A block password fault-tolerant algebraic bypass analysis method based on multi-inference utilization
A block cipher, bypass analysis technology, applied in encryption devices with shift registers/memory, digital transmission systems, electrical components, etc., can solve problems such as attack failures, errors, unsolved equations, etc., to improve fault tolerance. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] Embodiments of the present invention will be described in detail below according to the drawings provided by the present invention.
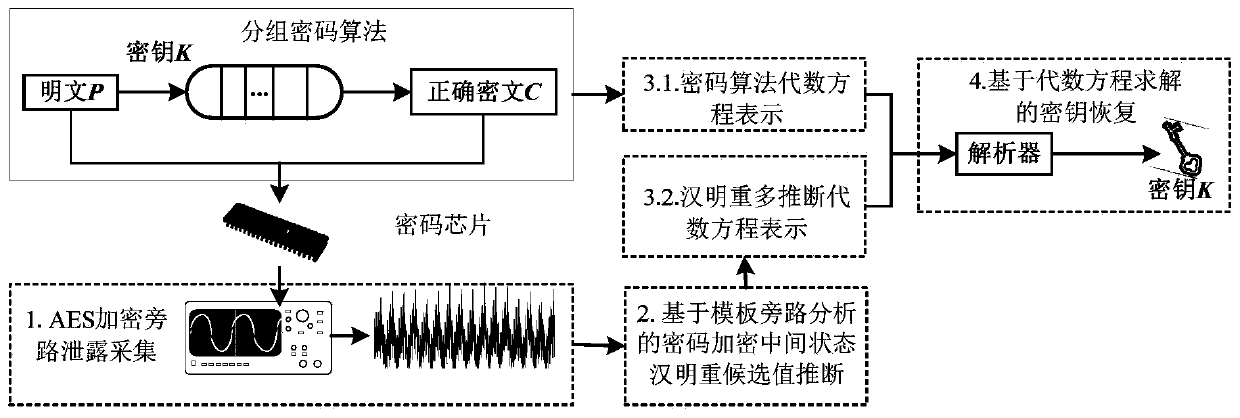
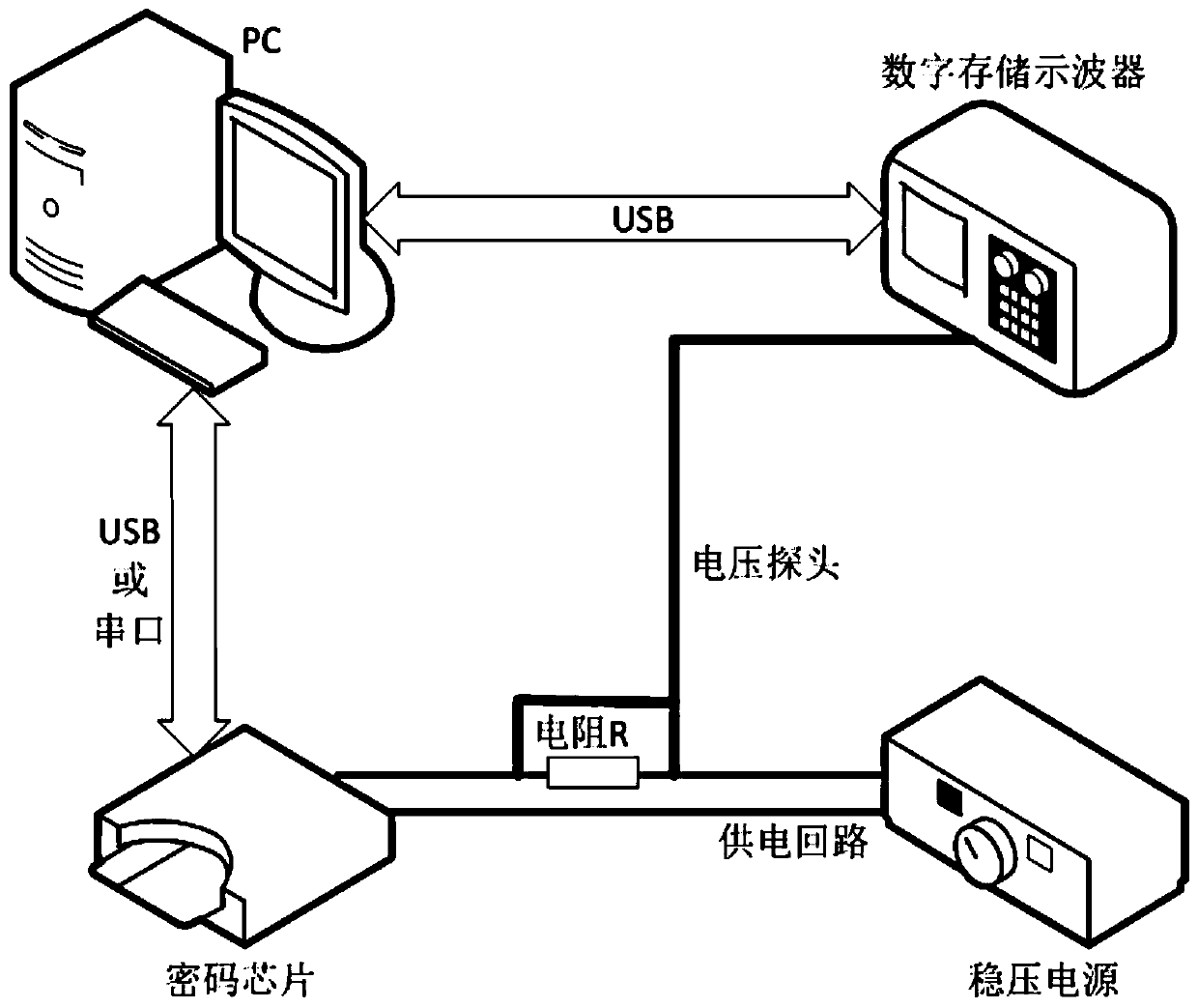
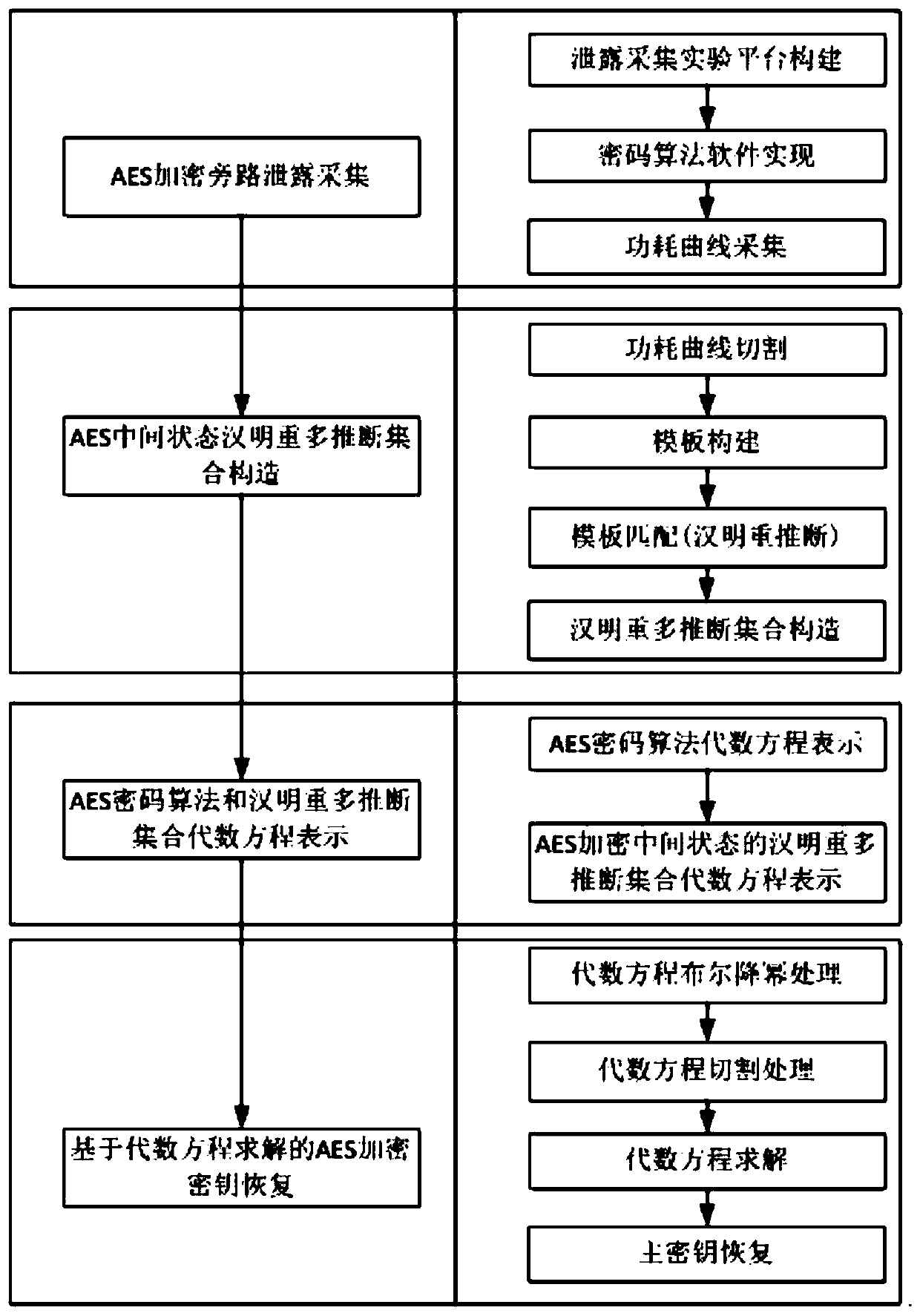
[0045] The invention discloses a block cipher fault-tolerant algebraic bypass analysis method based on multi-inference utilization. The method constructs an encryption intermediate state based on multiple power consumption traces in the block cipher encryption process performed by a controlled cipher chip when the key is known. The power consumption trajectory template corresponding to the Hamming weight candidate value; use the power consumption trajectory template and a power consumption trajectory in the block cipher encryption process of the cryptographic chip to be attacked to obtain the Hamming multiple inference value set of the encryption intermediate state; The block cipher algorithm and the Hamming multiplicity inference value set are expressed by algebraic equations; the algebraic equations are solved by using a parser to recove...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com