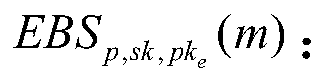Encrypted blind signature method based on quantum secret communication technology
A quantum secure communication and blind signature technology, which is applied in key distribution, can solve the problems of unproven actual security benefits, no unified industry standard, and large consumption of optical fiber resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
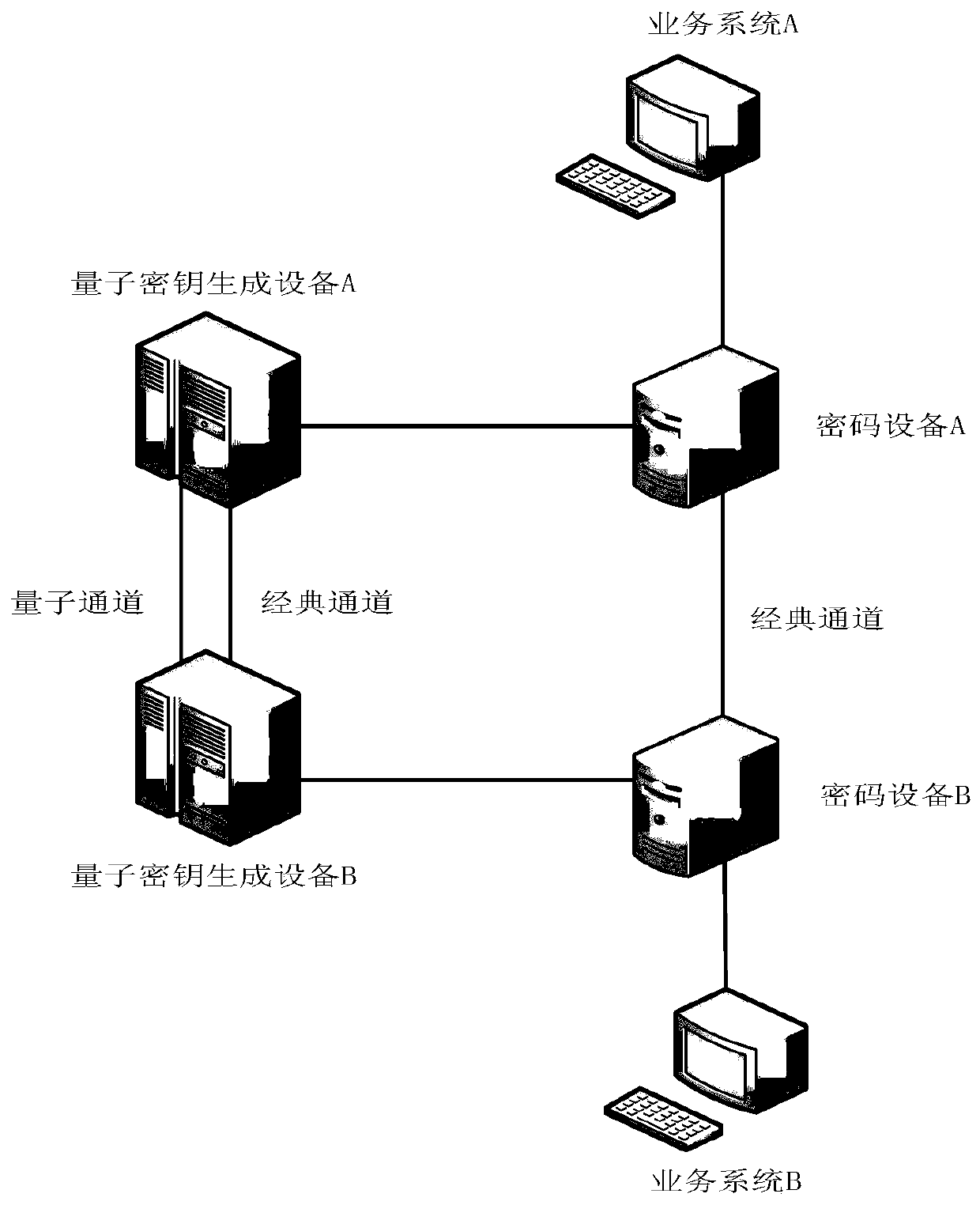
[0076] An encrypted blind signature method based on quantum secret communication technology, (1) select two algorithms of blind signature and linear encryption, (2) construct encrypted blind signature by blind signature and linear encryption algorithm; (3) confuse encrypted blind signature ; (4) The core parameters in the process of steps 1-3 are transmitted using quantum secure communication technology.
[0077] Discuss technical scheme of the present invention in detail below and verify
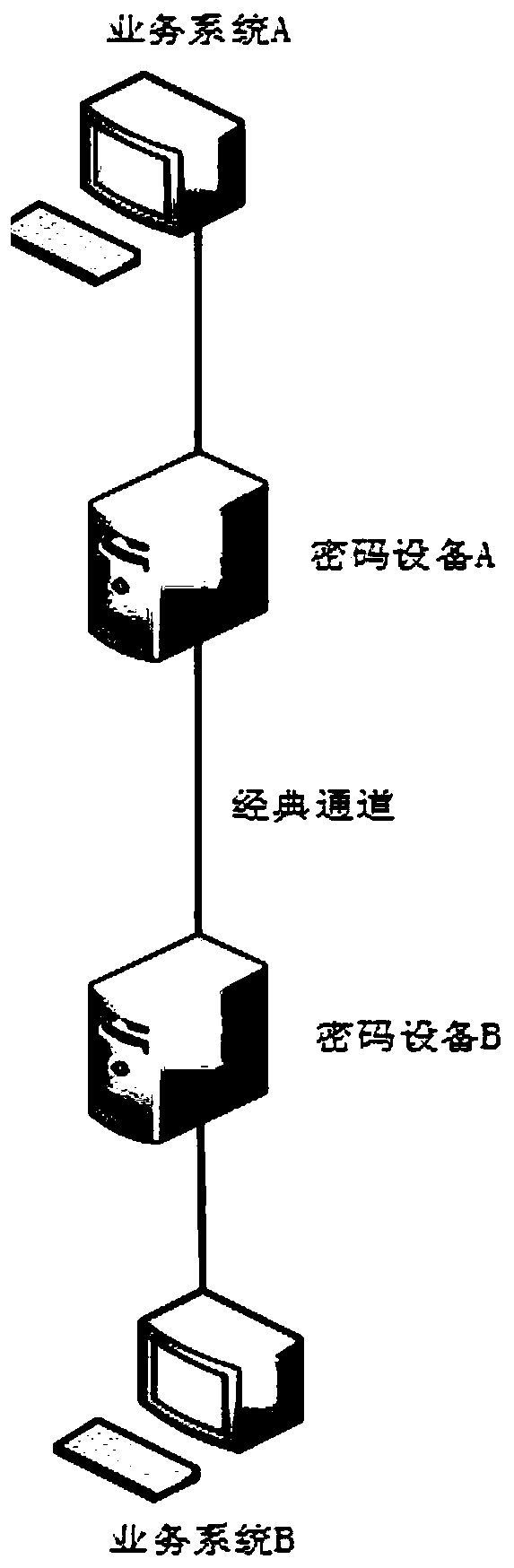
[0078] (1) Overall architecture deployment method
[0079] The main deployment methods of traditional cryptographic devices are point-to-point and point-to-multipoint, specifically as figure 1 shown. Key generation is generated by a random number generator, and the key is transmitted to the peer cryptographic device through a key transmission protocol such as Diffie-Hellman or a digital envelope to realize key sharing. The key agreement is directly performed between the encryption devic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com