Random ciphering method which needs to be deciphered by exhaust algorithm
An encryption method and random key technology, applied in user identity/authority verification, digital transmission systems, electrical components, etc., can solve the problems of random keys locked in password identification information, difficult to use, and kept at a distance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
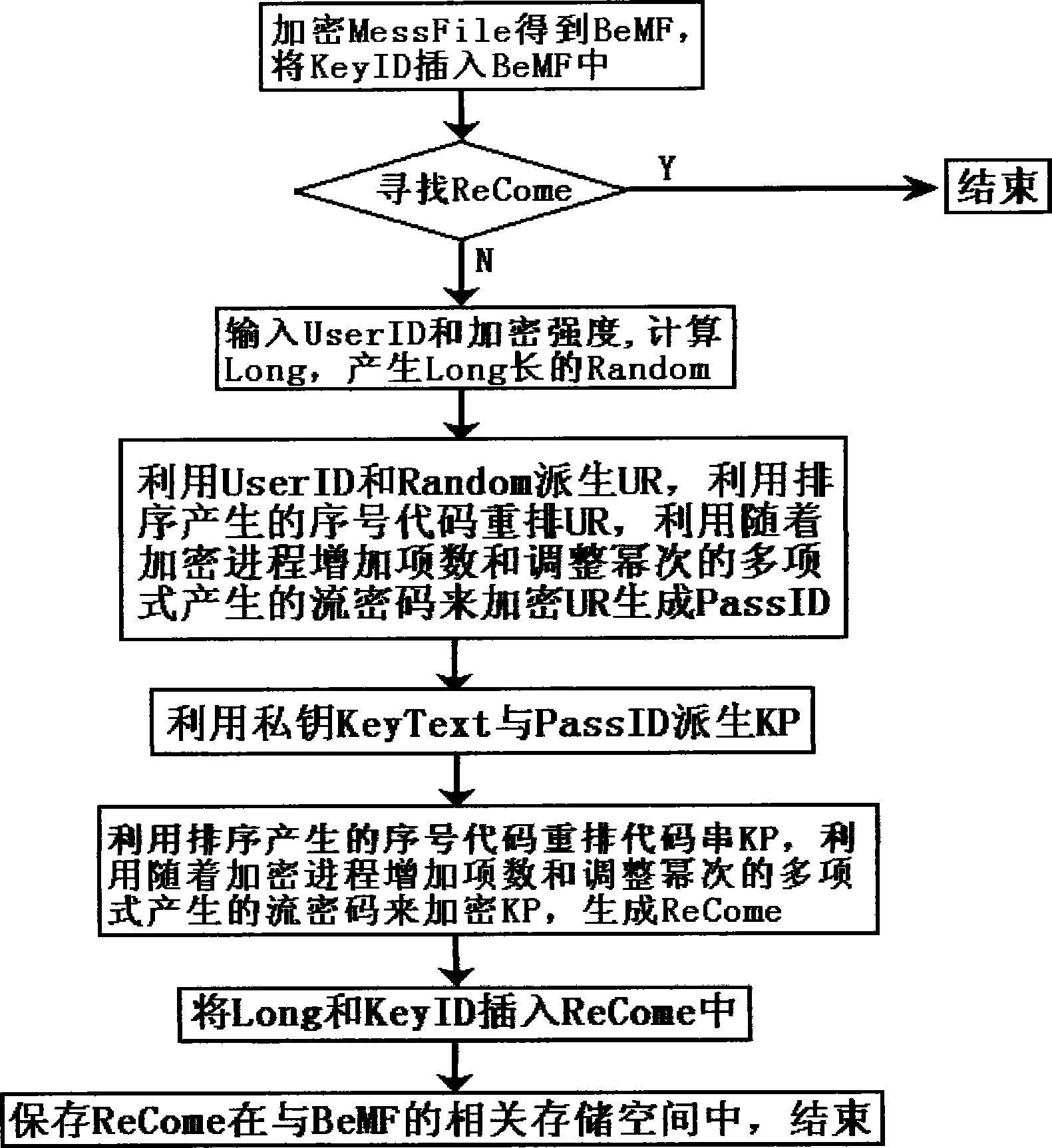
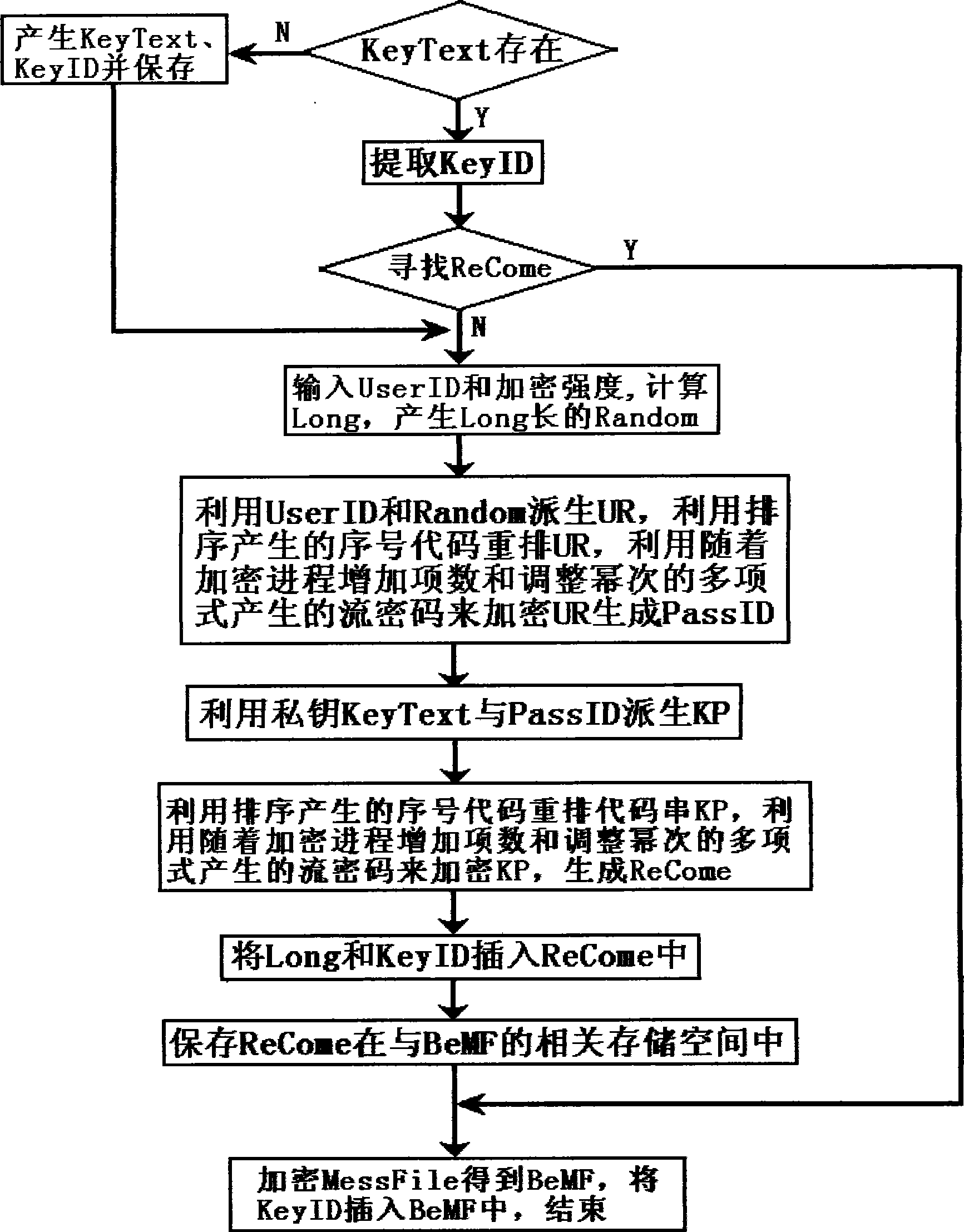
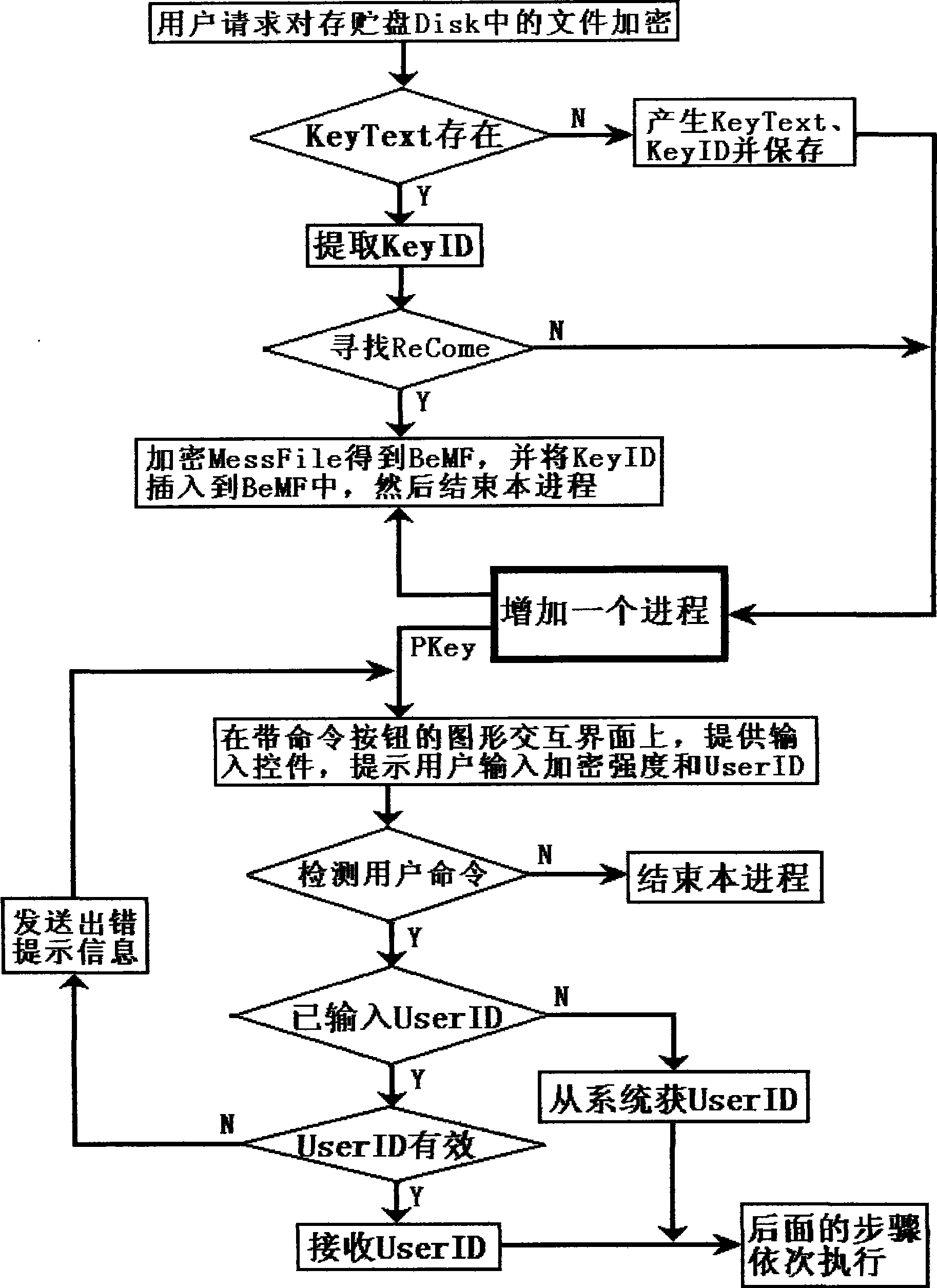
[0184] In order to distinguish it from ordinary files and information, information such as private keys, certificates, and important files that are encrypted and protected by the encryption method of the present invention are called important plaintext in this paper. The invention utilizes the user identity information and the random key to encrypt together, locks the random key and the user identity information in the password identification information, and adopts the measure of anti-cryptanalysis method when generating the password identification information. According to the encrypted ciphertext of the present invention, no matter how the cracker writes the decryption program, except for using the exhaustive method or the method combining the exhaustive method and the cryptanalysis technique, other cryptanalysis methods cannot be effectively used to decipher the ciphertext, even if In the case that the user identity information provided is correct, any decryption program fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com