Method for full-disk encryption based on trusted cryptography module
A cryptographic module and full-disk encryption technology, applied in the field of information security, can solve the problems of low encryption and decryption efficiency, inconvenient use, etc., and achieve the effect of improving encryption and decryption efficiency, encryption efficiency, and security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] A full-disk encryption method based on a trusted cryptographic module provided by the present invention will be described in detail below in conjunction with the accompanying drawings.
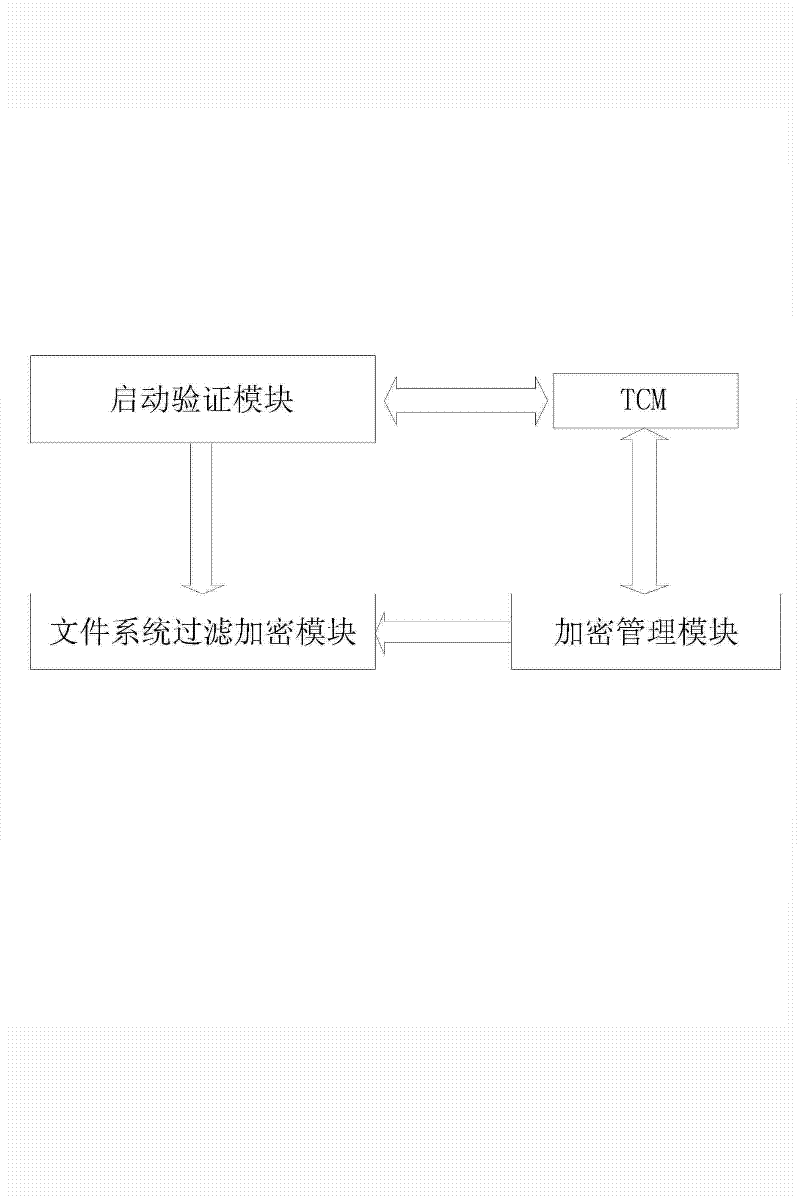
[0031] as attached figure 1 As shown, a method for full-disk encryption based on a trusted cryptographic module is now provided, including an encryption management module, a startup verification module, a file system filtering encryption module, and a trusted cryptographic module, wherein:
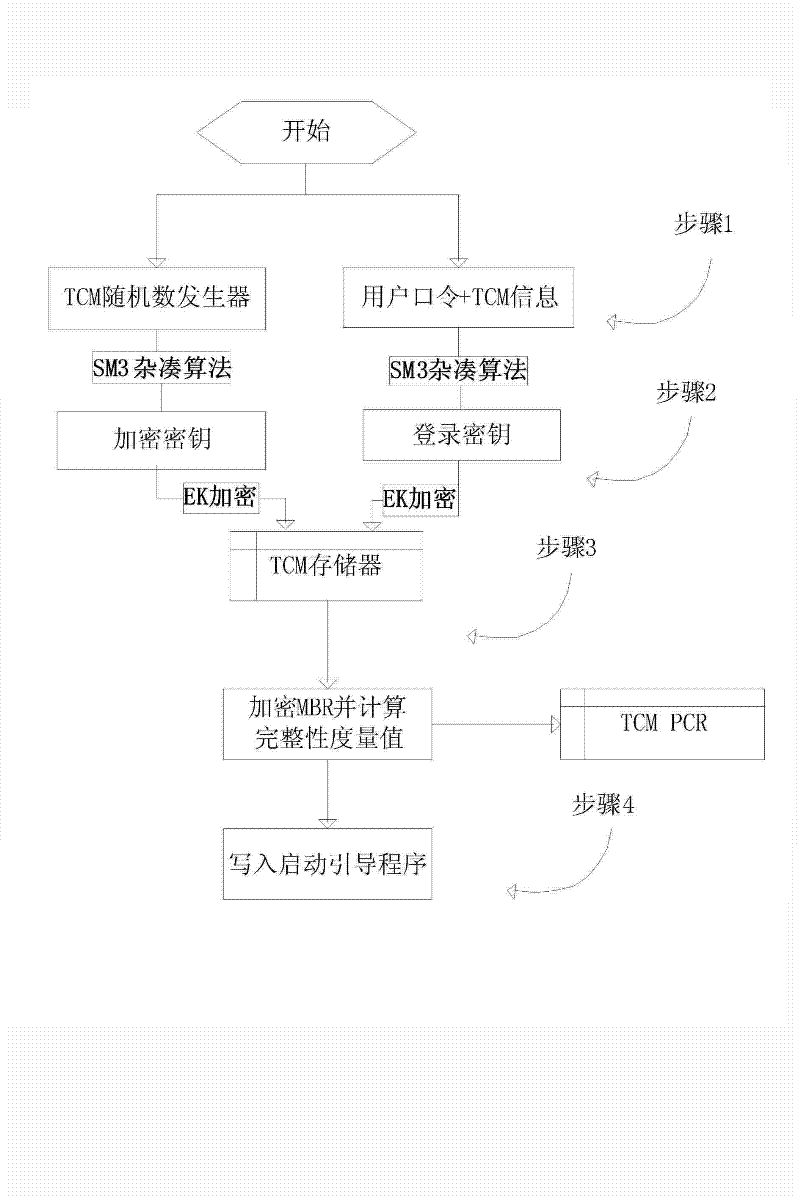
[0032] The encryption management module is used to generate encryption keys and encrypt MBR data and write them into the target disk to complete the establishment of the full disk encryption system, bootloader loading and key management functions.
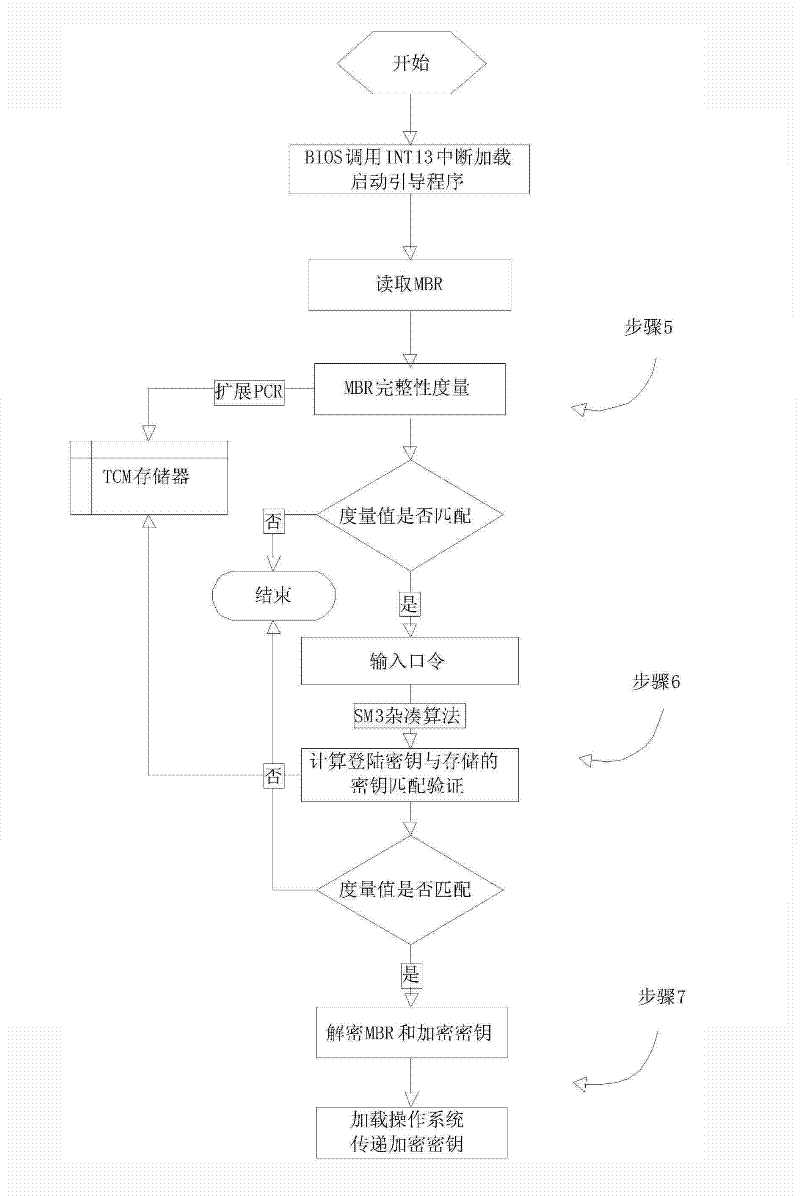
[0033] The boot verification module is a boot boot program, which is loaded before the operating system starts, and communicates with the TCM to call the TCM hash cipher algorithm to perform login authentication and MBR integrity verification.
[0034] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com