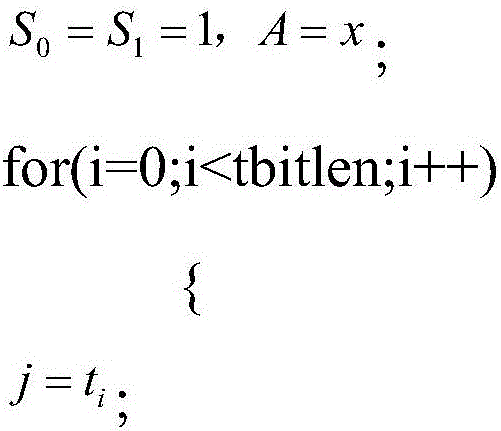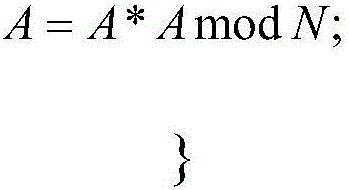Signature method of preventing side-channel attack from multi-azimuth
A channel attack and multi-directional technology, applied in the field of information security, can solve problems such as being vulnerable to attack, attacking, and unable to defend
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] A multi-directional anti-side channel attack signature method and scheme, the common RSA secret key is divided into public key and private key, where e and N are RSA public keys; d and N are RSA private keys.
[0032] The method of common RSA key signature is: Sign(M)=M d mod N. Among them, M is the abstract to be signed entered by the user; N and d are private keys, and N is the modulus.
[0033] Based on the basic modular exponentiation and modular exponentiation check, a multi-directional anti-side channel attack signature scheme is as follows:
[0034] (RSA signature) Sign(M,e,d,N);
[0035] Generate random number trng1, calculate z1=trng1*(e*d-1)-d;
[0036] Generate random number trng, calculate (S 0 ,S 1 )=EXP(trng,z1,N); if return 1, output S 0 , S 1 Continue to execute 3, otherwise return 0 directly without outputting any results;
[0037] Generate random number trng2, calculate z2=trng2*(e*d-1)+d;
[0038] Calculate maskM=M*trngmodN;
[0039] Calcula...
example 2
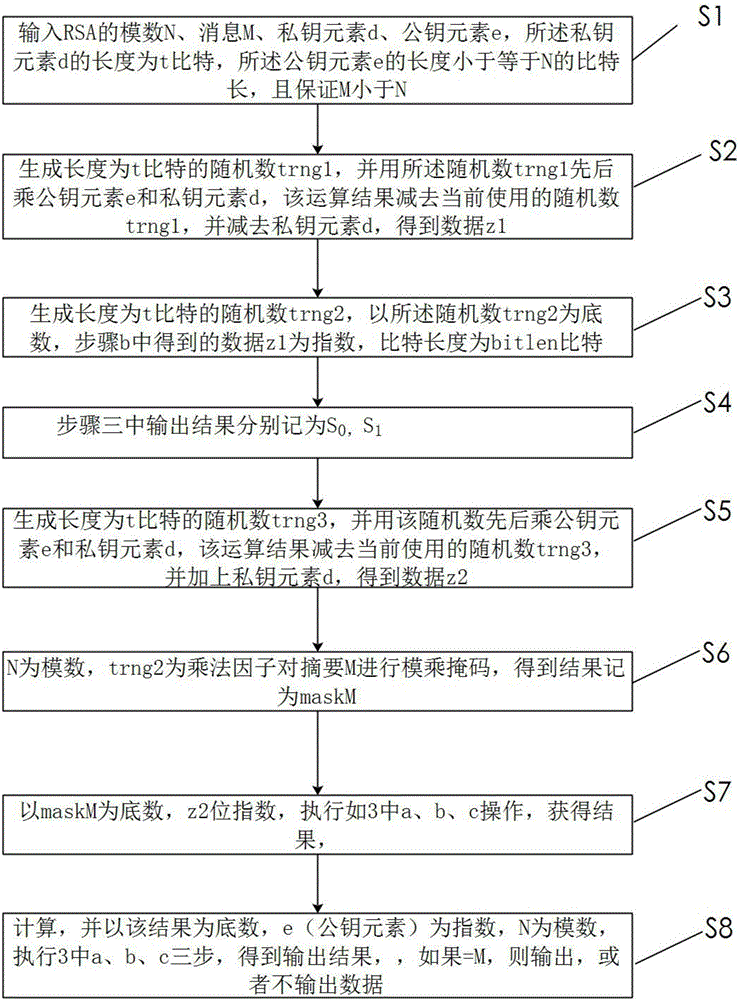
[0061] Input the modulus N of RSA, the message M, the length of the private key element d is t, the length of the public key element e is 32 or less than or equal to the number of bits of N, and ensure that M is less than N
[0062] Generate a random number trng1 with a length of t bits, and use the random number to multiply the public key element e and the private key element d successively, subtract the currently used random number trng1 from the operation result, and subtract the private key element d to obtain the data z1
[0063] Generate a random number trng2 with a length of t bits, take the data as the base, and the data z1 obtained in 2 as the index (its bit length is bitlen bits), and perform the following operations:
[0064] Set 3 blocks (respectively S 0 , S 1 , A) space of t bits, the three spaces are respectively assigned; S 0 = S 1 = 1, A = trng2
[0065] b. i performs the following process from 0 to bitlen:
[0066] ① Obtain the current bit value of z1
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com