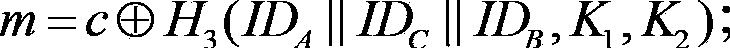Method and system for certificateless and pairing-free identity-based proxy signcryption
A proxy signcryption, certificateless technology, applied in the field of cryptography, can solve the problem of no pairing identity-based proxy signcryption scheme, no certificate, etc., and achieve the effect of solving the problem of key escrow
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
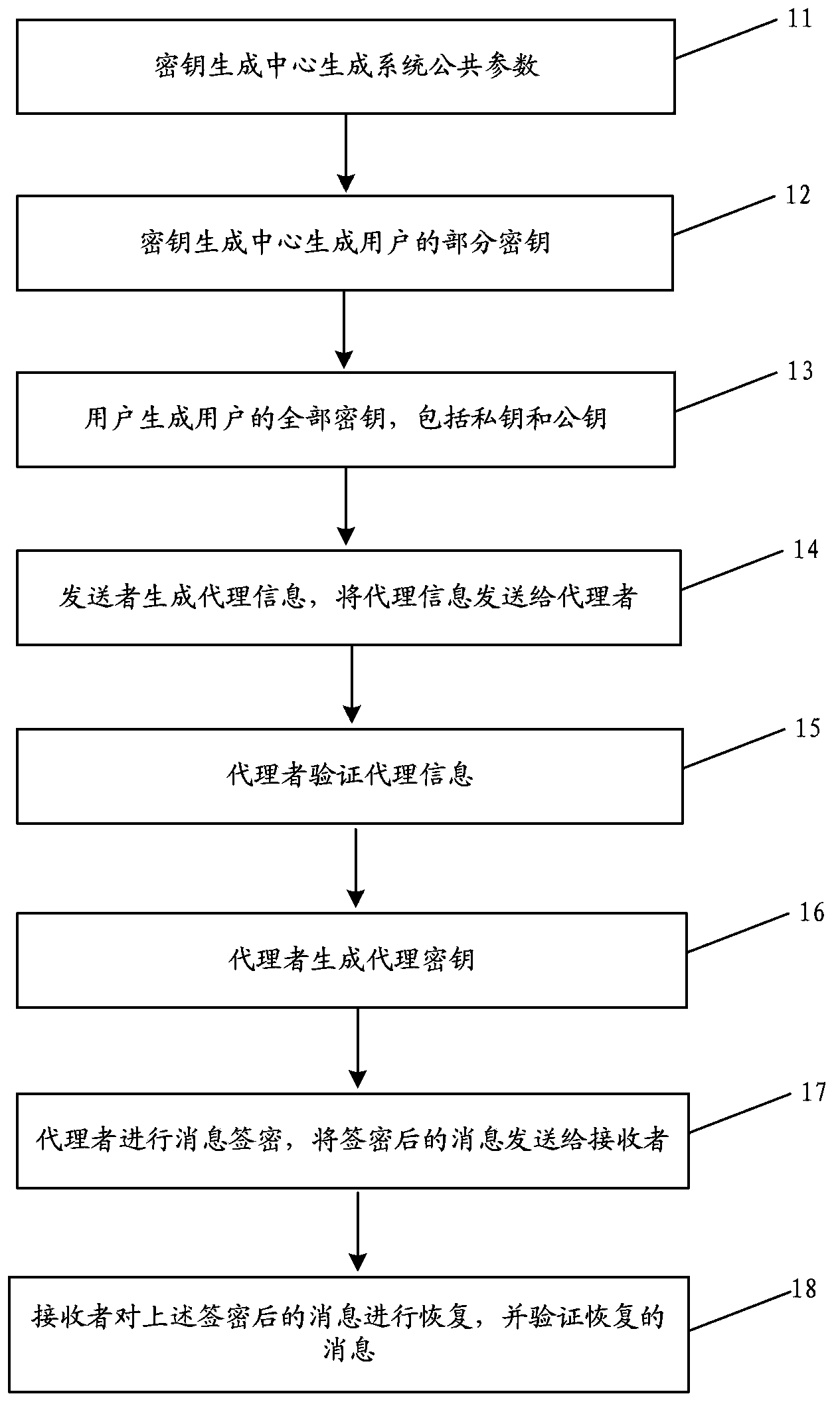
[0022] The entities involved in the technical solutions described in the embodiments of the present invention are as follows:
[0023] (1) Key generation center: The key generation center is responsible for generating system parameters based on security parameters, selecting the master key, and combining the user's identity to generate the user's partial key, and send the partial key to the user through a secure channel.
[0024] (2) Sender: The sender verifies some of its keys and generates all of its keys. Combined with the agent's identity, use the private key to generate proxy information, and send the proxy information to the proxy.
[0025] (3) Proxy: The proxy verifies some of its keys and generates all of its keys. Receive the proxy information, verify the proxy information, and after the verification is passed, combine the identity of the sender, use your own private key, generate a proxy key, and use the proxy key, combined with the identity of the receiver and the ...
Embodiment 2
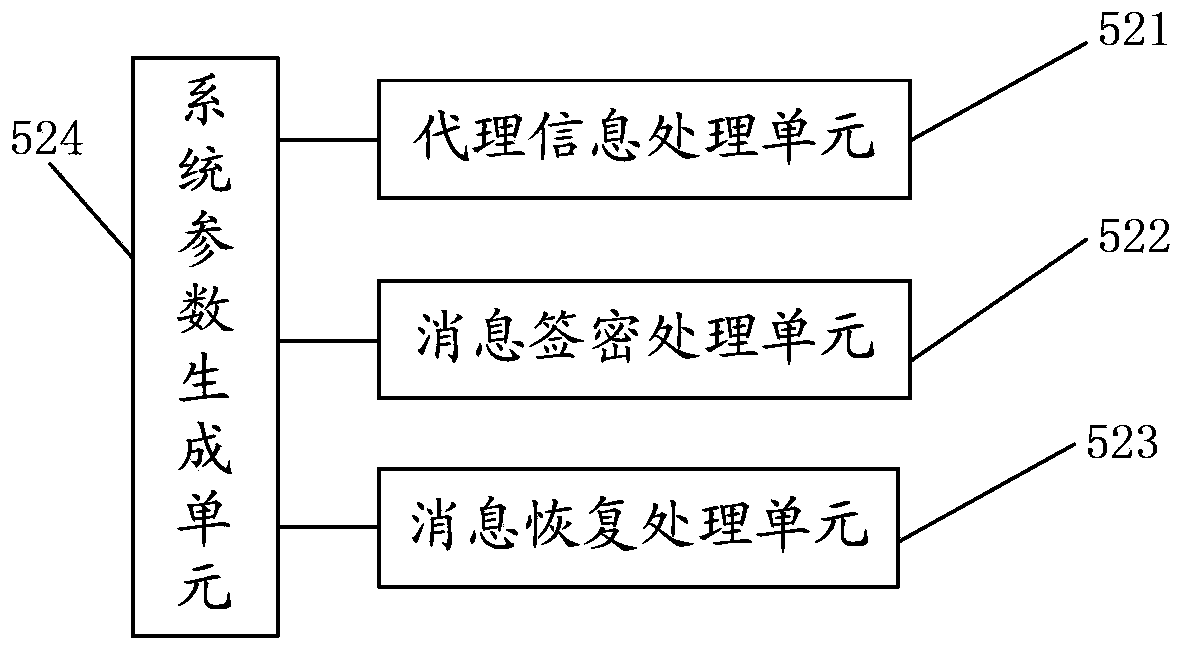
[0067] The specific structural diagram of a certificateless and pairless identity-based proxy signcryption system provided by this embodiment is as follows: figure 2 As shown, the following units are included:
[0068] The proxy information processing unit 21 is used to generate the private key and the public key of the sender according to the system public parameters and the identity information parameters of the sender, generate the proxy information with the private key and the public key of the sender, and send the proxy information to agent;
[0069] The message signcryption processing unit 22 is configured to generate a proxy key after verifying that the proxy information is passed by the proxy, and use the proxy key and system public parameters to signcrypt the message to be sent by the proxy Processing the signcrypted message and intermediate parameters obtained, and sending the signcrypted message and intermediate parameters to the receiver;
[0070] The message re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com