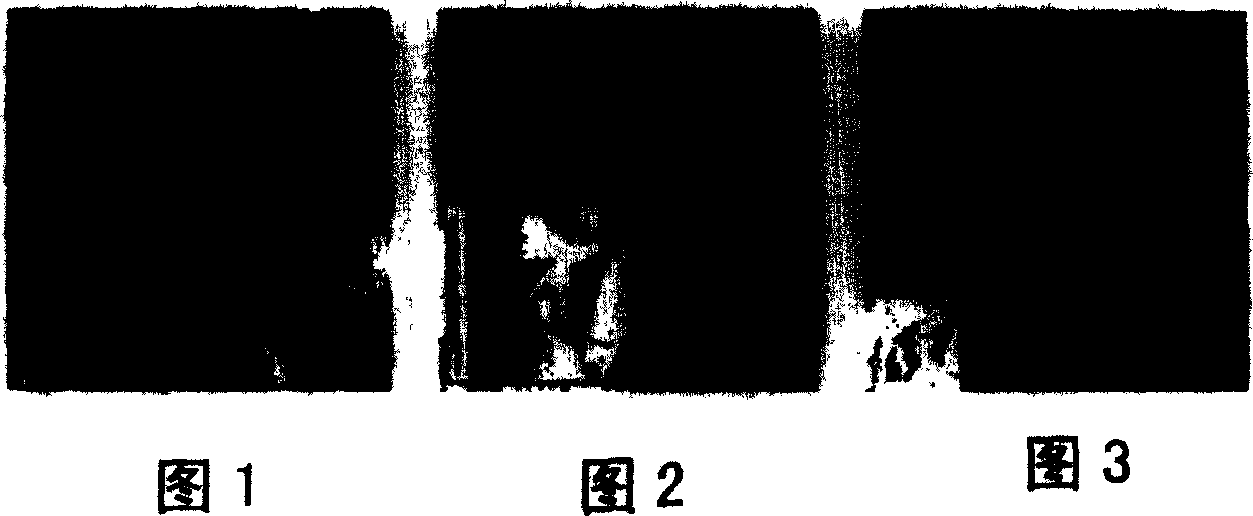Effective image compression and encryption amalgamation method
An image compression and image technology, applied in image coding, image data processing, complex mathematical operations, etc., can solve the problem that the 56-bit key length is difficult to resist exhaustive attacks, and achieve the effect of reducing the amount of calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] Figures 1, 2, and 3 show examples of wavelet decomposition of actual images. It reveals that the energy of the digital image after wavelet transform is highly concentrated in the smooth version (low frequency part or brightness sub-image). In addition, due to the typesetting requirements of the article, Figures 1, 2, 3, 5, and 6 are the results of using WINDOWS drawing tools to reduce the length and width by one time, which all bring a small amount of distortion, but none of them hinder the explanation of the problem.
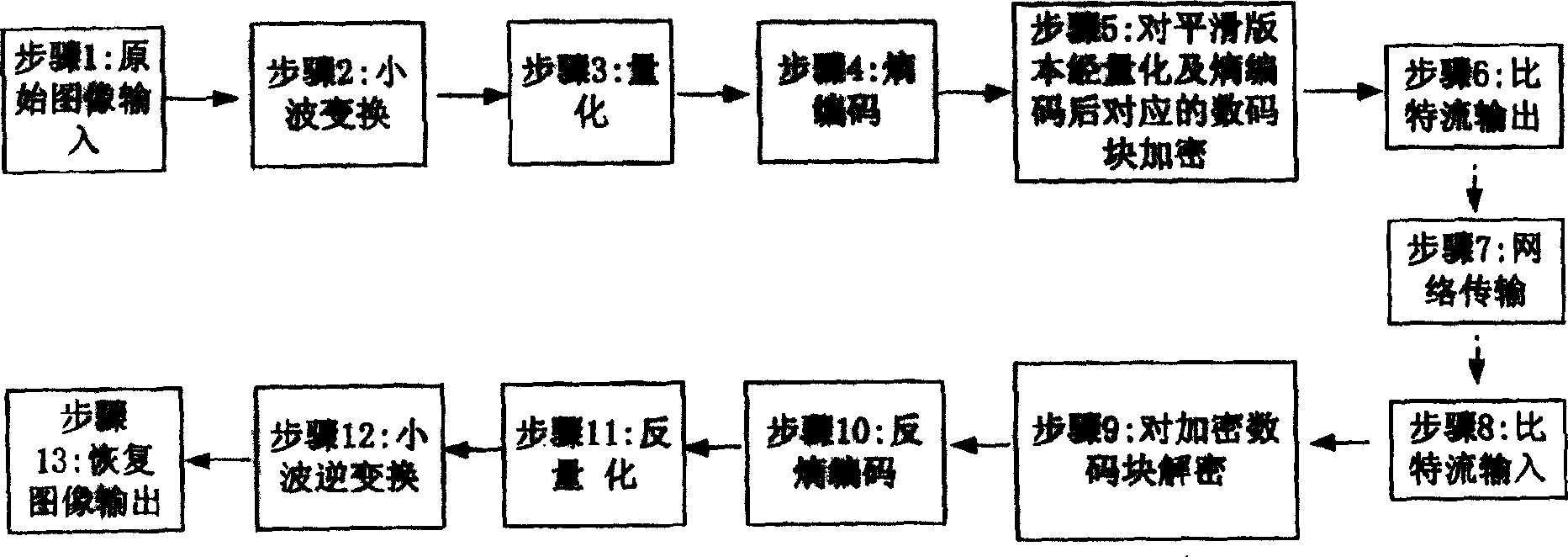
[0019] Combine below Figure 4 The specific implementation steps of the method of the present invention are described in detail.
[0020] Step 1: For original image input, digital images (such as images in BMP format) collected by various image acquisition devices can be input. The experimental image of the method of the present invention is as shown in FIG. 1 : a Lena image of 256×256×8, which is a standard use case of image processing experiments.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com