Ring arithmetic method, system, and apparatus
a ring arithmetic and operation technology, applied in the field of ring arithmetic operations, can solve the problems of increasing vulnerability, symmetric encryption is vulnerable, and many security challenges
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
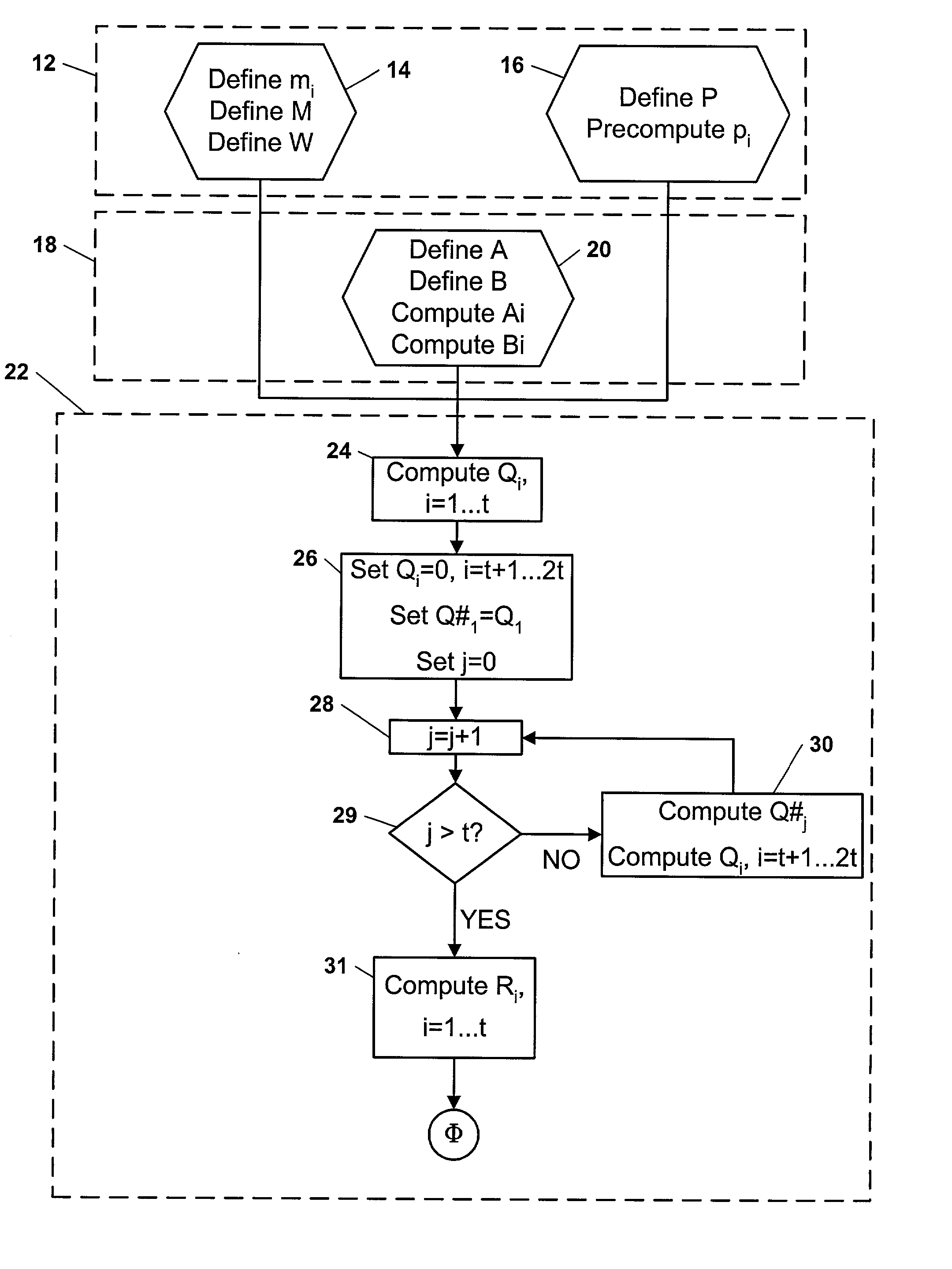
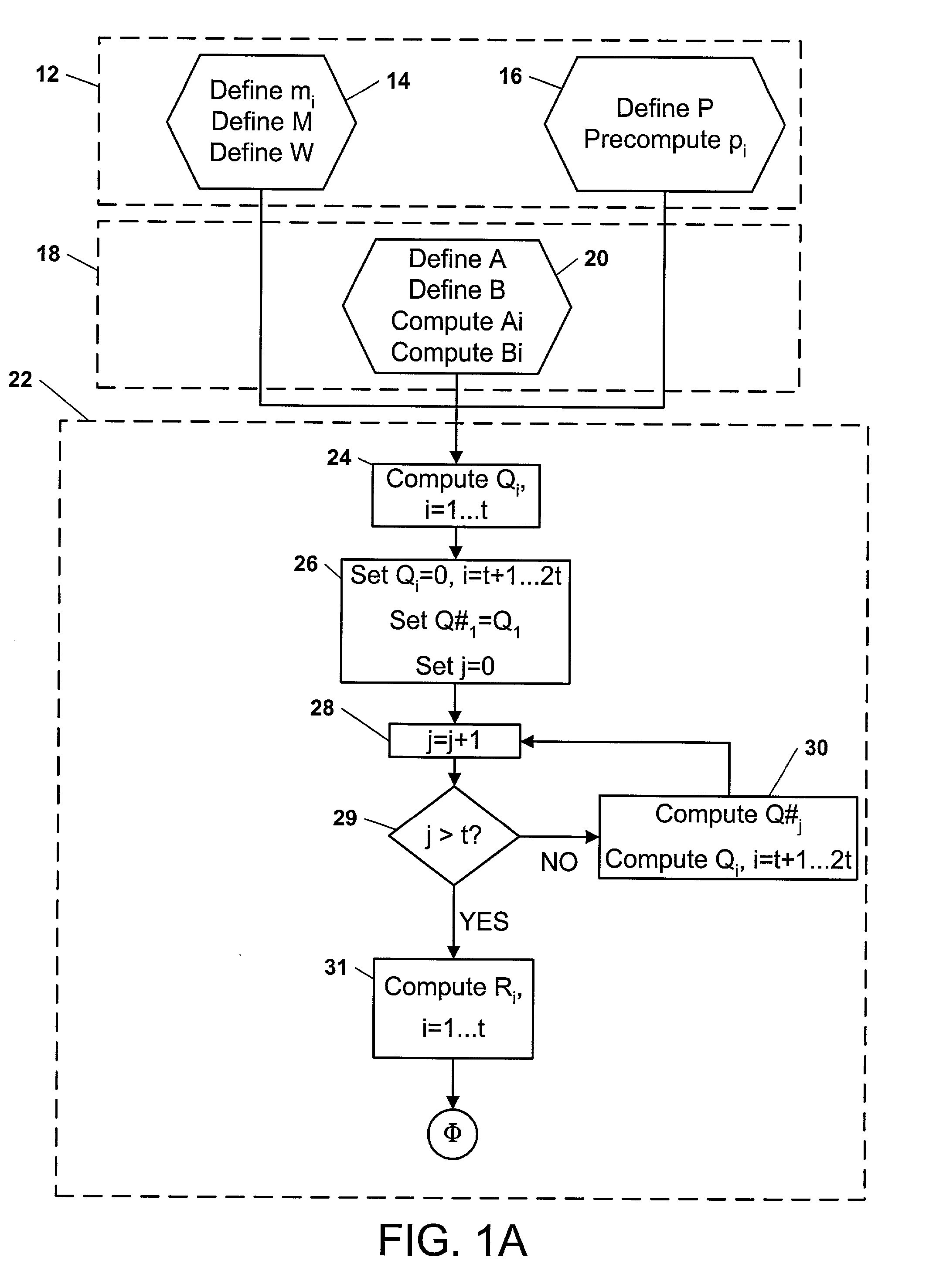
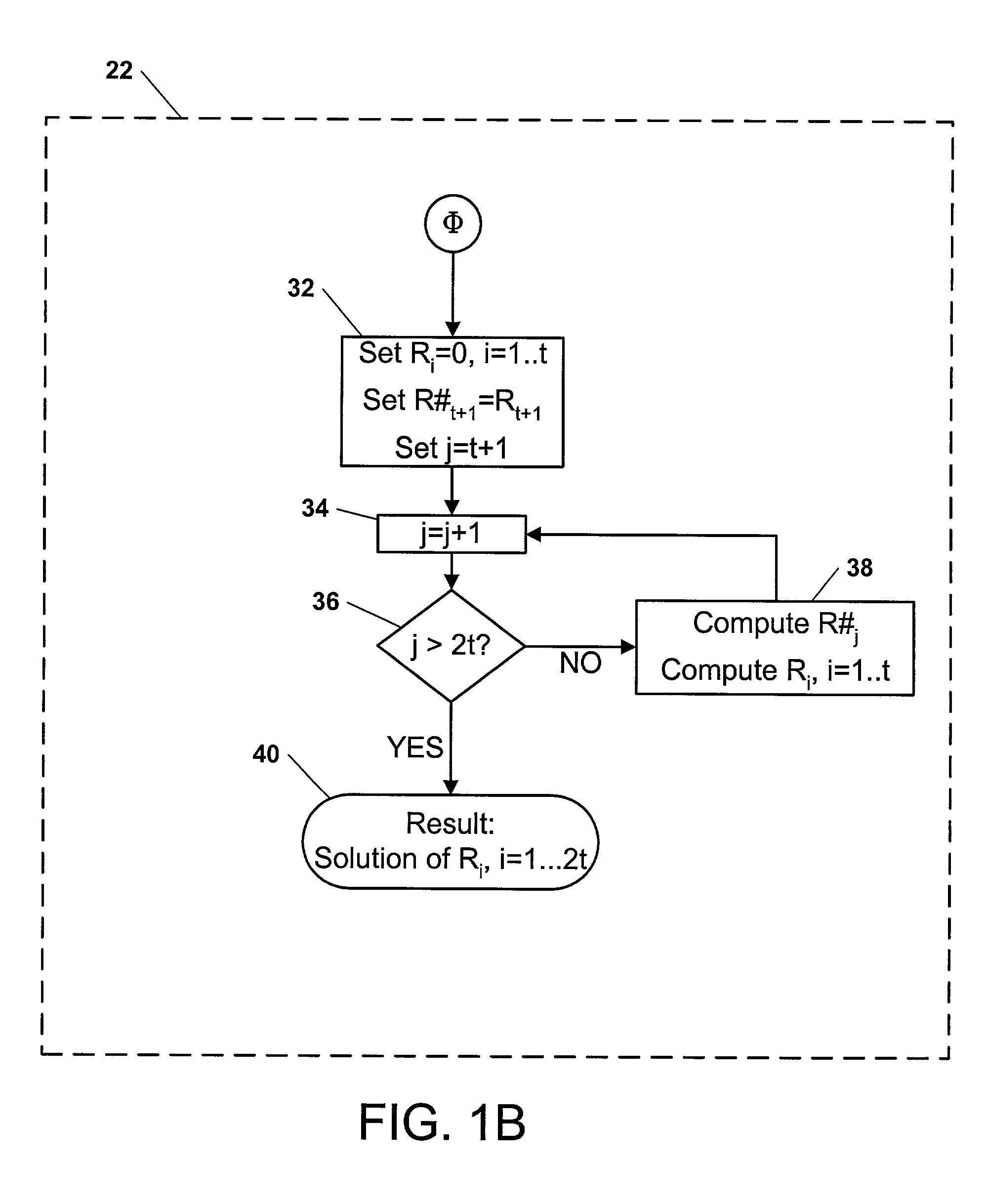
[0137] A factor in slowing some public-private key cryptosystem processes is their requirement for modular exponentiation of large numbers. Even though this description most thoroughly focuses on encryption / decryption embodiments, many other embodiments are contemplated. Examples of other embodiments--readily apparent to typical practitioners of this technical area--include (1) tomography / transforming data, (2) decryption / encryption, (3) keyless encryption, (4) combination transforming / detransforming, (5) random number generation / monte carlo, (5) simulation of real-life scenarios, etc. Those applications typically require heavy exponentiation and for that and other reasons would be particularly well adapted to application of the present invention.
[0138] In an embodiment, shotgun multiplication is used to facilitate high security log-ins that use high-degree-sparse polynomials. One example is Purdy. See G. B. Purdy, "A high security log-in procedure", Communications of the ACM, 17 (1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com