Distributed cloud security storage method and system and storage medium
A secure storage and distributed technology, applied in the field of cloud storage, can solve the problems of high decompilation risk, theft, application and data loss, etc., to avoid data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
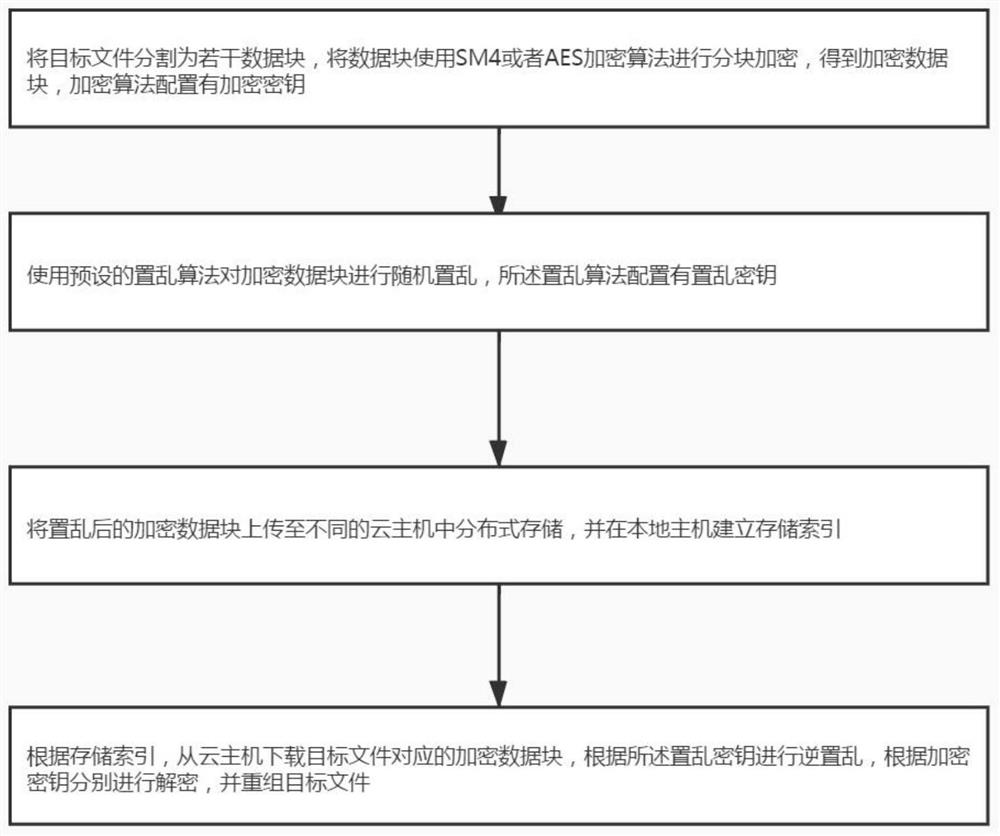
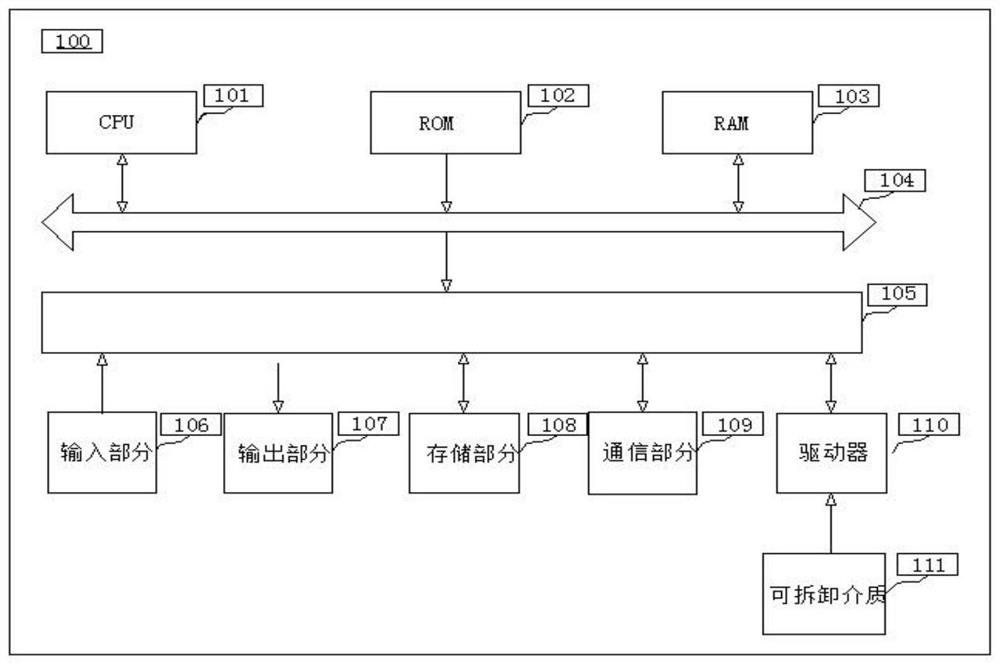
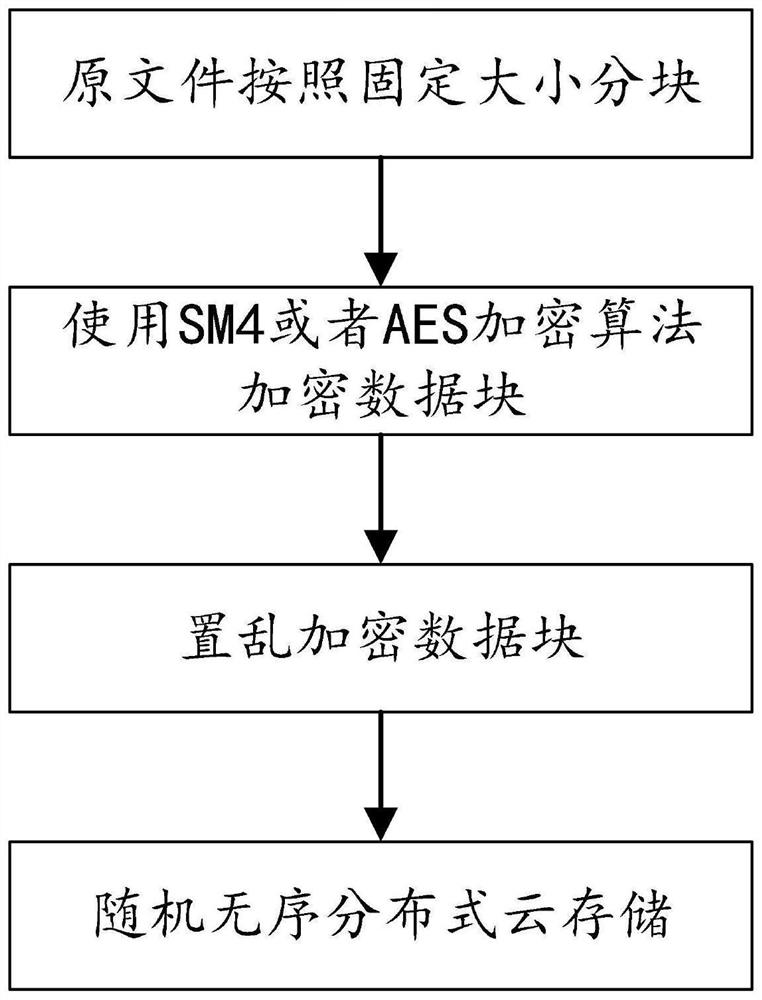
[0048] This embodiment provides a distributed cloud security storage method, including:
[0049] Step 1: Divide the target file into several data blocks, preferably divided into data blocks of the same size, and encrypt the data blocks using SM4 or AES encryption algorithm to obtain encrypted data blocks. The encryption algorithm is configured with an encryption key; specifically of:
[0050] If the size of the target file is not greater than the preset threshold, it will be divided according to the first mode, otherwise it will be divided according to the second mode; the first division mode and the second division mode are to divide the target file according to the preset size, and finally Supplementary information is appended to the end of a data block to make it the same size as other data blocks. For example: for a file not larger than 1M, it is divided into blocks according to the size of 64K; for data larger than 1M, it is divided into blocks according to the size of 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com