A kind of private cloud system and operation method
An operation method and cloud system technology, applied in transmission systems, electrical components, etc., can solve the problems of high failure rate, high complexity of cloud platform systems, and high maintenance costs, and achieve high security, reduced technical complexity, and reduced operational costs. The effect of dimension cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
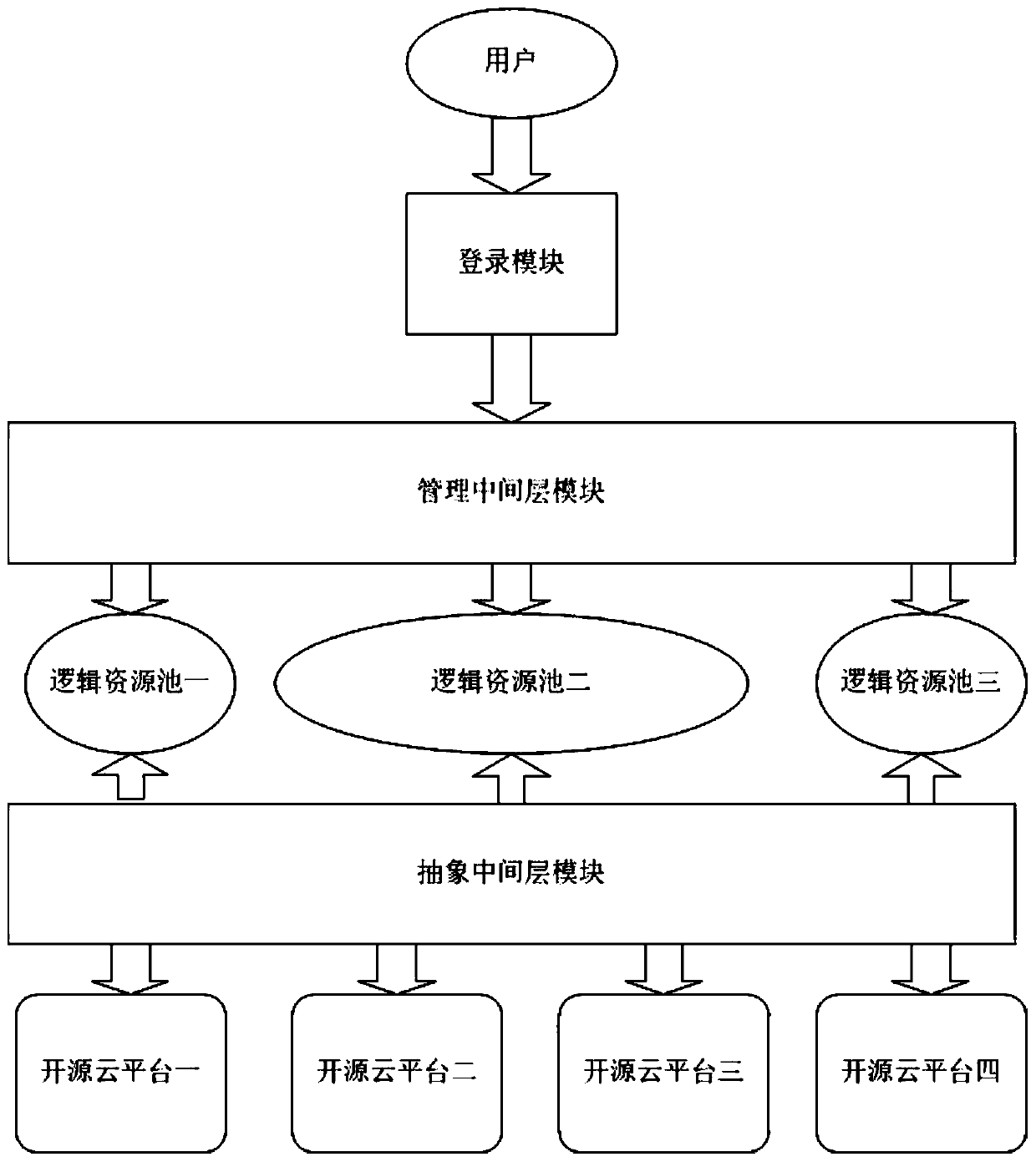
[0048] Such as figure 1 As shown, a private cloud system includes the following modules:
[0049] Login module: including a unified user login interface; user login and user permission acquisition; ensuring that users can see their own logical resources.
[0050] Management middle layer module: accept user's request and manage logical resource pool;
[0051] Abstract middle layer module: manage the resource information of each independent cloud platform in a unified manner, and divide multiple independent cloud platform resources into multiple logical resource pools according to requirements; receive management middle layer operation requests, call the physical platform API to perform operations, and send The management middle layer returns operation results; the abstract middle layer module abstracts several open source cloud platforms into multiple virtual logical resource pools, and each virtual logical resource pool is composed of one or more open source cloud platforms. ...
Embodiment 2
[0057] Embodiment 2 is basically the same as Embodiment 1, and the abstract middle layer module can also perform resource scheduling to create a virtual machine on the open source cloud platform.
Embodiment 3
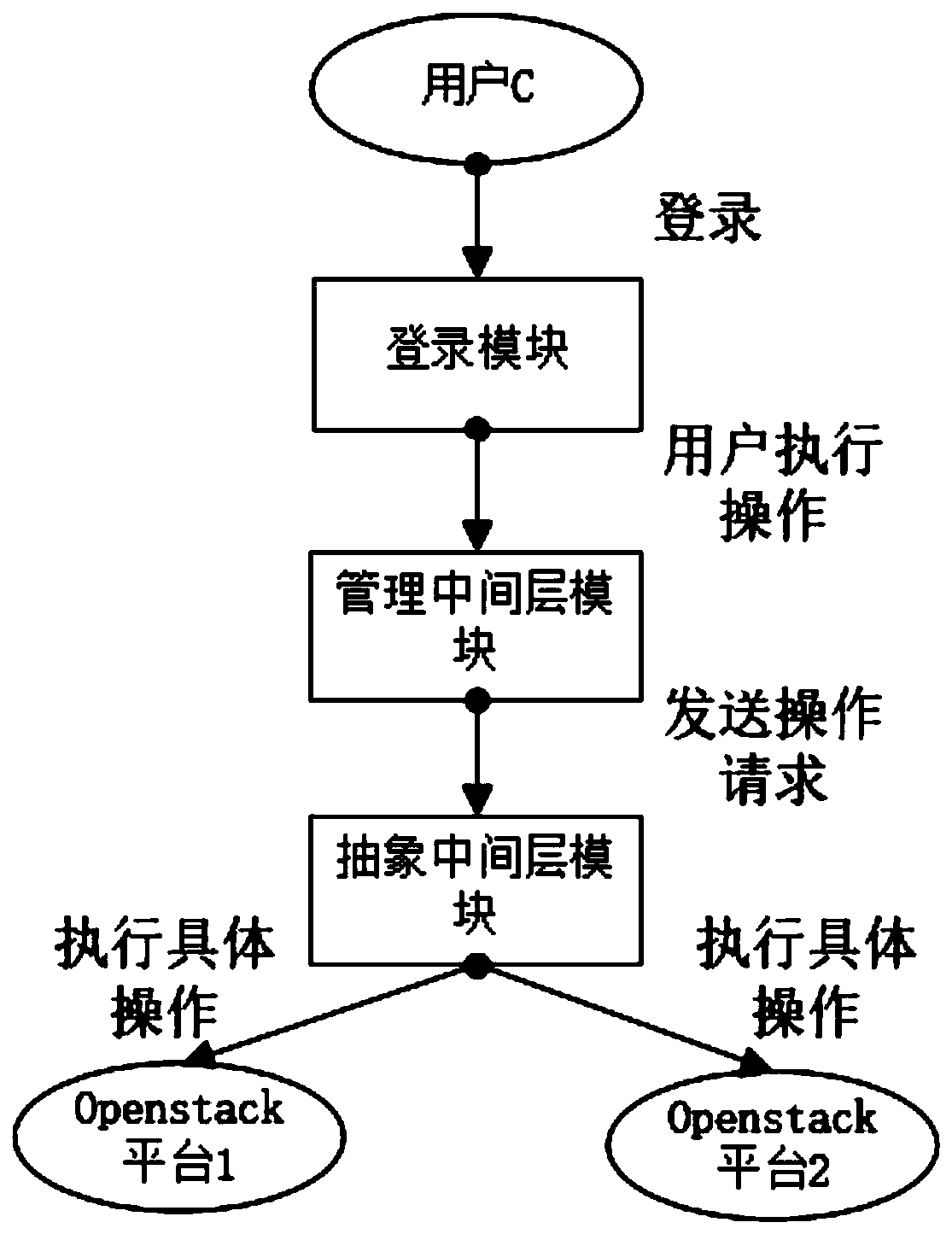
[0059] Such as image 3 As shown, based on the private cloud system of the above-mentioned embodiments 1 and 2, the operation method at runtime, the steps are as follows:
[0060] A. The user creates a user account, obtains user permissions, and logs in to the private cloud system through the login module; after the user logs in, obtains relevant permission information, and the steps for obtaining user permissions are as follows:
[0061] Obtain relevant permission function realization:
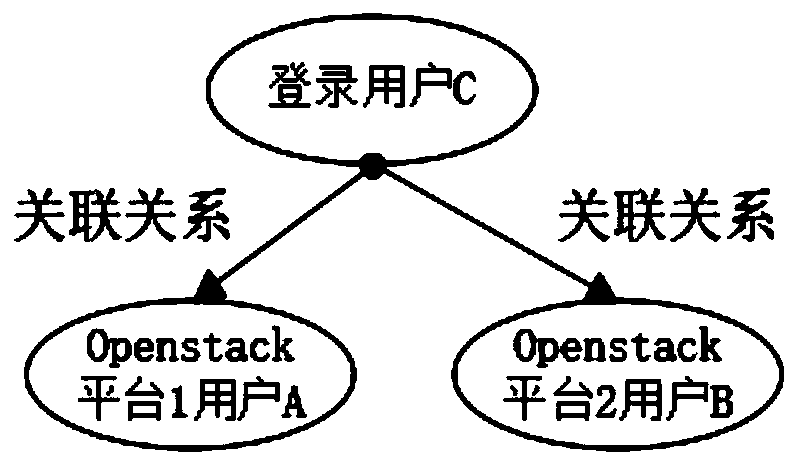
[0062] Query the project table, verify the login name and login password; after successful login, do a connection query in the three tables of physical platform table, project table, project and Openstack platform tenant correspondence table, and find out the physical platform information (including Openstack platform) belonging to the user. user password); and save the relevant restfulAPI information and permission verification information in the physical platform table in the current sessi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com