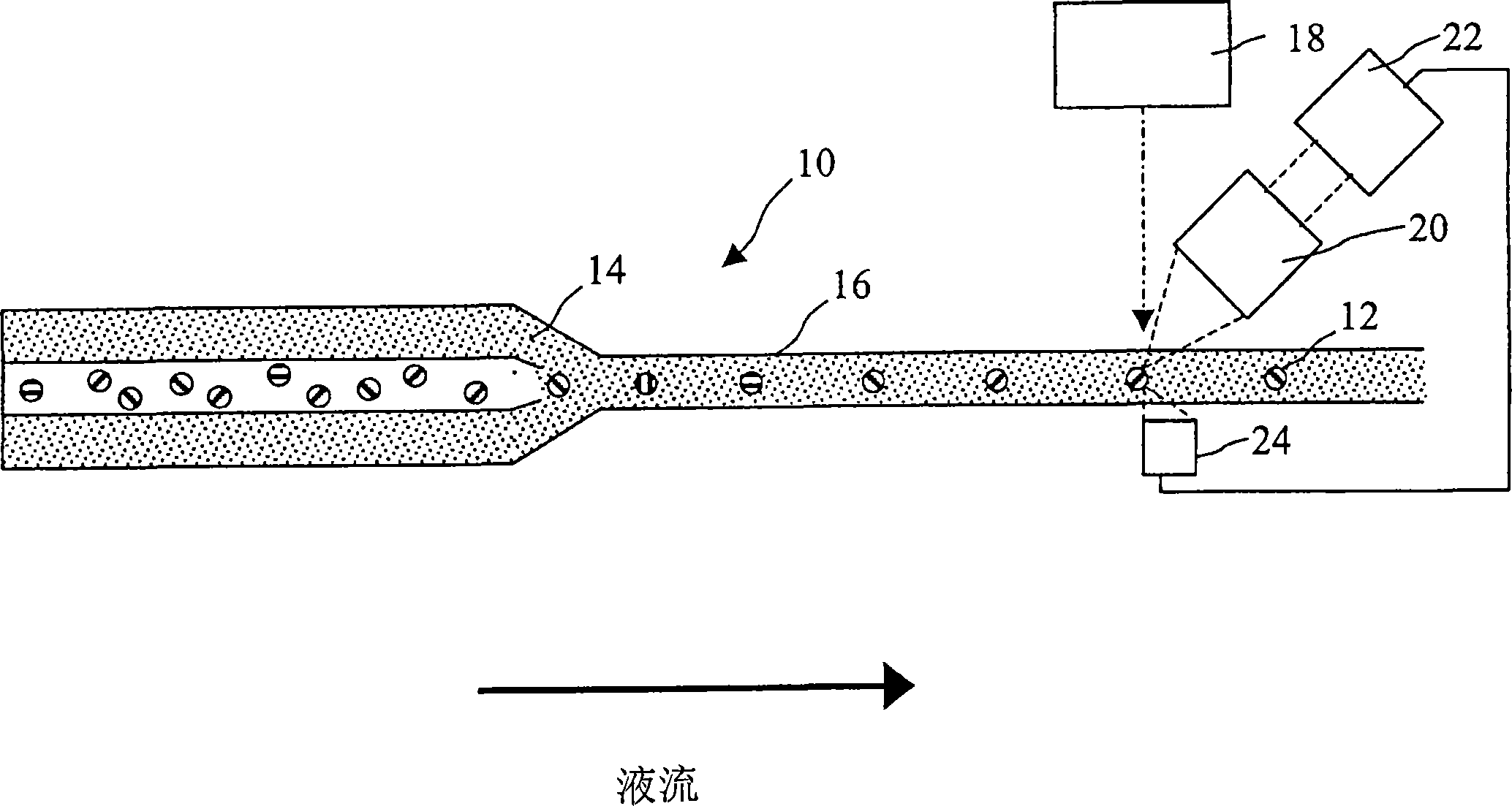
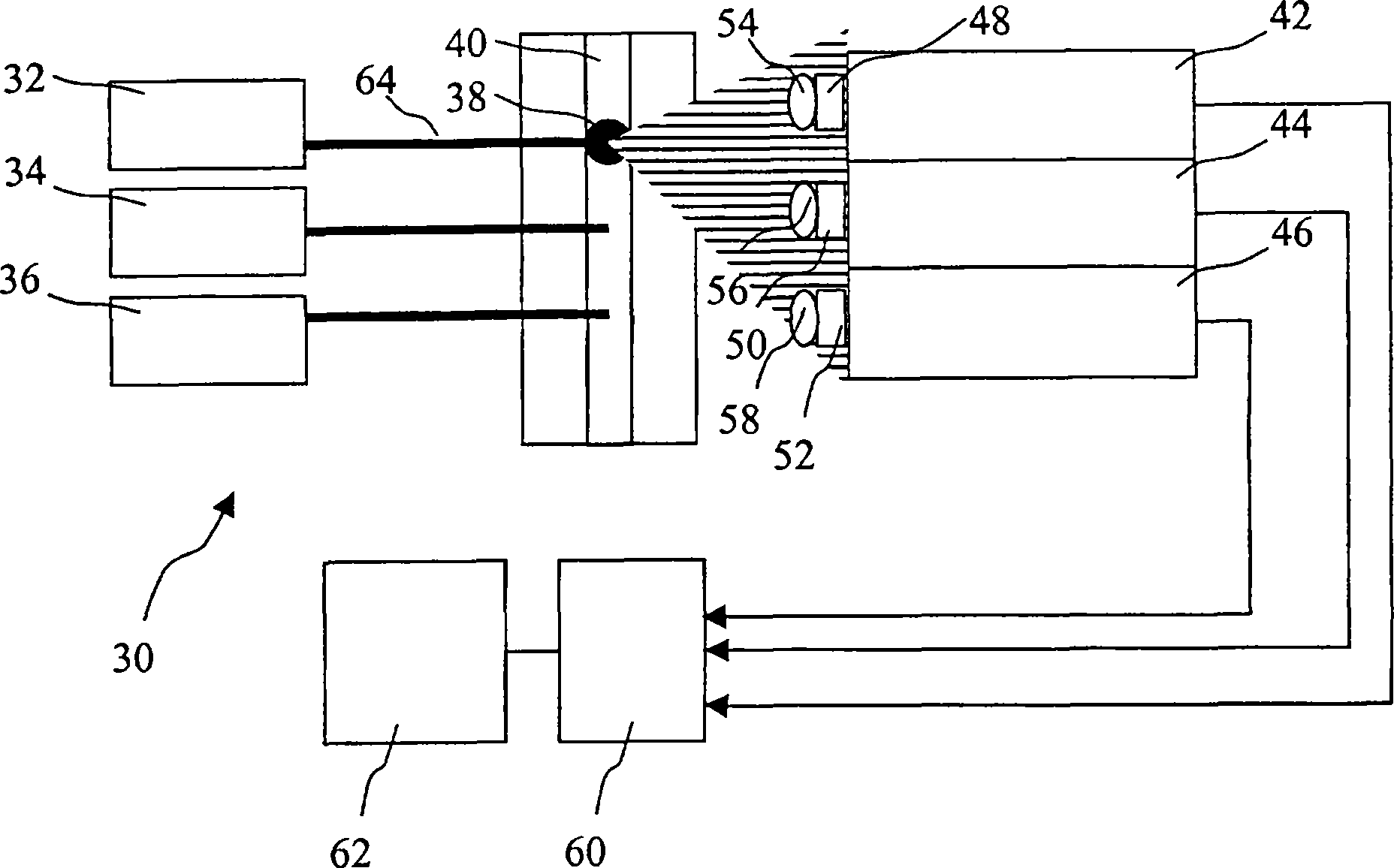
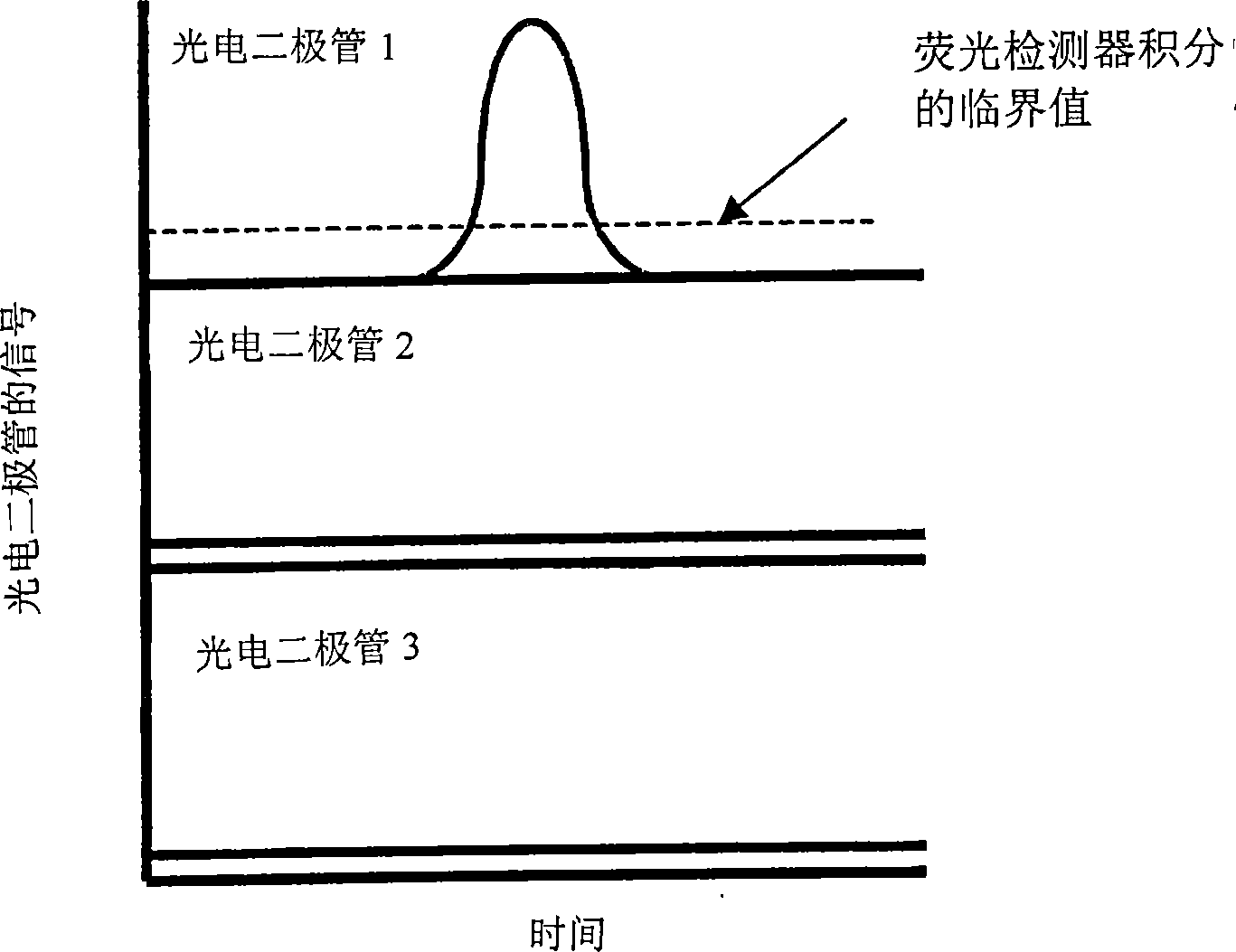
InactiveCN1910439APrevent gettingMaterial analysis by optical meansIndividual particle analysisIntegratorFluorescence
A system for measuring the irradiance of a fluorescently labeled particle having a cytometric flow chamber; a plurality of excitation light sources; a plurality of scatter detectors, each configured to detect light from only one of the plurality of excitation light sources and arranged so as to detect scattered light from the particle; a trigger connected to the plurality of scatter detectors, the trigger emitting a signal when scattered light incident on one of the scatter detectors is exceeding a predetermined threshold value; collection optics; at least one fluorescence detector to receive emissions collected by the collection optics and generate an output, the at least one fluorescence detector being configured to respond only to a discrete number of wavelength bands; and an integrator for recording the output of the at least one fluorescence detector in response to a signal from the trigger.
Owner:BECKMAN COULTER INC
Radio frequency device, authentication server and authentication method
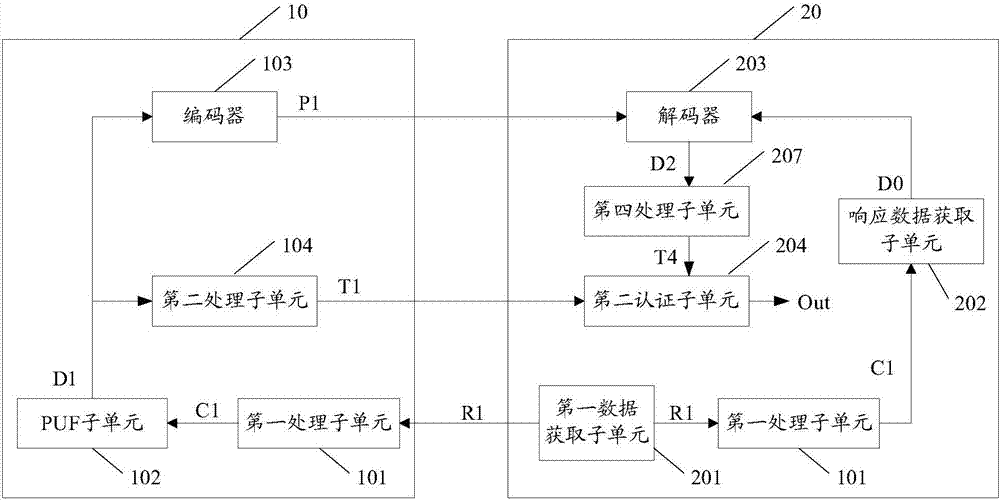
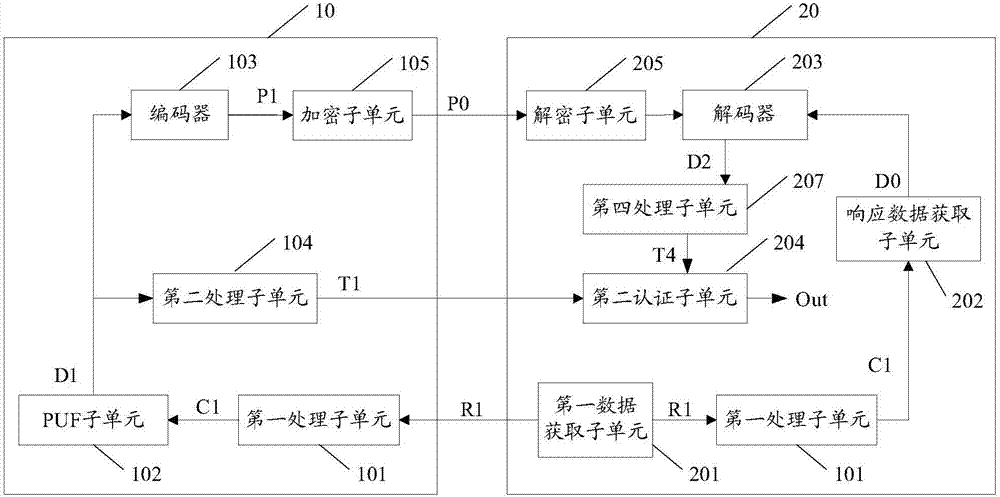
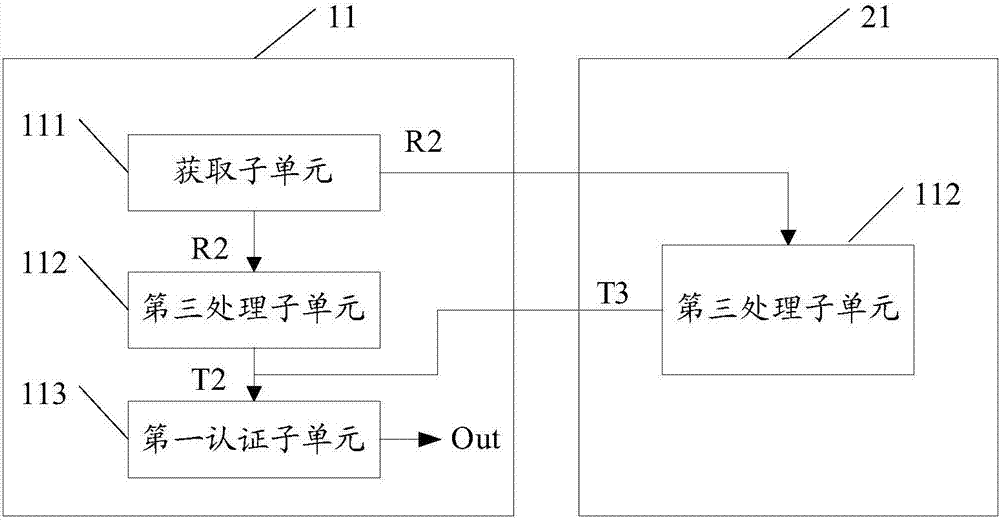
InactiveCN107493171APrevent forgeryAvoid gettingUser identity/authority verificationComputer hardwareAuthentication server
The invention discloses a radio frequency device, an authentication server and an authentication method. The radio frequency device comprises a first authentication unit. The first authentication unit comprises a PUF sub unit, an encoder and a second processing sub unit, wherein the PUF sub unit is suitable for processing a first challenge when the first challenge is acquired and outputting corresponding real response data; the encoder is suitable for carrying out encoding and processing on the real response data, acquiring corresponding auxiliary data and transmitting the auxiliary data to the authentication server; and the second processing sub unit is suitable for processing the real response data, acquiring corresponding first processing data and transmitting the data to the authentication server. When the above radio frequency device is applied, the safety during the authentication process between the radio frequency device and the authentication server can be improved.
Owner:SHANGHAI FUDAN MICROELECTRONICS GROUP
Safety certification method and system for intelligent television software based on android operation system
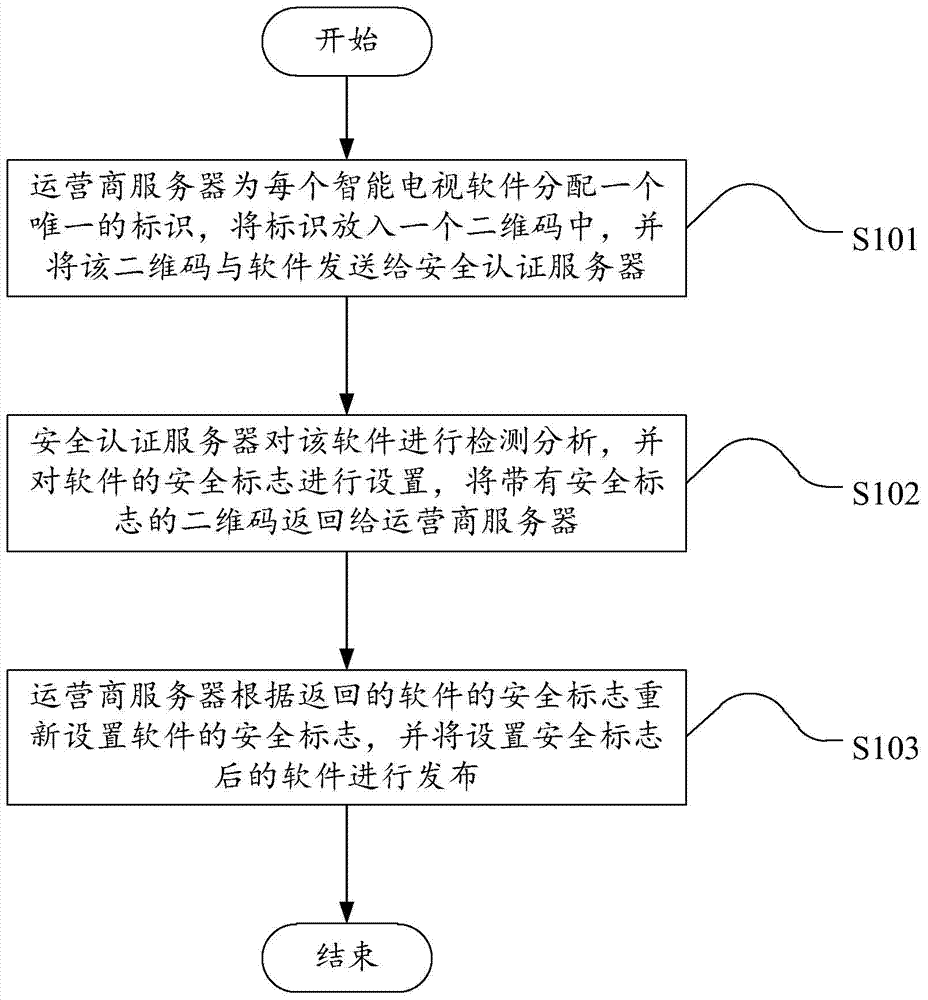
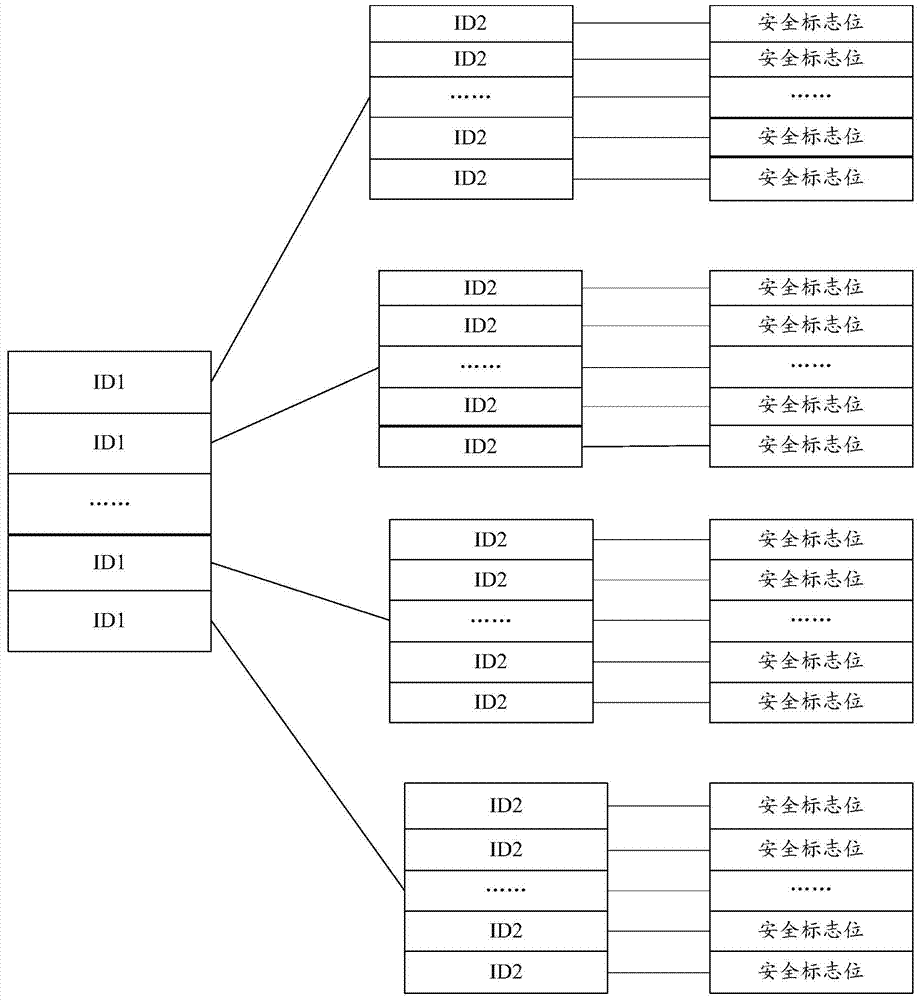
ActiveCN103501307AReduce waste of resourcesImprove processing efficiencyTransmissionOperational systemSoftware engineering
The embodiment of the invention discloses a safety certification method and a safety certification system for intelligent television software based on an android operation system, wherein the method comprises the following steps that an operator server allocates one unique mark for each intelligent television software, the mark is put into a two-dimension code, and in addition, the two-dimension code and the software are sent to a safety certification server; the safety certification server carries out detection analysis on the software and sets the safety mark of the software, and the two-dimension code with the safety mark is returned to the operator server; the operator server resets the safety mark of the software according to the returned safety mark of the software, and in addition, the software after the setting of the safety mark is issued. When the embodiment of the invention is implemented, the safety detection certification can be carried out on the intelligent television software, in addition, the resource waste of intelligent televisions can be reduced, the processing efficiency of the intelligent televisions on the software is improved, and the use by users is convenient.
Owner:SUN YAT SEN UNIV
Encrypted blind signature method based on quantum secret communication technology
PendingCN110601822ASolve reversible problemsSolve secure transmissionKey distribution for secure communicationUser identity/authority verificationObfuscationDistribution system
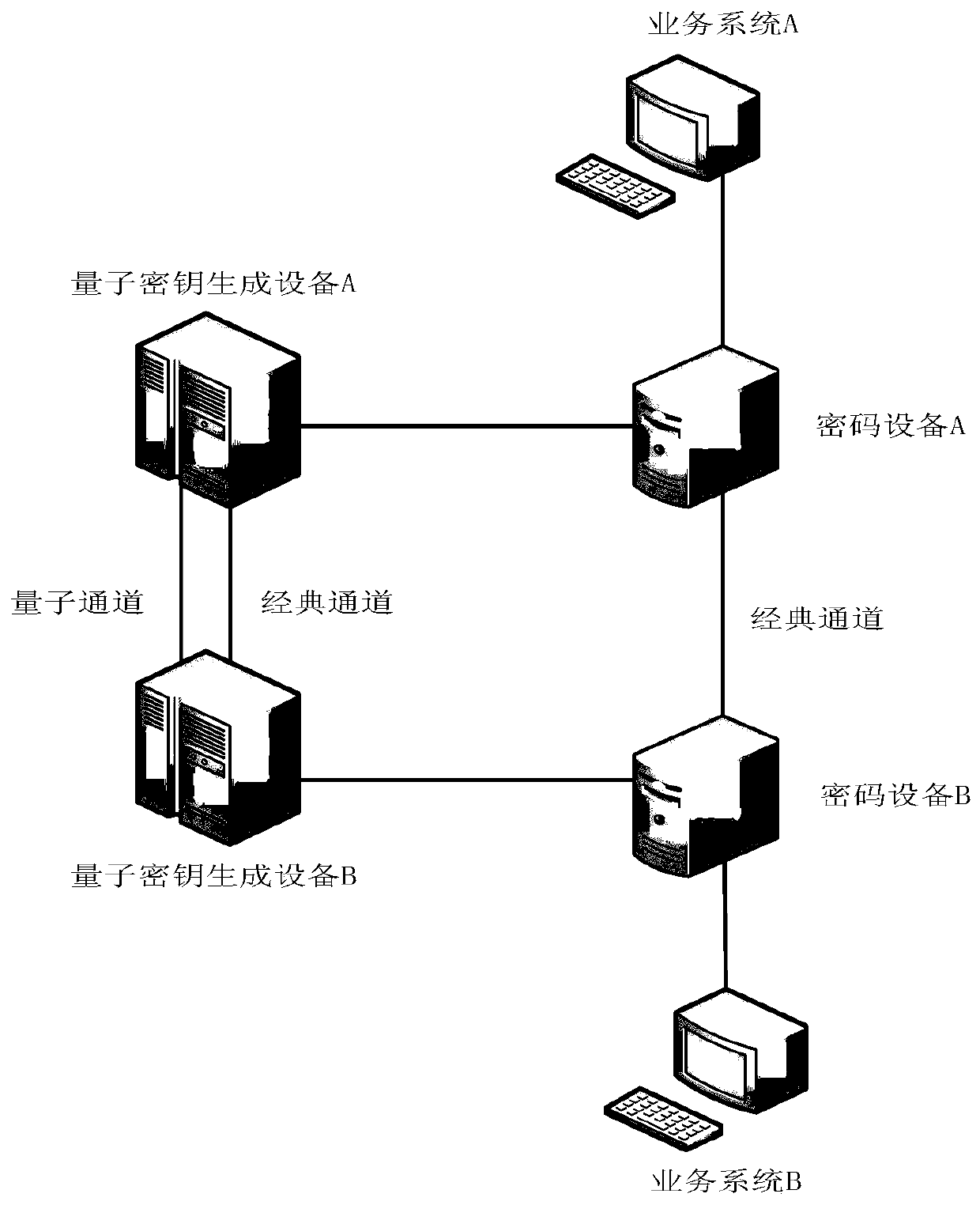
The invention discloses an encrypted blind signature method based on a quantum secret communication technology. According to the method, the encrypted blind signature function is obfuscated by adopting an obfuscation technology, so that the code of the code obtained by reverse engineering of an enemy is an obfuscated code, the blindness and the one-mcore unforgeability under the encrypted blind signature obfuscator are proposed, and a source program is prevented from being obtained by a user or an unauthorized user. Then, in the protocol interaction process, a cooperation mode of a quantum keygeneration device and an encryption device is adopted, and the transmission security is ensured through a quantum key security distribution system of the quantum key generation device.
Owner:STATE GRID CORP OF CHINA +4
Private transaction based on a block chain and an application method and device thereof
ActiveCN109584066APrivacy protectionPrevent gettingFinanceDigital data protectionData informationPrivacy protection
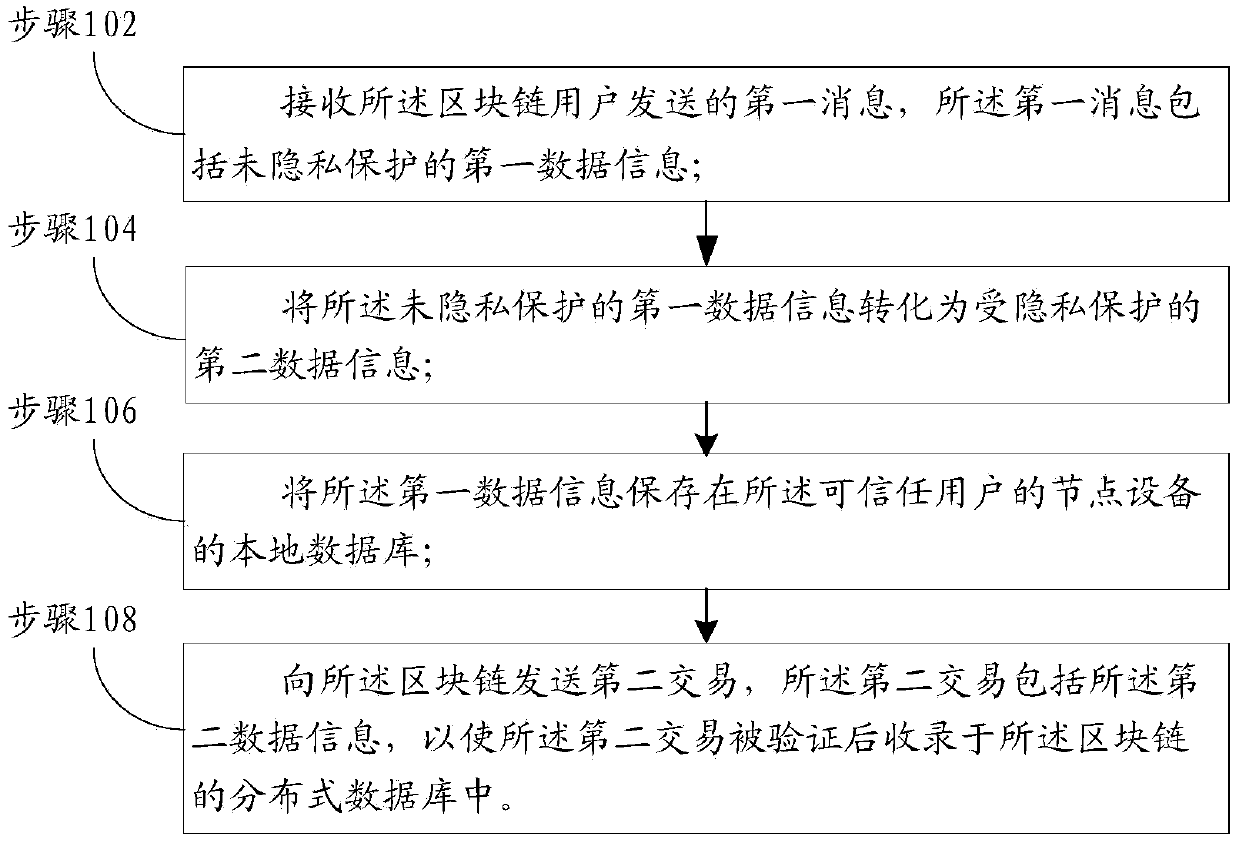
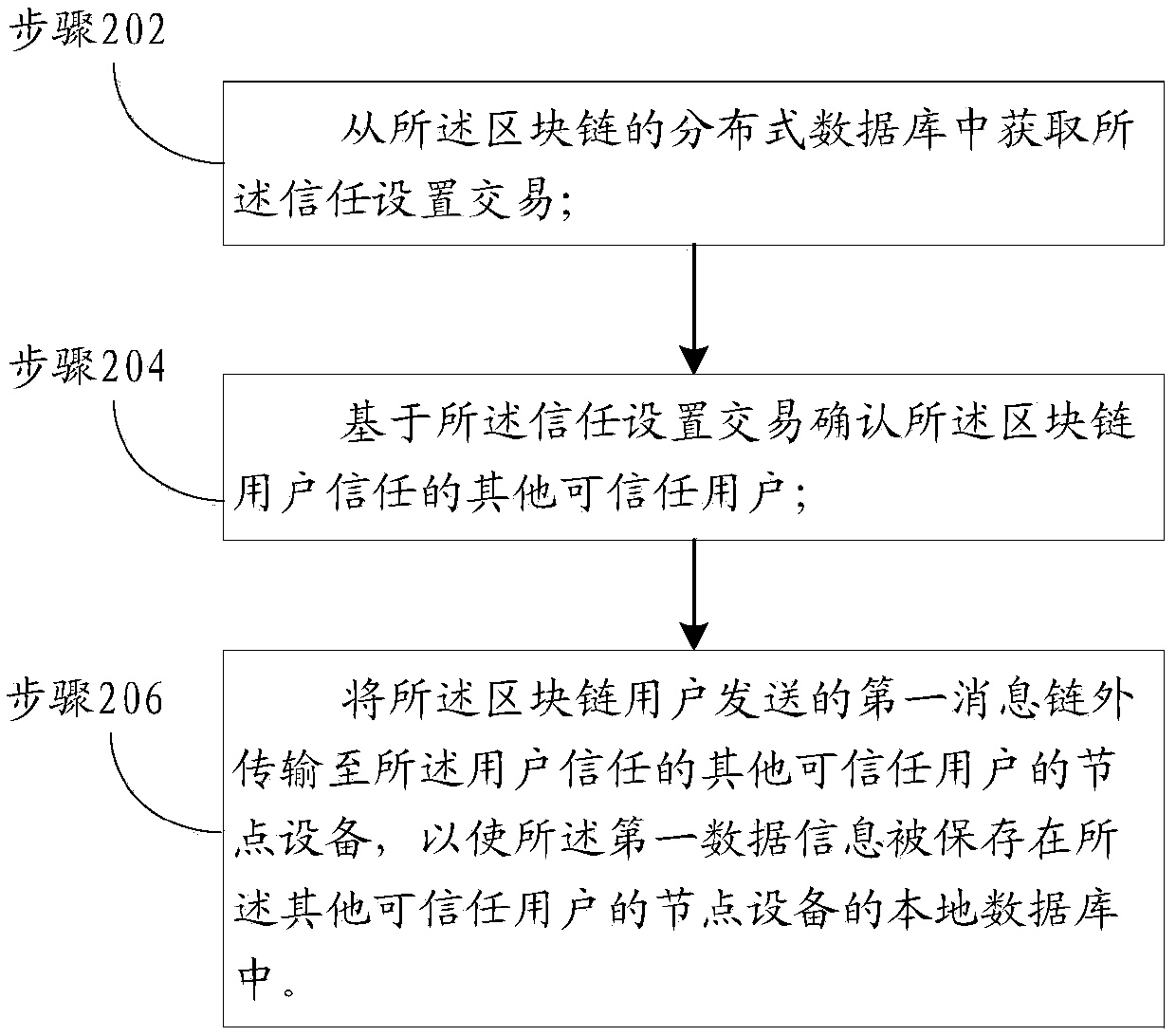
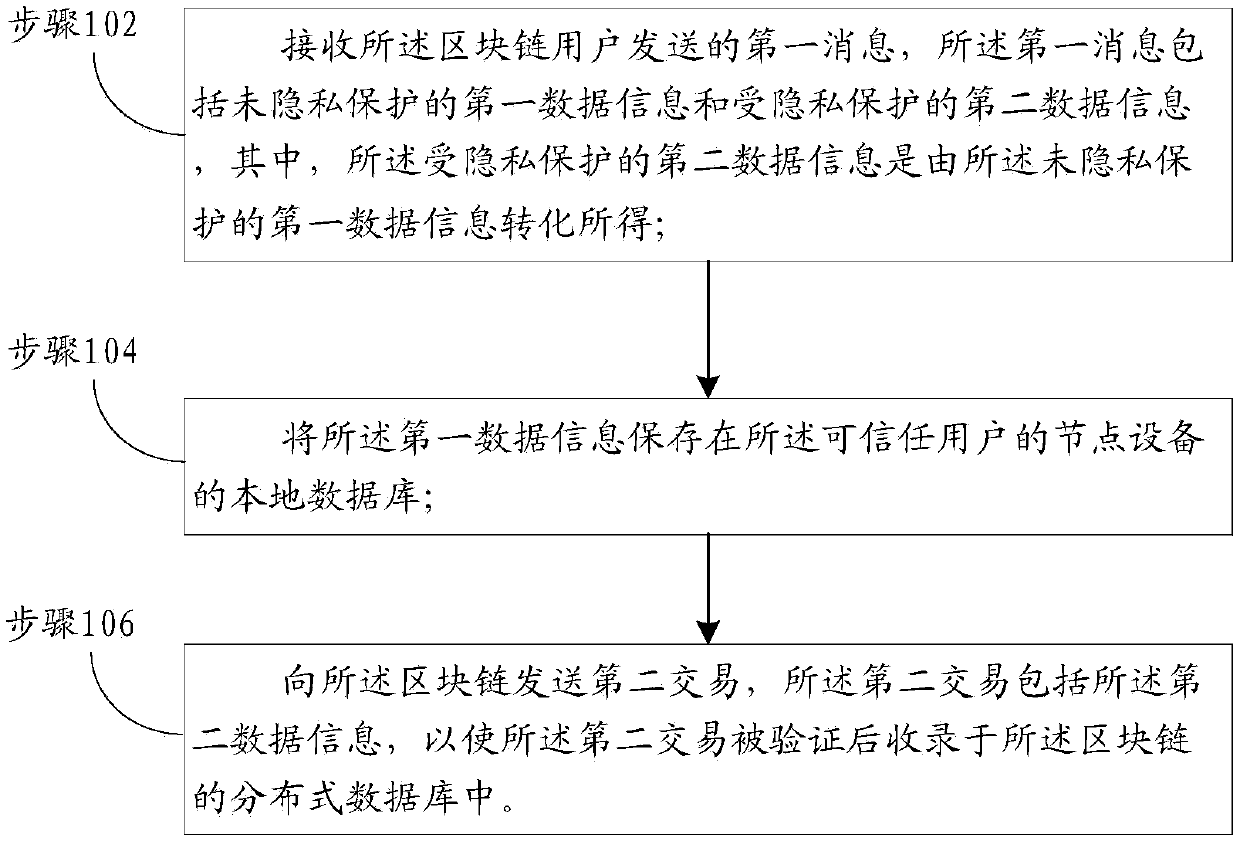
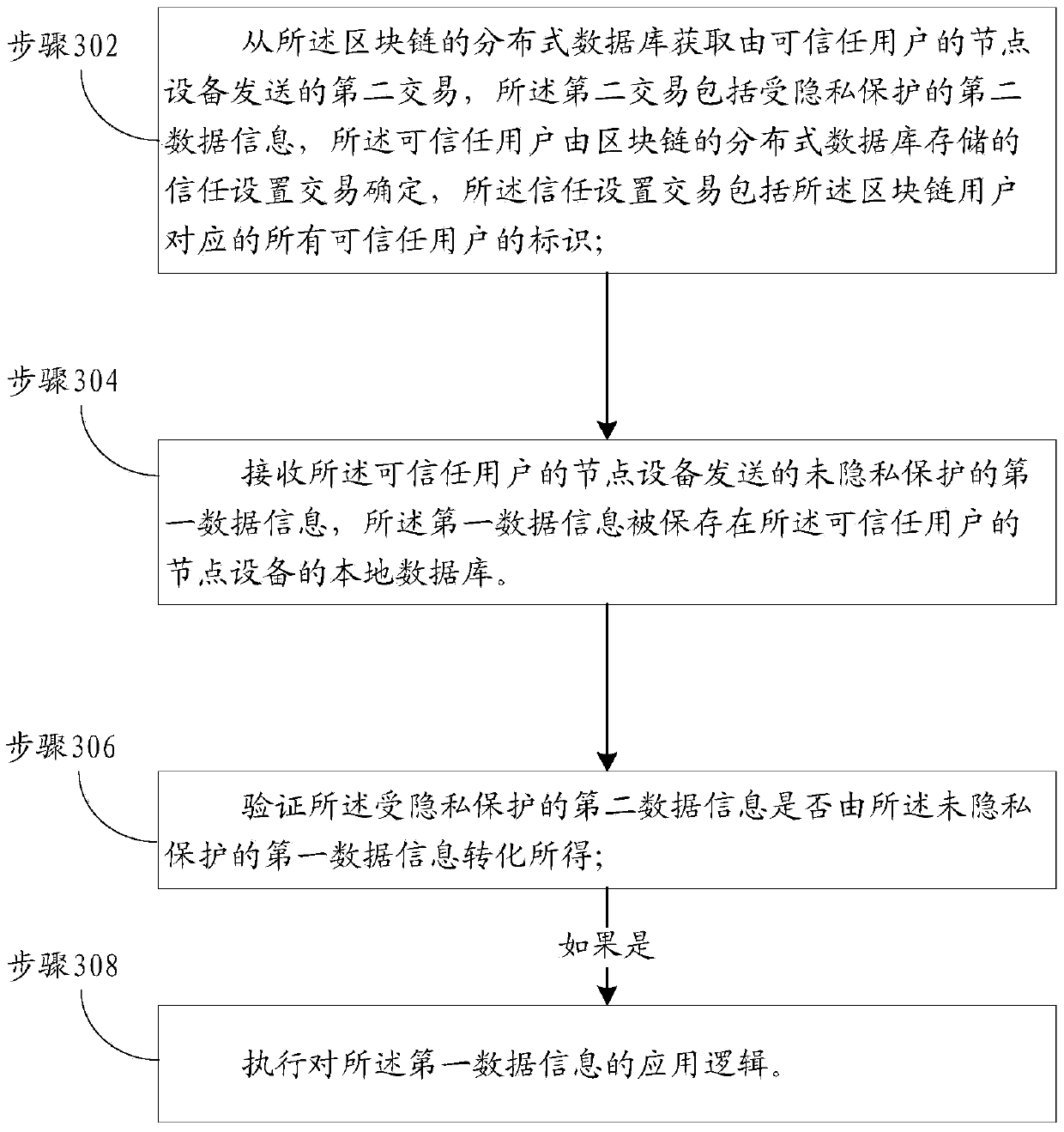
One or more embodiments of the present specification provide a blockchain-based private transaction method. The private transaction method based on the block chain is applied to node equipment of a trustable user and comprises the steps that a first message sent by the block chain user is received, and the first message comprises first data information which is not subjected to privacy protection;Converting the first data information which is not subjected to privacy protection into second data information which is subjected to privacy protection; Storing the first data information in a localdatabase of node equipment of the trusted user; And sending a second transaction to the block chain, the second transaction comprising the second data information, so that the second transaction is verified and recorded in a distributed database of the block chain.
Owner:ADVANCED NEW TECH CO LTD
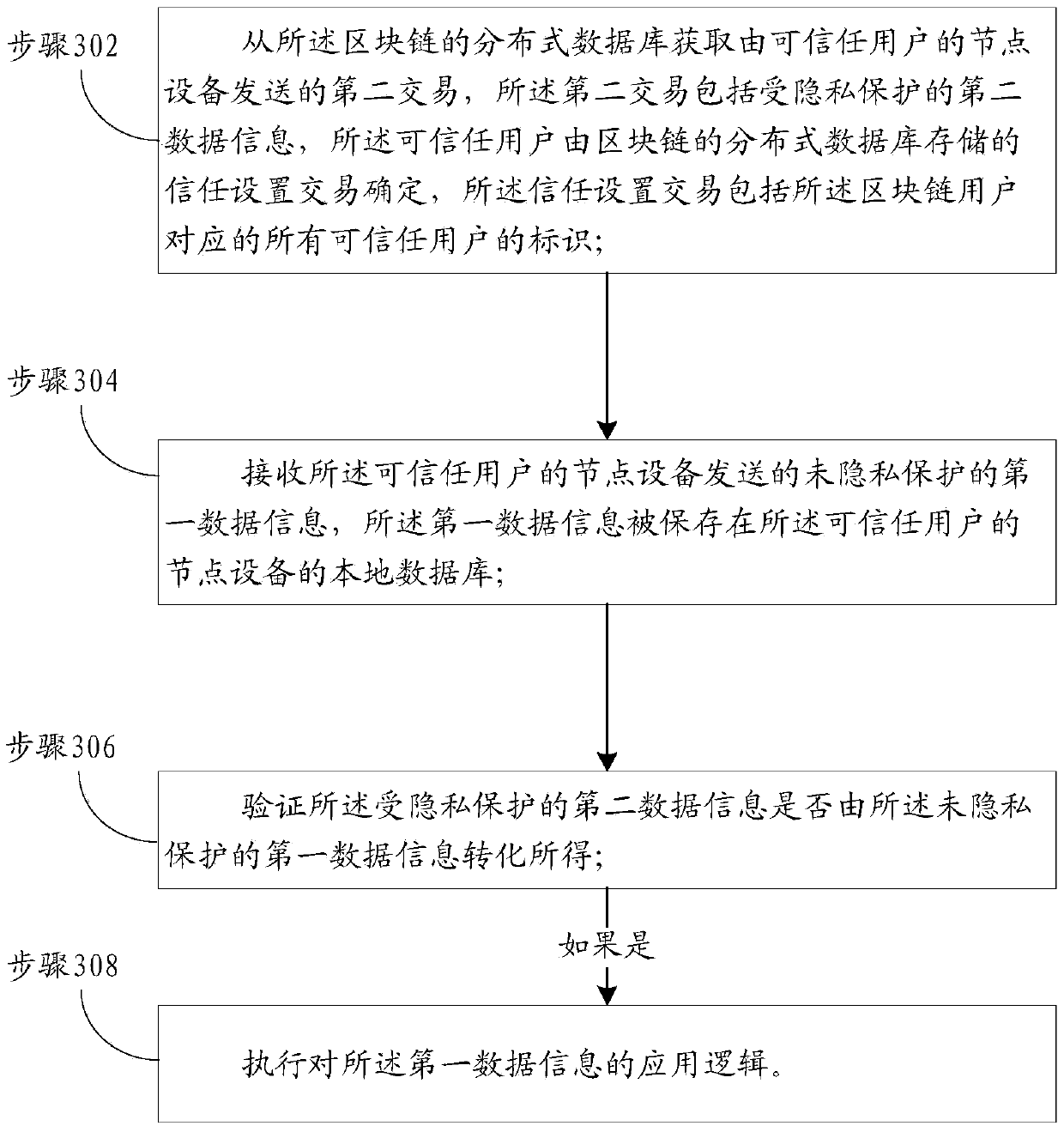
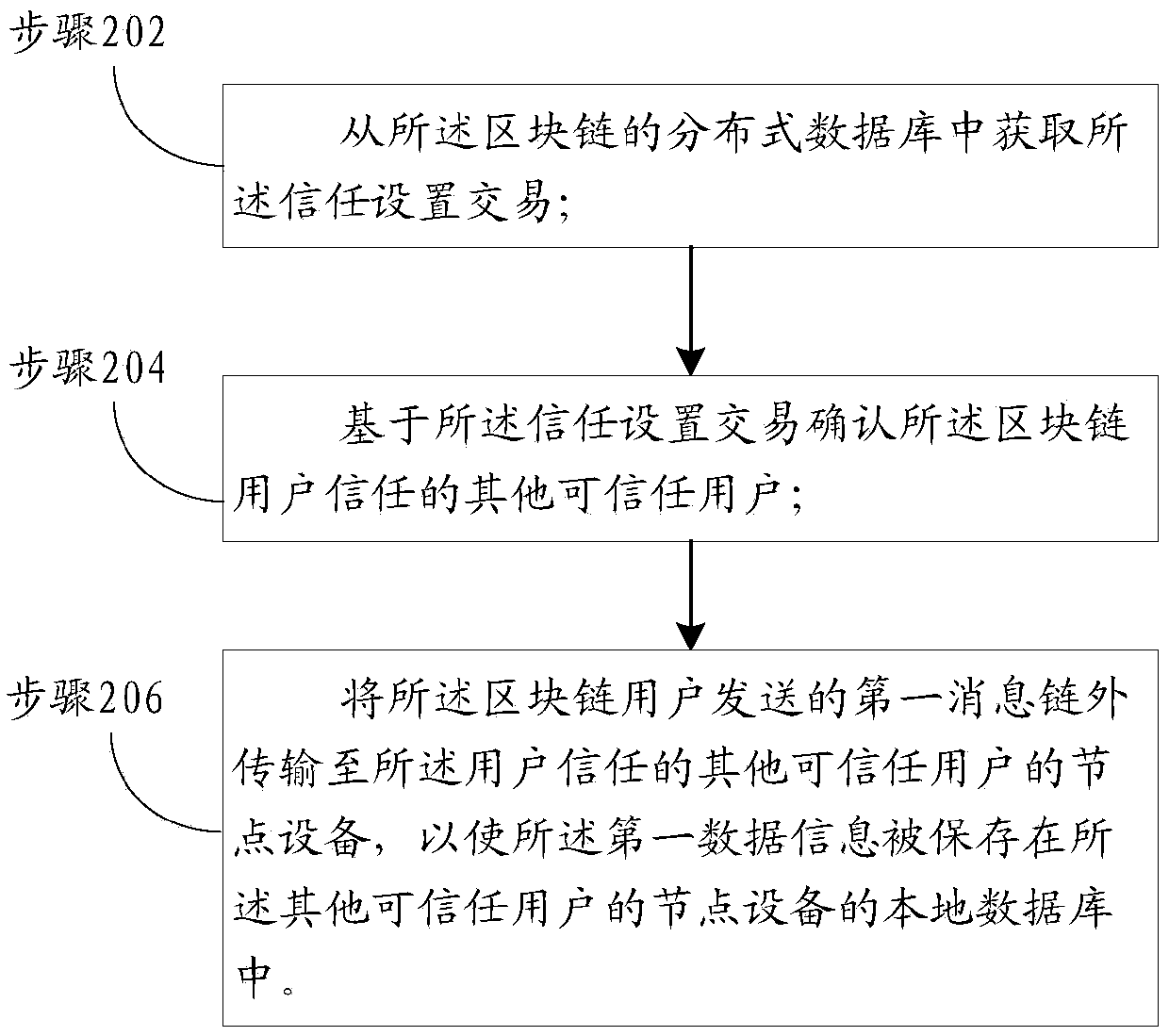
Privacy transaction method and device based on block chain and application method and device thereof
ActiveCN109614813APrivacy protectionPrevent gettingFinanceDigital data protectionBlockchainData information
One or more embodiments of the present specification provide a privacy transaction method and device based on block chain and application method and device thereof. The private transaction method based on the block chain is applied to node equipment of trusted users. The method comprises the steps that a first message sent by a block chain user is received, the first message comprises first data information which is not protected by privacy and second data information which is protected by privacy, and the second data information which is protected by privacy is obtained by converting the first data information which is not protected by privacy; storing the first data information in a local database of node equipment of the trusted user; and sending a second transaction to the block chain,the second transaction comprising the second data information, so that the second transaction is verified and recorded in a distributed database of the block chain.
Owner:ADVANCED NEW TECH CO LTD
Intelligent cabinet special for gun and bullet management
The invention discloses an intelligent cabinet special for gun and bullet management, and belongs to the technical field of gun management. According to the intelligent cabinet special for gun and bullet management, a cabinet door lock is arranged outside a cabinet body, and connected with a resistance type touch control portion, the resistance type touch control portion is respectively connected with a vein living-body fingerprint collector, an infrared inductance gauge and a radio frequency identification chip, a wire is arranged on the cabinet door lock and connected with the radio frequency identification chip, a gun storage chamber and an ammunition storage chamber are arranged in the cabinet body, a gun self-destruction device is arranged in the gun storage chamber, and an ammunition self-destruction device is arranged in the ammunition storage chamber. According to the intelligent cabinet special for gun and bullet management, due to the fact that the vein living-body fingerprint collector is adopted for living-body fingerprint unlocking, a user does not need to remember a password, and does not need to worry that the password is released; the infrared induction electronic lock can monitor and feed back the usage condition of guns and bullets; due to the fact that the self-destruction devices are arranged, a thief can be prevented from obtaining undamaged guns and bullets; because an embedded intelligent operating system is installed on the cabinet body, an industrial standard communication mode is adopted, data transmission can be carried out through a wired network or a wireless network, and data security is ensured.
Owner:GUANGDONG GUANGYU SCI & TECH DEV
Anti-counterfeiting mark generation method and device
ActiveCN106295761AStrong anti-counterfeiting featuresPrevent gettingRecord carriers used with machinesProgramming languageCode coverage
The embodiment of the invention proposes an anti-counterfeiting mark generation method and device. The method comprises the steps: obtaining a mark code on a product or a package and the texture of a mark code coverage region; and generating an anti-counterfeiting mark according to the mark code and the texture of the mark code coverage region. According to the technical scheme provided by the embodiment, the method can effectively prevent others from obtaining the information of the product in a simple mode of copying the mark code.
Owner:成都零壹矩阵科技有限公司
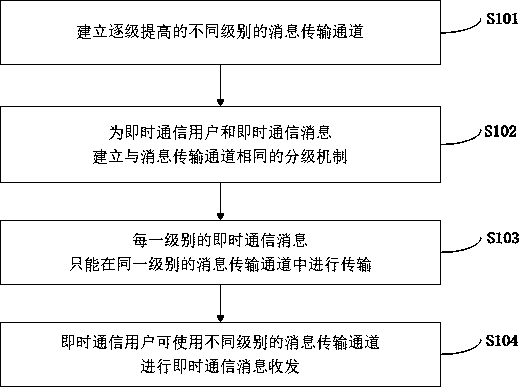
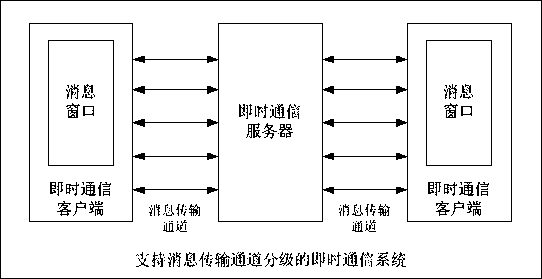
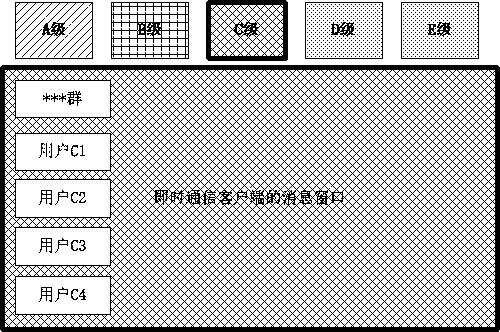
Instant messaging method and instant messaging system supporting message transmission channel classification
ActiveCN109617790AAvoid sending and receivingPrevent gettingSpecial service provision for substationTransmission monitoringCommunications systemTransmission channel
The invention discloses an instant messaging method supporting message transmission classification. The method comprises the following steps: establishing message transmission channels with differentlevels, wherein the message transmission channels are improved step by step; establishing a classification mechanism same as the message transmission channel for the instant messaging user and the instant messaging information, wherein the instant messaging information at each level can be only transmitted in the message transmission channel at the same level, and the instant messaging user can perform instant messaging information transceiving by using the message transmission channel at different levels. The invention further discloses an instant messaging system supporting the message transmission channel classification. Through the method disclosed by the invention, the security of the instant messaging is greatly improved when the instant message interaction flexibility is guaranteed,and the intended or unmeant information leakage is prevented.
Owner:BEIJING VRV SOFTWARE CO LTD
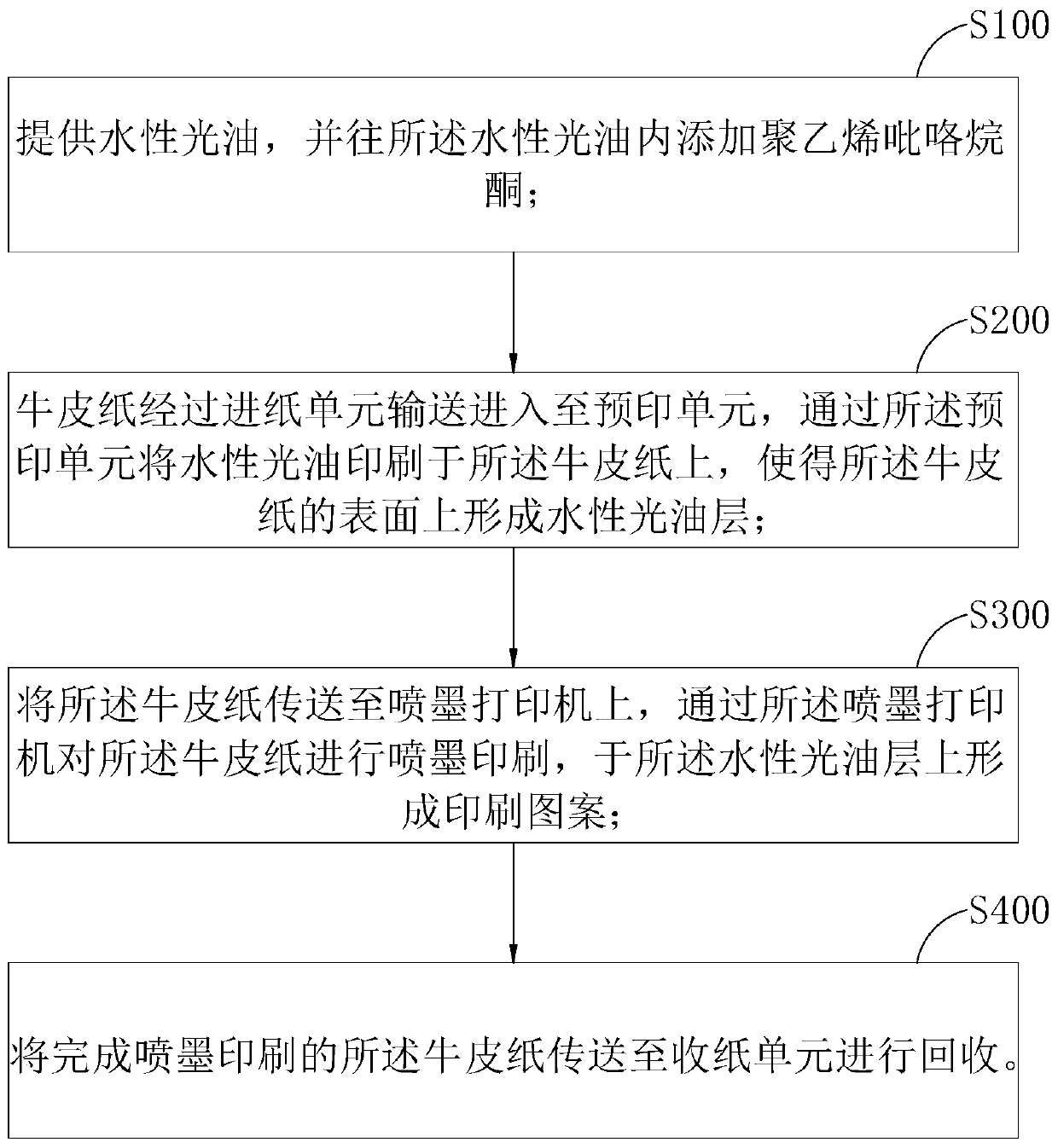
Kraft paper natural color high-definition color saturation printing method
ActiveCN110978836ALess waterproofImprove surface porosityDuplicating/marking methodsWater basedComputer printing
The invention belongs to the technical field of ink jet printing, and particularly relates to a kraft paper natural color high-definition color saturation printing method. The method comprises the following steps that S100, a water base vanishing is provided, and polyvinylpyrrolidone is added to the water base vanishing; S200, kraft paper is conveyed into a pre-printing unit passing through a paper feeding unit, the water base vanishing is printed on the kraft paper through the pre-printing unit, so that a water base vanishing layer is formed on the surface of the kraft paper; S300, the kraftpaper is conveyed to an ink-jet printer, the kraft paper is subjected to ink-jet printing through the ink-jet printer, and a printing pattern is formed on the water base vanishing layer; and S400, thekraft paper which is subjected to the ink-jet printing is conveyed to a paper collecting unit for recycling. According to the method, the high optical density and the color saturation of the ink printing can be enhanced, and the printing surface is smoother; secondly, the early-stage investment is less, and the later maintenance cost is low; in addition, and the water base vanishing layer has thecapability of increasing the waterproof capability of the kraft paper.
Owner:苏州美盈森环保科技有限公司
Cryptographic key generation and distribution method and system based on Diameter server
InactiveCN101197661ADistribution impactAvoiding Domino Effect ProblemsKey distribution for secure communicationWireless network protocolsCryptographic key generationDistribution method
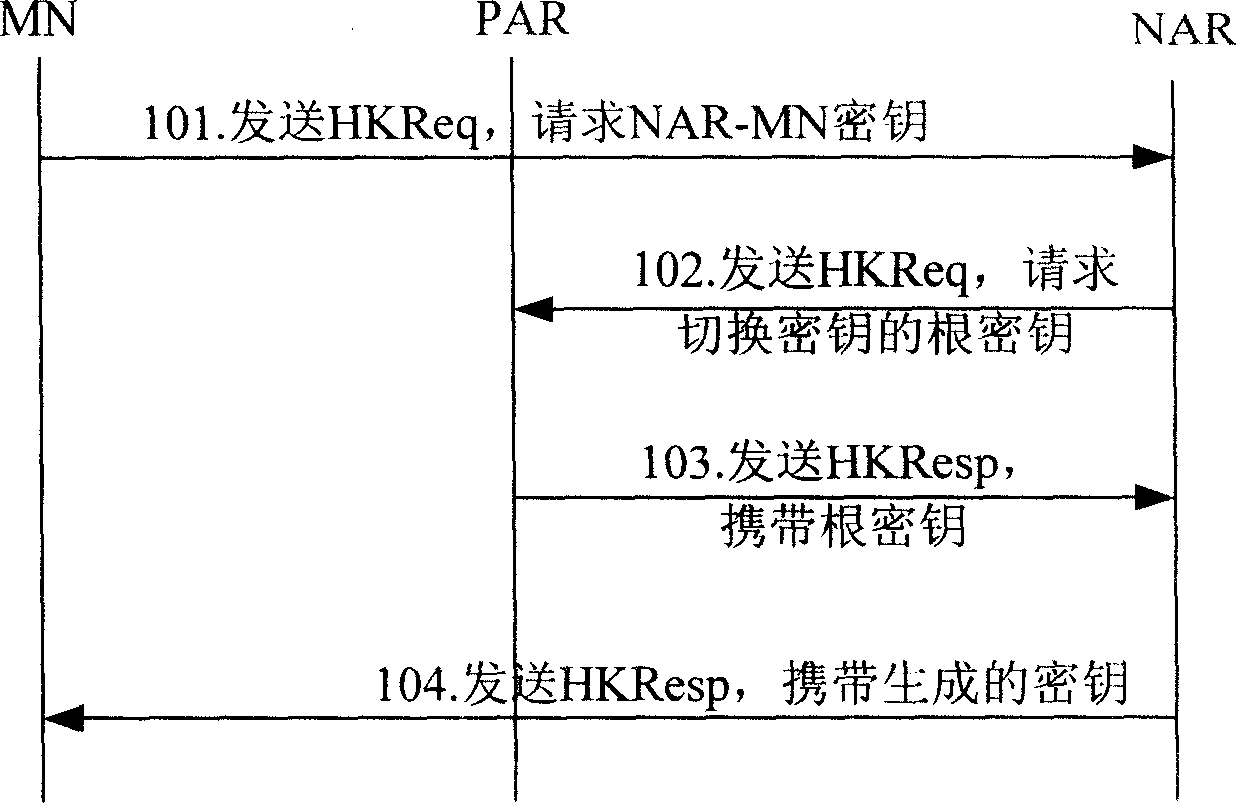
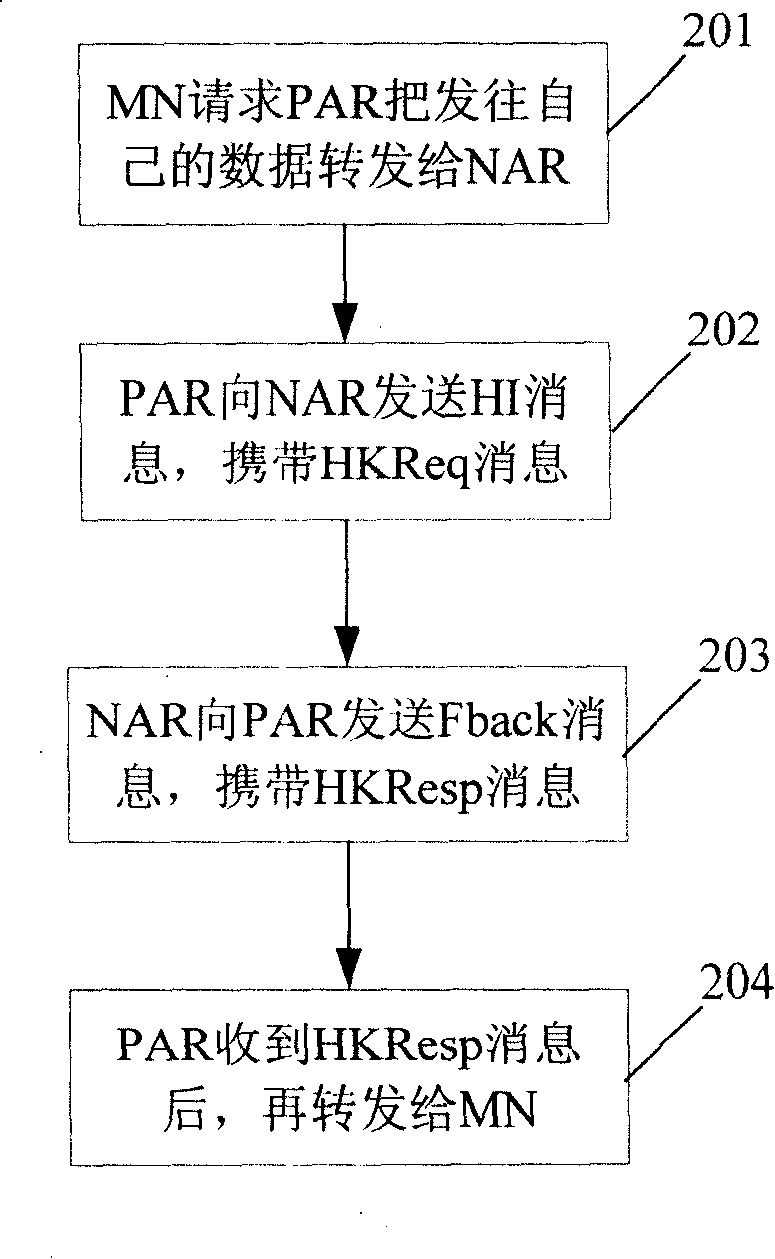
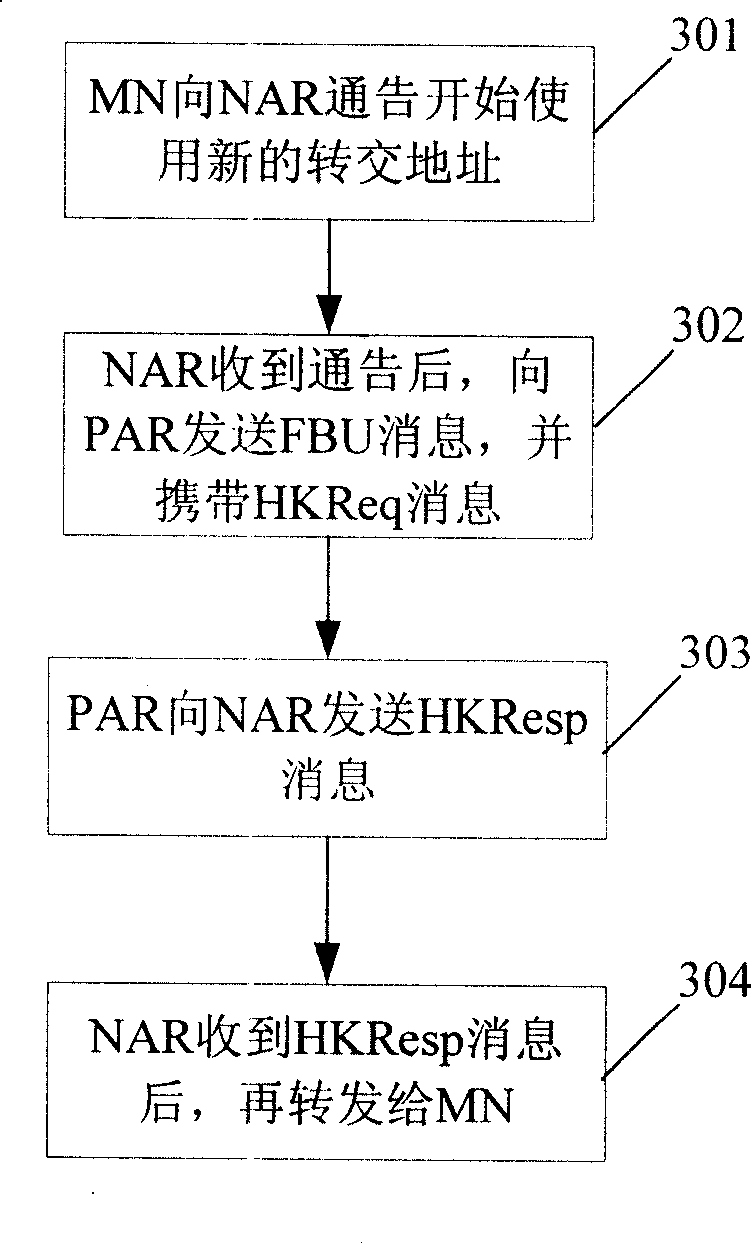
The invention provides a key generating and distributing method based on a Diameter server and a system, belonging to the mobile communication filed. In order to solve the problems of the prior art of the unsafe distribution of the key of a movable node and the high fee, the invention provides a key generating and distributing method based on a Diameter server. The method comprises the following steps that: an MN sends a mark of an NAR to a PAR; after receiving the mark, the PAR sends the mark of the NAR and a mark of the MN to the Diameter server; after the Diameter receives the marks, a uniform random number is firstly generated and a share key is generated according to the uniform random number; the Diameter server sends the share key to the NAR and sends the uniform random number to the MN; after the MN receives the uniform random number, a share key is generated. The invention also provides a key generating and distributing system based on the Diameter server. The technical proposal adopted the invention avoids the domino effect and improves the security of the share key.
Owner:HUAWEI TECH CO LTD
Offline synchronous two-dimensional barcode anti-counterfeiting method, anti-counterfeiting verification method and anti-counterfeiting device
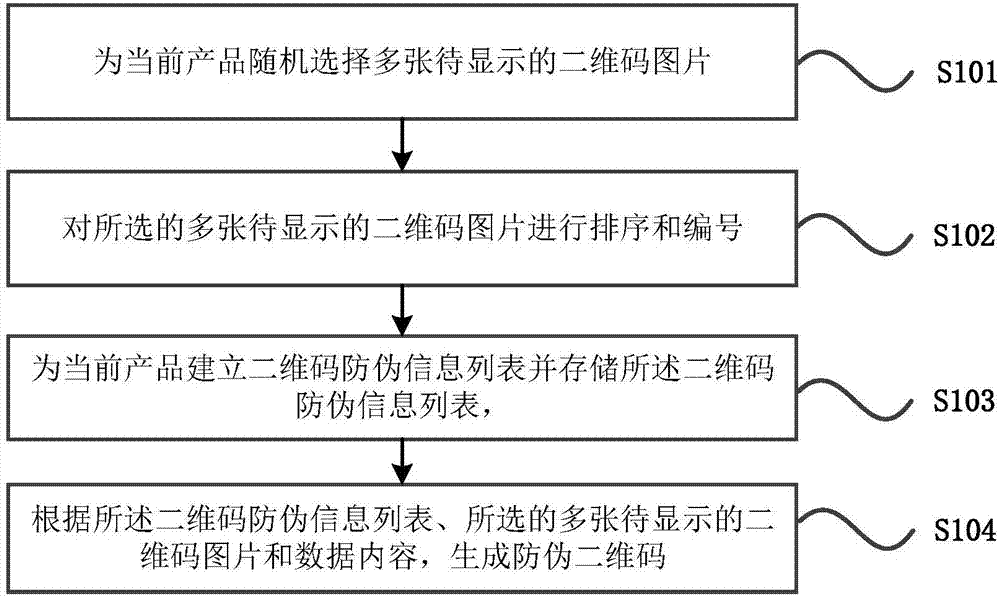
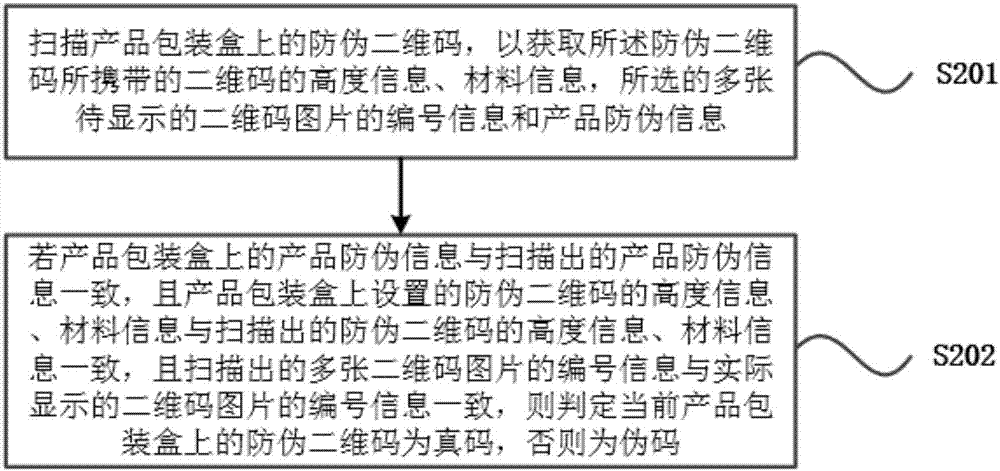
ActiveCN107316072AAvoid copying and counterfeitingIncrease the difficultyCo-operative working arrangementsCommerceData contentBarcode
The invention relates to an offline synchronous two-dimensional barcode anti-counterfeiting method, an anti-counterfeiting verification method and an anti-counterfeiting device. The anti-counterfeiting method comprises steps: multiple to-be-displayed two-dimensional barcode pictures are randomly selected for the current product; the selected multiple to-be-displayed two-dimensional barcode pictures are ranked and numbered; a two-dimensional barcode anti-counterfeiting information list is built for the current product, and the two-dimensional barcode anti-counterfeiting information list is stored, wherein the two-dimensional barcode anti-counterfeiting information list comprises the height information and the material information of a to-be-made two-dimensional barcode, and the number information and the product anti-counterfeiting information of the selected multiple to-be-displayed two-dimensional barcode pictures; and according to the two-dimensional barcode anti-counterfeiting information list, the multiple to-be-displayed two-dimensional barcode pictures and a data content, an anti-counterfeiting two-dimensional barcode is generated, wherein the data content is a pre-stored data content or a randomly-generated data content. Through the technical scheme of the invention, the problem that the two-dimensional barcode is easily counterfeited in the prior art can be solved.
Owner:彭戴予晗
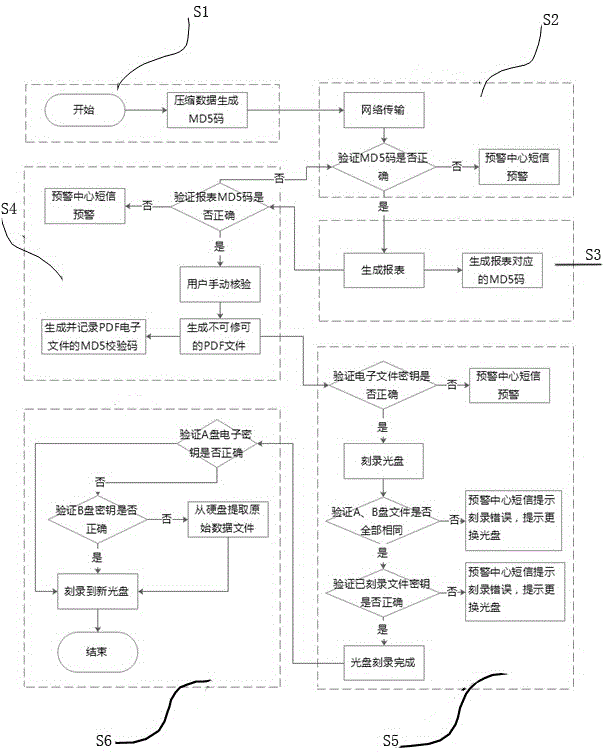
Bank business archive optical disk offline secure storage system and storage method
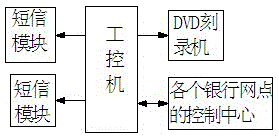
ActiveCN105096973ASmall footprintSimple structureOptical recording systemsComputer hardwareBanking industry
The invention discloses a bank business archive optical disk offline secure storage system and storage method. The bank business archive optical disk offline secure storage system comprises an industrial control computer, a short message module and a DVD carving machine. The industrial control computer is provided with an information communication end, a DVD carving control output end and an alarm signal output end. The information communication end of the industrial control computer is connected with the control center of each bank outlet so as to acquire intraday customer business information of each outlet. The signal input end of the short message module is connected with the alarm signal output end of the industrial control computer, and the signal output end is connected with the mobile phone of archive responsible personnel via the network. The signal input end of the DVD carving machine is connected with the DVD carving control output end of the industrial control computer. The bank business archive optical disk offline secure storage system is simple in structure and convenient to operate so that accurate electronic archive information can be generated. The bank business archive optical disk offline secure storage system is suitable for the archive system of all banks.
Owner:SHIJIAZHUANG HARMONY IS SCI & TECH CO LTD
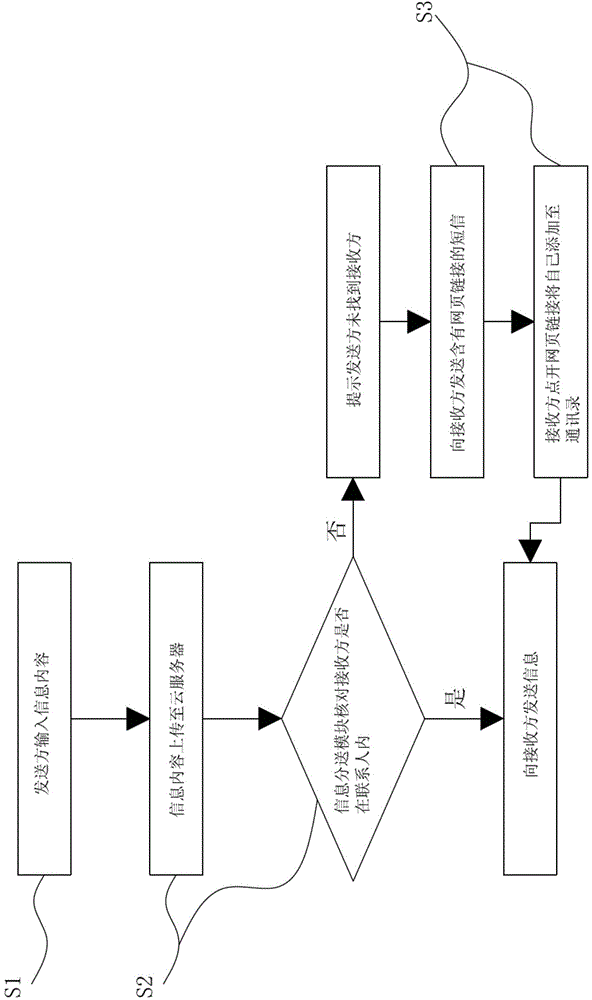
Instant communication method and platform for three-party information from teacher, student, and parents
ActiveCN104883295AImprove accuracy and safetyEfficient and smooth information communicationData switching networksAddress bookThree party
The invention discloses an instant communication method for three-party information from a teacher, a student, and parents. The method comprises: a sender inputs an information content containing a receiver name; the information content is uploaded to a cloud server and an information distribution module checks whether the receiver is in a contact list; if not, the cloud server sends a short message containing a web page link to the receiver; the receiver clicks on the web page link and enters an address book adding module of the could server; and the receiver clicks on ''adding based on receiving'' to add the receiver himself / herself to the address book and the cloud server sends the information content of the sender to the receiver continuously. In addition, the invention also discloses an instant communication platform for three-party information from a teacher, a student, and parents. With the method and platform, confidentiality of information communication is enhanced and the cloud server checks the receiver repeatedly, thereby improving safety and accuracy of the information communication. Meanwhile, information communication becomes efficient and smooth.
Owner:SUZHOU D&T EDUCATION TECH
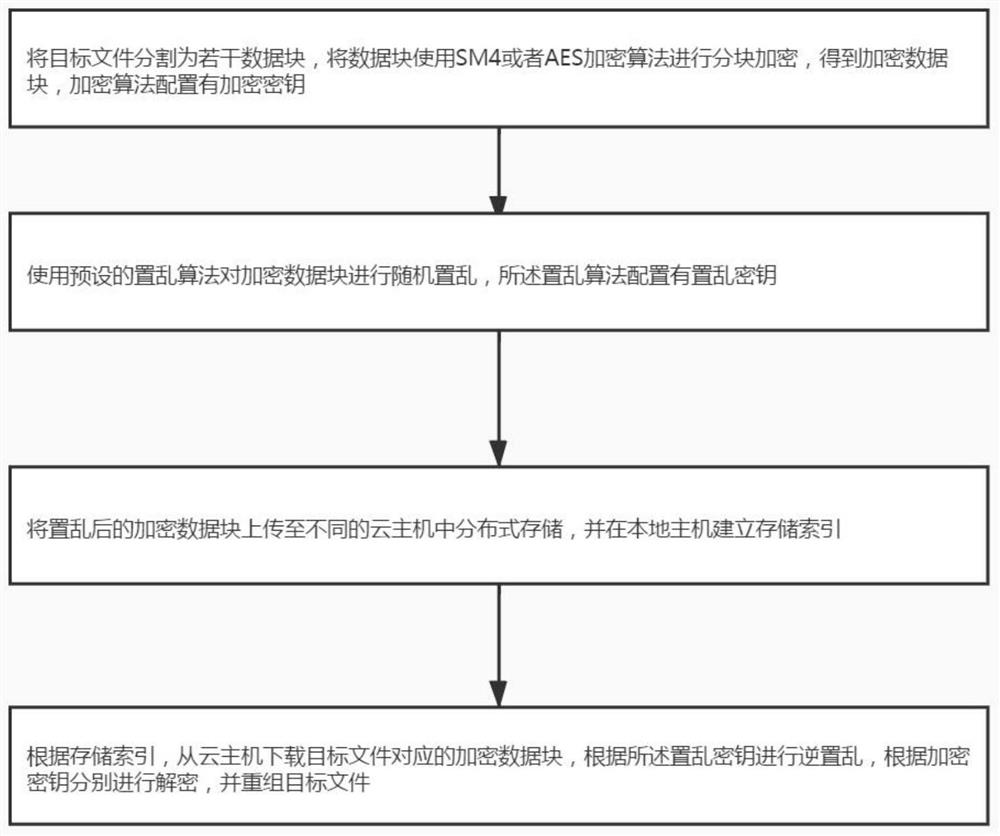
Distributed cloud security storage method and system and storage medium
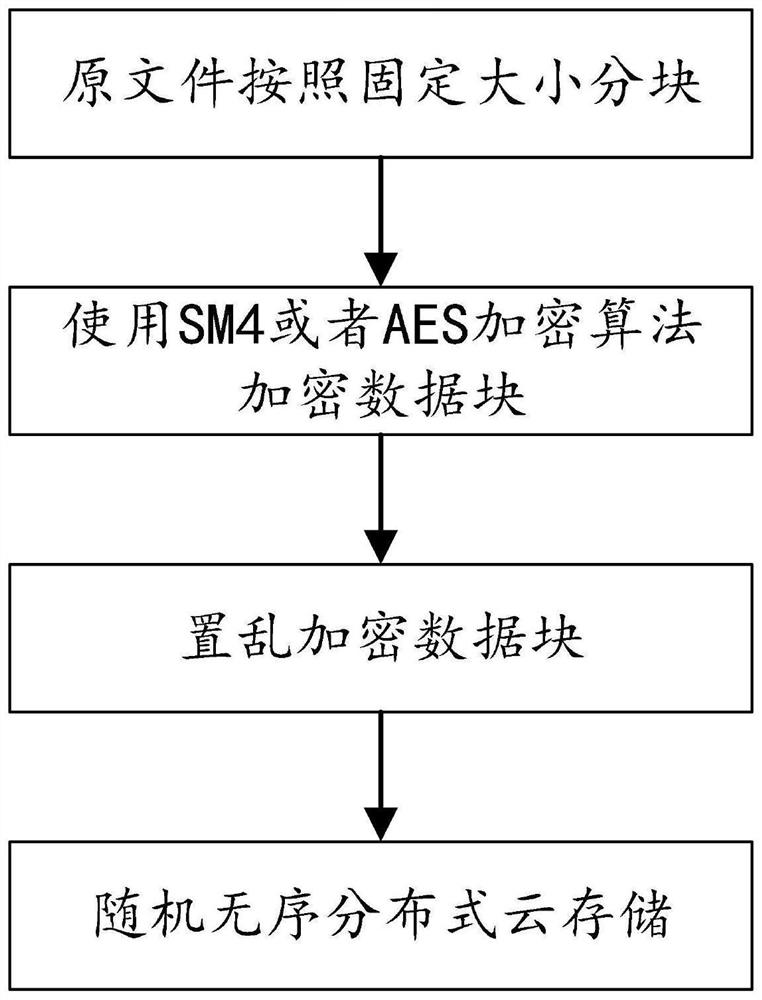
PendingCN113641648APrevent Data LeakagePrevent leakageDigital data protectionFile access structuresEngineeringDistributed computing
The invention discloses a distributed cloud security storage method and system and a storage medium, and the method comprises the steps: segmenting a target file into a plurality of data blocks, carrying out the block encryption of the data blocks through an SM4 or AES encryption algorithm, and obtaining encrypted data blocks; randomly scrambling the encrypted data block by using a preset scrambling algorithm; uploading the scrambled encrypted data blocks to different cloud hosts for distributed storage, and establishing a storage index in a local host; and according to the storage index, downloading the encrypted data block corresponding to the target file from the cloud host, performing inverse scrambling according to the scrambling key, performing decryption according to the encryption key, and recombining the target file. Block encryption and random scrambling of the target file are supported, distributed storage of a plurality of different cloud hosts at the cloud end is transmitted, an authorized user can open a system and download encrypted data blocks corresponding to the target file from the cloud hosts, the user is supported to browse and use the file without barriers, and the data leakage in the transmission process can be effectively avoided.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Method for robot preventing hacker authority management
The invention discloses a method for robot preventing hacker authority management. The method comprises following steps: extracting a motor control command contained in a remote connection request sent by another node of a network, outputting the motor control command contained in a remote connection request sent by another node of a network, and waiting for the motor to trigger the authenticity of the remote connection request sent by the another node of the network. The operation of the motor is controlled by the motor control command contained in the remote connection request sent by another node of the network. The information, pressing a button, is difficult for hackers to break. Therefore, by means of the method for robot preventing hacker authority management, the robot is made to effectively prevent hackers from obtaining management authority.
Owner:重庆友武科技有限公司
Android application protection method based on code sinking and residual code interpretation
ActiveCN108681457BImprove compatibilityExtension of timeDecompilation/disassemblyDigital data protectionVirtualizationAttack
Owner:NORTHWEST UNIV
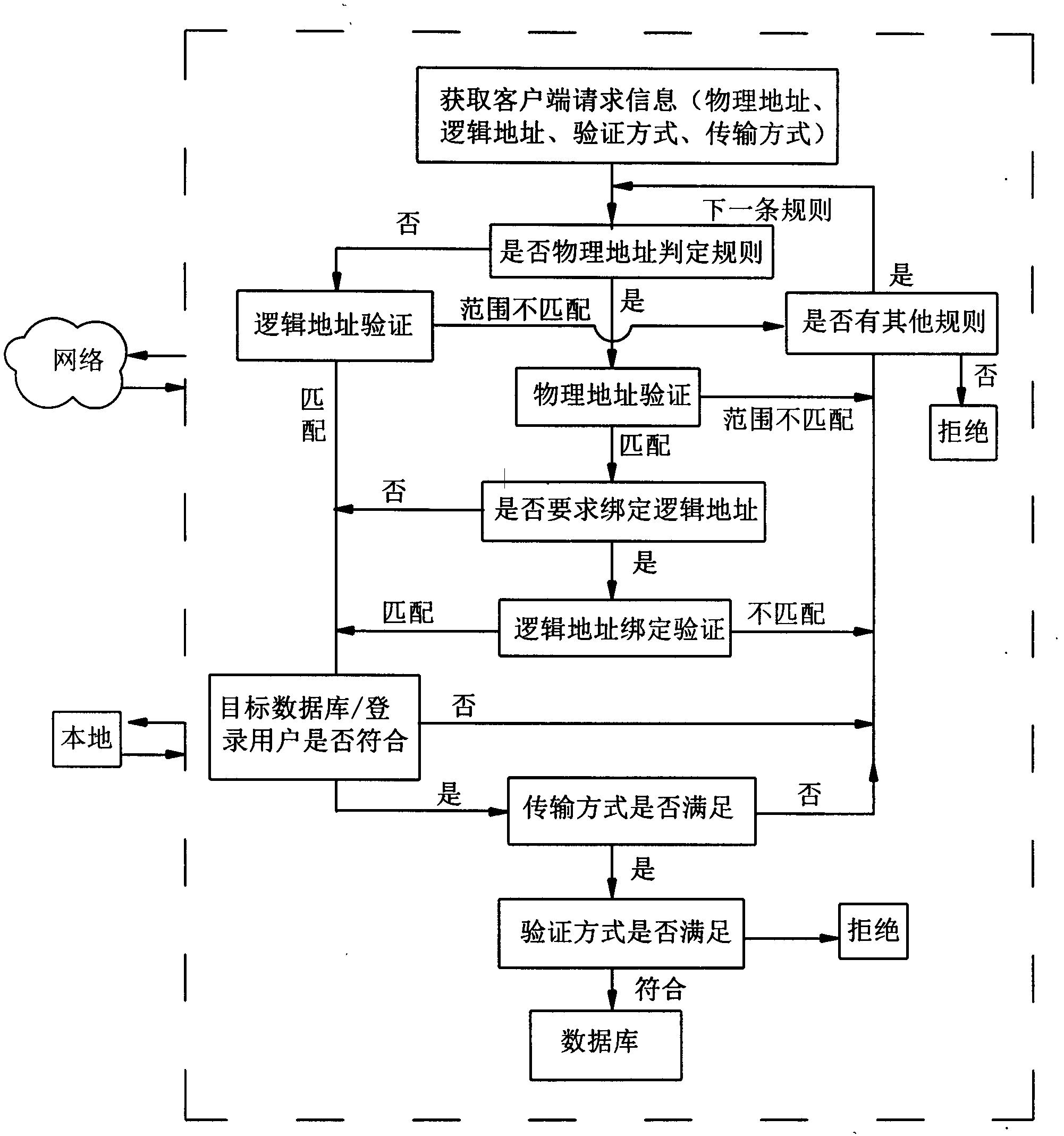
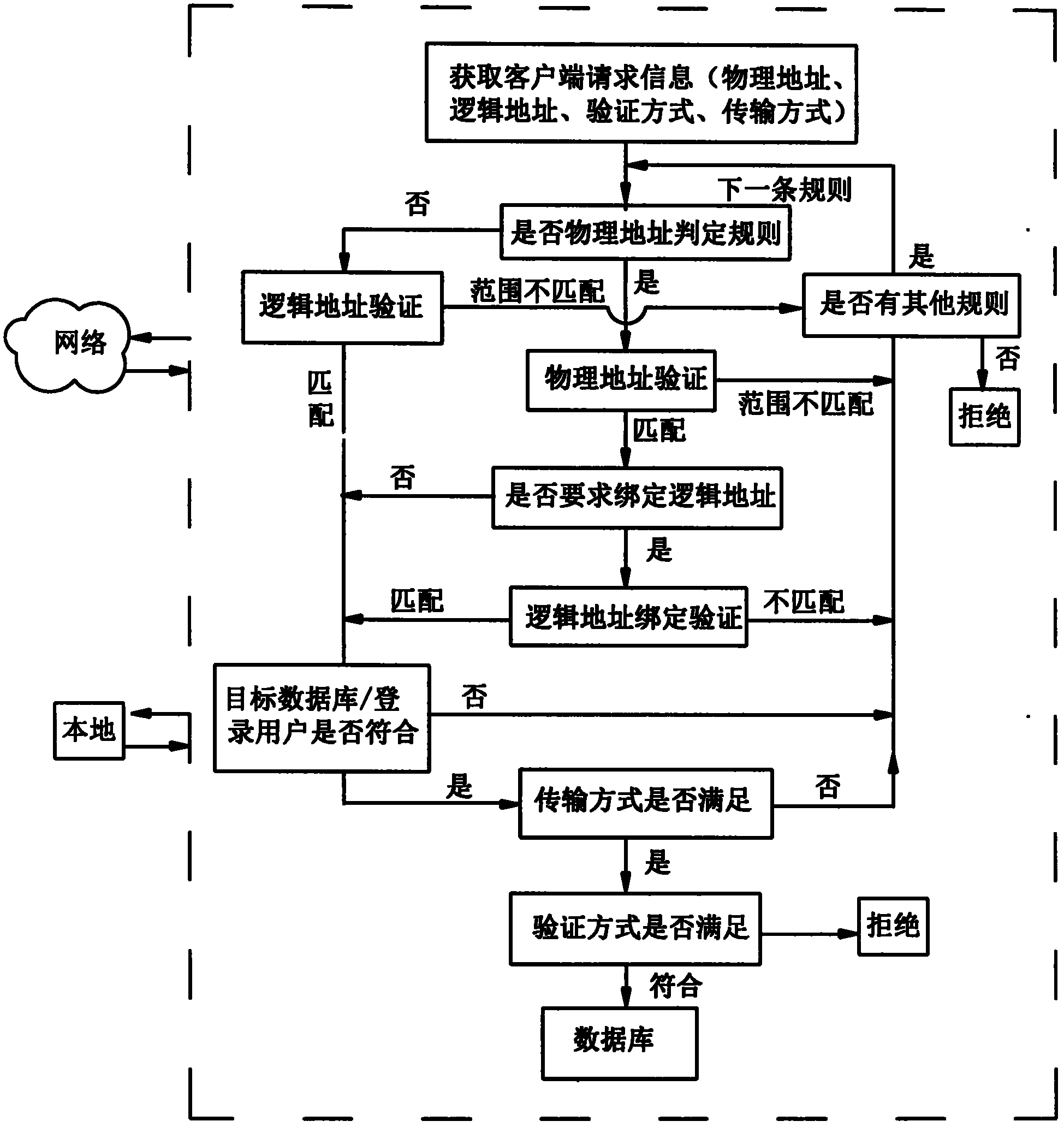
Database protection method
ActiveCN102508931APossibility of blocking leaksPrevent gettingDigital data protectionSpecial data processing applicationsPasswordProtection layer
The invention provides a database protection method. In the method, a verification mechanism and multiple rules form a protection layer; each rule includes a verification definition allowing or rejecting database access; and after receiving a user access request and before verifying the user / password in the database, the protection layer verifies the connection request and judges whether to allowor reject the request according to all rule definitions. Through the method, the protected database is only accessible to the network domain in the designated range, and the possibility of data leakage can be effectively avoided even in the case of user / password leakage in the database. The client connection is necessary to conform to the designated transmission and verification mode; and the method can forcibly requires encryption of the transmission process and adoption of a stricter verification mode so as to prevent acquisition of password and data through network peep.
Owner:HIGHGO SOFTWARE
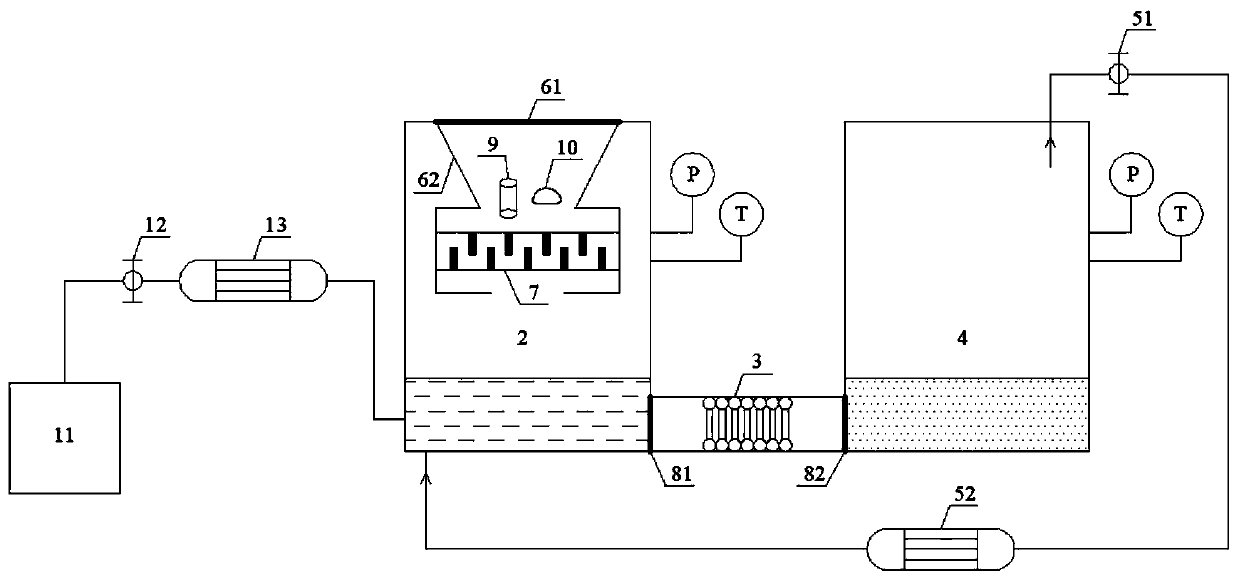
Device for electrified crushing and electrolyte recovery of waste power lithium battery
InactiveCN111416169ATo preventAvoid decompositionWaste accumulators reclaimingBattery recyclingToxic gasElectrolytic agent
The invention discloses a device for electrified crushing and electrolyte recovery of a waste power lithium battery. The device comprises a gas inlet system, a fixed reaction kettle, a filtering device, an electrolyte collecting kettle and a gas outlet system which are connected in sequence; an outlet of the gas outlet system is connected to the fixed reaction kettle in a returning manner, a feeding device is arranged at the top in the fixed reaction kettle, a crushing device is connected below the feeding device, and opening and closing devices are arranged between the fixed reaction kettle and the filtering device and between the filtering device and the electrolyte collecting kettle. The device disclosed by the invention aims at recycling the electrolyte in the waste power lithium battery while breaking and disassembling the waste power lithium battery in an electrified manner; on the one hand, the waste power lithium battery does not need to be subjected to discharge pretreatment;on the other hand, the electrolyte is effectively recycled, the emission of toxic gas is reduced, the whole device and technological process are simple, large-scale production is easy, the recycled electrolyte can be reused, the electrolyte recycling efficiency is greatly improved, and resource and high-value utilization of waste is achieved.
Owner:CINF ENG CO LTD +1
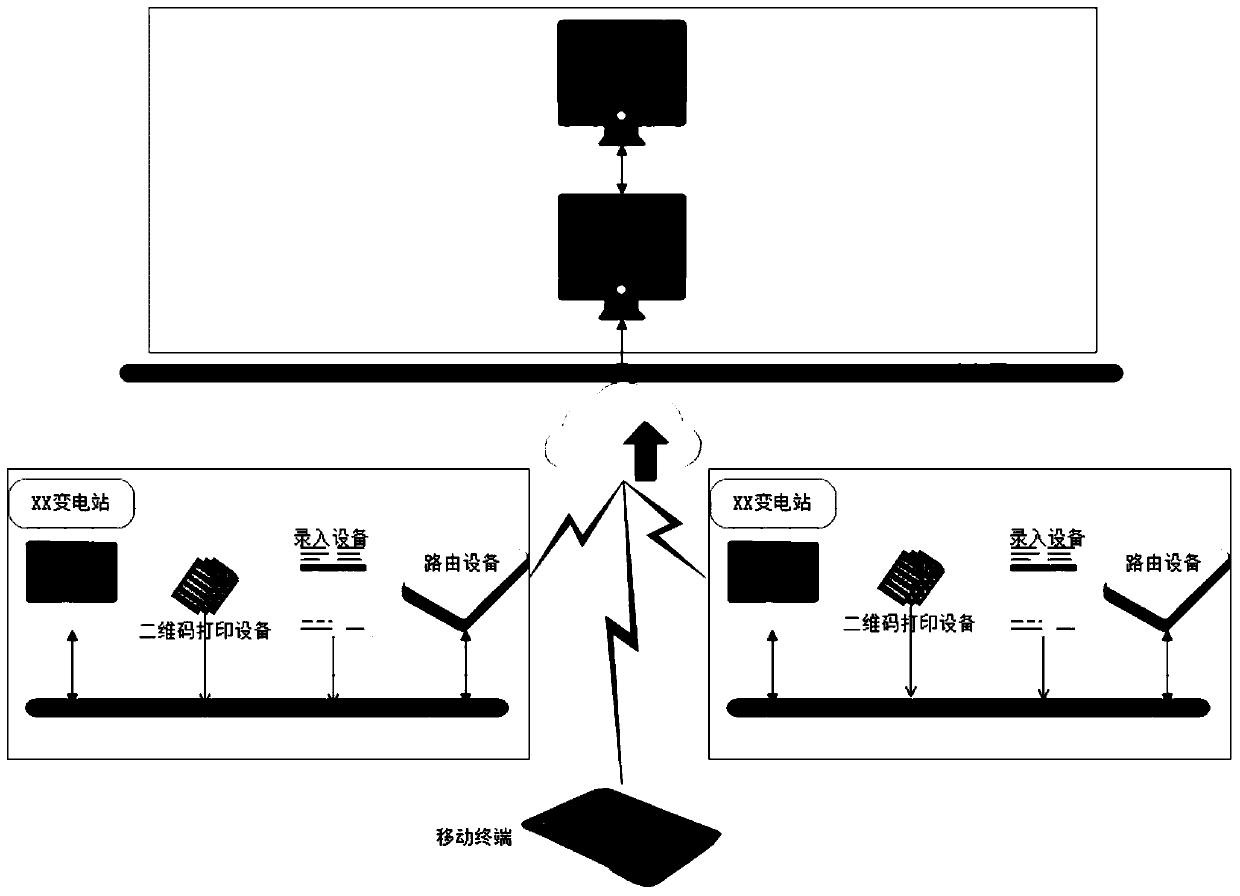
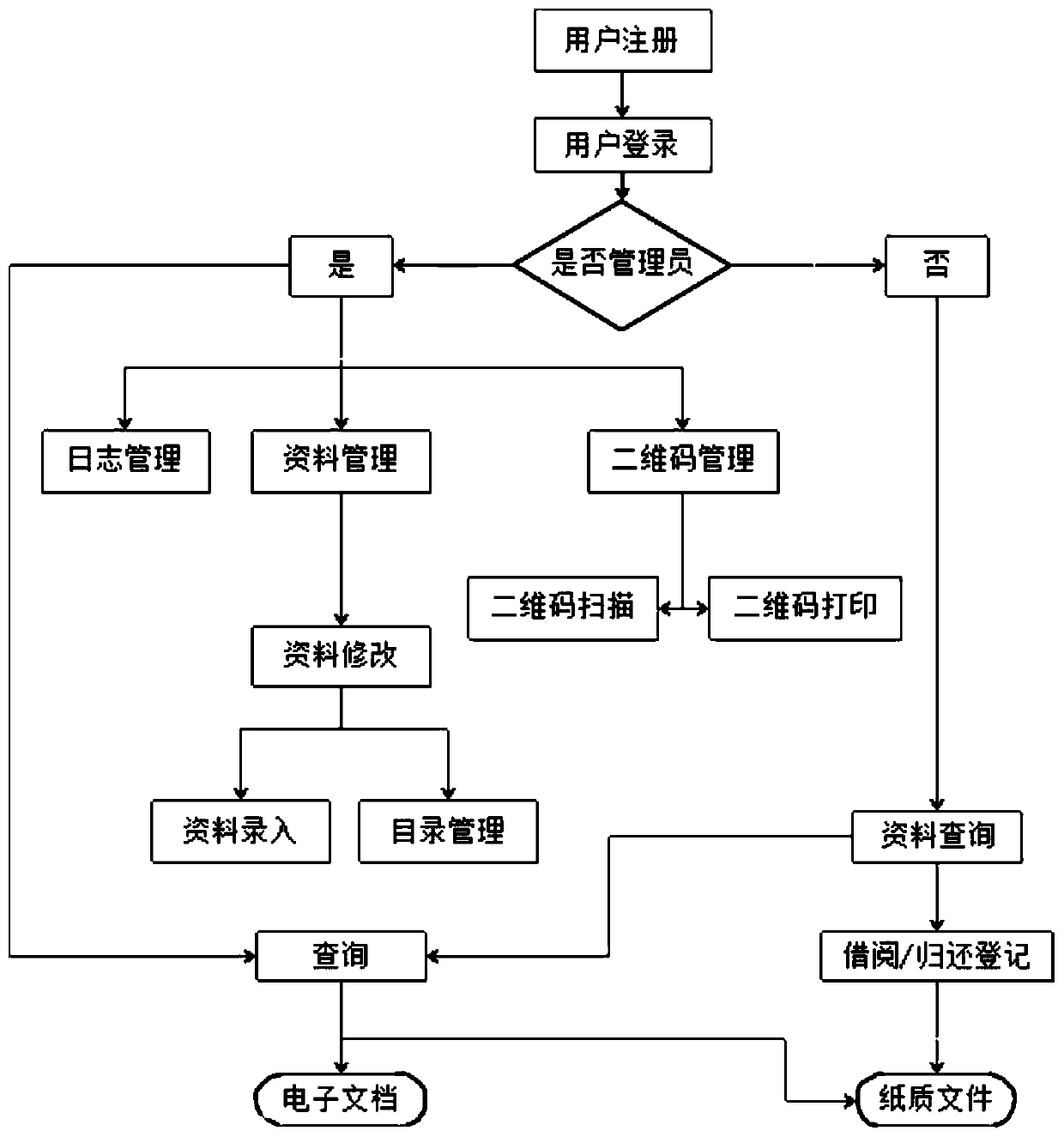
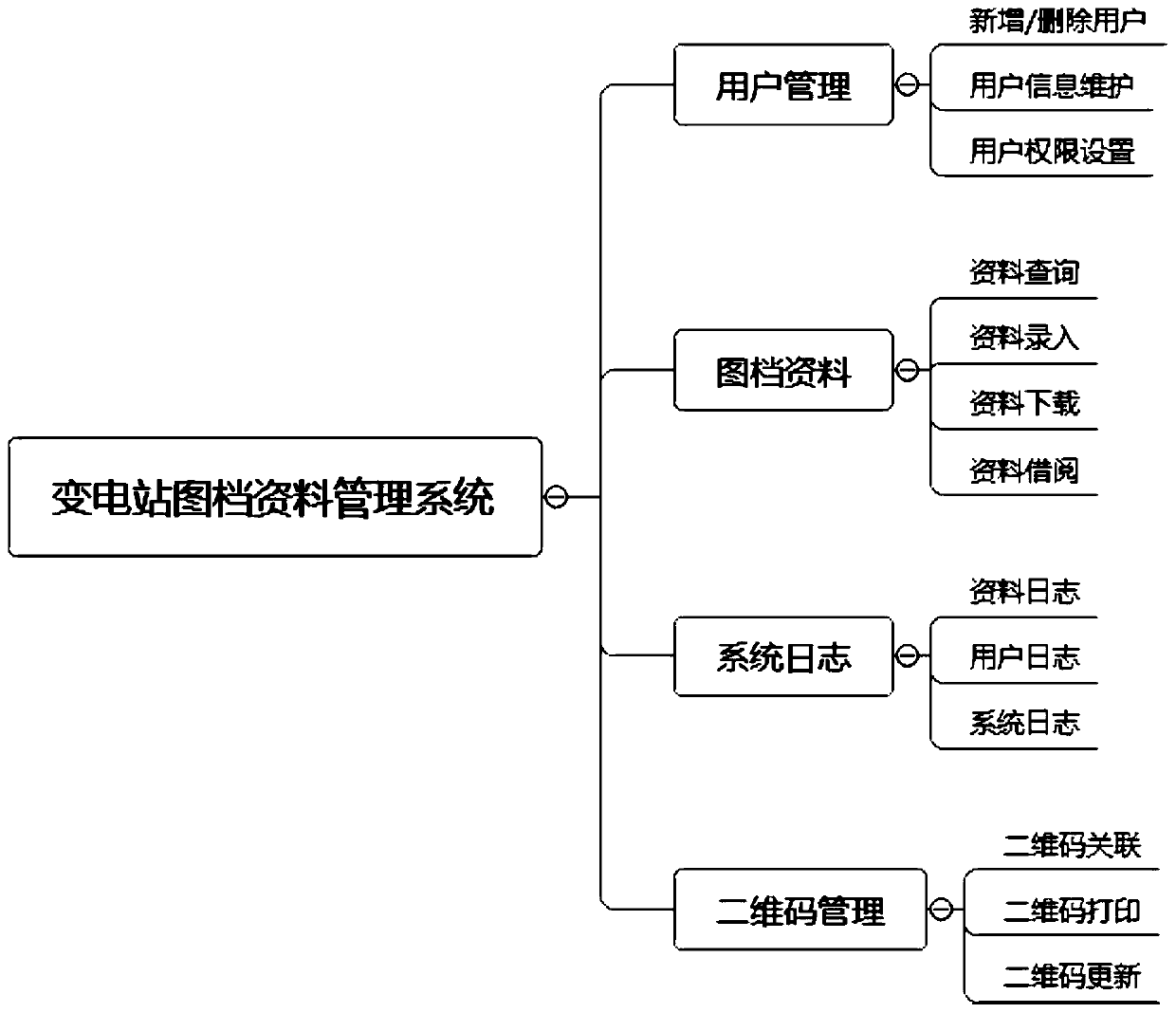
Transformer substation drawing and document data intelligent management method based on intelligent technology application
PendingCN110990620AExact searchImprove retrieval efficiencyData processing applicationsStill image data indexingData informationSoftware engineering
The invention discloses a transformer substation drawing and document data intelligent management method based on intelligent technology application, and aims to provide the transformer substation drawing and document data intelligent management method based on the intelligent technology application such that the management efficiency can be improved. The method comprises the following steps: 1) designing a system; 2) submitting and correlating drawing document data information, constructing a drawing document data database, and designing keywords for retrieval and statistics; 3) making drawing and document data two-dimensional code labels corresponding to an equipment object and a working object; 4) analyzing drawing file data information; and 5) completing application and deployment. Management is convenient, and the workload of an administrator is reduced. The administrator does not need to establish a paper document for each drawing and does not need to worry about the arrangementof the paper documents. The version management function enables a user to easily obtain the latest version and historical version file resources, the trouble of manually managing multiple versions ofthe file resources is omitted, and the method is convenient and practical.
Owner:云南电网有限责任公司保山供电局
Continuous query oriented location anonymizing method applicable to location service system
InactiveCN102892073BFix the leakSufficiently diverseTransmissionLocation information based servicePersonalizationPrivacy protection
The invention discloses a continuous query oriented location anonymizing method applicable to a location service system, belonging to the technical field of privacy protection of location service, which comprises the steps of: proposing an anonymizing request by a mobile user; anonymizing the request by an anonymizing module in an anonymizing server, and sending the anonymized request to a location server; processing the request by the location server, integrating query results and sending to the anonymizing server; integrating and filtering received candidate results by a query processing module of the anonymizing server, and sending a precise result to the corresponding mobile user. According to the anonymizing method, personalized customization of privacy protection parameters of the user is permitted. The anonymizing module operates in the anonymizing server, and is used for calculating by the anonymizing method provided by the invention depending on the privacy protection parameters of the mobile user, to guarantee that all anonymizing regions of the mobile user include an identical number of queries in a query valid period and the anonymizing space is shared by the mobile users in the space; and the query privacy of the mobile user who proposes a continuous query in the location service is effectively protected.
Owner:BEIHANG UNIV
Dyeing device with drying function for cotton yarn processing
PendingCN113322609AWith drying functionEasy to placeTextile treatment machine arrangementsTextile treatment cleaning apparatusYarnPolymer science
The invention discloses a dyeing device with a drying function for cotton yarn processing. The dyeing device comprises a box body, a stirring device, an electric telescopic rod and an air inlet pipe; supporting legs are mounted on the left and right sides of the bottom of the lower end of the box body; the stirring device is mounted in the middle of the bottom of the box body and extends into a dyeing cavity; the electric telescopic rod is mounted at the upper end of the interior of the drying cavity; a placing frame is arranged on two clamping blocks; a fan is arranged on the rear side of the interior of the air inlet pipe; and a plurality of air outlets are formed in a vertical pipe. The dyeing device with the drying function for cotton yarn processing is provided with a partition plate, a through hole, the dyeing cavity and a drying cavity; the box body is divided into the dyeing cavity and the drying cavity through the partition plate, so that the device can complete dyeing and drying in the box body, and the processing time is saved; and through the through hole, cotton yarn can be conveniently placed in the dyeing cavity for dyeing, then the cotton yarn is conveniently taken out of the dyeing cavity during drying, and dye in the dyeing cavity is not easily brought to the outside, so that the practicability of the device is improved.
Owner:宿迁至诚纺织品股份有限公司
Child resistant visible blister end cap
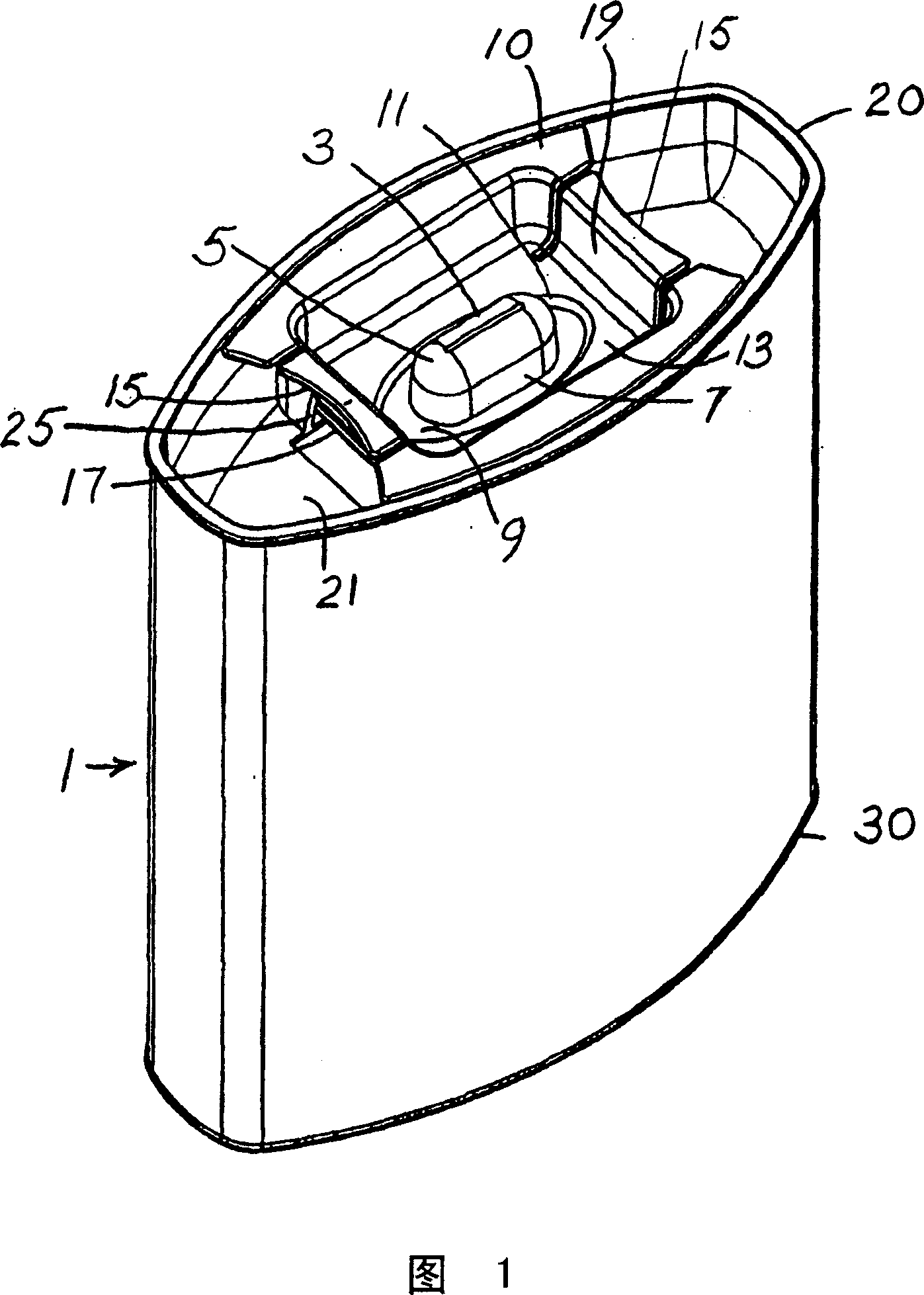
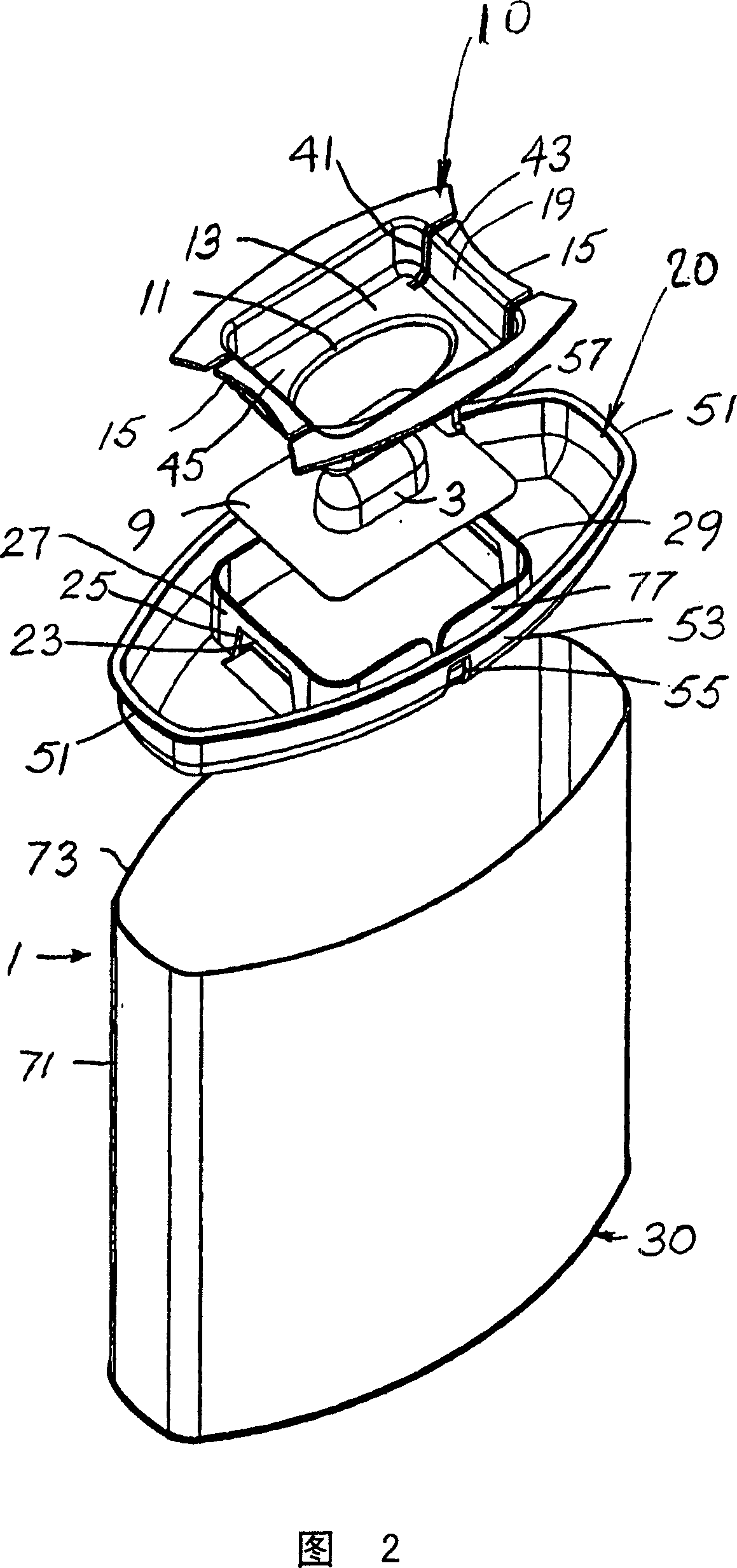
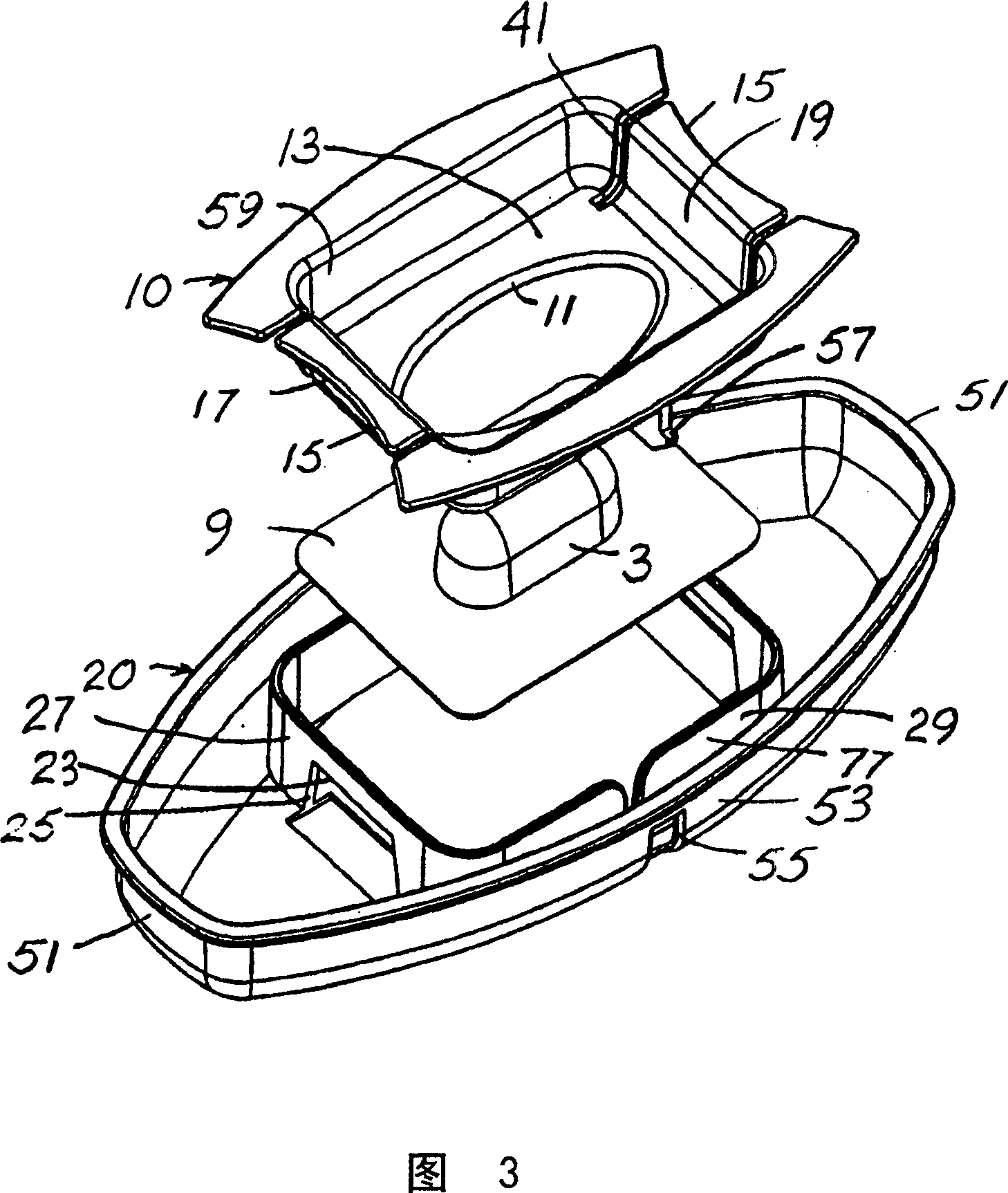
A product is packaged in a blister, which is displayed and securely held in a child resistant gripper (10) on the top of a package. The blister bubble (7) is made of a strong plastic material, which is sufficiently rigid to hold its shape and which is difficult to tear or puncture without a sharp tool. The individual blister (3) is displayed with the blister exposed through an opening (11) of a holder (10). A base flange (9) of the blister is secured under the frame (13) around the opening (11) of the holder (10). A backing for the blister, through which the medication (5) is conventionally removed, is held tightly against the bottom (21) of the cap (20). Precise manipulations are required to remove the blister package. The blister package (3) is removed from between the holder (10) and the end cap (20) before the backing on the blister is opened.
Owner:MEADWESTVACO CORP
Shoe sole gluing device
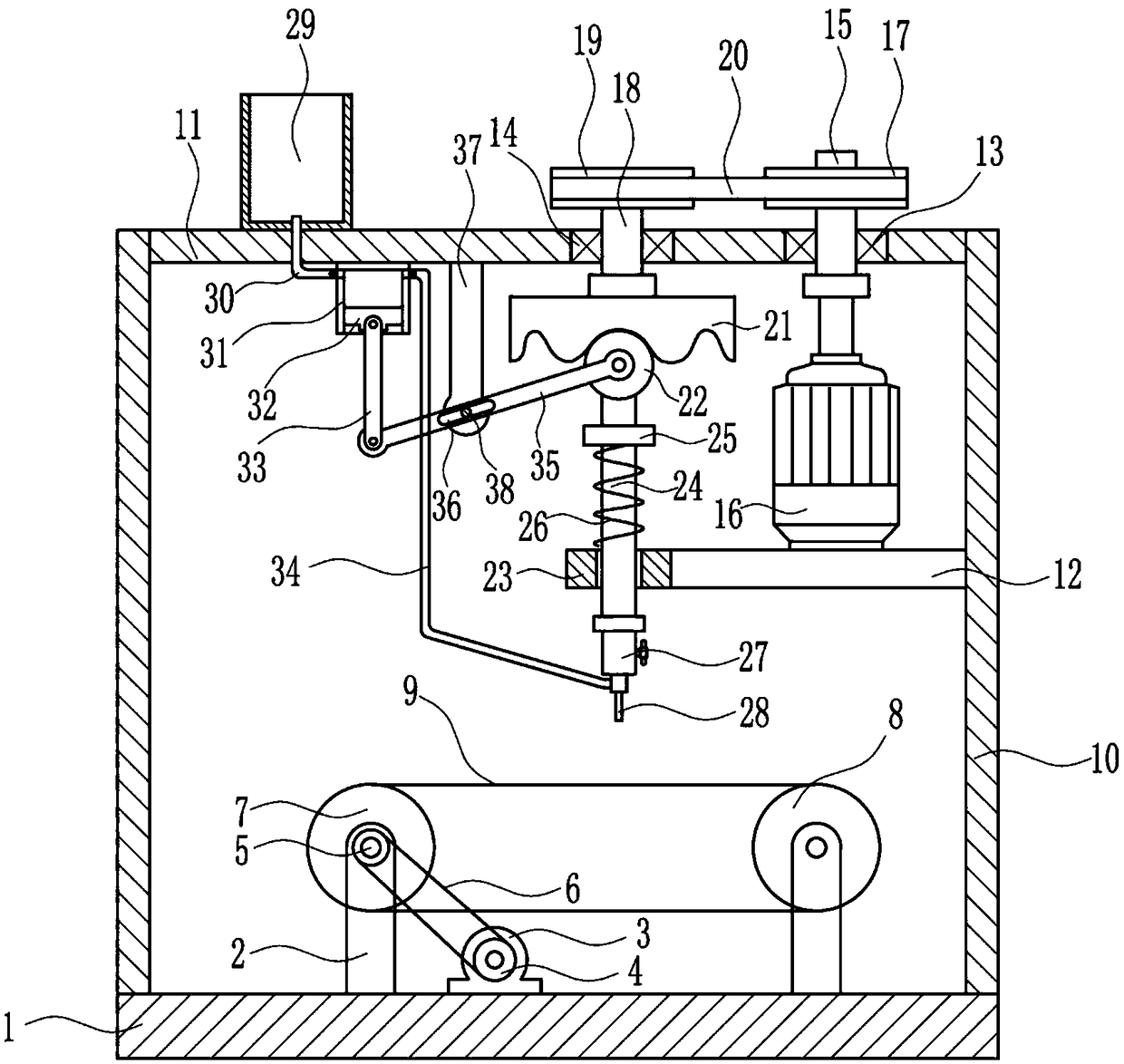
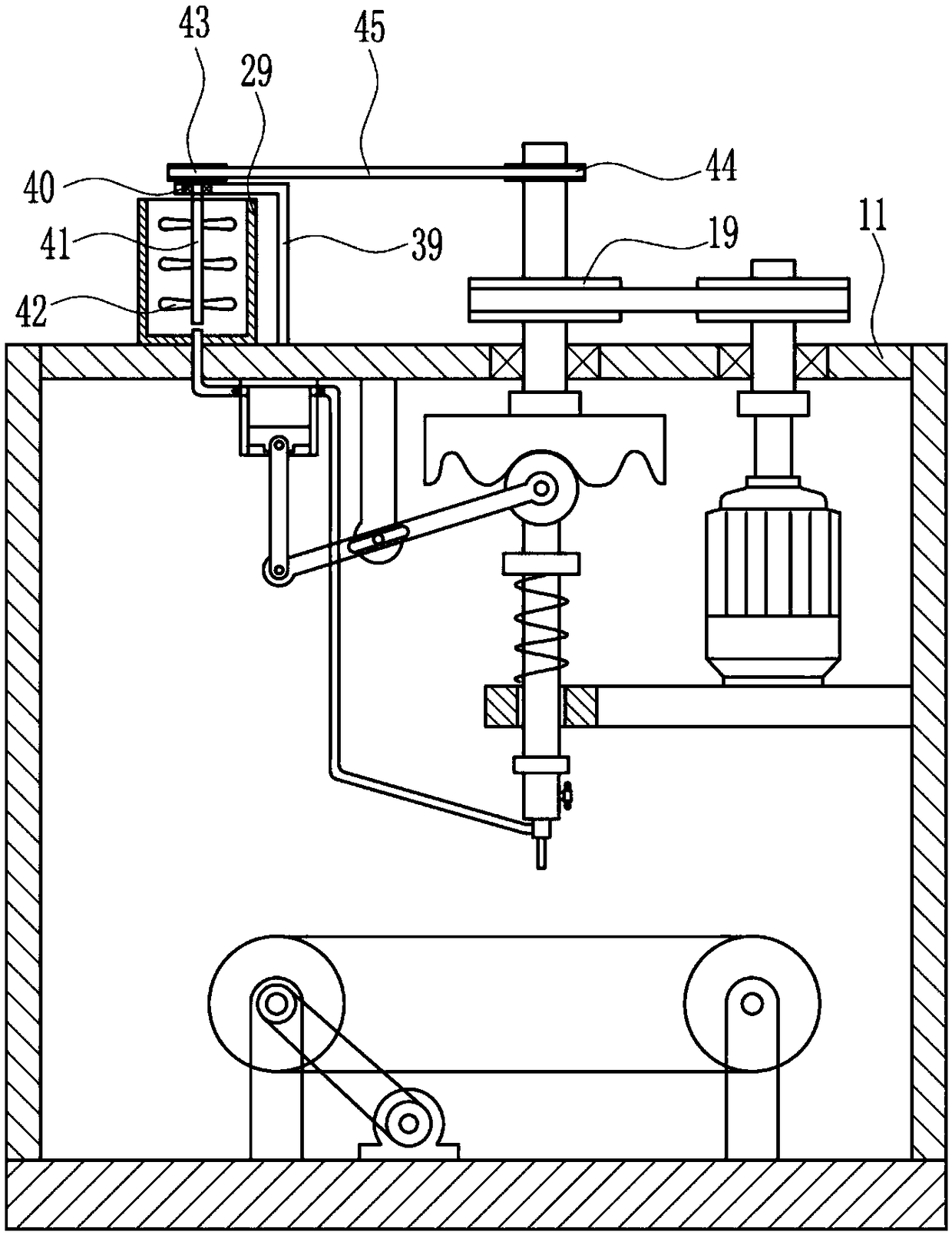
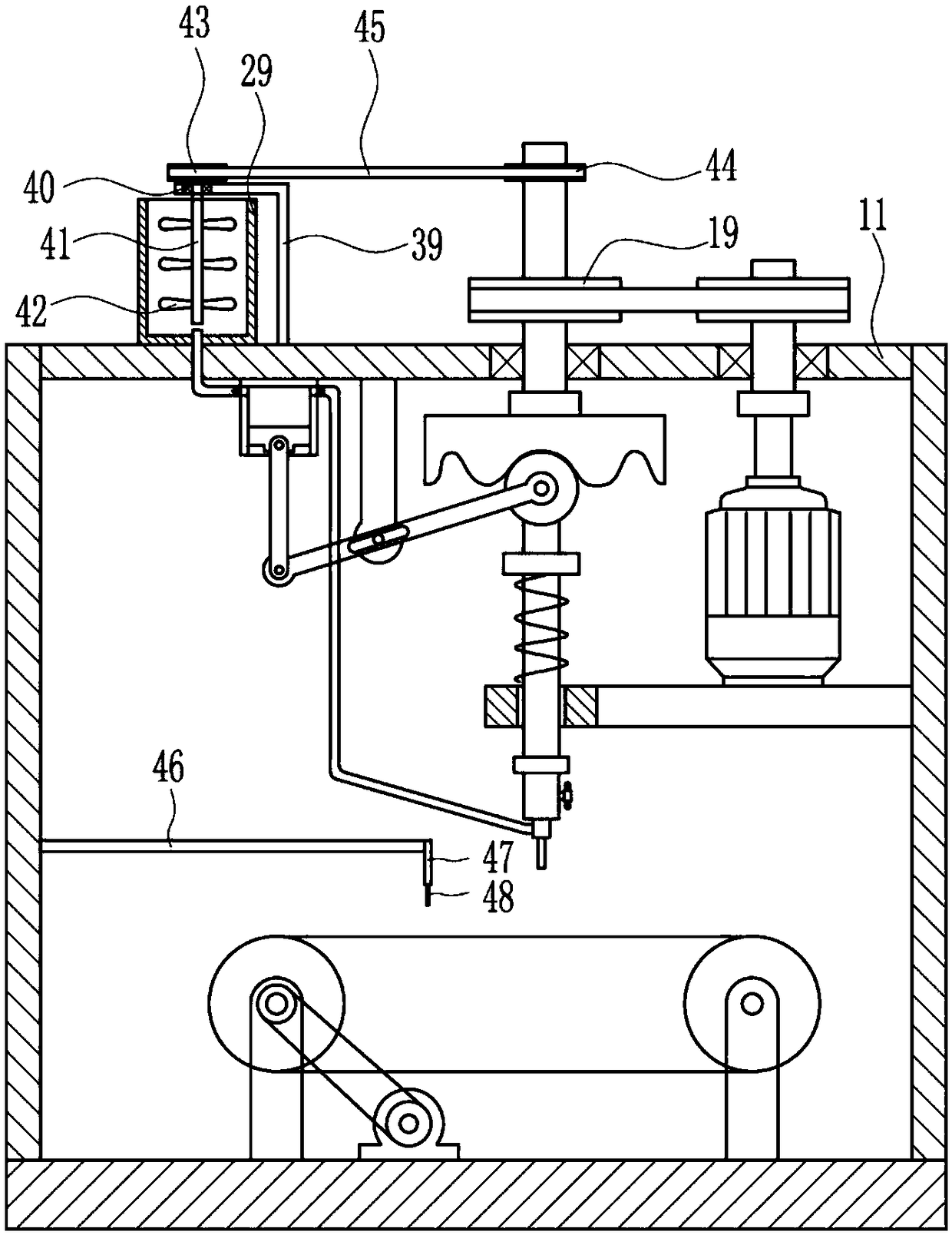
The invention relates to a gluing device, in particular to a shoe sole gluing device. The technical problem to be solved is how to provide a shoe sole gluing device which is high in efficiency and canprotect both hands. The technical scheme of the invention is that the shoe sole gluing device includes a base plate, supporting rods, a first motor, a first belt pulley, a second belt pulley, a firstflat belt and a first large belt pulley and the like. The top of the base plate is provided with the two supporting rods, the two supporting rods are arranged at a certain interval, the first motor is mounted at the middle of the top of the base plate, an output shaft of the first motor is connected with the first belt pulley through a coupling, the upper portion of the first bracket on the leftside is connected with the second belt pulley, and the first flat belt is connected between the second belt pulley and the first belt pulley. A conveying belt of the shoe sole gluing device drives shoes to move, and a piston moves up and down to drive glue to be sprayed out of a spray head, so that the glue is smeared on shoes, thereby improving gluing efficiency. Moreover, glue liquid on a shoe sole can be scraped more evenly through a soft scraping plate, and thus the glue is prevented from getting on your hands.
Owner:NANJING LISHUI HIGH-TECH VENTURE CAPITAL MANAGEMENT CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com