Android application protection method based on code sinking and residual code interpretation
An application and code technology, applied in the field of Android APP protection, can solve problems such as ineffectiveness and function, and achieve the effect of eliminating secondary packaging, high flexibility, and enhancing time and cost overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
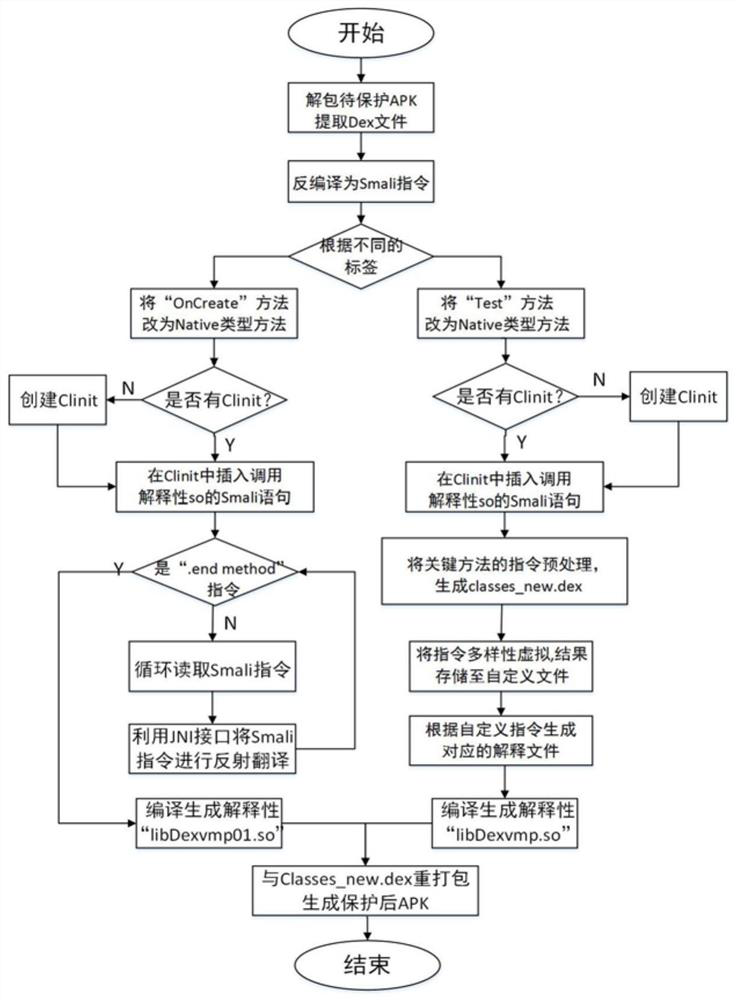
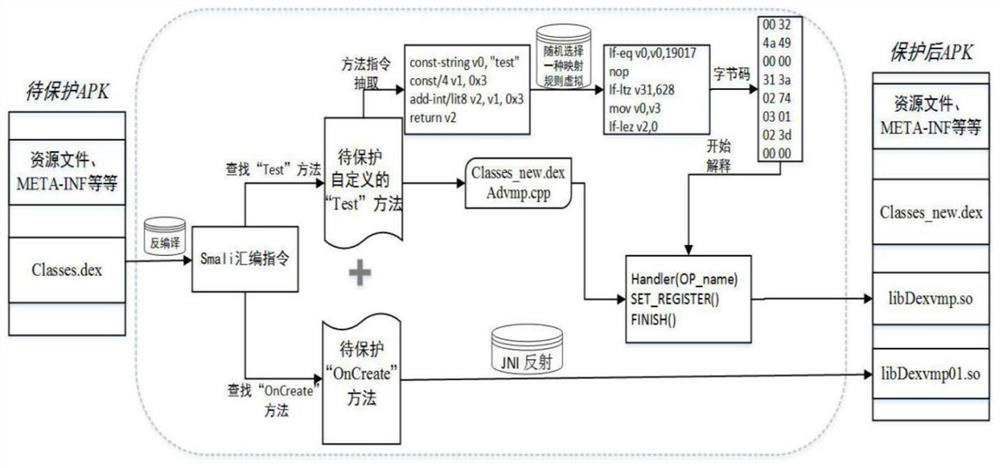
[0035]This embodiment proposes an Android application program protection method based on code sinking and residual code interpretation, and we will describe it from two aspects: the reinforcement process of the protection method and the execution process of the protected Android program. In the present invention, we choose the "OnCreate" method of the "MainActivity" class in the APP as the target function of Native to carry out JNI reflection sinking, realize the function of the "OnCreate" method in the local layer, compile and generate explanatory so files, which is The first step in this protection method. Considering that some methods except the OnCreate method may contain important logic, and at the same time, in order to increase the difficulty of reverse analysis, the present invention proposes a technology of diverse virtual interpretation of residual codes. This solution adopts code virtualization technology, that is, to extract the instructions of the method to be pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com