Apparatus and method for precluding e-mail distribution
a technology for e-mail and apparatus, applied in the direction of instruments, data switching networks, unauthorized memory use protection, etc., can solve the problems of message overload, slow and expensive direct solicitation by telemarketing, and almost instantaneous receipt of error notifications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
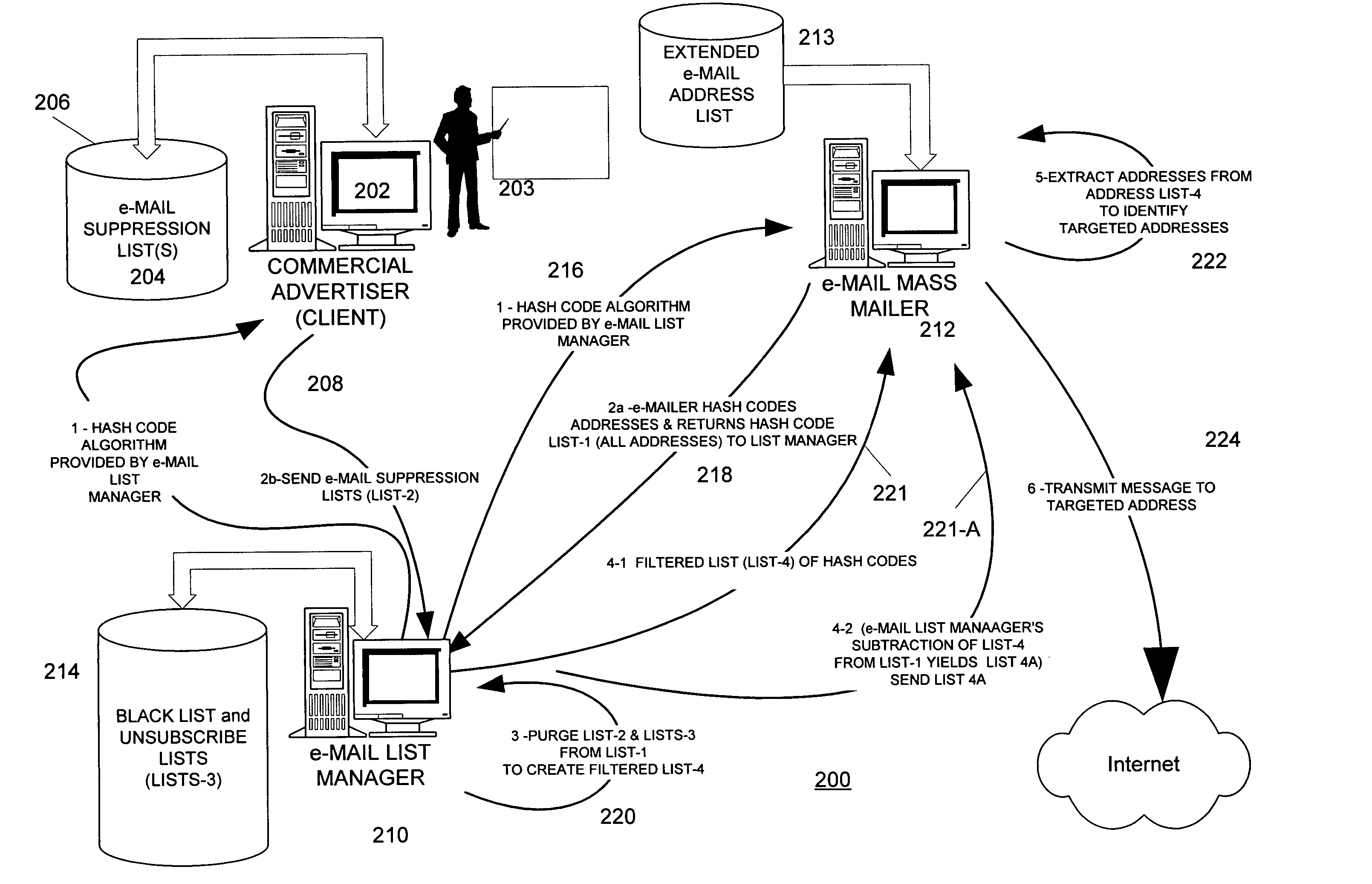
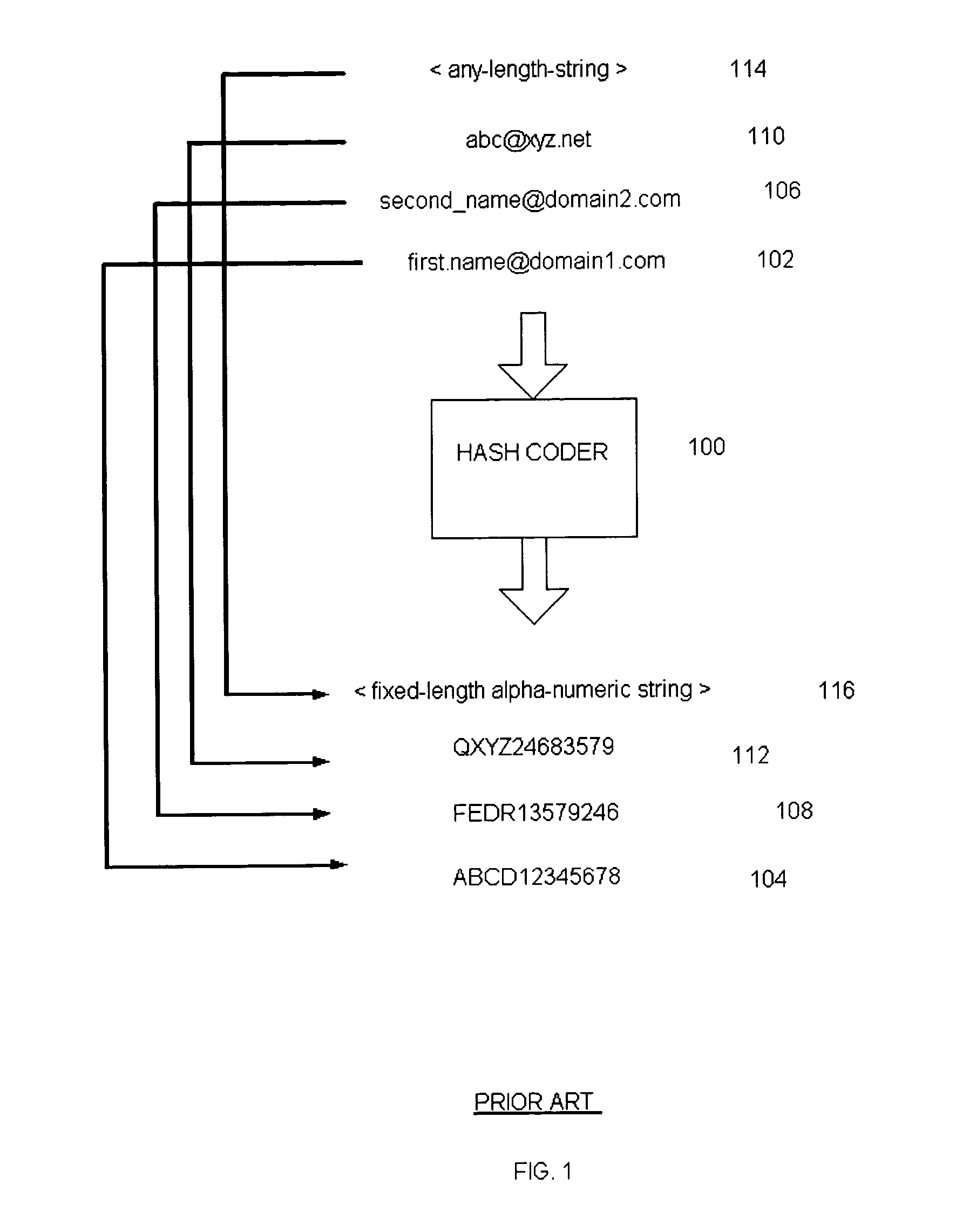
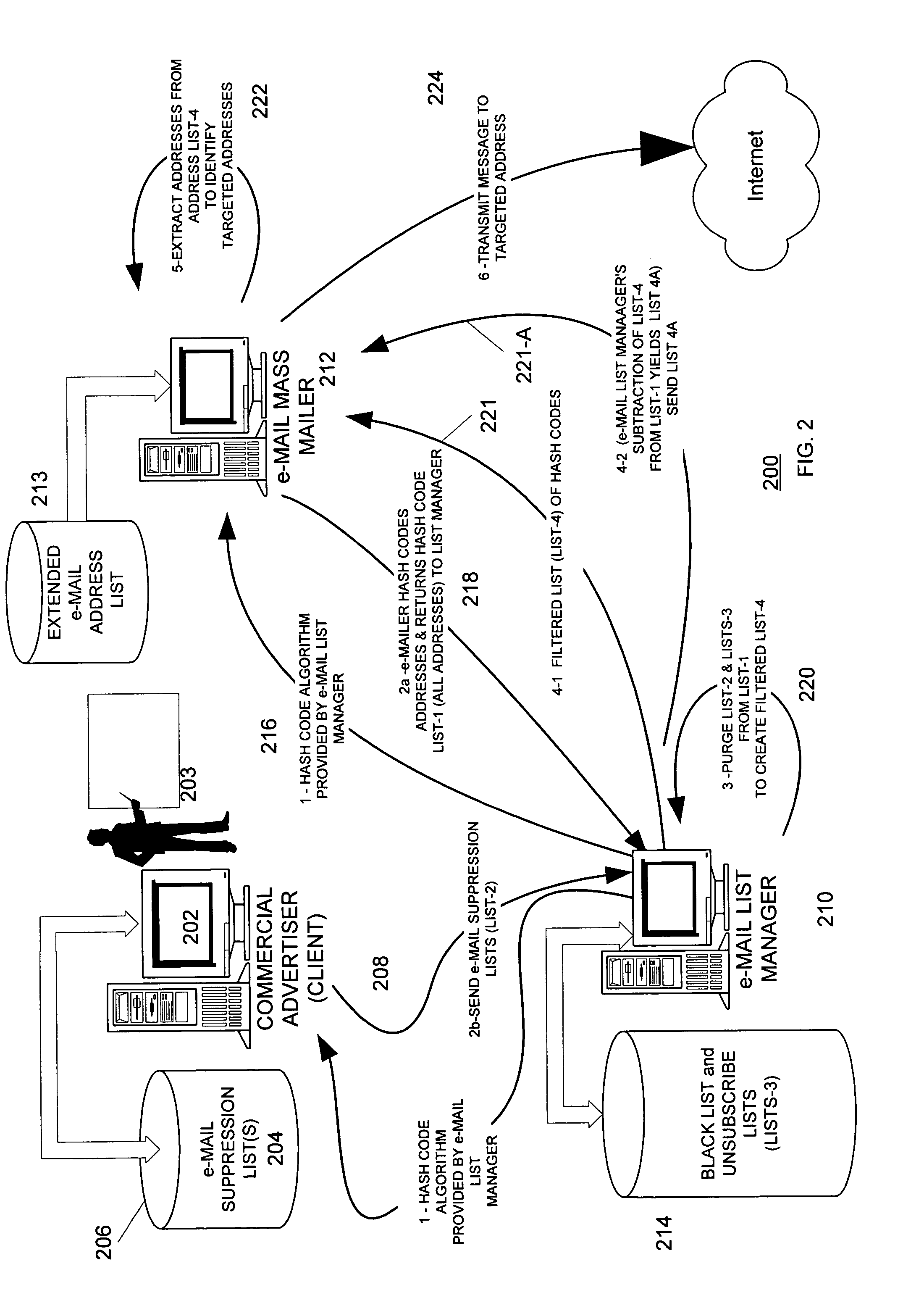
[0011] A hash function is any mathematical algorithm that converts a variable-length string of letters and / or numbers into a fixed-length output string of letters and / or numbers. The output of a hash function is known as a “hash value” or “hash code.” Among other things, hash functions are used to create digital signatures of strings of characters.
[0012] As is well known, an e-mail address has at least three parts: a name or other designation of an addressee followed by a domain name and a domain. The name and domain name are usually separated by the “@” symbol.
[0013] E-mail addresses in general take the form of: [0014]@.
[0015] Where is an message recipient identifier.
[0016] Examples of e-mail addresses (all of which are fictitious) include: [0017] john.smith@xyz.com [0018] fred_morgan@abc.gov [0019] s.person@internetserviceprovider.com
[0020] A hash coder is considered to be a device or software-implementation of a hash function. A hash coder processes variable-length input str...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com