Hardware security assessment method for chaotic cryptosystem
A chaotic cryptography and hardware security technology, applied in the field of information security, can solve problems related to cryptographic algorithms, small computational complexity, and less research on side-channel attacks of chaotic cryptography systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
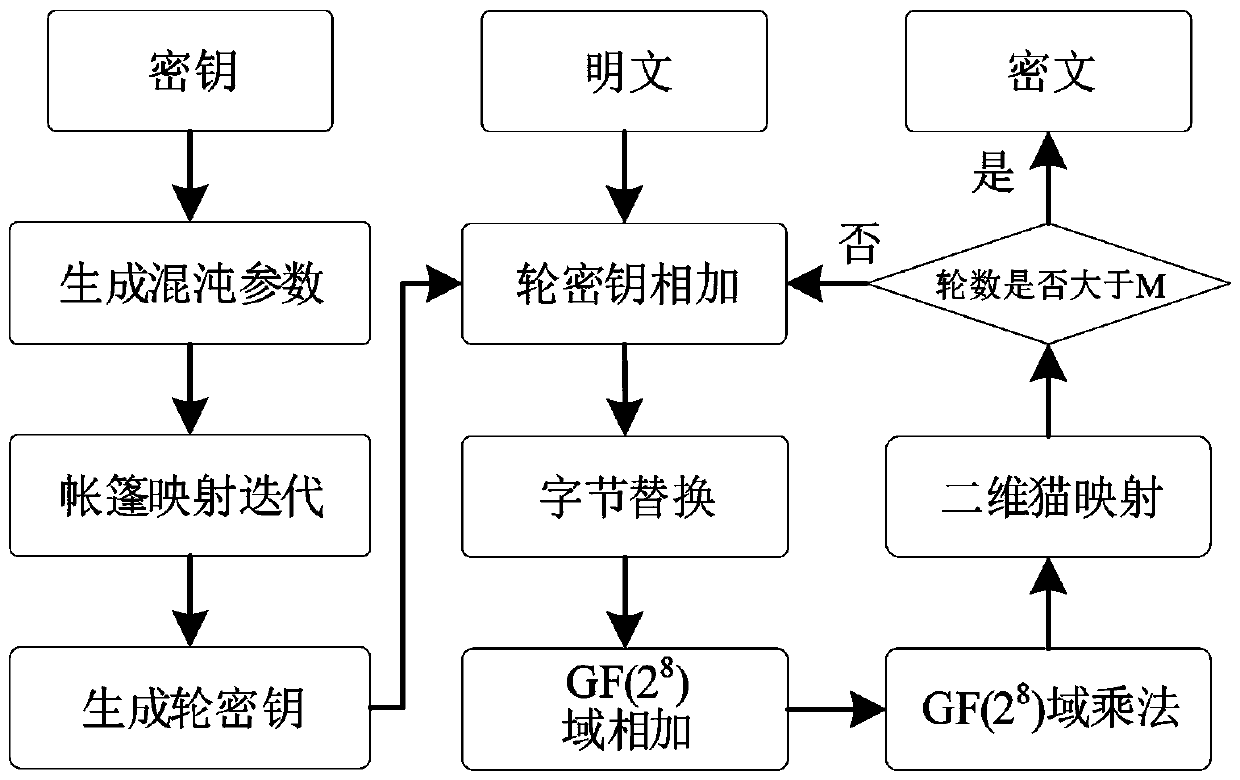
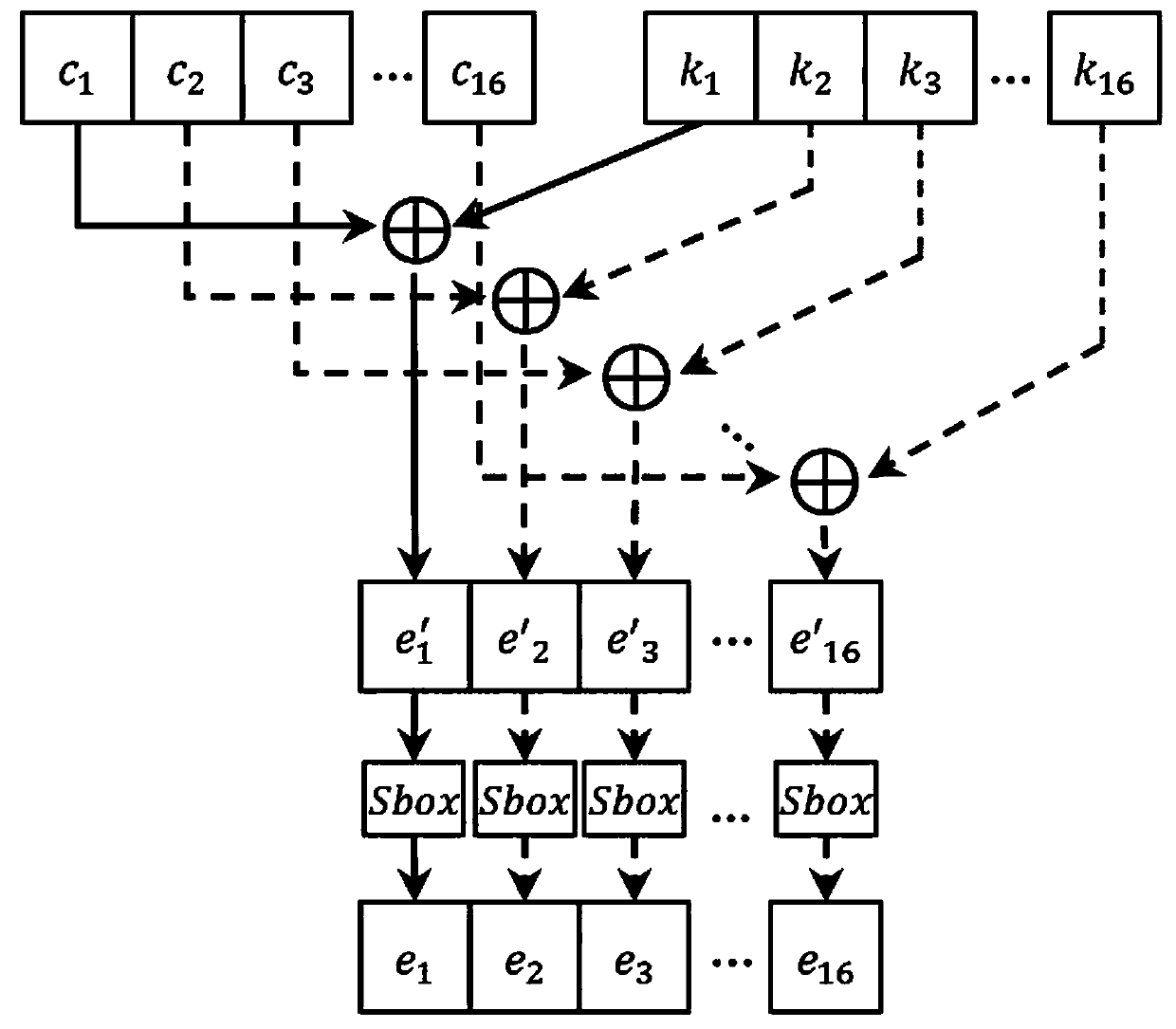
[0061] 1) Analyze the structure of the chaotic block cipher system using the substitution-replacement network structure, and judge the possible bypass information leakage. The work flow of the chaotic block cipher is as follows: figure 1 As shown, each group of plaintext, ciphertext, and key contains 128 bits, and the 128-bit master key is used as the parameter of the tent mapping. The tent mapping is iterated multiple times and mapped to the integer field to generate the round key. In the round key After the addition operation, use the S-box lookup table to perform the replacement operation, and then perform GF(2 8 ) finite field addition, multiplication and cat mapping operations to satisfy the diffusion property, where GF(2 8 ) means 2 8 The finite field of order, and finally repeat these steps M times to ensure security, the specific process is:
[0062] (1) Generate round keys: Assume that the chaotic block cipher process includes M rounds of iterations, and for each it...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com