Encryption method and system based on data attributions
A technology of data attributes and encryption methods, applied in the direction of preventing unauthorized use of memory, etc., can solve problems such as the inability to meet the diversity of file encryption, and achieve the effects of reducing data processing volume, improving efficiency, and flexible selection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
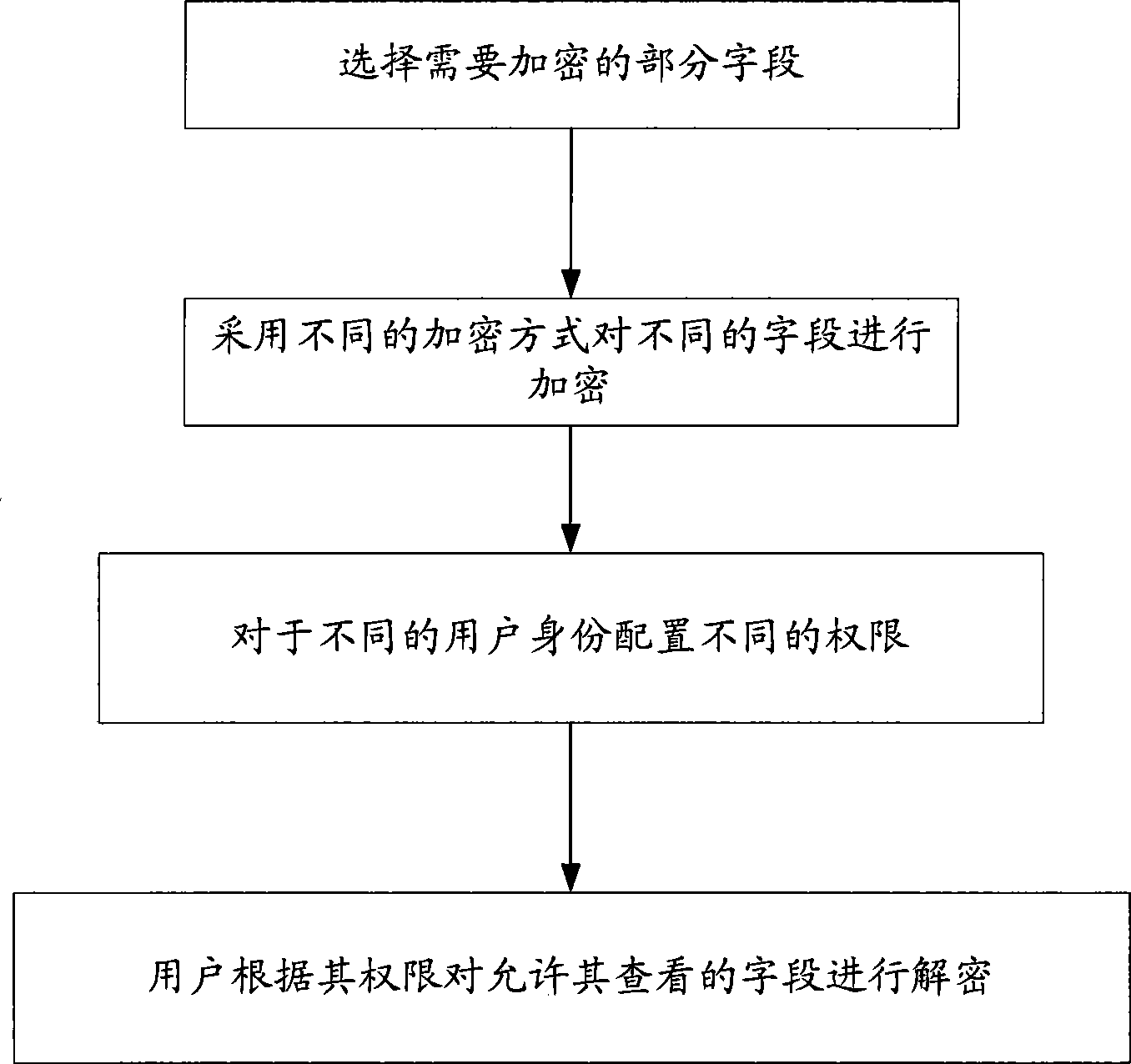
[0029] In this embodiment, an encryption method based on data attributes is provided, and the flow chart is as follows figure 1 As shown, including: select some fields that need to be encrypted, and use different encryption methods to encrypt different fields; configure different permissions for different user identities, and users can decrypt the fields that they are allowed to view according to their permissions.
[0030] The above-mentioned encryption of different fields by using different encryption methods includes: encrypting according to attributes of the fields, and different attributes are encrypted using different methods. When the amount of data is large but not critical, a symmetric encryption method is used; when the amount of data is small but critical, a symmetric decryption algorithm is used for encryption, and an asymmetric encryption method is used to protect the symmetric key. By adopting different encryption methods for key data and non-key data, the effici...
Embodiment 2
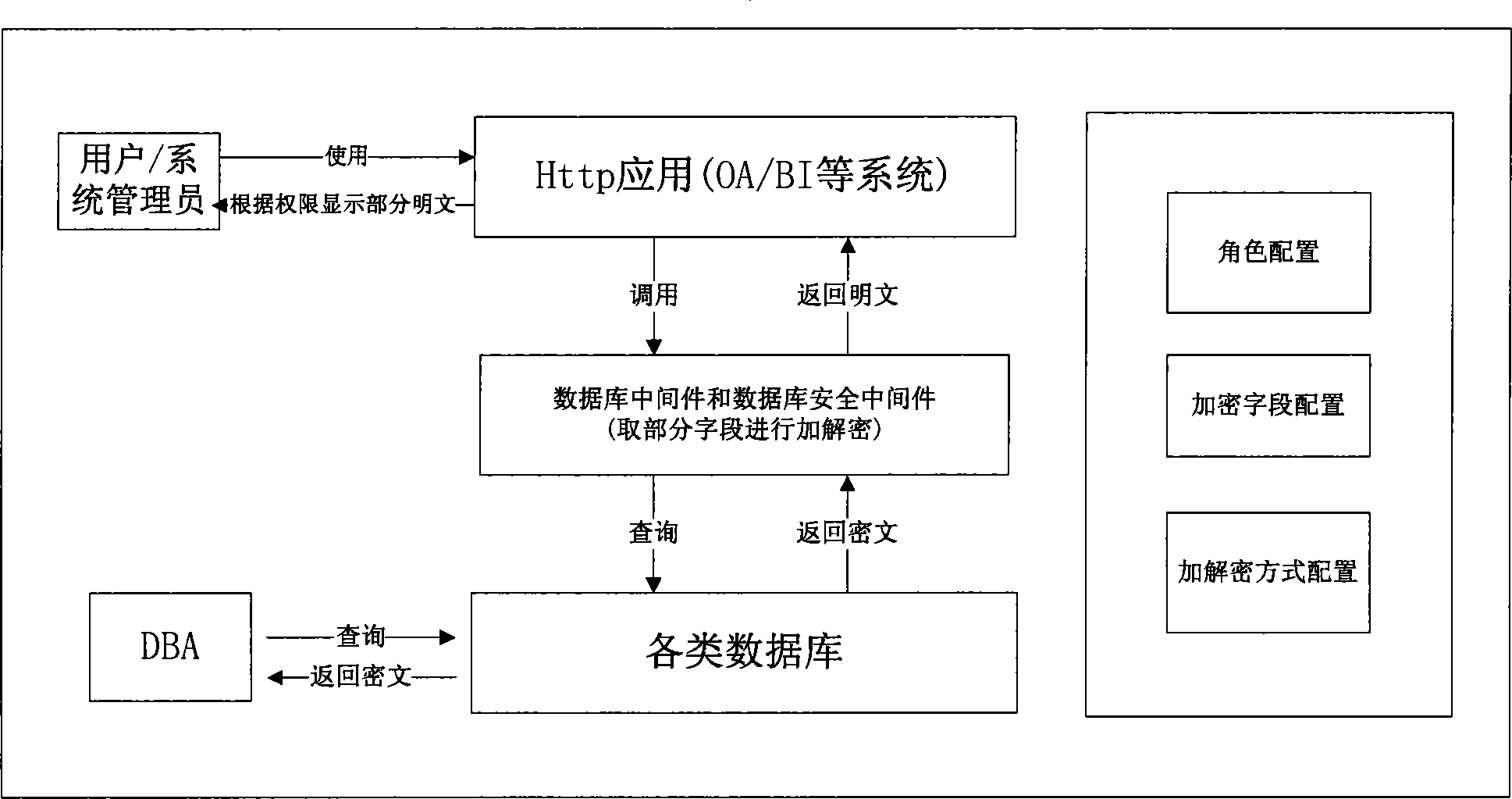
[0047] In this embodiment, an encryption system based on data attributes is provided, and the structural block diagram is as follows image 3 As shown, the encryption method corresponding to the data attribute given in the above-mentioned embodiment 1 includes:
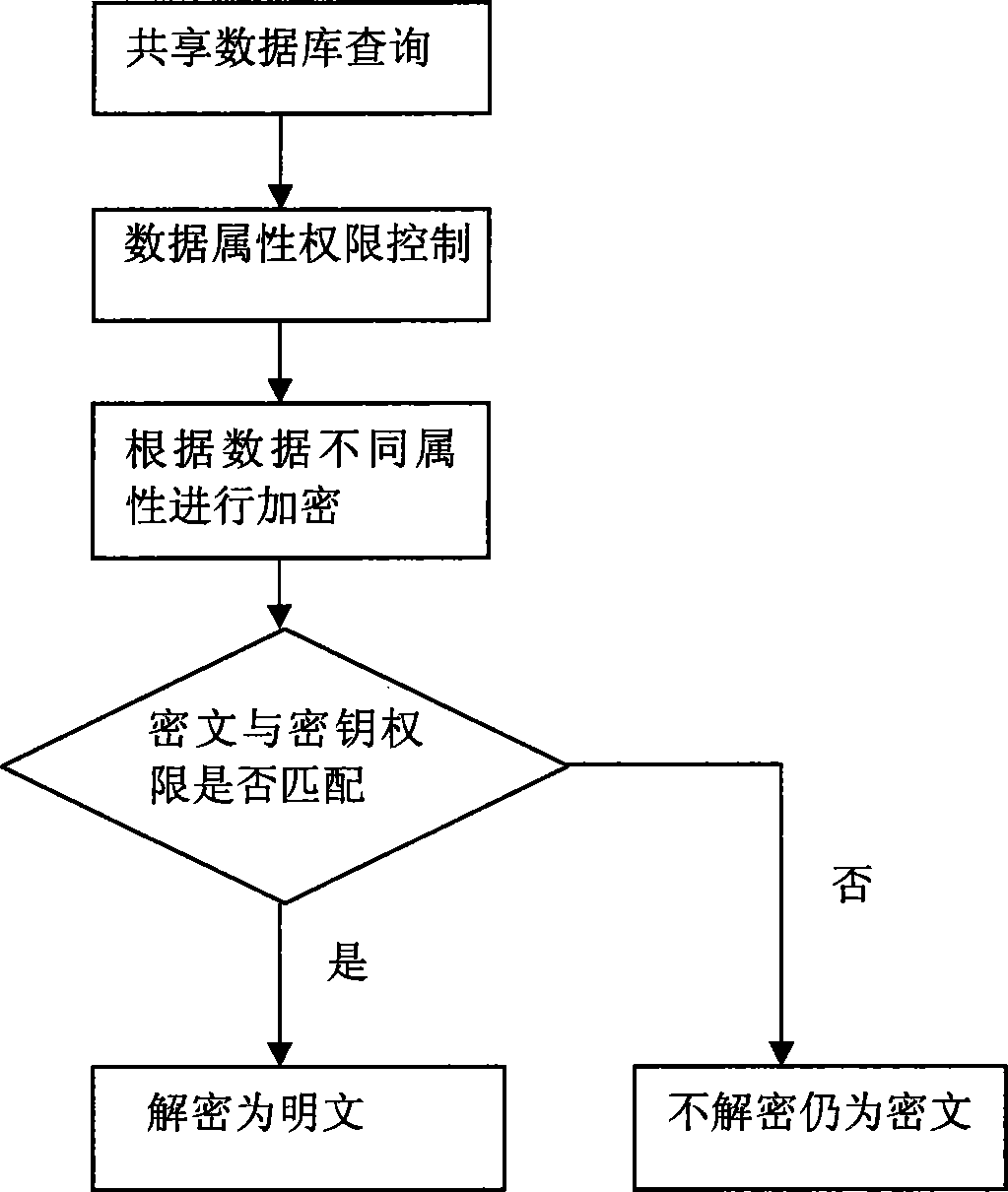
[0048] The database layer stores data information, and the data information is encrypted and stored; wherein, different fields in the database are encrypted before being stored according to the system configuration.
[0049] The application layer is integrated with database middleware and data security middleware. The database middleware takes over the access interface of the database layer and acts as an agent for accessing the database layer; the data security middleware performs data processing on the data returned by the database layer to the application layer Encryption and decryption of sensitive data, for some fields that need to be encrypted, different encryption methods are used to encrypt different fields, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com