Automobile key system with configurable safety strategy and realizing method thereof
A security strategy and system implementation technology, applied in the field of car key system, can solve the problems of not being able to drive the car, waiting for a long time, unable to make physical keys, etc., and achieve the effect of convenient use of car authorization and strong encryption strength
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
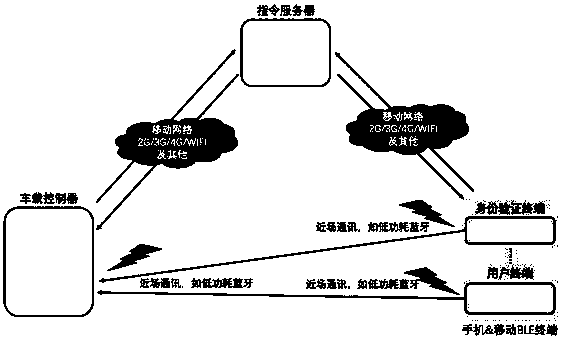
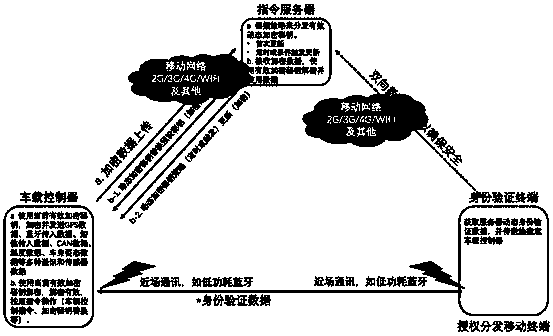
[0035] Such as figure 1 , figure 2 , image 3 , Figure 4 and Figure 5 As shown, a car key system implementation method with configurable security policy, the implementation method includes: setting a user terminal and a background command server and installing a vehicle controller on the car, and also includes the following steps:
[0036] Step S1: The on-board controller initiates a connection request to the command server through a preset encryption key;
[0037] The specific implementation manner of the step S1 in which the vehicle-mounted controller initiates a connection request to the command server through a preset encryption key may be: the vehicle-mounted controller sends various communication and sensor data to the command server through a preset encryption key.
[0038] In practical applications, the communication and sensor data may include: GPS information, Bluetooth incoming information data, SMS incoming information data, CAN data, temperature and humidit...
Embodiment 2
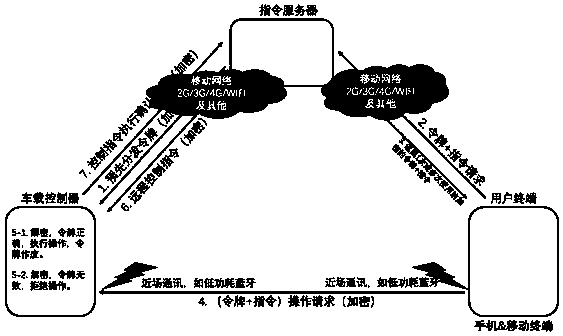
[0053] Such as image 3 and Figure 4 As shown, the encryption and command control process of the car key system implementation method with configurable security policy is as follows:
[0054] 1) The user terminal requests the encryption control command from the command server when necessary;
[0055] 2) instructing the server to return an encrypted control command to the user terminal according to the situation;
[0056] 3) The user terminal sends the encrypted control command to the vehicle controller through near-field communication;
[0057] Wherein, the near field communication is BLE (Bluetooth Low Energy).
[0058] 4) The on-board controller decrypts and judges whether the command is valid, executes the command if it is valid, and rejects the command if it is invalid;
[0059] 5) The on-board controller feeds back the execution result of the control command to the command server.
[0060] In practical applications, the user terminal can use the pre-cached encrypted...
Embodiment 3
[0065] Such as figure 1 and Figure 5 As shown, a car key system with configurable security policies is constructed according to the method for implementing a car key system with configurable security policies, including a vehicle-mounted controller, a user terminal and a background command server system, wherein the vehicle-mounted controller Including CPU core, memory, encryption and decryption calculator, random number generator, output module, input module, CAN communication module, near field communication device and mobile data network communication module, the CAN communication module, input module and output module are compatible with the vehicle Related circuits are connected, the near-field communication device establishes a connection with the user terminal, the mobile data network communication module establishes a connection with the background command server system, and the input module includes a gyroscope, a 3D acceleration sensor, GPS, a temperature sensor, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com