Database protection method
A database and protection layer technology, applied in the computer field, can solve problems such as the inability to fully protect the database, and achieve the effect of blocking possibility and data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The method for protecting the database of the present invention will be further described in detail below in conjunction with the accompanying drawings.
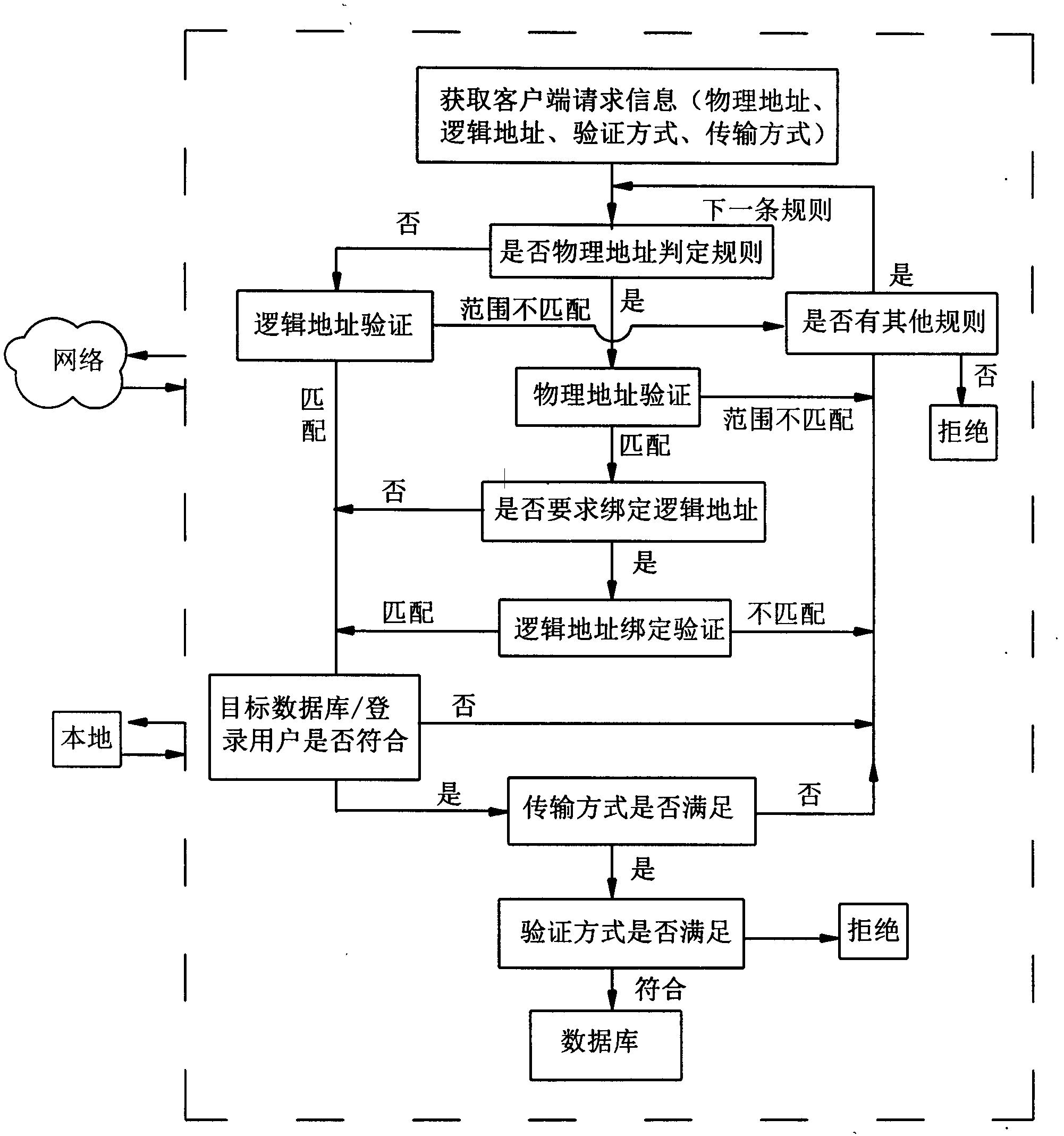
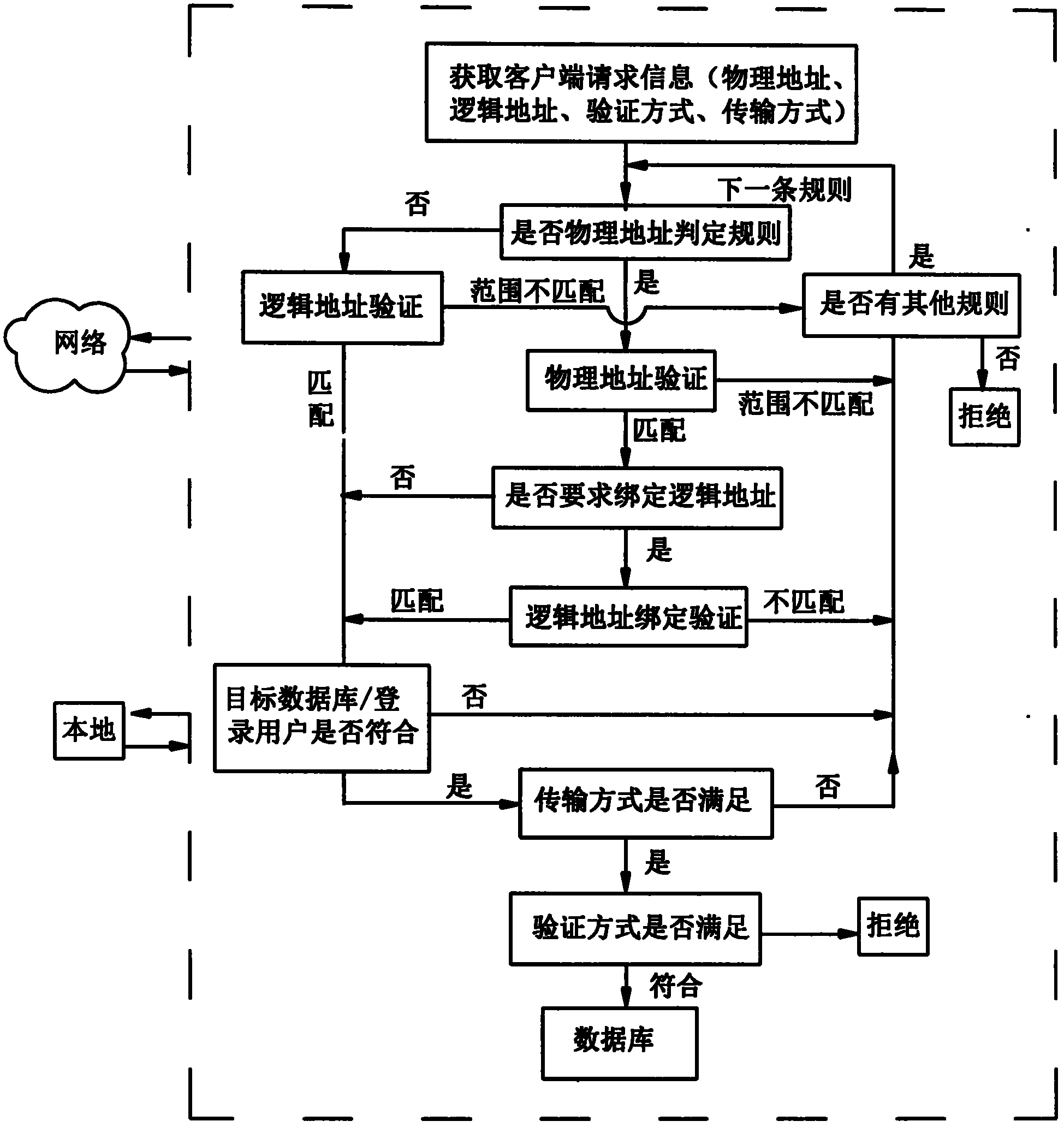
[0019] The method for protecting a database of the present invention includes a protection layer made up of a verification mechanism and several rules, each rule contains a verification definition for allowing or denying access to the database, and when a user access request is received, a user / password verification is performed when the user / password is reached at the database. Before the verification, the protection layer verifies the connection request, and decides whether to allow or deny the request according to all rule definitions. The verification process is shown in the figure below:
[0020] 1) The access client (network or local) initiates a connection request, and the protection layer receives the request and obtains the detailed information of the request;
[0021] 2) Define circular validation for each ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com