Quantification and evaluation method for cipher safe chip side channel safe degree
A technology of cryptographic security and security degree, which is applied in the field of quantitative evaluation of cryptographic security chip side channel security degree, and can solve problems such as inability to evaluate the security degree of cryptographic security chip
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
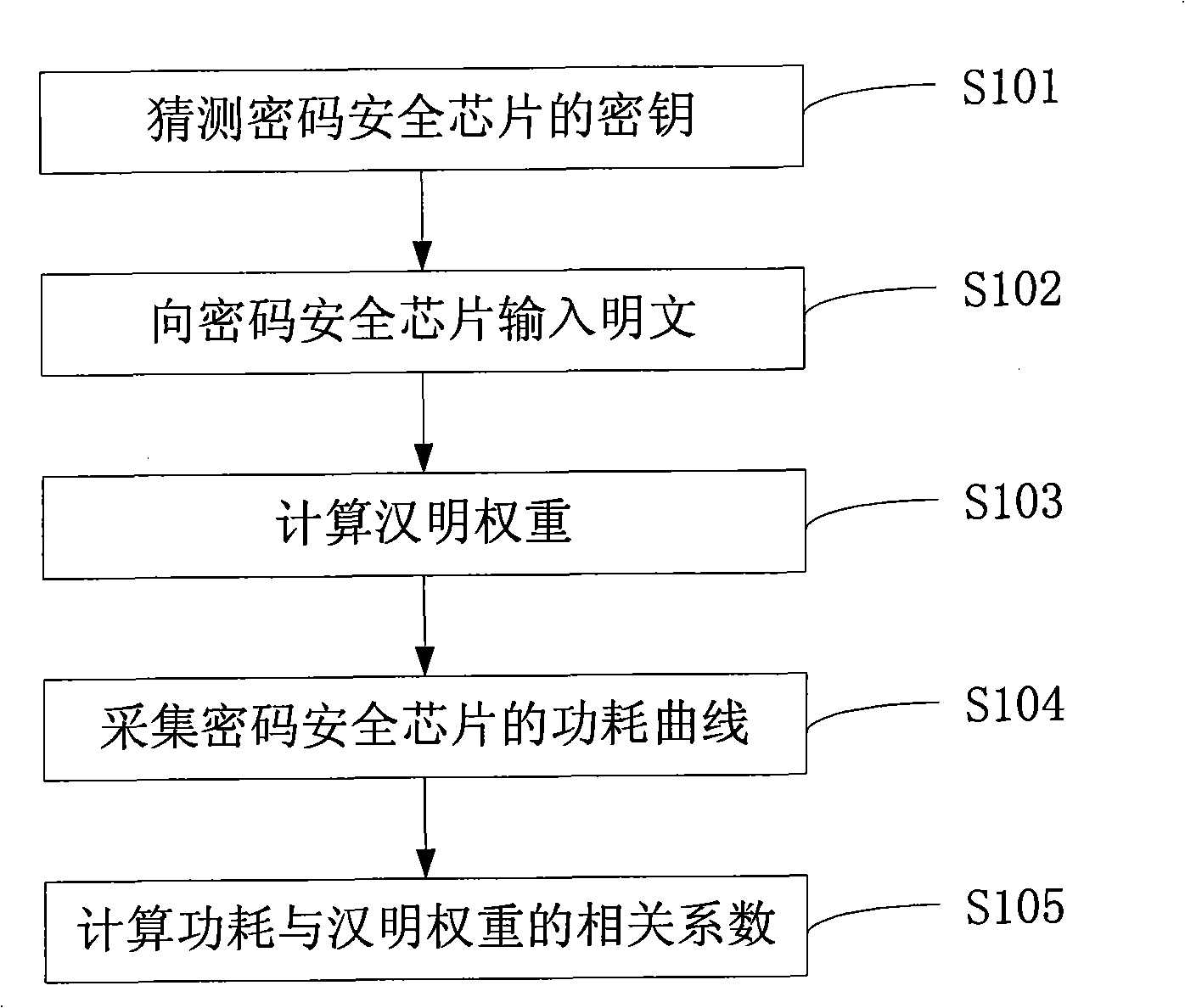
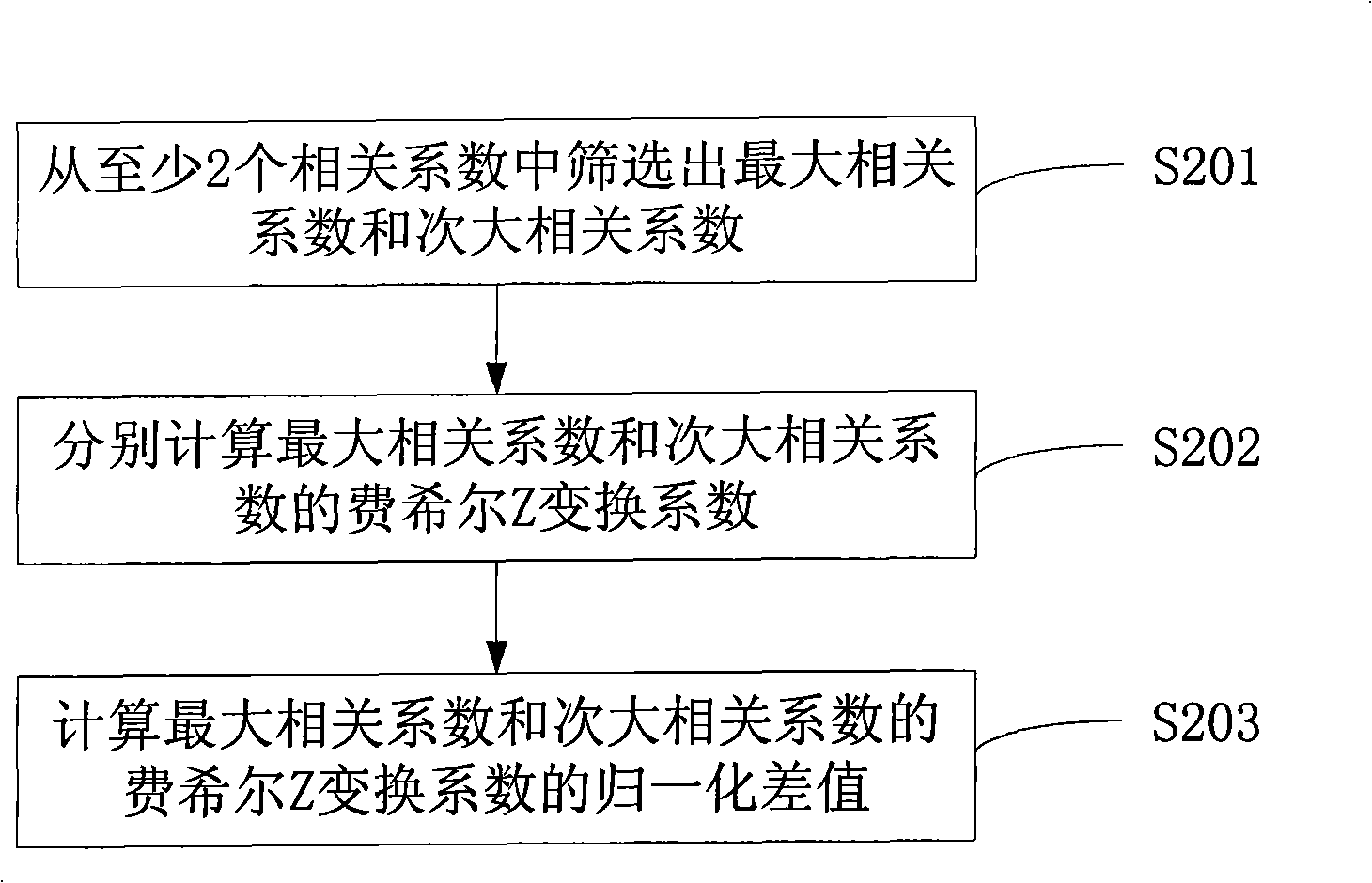
[0025] The quantitative evaluation method for side channel security degree of cryptographic security chip includes: obtaining at least two correlation coefficients between power consumption and Hamming weight; calculating normalized difference; outputting evaluation results.
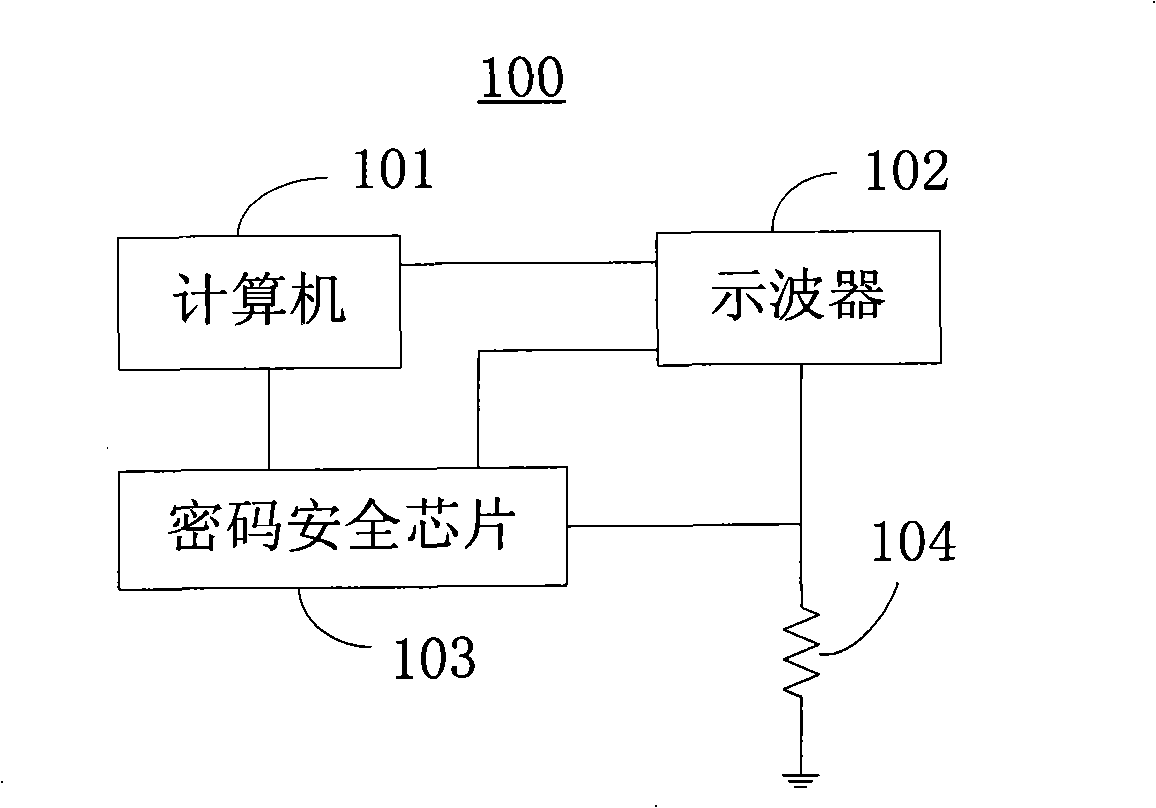
[0026] figure 1 It is a schematic diagram of the system for evaluating the security level of the side channel of the cryptographic security chip. The system 100 for evaluating the side channel security degree of a cryptographic security chip includes a computer 101 , an oscilloscope 102 , a cryptographic security chip 103 and a test resistor 104 . The common ground pin (VSS) of the cryptographic security chip 103 is grounded through the test resistor 104 . The voltage at both ends of the test resistor 104 represents the magnitude of the current flowing from the supply voltage pin (VCC) of the cryptographic security chip 103 to the common ground pin, thereby characterizing the power consumption of the cr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com