Security protection system of a computer information network
An information network and security protection technology, applied in the field of information security, can solve problems such as insufficient storage and hard disk loss in the database, and achieve the effect of ensuring security and preventing data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
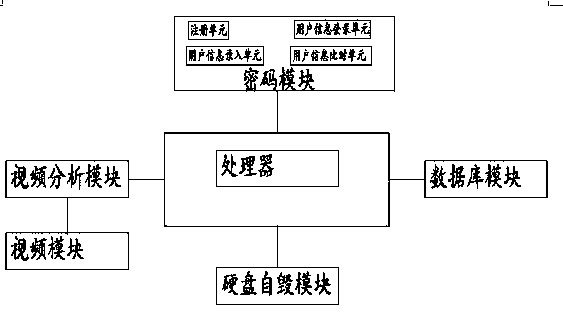
[0031] see figure 1 In Embodiment 1 of the present invention, a security protection system for a computer information network includes a video module, a video analysis module, a password module, a database module, a hard disk self-destruct module, and a processor, the video module is connected to the video analysis module, The video analysis module, password module, hard disk self-destruction module and database module are all connected to the processor.
[0032] The video module is used to record the video of the database module area, and the recorded video data is transmitted to the video analysis module, so as to observe whether there is any suspicious situation near the data module.
[0033] The video analysis module analyzes the video data transmitted by the video module. The result of the analysis is that there is suspicious person active in the database module area, or there is no suspicious person in the data module area, and the database module is in a safe state; and...
Embodiment 2
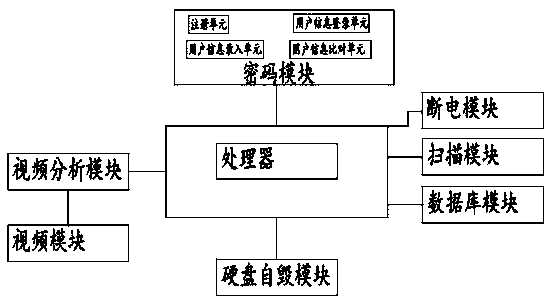
[0043] see figure 2 The main difference between the second embodiment and the first embodiment is that a security protection system for a computer information network also includes a data scanning module and a power-off module. The data scanning module is connected to the processor; the power-off module is connected between the processor and the database module.
[0044] The data scanning module is used to scan the data in the system and send the scanning result to the processor.
[0045] The power-off module is used to control the power supply of the database module, and the power-off module controls whether the database module is powered off according to the processor signal.
[0046] The power-off module and the hard disk destruction module are powered independently.
[0047] The processor is also used to receive the signal from the data scanning module. If the signal is safe, it will process it. If the signal is dangerous, the processor will send a power-off signal to t...
Embodiment 3
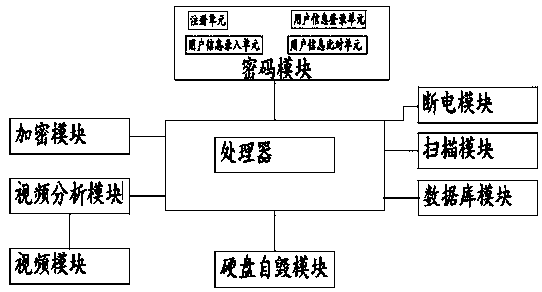
[0049] see image 3 The main difference between the second embodiment and the first embodiment is that a security protection system for a computer information network also includes an encryption module. The encryption module is connected to the processor.
[0050] The encryption module is used to encrypt data.
[0051] The working principle of the present invention is:
[0052] The system sets up a video module and a video analysis module to record the area near the database module to determine whether the database module is safe. The processor controls the hard disk destruction module to destroy the hard disk in the database module according to the signal from the database video analysis module. This setting prevents Data leakage; at the same time, a power-off module is set to prevent data leakage through the network; at the same time, an encryption module is set to further ensure data security.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com