Implementation method for specific security terminal system based on iOS system
A technology of a terminal system and an implementation method, which is applied in the field of information security, can solve problems such as high complexity, does not provide identity authentication function, and cannot guarantee the identity security of both parties in communication, and achieves the effect of improving encryption efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
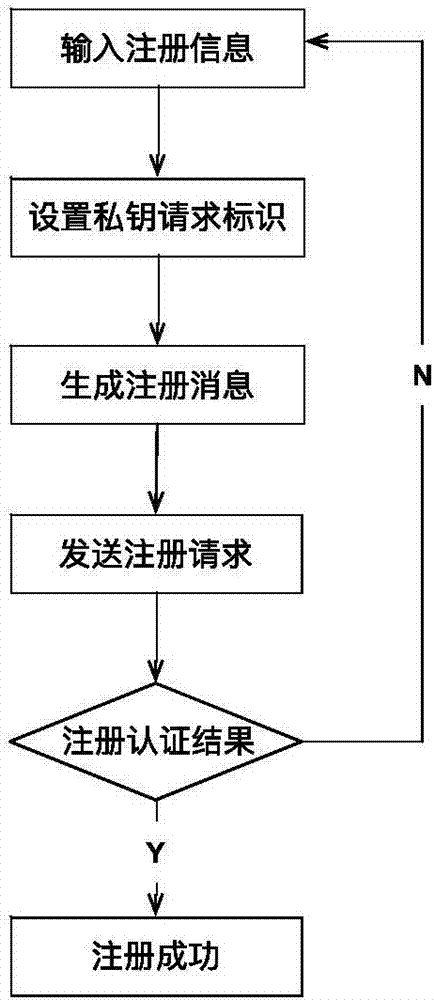
Embodiment 1
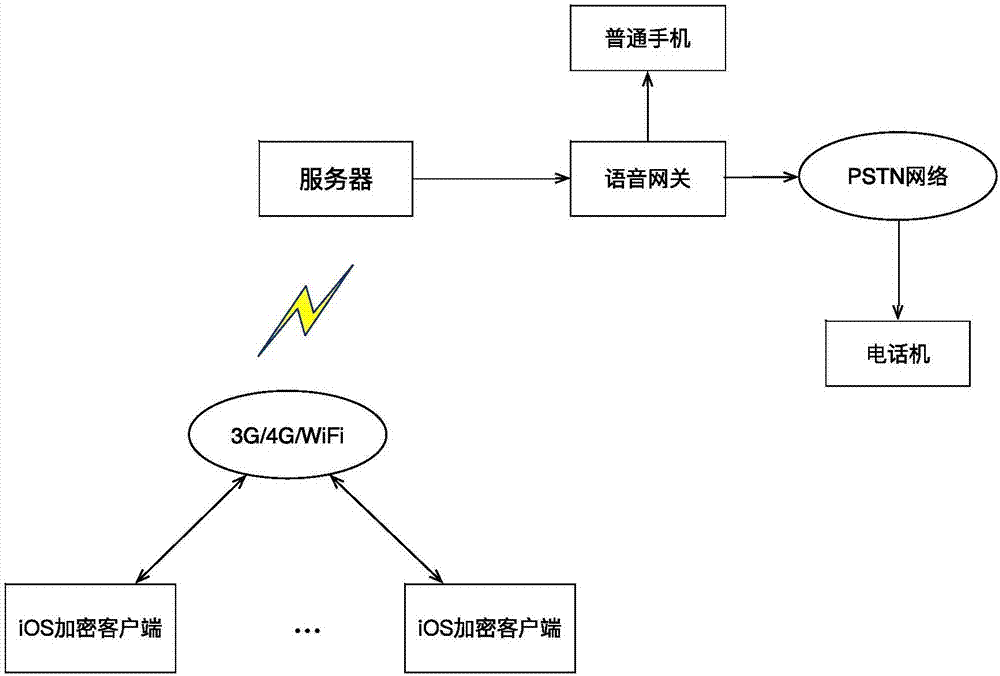
[0046] figure 1Shown is the application scene diagram of the present invention. The encrypted client initiates a call request to the server through the 3G / 4G / WiFi network, and the server judges whether the called party is an Internet phone client. If the called party is an Internet phone client, it calls the called party through the 3G / 4G / WiFi network ; If the called party is not an Internet phone client, the call request is forwarded through the voice gateway. When the called party is an ordinary mobile phone user, the voice gateway sends the call to the called party through the 3G / 4G network. When the called party is an ordinary phone , the voice gateway sends the call to the called party through the PSTN network to establish the call.
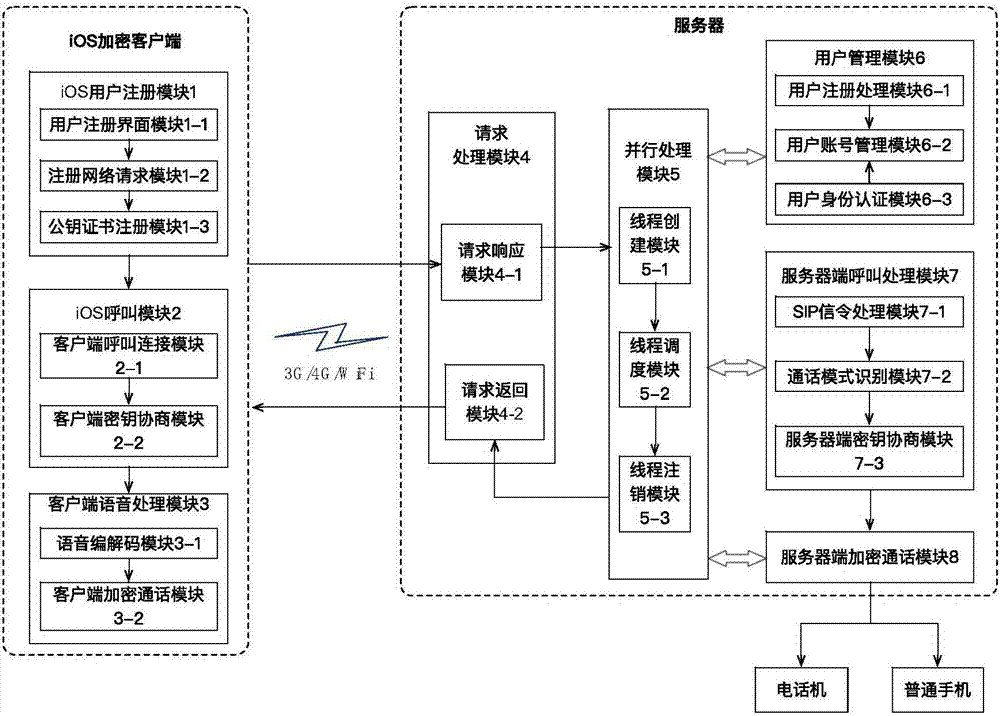
[0047] like figure 2 Shown is the overall principle structure diagram of the present invention. The present invention comprises the following eight modules: iOS user registration module 1, iOS call module 2, client voice processing modul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com