Identity combination method
A technology of identity federation and identity management, applied in the field of identity federation of mapping relationships, which can solve problems such as limiting the scope of SPs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
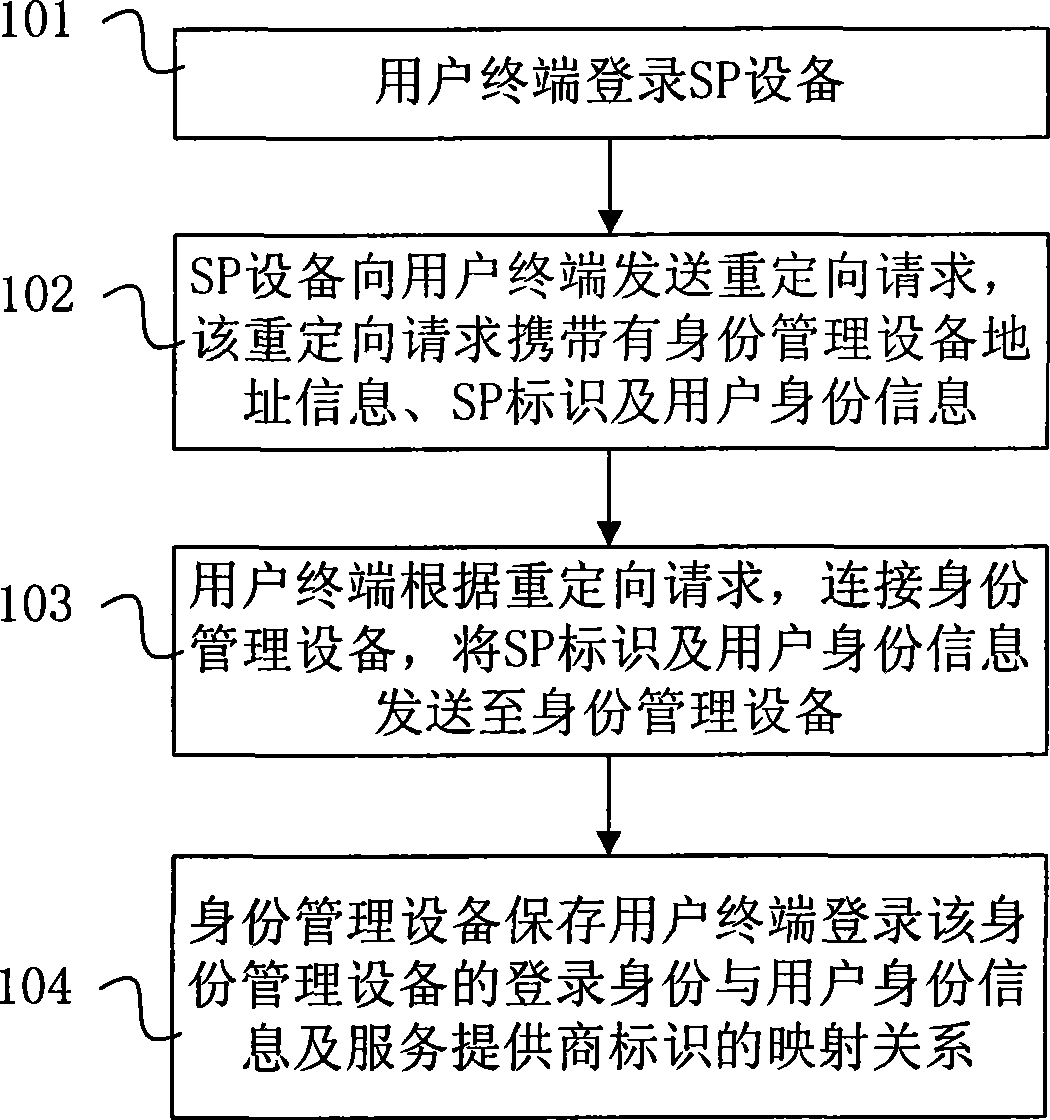
[0026] like figure 1 As shown, it is a flow chart of Embodiment 1 of the identity federation method of the present invention, including the following steps:
[0027] Step 101, the user terminal logs in to the SP device;
[0028] Step 102, the SP device sends a redirection request to the user terminal, and the redirection request carries the address information of the identity management device, the SP identifier and user identity information;
[0029] Step 103, the user terminal connects to the identity management device according to the redirection request, and sends the SP identification and user identity information to the identity management device;
[0030] Step 104, the identity management device saves the mapping relationship between the login identity of the user terminal logging into the identity management device, the user identity information and the service provider identifier.
[0031] This embodiment realizes that after the user logs in to the SP device, the SP...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com